Enabling BitLocker Encryption to Remote Windows Devices: Workspace ONE Operational Tutorial
Overview
This tutorial helps you to configure remote encryption for Windows 10/11 devices with Omnissa Workspace ONE UEM (unified endpoint management).
In these exercises, we will configure a BitLocker Encryption profile and verify that the profile has been applied to devices.
We will also explore Workspace ONE UEM device compliance and remediation actions; and creating reports, dashboards, and automated action with Omnissa Intelligence.
The steps are sequential and build upon one another. Ensure that you complete the steps in order.
What Is BitLocker Encryption
- Consumer Simple Encryption - When it comes to BitLocker encryption for Windows 10 devices, the security by design approach provides the best user experience. Security by design implements device encryption in a way that feels like a non-disruptive, natural part of the device experience.
- Enterprise Secure Devices - Create a BitLocker encryption profile to keep Windows 10 device data enterprise secure. After the profile is configured, Workspace ONE Intelligent Hub automatically enforces encryption settings as part of the device’s general security posture. Use the Workspace ONE UEM compliance engine to ensure devices remain compliant.
For more information, see Microsoft Docs: BitLocker Overview.
Solving Current Device-Encryption Challenges
Two security principles that are top of mind when dealing with device encryption are least privilege and separation of duties.
Workspace ONE UEM leverages role-based access controls (RBAC) for admins, allowing you to grant access to view recovery keys only to the admins who require access.
In addition to RBAC, Workspace ONE UEM logs each action of viewing a recovery key by each admin to the console event logs, which can also be sent to your preferred Syslog provider. This allows for InfoSec to audit admin access to recovery keys to prevent rogue admins from capturing all recovery keys, for example.
Workspace ONE UEM BitLocker encryption also helps in the following ways:
| Current Device Encryption Challenges | Workspace ONE UEM BitLocker Encryption |
| Additional license costs with third-party tools | Eliminate third-party license cost |
| Another third-party agent for encryption | Single agent for all advanced management capabilities |
| Inability to enforce encryption locally on the device | Local enforcement for off-network & off-domain devices |
| No separation of duties for admins | Granular, role-based access controls |
| Complex management via GPOs/scripts | Simple profile with comprehensive controls |
| Recovery key management | Auto escrowing of recovery keys |
| High help desk costs for end-user recovery | Self-service portal key retrieval |
Note: The Workspace ONE UEM self-service portal for Bitlocker key retrieval does not utilize the OMA-DM protocol, so does not incurs additional Microsoft fees for key retrieval.
Audience
This operational tutorial is intended for IT professionals and Workspace ONE UEM administrators of existing production environments.
Knowledge of additional technologies such as network, VPN configuration, Omnissa Intelligence and Omnissa Workspace ONE UEM is also helpful.
Prerequisites
Before you can perform the procedures in this tutorial, you must satisfy the following requirements. For more information, see the Workspace ONE UEM Documentation and Encryption Profile (Windows Desktop)
Workspace ONE Requirements
Ensure that you have the following Workspace ONE components installed and configured:
- A Workspace ONE UEM tenant with admin access to:
- Enroll a Windows 10/11 device into the Workspace ONE UEM environment.
- Configure and deploy a BitLocker policy.
- Workspace ONE self-service portal URL for retrieval of the recovery keys.
- Workspace ONE Intelligence with admin access to:
- Configure reports, dashboards, and automations.
For more details about BitLocker profiles, see Encryption Profile (Windows Desktop).
Windows 10/11 Device Requirements
On the Windows 10/11 device, check that you have the following components installed and configured:
- Windows Pro, Enterprise, or Education device - enrolled in Workspace ONE UEM.
- For more information, compare Windows 10 and 11 editions, or contact a Microsoft representative.
- Disk with Two partition minimum.
- 350 MB boot partition with the appropriate format:
- NTFS Mode — Use if booting in legacy BIOS mode.
- FAT32 Mode — Use if booting in UEFI mode.
- TPM version 1.2 or later.
- Workspace ONE can provide encryption for devices without TPM. The best practice is to use devices with TPM.
- Meet Windows system requirements for BitLocker.
For additional assistance and information, see:
Enabling BitLocker Encryption with Workspace ONE UEM
Secure your organization’s data on Windows Desktop devices with an encryption profile. The encryption profile configures the native BitLocker encryption policy on Windows devices to ensure that data remains secure.
Configuring BitLocker Encryption in Workspace ONE UEM
Profiles allow you to modify how the enrolled devices behave. This section helps you configure and deploy BitLocker encryption using a profile, and verify that the profile has been applied to the device.
Configuring BitLocker Encryption in Workspace ONE UEM consists of the following tasks:
- Add Windows Device Profile.
- Configure Profile General Settings.
- Configure BitLocker Encryption Settings.
- Configure BitLocker Authentication Settings.
- Configure BitLocker Static Recovery Key Settings.
- Configure BitLocker Suspend.
- Assign and Review BitLocker Profile in Workspace ONE UEM.
Task 1. Add Windows Device Profile
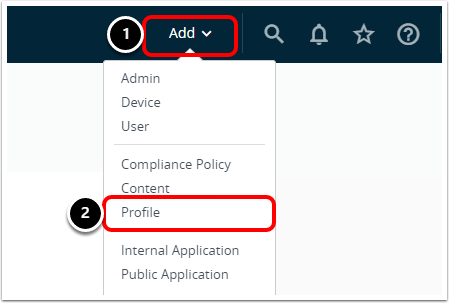
- In the Workspace ONE UEM console, select Add.
- Select Profile.
Task 2. Select the Windows Platform
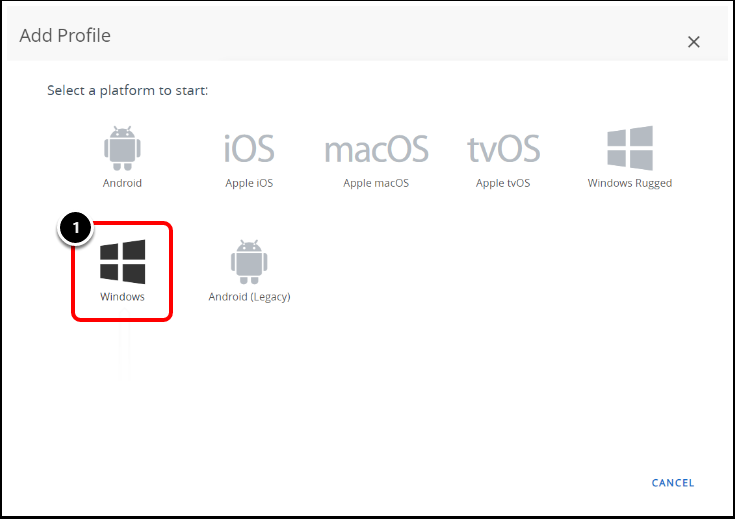

- Select the Windows platform.
- For the Device Type, select Windows Desktop.
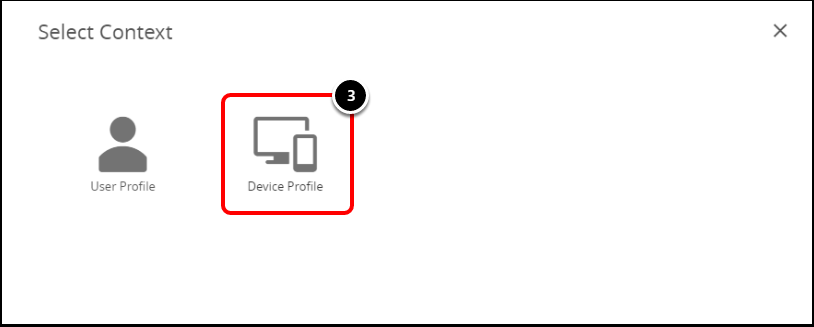
- Select the Context of the profile to Device.
Task 3. Configure Profile General Settings
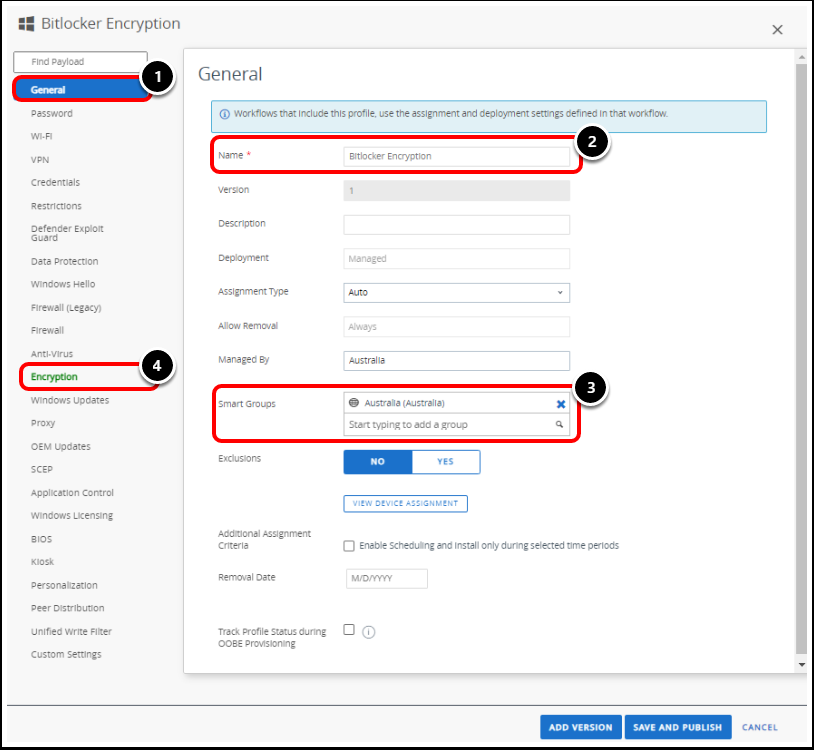
- Select General if it is not already selected.
- Enter a profile name in the Name text box, for example, BitLocker Encryption.
- Click in the Assigned Groups text box.
- This will pop up the list of created Assignment Groups. Select the Assignment Group you want to deploy the profile to.
- Select the Encryption payload and click Configure.
Note: You do not need to click Save & Publish at this point. This interface allows you to move around to different payload configuration screens before saving.
Note: When initially setting a payload, a Configure button will show to reduce the risk of accidentally setting a payload configuration.
Task 4. Configure BitLocker Encryption Settings
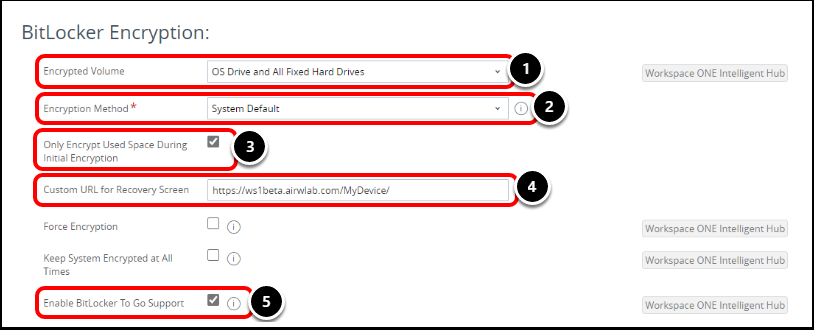
- Select OS Drive and All Fixed Hard Drives from the Encrypted Volume drop-down menu.
- Choosing this option encrypts the entire hard disk on the device, including the System Partition where the OS is installed and any additional drives.
- Leave Encryption Method set to System Default.
- When you select another encryption method such as XTS AES 128 bit from the Encryption Method drop-down menu, another option will appear.
- Use the option Default to the System Encryption Method as a fail-safe for devices that do not support the selected encryption method.
- For example, selecting this setting ensures that Windows 10 1507 and below devices—which do not support XTS encryption—will still get encrypted.
- Enable Only Encrypt Used Space During Initial Encryption to reduce the time required for encryption.
- Important: The drive’s unused space remains unencrypted, potentially placing confidential data at risk.
- Enter the Self-Service Portal URL, https://[Your Device Services Host Name]/MyDevice in the Custom URL for the Recovery text box.
- This URL displays on the lock screen and directs end users to their recovery key.
- Tip: URL shorteners and URL redirections can be used to help users to remember the URL.
- For example https://staff.company.com/mydevice (redirecting to the Workspace ONE UEM Self-Service Portal URL).
- Select Enable BitLocker To Go to enable encryption on removable drives.
Warning:
The Force Encryption setting will force encryption on the device and immediately re-encrypt the device if BitLocker is manually turned off. Be cautious when enabling this setting as it may interfere with BitLocker Suspend functions.
Use the Keep system Encrypted at all times to retain encryption if the profile is removed, the device is wiped, removed from Azure AD, disconnected from Work/School account, deleted from the Workspace ONE UEM console, or the Intelligent Hub is uninstalled. This does not apply to Employee Owned devices.
This means encryption is always set on the device, even when un-enrolled. The device may boot into BitLocker recovery Mode and the BitLocker Recovery Key may need to be entered.
Use these settings in use cases that are purpose-fit for the encryption rules required by your organization.
