A primer on Declarative Device Management for Apple devices
Overview
Omnissa Workspace ONE® UEM provides a comprehensive management solution for iOS and macOS devices, supporting iOS and iPadOS 14 and later, and macOS 11 and later. With the ability to manage Corporate-Dedicated, Corporate Owned, or Employee Owned (BYOD) devices, Workspace ONE UEM offers enterprises the flexibility to meet their employees’ needs at any level.
At Apple’s Worldwide Developer Conference (WWDC) in 2021, Apple unveiled a significant shift in its device management strategy, aimed at enhancing the speed and efficiency of its Mobile Device Management (MDM) protocol. This innovative approach, aptly named Declarative Device Management (DDM), represents a paradigm shift in how Apple manages its devices. This tutorial delves into the intricacies of DDM and provides an overview of its implementation within Workspace ONE UEM.
Purpose of this tutorial
This tutorial introduces Apple’s Declarative Device Management methodology and explores how Workspace ONE UEM is adapting to this new paradigm in device management.
Audience
This operational tutorial is intended for IT professionals and Workspace ONE UEM administrators of existing production environments.
Knowledge of additional technologies such as network, VPN configuration, Omnissa Intelligence, and Workspace ONE® UEM is also helpful.
Declarative Device Management
Apple’s Mobile Device Management (MDM) protocol for managing macOS, iOS, and iPadOS devices has long been considered an imperative process. The requirement for the MDM servers to routinely poll devices for status, push changes to devices, and essentially “micromanage” the execution of every action or command on devices has long been the norm. This reactive management paradigm results in multiple round trips between the MDM server and the device, potentially creating performance bottlenecks when running at scale across thousands or tens of thousands of devices.
For instance, an administrator creates an assignment to deploy an app to all corporate owned iOS devices being managed by MDM. Using Apple’s existing MDM protocol, the MDM servers would send the command to each device. Each device would return its own acknowledgement of the command. Then, the servers would poll each device to check on the status of the app installation. Each device would respond with a status update indicating that the app is installing. The server would again poll each device for a status on the app installation. This cycle would continue between each device and the servers until each device returns a status that states that the app has been installed.
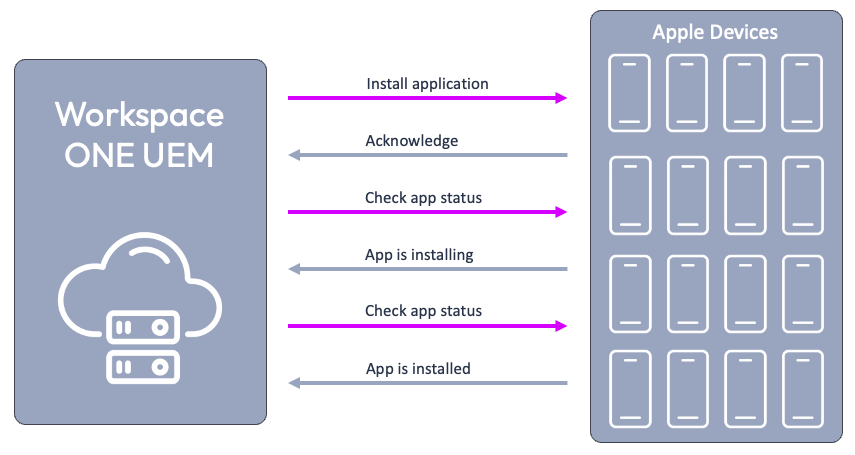
This back and forth between the servers and a device may not seem like much. But consider for a moment the impact that these roundtrips to thousands of devices might have on the MDM servers.
Apple is constantly striving to enhance its device management features and functionality, as well as optimize the performance and scalability of its Mobile Device Management (MDM) protocol. During Apple’s Worldwide Developers Conference (WWDC) in 2021, Apple unveiled a significant paradigm shift in their MDM protocol, which they refer to as Declarative Device Management.
Declarative Device Management
Declarative Device Management (DDM) shifts the responsibility of policy management from MDM servers to individual devices. Each device operates autonomously, applying management logic in response to its own state changes. Proactively, the device reports significant state changes to MDM servers, eliminating the need for constant polling. A key advantage of Apple’s DDM is its integration with the existing MDM protocol, allowing seamless coexistence with legacy MDM functionality. This enables companies to maintain their existing user and device profiles alongside new DDM declarations and configurations. Consequently, IT administrators can transition to DDM more easily by gradually adopting the new paradigm rather than undergoing a complete migration at once.
