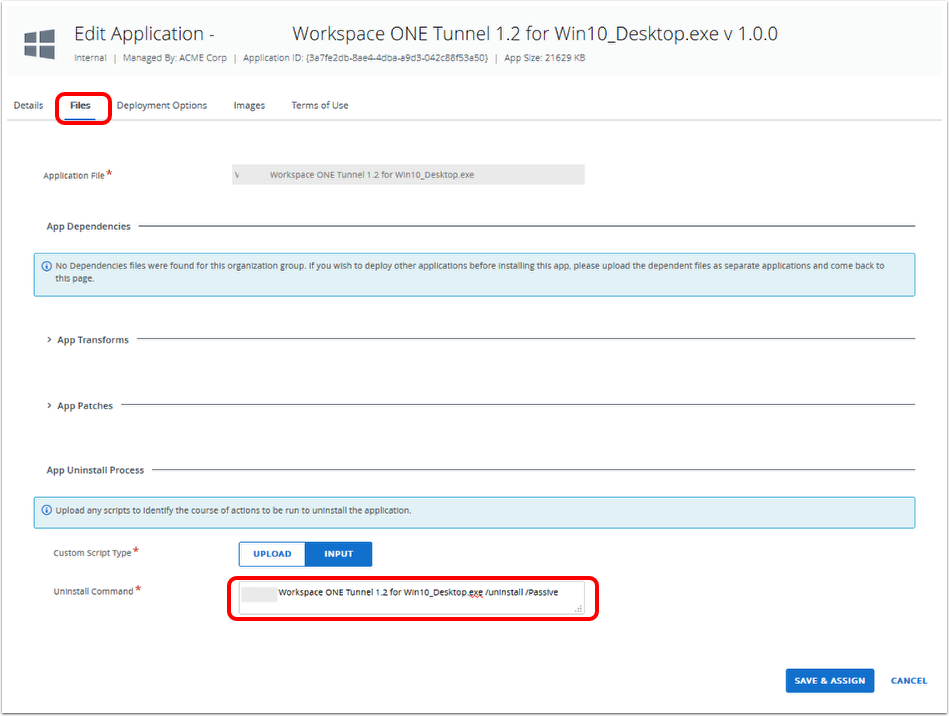
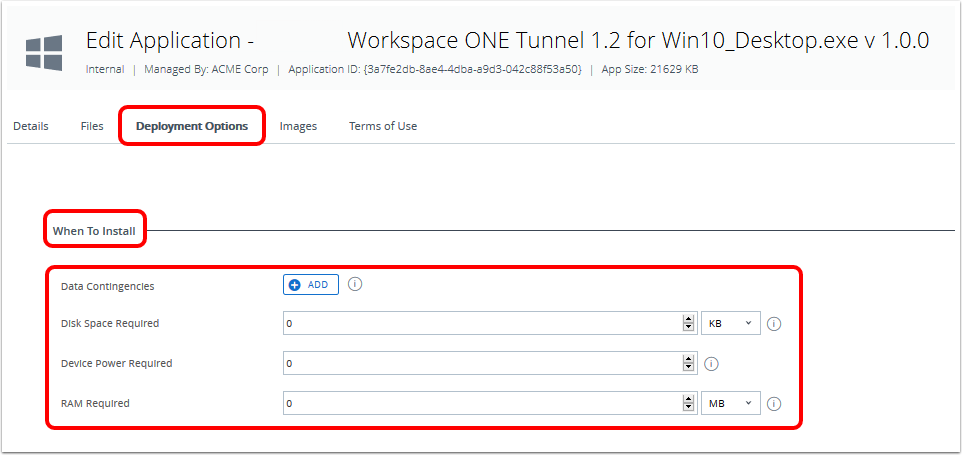
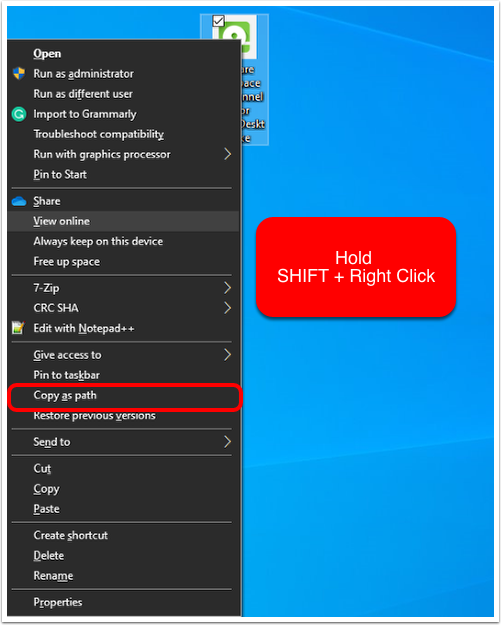
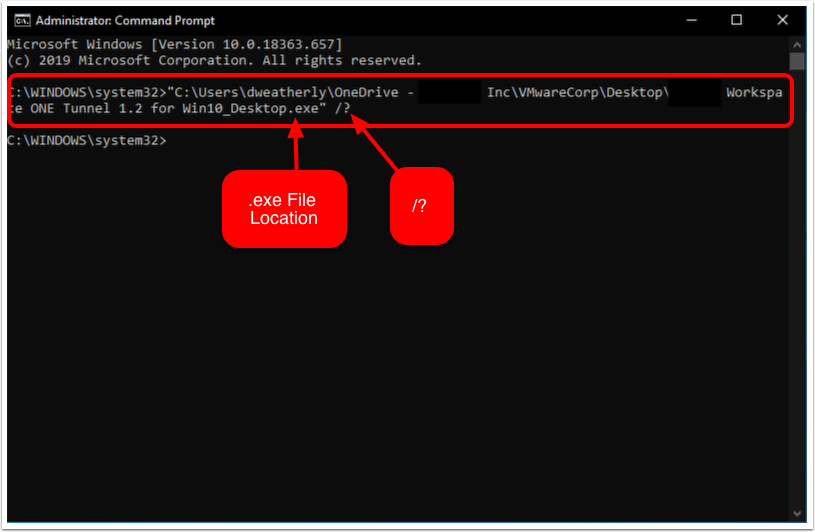
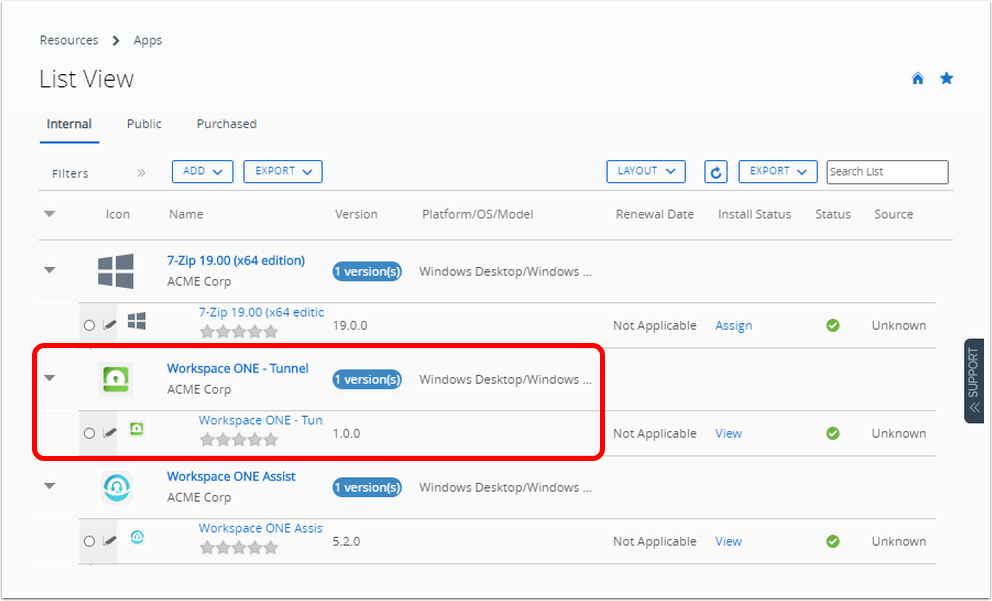
Deploying Workspace ONE Tunnel: Workspace ONE Operational Tutorial
Overview
Omnissa provides this operational tutorial to help you with your Omnissa Workspace ONE® environment. In this tutorial, explore how to configure and deploy the Workspace ONE Tunnel app across iOS, Android, macOS, and Windows platforms to enable Per-App Tunnel on a managed device. Procedures include enabling per-app tunnelling on managed devices and SDK-enabled applications, configuration of Tunnel policies, deployment of the client and profiles to devices, and general lifecycle maintenance.
Audience
This operational tutorial is intended for IT professionals, network and security administrators, and Workspace ONE administrators of existing production environments. Both current and new administrators can benefit from using this tutorial. Familiarity with networking in a virtual environment, knowledge of Tunnel Service on Unified Access Gateway, and Workspace ONE® UEM is assumed.
Getting Started with Workspace ONE Tunnel
Workspace ONE Tunnel enables secure access for mobile workers and devices. Users have a simple experience and need not enable or interact with Tunnel, and IT organizations may take a least-privilege approach to enterprise access, ensuring only defined apps and domains have access to the network.
Tunnel provides industry-best security and builds on TLS 1.3 libraries, implements SSL Pinning to ensure no MITM attacks, and includes client certificates on the allowlist to ensure identity integrity. Combined with explicit definitions of managed applications and integration with the Workspace ONE compliance engine, Tunnel can help customers attain Zero Trust goals for their workforce.
Prerequisites
Before you can perform the steps in this tutorial, you must install and configure the following components:
- Tunnel Service configured in Unified Access Gateway
- Workspace ONE UEM 2302 and later
- A device for the platform you plan to use (Windows, macOS, Android, or iOS)
Ensure the following settings are enabled in the Workspace ONE UEM Console:
- Organization Group created and set as Customer Type
- UEM REST API enabled and setting override
- Device Root Certificate issued
- Tunnel configured
Confirm that Tunnel Service is Configured
The remainder of this section assumes that Tunnel Service is properly configured and running on the Unified Access Gateway. For more details, see Configuring the Tunnel Edge Service: Workspace ONE Operational Tutorial.
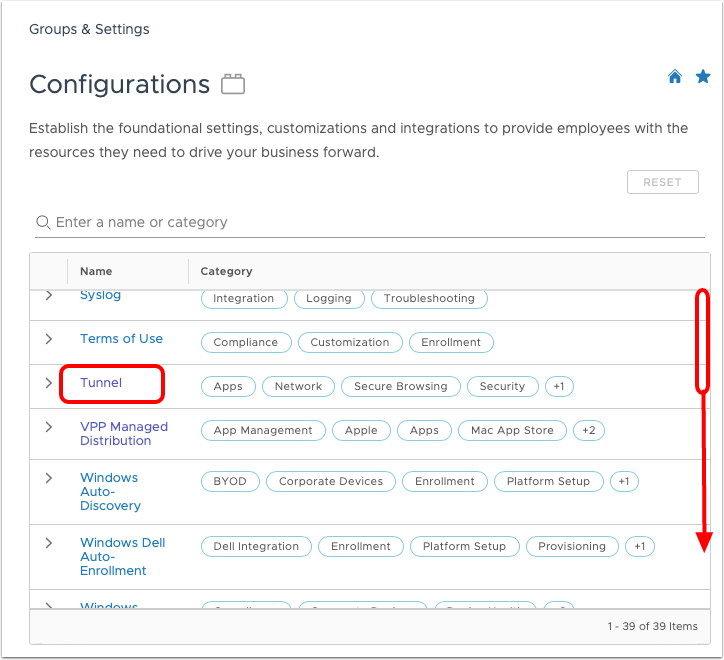
- In the Workspace ONE UEM console, navigate to Groups & Settings > Configurations.
- Scroll through the list of configurations if necessary and select Tunnel.

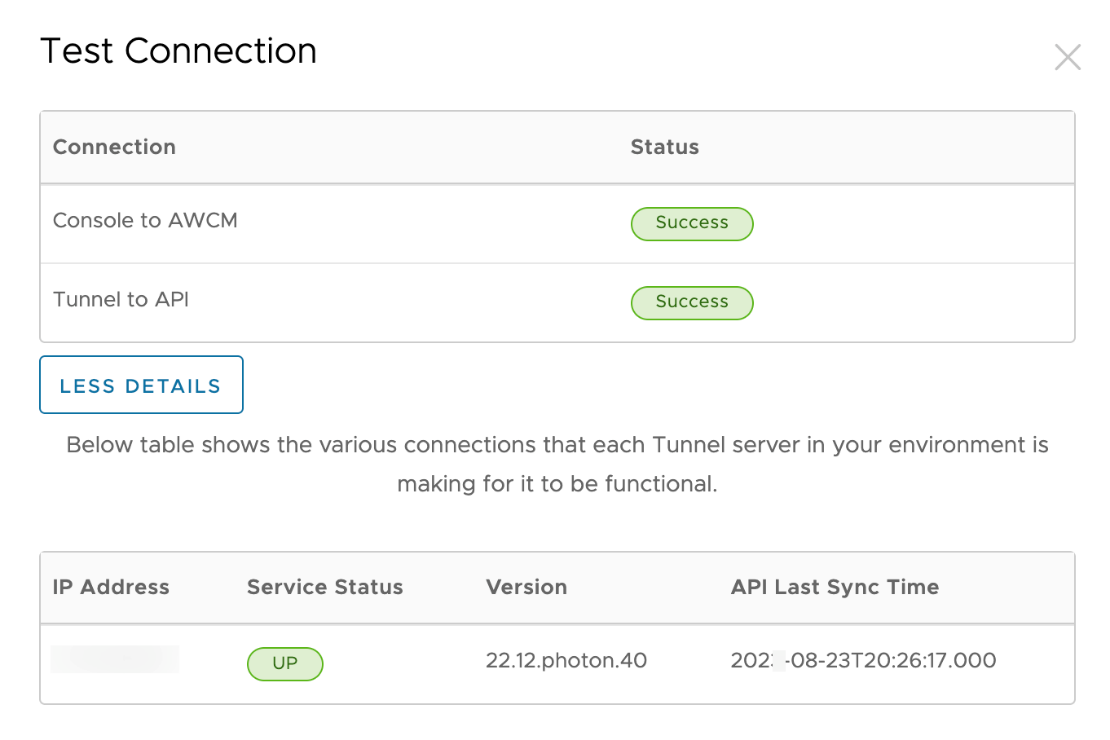
- Select Test Connection and confirm that both the Console to AWCM and Tunnel to API tests report Success and the Tunnel server reports service status UP.