Task 5. Configure BitLocker Authentication Settings
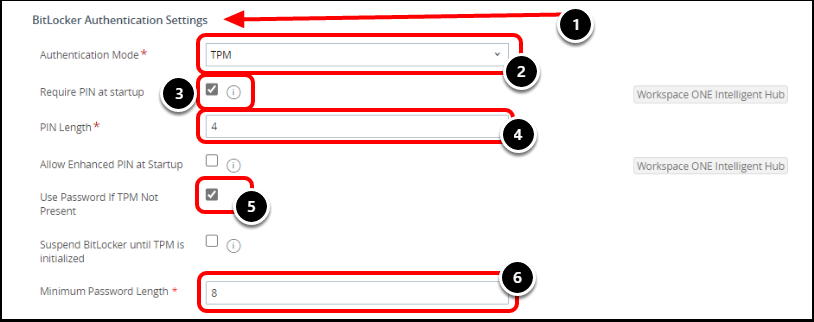
- Using the scroll bar on the right, scroll down to the BitLocker Authentication Settings section.
- Select TPM as the Authentication Mode to use the device’s Trusted Platform Module to authenticate.
- Select Require PIN at startup.
- This option locks out the OS start up and auto-resume from suspend or hibernate until the user enters the correct PIN.
- Specify the Pin Length to match organizational complexity requirements. For example, enter 4.
- Select Use Password if TPM Not Present to use a password as a fallback if TPM is unavailable.
- If deselected, devices that do not have TPM do not encrypt.
- Configure Minimum Password Length to match organizational complexity requirements.
- For example, enter 8. Settings apply to the Password Authentication Mode, and the setting Use Password if TPM Not Available.
Task 6. Configure BitLocker Static Recovery Key Settings
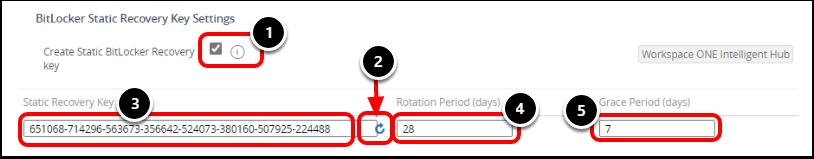
- Using the scroll bar on the right, scroll down to the BitLocker Static Recovery Key Settings section.
- Select Create Static BitLocker Recovery Key to create a shared key for a group of devices. This simplifies key recovery for IT personnel who use the shared key to unlock devices.
- Click the arrow icon to generate a static recovery key.
- Enter 28 or any value greater than 0 into the Rotation Period text box to create a rotation schedule. Enter 0 to opt out of the rotation schedule.
- Enter 7 into the Grace Period text box to specify the number of days after rotation that the previous recovery key still works.
Task 7. Configure BitLocker Suspend
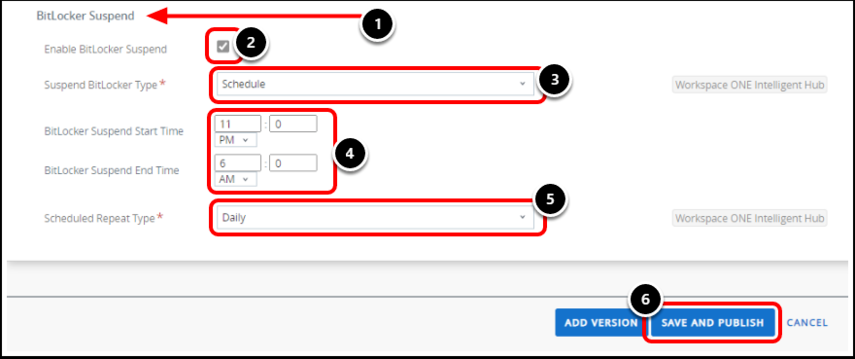
- Using the scroll bar on the right, scroll down to the BitLocker Suspend section.
- Select Enable BitLocker Suspend.
- This suspends BitLocker encryption during maintenance periods and allows devices to reboot without end-user interaction.
- This setting is particularly important for kiosk or shared devices or updating device drivers or some windows updates.
- Select Schedule from the Suspend BitLocker Type drop-down menu. This suspends BitLocker during a specific time period that repeats daily or weekly.
- Enter the suspend start and end time.
- BitLocker Suspend Start Time — Set to 11:00 PM
- BitLocker Suspend End Time — Set to 6:00 AM
- Select Daily from the Scheduled Repeat Type drop-down menu.
- Click Save & Publish, review the devices assigned, and select Publish.
TIP: You can also Suspend BitLocker encryption manually on individual devices from the Device Details Screen in Workspace ONE UEM.
Task 8. Review BitLocker Profile in Workspace ONE UEM
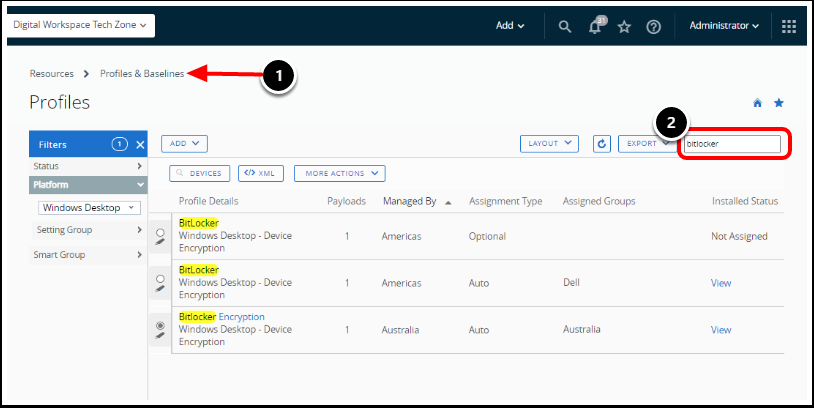
- In the Workspace ONE UEM console, navigate to Resources then Profiles and Baselines, then Profiles.
- Search for the BitLocker Encryption Profile. The BitLocker Encryption Profile now appears in the Device Profiles list view.
Verifying BitLocker Encryption Settings
Now that you have configured and deployed BitLocker encryption using a profile, you verify that the profile has applied to the device.
Confirming BitLocker Encryption consists of the following tasks:
- Verify Encryption Status in the Workspace ONE UEM Console.
- Confirm Encryption in Windows Device Settings.
- Confirm Encryption in Elevated Command Prompt (Optional).
On your Windows 10/11 device, follow the steps to confirm that the encryption settings have applied.
Task 1. Verify Encryption Status in the Workspace ONE UEM Console
There are a few different locations in the Workspace ONE UEM console where you can view the device's encryption details. Let's explore these.
Important:
The Workspace ONE UEM console displays device encryption details specific to BitLocker and not any third-party anti-virus encryption (for example, McAfee).
For details on how to get third-party anti-virus encryption details, we recommend using Workspace ONE Sensors.
Task 1.1. Navigate to Device Details Tab
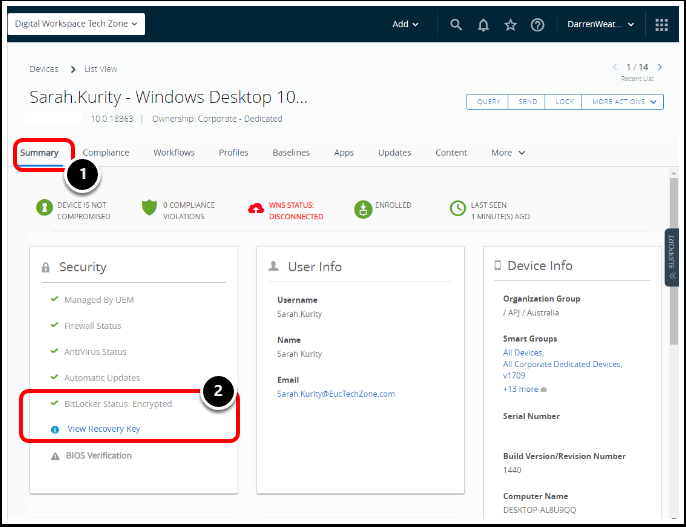
- Select a device in the Workspace ONE UEM console and ensure that you are in the Devices Details view.
- Navigate to the device Summary tab.
- Review BitLocker Status details in the Security section.
Task 1.2. Navigate to Device Security Tab
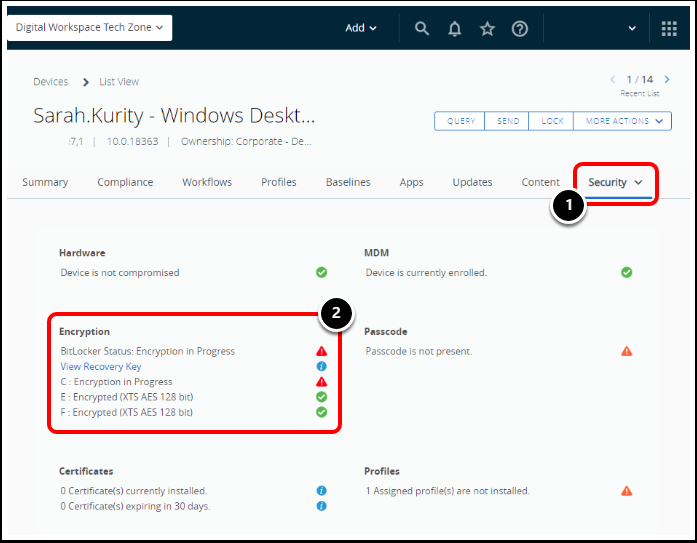
- Navigate to the Security tab. Select it from the drop-down list if necessary.
- Review BitLocker Encryption details and statuses.
Task 2. Confirm BitLocker Encryption in Windows Device Settings
Encryption can also be confirmed on the device itself. The following steps detail how to confirm BitLocker encryption on the device.
Task 2.1. Open BitLocker
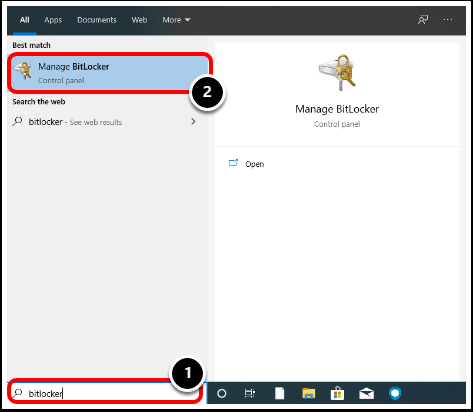
- In the Windows search bar, enter BitLocker.
- Select Manage BitLocker.
Task 2.2. Verify that BitLocker Encryption is Enabled
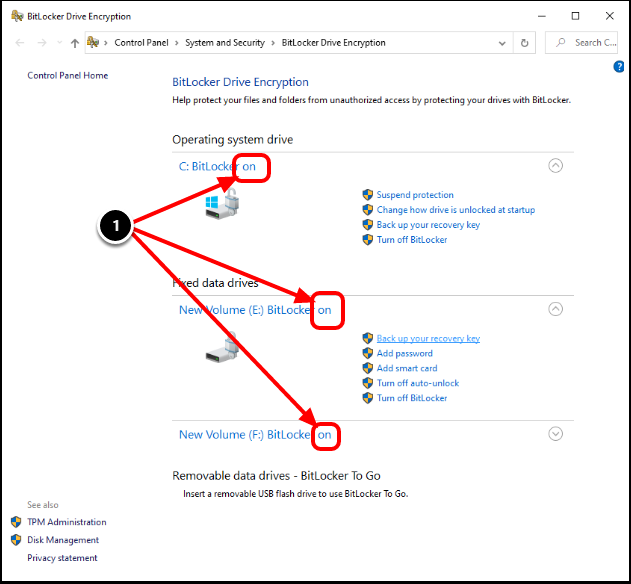
- Confirm that BitLocker Encryption is on or is still currently encrypting.
Task 3. Confirm Encryption in Elevated Command Prompt (Optional)
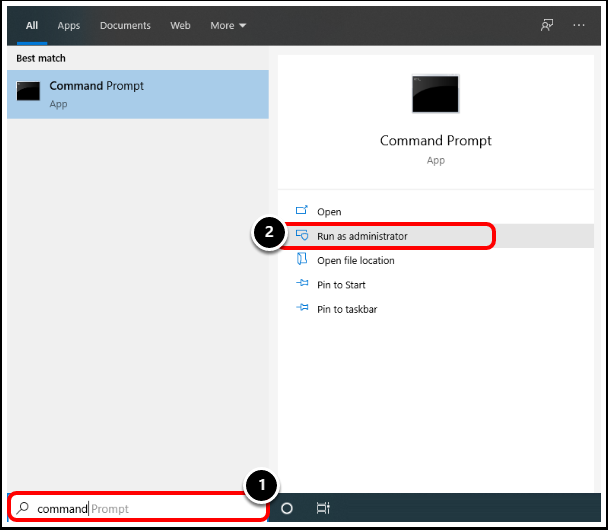
- In the Windows Search bar, enter Command Prompt.
- Select Run As Administrator.