Apple’s objective with declarative device management is to enhance the experience of managed device users, reduce the repetitive tasks typically performed by IT administrators, and empower devices to control their own managed state. This declarative approach ensures that IT administrators can be confident that their devices are in the desired state and remain in a secure state that safeguards organizational data even when connectivity to the MDM servers is lost. For device users, declarative device management provides a more responsive and reliable experience, including faster onboarding and improved organizational support.
DDM enhances performance and scalability by minimizing the number of roundtrip commands between MDM servers and devices. For instance, in the context of app installation, an IT admin creates a declaration to install an app on all corporate-owned iOS devices managed by MDM. Through the DDM process, MDM servers transmit the command to each device, which then responds with its acknowledgment. This is where DDM distinguishes itself from the traditional MDM mechanism. The device executes the installation command as instructed by the server. Unlike our previous example, MDM servers don’t continuously monitor the device for updates on the installation progress. Instead, they wait for the device to provide an acknowledgment that the app has been successfully installed.

Declarative Device Management components
Declarative device management consists of three primary pillars, which are further discussed in this section.
- Declarations – The payloads that the server defines and sends to devices. Think of these as the existing profiles you currently use in your environment.
- Status – A communication channel used by the device to proactively update the MDM server with new information about itself.
- Extensibility – A mechanism built into DDM to allow devices and MDM servers to seamlessly support new features as they are released.
Declarations
Declarations are the policies and configurations that your organization wishes to enforce on iOS and macOS devices. These can include, but are not limited to, email account configuration, passcodes, and restrictions. Like profiles, declarations are dictionaries that contain sets of keys and standard types for values that represent the payload to be applied to the device.
There are four types of declarations:
Configuration – Configurations represent the policies to be applied to the device. These are similar to current profile payloads.
Asset – This new concept with DDM provides ancillary data required by configurations. An asset references data, such as user identity or certificates. Assets can have a one-to-many relationship with configurations, meaning that a credential asset can be referenced by multiple configurations, avoiding the need to replicate the same information in each configuration.
Activation – An activation is a declaration sub-type that is used to determine when to “activate” a configuration on a device. Each activation can be configured with prerequisites or “predicates” that must be met for successful activation of any configurations associated with it. Activations and configurations can have a many-to-many relationship, and all activations associated to a configuration must evaluate to true for the configuration to activate. The MDM server will send all declarations for any device state, and the device will determine which ones to apply based on the activations. For example, an activation might include a predicate that states the OS version must be “iOS 17.” If the OS version does not meet that predicate, the device will not activate the associated configurations.
Management – A management declaration shares general information about the state of the device. This can include details about the organization or the capabilities of the MDM server.
Status
Status, or more appropriately called the Status Channel, is the mechanism used by devices to proactively communicate any updates about their state to the MDM servers. The MDM servers subscribe to specific device attributes, such as serial number, OS version, UUID, and Managed App Install State. These subscriptions are communicated to the device, which then returns an initial status report. Then the device will send an update any time that the subscribed item changes. For example, the MDM server might subscribe to three status items: device operating system version, device type, and device model. The device will send its initial status for each of these items to the MDM server. In this case, the device reports that its operating system version is iOS 16. When the user upgrades the device to iOS 17, the device will report a status change for the operating system version to the MDM server. It will not report a status change for the other two subscription items because they have not changed. This reduces the amount of data sent between the device and the MDM server by eliminating the need to send redundant data that the server already knows.
Extensibility
Apple products are constantly evolving with new operating system versions and new hardware platforms. As new features are released, it is crucial that capability be maintained between differing versions of software, hardware, and MDM servers. With declarative device management, upgraded MDM servers and the devices advertise their supported capabilities so that each knows when it can take advantage of new features. These advertisements from the device include supported payloads, while the server reports its full capabilities through a management declaration. This way, the server can immediately take advantage of new features and payloads on devices.
Supportability
In 2021, Apple initially announced declarative device management support for iOS/iPadOS 15 and later, with plans to expand that support to other Apple platforms and devices. At WWDC 2022, Apple added support for iOS/iPadOS 16, tvOS 16, and macOS Ventura, as well as making DDM available to all device enrollment types, including Shared iPad. These first two years were focused on developing the foundational elements of declarative device management.