This status confirms that the Tunnel Service is up and running on the server-side, and properly communicating with Workspace ONE UEM.
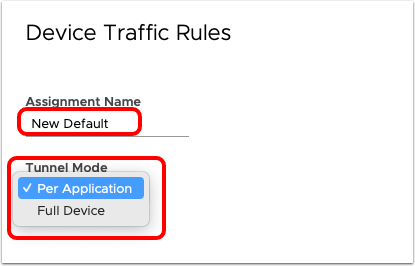
Tunnel Mode (Per-App vs Full Device Tunnel)
Workspace ONE Tunnel provides two modes for tunneling traffic: Per-Application or Full Device. Each mode is configured as part of the Device Traffic Rules and assigned to a device based on the Profile configuration. A device cannot perform Per-App and Device Tunnel at the same time.
Per-App Tunnel
Per-App Tunnel restricts tunnel traffic only to authorized applications and destinations (domain) specified by the UEM administrator when configuring the Device Traffic Rules.
Full Device Tunnel
On Full Device Tunnel configuration, traffic is restricted based on the authorized destinations (domains or IPs), regardless of the application. Full Device mode on Windows requires Workspace ONE Desktop Tunnel 2.1.8+ for all MDM use cases. For standalone enrollment use cases, the Workspace ONE Desktop Tunnel version 3.1 is required and will support Per-App and Full Device tunnel mode. Consolidating the MDM and standalone workflows in a unified Windows Tunnel client is on our roadmap.
Supported Platforms
Workspace ONE Tunnel app is available for managed and unmanaged devices providing Per-App and Full Device Tunnel across multiple platforms. Only TCP and UDP traffic will be routed to the Workspace ONE Tunnel App; ICMP-based traffic used by ping utilities is not supported. The Workspace ONE Tunnel app on Windows and macOS platforms now supports Standalone enrollment without Workspace ONE Intelligent Hub or any device management.
Tunnel Mode (Per-App and Full Device) is available based on the device platform and how it is managed as described in the following table.
Feature availability based on Management Mode and Device Platform
Management | Tunnel Mode | Windows | macOS | iOS | Android | ChromeOS | Linux |
UEM Managed | Per-App | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ |
Full Device | ✔ | ✔ | ✔ | ✔ | ✖ | ✖ | |
Registered Mode (unmanaged) | Per-App | ✔ | N/A1 | ✔* | ✔* | ✖ | ✖ |
Full Device | ✔ | N/A1 | N/A2 | N/A2 | ✖ | ✖ | |
App Level (MAM/Standalone) | Per-App | ✔** | ✔** | ✔* | ✔* | ✖ | ✔** |
Full Device | ✔** | ✔** | ✔** | ✔** | ✔** | ✔** |
* MAM requires use of the Tunnel module (Tunnel SDK) available on Workspace ONE SDK.
** Standalone method does not require Intelligent Hub; enrollment is done through the Workspace ONE Tunnel App.
N/A1 – Management mode not supported on the specific platform.
N/A2 – Not applicable for the specific Tunnel mode.
For more information, see Supported Platforms for Workspace ONE Tunnel.
For more information on Standalone requirements, see Configuring Tunnel Client for Standalone enrollment.
Per-App Tunnel Support for MAM Mode Workflow
Many organizations do not need to manage devices for their mobile fleets for various reasons, including possible privacy or legal issues. However, they might need to distribute mobile applications to access internal resources, so Workspace ONE UEM offers the flexibility of using a standalone catalog through Intelligent Hub that works independently of the MDM feature.
Applications that leverage the Workspace ONE SDK, such as Workspace ONE Web, can be configured to access internal web applications through Per-App Tunnel. The Workspace ONE Tunnel app is not required for this scenario. Also, organizations that develop mobile internal apps can be integrated with Workspace ONE SDK to enable access from unmanaged devices. Workspace ONE SDK is available on iOS and Android platforms.
In a MAM mode scenario, users do not have to enroll the device as UEM Managed and the Workspace ONE Tunnel app is not required, but rather they can:
- Use SDK-Enabled apps like Boxer or Web that will manage the registration of the device and be identified as App Level registration on UEM.
- Use the Intelligent Hub app in registered mode to access the Intelligent Hub catalog part of Workspace ONE UEM. This catalog distributes all application types; public, purchased, internal, and Web. Although end-user devices are not enrolled in MDM, you can access a device record in the Workspace ONE UEM console.
In both cases, the device record is for auditing purposes and the status of these devices in the UEM console displays as App Level (#1) or Hub Registered (#2).
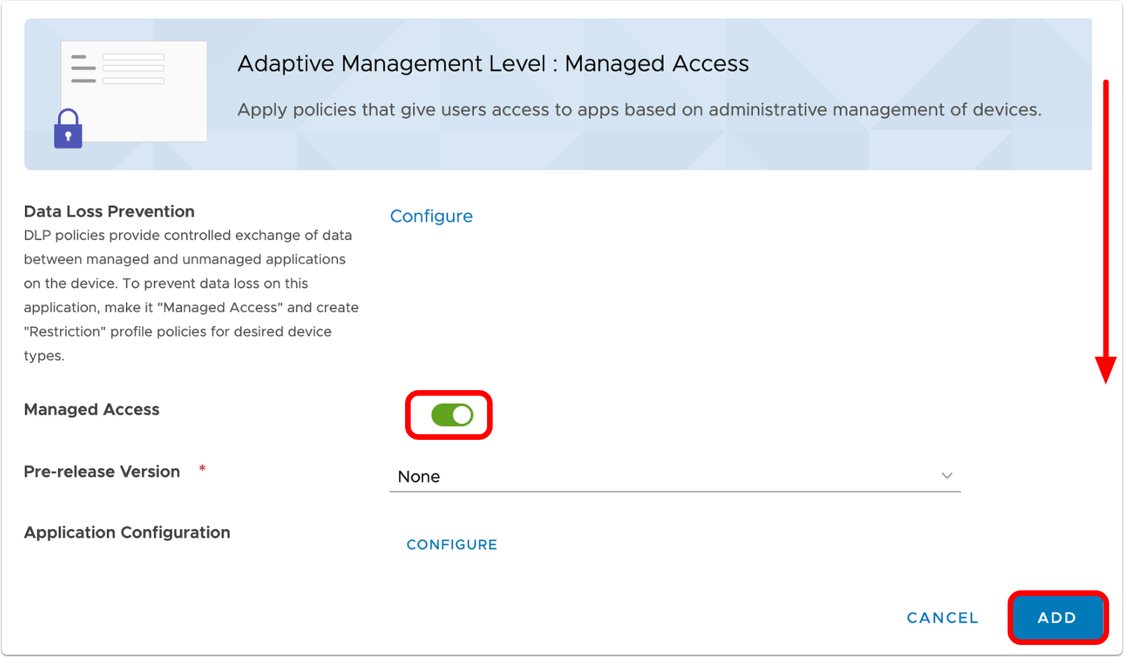
Configuration Requirements for MAM
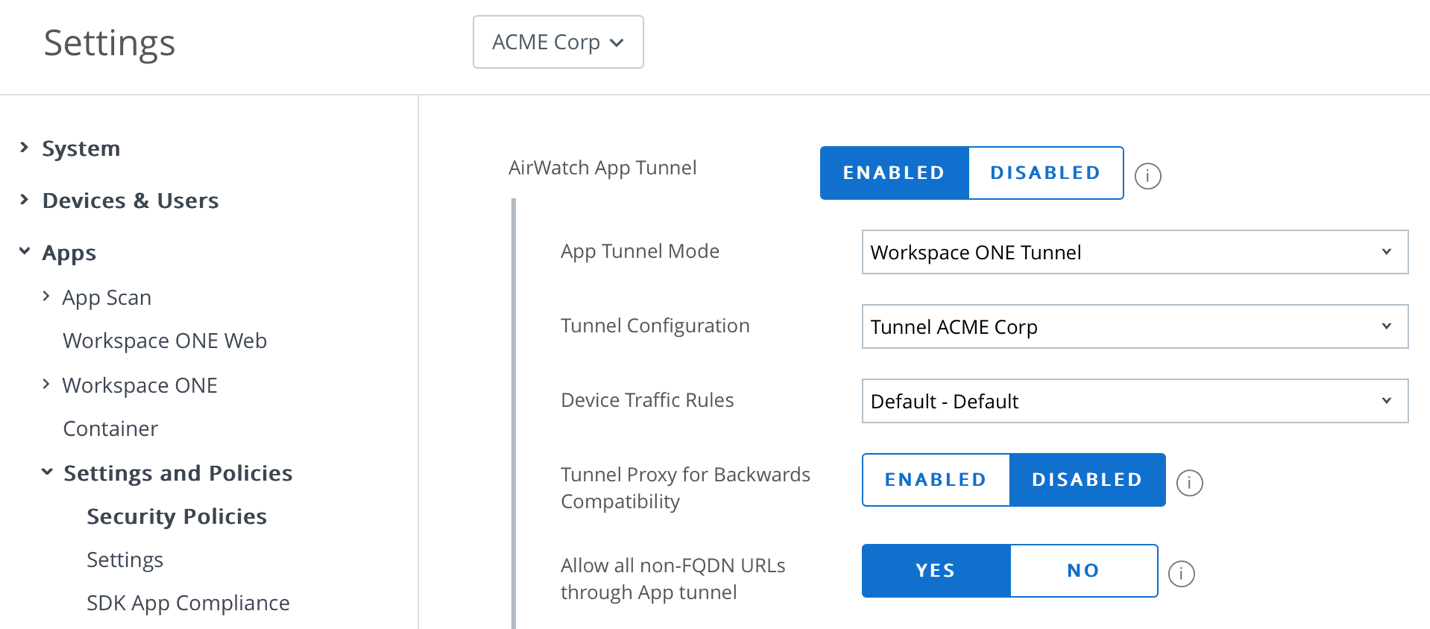
To enable Tunnel for SDK-based apps, navigate to Groups and Settings > Apps > Settings and Policies > Security Policies in the Workspace ONE UEM Console.
- Select Enabled to enable the AirWatch App Tunnel.
- Select Workspace ONE Tunnel for the App Tunnel Mode.
- Set the Tunnel Configuration and Device Traffic Rules.
After that, define the Device Traffic Rules for the iOS and Android SDK-enabled applications which will be covered later as part of this tutorial.
As a reminder, when using the MAM workflow and registered mode using the Workspace ONE Intelligent Hub, the SDK-enabled apps must be deployed through the Intelligent Hub catalog, and the Workspace ONE Tunnel app is not required.
The Workspace ONE Tunnel app can be deployed as a standalone app and perform enrollment without Workspace ONE Intelligent Hub or any device management. In this scenario, Workspace ONE UEM will only contain the device record.
Understanding Device Traffic Rules
This section discusses the two types of network traffic rules–server traffic rules and device traffic rules.
What are Device Traffic Rules?
Network traffic rules allow you to set granular control over how the Tunnel Service directs traffic from devices.
Workspace ONE UEM defines two types of network traffic rules in support of Workspace ONE Tunnel:
- Server Traffic Rules
- Device Traffic Rules
You can create device traffic rules to control how devices handle traffic on the device; Per-Application or Full Device.
Server Traffic Rules
The Server Traffic Rules enable you to manage how application traffic is routed throughout your network after traversing the Tunnel Service on Unified Access Gateway infrastructure. Specifically, if you require the use of proxies in your network or for external access, these proxies can be defined and configured as part of Server Traffic Rules.
Configuration of Service Traffic Rules will not be covered in this tutorial. For additional information, see Configure Server Traffic Rules in the product documentation.
Device Traffic Rules
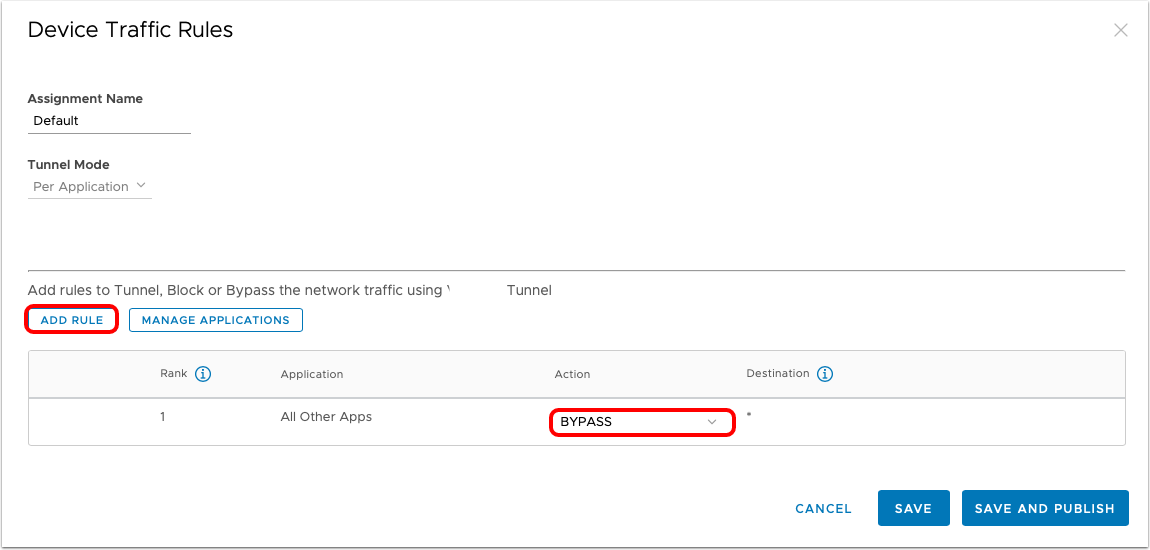
The Device Traffic Rules define how traffic from specified applications (Per Application) or devices (Full Device) is routed by the Workspace ONE Tunnel application. The device traffic rules serve as a locally enforced Access Control List, defining which apps and destinations should be blocked, tunneled, proxied, or bypass the tunnel completely.
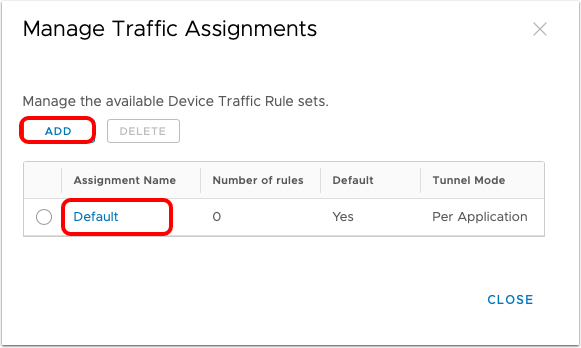
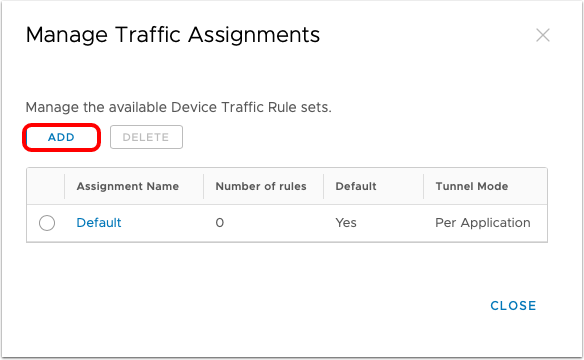
Under Manage Traffic Assignments, administrators can create multiple Device Traffic Rule sets to segment traffic to internal resources, such as rules for employees' devices that are less restricted than access to contractor devices.
- Each traffic assignment (Device Traffic Rule Set) contains multiple rules.
- A profile can only have a single traffic assignment (Device Traffic Rule Set).
- A device can only apply a single VPN profile at any one time.
Manage Traffic Assignments requires Workspace ONE UEM 2011, otherwise, a single Device Traffic Rule set can be created.
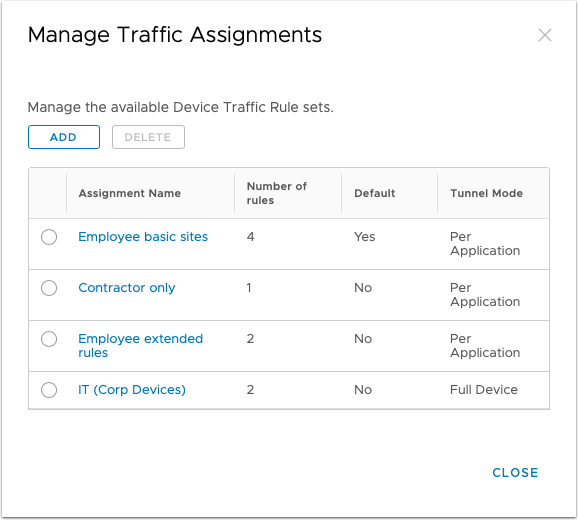
For each device traffic rule, you must set a Tunnel Mode to determine if traffic will be tunneled Per-Application or Full Device, then defined rules are ranked in order of execution. Multiple device traffic rules can be created and assigned to a profile that uses smart groups to determine the device assignment of the rules.
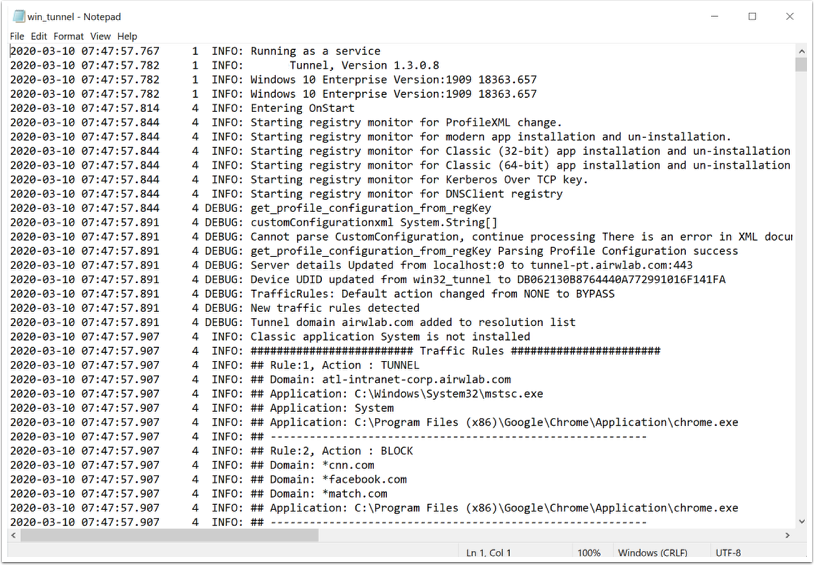
As an example, in device traffic rules set for Per-Application tunnel mode, every time a specified application is opened, the Tunnel client evaluates the Device Traffic Rule assigned to it before making any routing decisions. If no set rules match the situation, the Tunnel applies the default action. The default action behavior can vary per platform:
- On the iOS platform, the default action, set for all managed applications with tunnel profile associated except for Safari, applies to domains not mentioned in a rule. If no rules are specified, the default action applies to all domains and all managed applications associated with the VPN Profile.
- On the macOS platform, the default action, set for all macOS applications specified on the DTR rules, applies to domains not mentioned in a rule. At least one rule must be defined and when it doesn’t match any rule the default action applies to all domains and all macOS applications mentioned above in the Rank.
- On the Windows 10+ platform, the default action, set for all Windows applications specified on the DTR rules, applies to domains not mentioned in a rule. At least one rule must be defined and when it doesn't match any rule the default action applies to all domains and all Windows applications mentioned above in the Rank.
- On the Android platform, the default action, set for all Android managed applications with tunnel profile associated, applies to domains not mentioned in a rule. If no rules are specified, the default action applies to all domains and all managed applications associated with the VPN Profile.
More information about the specifics of device traffic rules per platform will be covered as part of this tutorial in the following chapters.
The device traffic rules help to separate personal and corporate traffic. Think of a scenario where the end-user can check their personal email, visit social media, and so on, without having their personal traffic inspected. We provide privacy where a traditional VPN cannot.
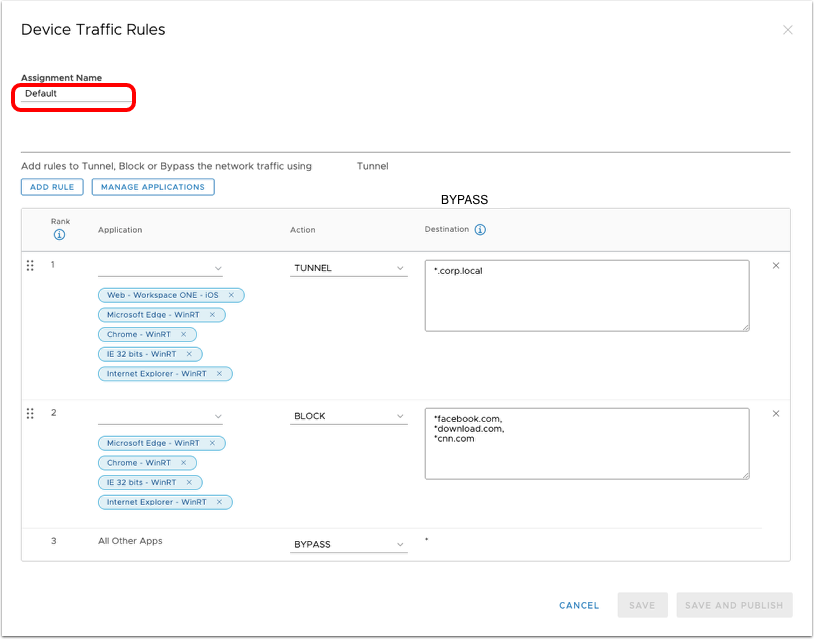
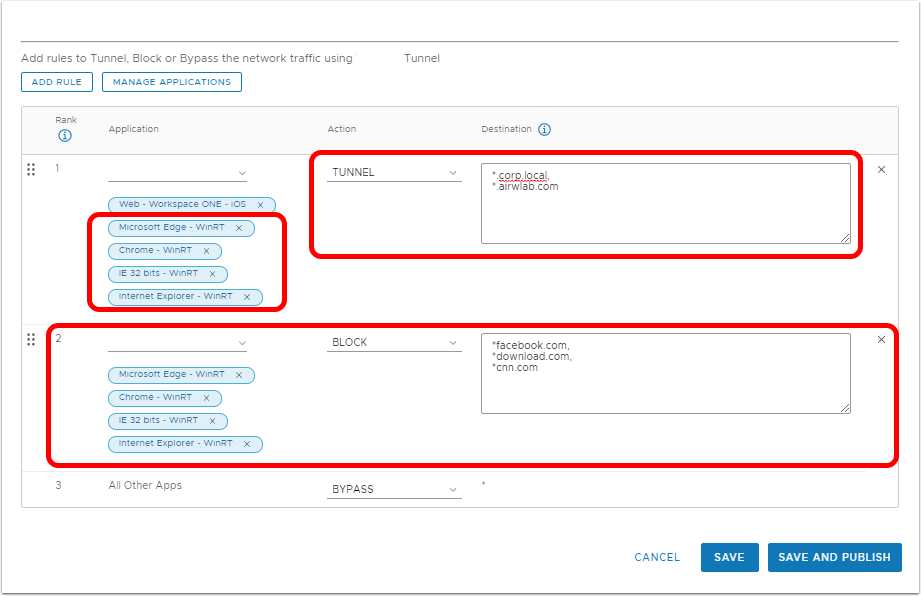
Per-Application Traffic Rules
When configuring the Device Traffic Rules and setting Tunnel Mode to Per Application, the administrator is required to configure the rules per application and domain. These rules will be used by the Workspace ONE Tunnel application to restrict the tunnel traffic only to authorized applications and domains.
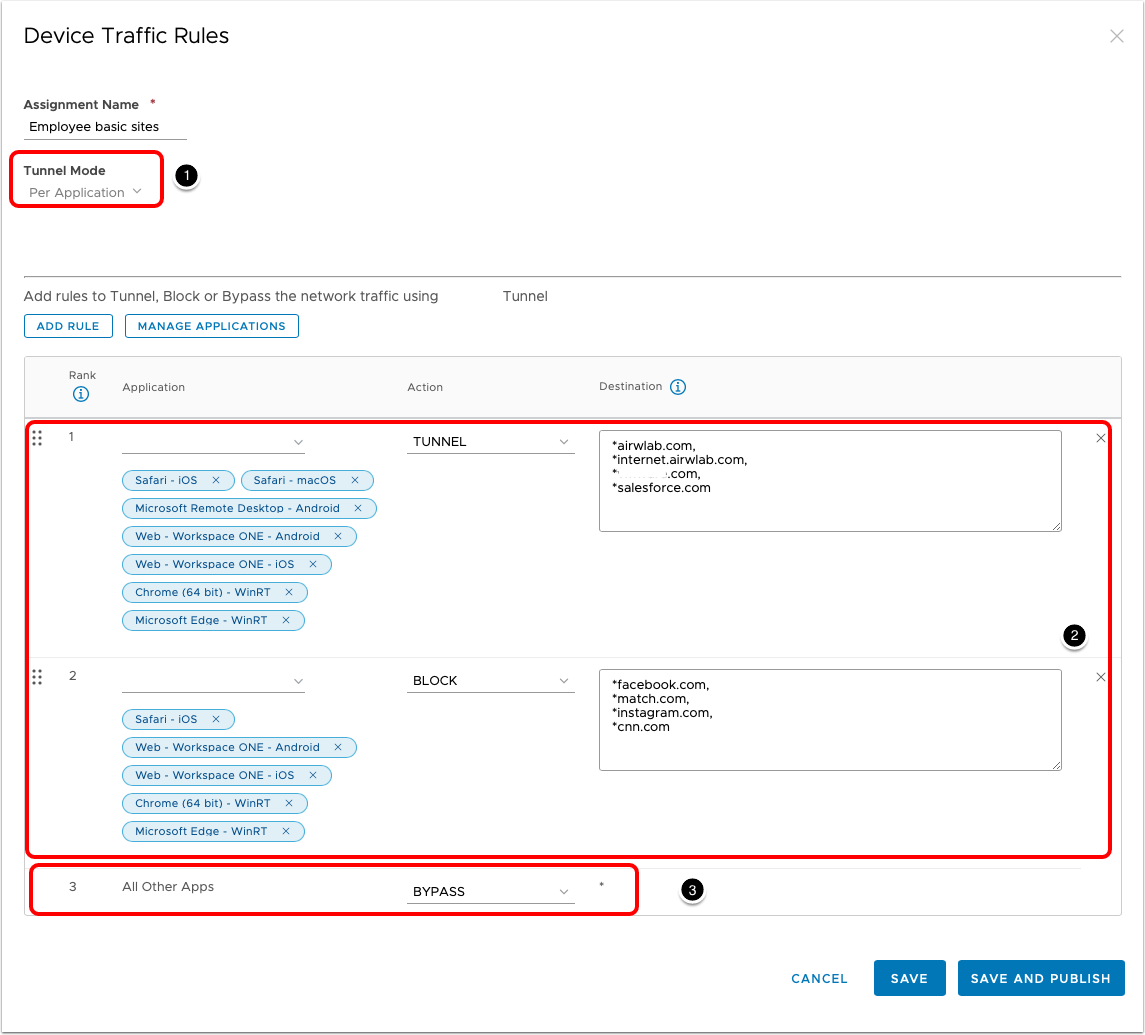
Note the following:
- Tunnel Mode for the Device Traffic Rules Set.
- Per-Application Rules.
- Default Action Rule that will be performed when the client traffic doesn't match rules 1 and 2.
Full Device Traffic Rules
When the Tunnel Mode is set to Full Device, traffic is restricted based on the domains specified in the rules. Note: You cannot configure applications as part of this rule.
Full Device mode requires Workspace ONE UEM 2102+, Workspace ONE Desktop Tunnel 2.1+, and it is available only on Windows 10+.
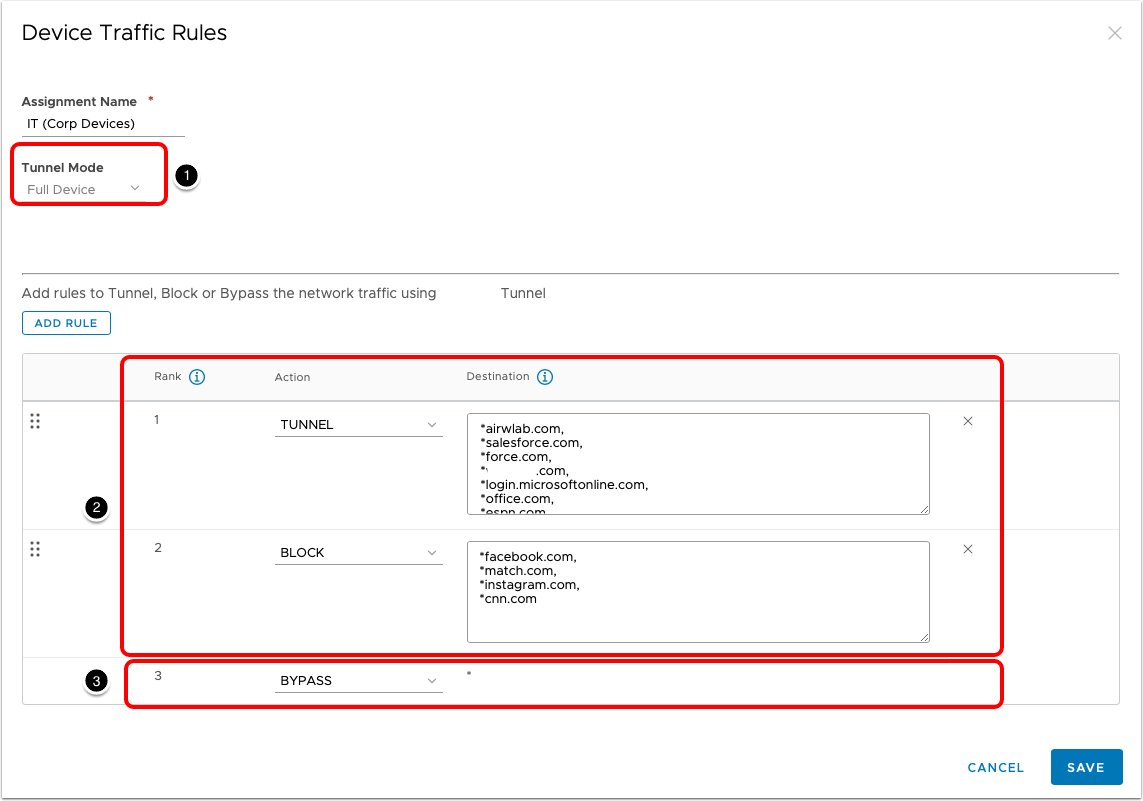
Note the following:
- Tunnel Mode for the Device Traffic Rules Set.
- Full Device Rules.
- Default Action Rule that will be performed when the client traffic doesn't match rules 1 and 2.
Device Traffic Rules Wildcard Guidelines and use of asterisk (*)
When defining the Device Traffic Rules destination, the administrator can enter a list of domains to allow, block, or bypass traffic.
The wildcard is supported for the hostnames and multiple entries must be separated by a comma (,).
Supported Wildcard and use of asterisk (*)
You can use wildcard characters for your hostnames. Wildcards must follow the format:
- *.<domain>.*
- *<domain>.*
- Includes primary domain and subdomains - for example, www.example.com, example.com, store.example.com
- *.* — You cannot use this wildcard for Safari domain rules (iOS and macOS specific)
- — You cannot use this wildcard for Safari domain rules (iOS and macOS specific)
IP and Port Ranges Format Support on Device Traffic Rules
Use of IPs and port ranges are only supported for Device Traffic Rules on Windows 10+ devices. The following list contains supported formats for the IPv4 & Port range when applying the Device Traffic Rules (DTR).
- Single IP
- 10.10.0.1 or 10.10.10.1/32
- IP range or subnet
- 10.10.10.1/24
- 10.10.0.0/16
- Single Port
- *.example.com:80, 10.10.10.1:80,10.10.11.1/32:80
- *.example.com:[443], 10.10.11.1/24:[443]
- Port Range
- *.example.com:[80-443], 10.10.10.1:[80-443],10.10.11.1/32:[80-443]
- 10.10.11.1/24:[80-443]
- List of Ports
- *.example.com:[80,443], 10.10.10.1:[80,443],10.10.11.1/32:[80,443]
- 10.10.11.1/24:[80,443]
- List of Ports and Ranges
- *.example.com:[80,443, 8080-8085], 10.10.10.1:[80,443,8080-8085],10.10.11.1/32:[80,443,8080-8085]
- 10.10.11.1/24:[80,443,8080-8085]
Publishing Device Traffic Rules
When making changes to the Device Traffic Rules, they need to be sent to the device to take effect. This process requires synchronization between the device and UEM and can be applied to existing managed devices or only newly enrolled devices. This chapter describes the difference between Save and Save and Publish device traffic rules set, in addition to how the changes will be sent to the device.
Save and Publish Device Traffic Rules Flow
When the administrator changes the Device Traffic Rules and clicks Save and Publish, an updated version of the VPN profile mapped to the Device Traffic Rules will be created and queued for all the assigned devices. That process will reissue the client certificate as part of the profile to the device with a new thumbprint.
The Tunnel client app might not be able to establish a connection with Tunnel Service until the new VPN profile gets installed on the device. Forcing a sync on the device can speed up the profile installation but in environments with a large number of devices, this process can take additional time.
The Save and Publish option is only available on the default Device Traffic Rules set.
Save Device Traffic Rules Flow
When the administrator changes the Device Traffic Rules set and clicks Save, the Device Traffic Rules get mapped to the profile, but the updated Device Traffic Rules are not replaced for the devices where the VPN profile is already installed. Device Traffic Rules are only updated for the newly enrolled devices or for the devices that have the VPN profile reinstalled.
Save is the only option available for a non-default Device Traffic Rules set - this means that after you change the device traffic rule set and hit save, you must push a new version of the VPN profile to current devices where the profile was already deployed.
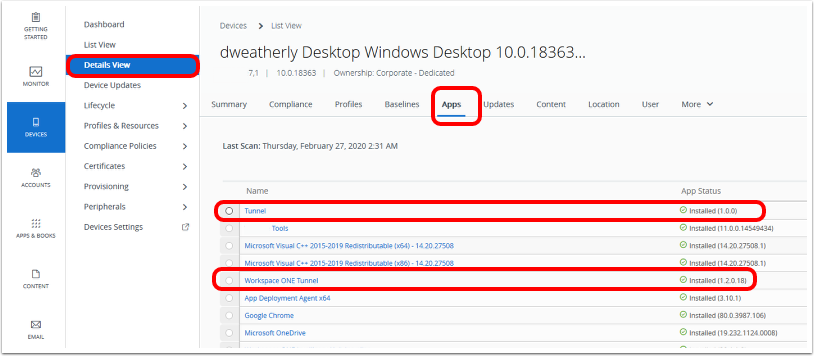
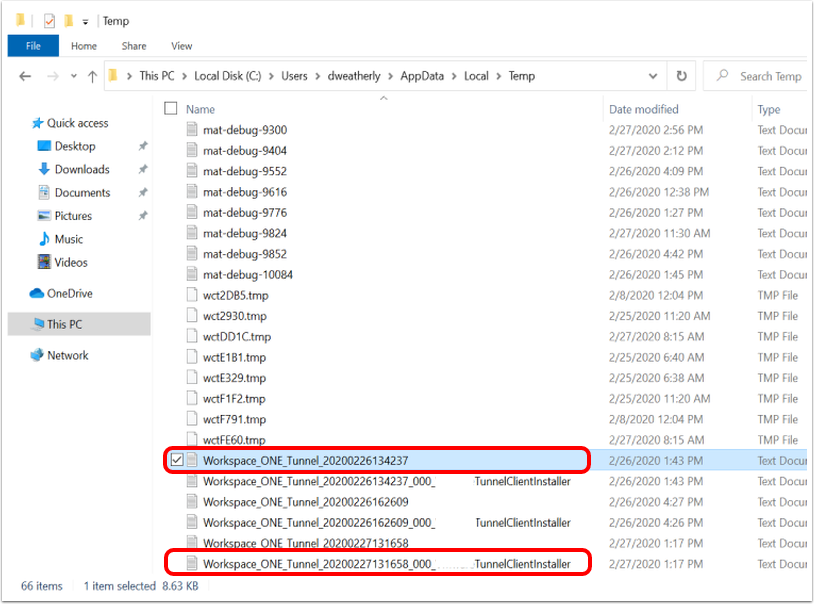
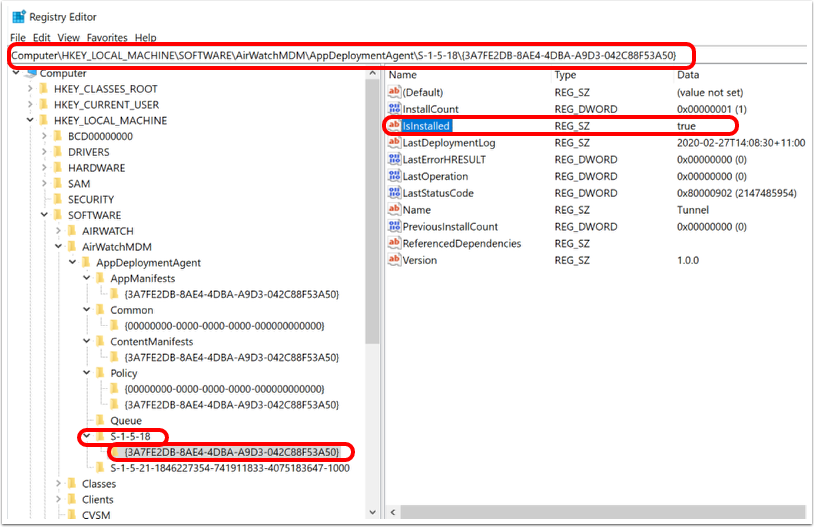
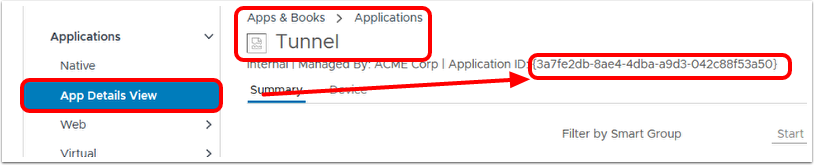
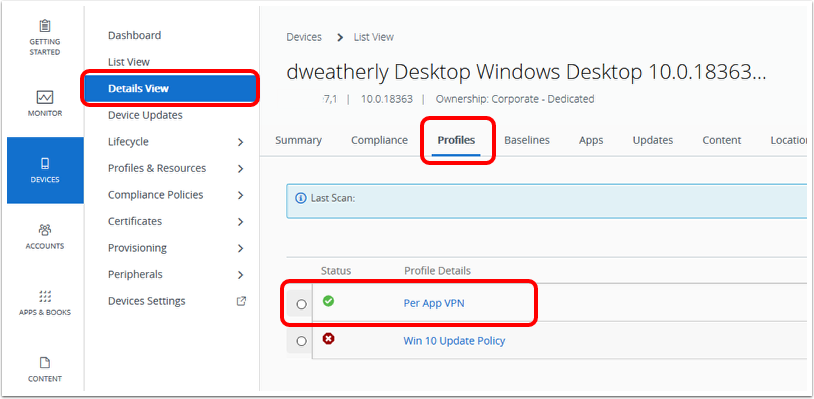
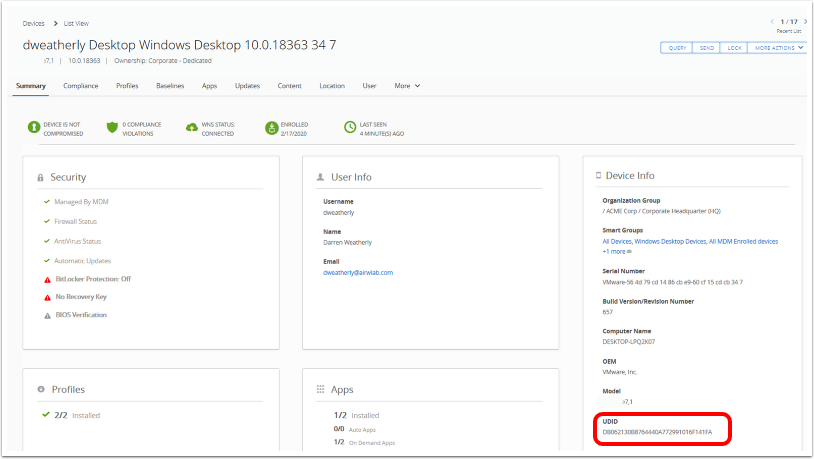
Identify the VPN Profile Status (Installed, Not Installed, Pending Install, and Assigned)
As mentioned previously, publishing a device traffic rule or changes on the VPN Profile will create a new profile version and queue it to all assigned devices. The tunnel client might not be able to establish a connection with the Tunnel Service until the new profile comes down to the device. The administrator can monitor the deployment status of the new VPN profile with the following steps:
Locate the VPN profile under the Resources / Profiles & Base Lines / Profiles and click the View link to identify the total number of profiles not installed, installed, and assigned. Click the Not Installed hyperlink to push the profile manually.
Locate the device under the Devices / List View, select the Profile page, and point to the Profile Status. Selecting the profile allows you to send a command to remove or install the profile on the respective device.
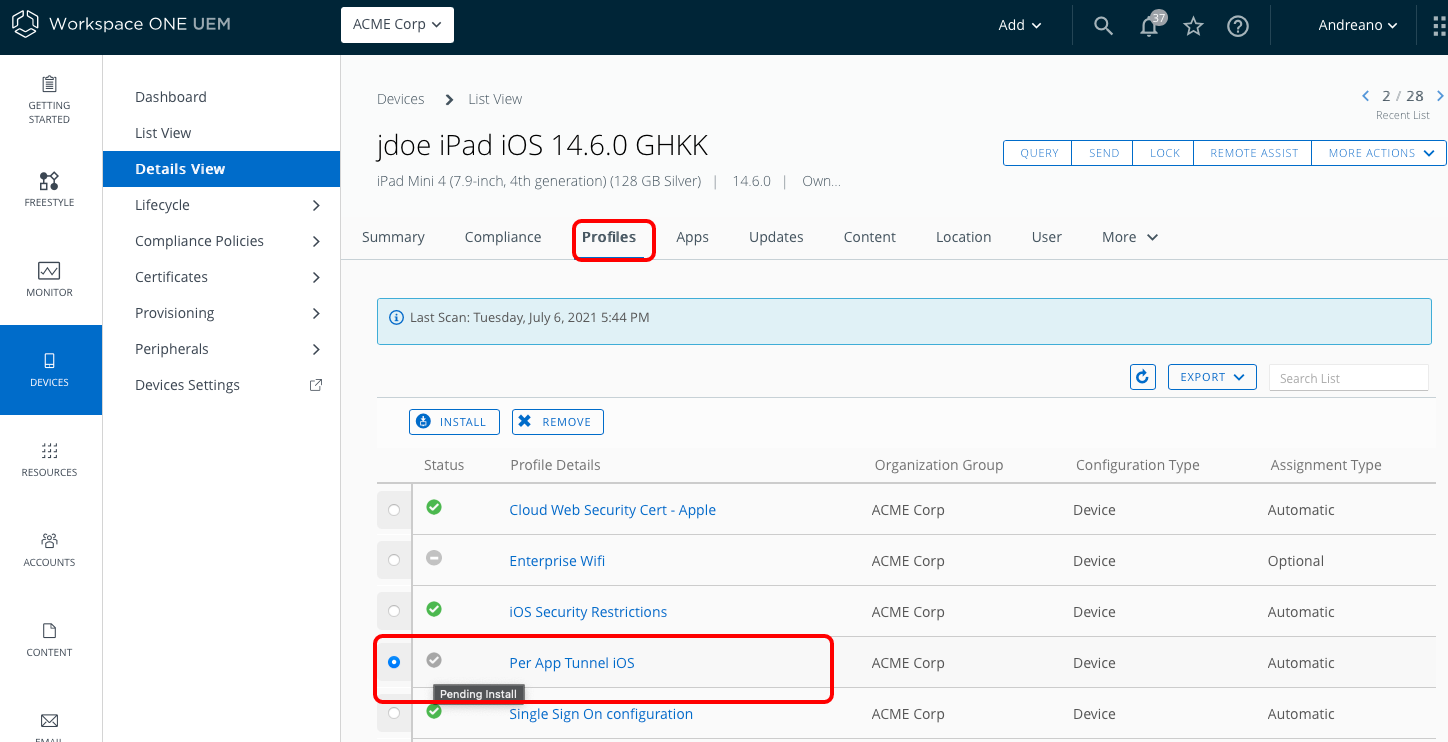
New Device Traffic Rules Sync Process
A new process to sync Device Traffic Rules (DTR) will be implemented on the Workspace ONE Tunnel App to minimize the push of the Tunnel profile to the device every time the DTR changes. This new process, as of today, is only available for Android and requires Workspace ONE UEM 2209+ and Workspace ONE Tunnel version 2209.
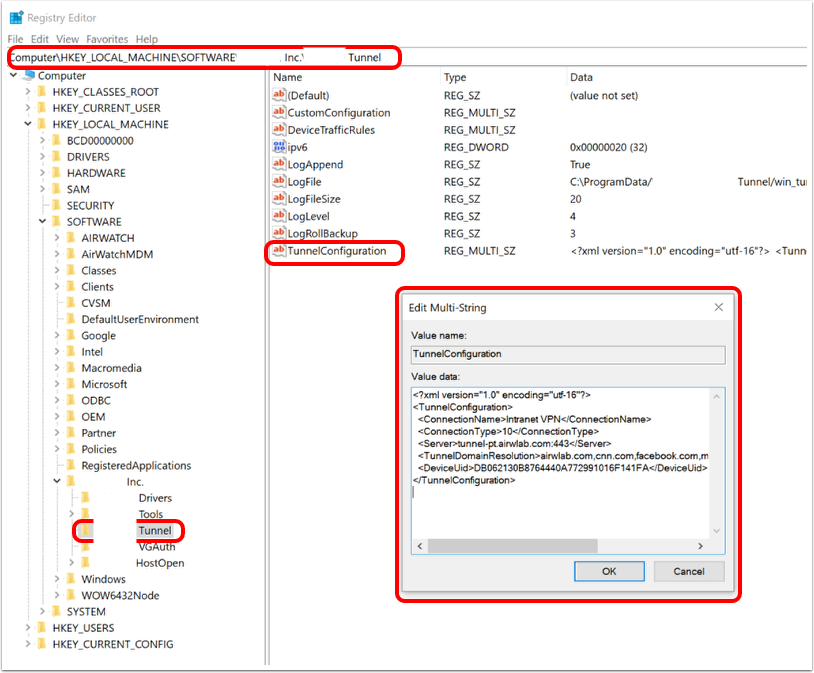
The new process requires you to enable the Workspace ONE Tunnel client to request the DTR from a Tunnel API endpoint (hosted on UEM) automatically on every launch or every 4 hours (default). The new Tunnel API endpoint is identified as http://ws1-api-server/DevicesGateway/devices/{deviceuuid}/tunnel/{tunnelconfiguuid}/configuration?device-traffic-rule-set-uuid={dtr-set-uuid} (TunnelConfigurationSyncEndpointUrl) and is invoked by the Workspace ONE Tunnel client to obtain the new DTR.
- By default, the client syncs DTR every 4 hours.
- This value can be changed via the client_sync_interval key in Custom Settings on the Tunnel Configuration Page. The value is specified in minutes.
Workspace ONE Tunnel client would reach the TunnelConfigurationSyncEndpointUrl on every launch, so modifying the client_sync_interval is not recommended unless you have a critical use case. The following table provides the sync interval recommendation based on the number of devices enrolled.
| Number of devices in the environment | Sync Interval |
| 1 – 50,000 | 15 minutes |
| 50,000 – 100,000 | 30 minutes |
| 100,000 – 200,000 | 60 minutes |
| 200,000 – 500,000 | 120 minutes |
| 500,000 – 1,000,000 | 240 minutes |
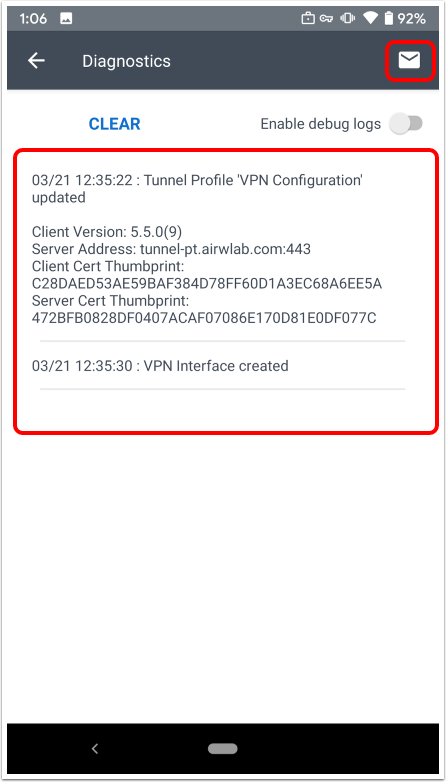
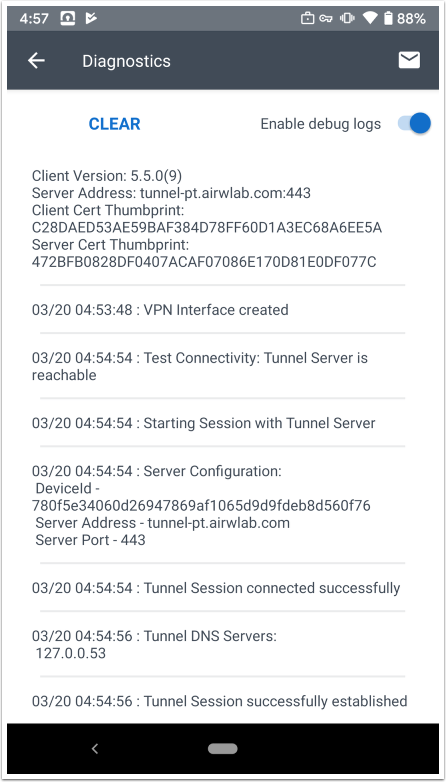
To verify if the tunnel client can sync with the endpoint, open the Diagnostics UI.
Tunnel Client Codes in the UI:
- 200 - DTR was modified in UEM and successfully synced.
- 304 - sync triggered but no changes in DTR.
- 204 - sync triggered but admin has possibly deactivated FF and has not republished the profile to remove sync settings.
To ensure that the client received the settings, the Diagnostics UI displays the Sync Interval and Sync URL as well.
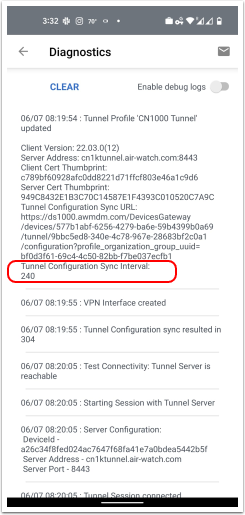
Trusted Network Detection
Trusted Network Detection is a mechanism in the Workspace ONE Tunnel app that determines whether to establish a connection with the Tunnel Service to tunnel access to corporate applications. If the device is connected to the corporate network and trusted network detection is configured, the Workspace ONE Tunnel app does not tunnel traffic to the corporate applications.
The Trusted Probe URL and Trusted Network Detection methods does the same thing by alternate means. In both cases, if Tunnel Client app determines it's on a trusted network, Tunnel will disable itself and displays a Tunnel Disabled - Trusted Network Detected notification in the Tunnel app.
- TrustedProbeURL posts a GET against a URL to determine if it's on a trusted network, if it hits an internal-only endpoint, we know device is on that network. This is the preferred method.
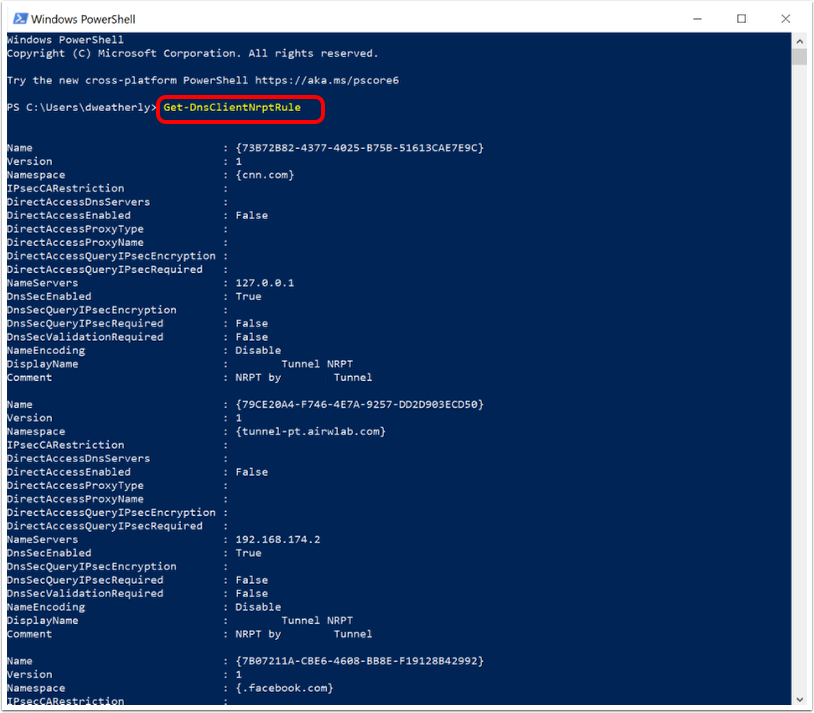
- Trusted Network Detection based on DNS Suffix checks the DNS domain name of network interface to see if it matches. This method is only applicable for windows devices, routing is dependent on DNS and will ignore HOSTS file entries, for other platforms Tunnel uses Probe URL.
- It’s configured at the Workspace ONE Tunnel app level for Android, for other platforms you configure it as part of the VPN payload profile.
Trust Network Detection is supported across multiple platforms, to learn more about other platform support see the How to configure Trusted Network Detection for the Omnissa Tunnel client knowledgebase article.
Trusted Network Detection Based on Probe URL
When using Probe URL (recommend method), Workspace ONE Tunnel will make HTTP calls against the list of private URLs defined in the custom configuration probe URLs to determine if the device is on the trusted network or not.
Administrators can add a list of domains separated by a comma into the Trust Network Detection field. Workspace ONE Tunnel will disable when the device is on a trusted network.
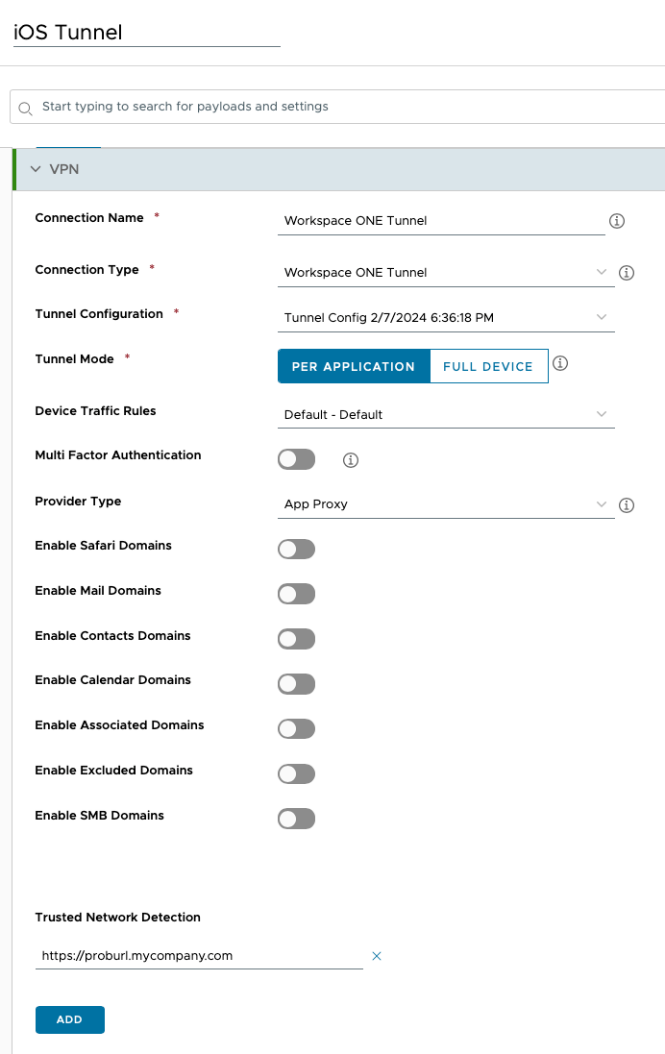
Trusted Network Detection on iOS
For iOS devices, Trusted Network Detection is configured as part for the VPN Profile payload, setting the Trusted Network Detection field.
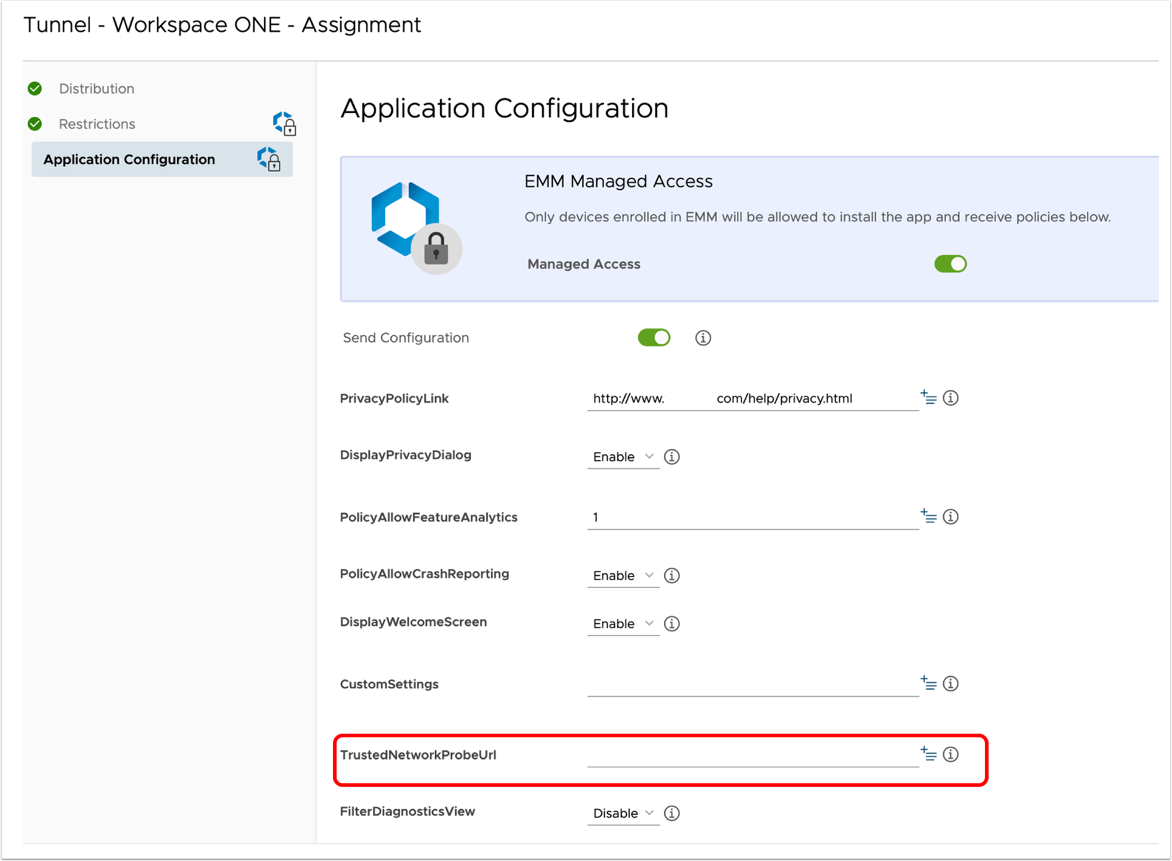
Trusted Network Detection on Android
For Android devices, Trusted Network Detection is configured on the Workspace ONE Tunnel app through App Config, using the TrustedNetworkProbeUrl key, and the value is a list of URLs separated by a comma that can optionally have http/https scheme and an assigned port.
Format examples:
-
<internal-site> -
<internal-site>:<port> -
http://<internal-site> -
http://<internal-site>:80 -
https://<internal-site> -
https://<internal-site>:443
Workspace ONE Tunnel app for Android determines if the device is on the internal network based on the device's ability to reach the private URLs defined as part of the TrustedNetworkProbeUrl.
Trusted Network Detection based on DNS Suffix
When using DNS suffix, Workspace ONE Tunnel compares the DNS suffix defined on the device against the list of trusted networks configured on the Trusted Network Detection field to determine if the device is on the trusted network or not. Every network has its own DNS suffix info. If for a particular network, the DNS suffix matches the pre-configured one, Workspace ONE Tunnel Desktop client know you are on a trusted network
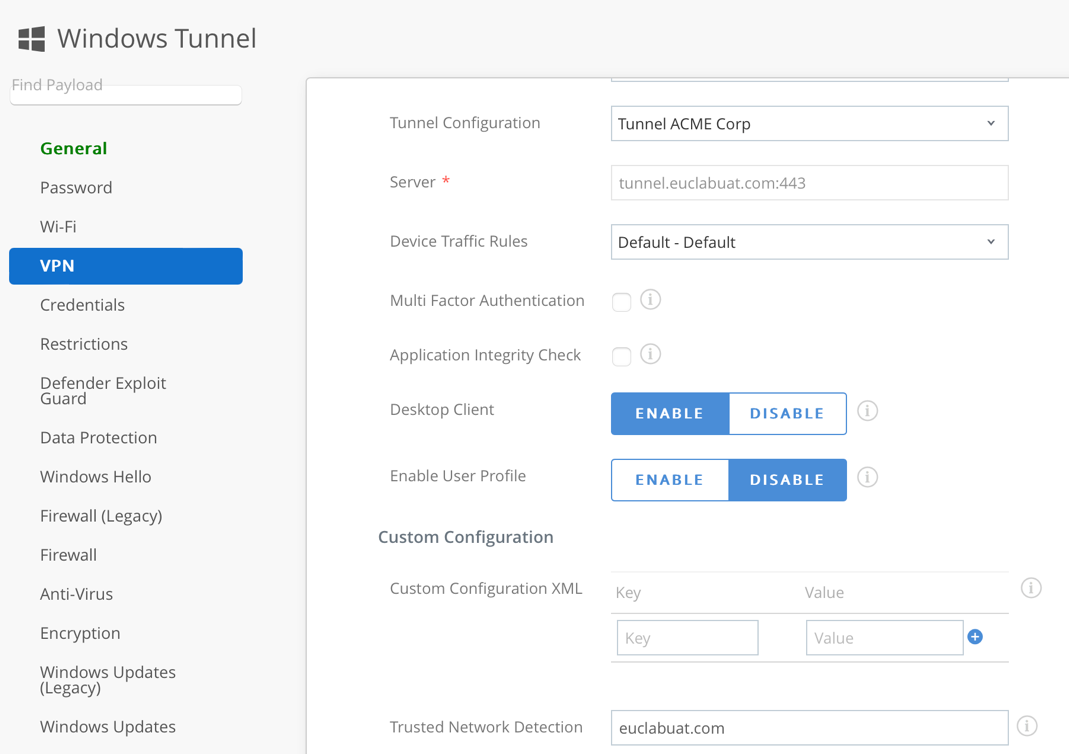
Trusted Network Detection on Windows Devices
For Windows devices, Trusted Network Detection is configured as part of the Per-App VPN payload and can be configured leveraging DNS suffix or internal URL (probe URL using Custom Config XML).
Administrators can add a list of domains separated by a comma into the Trusted Network Detection field (see the following screenshot) and that will leverage DNS suffix. Workspace ONE Tunnel fails to connect when the device is on a trusted network.
Next Steps
The procedures in this tutorial consist of the following:
- Device Traffic Rule configuration
- Deployment of Per-App VPN Profile
- Deployment of Workspace ONE Tunnel Client
- Testing configurations on the chosen device
The procedures are almost the same for each platform. To ensure you understand any existing particularity and stay focused on the platform of your choice, the following steps in this tutorial are organized per platform.
Deploying Workspace ONE Tunnel for iOS
Per-App Tunneling helps users to access critical information using applications on their devices from their devices. Mobile flows help users perform business-critical tasks from a single app — streamlining the user experience.
Leveraging Per-App Tunnel allows you to control which applications are on a device and what internal resources the applications have access to by automatically activating or deactivating Per-App VPN access, based on which applications are active. By enabling remote access, you no longer need to provide a device-wide VPN on your devices, which can allow unintended or unauthorized apps or processes to access your VPN. In this tutorial, you configure and deploy Workspace ONE Tunnel to enable the Per-App Tunnel component on managed devices.
These exercises involve the following components:
- Workspace ONE Tunnel – The app used on the device to securely connect to the Unified Access Gateway to provide Per-App Tunnel functionality, also referred to as Tunnel Client.
- Unified Access Gateway – The virtual appliance where the Tunnel edge service is installed, and to which the tunnel client connects.
- Per-App Tunnel – Component of Tunnel edge service for connecting to a secure tunnel channel on a per-application basis, which is controlled and configured by the VPN profile payload and Device Traffic Rules.
- Per-App VPN Profile and Device Traffic Rules – The Workspace ONE UEM configuration is pushed to the device that contains the Per-App Tunnel configurations. Every time a specified application is opened, the Workspace ONE Tunnel client evaluates the Device Traffic Rules assigned to it before making any routing decisions and establishes a Per-App tunnel connection with the Unified Access Gateway based on the Per-App VPN Profile configuration.
High-Level Architecture
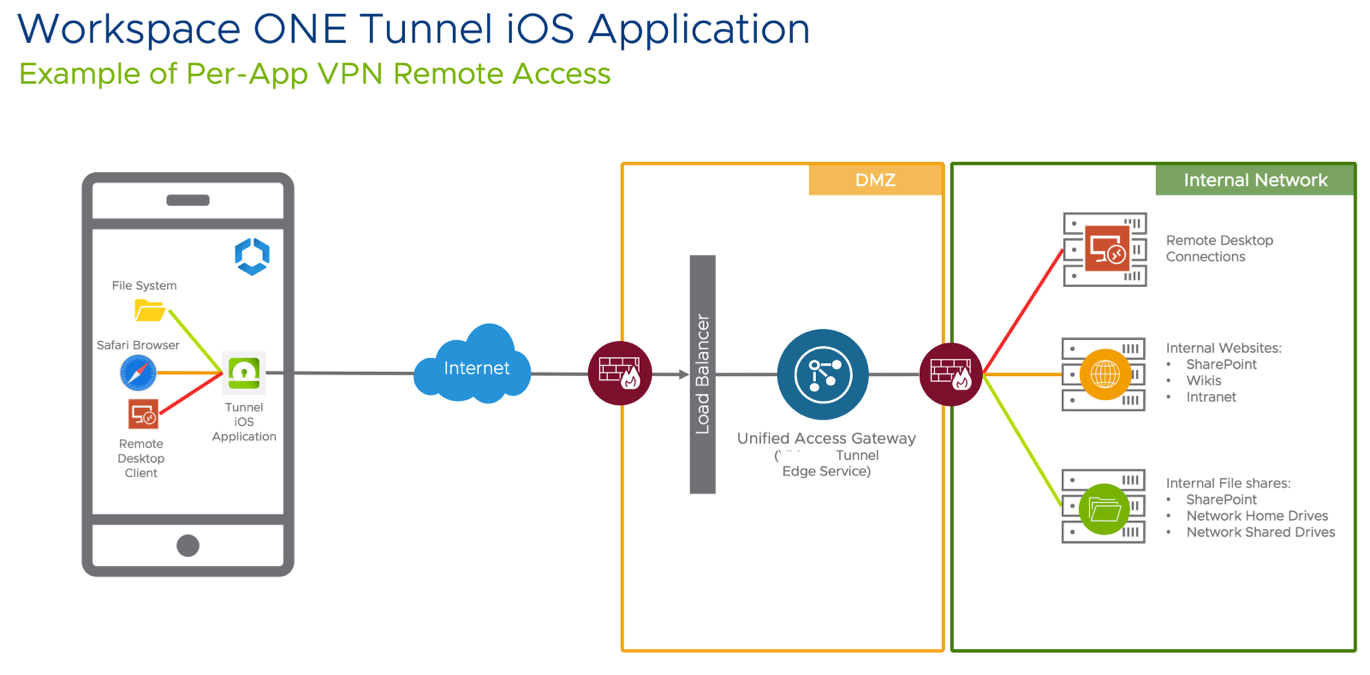
The device contains the applications required by the end-user to perform their daily job. Some applications require access to internal resources to function. Those applications, based on Per-App VPN configuration, use Workspace ONE Tunnel which communicates with the Tunnel Service on Unified Access Gateway hosted on the DMZ, to validate if the device requesting access complies or not before authorizing access through the internal resource.
Prerequisites
Before you can configure the Per-App Tunnel component for iOS, you must have the following components installed and configured:
- Workspace ONE UEM version 2011 and later
- iOS 10.3+ device enrolled in Workspace ONE UEM
- VPN Tunnel must be configured before you can add it as an application
- Workspace ONE Tunnel application for iOS
- Deploy Workspace ONE Tunnel using volume-purchased licenses from Apple Business Manager or Apple School Manager.
- Workspace ONE Administrators must upload the Location token from Apple Business Manager to sync licenses to Workspace ONE UEM for managed distribution.
Configuring Device Traffic Rules for iOS
First, because Apple's Mail, Calendar, and Contacts applications may contain both corporate and personal data, administrators must take an extra step to define corporate-owned domains which should be marked for Per-App Tunnel.
Device traffic rules provide a centralized location to configure which domain traffic uses per-app tunneling. When a Workspace ONE administrator configures devices for Safari on iOS, Workspace ONE automatically merges these parameters into the VPN payload sent to iOS devices. These parameters allow the Tunnel edge service to apply the appropriate device traffic rules for those specific domains.
Second, Safari is another app that may be used for personal use on a corporate device. As such, Safari cannot be configured to tunnel all traffic. Device traffic rules for Safari must specify the domain and top-level domain component (for example, mycompany.com) although an asterisk (*) may be used to wildcard subdomains (for example, *.mycompany.com).
Note: Domain values used in this section are examples only. Your values will differ.
In the Workspace ONE UEM console:
- Navigate to Groups & Settings > Configurations.
- Select Tunnel.