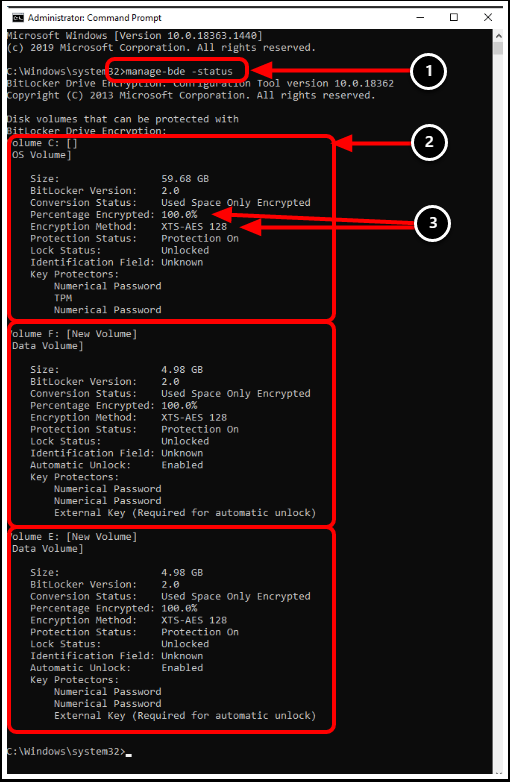
- For a more detailed view, launch an elevated command prompt and enter manage-bde -status.
- Review the Encryption details of each hard drive.
- Review the properties of each status. For example Encryption Method and Percentage Encrypted.
BitLocker Encryption Policy for Multiple Hard Drives
When you are working with a BitLocker encryption policy for multiple hard drives, the encryption method must be the same for all hard drives.
For example:
| ✅ Supported | ❌ NOT Supported |
| ✅ C: Drive using XTS 256 bit & ✅ D: Drive using XTS 256 bit | ❌ C: Drive using XTS 128 bit & ❌ D: Drive using XTS 256 bit |
After you have completed Task 2. Confirm BitLocker Encryption in Windows Device Settings in the Verifying BitLocker Encryption Settings section, perform the following:
Note: BitLocker authentication policies and suspension policies apply to the device, not for each individual drive.
If you set the TPM for BitLocker authentication, it will be used for all encrypted drives.
Review BitLocker Policy
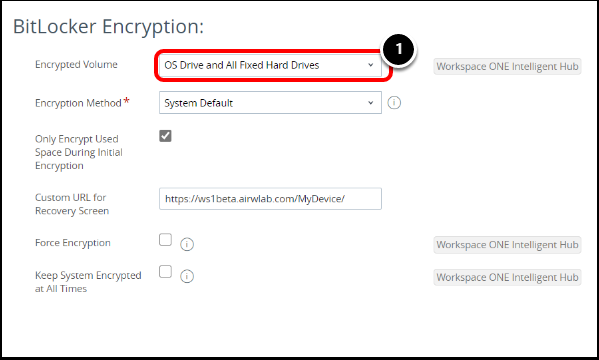
- Review the BitLocker policy and ensure the Encrypted Volume is set to OS Drive and All Fixed Hard drives.
Enabling BitLocker Encryption for Removable Storage (BitLocker To Go)
BitLocker To Go is BitLocker Drive Encryption on removable data drives. This feature includes the encryption of:
- USB flash drives
- SD cards
- External hard disk drives
- Other drives that are formatted by using the NTFS, FAT16, FAT32, or exFAT file system.
When BitLocker To Go is enabled, the Workspace ONE Intelligent Hub will prompt the user to enter in an 8 character minimum password/PIN number to encrypt the removable drive. The removable drive encrypts using AES-128 bit cipher.
In this section, we will cover the following topics.
- How to Enable BitLocker To Go Encryption Settings
- Setting up a BitLocker To Go Pin
- Unlocking BitLocker to Go Devices - Notification Prompt
- Unlocking BitLocker to Go Devices - File Explorer
- Viewing Removable Removable Storage (BitLocker to Go) in Workspace ONE UEM
- Access Recovery Keys for Removable Storage (BitLocker to Go)
- Entering Recovery Keys for Removable Storage (BitLocker to Go)
Task 1. How to Enable BitLocker To Go Encryption Settings
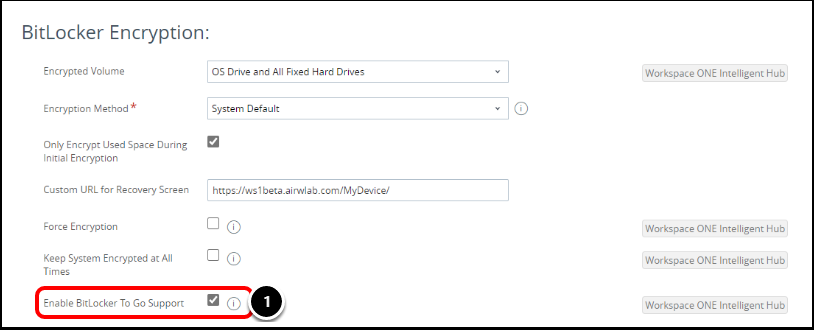
- When configuring a BitLocker profile, ensure to select Enable BitLocker To Go to enable encryption on removable drives.
Task 2. Set Up a BitLocker To Go PIN
When a removable drive is inserted, the Workspace ONE Intelligent Hub detects the removable drive, then:
- The Workspace ONE Intelligent Hub suppresses the Microsoft Wizard for BitLocker to Go
- The Workspace ONE Intelligent Hub will launch the password capture screen
- Screen validates password meets 8 character criteria and inputs match
- The Workspace ONE Intelligent Hub begins the encryption process on Removable Storage Device (BitLocker to Go)
Encryption progress on the local device can be viewed under BitLocker in Windows Control Panel or from Command Prompt by entering the command manage-bde.
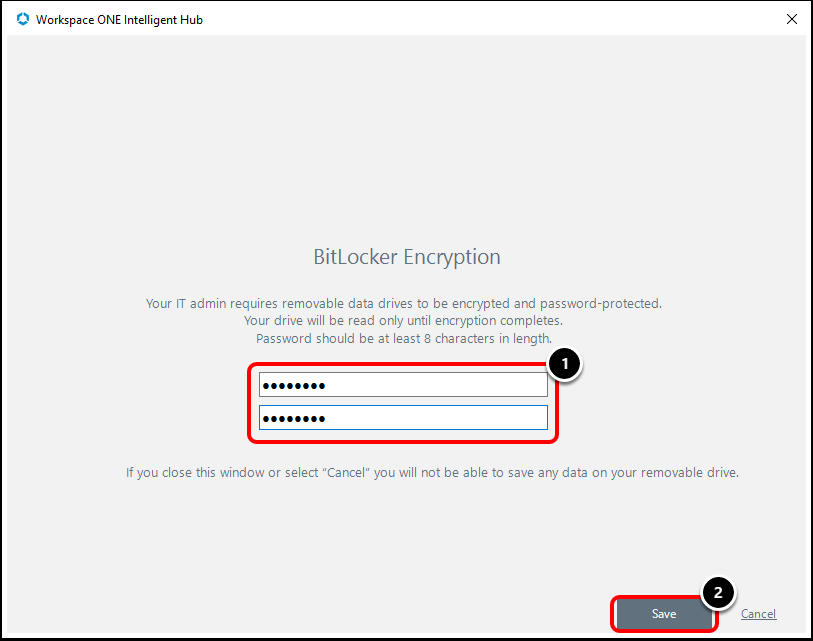
- Enter an 8 character minimum password/PIN number to encrypt the removable drive.
- Click Save.
Task 3. Unlock Removable Storage Devices (BitLocker to Go) - Notification Prompt
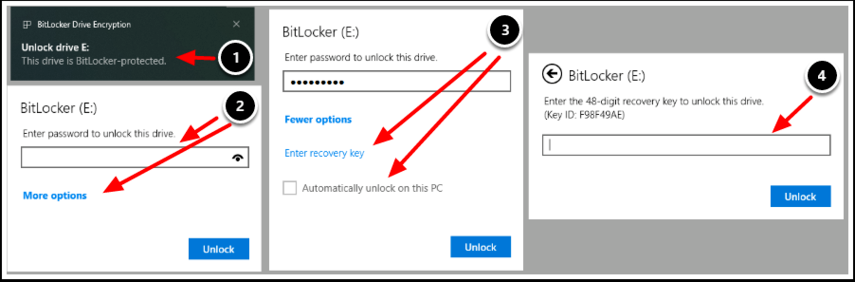
When the Removable Storage Device is inserted into the Operating system, the user will be prompted to enter in the 8 character minimum password/PIN number
- This can be done by clicking on the pop-up notification once the drive is inserted.
- The user can then enter in the password or select More options.
- Selecting More options allows users to Enter in a Recovery Key (Obtained from Workspace ONE UEM via help desk) or select "Automatically unlock on this PC" so they don't always have to enter in the password every time they insert the drive.
- If the user selects Enter in a Recovery Key, the user will be prompted to enter in the 48 digit recovery key after obtaining it from the help desk.
Task 4. Unlock Removable Storage Devices (BitLocker to Go) - File Explorer
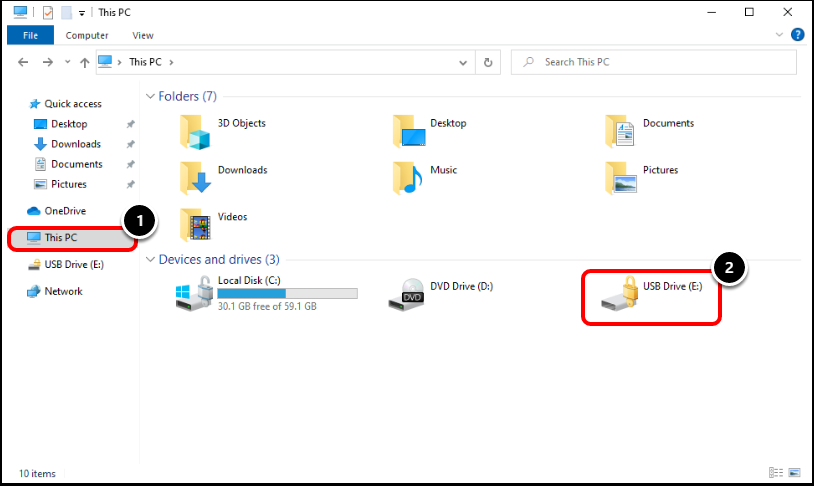
Users can also unlock the Removable Storage Device by opening up File Explorer.
- Ensure you are on This PC.
- When encrypted, the USB device will show with a padlock. Double-click the USB drive to enter in the password and unlock.
Task 5. View Removable Storage (BitLocker to Go) in Workspace ONE UEM
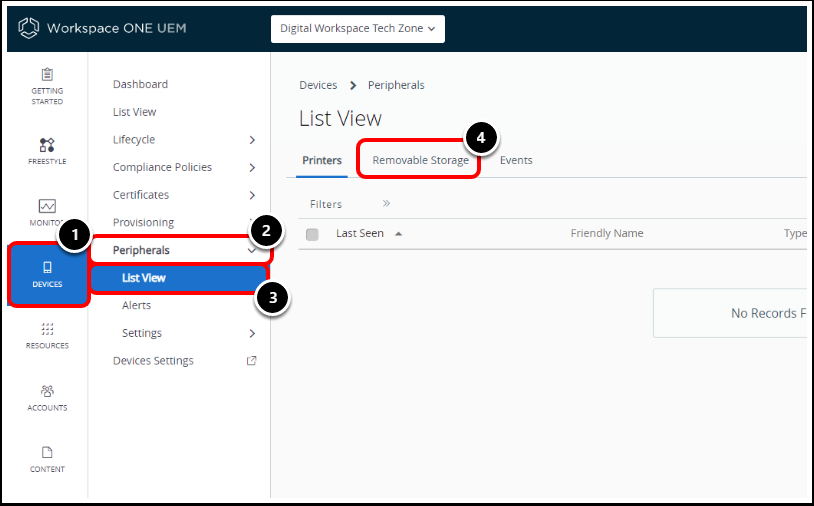
In the Workspace ONE UEM Console
- Navigate to Devices.
- Select Peripherals.
- Select List view.
- Click Removable Storage.
Task 6. Access Recovery Keys for Removable Storage (BitLocker to Go)
You can review all removable drives information fields such as:
- Device Name
- Recovery ID
- Username
- Capacity
- Date Encrypted
- Recovery Key
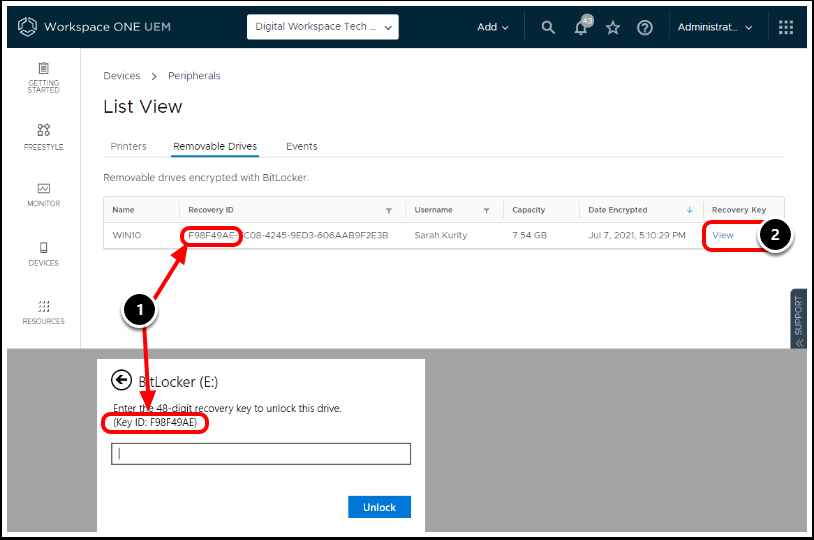
- If the user has forgotten their password and needs to enter in the Recovery Key, the first 8 digits of the recovery ID will be shown to them. The full recovery ID will be shown in the Workspace ONE UEM console.