In 2023, Apple added new features to declarative device management that include support for watchOS 10 and later, additional core management functionality, and new features for software updates, securing devices, managing apps and credentials, and transition profiles.
The following table outlines the supported versions of Apple platforms in declarative device management.
| Operating System | Supported Versions |
| macOS | Ventura 13 and later |
| iOS | 15 (user enrollment only), 16 and later (all enrollment types) |
| iPadOS | 15 and later |
| tvOS | 16 and later |
| watchOS | 10 and later |
NOTE: This list is valid as of the date the tutorial was published. Check with Apple for the latest supported operating systems.
Using Declarative Device Management with Workspace ONE
Since the initial announcement about Apple’s new declarative device management, Omnissa has been diligently working toward incorporating this new framework into Workspace ONE UEM. With the release of version 2306 in September of 2023, Omnissa announced support for declarative device management for iOS and iPadOS as a tech preview feature. As of version 2406 released in August of 2024, Declarative Device Management support for iOS and iPadOS devices is in general availability in Workspace ONE UEM. Additionally, with the release of 2410, Omnissa added support for macOS in Workspace ONE UEM. With each new release, Omnissa strives to expand our support of DDM in Workspace ONE UEM.
NOTE: Declarative Device Management is part of the new Workspace ONE UEM Modern SaaS Architecture released with v2406. The modern SaaS architecture must be enabled in your environment to use DDM with your Apple devices.
To facilitate the simultaneous utilization of both Apple’s imperative MDM mechanisms and the new DDM commands, Omnissa has introduced a new workflow within the profile-builder user interface. The process for creating a new DDM configuration mirrors the approach taken by IT administrators when creating an imperative profile. However, upon selecting your platform (in this case, iOS), a new screen will appear, presenting the option to opt for Imperative management or Declarative management. By choosing Imperative, you can then select either Device or User context for the profile and proceed with the creation process as usual.
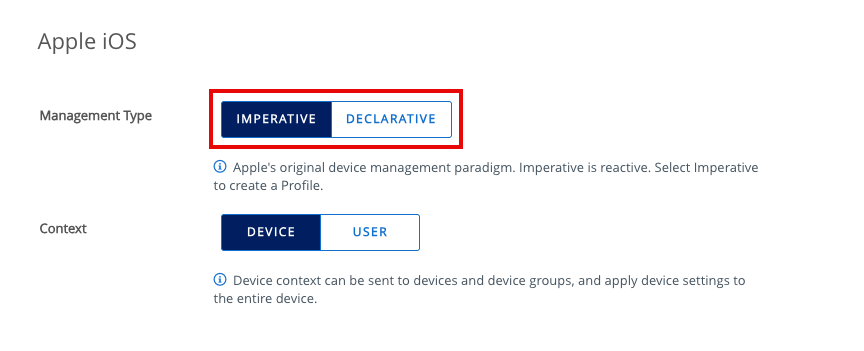
This is where the process for configuring the two management types diverges. If the Declarative management type is selected, you are given the option to create an asset or a configuration. If you choose to create a configuration, you will also be given the option to select a context, either Device or User.
NOTE: For iOS, you will only be given the option to select Device context.
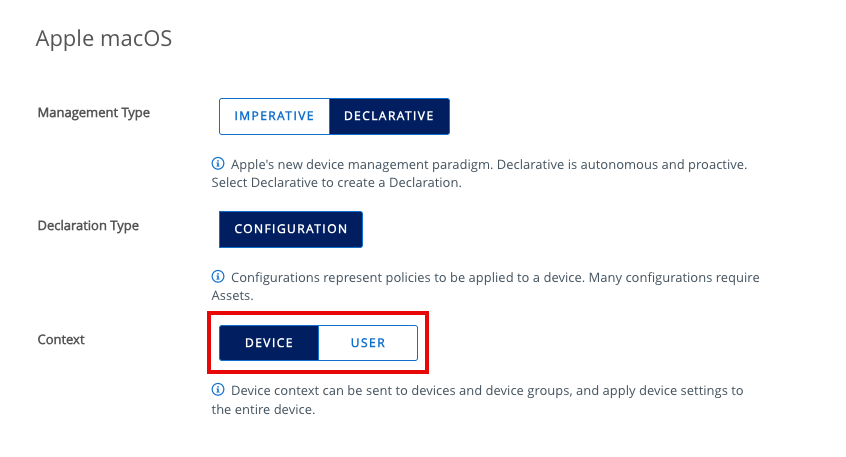
The rest of the process is similar to creating an imperative profile. The screens for configuring required payloads and assigning Smart Groups will be familiar to IT administrators who have experience configuring imperative device and user profiles.