- From the Device Traffic Rules tile, click Edit.
- Click Add or the Default assignment to manage the device traffic rules.
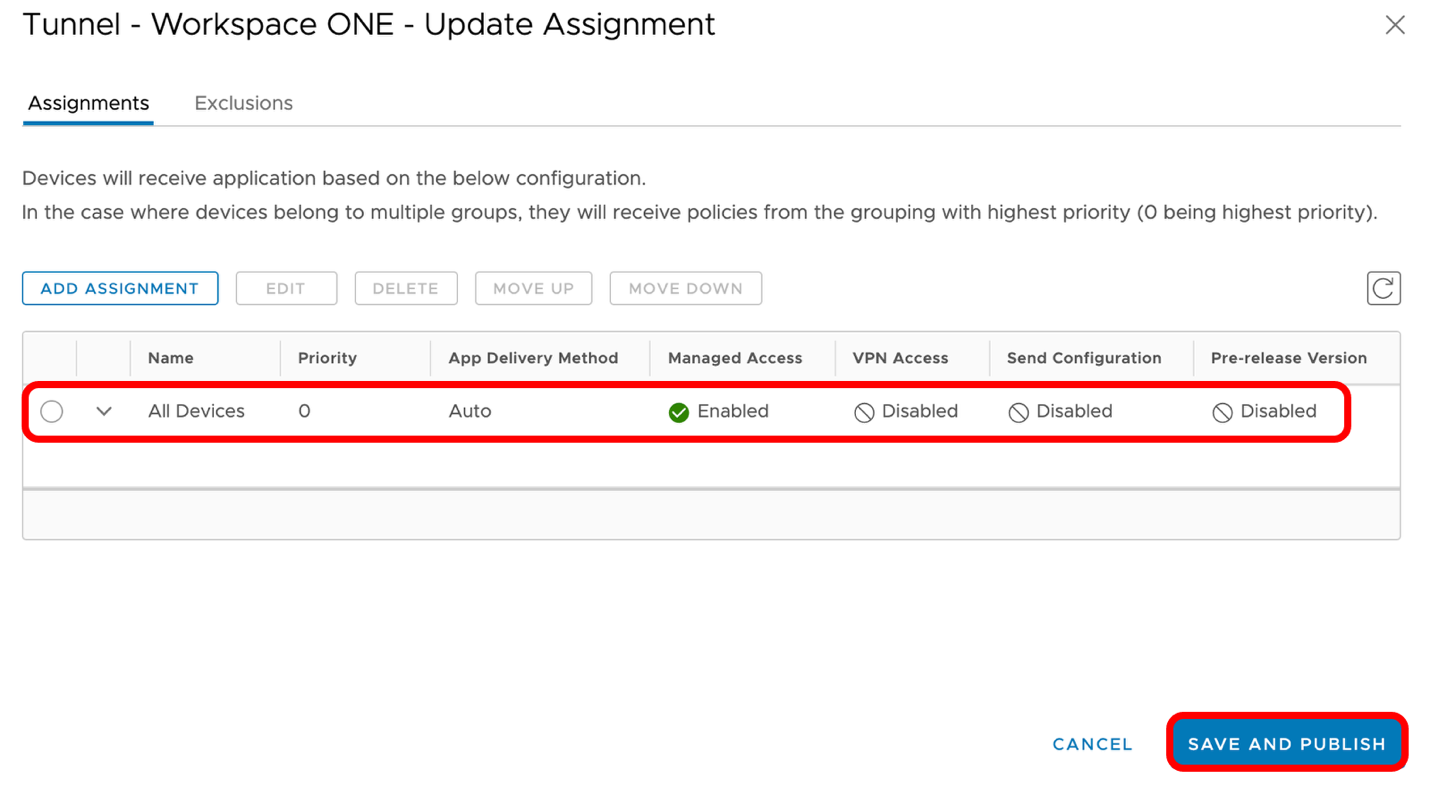
Administrators can create multiple Device Traffic Rules that will be assigned to the Per-APP VPN profile and will deploy to the devices based on the smart group assigned to the Profile. The first device traffic rule assignment created will be set as default.
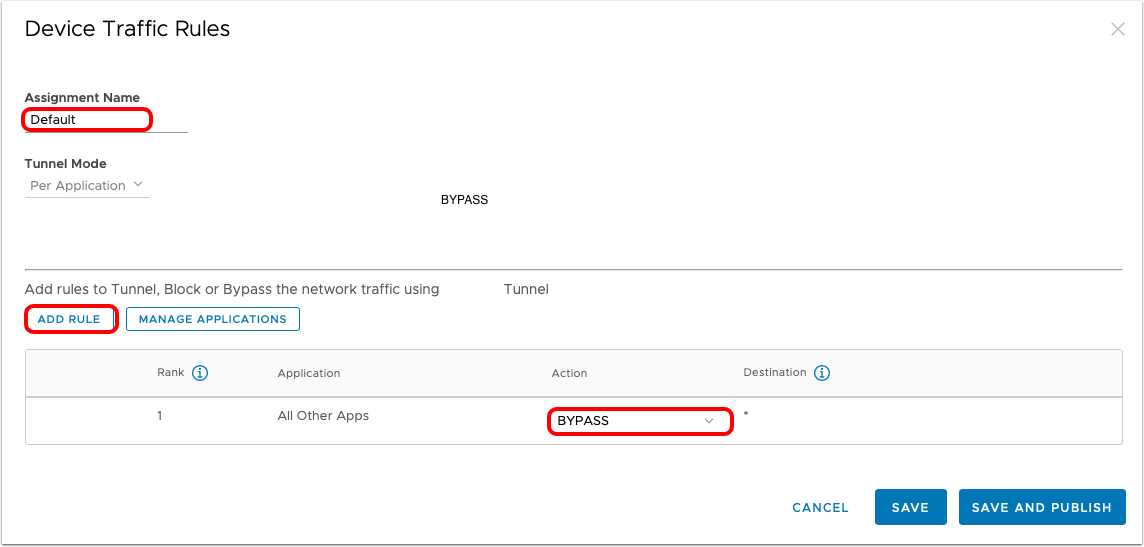
- Observe the default device traffic rule.

- Update the Assignment Name with the name of your choice.
- Observe (or modify) the default action that applies to all iOS applications selected to use Per-App VPN except Safari:
- Tunnel – All apps, except Safari, on the device configured for Per-App Tunnel send network traffic through the tunnel. For example, set the Default Action to Tunnel to ensure all configured apps without a defined traffic rule use the Workspace ONE Tunnel for internal communications.
- Block – Blocks all apps, except Safari, on the device configured for Per-App Tunnel from sending network traffic. For example, set the Default Action to Block to ensure that all configured apps without a defined traffic rule cannot send any network traffic regardless of destination.
- Bypass – All apps, except Safari, on the device configured for Per-App Tunnel, bypass the tunnel and connect to the Internet directly. For example, set the Default Action to Bypass to ensure all configured apps without a defined traffic rule bypass the Workspace ONE Tunnel to access their destination directly.
- Proxy – Redirect traffic to the specified HTTPS proxy for the listed domains. The proxy must be HTTPS and must follow the correct format: https://example.com:port.
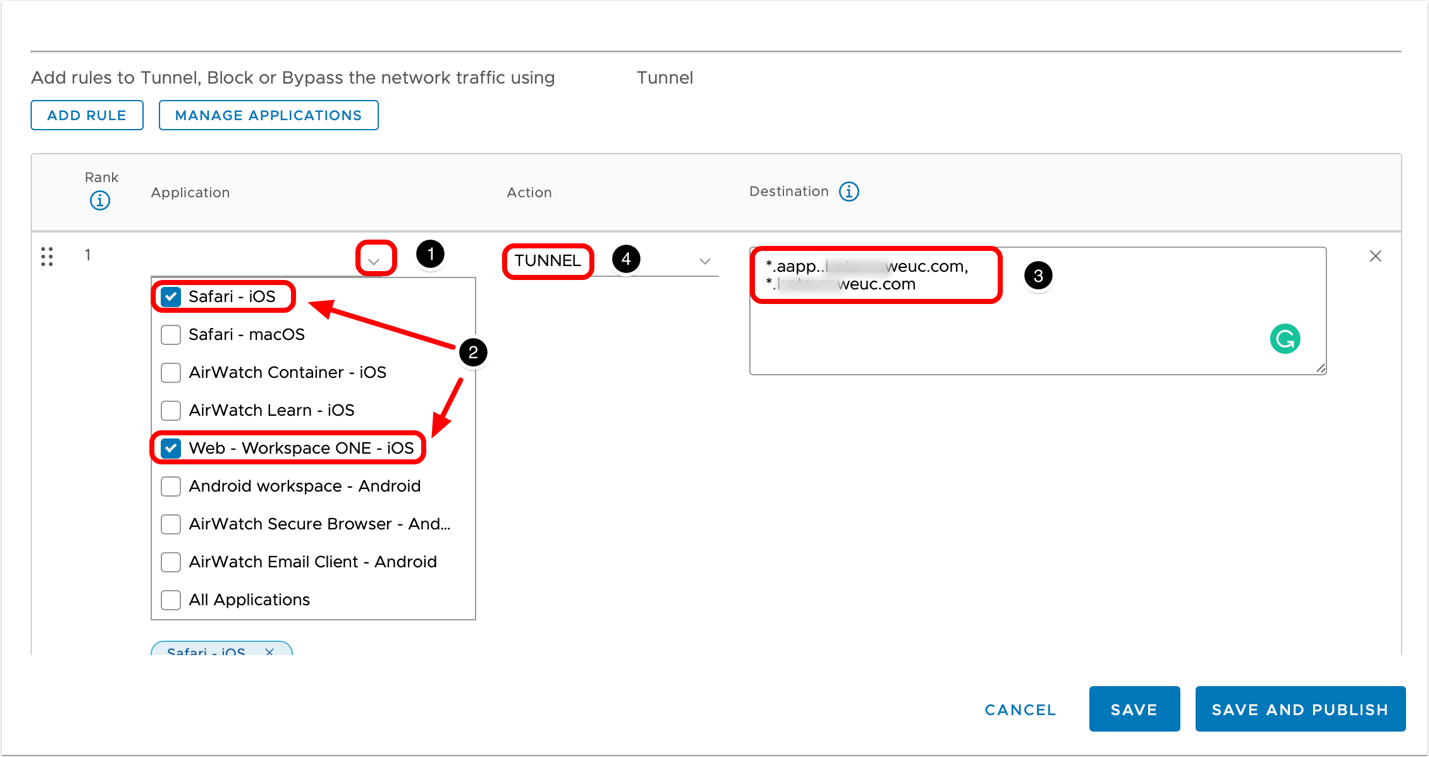
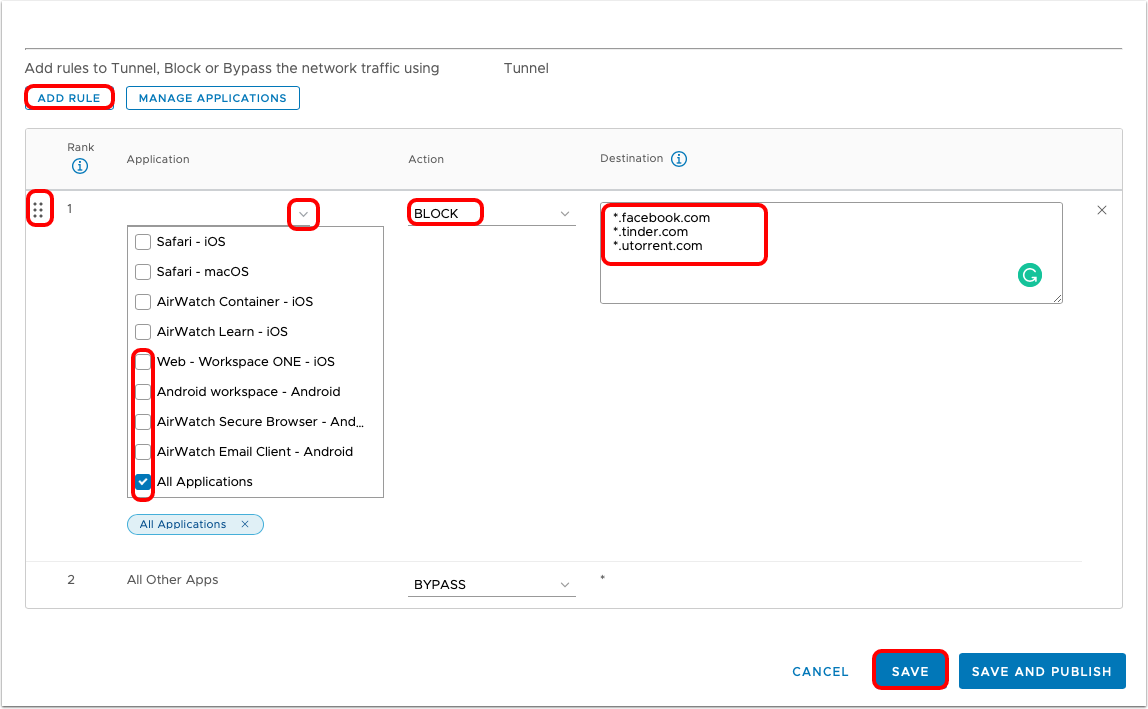
- Click ADD RULE.
- Build the device traffic rule.

- Click the drop-down for the Applications list. Alternatively, select All Applications to apply the rule to all iOS applications listed in the drop-down, which are the ones that you assigned the Per-App VPN profile.
- Select one or more iOS apps for which this rule applies.
- Enter one or more destinations to control via Workspace ONE Tunnel.
- Select the Action to apply for the selected apps when they attempt to access the specified destinations.
For more information on the formats (wildcards, IP, ports) allowed into the Destination field, see the Device Traffic Rules Destination formats supported chapter.
Tip: iOS apps are automatically added to the Applications selection list after you enable an application for Per-App Tunnel when creating assignments in Resources.
Note: Wildcards must follow one of these formats:
- *.<domain>.*
- *<domain>.*
- *.* — You cannot use this wildcard for Safari rules.
- * — You cannot use this wildcard for Safari rules.
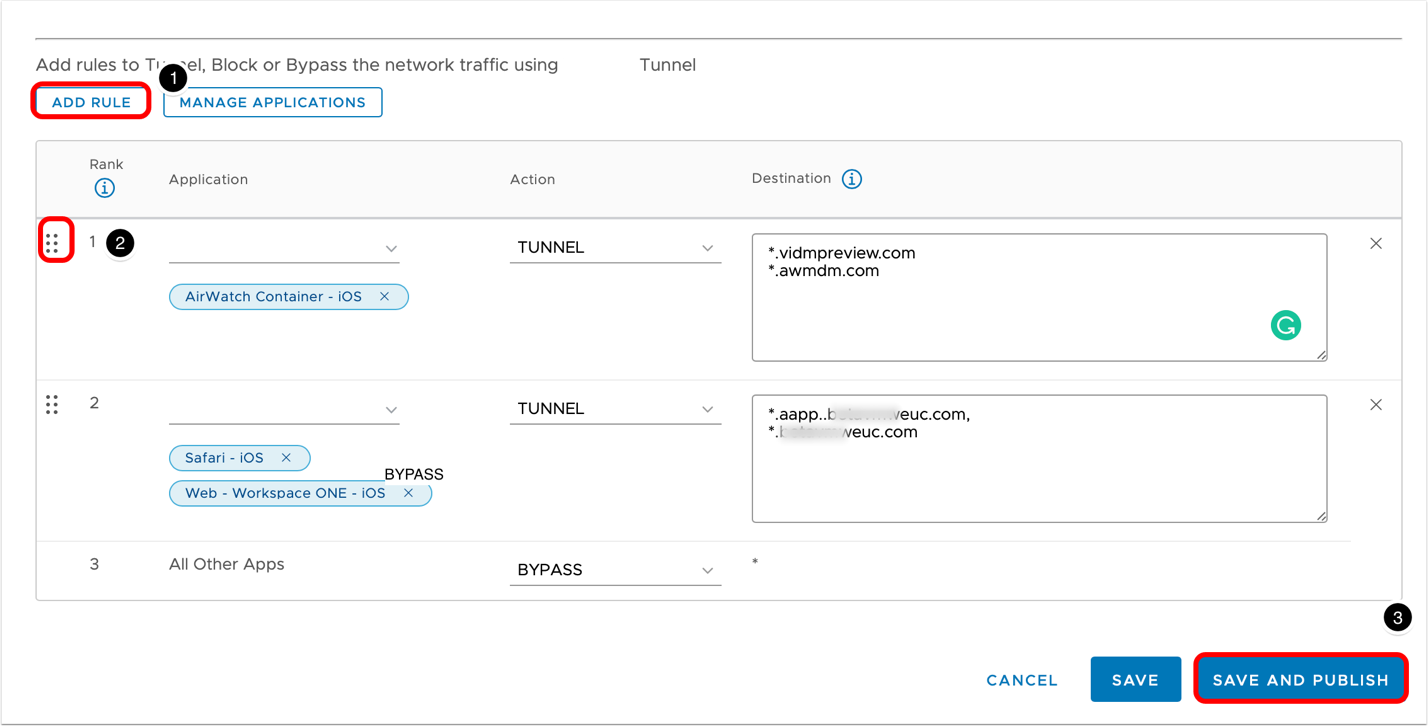
- Add additional rules and publish.