- Select View to view the recovery key.
Task 6.1. View Recovery Keys for Removable Storage (BitLocker to Go)
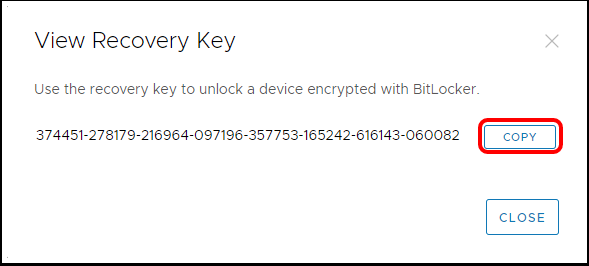
- Select copy to copy the recovery Key to pass on to the end user.
Task 7. Enter Recovery Keys for Removable Storage (BitLocker to Go)
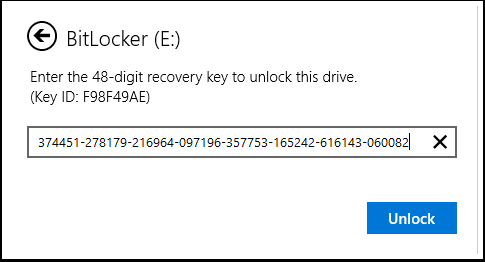
- The user will be prompted to enter in the 48 digit recovery key.
BitLocker Suspend and Resume
Suppose you need to install new software that BitLocker might otherwise block. In that case, you can suspend BitLocker, then resume BitLocker protection on the drive again when you have completed the action during the suspension times.
Suspension of BitLocker does not mean that BitLocker decrypts data on the volume. Instead, the suspension makes the key used to decrypt the data available to everyone in the clear. New data written to the disk is still encrypted.
While suspended, BitLocker does not validate system integrity at start-up. You might suspend BitLocker protection for firmware upgrades or system updates.
For more information, see Microsoft Docs: BitLocker Suspend.
Task 1. Suspend and Resume BitLocker by Policy
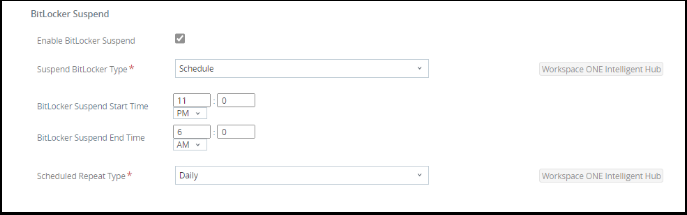
You can configure BitLocker encryption to temporarily Suspend and Resume during a specific time, repeating daily or weekly.
For configuration options, review the Configure BitLocker Suspend section in Configuring BitLocker Encryption in Workspace ONE UEM.
Task 2. Suspend and Resume Bitlocker by Individual device.
You can also temporarily Suspend and Resume for a specific device, specifying the number of reboots before BitLocker is Resumed.
Task 2.1. Select the Device
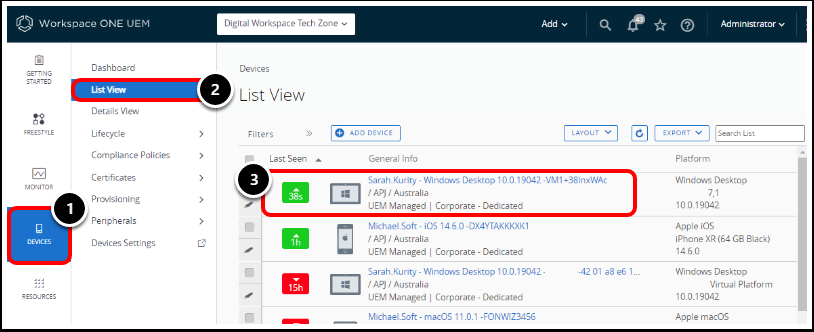
- In the Workspace ONE UEM console, navigate to Devices.
- Select List View.
- Select the device on which you want to individually suspend BitLocker Encryption.
Task 2.2. Suspend BitLocker from Device Details More Actions
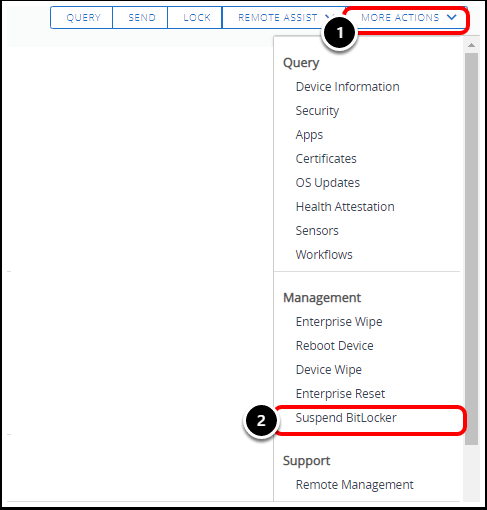
- Click More Actions.
- Select Suspend BitLocker.
Task 2.3. Suspend BitLocker Encryption
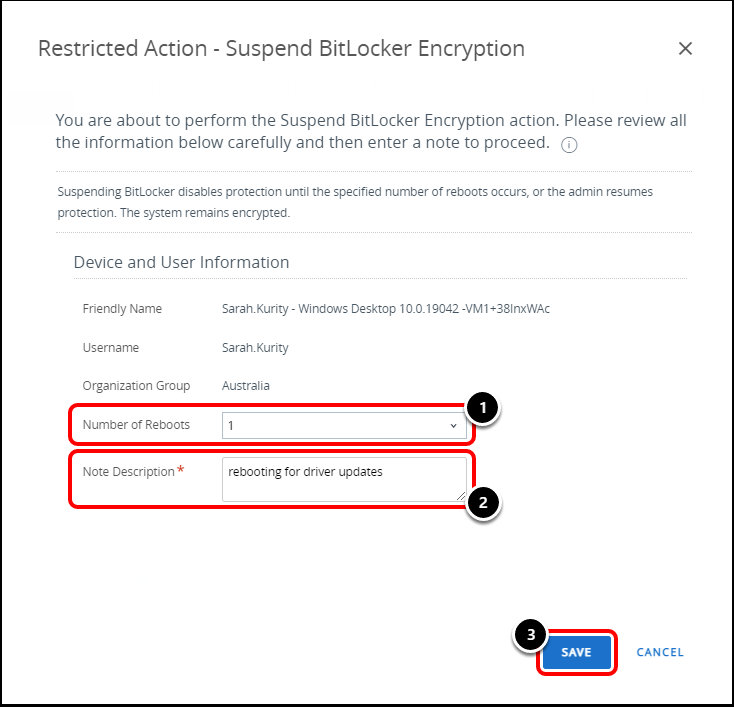
- Select the number of reboots until BitLocker resumes.
- Enter the reason for BitLocker Suspension.
- Click Save.
Task 2.4. Review BitLocker Suspension
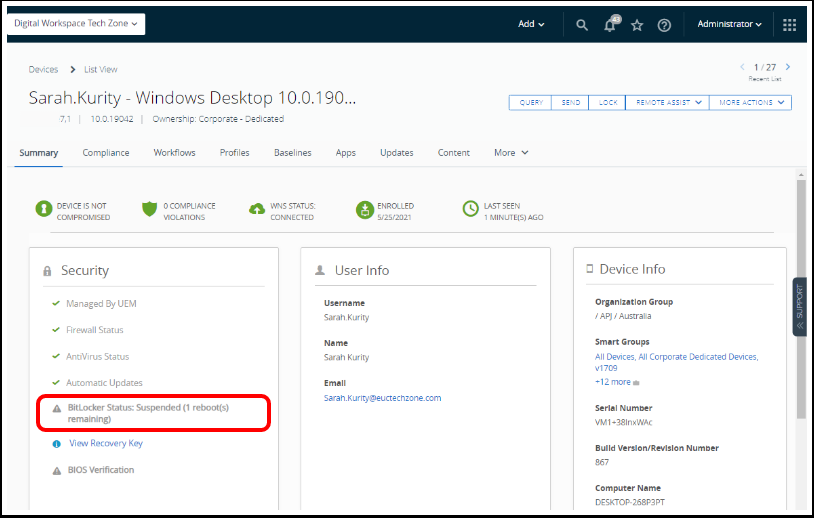
Review the BitLocker Status for the device. This will also display how many reboots are remaining until BitLocker resumes.
Task 2.5. Resume BitLocker from Device Details More Actions
While BitLocker is in a suspended state, admins can resume BitLocker encryption directly from the Workspace ONE UEM console.
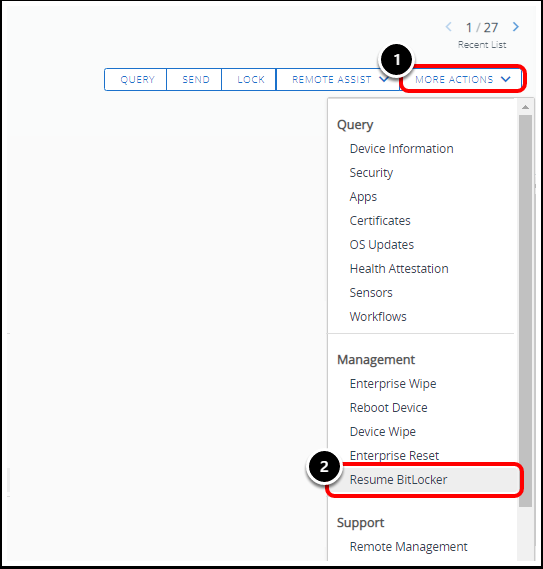
- Click More Actions
- Select Resume BitLocker
Accessing BitLocker Device Recovery Keys
Important: Ensure that you read What causes BitLocker recovery in the Microsoft Docs: BitLocker recovery guide. Having a Recovery Key process plan is critical for users to get back into their Windows devices.
Understanding Device Recovery Keys
BitLocker recovery is the process by which you can restore access to a BitLocker-protected drive in the event that you cannot unlock the drive normally.
Workspace ONE UEM leverages role-based access controls (RBAC) for admins, allowing you to grant access to view recovery keys only to the admins who require access.
End users can log into Workspace ONE and view the BitLocker Recovery Key in the Support Tab when configured. Role-based access controls (RBAC) are available for the self-service portal controls to turn this feature off.
There are many different scenarios where a machine might prompt a user for the recovery key on reboot. These are well documented in the Microsoft Docs: BitLocker recovery guide.
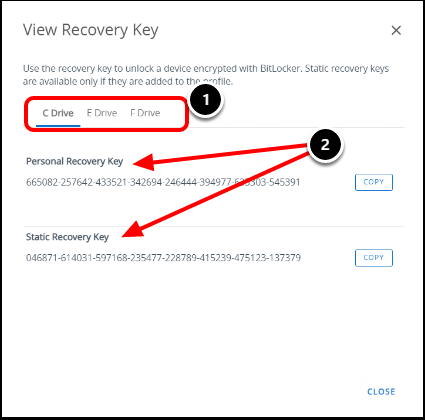
- Toggle between the drive letters to see the Recovery keys. In this example, we have additional fixed drives.
- Review the Personal Recovery Key and the Static Recovery Key.
Administrators can also access the recovery keys for devices they have permissions to access through their RBAC. This may be required when devices are shared across users, such as with a kiosk.