The focus of this initial release is on declarations, the first of the three pillars in declarative device management. Specifically, Workspace ONE provides support for Configurations and Assets.
NOTE: This document will be updated as new supported DDM features are added to Workspace ONE UEM.
Supported configurations
In this release, Workspace ONE UEM supports the following configurations for iOS, iPadOS, and macOS.
| Declaration | Supported OS | Description |
| Disk Management | macOS | Restrict access to external and network storage devices. |
| Passcode | iOS, iPadOS, macOS | Configure a password payload to manage such settings as passcode complexity, maximum number of failed attempts, maximum passcode age, auto-lock settings, and others. |
| CalDAV | iOS, iPadOS | Deploy a CalDAV profile to allow end users to sync corporate calendar items. |
| CardDAV | iOS, iPadOS | Deploy a CardDAV profile to allow end users to sync corporate contacts. |
| LDAP | iOS, iPadOS | Configure an LDAP profile to allow end users to access and integrate with your corporate LDAPv3 directory information. |
| Subscribed Calendar | iOS, iPadOS | Push calendar subscriptions using the native Calendar app in macOS to iOS devices by configuring this payload. |
| Exchange | iOS, iPadOS | Configure devices to check into your mail server to sync email, calendars, and contacts. |
| iOS, iPadOS | Configure an email profile to configure email settings on the iOS device. | |
| iOS, iPadOS | Enable an end user to use their Google account on their iOS device Native Mail application. | |
| Audio Accessory | iOS, iPadOS | Manage audio accessory pairing on an iOS device. Requires iOS 26 or higher. |
| Math Settings | iOS, iPad OS | Configure the calculator app on iOS 18 or higher. |
| Screen Sharing | macOS | Manage screen sharing on macOS devices, including the maximum number of displays and copying files to and from the host device. |
| Safari Settings | iOS, iPadOS | Manage Safari browser settings on iOS 26 or higher devices. |
| Safari Extension Settings | iOS, iPadOS | Configure allowed and denied Safari extensions on iOS devices. |
| Software Update Enforcement | iOS, iPadOS, macOS | Forces a device to update to a specified OS version at a specific date & time. |
| Software Update | iOS, iPadOS, macOS | Manage the settings for the Software Update Utility in iOS. |
Supported assets
In this initial release, Workspace ONE UEM supports the User Identity Asset for iOS and iPadOS. This asset can be used to define a user’s full name and email address. This asset type takes the per-user data out of configurations and moves it into a smaller, dedicated asset-type declaration. This single asset type can be referenced by multiple configurations, eliminating the need to duplicate the same information across those configurations. Any required change to the user credential can be done on the asset only without the need to update the referencing configurations.
Omnissa plans to incorporate additional asset types in future releases.
Summary and additional resources
This tutorial provided an introduction to Apple’s new Declarative Device Management methodology and discussed how Workspace ONE UEM is changing to incorporate this new paradigm in device management.
Among the items discussed were:
- An introduction to Declarative Device Management.
- An overview of the three main pillars of DDM: declarations, status, and extensibility.
- How Omnissa is incorporating DDM into Workspace ONE UEM.
Additional resources
You may also wish to read these additional operational tutorials from iOS on the Omnissa Tech Zone.
- Managing iOS Updates
- Blocking Unwanted Apps on Managed iOS Devices
- Using Apple Automated Device Enrollment with Workspace ONE UEM
You may also wish to read these additional operational tutorials from macOS on Omnissa Tech Zone.
- Configuring Basic macOS Management
- Getting Started with Freestyle Orchestrator on macOS Devices
- Managing Updates with the macOS Updater Utility
- Distributing Scripts to macOS Devices
- Deploying a Third-Party macOS App
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 12/1/2025 |
|
| 02/14/2025 |
|
| 08/22/2024 |
|
| 05/21/2024 |
|
| 10/24/2023 |
|
About the author and contributors
This tutorial was written by:
- Michael Bradley, Senior Technical Marketing Architect, Omnissa.
Considerable contributions were made by the following subject matter experts:
- Adam Henry, Omnissa alumni.
- Paul Evans, Omnissa alumni.
Questions and feedback
For questions or feedback, send to tech_content_feedback@omnissa.com.