- Click Add Rule and repeat step 6 for any additional required rules.
- Drag the rules to adjust your Device Traffic Rules priority.
- After the Device Traffic Rules are configured as necessary, click Save and Publish.
Distributing Workspace ONE Tunnel for iOS
Workspace ONE Tunnel is an iOS application available for free on the App Store. It is also available for managed distribution volume licensing through Apple Business Manager and Apple School Manager. In both cases, the Workspace ONE Tunnel app can be deployed over-the-air through Workspace ONE UEM as a:
- Public App - this method pushes the application to the device from the App Store and is recommended when your organization doesn't use the Apple VPP program.
- Purchased App - Workspace ONE Tunnel app is free; however, it is also available for managed distribution volume licensing through Apple Business Manager and Apple School Manager. Use device-based licensing to distribute Workspace ONE Tunnel to corporate-managed iOS devices. If your organization has access to Apple Business Manager and you want to manage the license distribution, use this method.
This section demonstrates how to obtain Workspace ONE Tunnel and assign it to devices as a Public or Purchased App.
Note: The VPN tunnel profile should already be configured as part of the Prerequisites.
Distribute Workspace ONE Tunnel as Public App (Apple Store)
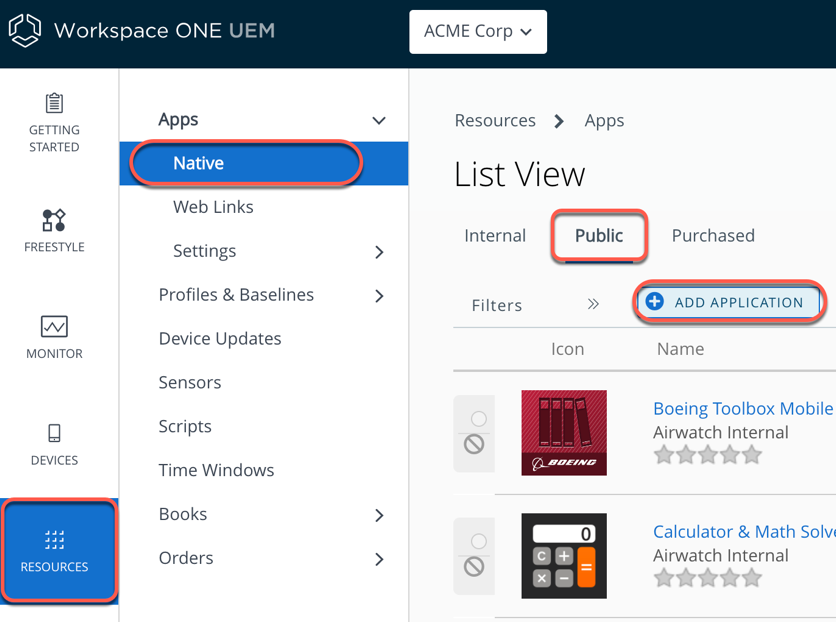
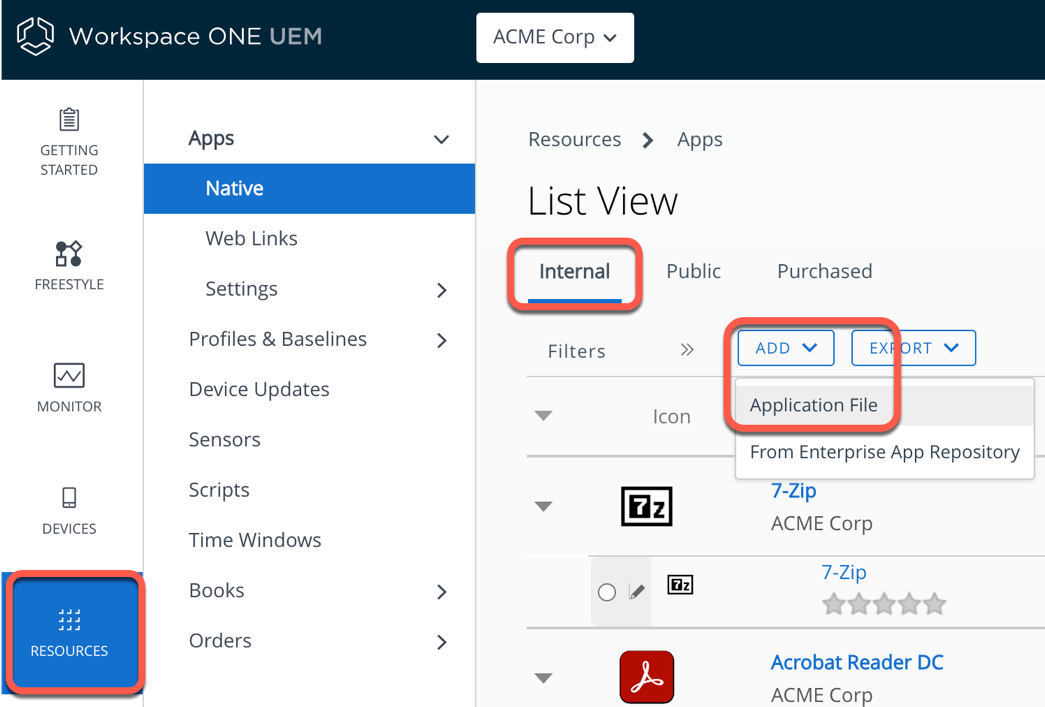
- Add Workspace ONE Tunnel as a public app.

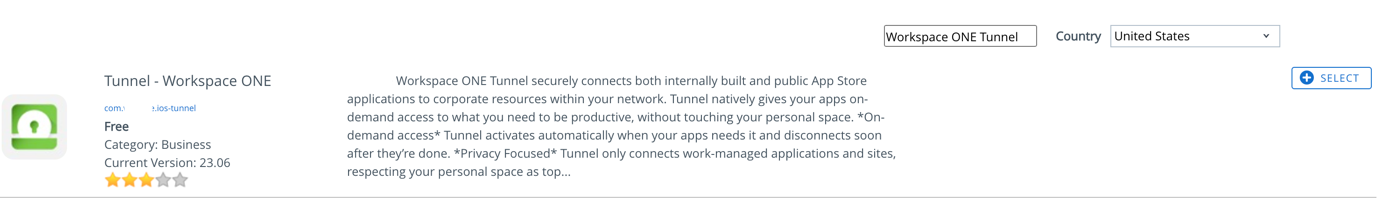
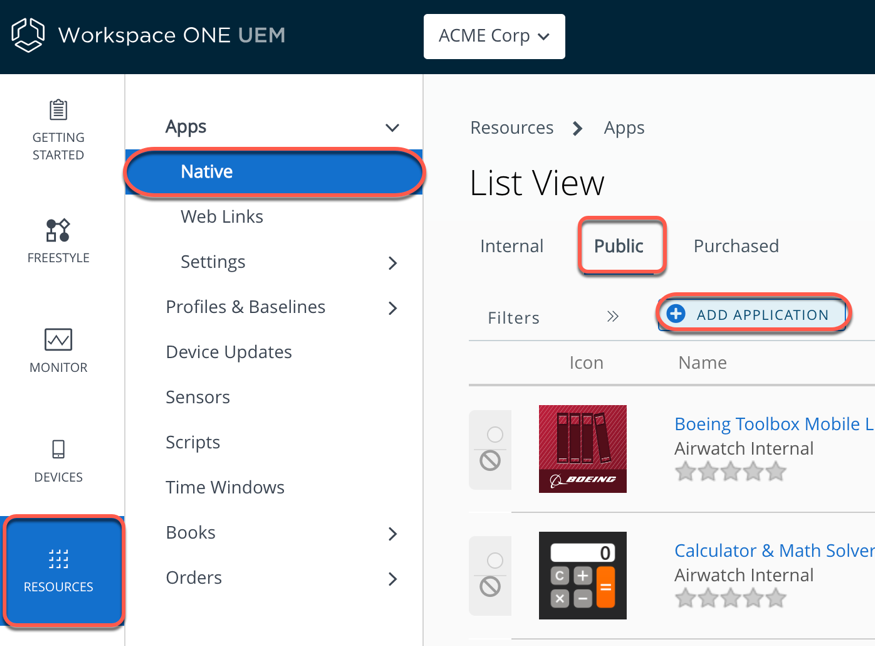
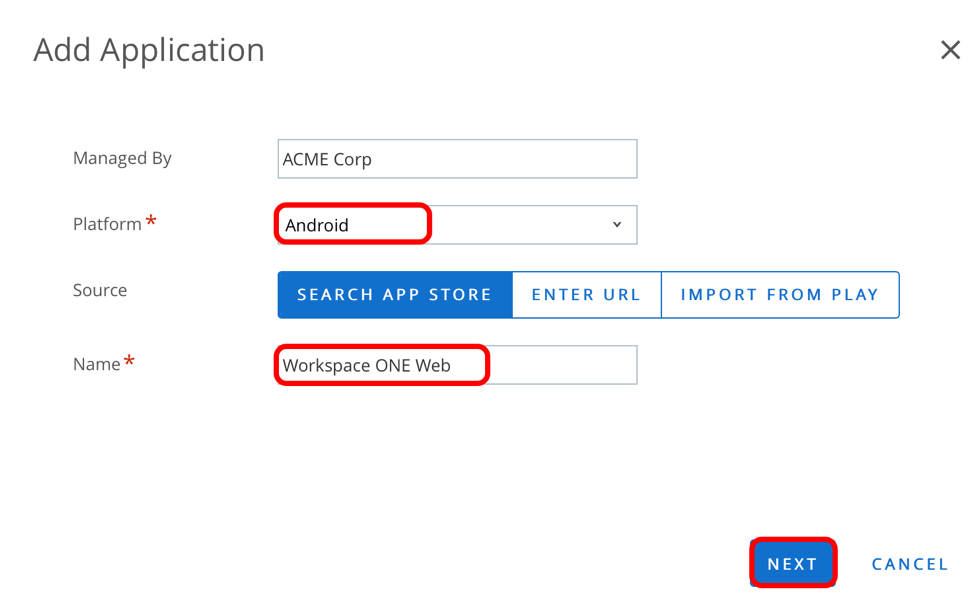
- In the Workspace ONE UEM console, navigate to Resources > Native > Public > Add Application.
- Search for Workspace ONE Tunnel on the Apple store.

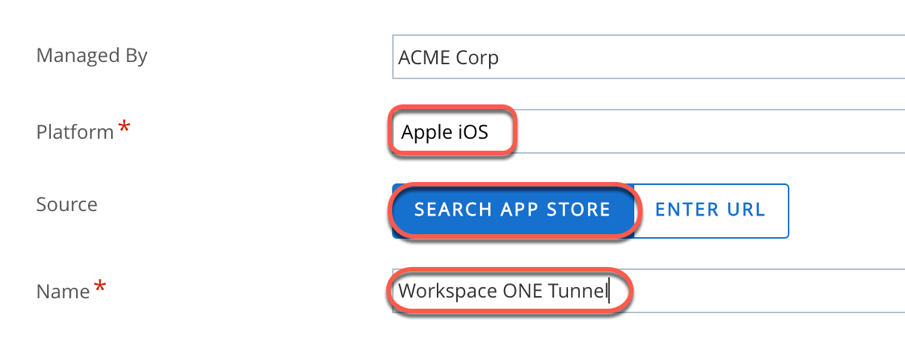
- Select Apple iOS as Platform.
- Select Search App Store for Source.
- Enter Workspace ONE Tunnel.
- Click Next.
- From the search result, click select for Tunnel – Workspace ONE.

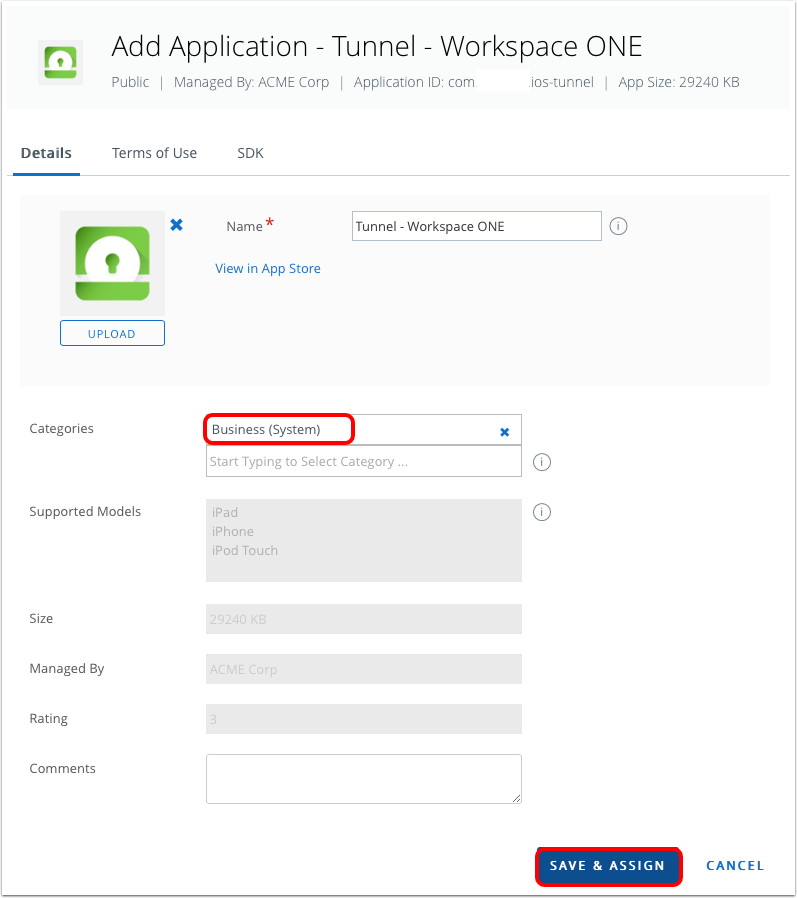
- Save and add the assignment.

- Select Business (System) for the Categories; this is not required; however, it will show the Tunnel app under the specific category in the Intelligence Hub Catalog.
- Click Save & Assign.
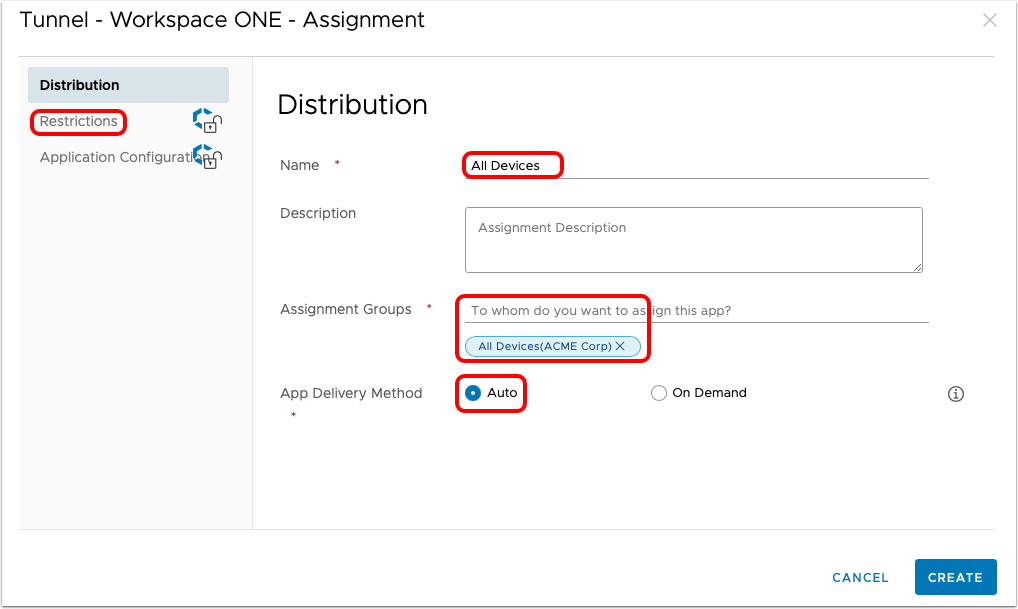
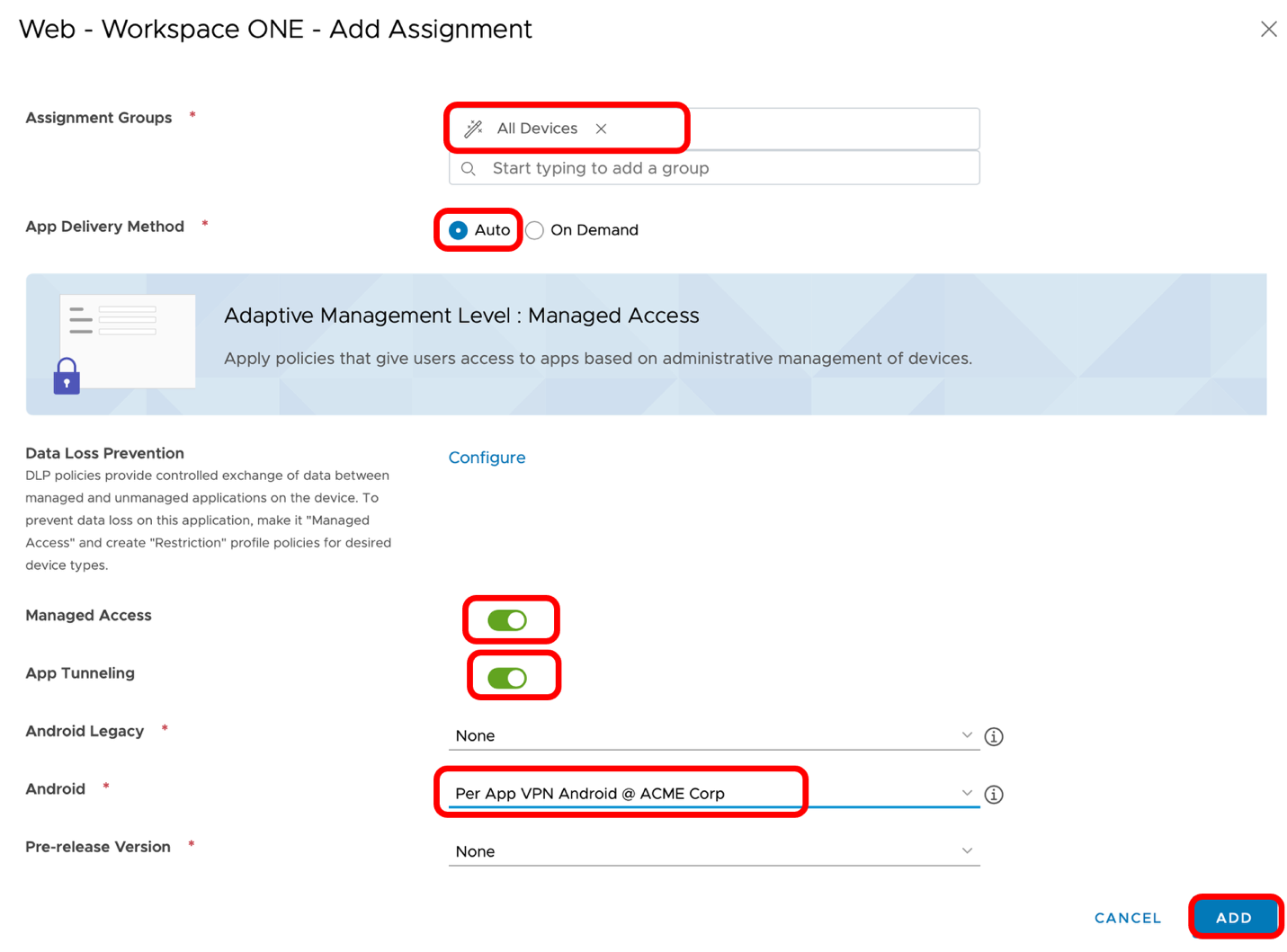
- Define the Assignment.


- Enter All Devices for Name.
- Select All Devices for Assignment Groups or a specific group of devices that you want to target for the tunnel deployment.
- Select Auto for App Delivery Method.
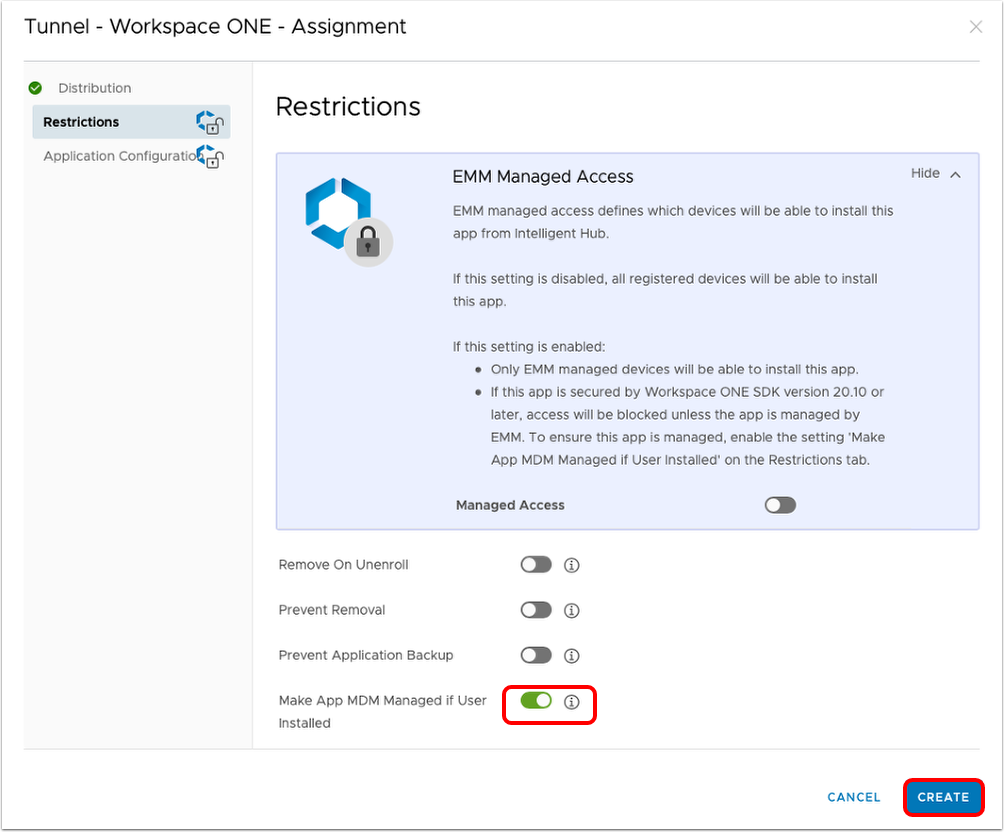
- Click Restrictions.
- Turn ON the Make App MDM Managed if User Installed.
- Click Create.
- Click Save, and then click Publish.
Distribute Workspace ONE Tunnel as Purchased App (Apple Business Manager)
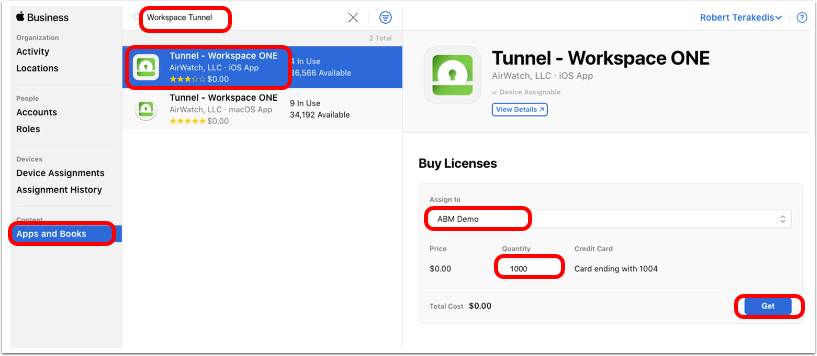
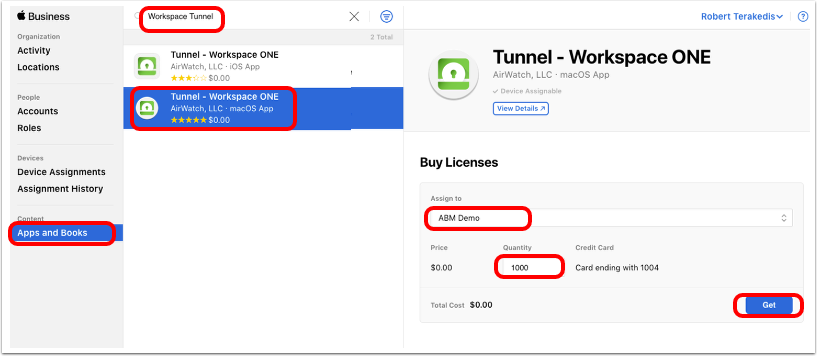
- Get Workspace ONE Tunnel licenses.

- In Apple Business Manager (or Apple School Manager), click Apps and Books.
- Search for workspace tunnel in the search text box.
- Select Tunnel - Workspace ONE for iOS.
- Select the location for which you have uploaded the
sTokeninto Workspace ONE UEM. - Enter the quantity of licenses you want to purchase.
- Click Get. The button changes to Purchasing and when the purchase is complete changes back to Get.
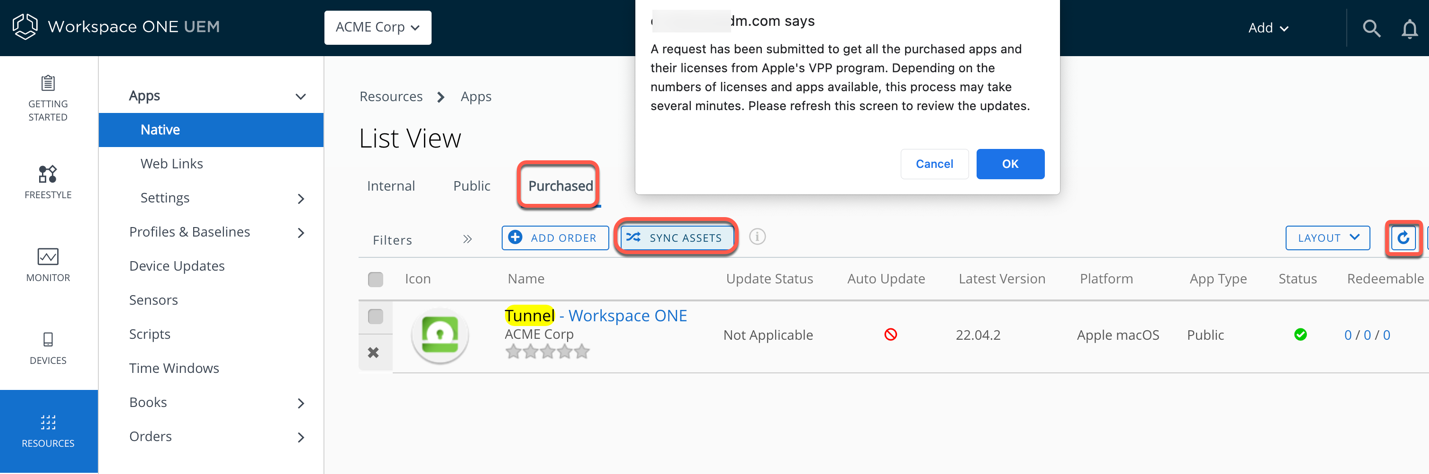
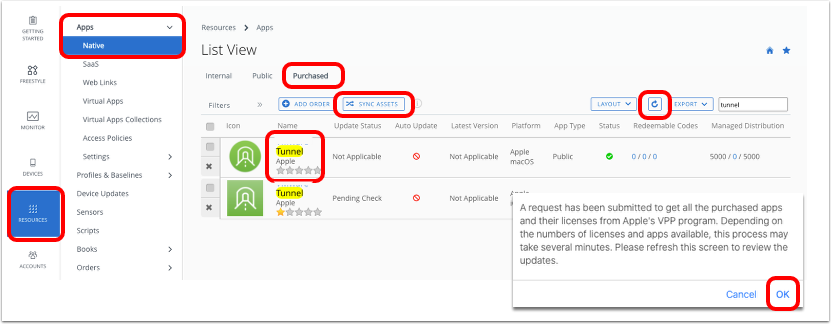
- Sync assets in Workspace ONE UEM.

- In the Workspace ONE UEM console, click Resources.
- Expand Apps and click Native.
- Select Purchased.
- Click Sync Assets.
- Click OK on the dialog box.
- Wait a few moments and click Refresh to update the app list.
- Click the Workspace ONE Tunnel app for iOS in the app list.
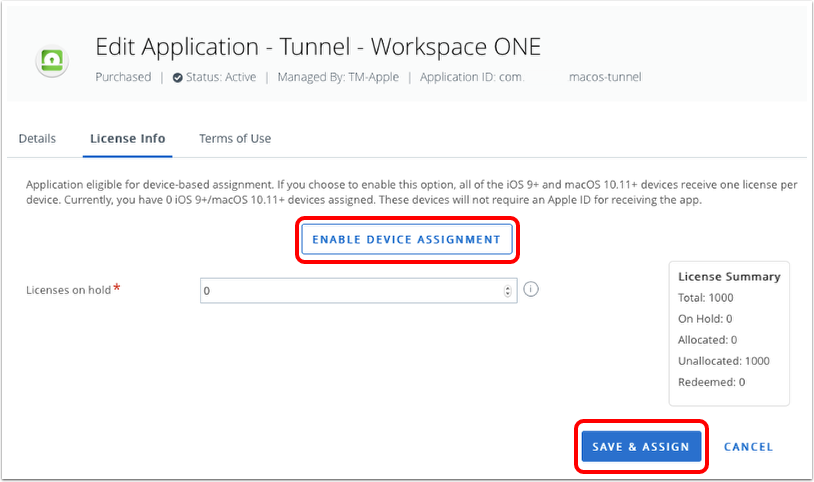
- Enable device assignment.
- Click Enable Device Assignment.
- Click OK to confirm device-based licensing.
- Click Save & Assign.
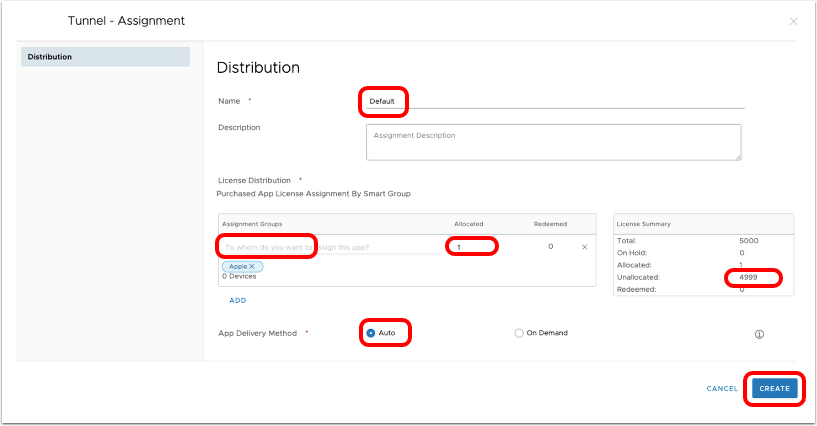
- Click Add Assignment.
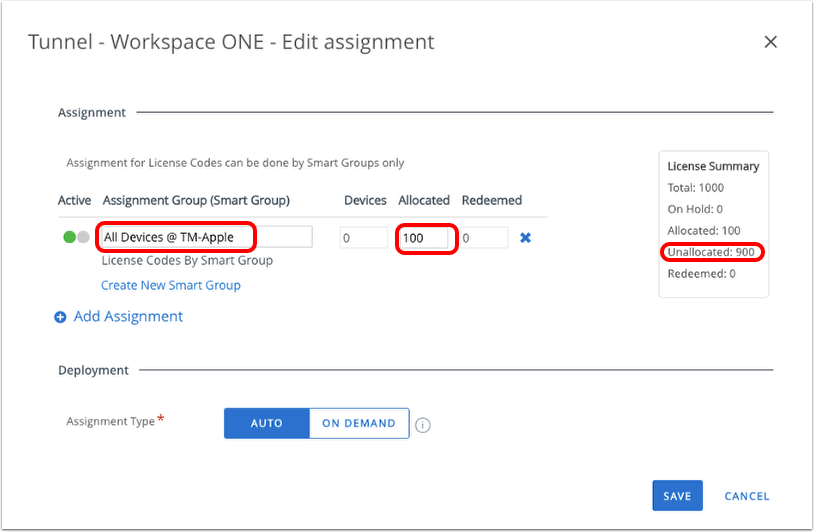
- Edit Assignment.