Access Encryption Keys in the Workspace ONE UEM Console
- Navigate to the Workspace ONE UEM Console, click on the Device in question from the Devices > List View
- From the Device Summary screen, in the Security Widget, select View Recovery Key
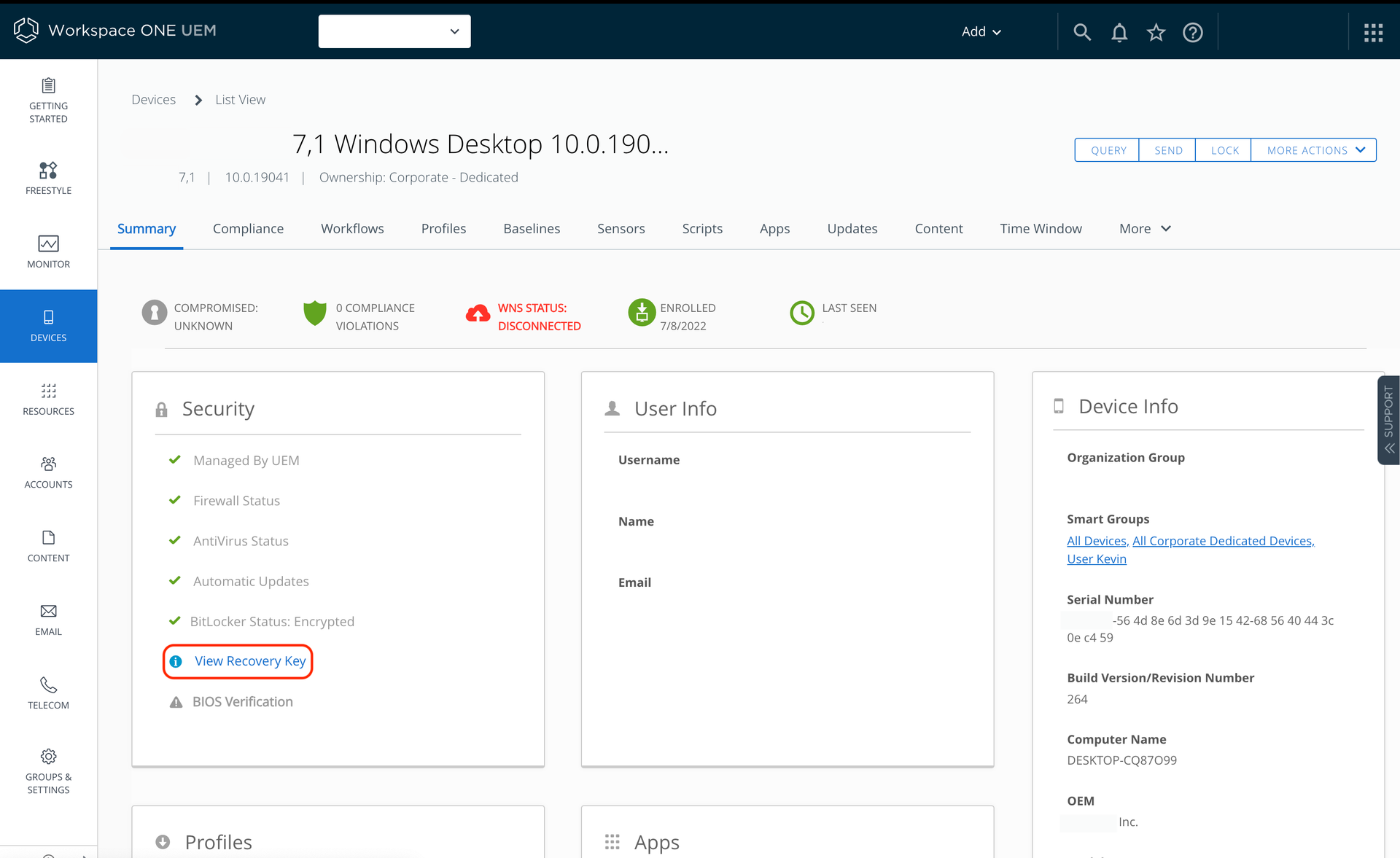
- Review BitLocker Encryption details and statuses for all hard drives.
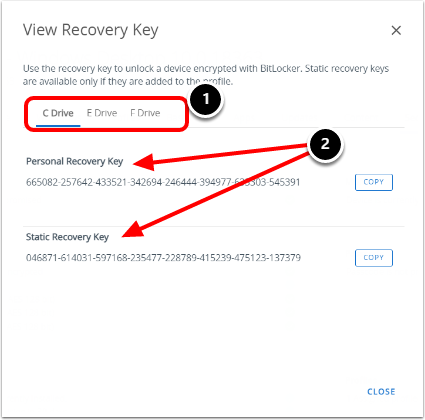
- Toggle between the drive letters to see the Recovery keys. In this example, we have two additional fixed drives.
- Review the Personal Recovery Key and the Static Recovery Key.
Note: The Static Recovery Key will remain the same for all encrypted drives.
User Access to Recovery Key in the Workspace ONE Portal
When this setting is enabled, users can retrieve the BitLocker Recovery Key from the Workspace ONE portal without the need to contact the HelpDesk for assistance. To turn on the recovery key in the Workspace ONE portal, follow the next steps.
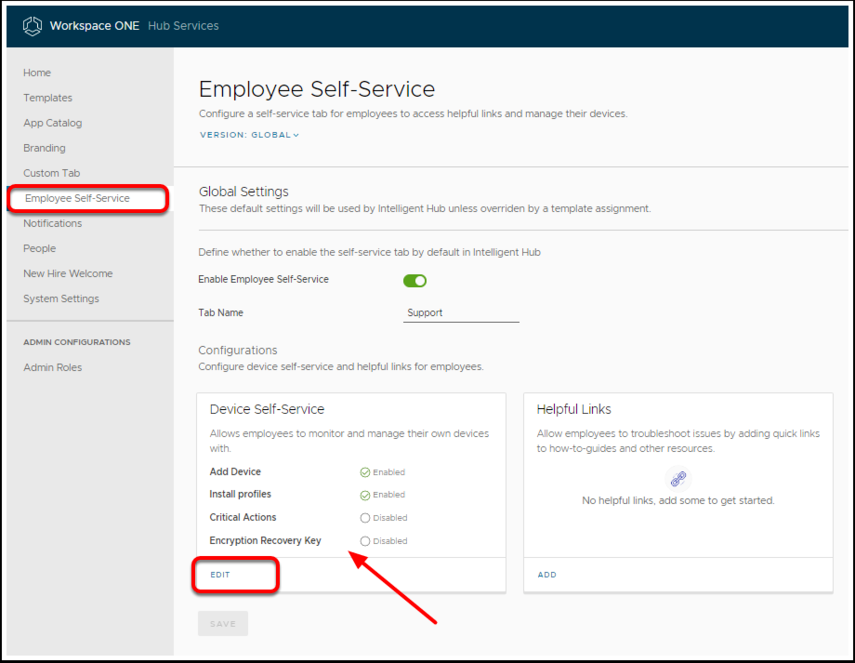
- Log in to Workspace ONE Hub Services and select the Employee Self-Service Tab.
- Under the Device Self-Service box, you can enable access to the Encryption Recovery Key.
- Click Edit to change this setting.
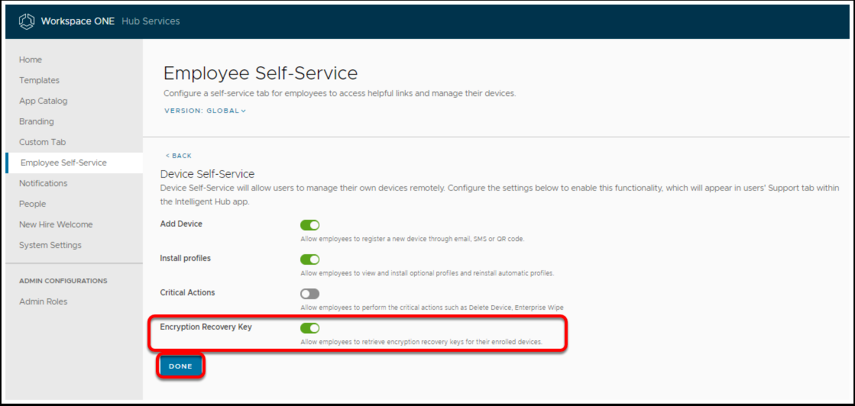
- Enable the Encryption Recovery Key.
- Click Done.
User Access to Recovery Key in the Workspace ONE Portal
After the Encryption Recovery Key has been enabled in Workspace ONE Hub Services, Users can log in to the Workspace ONE portal and retrieve the Encryption Recovery Key. The user will perform the following steps.

- Log in to the Workspace ONE portal and select the Support tab.
- From the Support tab, select the Windows device.
- Under encryption, select View Recovery Key.
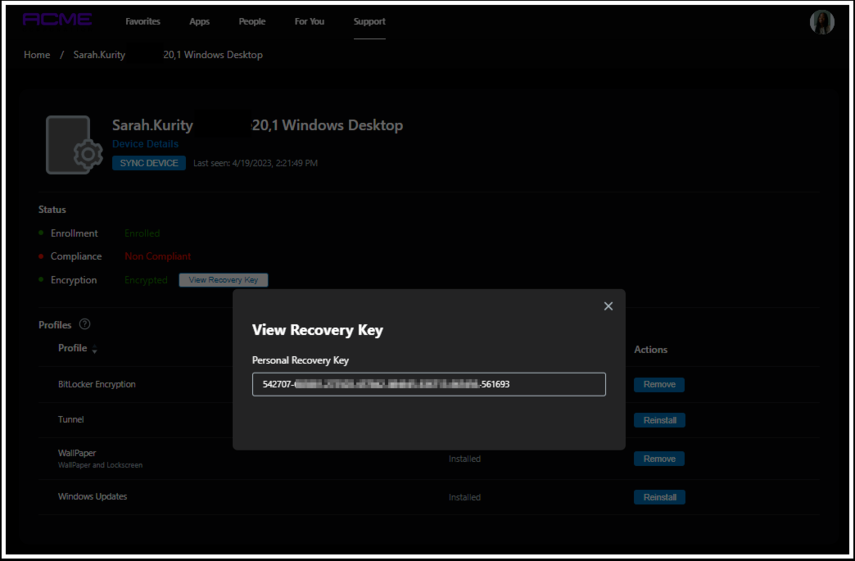
- Select the Recovery Key and enter it on the device that is asking for the recovery key to be entered.
Entering the Device Recovery Key at Boot Up
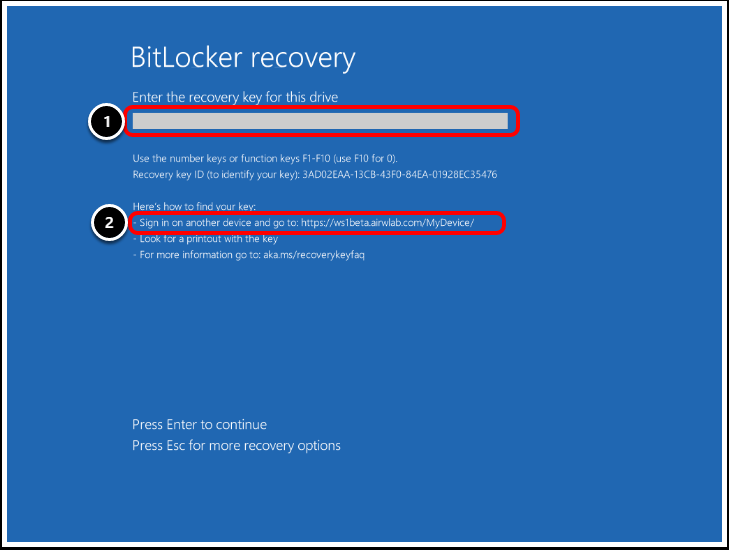
- Enter the BitLocker recovery key.
- In the policy, we set up a self-service URL; the Self Service URL appears here.
As a test, you can force a drive into recovery. Open Windows PowerShell as an administrator and enter the following command:
Replace "C:" with the drive letter.
manage-bde C: –forcerecovery
For more information, see Microsoft Docs: BitLocker ManageBDE ForceRecovery.
Accessing Recovery Keys for Removable Storage (BitLocker to Go)
Removable Storage devices are distinct from Windows PCs. Removable storage device keys must be accessible even if devices or users are no longer in the Workspace ONE UEM console.
You can find the Recovery Keys and list of Removable Storage Devices in Workspace ONE UEM under
- Devices > Peripherals and
- Accounts > Users > Removable Storage
Task 1. Recovery Keys for Removable Storage Device by User
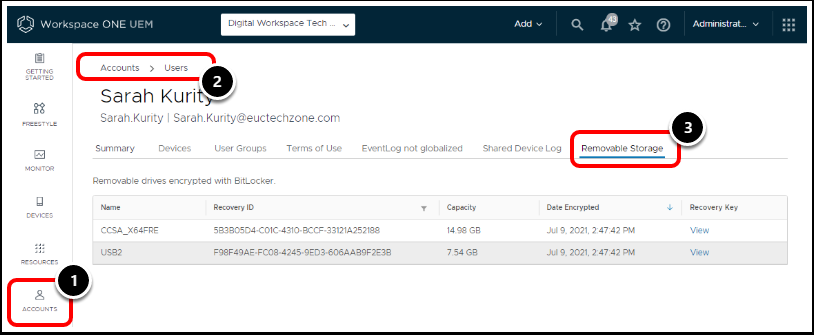 In the Workspace ONE UEM console:
In the Workspace ONE UEM console:
- Navigate to Accounts.
- Select Users and Select a User.
- After a User is selected, click the Removable Storage tab.
Task 2. View All Removable Storage Devices
 In the Workspace ONE UEM console:
In the Workspace ONE UEM console:
- Navigate to Devices.
- Select Peripherals.
- Select List view.
- Click Removable Storage.
TIP: See Enabling BitLocker Encryption for Removable Storage (BitLocker to Go).