- Click Add Assignment.
- Select an Assignment Group (or create a new smart group containing the targeted devices).
- Enter the number of licenses to allocate. Allocate up to the total number of unallocated licenses.
- Select Auto.
- Click Save.
- Save Assignment.
- If more assignments are necessary, click Add Assignment and repeat the steps in Edit Assignment.
- Click Save and Publish, then click Publish when all assignments have been added.
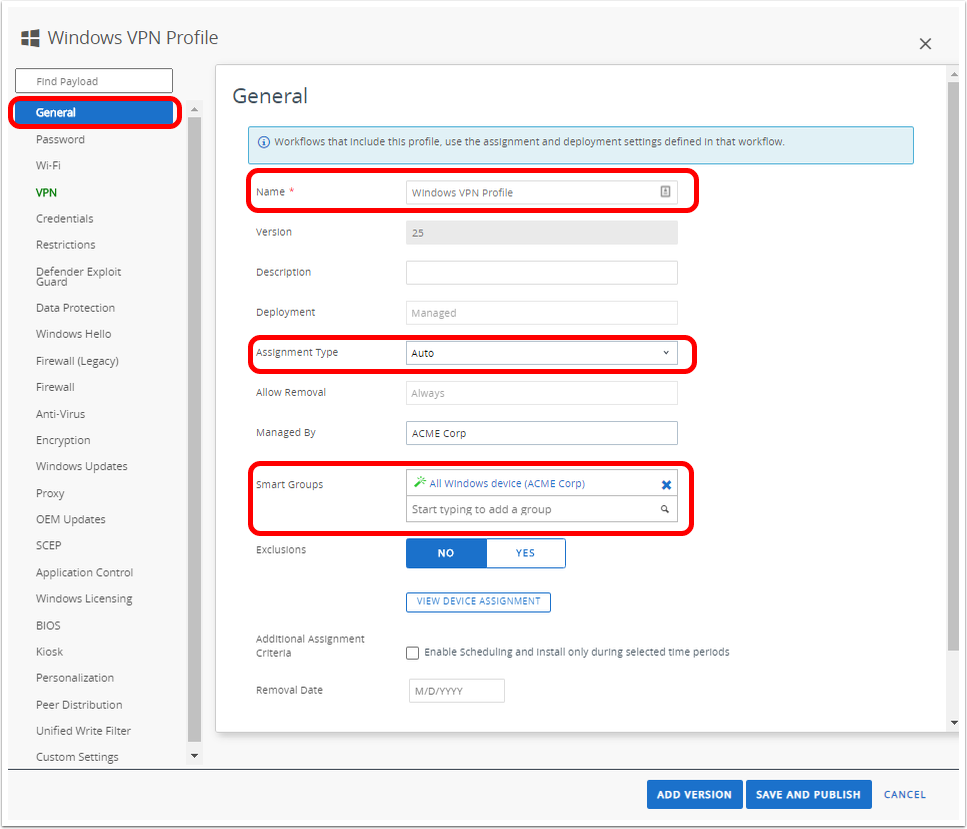
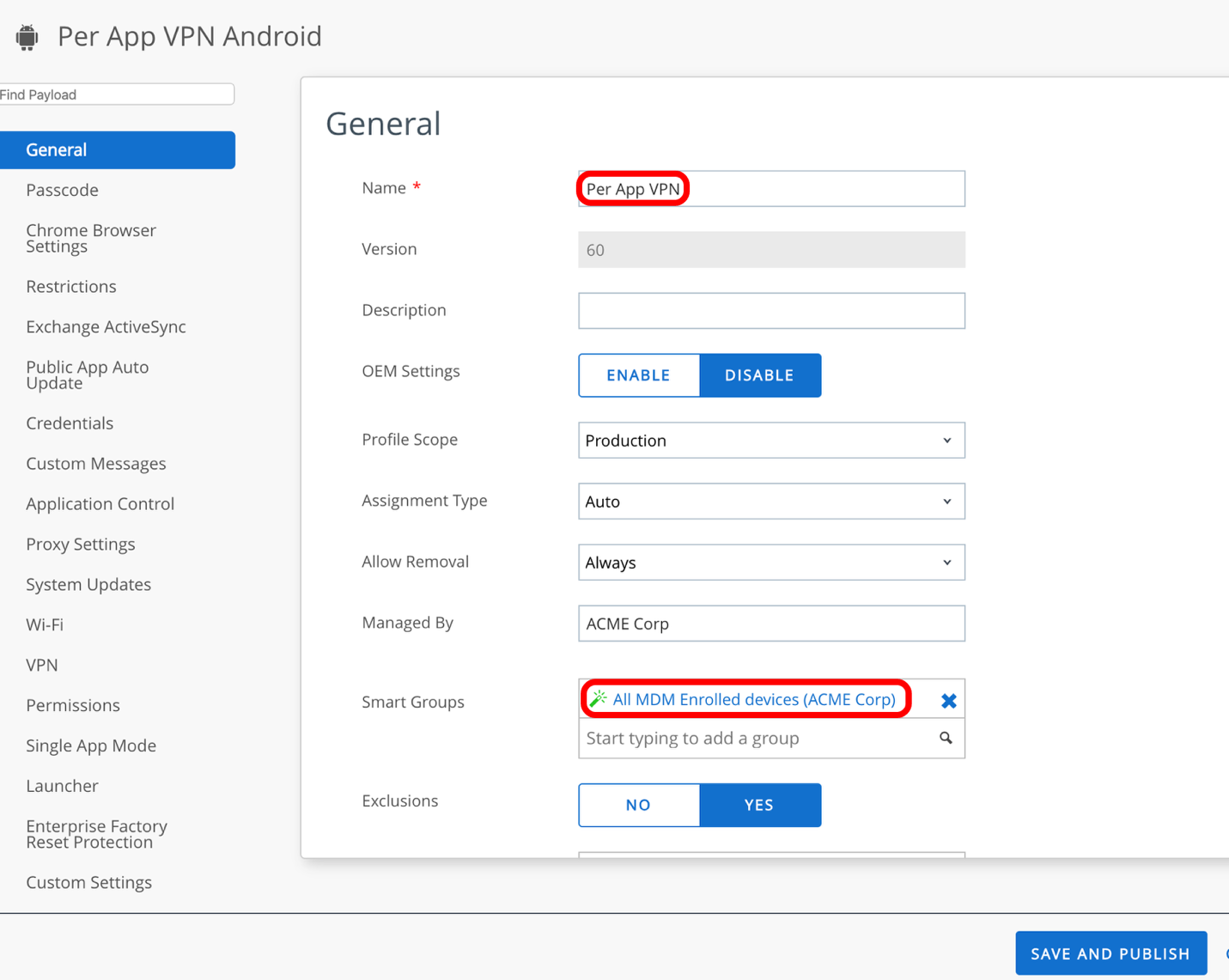
Creating Per-App VPN Profile for iOS
For iOS 7+ devices and Android Enterprise devices, you can force selected applications to connect through your corporate VPN. Your VPN provider must support this feature, and you must publish the applications as managed applications.
In this exercise, you configure the iOS profile which configures the tunnel client on the device to allow only designated applications to access content on internal servers.
- To add a new profile, click Add and then click Profile.
- Select Apple iOS.
- Select Device Profile.
- Select Imperative as Management Type.
- Select Device Context.
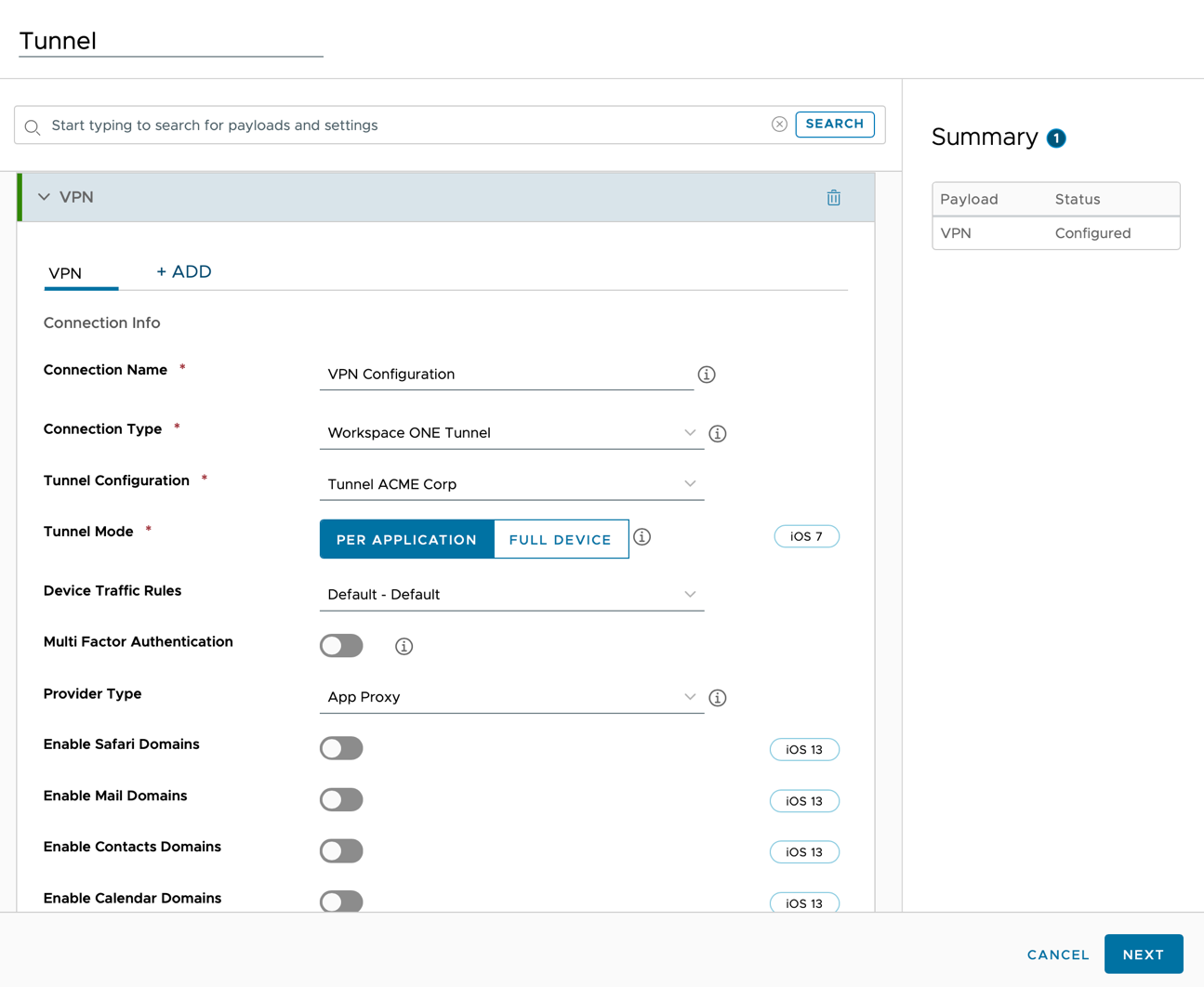
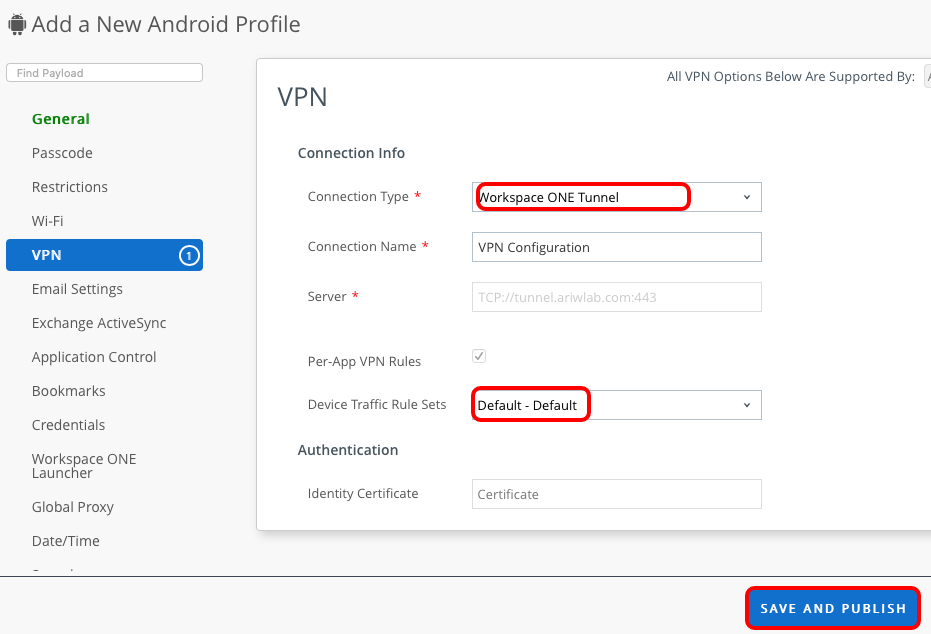
- Configure the VPN payload.

- Select Workspace ONE Tunnel from the Connection Type drop-down menu.
- Select the Tunnel Configuration.
- Select the Tunnel Mode, for this tutorial Per Application.
- Select the Device Traffic Rules that will be assigned to this profile.
- Add any Mail, Contacts, and Calendar Domains. Do not configure Safari Domains - these are configured in the Tunnel Configuration later in this guide.
- Click Next.
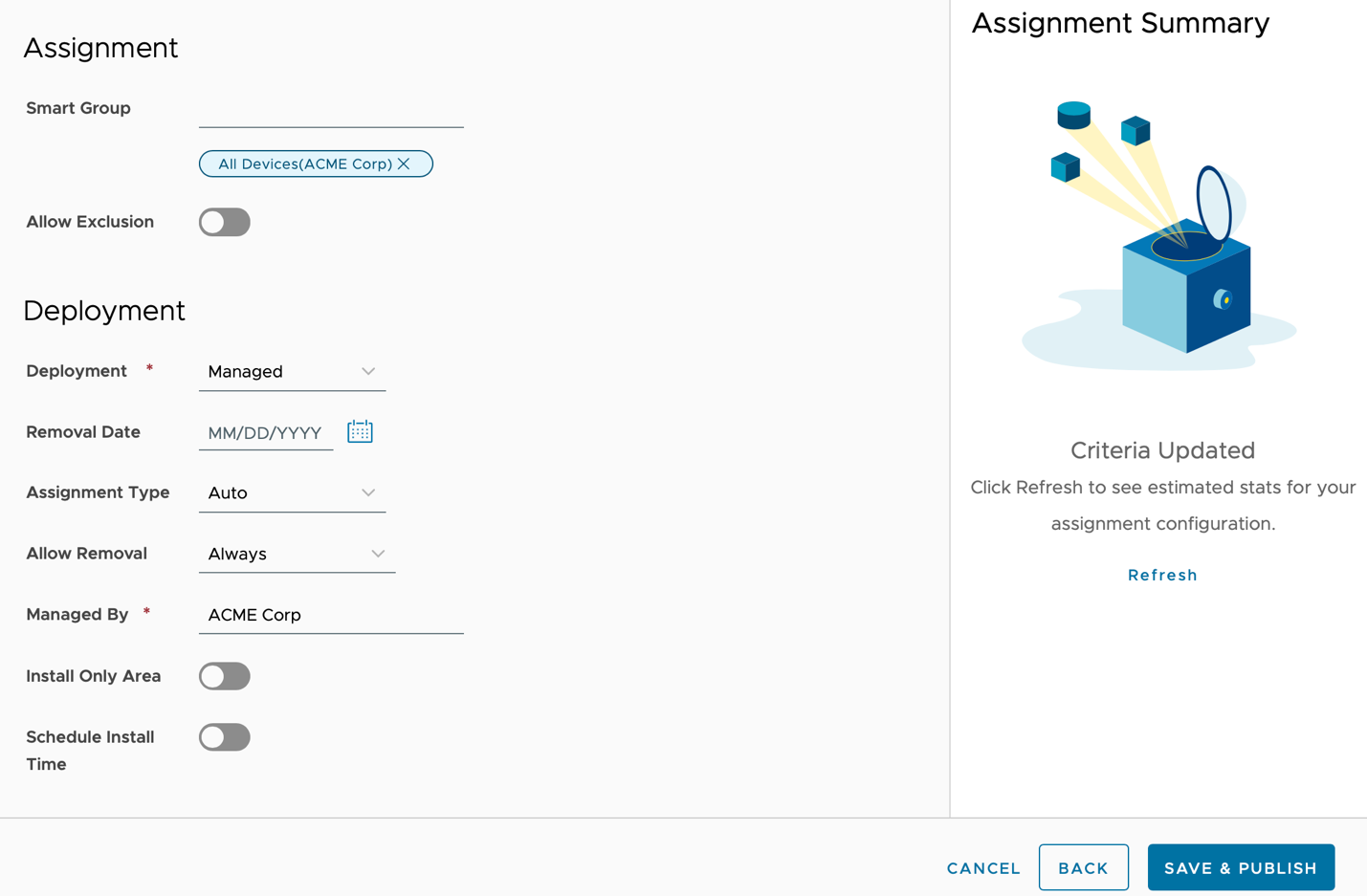
- Configure the Assigment.

- Enter the Smart Group, for this example All Devices.
- Set Assignment Type to Auto.
- Click Save & Publish.
Note: Safari Domains should be configured in the Device Traffic Rules for Workspace ONE Tunnel.
Configuring Workspace ONE Web for Per-App Tunnel
Workspace ONE Web is part of the secure productivity app suite from Workspace ONE UEM. Administrators can deploy Workspace ONE Web when data loss and copy/paste restrictions are critical to the business use case. In this exercise, you distribute and configure Workspace ONE Web for Per-App Tunnel on iOS.
This section demonstrates how to obtain Workspace ONE Web and assign it to devices as a Purchased App using the integration of Workspace ONE UEM and Apple Business Manager.
Workspace ONE Web is available for free on the App Store. To deploy as a Public App managed by Workspace ONE UEM, follow the same steps described in the previous chapter to deploy Workspace ONE Tunnel.
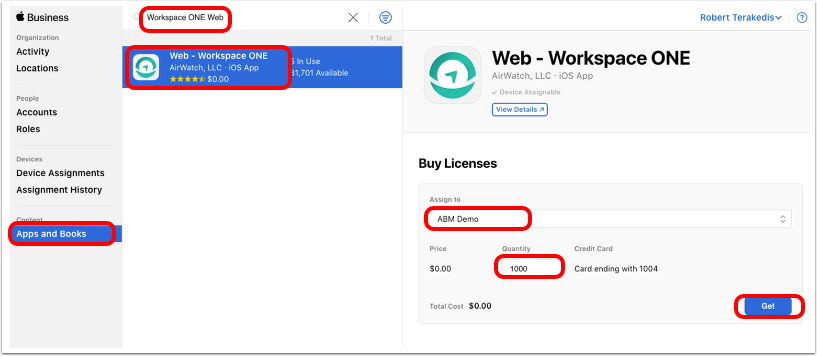
- Get Workspace ONE Web licenses. In Apple Business Manager (or Apple School Manager):

- Click Apps and Books.
- Search for Workspace ONE Web in the search text box.
- Select Web - Workspace ONE for iOS.
- Choose the location for which you have uploaded the
sTokeninto Workspace ONE UEM. - Enter the quantity of licenses you want to purchase.
- Click Get. The button changes to Purchasing and when the purchase is complete, it changes back to Get.
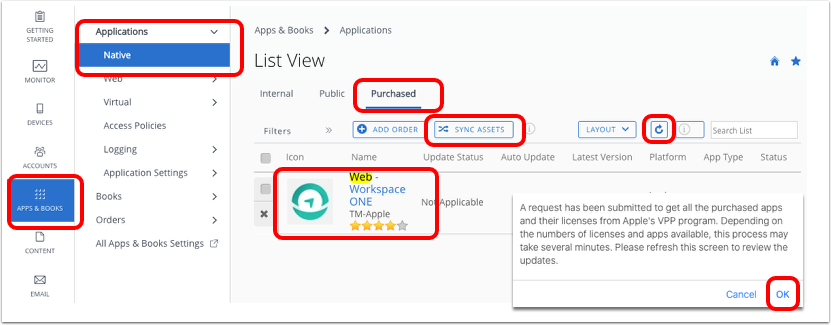
- Sync assets in Workspace ONE UEM.

- In the Workspace ONE UEM console, click Resources.
- Expand Applications and click Native.
- Click Purchased.
- Click Sync Assets.
- Click OK on the dialog box.
- Wait a few moments and click Refresh to update the app list.
- Click the Web - Workspace ONE app for iOS in the app list.
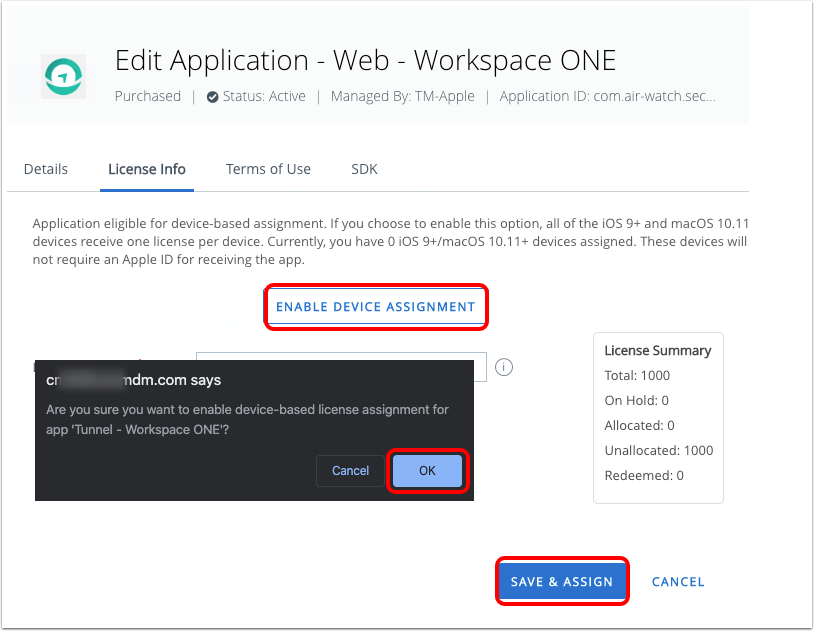
- Enable device assignment.

- Click Enable Device Assignment.
- Click OK to confirm device-based licensing.
- Click Save & Assign.
- Click Add Assignment.
- Edit assignment.

- Click Add Assignment.
- Select an Assignment Group (or create a new smart group containing the targeted devices).
- Enter the number of licenses to allocate. Allocate up to the total number of unallocated licenses.
- Select Auto for Assignment Type.
- Select Enabled for Remove on Unenroll.
- Select Enabled for Prevent Application Backup.
- Select Enabled for Make App MDM Managed if User Installed.
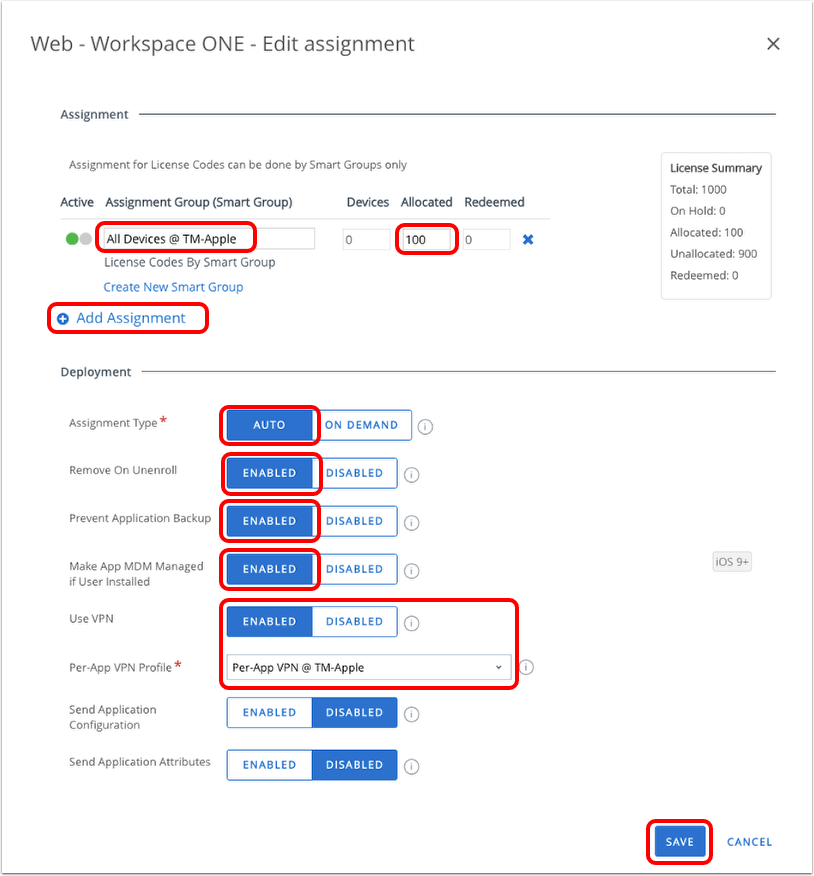
- Select Enabled and then select the Per-App VPN profile created in Creating Per-App VPN Profile for iOS.
- Click Save.
- Save assignment.
- If more assignments are necessary, click Add Assignment and repeat the steps in Edit Assignment.
- Click Save and Publish, then click Publish when all assignments have been added.
Testing Safari Domains with Per-App Tunnel
Now that the VPN profile includes a domain in the Safari Domains list, you can confirm that these settings have been updated on the device and test the settings in the native Safari application.
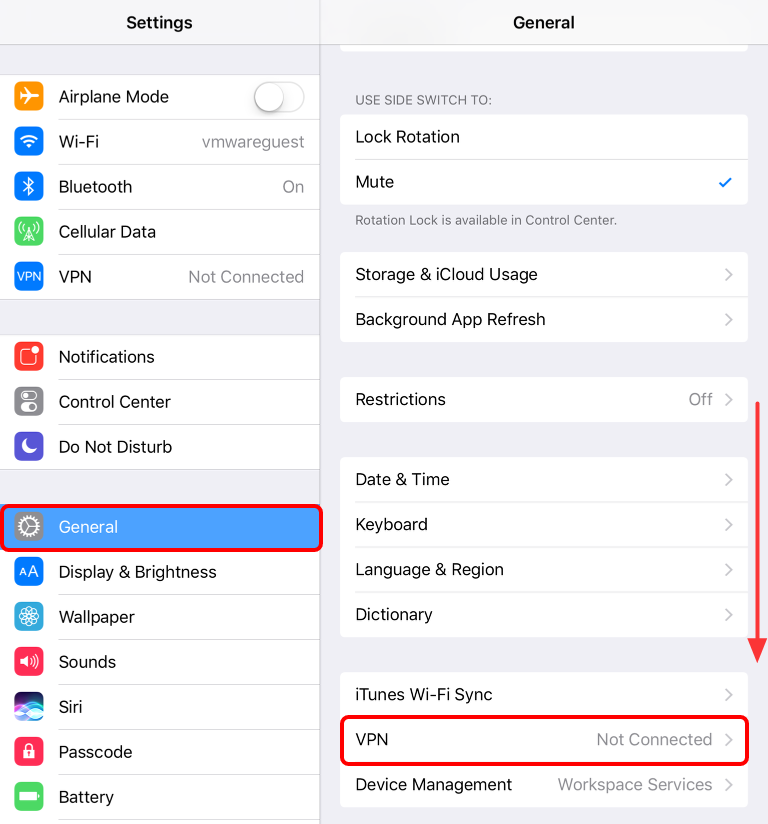
- Tap Settings.
- Open VPN settings.

- Tap General and scroll down to the VPN section.
- Tap VPN.
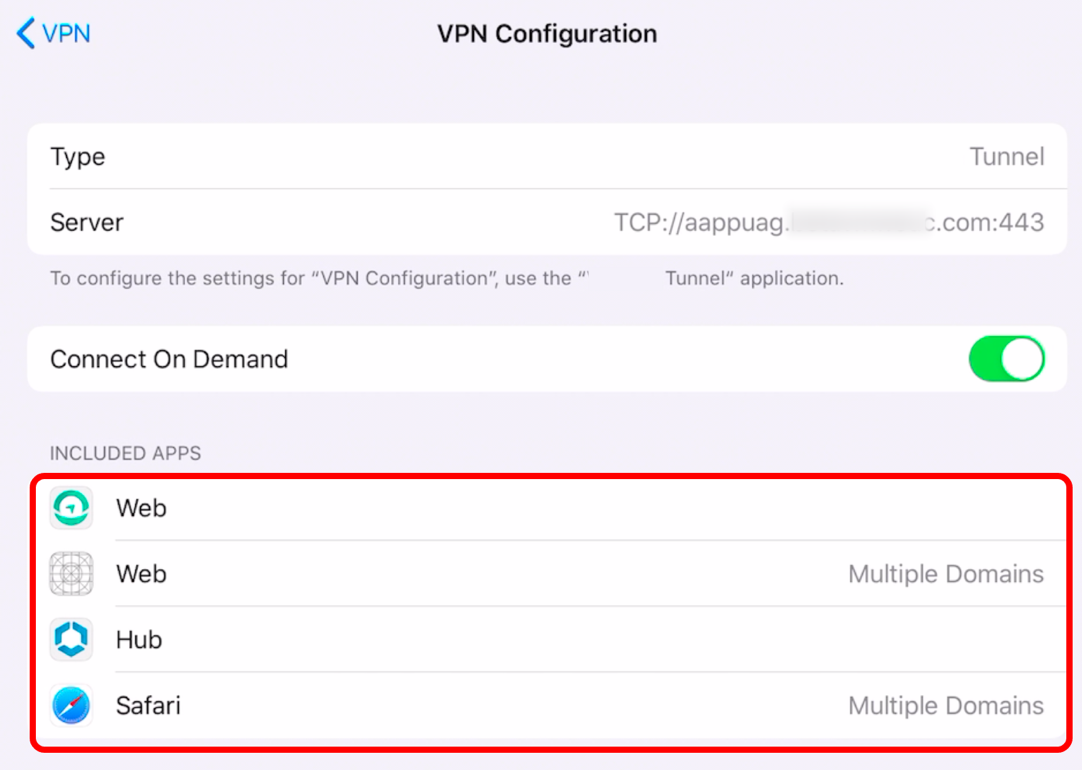
- Tap VPN Configuration from your Per-App VPN profile.
- Verify included Per-App VPN apps.

- All managed applications from the Workspace ONE UEM Console that are enabled to use Per-App VPN and have an associated Device Traffic Rule appear in this list. Note that Safari is displayed to show that domains are configured for tunneling in Safari.
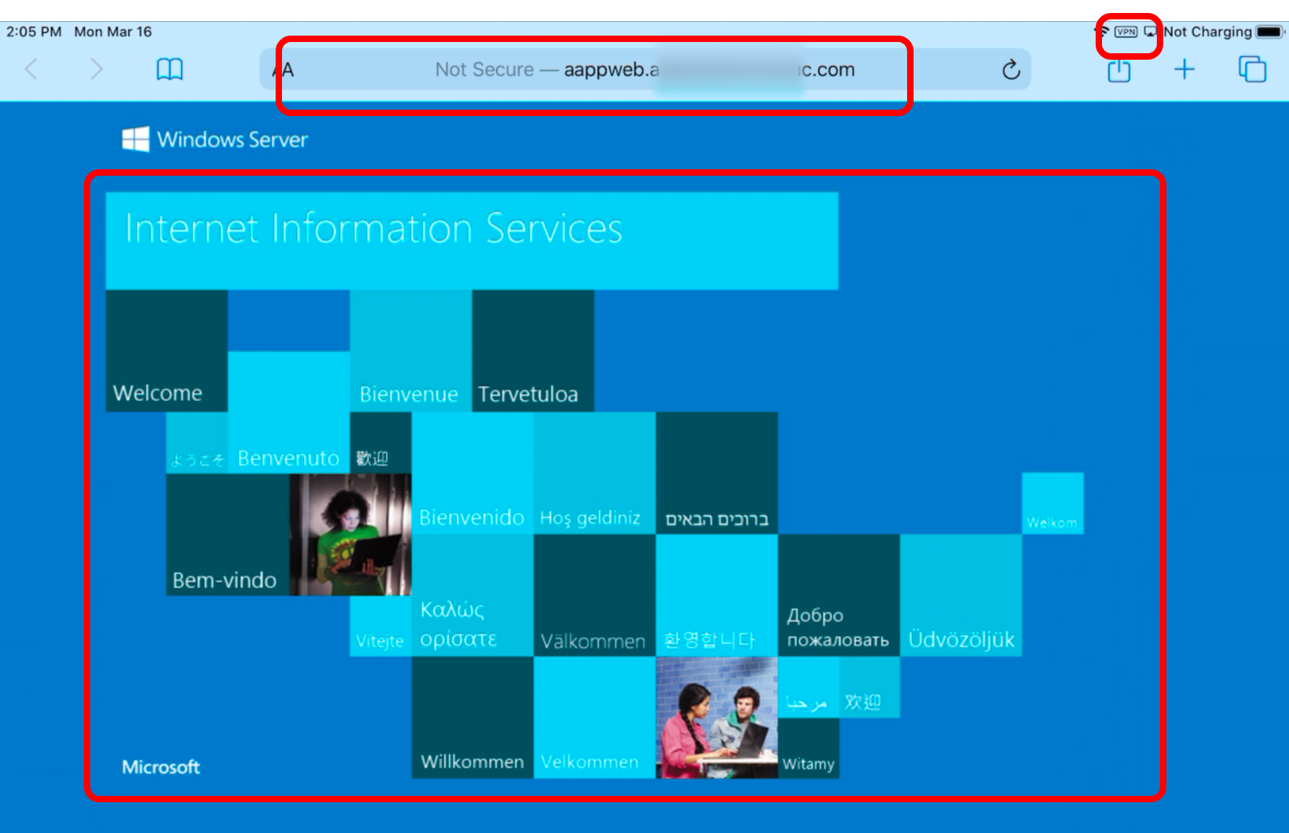
- Next, tap the Safari icon. The VPN icon should not be displayed in the toolbar.
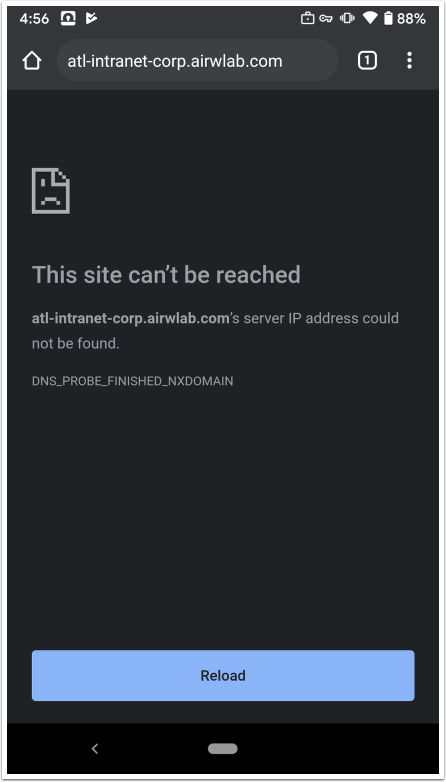
- Browse to the internal URL.

- Enter the URL for a website that is accessible only through VPN.
- Confirm that the VPN indicator is displayed when iOS launches the VPN and connects.
- Confirm that the internal page loads.
Testing Per-App Tunnel on iOS
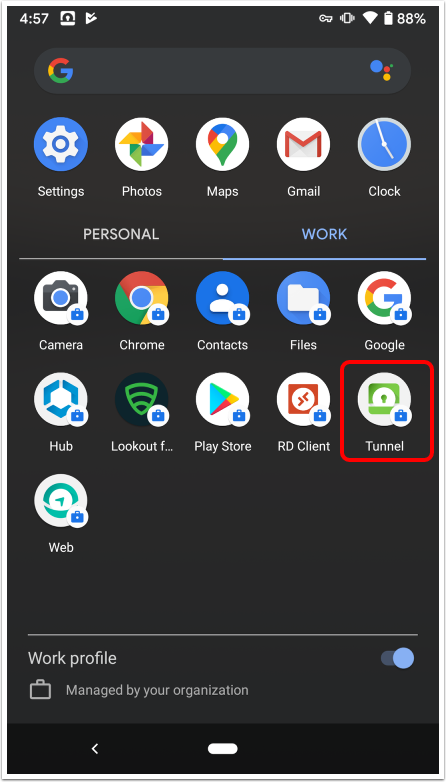
Now that the enrolled device has received the settings configured in the Workspace ONE UEM Console, you are ready to begin testing the Per-App Tunnel functionality. The applications assigned in the previous exercises should be pushed down during enrollment. The Tunnel and Workspace ONE Web applications should be installed on your device.
In this exercise, launch Workspace ONE Web and access the internal website. Then verify that, although the VPN connection is active, other applications on the device cannot access the tunnel or internal resources.
- Launch Workspace ONE Web.
- Press the Home button on your device to return to the Launchpad. Swipe right to see the downloaded applications, if needed.
- Tap the Workspace ONE Web icon to launch the application. If prompted, select OK to allow the Web to send your device push notifications.
- Create and confirm password.
- If prompted, create a passcode for Workspace ONE Web.
- Click Next.
- Confirm the passcode by entering it again.
- Click Confirm.
- Tap I understand to accept the Privacy prompt.
- Tap I agree to accept the Data sharing prompt.
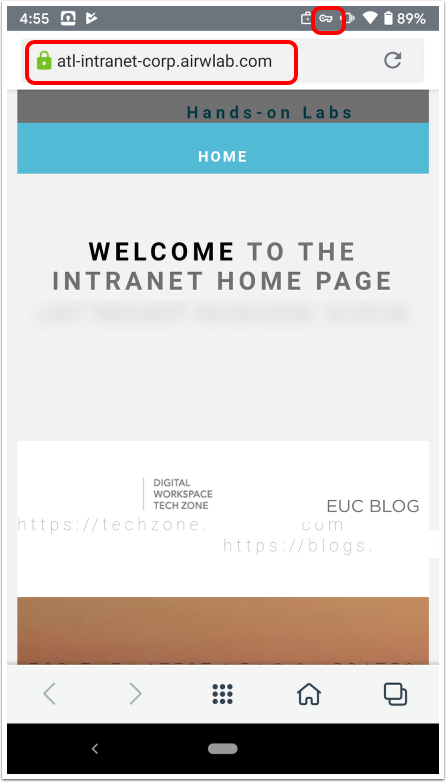
- Access the internal website with Workspace ONE Web.

- When the application launches, enter the URL for your intranet website.
- Confirm that the VPN icon appears, indicating the connection is active. The application now connects to Workspace ONE UEM and retrieves the settings for your Organization Group.
- Confirm that the website loads.
Note: Depending on the Workspace ONE Web and SDK settings configured at your particular organization group level, the address bar may not be editable. This configuration is called Kiosk Mode. To work around this, two options can be configured at Groups & Settings > Configurations > Workspace ONE Web:
- Click the Bookmarks tab, click Override (if necessary), click Add Bookmark, enter a name and URL for the testing URL, and click Save.
- Scroll the settings to Kiosk Mode and click Disabled. Click Save.
These changes affect the Default settings for Workspace ONE Web in this Organization Group and all inherited organization groups unless otherwise configured.
Troubleshooting the Workspace ONE Tunnel on iOS
This section contains some basic steps for troubleshooting Per-App Tunnel on iOS.
- On an enrolled iOS device, tap Tunnel.

- Tap Continue.
- Tap I understand to accept the Privacy prompt.
- Tap I agree to accept the Data sharing prompt.
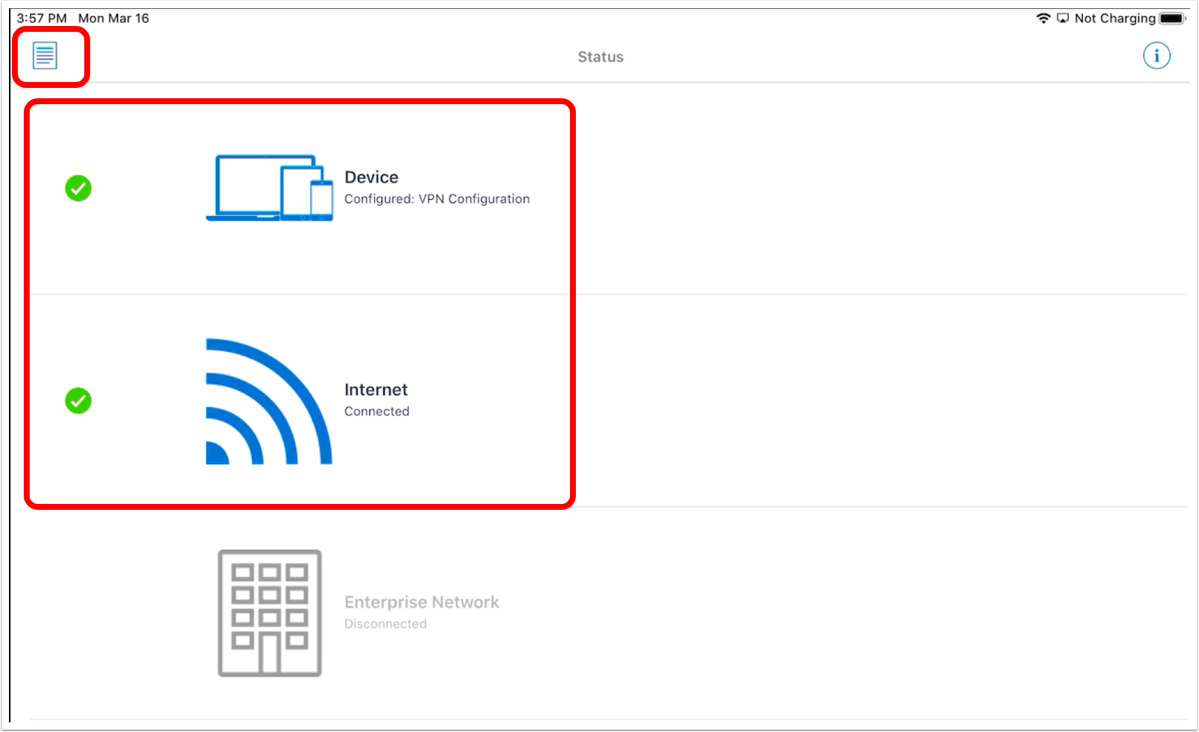
- Validate device connectivity.

- Ensure the device and Internet connectivity are OK (showing a green check mark symbol).
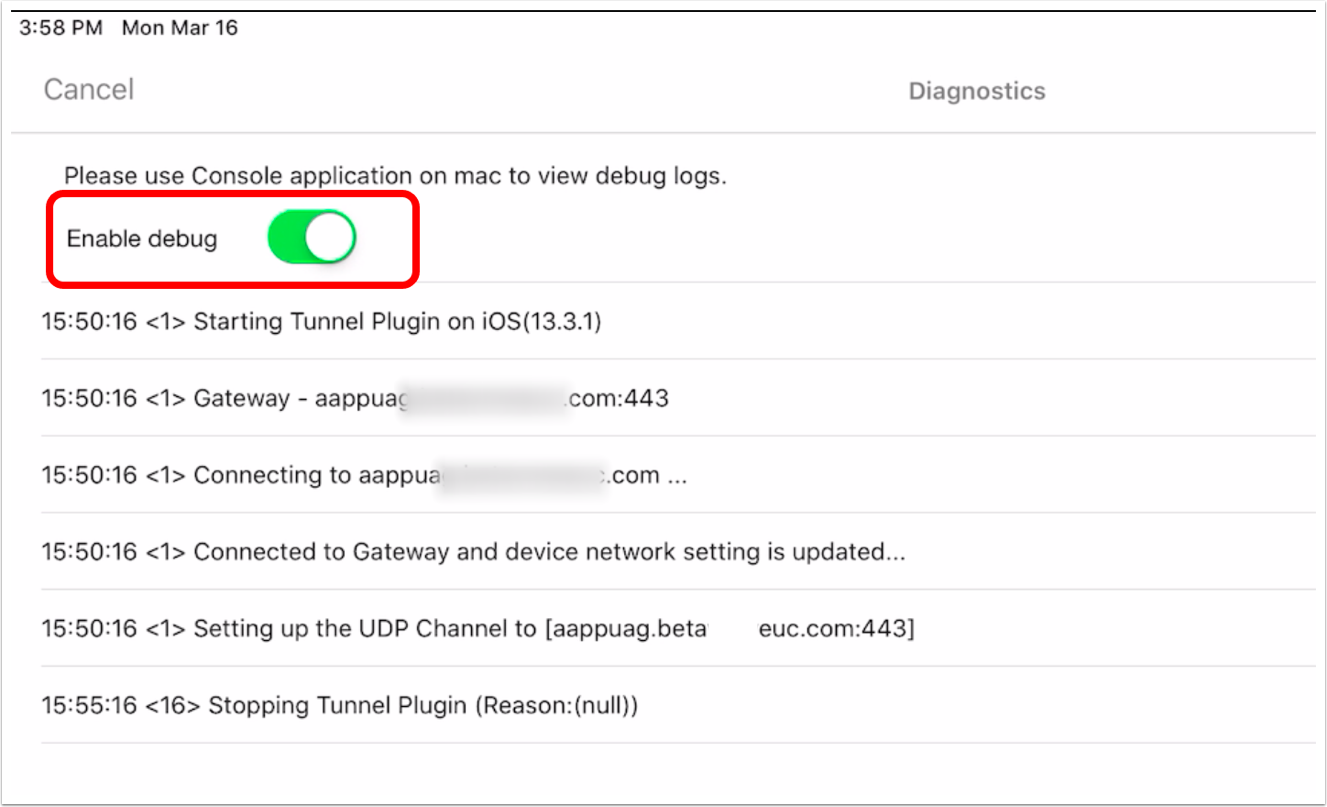
- Tap the logging icon.
- Activate the Enable debug toggle.

Tip: With Enable Debug turned on, Workspace ONE administrators can view logging information for the iOS device as follows:
- Plug the iOS device into a device running macOS.
- Ensure the iOS device trusts the connection to macOS.
- Connect to the Console, by either:
- Open Apple Configurator 2 and double-click the test iOS device. Click Console to view the output from the device.
- Open Console.app and select the iOS device from the left side.
- Search for tunnel or iOSAppProxyProvider.
Deploying Workspace ONE Tunnel for macOS
Per-App Tunneling helps users to access critical information using applications on their devices from their devices. Mobile flows help users perform business-critical tasks from a single app — streamlining the user experience.
Leveraging Per-App Tunnel allows you to control which applications are on a device and what internal resources the applications have access to by automatically activating or deactivating Per-App VPN access, based on which applications are active. By enabling remote access, you no longer need to provide a device-wide VPN on your devices, which can allow unintended or unauthorized apps or processes to access your VPN. In this tutorial, you configure and deploy Workspace ONE Tunnel to enable the Per-App Tunnel component on managed devices.
These exercises involve the following components:
- Workspace ONE Tunnel – The app used on the device to securely connect to the Unified Access Gateway to provide Per-App Tunnel functionality, also referred to as Tunnel Client.
- Unified Access Gateway – The virtual appliance where the Tunnel edge service is installed, and to which the tunnel client connects.
- Per-App Tunnel – Component of the Tunnel edge service for connecting to a secure tunnel channel on a per-application basis, which is controlled and configured by the VPN profile payload and Device Traffic Rules.
- Per-App VPN Profile and Device Traffic Rules – The Workspace ONE UEM configuration is pushed to the device that contains the Per-App Tunnel configurations. Every time a specified application is opened, the Workspace ONE Tunnel client evaluates the Device Traffic Rules assigned to it before making any routing decisions and establishes a Per-App tunnel connection with the Unified Access Gateway based on the Per-App VPN Profile configuration.
High-Level Architecture
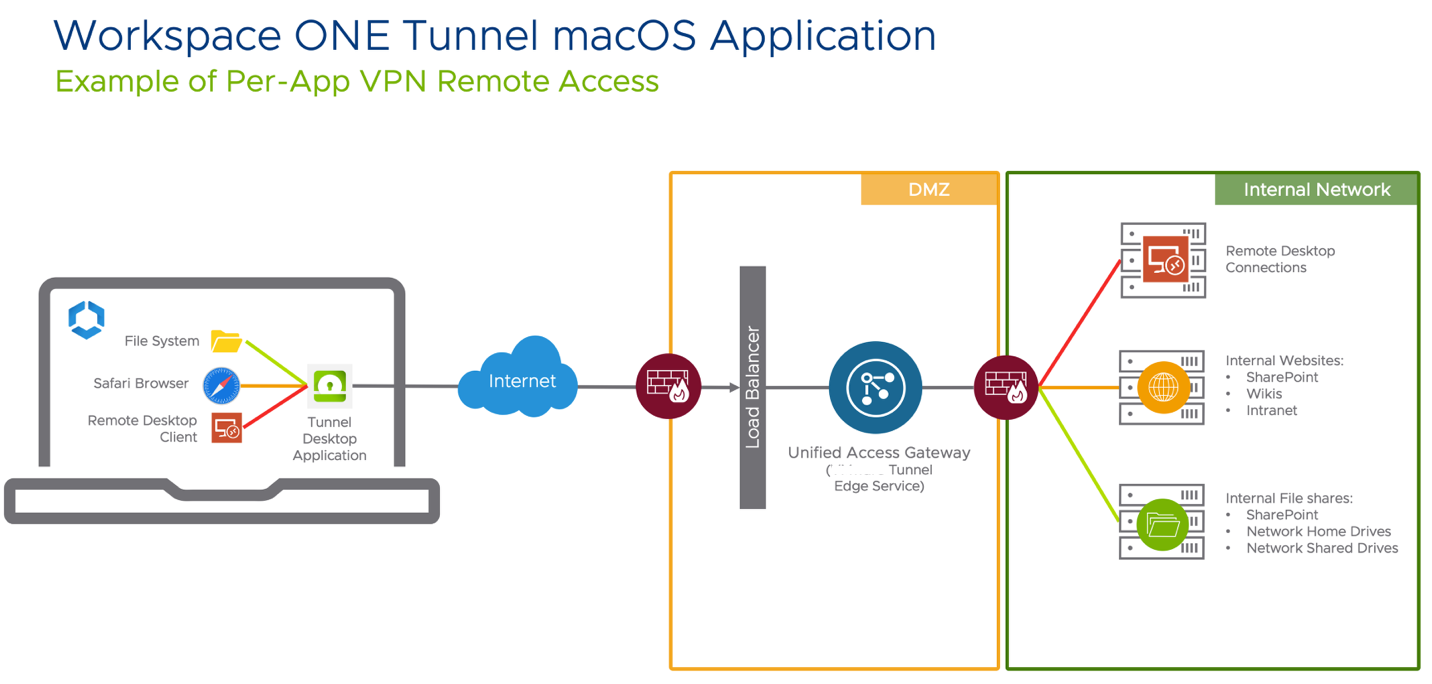
The device contains the applications required by the end-user to perform their daily job. Some applications require access to internal resources to function. Those applications, based on Per-App VPN configuration, use Workspace ONE Tunnel which communicates with the Tunnel Service on Unified Access Gateway hosted on the DMZ, to validate if the device requesting access is in compliance or not before authorizing access through the internal resource.
Prerequisites
Before you can perform the steps in this exercise, you must have the following components installed and configured:
- Workspace ONE UEM version 2302 and later.
- macOS Mojave and later enrolled in Workspace ONE UEM.
- The latest version of macOS Tunnel from the Apple macOS App Store.
- Deploy Workspace ONE Tunnel using volume-purchased licenses from Apple Business Manager or Apple School Manager.
- Workspace ONE Administrators must upload the Location token from Apple Business Manager to sync licenses to Workspace ONE UEM for managed distribution.
Configuring Device Traffic Rules for macOS
First, because the Apple Mail, Calendar, and Contacts applications might contain both corporate and personal data, administrators must take an extra step to define corporate-owned domains, which should be marked for Per-App VPN. The Mail, Calendar, and Contacts apps do not automatically adhere to device traffic rules. Administrators must specify which domains are corporate-owned by enabling the Mail, Contacts, and Calendar domain parameters in the VPN profile payload. Enabling these parameters in the VPN payload allows Tunnel Edge service to apply the appropriate device traffic rules for those specific domains.
Second, Safari is another app that might be used for personal use on a corporate device. As such, Safari cannot be configured to tunnel all traffic. Device traffic rules for Safari must specify the domain and top-level domain component (for example, mycompany.com), although an asterisk (*) may be used to wildcard subdomains (for example, *.mycompany.com).
Note: Domain values used in this section are examples only. Your values will differ.
- Access configurations.
- In the Workspace ONE UEM console, click Groups & Settings.
- Click Configurations.
- Scroll through the list of configurations and select Tunnel.

- Edit Device Traffic Rule sets.
- From within the Device Traffic Rules information block on the Tunnel Configuration page, click Edit.
- Add or modify device traffic rule set.

Introduced in Workspace ONE UEM 2011, Device Traffic Rule Sets expand the functionality of device traffic rules allowing for granular assignment of rule sets to different groups of users and devices. Device Traffic Rule Sets are assigned when creating the per-app VPN profile in a later step.
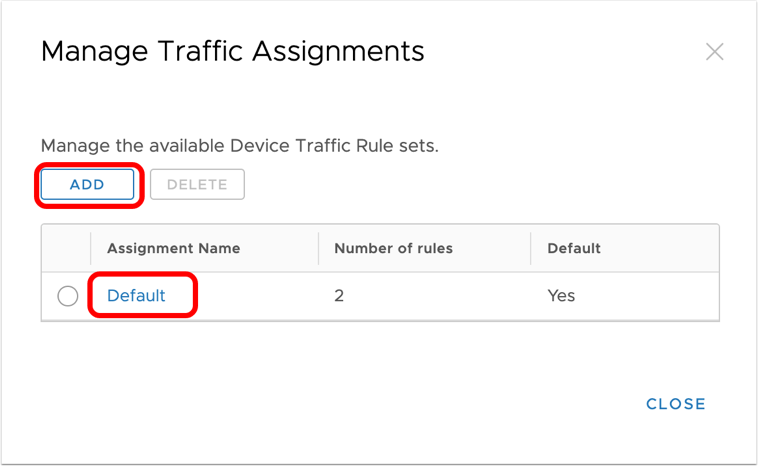
To get started with Device Traffic Rule Sets, perform the following in the Manage Traffic Assignments screen:- If no other Device Traffic Rule Sets exist (or a new rule set is required), click Add to create a new Device Traffic Rule Set.
- If modifications to an existing rule set are required, click the Device Traffic Rule Set name.
- Enter a name for the Device Traffic Rule Set (or if necessary, modify the name of an existing rule set).
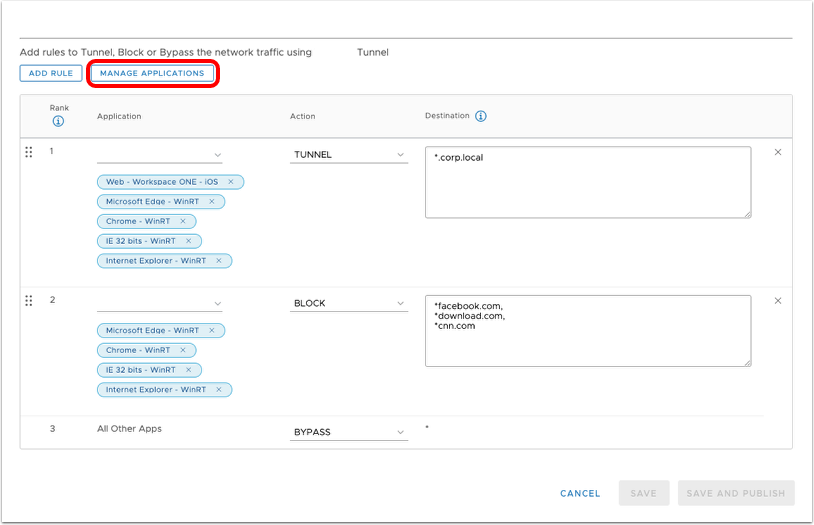
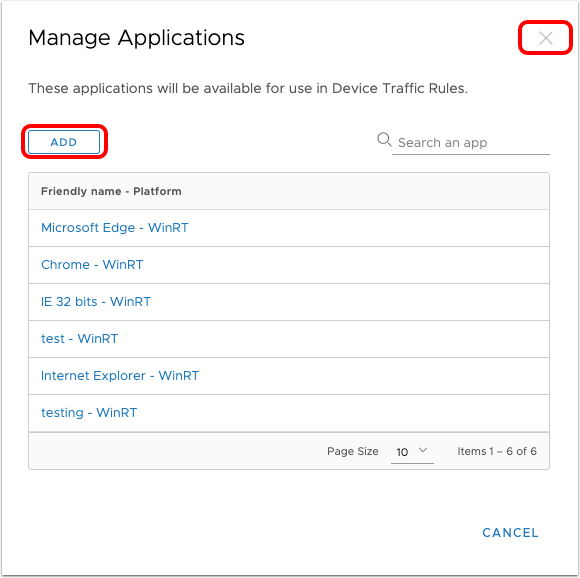
- Click Manage Applications.

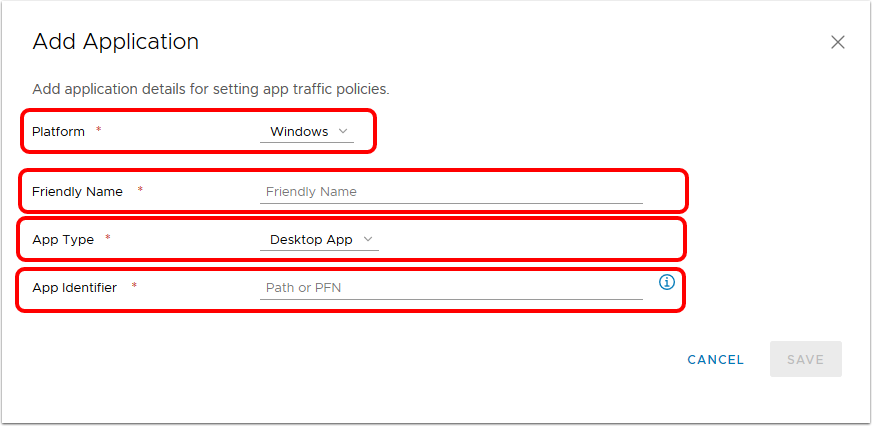
- Click Add to add a new application for device traffic rules.
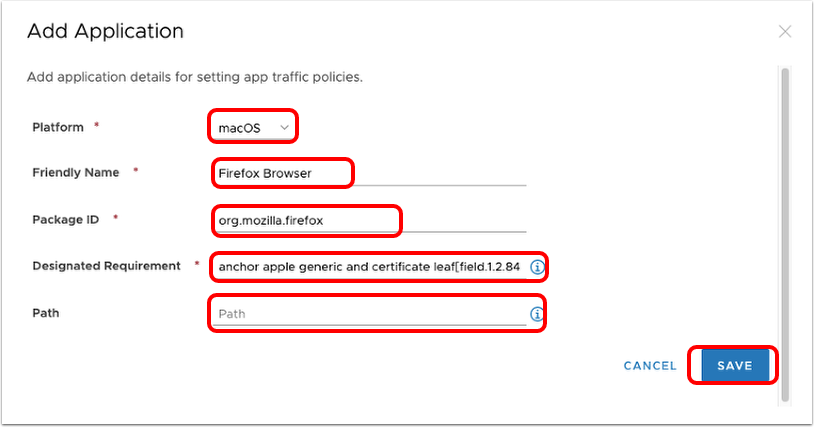
- Define the application.

- Select macOS for Platform.
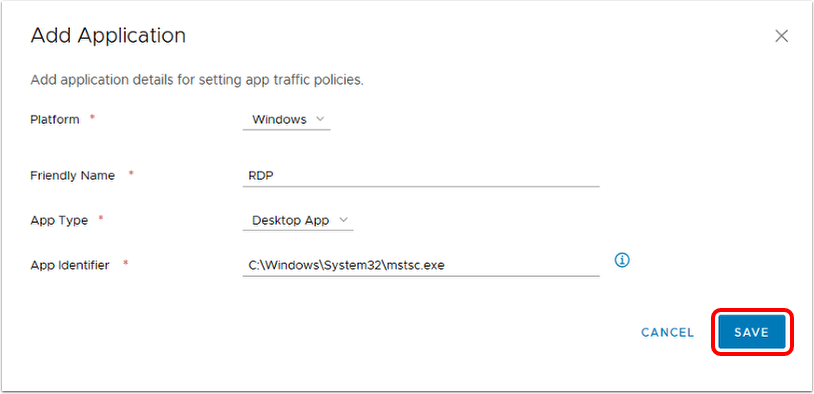
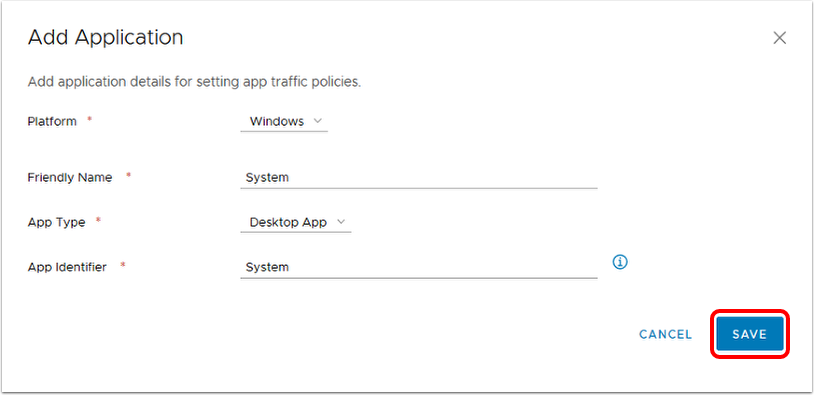
- Enter the friendly name of the application, for example,
Firefox Browser. The friendly name is displayed in the Device Traffic Rule. - Enter the application's package id, which is the Identifier value displayed by running the command:
codesign -dv --entitlements - /path/to.app - Enter the application's designated requirement, which is displayed to the right of the => sign of the following command:
codesign -d -r- /path/to.app - For macOS 10.15 (Catalina) and later, enter a path if creating a device traffic rule for a binary or command-line utility bundled within an application. For example, the executable
omnissa-remotemksmust be allowlisted with path details along with the Horizon Client application. - Click Save.
Using Firefox as an example, a Workspace ONE administrator would see the commands and values as follows:
techzone@testmac ~ % codesign -dv --entitlements - /Applications/Firefox.app
Executable=/Applications/Firefox.app/Contents/MacOS/firefox
Identifier=org.mozilla.firefox
Format=app bundle with Mach-O thin (x86_64)
CodeDirectory v=20500 size=415 flags=0x10000(runtime) hashes=4+5 location=embedded
Signature size=9018
Timestamp=Oct 1, 2019 at 9:08:41 PM
Info.plist entries=26
TeamIdentifier=43AQ936H96
Runtime Version=10.11.0
<<< trimmed for length >>>
techzone@testmac ~ % codesign -d -r- /Applications/Firefox.app
Executable=/Applications/Firefox.app/Contents/MacOS/firefox
designated => anchor apple generic and certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "43AQ936H96"
As highlighted in the terminal output, the necessary information is as follows:
Package ID: org.mozilla.firefox
Designated Requirement: anchor apple generic and certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "43AQ936H96"
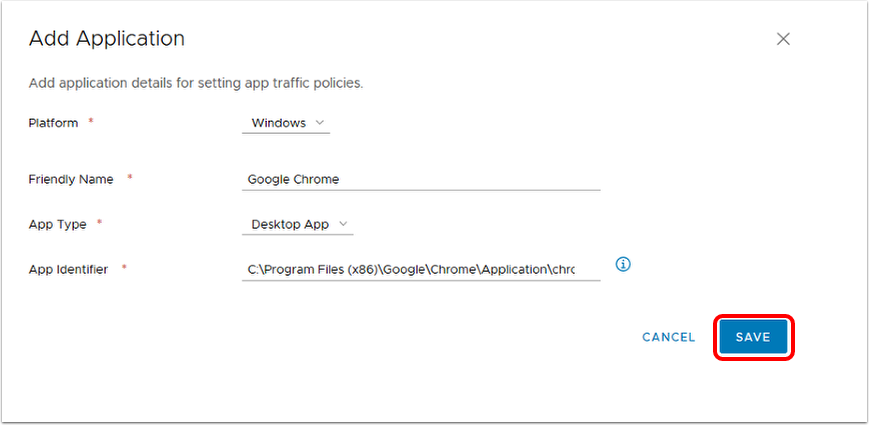
Caution: Some apps spawn helper applications to assist with background tasks. One example of this is Google Chrome, which performs network functions outside the Google Chrome.app process in a Google Chrome Helper process. In this case, the helper application must be added to the Device Traffic Rule, otherwise, specific settings must be changed client-side.
In the case of Google Chrome, perform the following:
- In the URL field, type chrome://flags
- Search for network in the Search Flags text box.
- Set Runs network service in-process to Enabled and relaunch Google Chrome before proceeding with testing.
- Add a new application for device traffic rules.

- If more applications are needed for the rule set, click Add and repeat starting at Define the Application.
- If all the required applications have been defined, click the [X] to close the Manage Applications window.
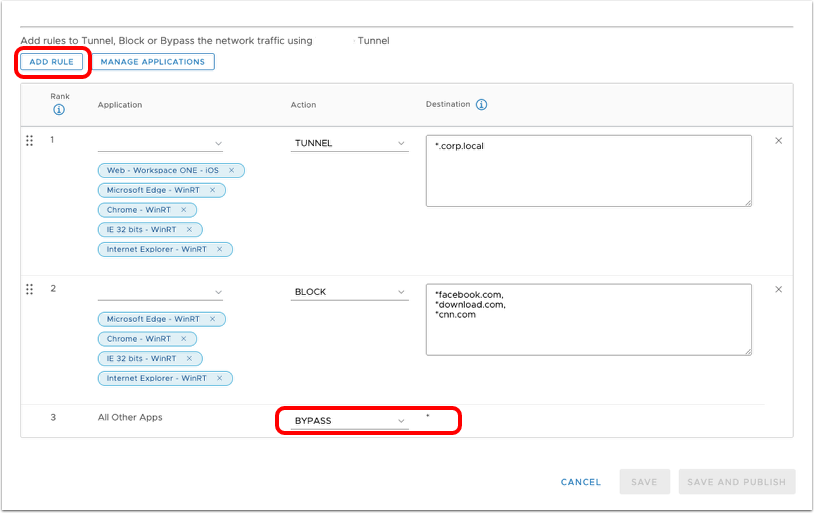
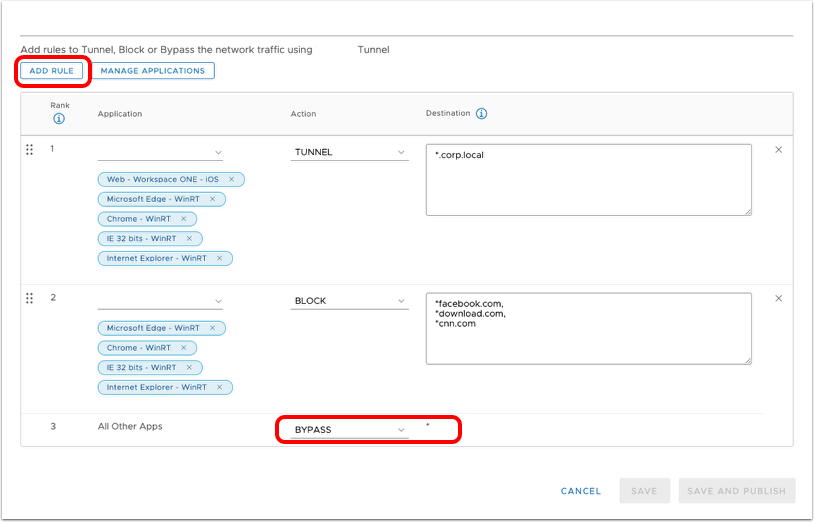
- Add device traffic rule.

- Observe (and optionally modify) the default action which applies to all macOS applications except Safari:
- Tunnel – All apps, except Safari, on the device configured for Per-App Tunnel send network traffic through the tunnel. For example, set the Default Action to Tunnel to ensure all configured apps without a defined traffic rule use the Workspace ONE Tunnel for internal communications.
- Block – Blocks all apps except Safari, on the device configured for Per-App Tunnel from sending network traffic. For example, set the Default Action to Block to ensure that all configured apps without a defined traffic rule cannot send any network traffic regardless of destination.
- Bypass – All apps, except Safari, on the device configured for Per-App Tunnel, bypass the tunnel and connect to the Internet directly. For example, set the Default Action to Bypass to ensure all configured apps without a defined traffic rule bypass the Workspace ONE Tunnel to access their destination directly.
- Proxy - Redirect traffic to the specified HTTPS proxy for the listed domains. The proxy must be HTTPS and must follow the correct format: https://example.com:port
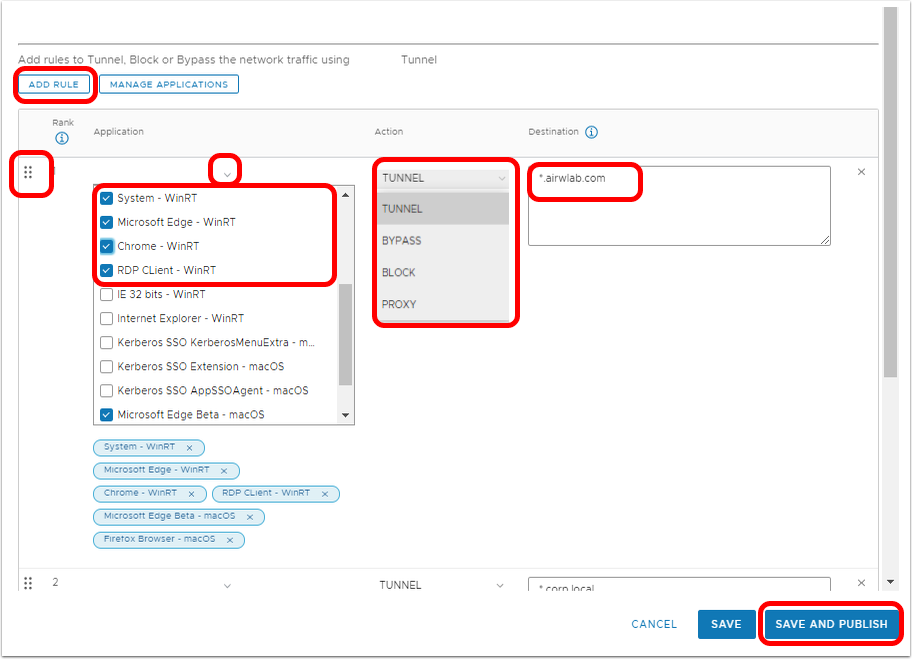
- Click Add Rule.
- Observe (and optionally modify) the default action which applies to all macOS applications except Safari:
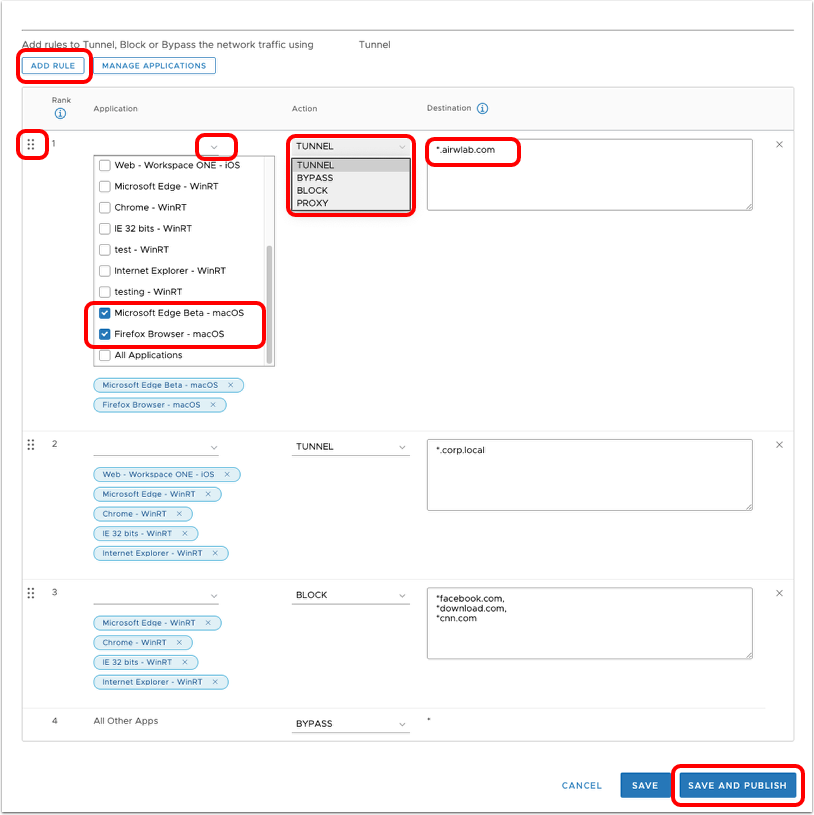
- Build device traffic rule.

- In the newly created device traffic rule, click the down arrow to display the Application list.
- Select one or more triggering applications to control with this rule. In case you select All Applications, the rule will be applied only to Safari and macOS applications selected in additional rules defined as part of the Device Traffic Rules.
- Enter one or more comma-separated fully qualified domain names as destinations to which Workspace ONE Tunnel should apply the Device Traffic Rule. A single asterisk (*) can be used as a wildcard for subdomains.
- Select the Appropriate Action for Workspace ONE Tunnel to perform on traffic from the selected apps:
- Tunnel – Sends app network traffic for specified domains through the tunnel to your internal network.
- Block – Blocks all traffic sent to specified domains.
- Bypass – Bypasses the Workspace ONE Tunnel so the application accesses specified domains directly.
- Proxy – Redirect traffic to the specified HTTPS proxy for the listed domains. The proxy must be HTTPS and must follow the correct format:
https://example.com:port.
- If necessary, adjust the Device Traffic Rules rank in the list. Lower-numbered rank is the highest priority.
- If necessary, click Add Rule and repeat the steps in Build Device Traffic Rule until you have added all the necessary Device Traffic Rules for your organization.
- Click Save and Publish to send the updated DTRs to all devices to which the DTR is assigned.
For more information on the formats (wildcards, IP, ports) allowed into the Destination field, see the Device Traffic Rules Guidelines and use of asterisk chapter.
Distributing Workspace ONE Tunnel for macOS
Workspace ONE Tunnel is a macOS application available for free on the Mac App Store. It is also available for managed distribution volume licensing through Apple Business Manager and Apple School Manager. Use device-based licensing to distribute Workspace ONE Tunnel to managed macOS devices. This section demonstrates how to purchase Workspace ONE Tunnel and assign it to devices.
Note: The VPN tunnel should already be configured as part of the Prerequisites.
- Get Workspace ONE Tunnel licenses.