Accessing Bitlocker Recovery Key as End-User from iOS
- Open the Intelligent Hub application on your managed device, go the Support Tab
- Under ‘My Devices’, Select the Managed Device for which you are trying to obtain the Recovery Key
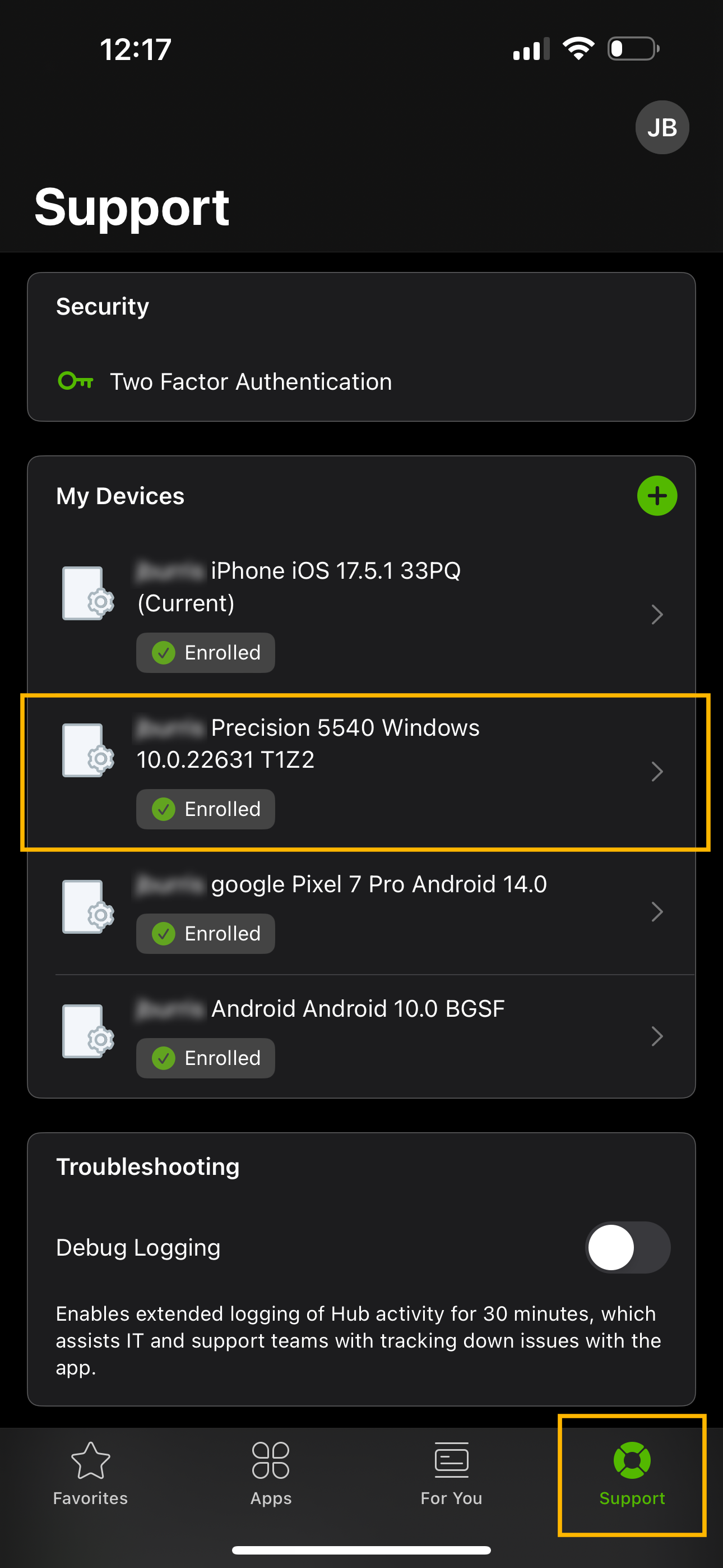
- Under the Device Status heading, go to Encryption
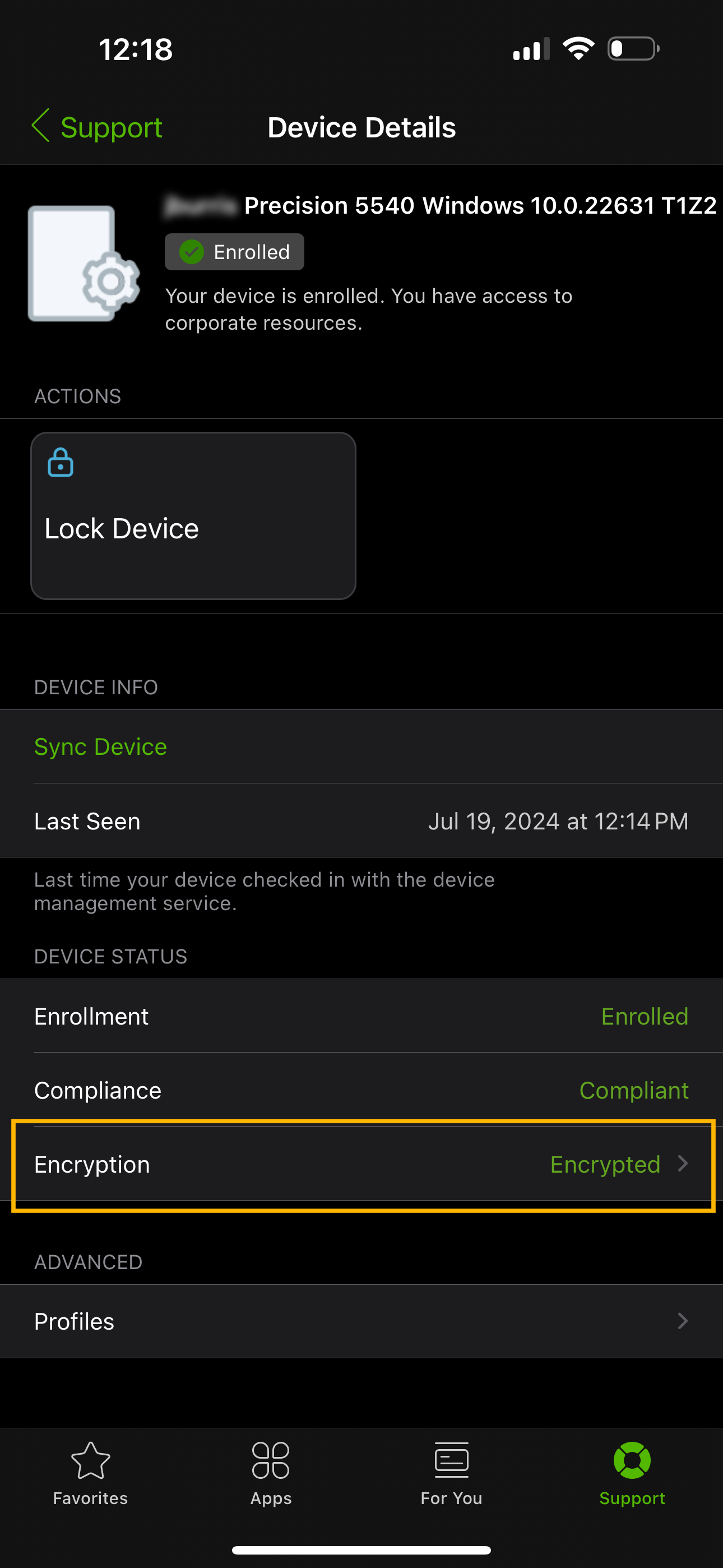
- Here you will see a heading called ‘Current Recovery Key’
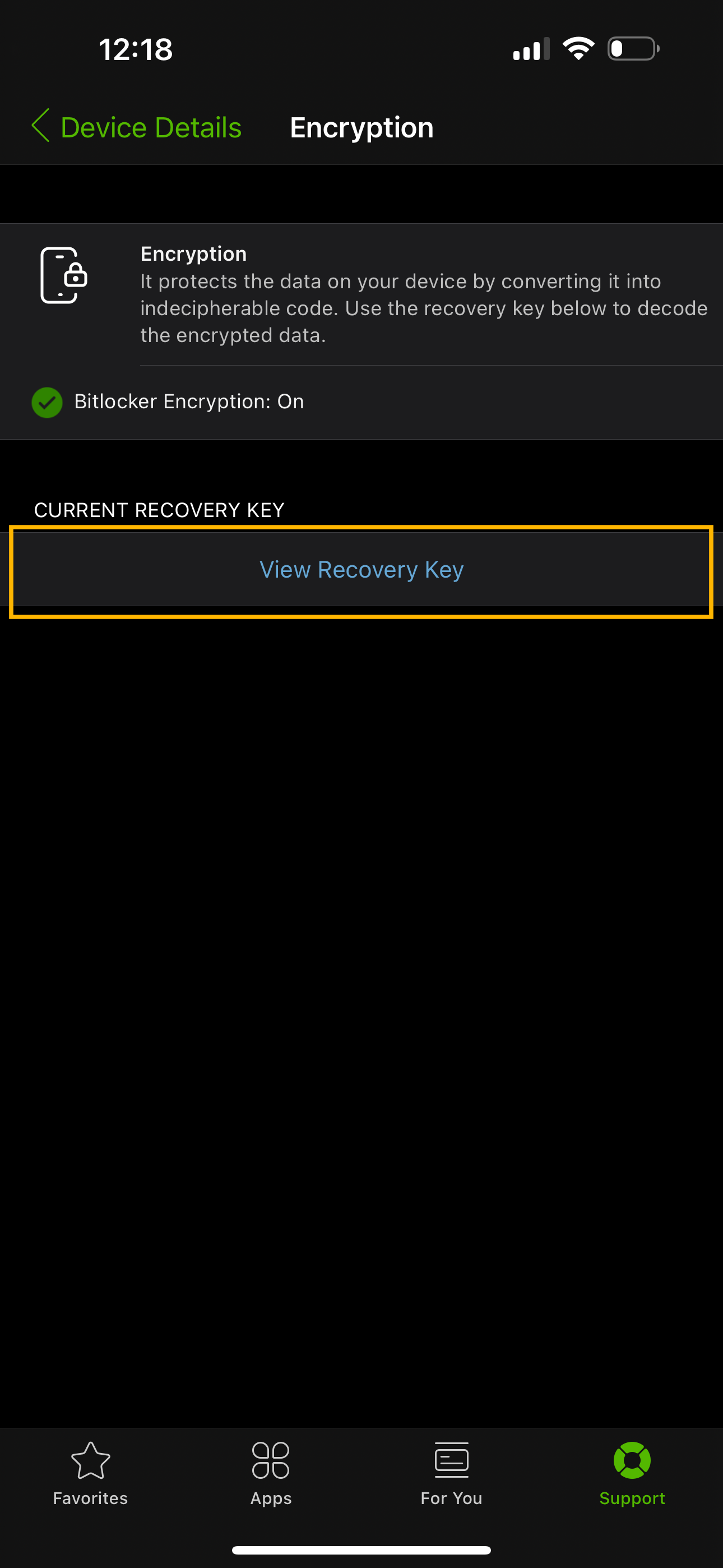
- Press ‘View Recovery Key’ button to view the device’s Recovery Key

Accessing Bitlocker Recovery Key as End-User from Android
- Open the Intelligent Hub application on your managed device, go the Support Tab
- Under ‘My Devices’, Select the Managed Device for which you are trying to obtain the Recovery Key

- Under the Advanced heading, go to Encryption
- Here you will see a heading called ‘Personal Recovery Key’.
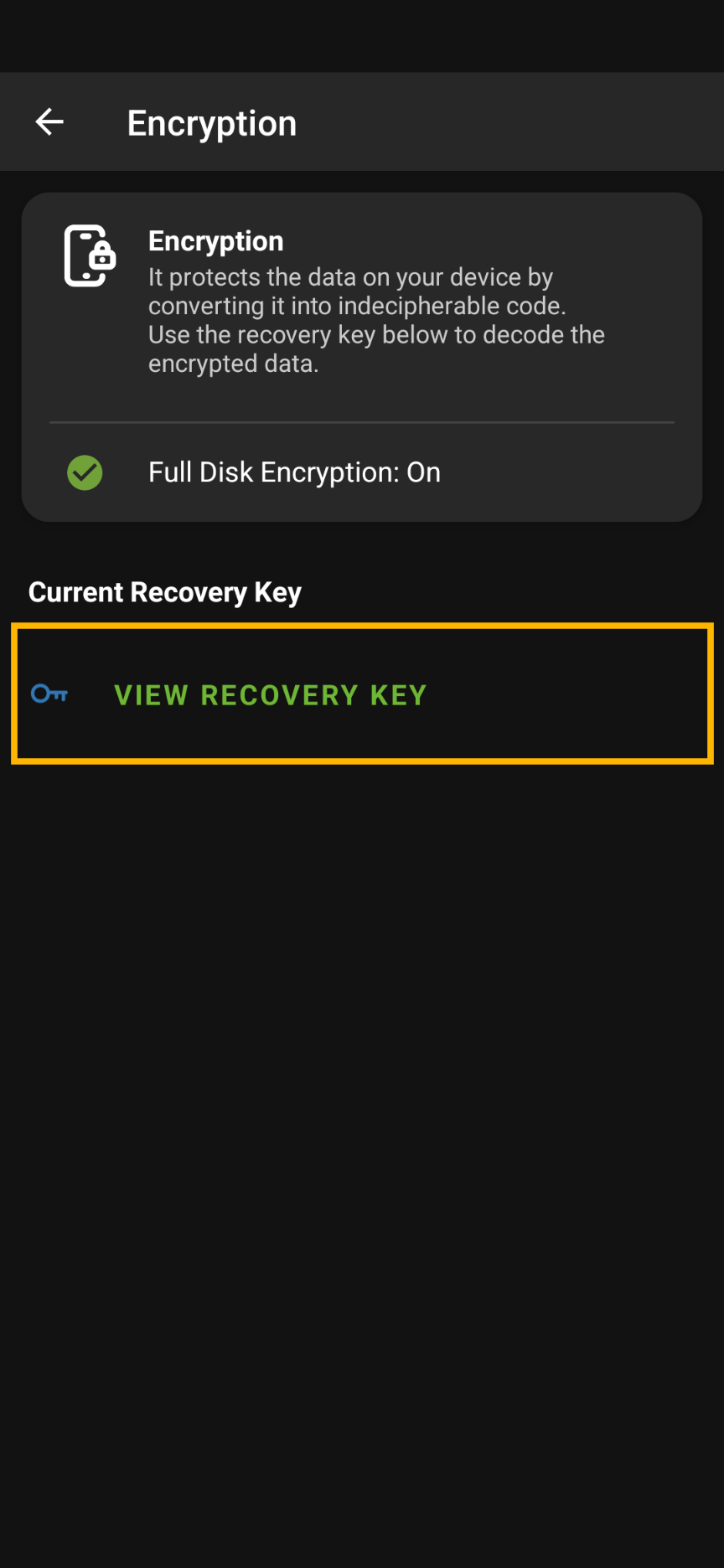
- Press ‘View Recovery Key’ button to view the device’s Recovery Key

Configuring Compliance Policy for Device Encryption
The compliance engine is an automated tool by Workspace ONE UEM that ensures all devices abide by your policies. These policies can include basic security settings such as device encryption status.
Configuring Device Compliance for BitLocker Encryption
The Workspace ONE compliance engine detects whether or not encryption is enabled on the device. Windows supports all third-party encryption solutions, therefore Workspace ONE can set a compliance policy around encryption, even if the device has been encrypted using a third-party encryption tool.
When devices are determined to be out of compliance, the compliance engine warns users to address compliance errors to prevent disciplinary action on the device. For example, the compliance engine can trigger a message to notify the user that their device is out of compliance.
You can automate escalations when corrections are not made, for example, locking down the device, marking the device as noncompliant to trigger Zero-Trust access policies with Workspace ONE Access, and notifying the user of any remediation steps. These escalation steps, disciplinary actions, grace periods, and messages are all customizable with the Workspace ONE UEM console.
For more information on Workspace ONE compliance policies, see Compliance Policies.
Task 1. Add Compliance Policy

- In the Workspace ONE UEM console, select Add.
- Select Compliance Policy.
Task 2. Select the Windows Platform

- Select the Windows platform.
- For the Device Type, select Windows Desktop.
Task 3. Add Compliance Policy Rule
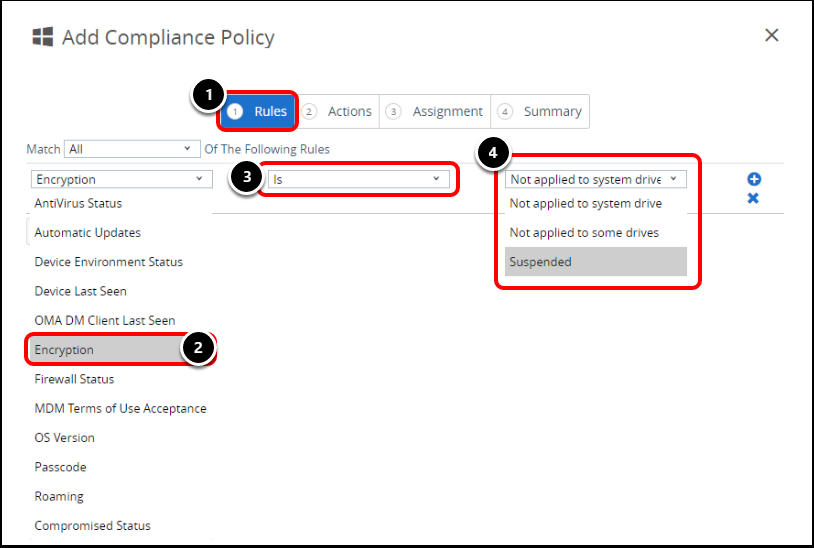
- Select the Rules tab.
- Select Encryption as the compliance flag.
- Change the Rule to Is.
- Select compliance value.
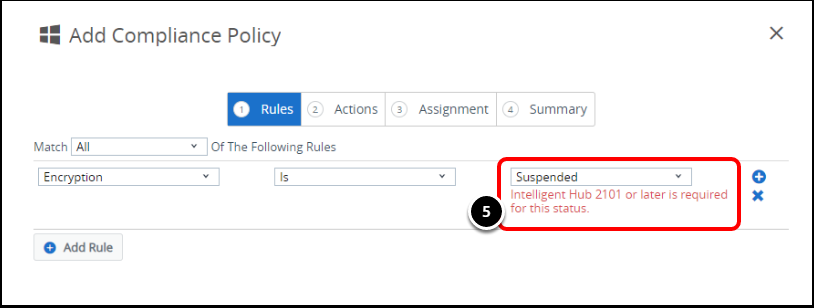
- Drop-down values include Not Applied to System Drive, Not Applied to Some Drives or Suspended.
- For BitLocker Status of Not Applied to Some Drives or Suspended, the Workspace ONE Intelligent Hub 2101 or later is required.
Task 4. Add Compliance Policy Action
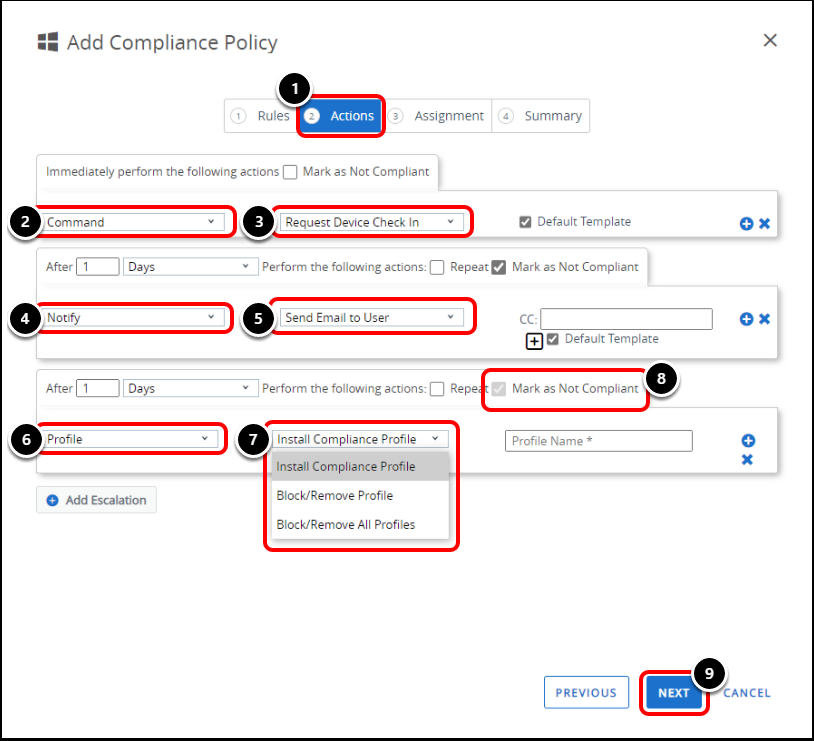 Define the consequences of noncompliance within your policy by completing the Actions tab.
Define the consequences of noncompliance within your policy by completing the Actions tab.
- Select the Actions tab.
- Select Command as an Action.
- Select Request Device Check In as the Command.
- This ensures that the device has checked into the Workspace ONE UEM console with the latest information. You can re-evaluate the compliance Rule in the Compliance tab of the device details.
- Select Notify as an Action.
- Select Send Email to User.
- This sends a compliance email to the end user with remediation actions they can take.
- You can select the default template, or customize the compliance templates based on the compliance rule.
- Select Profile as an Action.
- Select from
- Install Compliance Profile - Install a compliance profile.
- Block Remove Profile - Block or remove a specific profile - For example, Certificates.
- Block Remove ALL Profiles - Remove all Profiles from the device until the device is compliant.
- At any escalation step, you can mark the device as non-compliant. This will trigger any conditional access policies you may have set within Workspace ONE Access.
- Click Next.
Tip: The Mark as Not Compliant check box is enabled (selected) by default for each newly added Action.
Tip: If one action has the Mark as Not Compliant option enabled, then all subsequent actions and escalations are also marked as not compliant. These subsequent check boxes cannot be edited.
Task 5. Assign the Compliance Policy
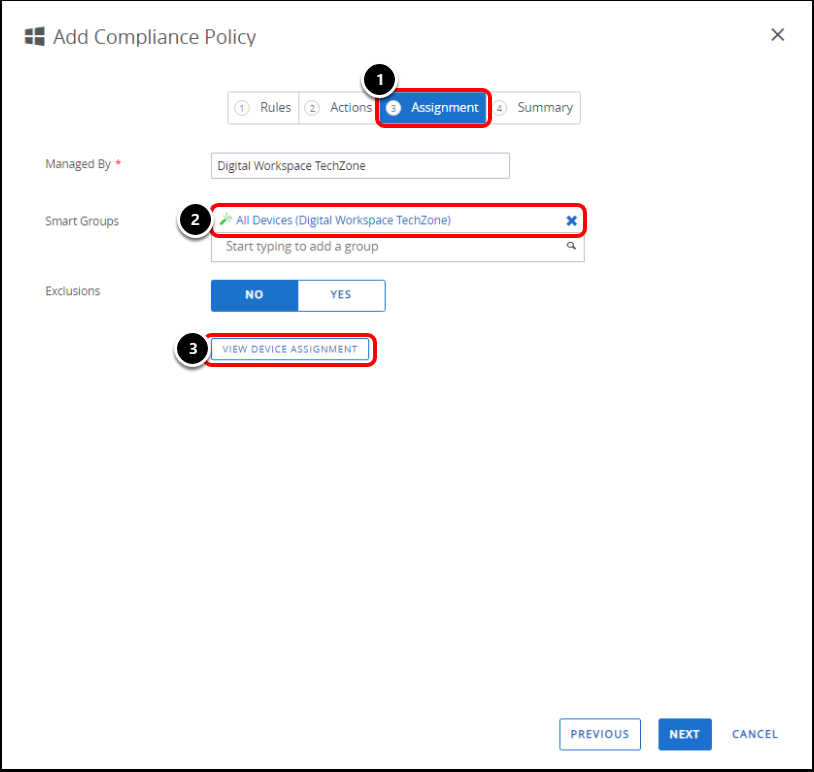
- Ensure that you are on the Assignment tab.
- Select a Smart Group to apply the device compliance policy to.
- Click View Device Assignment to see the devices.
Task 6. View Device Policy Assignment
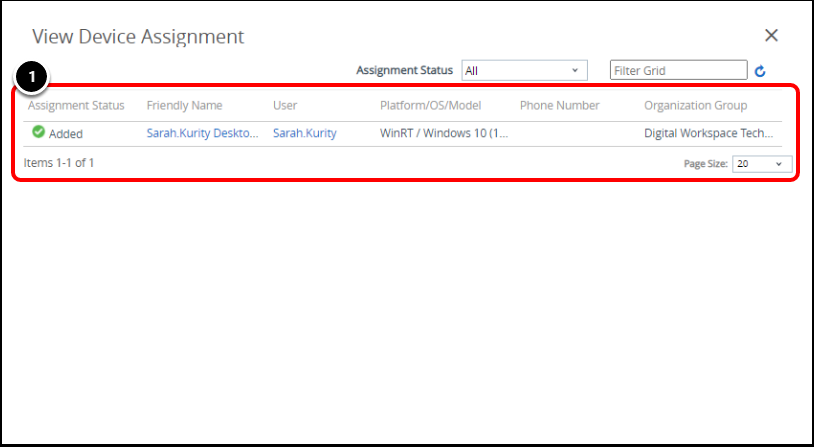
- Selecting View Device Assignment allows you to review the devices assigned to the compliance policy.
Task 7. Activate the Compliance Policy

- Ensure that you are on the Summary tab.
- Enter a Name for the Compliance Policy.
- For example, Encryption.
- Enter a description for the Compliance Policy.
- For example, Encryption. You might also want to specify in the description how a similar Encryption Compliance Policy will differ.
- Review the Device Summary.
- This displays how many devices in total have been assigned the Compliance Policy. This also displays how many devices are currently Compliant and how many are Non-Compliant.
- Use this information before you activate compliance policies. If your remediation action might cause calls to the help desk, you can apply the compliance policy in stages - or maybe extend the Escalated Actions to 7 days instead of 1 day, for example.
- Click Finish and Activate.
- This activates the policy and compliance actions are sent to the devices.
Task 8. Review Compliance Policy

- Navigate to Devices > Compliance Policies > List View.
- Ensure that the Encryption policy is active and review the Compliant status.