- In Apple Business Manager (or Apple School Manager), click Apps and Books.
- Search for workspace tunnel in the search text box.
- Select Tunnel - Workspace ONE for macOS.
- Choose the location for which you have uploaded the
sTokeninto Workspace ONE UEM. - Enter the quantity of licenses you want to purchase.
- Click Get. The button changes to Purchasing and when the purchase is complete changes back to Get.
- Sync assets in Workspace ONE UEM.

- In the Workspace ONE UEM console, click Resources.
- Expand Applications and click Native.
- Click Purchased.
- Click Sync Assets.
- Click OK on the dialog box.
- Wait a few moments and click Refresh to update the app list.
- Click the Workspace ONE Tunnel app in the app list.
- Enable device assignment.

- Click Enable Device Assignment and click OK for the
Are you sure?prompt. - Click Save & Assign.
- Click Enable Device Assignment and click OK for the
- Click Add Assignment.
- Edit assignment.

- Enter a name for the Distribution
- Select an Assignment Group (or create a new smart group containing the targeted devices).
- Enter the number of licenses to allocate. Allocate up to the total number of unallocated licenses.
- Select Auto for Assignment Type.
- Click Create.
- Save assignment.
- If more assignments are necessary, click Add Assignment and repeat the steps in Edit Assignment.
- Click Save and then Publish when all assignments have been added.
Creating Per-App VPN Profile for macOS
Before device traffic rules take effect on macOS, Workspace ONE administrators must deploy a VPN profile payload that configures macOS to leverage Workspace ONE Tunnel. In this exercise, you create the macOS profile which configures the tunnel client on the device to allow only designated applications to access content on internal servers.
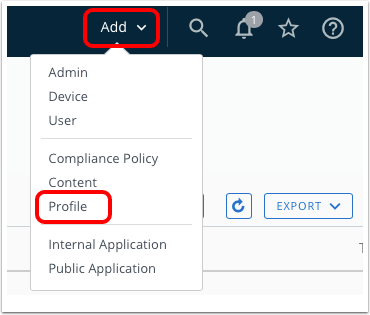
- To add a new profile, click Add and then click Profile.

- Select macOS.
- Select User Profile.
- Configure General profile settings.

- Enter a name for the profile, for example,
Per-App VPN. - Select Auto as the assignment type.
- Select one or more Smart Groups to assign the VPN profile (or create a new smart group).
- Click the VPN payload then click Configure.
- Enter a name for the profile, for example,
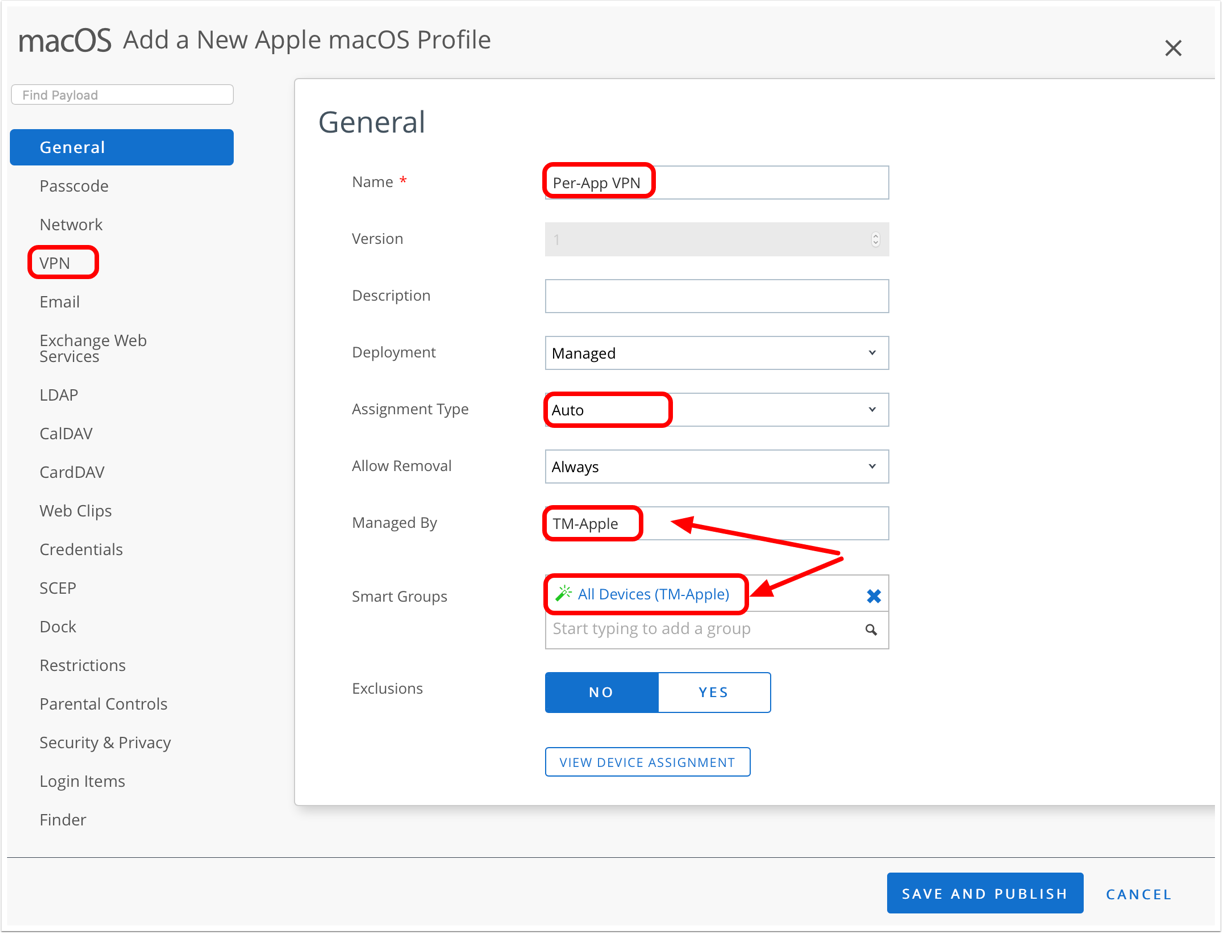
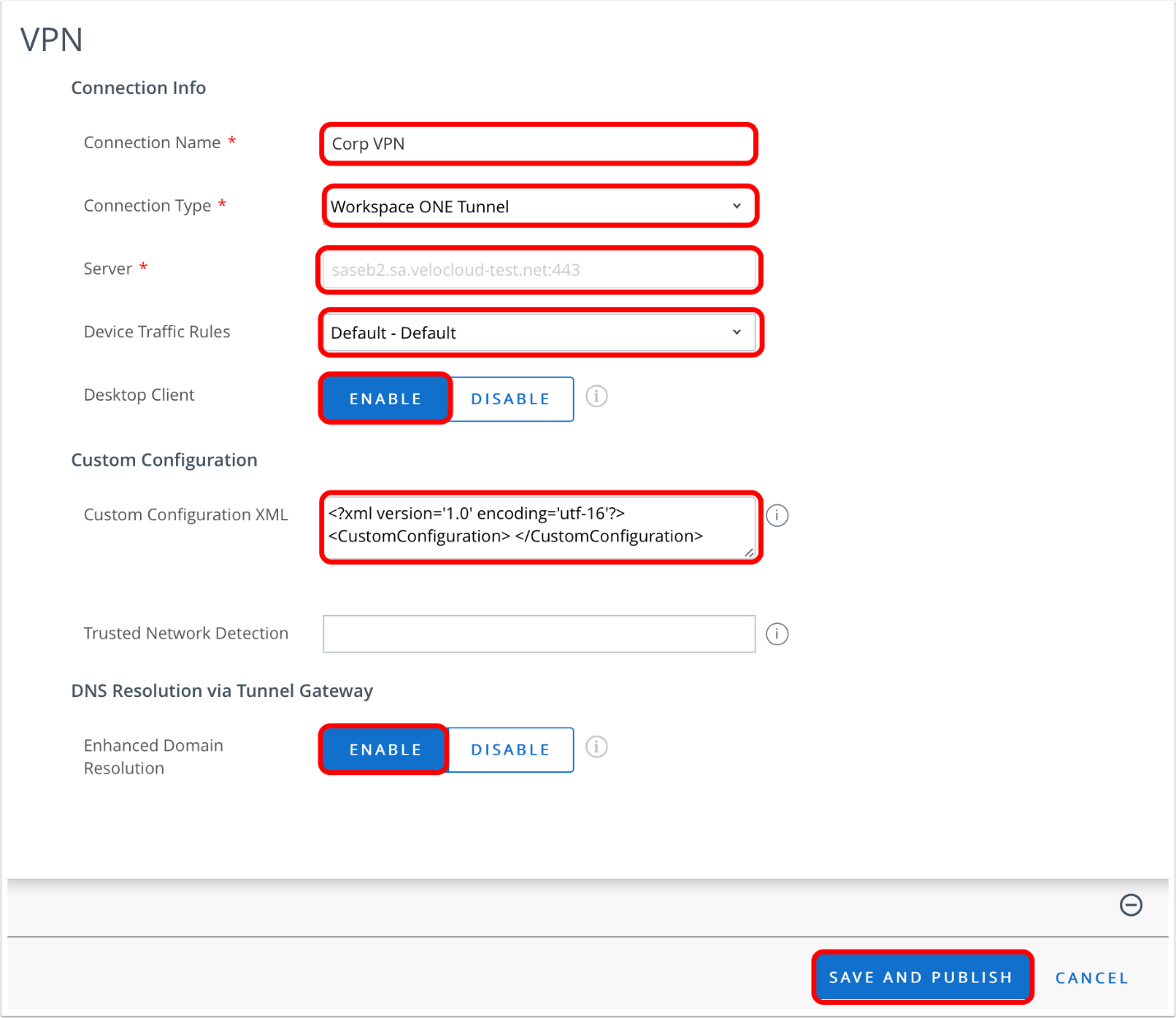
- Configure VPN payload.

- Enter a name for the Per-App VPN Connection, for example,
Corporate Per-App VPN. - Select Workspace ONE Tunnel as the Connection Type.
- Choose the Device Traffic Rule Set (as configured in Configuring Device Traffic Rules for macOS) to be assigned via this Profile Payload.
- If required, select the check boxes for Enable Mail Domains, Enable Contacts Domains, and Enable Calendar Domains.
- For each check box, enter a domain that should be tunneled.
- If multiple domains are required, click Add to enter an additional domain. Repeat as necessary.
- Click Save and Publish.
- Enter a name for the Per-App VPN Connection, for example,
- Click Publish.
Testing Per-App Tunnel on macOS
With the settings configured in the Workspace ONE UEM Console, administrators can test the Per-App Tunnel functionality on an enrolled device. The Workspace ONE Tunnel assigned in the previous exercises should install automatically during enrollment. As part of testing, the applications defined in the Device Traffic Rules should be deployed as described in Deploying a Third-Party macOS App: Workspace ONE UEM Operational Tutorial.
As a reminder, the prerequisites for testing Per-App Tunnel on macOS include the following:
- Tunnel Edge Service configured on Unified Access Gateway
- Device Traffic Rules configured in Workspace ONE UEM
- Workspace ONE Tunnel and additional apps defined in Define Traffic Rules deployed to an enrolled device running macOS
- A valid endpoint that is not accessible to the apps on the device except via per-app Tunnel
Validate Per-App Tunnel based on Device Rules
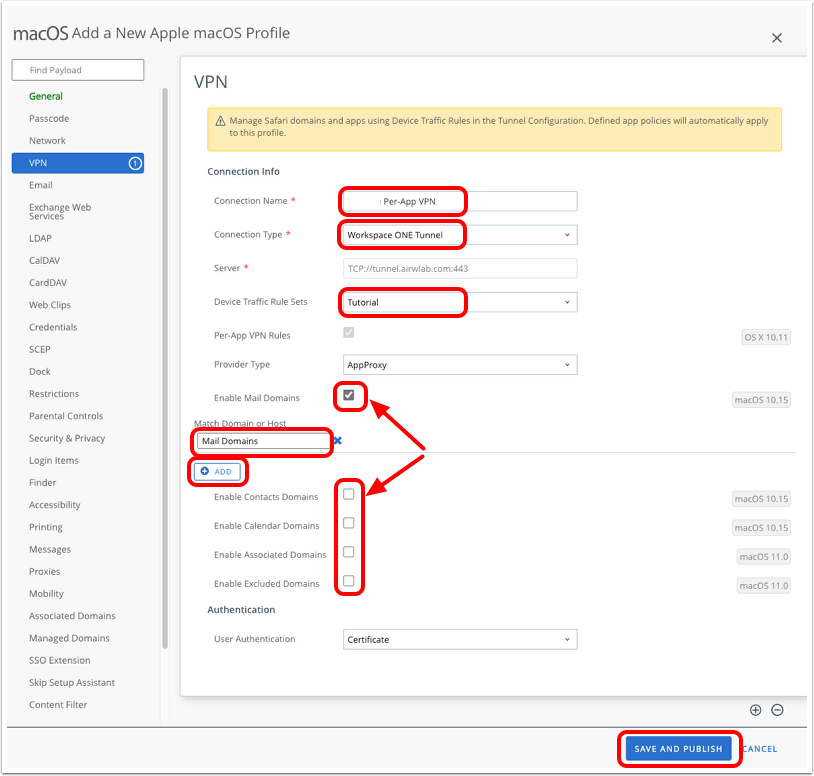
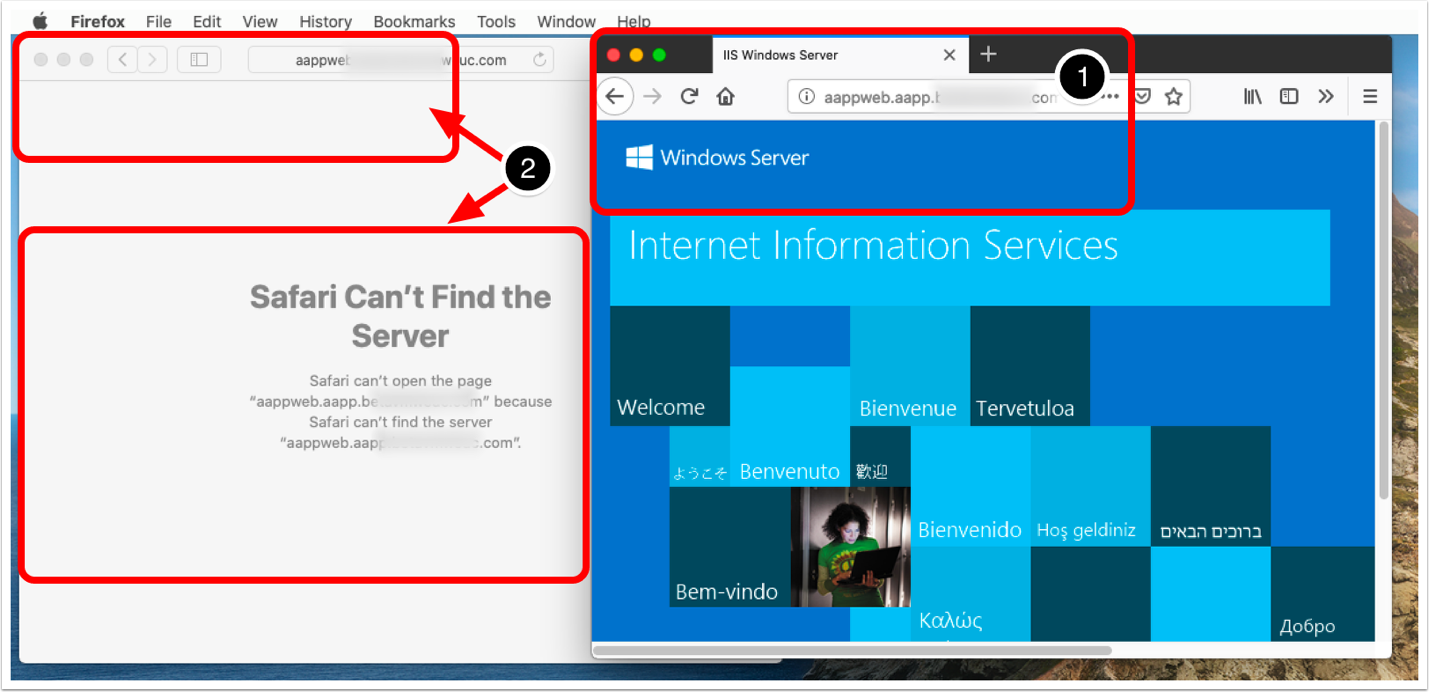
- Open an app specified in a Device Traffic Rule and ensure the application attempts to connect to the mapped domain name(s).
- Open an app that is not specified in a Device Traffic Rule, such as Safari (which will not adhere to the default Device Traffic Rule due to the wildcard mapping). Ensure the same mapped domain name does not work.

In the section of this tutorial where device traffic rules were created for macOS, Firefox was the allowed application. In the screenshot, note that Firefox is launched and attempted connection to an approved (wildcard) destination (#1). Also, observe that Safari (which was not granted access to the tunnel) cannot connect to the endpoint.
Extending Tunnel Configuration for Kerberos SSO Extension in macOS
With macOS Catalina, Apple introduced a new single sign-on (SSO) extension framework and included a built-in Kerberos SSO extension. The Kerberos SSO extension syncs passwords between a user's account in Active Directory and the local macOS account. It also brings Kerberos SSO functionality directly into the OS via MDM-manageable payloads. This tutorial aims to help experienced Workspace ONE administrators to configure the Kerberos SSO extension for macOS Catalina and enable off-network access for the extension through per-app tunneling.
IMPORTANT: This document is provided as a courtesy to aid anyone wishing to test the functionality. This document was created around the time macOS Catalina was released. Kerberos Ticketing worked as expected at that time, but the Kerberos SSO Extension had a known bug that prevented AD password sync and change over per-app tunnel. Since then, the Kerberos SSO Extension has continued to work for network-connected devices.
However, Kerberos SSO over per-app tunneling has been in varying states of functioning depending on major, minor, and development builds of the OS. We encourage customers interested in this functionality to test and file feedback with Apple (using Apple's Feedback Assistant) and also with us.
| Software Prerequisites | Configuration Prerequisites |
| Before using this section of the tutorial, Workspace ONE administrators must ensure the following software version prerequisites are met:
Optionally, if configuring the SSO Extension to use Per-App Tunnel, administrators should meet these additional prerequisites:
| Before using this section of the tutorial, Workspace ONE administrators must complete the following types of configurations within their environment:
|
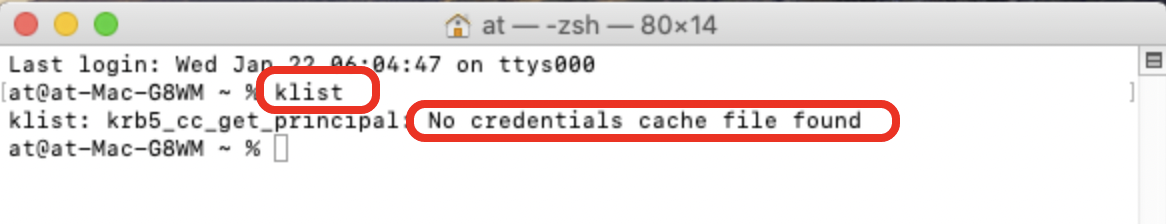
Validate No Pre-existing Kerberos Tickets
- Press CMD+SpaceBar (⌘+Space) and enter
terminalinto the Finder window. - Select Terminal to open
Terminal.app. - Enter
klistand press Return on the keyboard. - Ensure that there are no Kerberos Tickets and the command returns No credentials cache file found.

Validate Kerberos Application or Website Fails
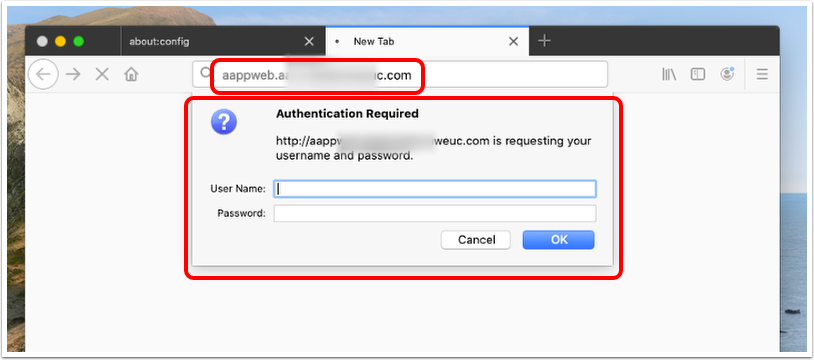
- Launch an application that should be Kerberos-enabled. If using a website, browse to the Kerberos-enabled website.

- Note that authentication either fails (as there are no Kerberos tickets) or reverts to a non-Kerberos authentication type (such as certificate authentication or username/password).
Define the Kerberos Extension in Device Traffic Rules
To connect the SSO Kerberos Extension over Per-App Tunnel, you must add the appropriate device traffic rules to the Tunnel configuration to support this. This section covers how to add the appropriate device traffic rules.
- Access configurations.
- In the Workspace ONE UEM console, click Groups and Settings.
- Click Configurations.
- Scroll through the list of configurations and select Tunnel.

- Edit Device Traffic Rule sets.
- From within the Device Traffic Rules information block on the Tunnel Configuration page, click Edit.
- Add or modify device traffic rule set.

Introduced in Workspace ONE UEM 2011, Device Traffic Rule Sets expand the functionality of device traffic rules allowing for granular assignment of rule sets to different groups of users and devices. Device Traffic Rule Sets are assigned when creating the per-app VPN profile in a later step.
To get started with Device Traffic Rule Sets, perform the following in the Manage Traffic Assignments screen:- If no other Device Traffic Rule Sets exist (or a new rule set is required), click Add to create a new Device Traffic Rule Set.
- If modifications to an existing rule set are required, click the Device Traffic Rule Set name.
- Enter a name for the Device Traffic Rule Set (or if necessary, modify the name of an existing rule set).

- Click Manage Applications.
- Click Add to add a new application for device traffic rules.
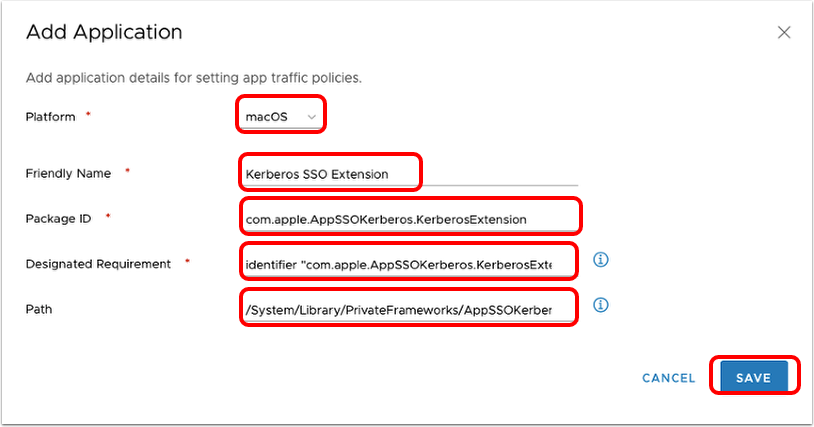
- Define the application.

- Select macOS for Platform.
- Enter the friendly name of the application, for example,
Kerberos SSO Extension. The friendly name is displayed in the Device Traffic Rule. - Enter the application's package id (
com.apple.AppSSOKerberos.KerberosExtension), which is the Identifier value displayed by running the command:
codesign -dv --entitlements - /System/Library/PrivateFrameworks/AppSSOKerberos.framework/PlugIns/KerberosExtension.appex/Contents/MacOS/KerberosExtension - Enter the application's Designated Requirement (
identifier "com.apple.AppSSOKerberos.KerberosExtension" and anchor apple), which is displayed to the right of the => sign of the following command:
codesign -d -r - /System/Library/PrivateFrameworks/AppSSOKerberos.framework/PlugIns/KerberosExtension.appex/Contents/MacOS/KerberosExtension - Enter the following path:
/System/Library/PrivateFrameworks/AppSSOKerberos.framework/PlugIns/KerberosExtension.appex/Contents/MacOS/KerberosExtension - Click Save.
- Define additional applications (macOS BigSur and later).
For macOS Big Sur and later, follow the same process defined in Add macOS Application to Rule Builder and Define the Application, configure these additional applications. These additional configurations allow the full functionality of the Kerberos SSO Extension with regard to Active Directory password sync and change.
AppSSOAgent:- Platform:
macOS - Friendly Name:
Kerberos SSO AppSSOAgent - Package ID:
com.apple.AppSSOAgent - Designated Requirement: identifier "com.apple.AppSSOAgent" and anchor apple
- Path: /System/Library/PrivateFrameworks/AppSSO.framework/Support/AppSSOAgent.app/Contents/MacOS/AppSSOAgent
- Platform:
KerberosMenuExtra:
- Platform:
macOS - Friendly Name:
Kerberos SSO KerberosMenuExtra - Package ID:
com.apple.KerberosMenuExtra - Designated Requirement:
identifier "com.apple.KerberosMenuExtra" and anchor apple - <No Path Required>
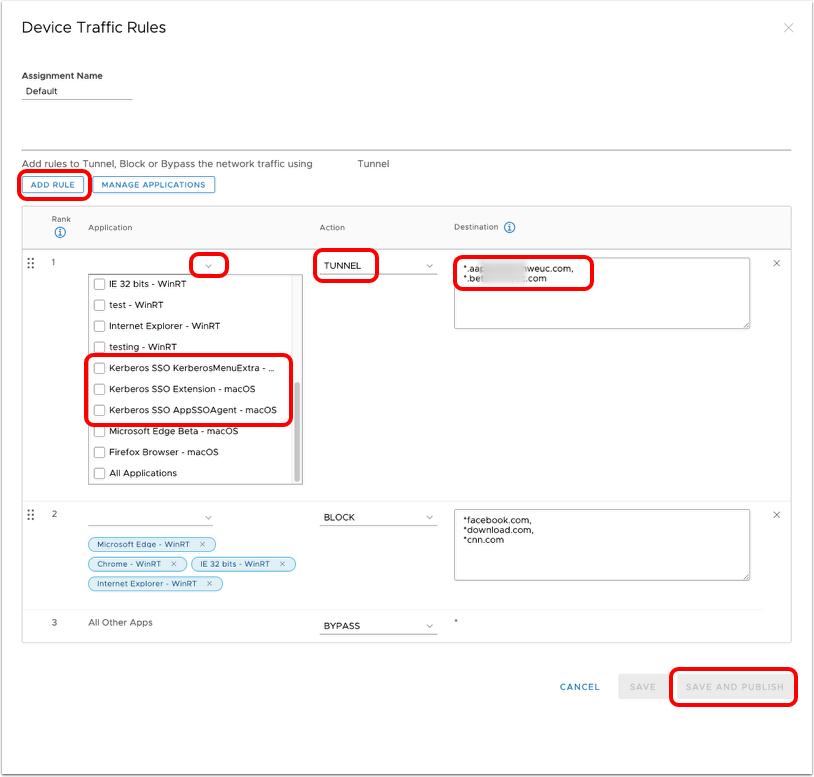
- Add device traffic rule.

- Click Add Rule.
- Click the down arrow in the Application column of the new device traffic rule.
- Select the three Kerberos SSO Extension apps you defined in the previous steps:
- com.apple.AppSSOKerberos.KerberosExtension
- com.apple.AppSSOAgent
- com.apple.KerberosMenuExtra
- Select Tunnel as the action.
- Configure destination domain names (include wildcards if needed) that match your domain controllers.
- Click Save and Publish.
Configure Kerberos Profile Payload
Next, create the Kerberos profile and configure the SSO extension payload.
- Click Add and click Profile.
- Select macOS.
- Select User Profile.
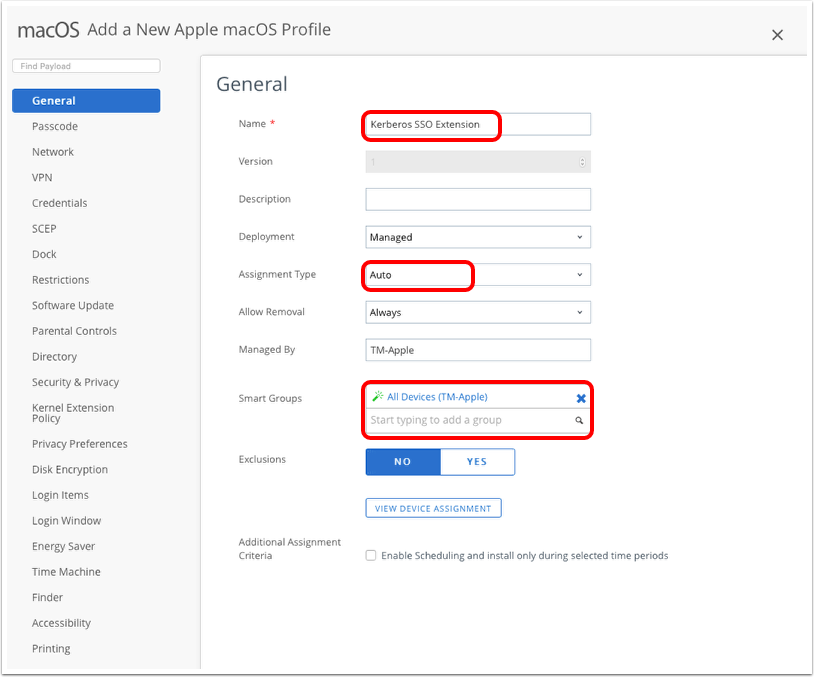
Note: The SSO Extension payload is available in both the User and Device context as of Workspace ONE UEM 2011 and later. The choice to use User Profile versus Device Profile will primarily be driven by the certificate used in the payload. In most cases, the certificate/credential should be used from the login keychain, and the Workspace ONE UEM administrator should use a User profile. Otherwise, choose Device Profile to use a certificate/credential from the system keychain. - Configure General Profile details.

- Enter a name for the profile, for example,
Kerberos SSO Extension. - Select Auto as the Assignment Type.
- Select one or more Smart Groups to assign the SSO Extension profile (or create a new smart group).
- Enter a name for the profile, for example,
- Configure SSO extension payload.

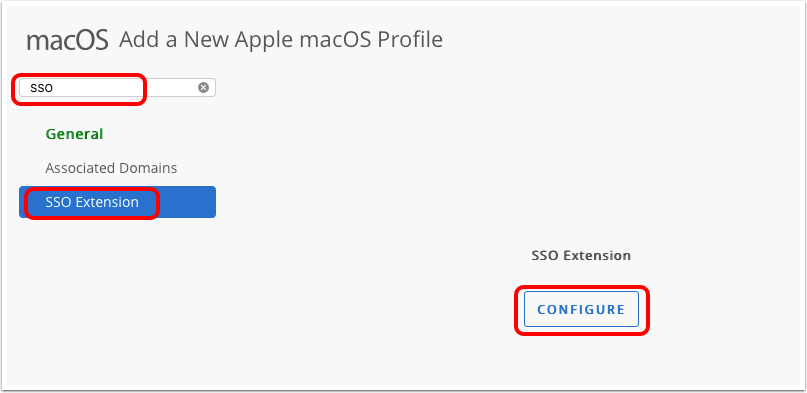
- Search for the SSO payload.
- Click SSO Extension.
- Click Configure.
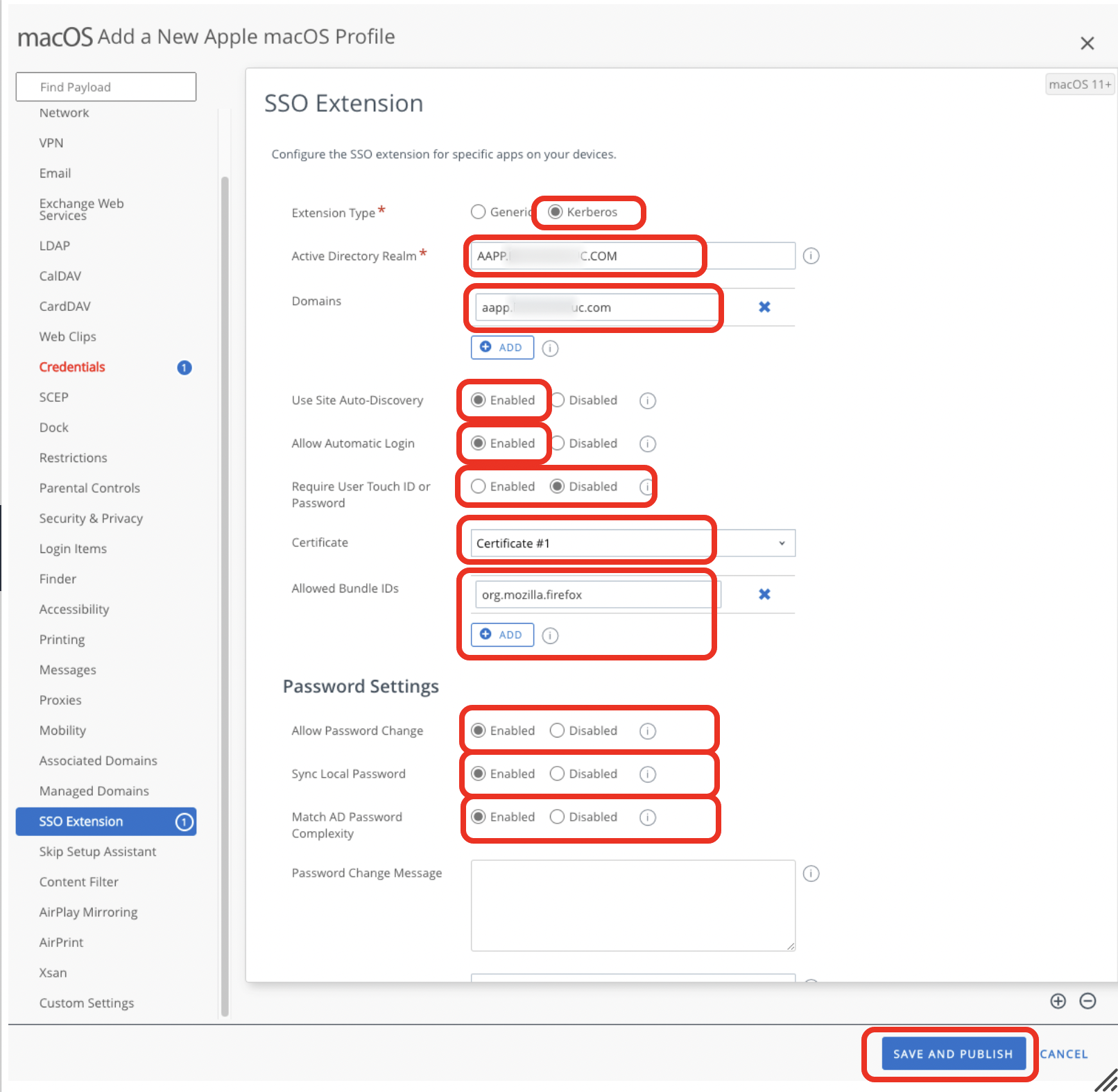
- Modify and save the SSO extension payload.