Automating Reports for Device Encryption
Workspace ONE Intelligence is designed to simplify user experience without compromising security. The intelligence service aggregates and correlates data from multiple sources to give complete visibility into the entire end-user computing environment.
Creating Reports for Windows 10/11 Encryption
In this exercise, you will use Workspace ONE Intelligence to generate a report displaying the Windows Device Encryption Details.
Before you begin, ensure that Workspace ONE Intelligence is set up and configured ready to generate the report.
For more information on this initial setup, see Getting Started with Workspace ONE Intelligence Reports and Dashboards: Workspace ONE Operational Tutorial.
Task 1. Create Reports with Workspace ONE Intelligence
Navigate to the Workspace ONE Intelligence console.
- Select the Reports tab.
- Click Add.
Task 2. Add Report
- Select Custom Report and click Start.
Task 3. Add Report Category

- Under Category, select Workspace ONE UEM, then select Devices.
Task 4. Configure Report Details
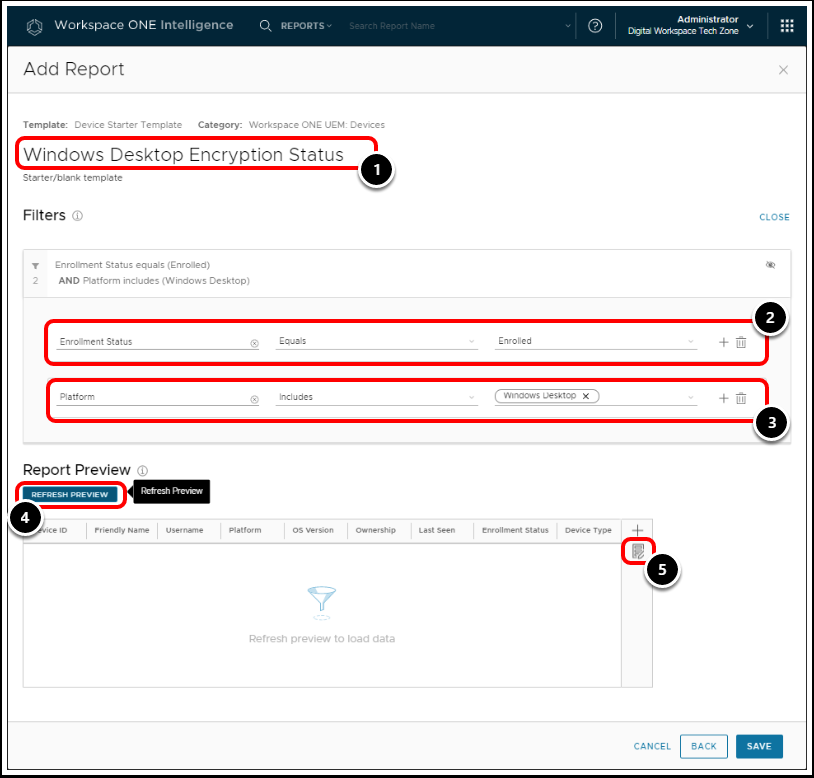
- Enter a report name.
- In this example, the report is called Windows Desktop Encryption Status.
- In the filters, select the following:
- Enrollment Status - Equals - Enrolled.
- This ensures that we are pulling in a report on currently enrolled devices.
- Click the plus icon + to add the following filters:
- Platform - Includes - Windows Desktop
- Click Refresh Preview to see the latest data.
- Next, we will edit the fields displayed. Select the edit columns option.
Task 5. Edit Workspace ONE Reports Columns

- Use the Search function to search for columns to add to the report.
- Expand the column categories to see all available columns.
- Select the column that you want to add.
- Click Add to add the column. This will appear on the right.
- Use the Remove buttons to remove columns from the report.
- Use the up and down arrows to change the column order.
- When you are satisfied with the arrangement of your report data, click Save.
Tip: In this example report, we use the following columns:
- Enrollment Date
- Last Seen
- Ownership
- Compliance Status
- Encryption Status
- bitlocker_encryption_method
- Friendly Name
- Username
- First Name
- Last Name
- OS Version
- Device Name
- Serial Number
- Device Organization Group Name
- Model
Task 6. Review Report Data

- Click Refresh Preview to see the preview of the current data.
- Review the report data and make any adjustments as necessary and ensure that you select Save.
Pro Tip: The field bitlocker_encryption_method comes from Workspace ONE Sensors. Ensure that Sensors are assigned to devices, so they can report back data.
Step 7. Edit, Run, Schedule, or Download the Report

You have now configured a report with data displaying Windows Device Encryption details.
- Select Edit to make any changes.
- Click Run to run the report.
- Select View to view report downloads.
- Select Add Schedule to automate data collection and collaboration.
Troubleshooting BitLocker
This section covers general troubleshooting information for BitLocker encryption.
BitLocker Drive Preparation Tool
The Workspace ONE Intelligent Hub for Windows automatically runs the BitLocker drive preparation tool to ensure that the partition requirements are met. You can run this command manually to test if there are compatible partitions. From an elevated command prompt, enter the following command:
bdehdcfg.exe -driveinfo
To prepare the drive, run the following commands in an elevated command prompt:
bdehdcfg.exe -target c: shrink
Bdehdcfg.exe -target c: merge
Bdehdcfg.exe -target default
Note: If you manually run these commands, we recommend adding the -skiphardwaretest switch so that the system does not require a reboot.
Use PowerShell Script to Convert FAT32 to NTFS System Partition
If you have upgraded your Windows 7 systems to Windows 10/11 and kept them in legacy BIOS mode, the system partition might still be FAT32. You must convert from FAT32 to NTFS for BitLocker to activate.
Note: FAT32 system partition works on Unified Extensible Firmware Interface (UEFI) systems.
To convert, run the following script in PowerShell:
if ($drive = (gwmi win32_volume -Filter "Label = 'System'"))
{
Write-Log "Detected a SYSTEM partition...system still in legacy mode."
#This finds as available drive letter
if (!(test-path H:\))
{
$driveletter = 'H'
}
elseif (!(test-path I:\))
{
$driveletter = 'I'
}
elseif (!(test-path J:\))
{
$driveletter = 'J'
}
elseif (!(test-path K:\))
{
$driveletter = 'K'
}
elseif (!(test-path L:\))
{
$driveletter = 'L'
}
$newletter = ($driveletter + ":")
$drive.DriveLetter = "$newletter"
$drive.Put() #assigning the drive letter
Write-Log "Attempting to convert system partition to NTFS...reboot required for changes to take effect."
$drive.Label | convert.exe $newletter /FS:NTFS /X #converting system partition to NTFS
$drive = (gwmi win32_volume -Filter "Label = 'System'")
Write-Log "Removing temporary drive letter"
Get-Volume -Drive $driveletter | Get-Partition | Remove-PartitionAccessPath -AccessPath "$newletter\" #removing the drive letter so it doesn't show up in file explorer
$global:status = 3
}
Check Trusted Platform Model (TPM) Health
To check health of TPM on a system, you can launch the TPM snap-in.
tpm.msc
Alternatively, run this PowerShell command:
Get-wmiobject -Namespace ROOT\CIMV2\Security\MicrosoftTpm -Class Win32_Tpm or
get-tpm
Task 1. Open TPM.msc
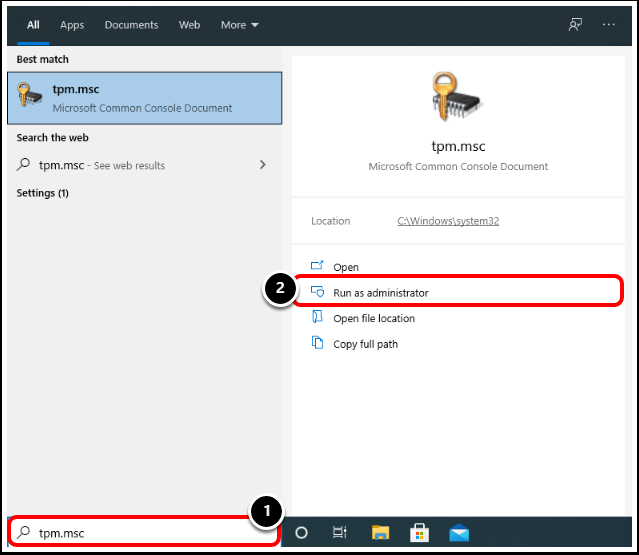
- On the Windows device, click in the search text box and enter
TPM.msc. - Select Run as administrator.
Task 2. Confirm TPM Status
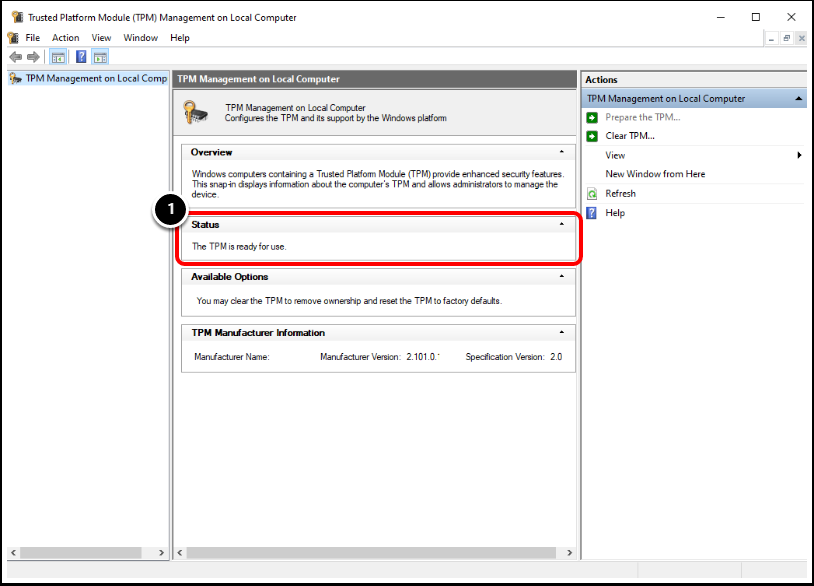
- Confirm that the TPM Status is Ready for Use
Task 3. Confirm TPM Status in PowerShell
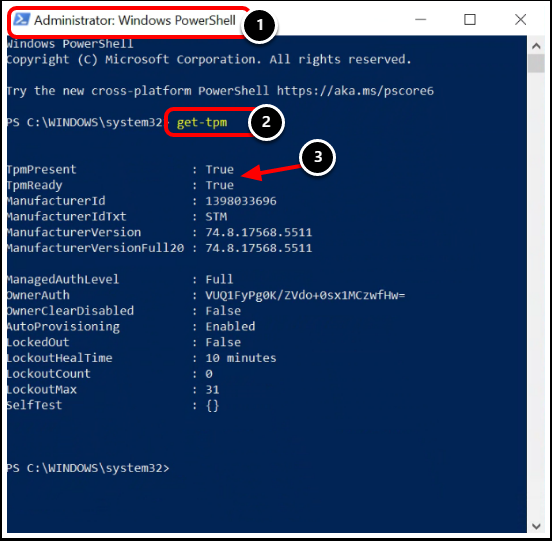
- Open PowerShell as an administrator.
- Run the command
get-tpm. - Confirm values for TPMPresent and TPMReady Status.
Export BitLocker Event Viewer Logs
To export BitLocker event viewer logs, enter the following in an elevated command prompt:
Get-WinEvent -logname 'Microsoft-windows-BitLocker/BitLocker management' -maxevent 30 | export-csv c:\eventviewer.csv
Summary and Additional Resources
This operational tutorial provided steps to configure remote encryption for Windows 10 and 11 devices with Workspace ONE UEM.
The exercises contained the steps on how to configure a BitLocker Encryption profile and verify that the profile applied. We also explored Workspace ONE UEM device compliance and remediation actions and creating reports, dashboards, and automated actions with Workspace ONE Intelligence.
Additional Resources
For more information about Windows Modern Management with Omnissa Workspace ONE, you can explore the following resources:
Interactive Demo
Getting Started with Windows Modern Management
- Evaluation Guide: Setting Up Workspace ONE Cloud
- Evaluation Guide: Managing Apps and Devices with Workspace ONE Cloud
Windows Onboarding
- Onboarding Windows Devices Using Command-Line Enrollment: Workspace ONE Operational Tutorial
- Enrolling Windows Devices Using Azure AD: Workspace ONE UEM Operational Tutorial
- Drop Ship Provisioning (Online): Workspace ONE Operational Tutorial
Windows Security and Policy Management
- Windows Modern Management Security Design and Implementation
- Deploying Workspace ONE Tunnel: Workspace ONE Operational Tutorial
Windows Application Management
Windows OS Patching
Windows Troubleshooting
Changelog
| Date | Description of Changes |
| 2024-08-19 |
|
| 2024-07-22 |
|
| 2024-07-19 | Added new sections for |
| 2023-05-04 |
|
| 2021-07-08 |
|
| 2021-04-08 |
|
| 2018-09-11 |
|
About the Author and Contributors
This tutorial was written by:
- Omnissa Compete and Technical Marketing
Feedback
Your feedback is valuable. To comment on this paper, either use the feedback button or contact us at tech_content_feedback@omnissa.com.