- Select Kerberos for Extension Type.
- Enter the Active Directory Realm (in capital letters) where the user logs in. For example,
AAPP.XXXX.COM. - Enter the Active Directory hosts and domains that can be authenticated through the extension. For example,
aapp.xxxx.com. - Select whether the extension should use active directory and DNS to discover its AD site.
- Select whether the extension should save passwords to the keychain.
- Select whether the user should be required to use biometrics or a password to use the keychain.
- Select the Certificate Credential that should be used for authenticating in the SSO Extension.
- Enter a list of application Bundle IDs allowed to use the Kerberos Ticket Granting Ticket. If more than one app is allowed, click Add to add additional bundle IDs.
- Select whether to allow users to initiate directory password changes from the extension.
- Select whether to keep the local macOS user account password synchronized with the Active Directory account password.
- Select whether passwords must meet Active Directory's definition of complex.
- Optionally, scroll down to configure additional parameters with regard to password settings.
- Click Save and Publish.
- Click Publish to publish the SSO extension profile.
Validate Kerberos Tickets
Finally, log in to Kerberos and confirm that the Kerberos credentials are obtained over Per-App VPN by the Kerberos SSO Extension.
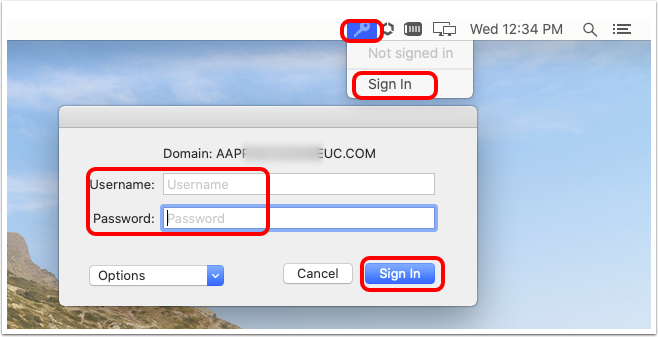
- Log in to Kerberos extension.

- Click the extension (key icon) in the menu bar.
- Click Sign In.
- Enter a user's username and password.
- Click Sign In.
- Click Yes to accept automatic sign-in.
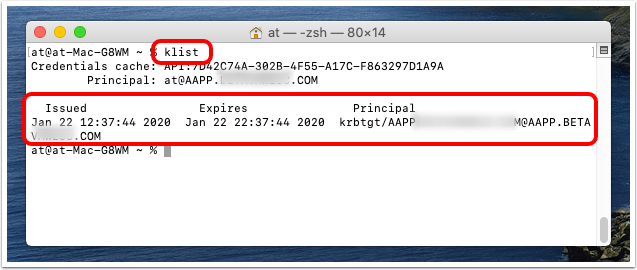
- Rerun
klistcommand.
- In
Terminal.app, enterklistand press return. - Observe the Kerberos Credential obtained over Per-App VPN by the built-in macOS Catalina Kerberos SSO Extension.
- In
- Validate Kerberos-enabled application or website.

- Launch an application that is Kerberos-enabled. If using a website, browse to the Kerberos-enabled website.
- Note the application or website is authenticated without any intervention from the user (no certificate chooser or username/password prompt).
Note: Some applications may require additional configuration to enable Kerberos Authentication. Google Chrome and Firefox also require additional configuration to enable Kerberos Authentication.
For Firefox:
- Open Firefox and enter about:config in the address bar.
- Search for negotiate and then double-click network.negotiate-auth.trust-uris.
- Enter a comma-separated list of domain names that should be enabled for Kerberos Authentication and click OK.
- Open a new tab and re-try the Kerberos-enabled website.
For Google Chrome:
- Create a Custom Settings payload in a User Profile for the device, targeting com.google.Chrome as the PayloadType.
- Include the following keys in your settings:
<key>AuthServerWhitelist</key>
<string>*.domain.name</string>
<key>AuthNegotiateDelegateWhitelist</key>
<string>*.domain.name</string>
Caution: Some apps spawn helper applications to assist with background tasks. In these cases, the helper apps may be making DNS calls or performing other network tasks requiring the Per-App Tunnel but may not be part of a device traffic rule. One particular example of this is Google Chrome, which performs network functions outside the Google Chrome.app process. In this case, the helper application must be added to the device traffic rule, otherwise, specific settings are required to be changed client-side within the application.
As an example, to validate Kerberos-enabled websites in Google Chrome using Per-App Tunnel, perform the following:
- In the URL field, enter chrome://flags
- Search for
networkin the Search flags text box. - Set Runs network service in-process to Enabled and relaunch Google Chrome before proceeding with testing.
This small change allows Google Chrome to leverage the Per-App Tunnel for connectivity required to query DNS and obtain Kerberos tickets. At the time of writing, the ForceNetworkInProcess key was not available in Chrome for macOS and must be enabled by the individual user.
Troubleshooting Workspace ONE Tunnel on macOS
If a Per-App Tunnel problem occurs on macOS, there are a number of places to troubleshoot. This section of the tutorial covers where to troubleshoot on macOS at a high level. Depending on the problem, there might be steps that should be performed on the Unified Access Gateway. However, troubleshooting the Unified Access Gateway is outside the scope of this tutorial. Workspace ONE UEM administrators should contact our support for assistance when troubleshooting Per-App Tunnel, Workspace ONE Tunnel, or the Unified Access Gateway.
This section covers a high-level set of initial troubleshooting steps.
To begin, open Workspace ONE Tunnel app.
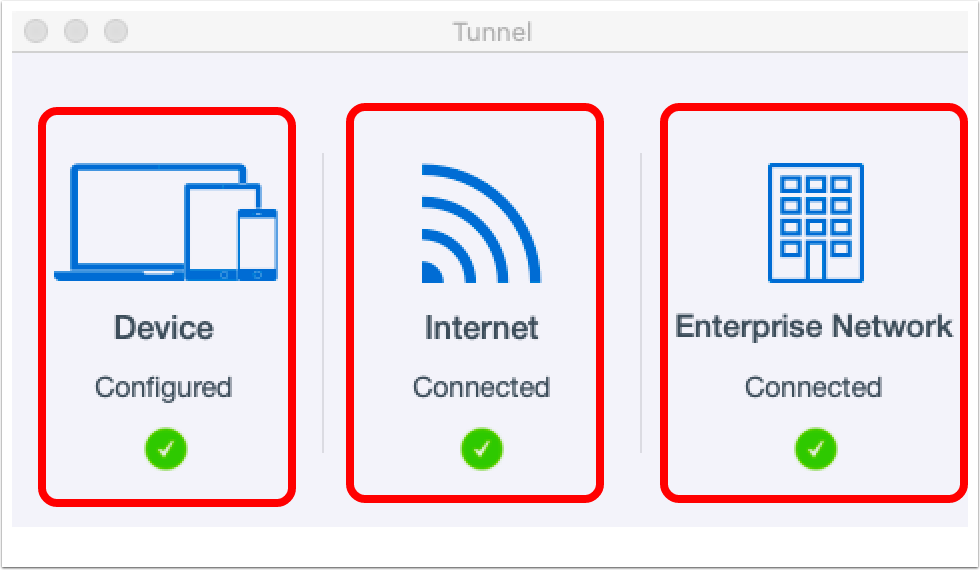
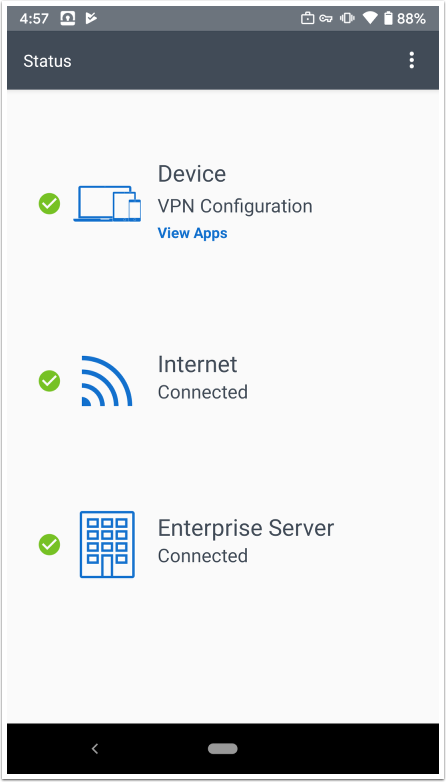
Ensure Tunnel is Configured
- Ensure that the Device Configured status shows Configured. This indicates that Workspace ONE Tunnel has received configuration data from Workspace ONE UEM. If the status is not configured, try one of the following:

- Check the Device Traffic Rules and Save and Publish the rules again.
- Check the last seen value for the device in the Workspace ONE UEM console. Is the device communicating with Workspace ONE UEM?
- Validate that other MDM commands are being sent to the device. Create an assignment (smart) group containing the single device and attempt to send it a new profile payload.
- Ensure that the Internet status shows Connected. If Tunnel cannot connect to the Internet, it probably cannot connect to the Unified Access Gateway.
- Validate that the device has a working Ethernet or Wi-Fi connection (IP address, subnet mask, gateway, and DNS addresses are present).
- Validate DNS resolution: Open Terminal and enter
nslookup uag.fully.qualified.domainto ensure that an IP address is resolved. - Validate Connectivity to UAG: Within Terminal, enter
nc -vz uag.fully.qualified.domain uagport(such asnc -vz uag.company.com 443).
- Ensure that the Enterprise Network status shows Connected. If Workspace ONE Tunnel is disconnected from the Enterprise network, apps cannot use Per-App Tunnel. This might indicate an issue with Workspace ONE Tunnel connecting to the Unified Access Gateway or an issue with Device Traffic Rules.
The remainder of this section details how to troubleshoot Tunnel connectivity.
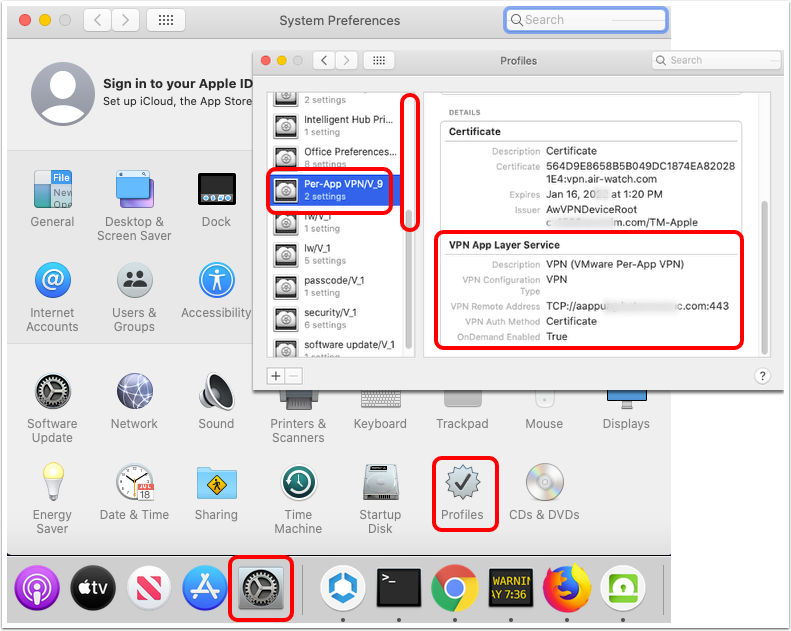
Validate Per-App VPN Profile
- Click System Preferences.

- Double-click Profiles.
- Scroll through the left panel.
- Click the Per-App VPN profile that was created.
- Ensure that the VPN App Layer Service details are correct, especially the VPN Remote Address and the OnDemand Enabled value.
- If the profile is missing or misconfigured, check the profile configuration and re-push the profile to the device from within the UEM Console Device Details view (on the Profiles tab).
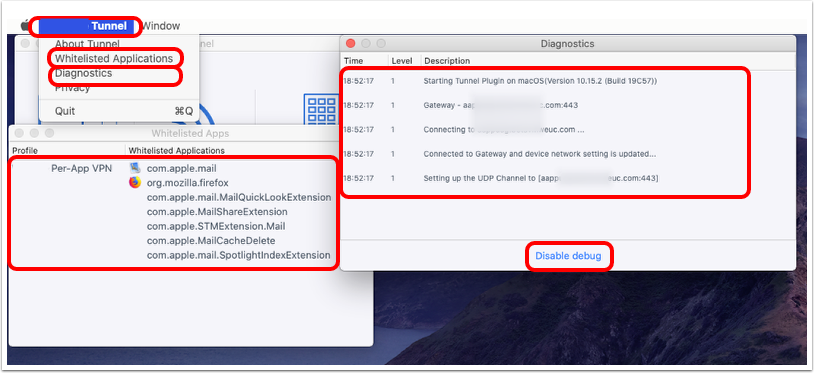
Validate Advanced Tunnel Information
- Open the Workspace ONE Tunnel client and click the Tunnel menu.

- Click Whitelisted Applications.
- Verify that the list of allowlisted applications matches the settings configured in the Device Traffic Rules.
- From the Omnissa Tunnel menu (#1), click Diagnostics.
- Click Enable Debug to get verbose information.
- Review Diagnostics information.
- Click Disable Debug when troubleshooting is complete.
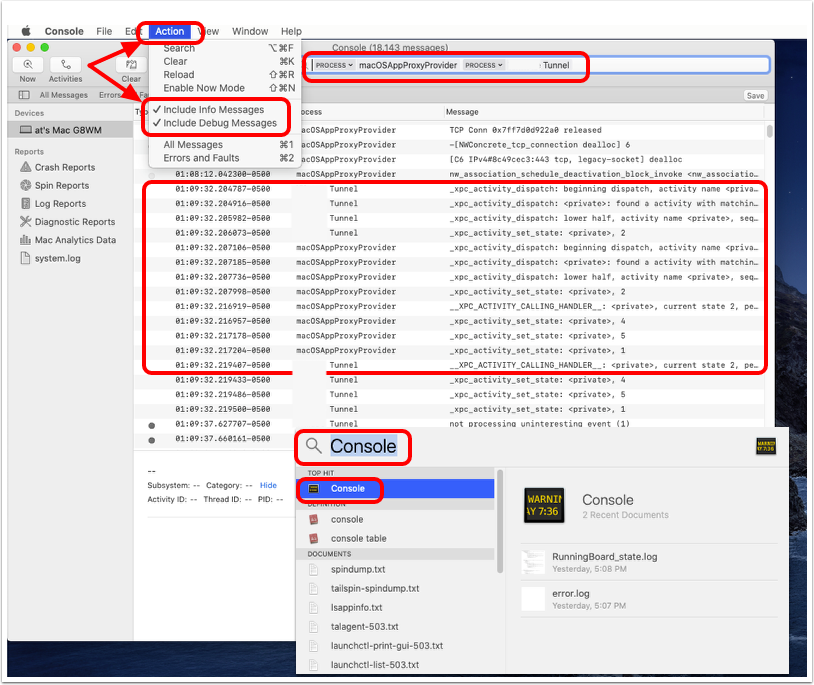
Review Tunnel-Related Unified Logging
- Press CMD+SpaceBar (⌘+Space) and enter
consoleinto the Finder window.
- Select the Console application.
- Enter
process:macOSAppProxyProviderinto the search bar and press Return on the keyboard. - Without clearing the contents of the search bar, add an additional filter parameter by adding
process:OmnissaTunnelinto the search bar and press Return on the keyboard. - Click the Action menu and confirm that Include Info Messages and Include Debug Messages are selected.
- Review the logging produced within the Console application.
Tip: If the console filters do not provide any meaningful data, you can optionally attempt to view information and debug messages from entire subsystems. Some filters that may help include:
-
process:macOSAppProxyProvider -
any:*.macos-tunnel
Also, if troubleshooting Kerberos over the Per-App Tunnel, you can include the following console filters:
-
subsystem:com.apple.appsso -
subsystem:com.apple.appssokerberosextension
The following Terminal command might provide meaningful output: log stream --debug --predicate '(subsystem == "com.apple.Heimdal") OR (subsystem == "com.apple.AppSSO") OR (subsystem == "org.h5l.gss") OR (subsystem == "com.apple.network") OR (process == "Omnissa Tunnel") '
General VPN Network Extension Troubleshooting
Per Apple's Developer Website (requires login), you can use the following commands to gather additional data from the VPN (Network Extension):
-
sudo defaults write /Library/Preferences/com.apple.networkextension.control.plistLogToFile -boolean true -
sudo defaults write /Library/Preferences/com.apple.networkextension.control.plistLogLevel -int 7
Reproduce the issue and then enter this command in Terminal.app:
-
/System/Library/Frameworks/SystemConfiguration.framework/Resources/get-mobility-info
You should find additional information in the resulting get-mobility-info output file.
You can later deactivate the logging by issuing the following commands:
-
sudo defaults delete /Library/Preferences/com.apple.networkextension.control.plistLogToFile -
sudo defaults delete /Library/Preferences/com.apple.networkextension.control.plistLogLevel
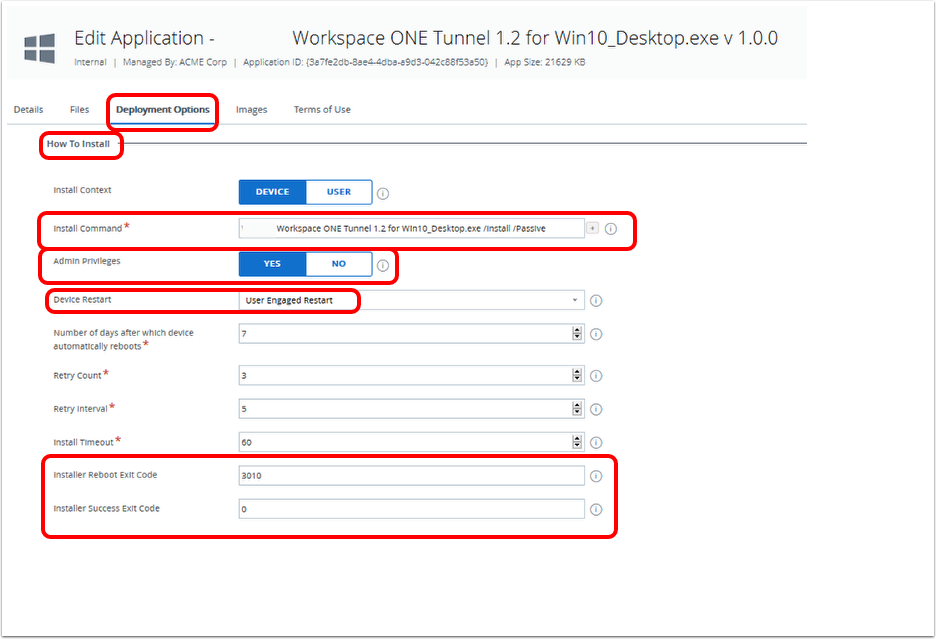
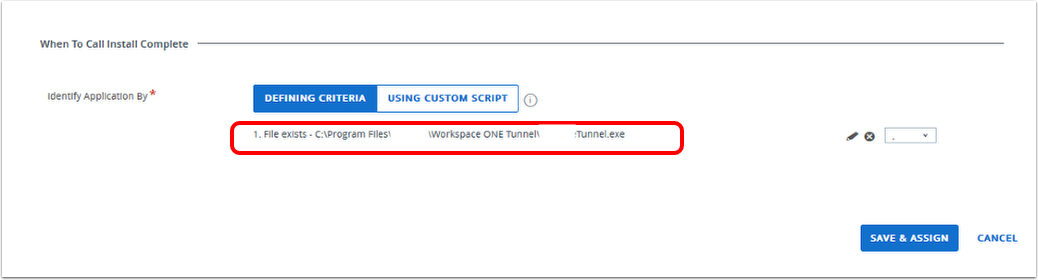
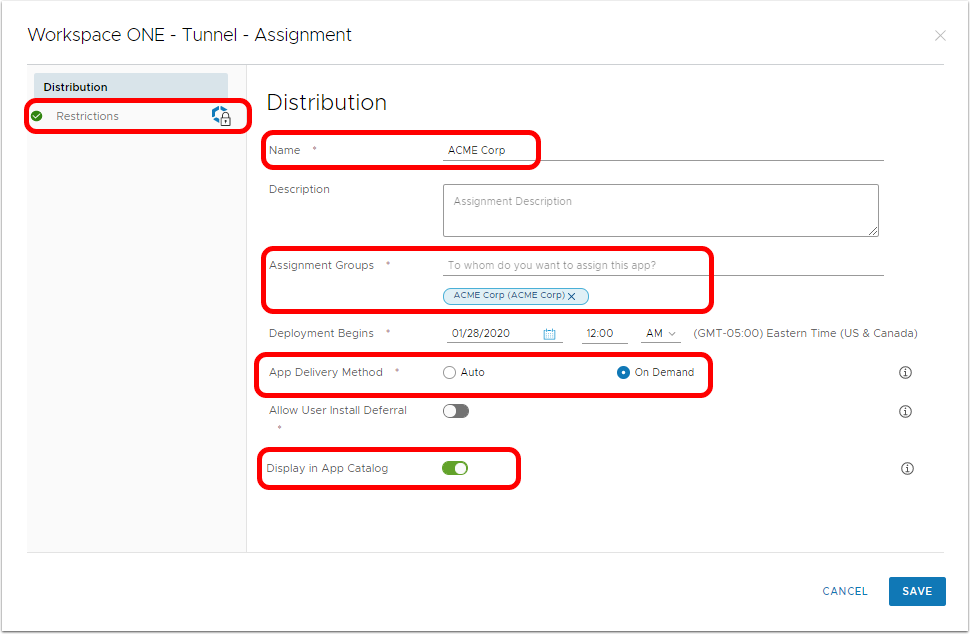
Deploying Workspace ONE Tunnel for Windows Desktop
Per-App Tunneling helps users to access critical information using applications on their devices from their devices. Mobile flows help users perform business-critical tasks from a single app — streamlining the user experience.
Leveraging Per-App Tunnel allows you to control which applications are on a device and what internal resources the applications have access to by automatically activating or deactivating Per-App VPN access, based on which applications are active. By enabling remote access, you no longer need to provide a device-wide VPN on your devices, which can allow unintended or unauthorized apps or processes to access your VPN. In this tutorial, you configure and deploy Workspace ONE Tunnel to enable the Per-App Tunnel component on managed devices.
These exercises involve the following components:
- Workspace ONE Tunnel – The app used on the device to securely connect to the Unified Access Gateway to provide Per-App Tunnel functionality, also referred to as Tunnel Client.
- Unified Access Gateway – The virtual appliance where the Tunnel edge service is installed, and to which the tunnel client connects.
- Per-App Tunnel – Component of Tunnel edge service for connecting to a secure tunnel channel on a per-application basis, which is controlled and configured by the VPN profile payload and Device Traffic Rules.
- Per-App VPN Profile and Device Traffic Rules – The Workspace ONE UEM configuration is pushed to the device that contains the Per-App Tunnel configurations. Every time a specified application is opened, the Workspace ONE Tunnel client evaluates the Device Traffic Rules assigned to it before making any routing decisions and establishes a Per-App tunnel connection with the Unified Access Gateway based on the Per-App VPN Profile configuration.
High-Level Architecture
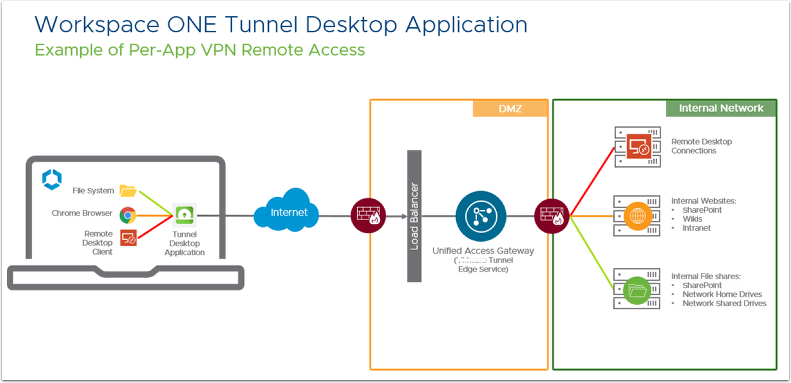
The device contains the applications required by the end-user to perform their daily job. Some applications require access to internal resources to function. Those applications, based on Per-App VPN configuration, use Workspace ONE Tunnel which communicates with the Tunnel Service on Unified Access Gateway hosted on the DMZ, to validate if the device requesting access is in compliance or not before authorizing access through the internal resource.
Prerequisites
Before you can perform the steps in this exercise, you must have the following components installed and configured:
- Workspace ONE UEM 2203+
- Windows 10 1704+ or Windows 11+ enrolled in Workspace ONE UEM
- Latest version of the Workspace ONE Tunnel Desktop Application
- Download the installer file: Workspace ONE Tunnel
- For more information, see Supported Platforms for Workspace ONE Tunnel
- VPN tunnel must be configured before you can add it as an application
Note: See Workspace ONE Tunnel for Windows Release Notes for updates to the client.
Configuring Device Traffic Rules for Windows
This exercise outlines how to configure device traffic rules for Windows. Before you start this section, read the Device Traffic Rules chapter for a better understanding of how device traffic rules are managed by Workspace ONE Tunnel.
For this example, the user must access internal websites, internal network file shares, and a remote desktop session. To allow secure access, you configure Workspace ONE Tunnel to allow only the applications required.
In this exercise, you configure the following:
- Internal web browser access - defining Chrome as the application
- Internal network file shares - allowing system access
- Remote Desktop Session Connection - defining Microsoft Remote Desktop client as the application
Note: Domain values used in this section are examples only. Your values will differ.
- Access configurations.
- In the Workspace ONE UEM console, click Groups & Settings.
- Click Configurations.
- Scroll through the list of configurations and select Tunnel.

- Edit Device Traffic Rule sets.
- From within the Device Traffic Rules information block on the Tunnel Configuration page, click Edit.
- Add or modify device traffic rule set.

Introduced in Workspace ONE UEM 2011, Device Traffic Rule Sets expand the functionality of device traffic rules allowing for granular assignment of rule sets to different groups of users and devices. Device Traffic Rule Sets are assigned when creating the per-app VPN profile in a later step.
To get started with Device Traffic Rule Sets, perform the following in the Manage Traffic Assignments screen:- If no other Device Traffic Rule Sets exist (or a new rule set is required), click Add to create a new Device Traffic Rule Set.
- If modifications to an existing rule set are required, click the Device Traffic Rule Set name.
- Set or modify device traffic rule name and tunnel mode.

- Enter a name for the Device Traffic Rule Set (or if necessary, modify the name of an existing rule set).
- Set the Tunnel Mode to Per Application.
This first tutorial on Windows shows you how to configure device traffic rules based on Per-Application Tunnel Mode. After completing the Windows tutorial return and switch the Tunnel Mode for this rule to Full Device. The Application fields will be removed and you will be required to specify only the actions and destination domains.
- Click Manage Applications.
- Click Add.
- Define the application.

- Select Windows as the Platform.
- Enter the friendly name of the application. The friendly name is displayed in the Device Traffic Rule.
- Select the App Type, for example, Desktop App. The App Type can be a traditional Windows application or a Windows Store application.
- Enter the App Identifier. For traditional Windows applications, use the File Path. For Store applications, you must enter the Package Family Name or PFN. You can use the PowerShell command
Get-AppxPackageto find the PFN. For more information, see Microsoft Docs: Find a package family name (PFN) for per-app VPN.
- Add Chrome Web browser access.

- In this example, the Chrome application is defined under the Program Files (x86) path. The App Identifier value should contain the full path where the EXE file is located on the Windows machine.
- The screenshot shows that the App Identifier used for Chrome is
C:\Program Files (x86)\Google\Chrome\Application\chrome.exe - After you have entered the application details, click Save.
- Add remote desktop (RDP) client.

- Next, add the Remote Desktop client. This allows end users to connect to Remote Desktop Hosts located behind the corporate firewall.
- As the Remote Desktop Client is built into the Windows Operating system, the file path of the executable is different.
- For example, in this screenshot, the App Identifier used for the RDP client is
C:\Windows\System32\mstsc.exe - After you have entered the application details, click Save.
- Add SMB for network drive and printer support.

- Next, add support for tunneling SMB traffic from the system to allow users to map network shares and network printers. This allows end users to connect to file shares and printers that are located behind the corporate firewall.
- As the SMB protocol is built into the Windows Operating system, the App Identifier is not an executable, instead, you define
Systemas the App Identifier. - After you have entered the application details, click Save.
- Add more applications to device traffic rules, if required.
- If more applications are needed for the ruleset, click Add and repeat starting at Define the Application.
- If all the required applications have been defined, click X to close the Manage Applications window.
- Add device traffic rule.

- Observe (and optionally modify) the default action which applies to all Windows applications.
- Tunnel – All apps on the device configured for Per-App Tunnel send network traffic through the tunnel. For example, set the Default Action to Tunnel to ensure all configured apps without a defined traffic rule use the Workspace ONE Tunnel for internal communications.
- Block – Blocks all apps on the device configured for Per-App Tunnel from sending network traffic. For example, set the Default Action to Block to ensure that all configured apps without a defined traffic rule cannot send any network traffic regardless of destination.
- Bypass – All apps on the device configured for Per-App Tunnel bypass the tunnel and connect to the Internet directly. For example, set the Default Action to Bypass to ensure all configured apps without a defined traffic rule bypass the Workspace ONE Tunnel to access their destination directly.
- Click Add Device Traffic Rule.
- Observe (and optionally modify) the default action which applies to all Windows applications.
- Build device traffic rule.

- In the newly created traffic rule, Click the down arrow to display the Application list.
- Select one or more triggering applications to control with this rule. All Applications not applicable to Windows.
- Select the Appropriate Action for Workspace ONE Tunnel to perform on traffic from the selected apps - For this exercise, select Tunnel.
- Tunnel – Sends app network traffic for specified domains through the tunnel to your internal network.
- Block – Blocks all traffic sent to specified domains.
- Bypass – Bypasses the Workspace ONE Tunnel so the application accesses specified domains directly.
- Proxy – Redirect traffic to the specified HTTPS proxy for the listed domains. The proxy must be HTTPS and must follow the correct format:
https://example.com:port. - Note: Proxy is not yet supported using the Workspace ONE Tunnel Desktop Application.
- Enter one or more comma-separated fully qualified domain names as destinations to which Workspace ONE Tunnel should apply the Device Traffic Rule. A single asterisk (*) can be used as a wild card for subdomains.
- If necessary, adjust the Device Traffic Rules rank in the list. Lower-numbered rank is the highest priority.
- If necessary, click Add Rule and repeat Build Device Traffic Rule until you have added all the necessary Device Traffic Rules for your organization.
- Click Save.
For more information on the formats (wildcards, IP, ports) allowed into the Destination field, see the Device Traffic Rules Destination formats supported chapter.
Note: For Windows Desktop devices, if Enhanced Domain Resolution is not enabled on the Per-App VPN profile, the domains added to the destination must also be added to the list of domains part of the DNS Resolution via Tunnel Gateway.
- Review the summary of the device traffic rule configurations.

- The Application list contains triggering applications Chrome, Remote Desktop, and System.
- The applications appear in the following format: Application Friendly Name - UEM Organization Group - Platform
- Google Chrome - ACME Corp - WinRT
- RDP - ACME Corp - WinRT
- System - ACME Corp - WinRT
- The applications appear in the following format: Application Friendly Name - UEM Organization Group - Platform
- The Appropriate Action for Workspace ONE Tunnel to perform is Tunnel.
- Tunnel – Sends app network traffic for specified domains through the tunnel to your internal network
- Destination - For this example, the domains are
*.corp.localand*.airwlab.com
- Optional - You can also configure Device Traffic Rules to Block.
- In this example, Chrome is set to block domains
*.cnn.com,*.facebook.com, and*.match.com.
- In this example, Chrome is set to block domains
- The Application list contains triggering applications Chrome, Remote Desktop, and System.
Distributing Workspace ONE Tunnel for Windows
In this exercise, you deploy the Workspace ONE Tunnel Desktop Application on Windows 10 devices.
Note: The Per-App VPN profile should already be configured as part of the Prerequisites.
- Download the Workspace ONE Tunnel desktop installer.

- Navigate to https://my.workspaceone.com/products and log in with your credentials.
- Click View All.
- Scroll to the end of the page and select Workspace ONE Tunnel.

- Select platform and version.

- Select Windows as the platform.
- Select the Latest version for the Workspace ONE Tunnel Desktop Application.
- Filter by console version.
- Select Install and Upgrades tab for a link to the download.
After you have Accepted the Terms of Use, the download should begin immediately.
Tip: It is helpful to have all Installation files pre-downloaded on your local machine, ready to upload into Workspace ONE UEM.
To improve user experience, have the application icons and screenshots of the application ready for the Application catalog.
- Upload Tunnel application into Workspace ONE UEM.

- In the Workspace ONE UEM console, click Resources.
- Select Internal Application.
- Click Add > Application File and Upload.
- Browse for the Workspace ONE Tunnel EXE installer file and click Save.
- Select No for Is this a dependency app?.
- Click Continue.
- On the Details tab, enter a name. For example, Workspace ONE Tunnel.

- On the Files tab, Scroll down to find the App Uninstall Process section. For Tunnel, enter
Workspace ONE Tunnel 1.2 for Win10_Desktop.exe /uninstall /Passiveas the Uninstall Command.
- Configure the Deployment Options tab.

- Select the Deployment Options tab.
- Locate the When to Install section.
- Configure any minimum requirements for the following:
- Data Contingencies - Use where criteria type needs to check for existing/non-existing Applications, Files or Registry Keys.
- Disk Space Required - This specifies the amount of disk space the device must have available to install the application.
- Device Power Required - This specifies the battery power, in percentage, that the device must have to install the application.
- RAM Required - This specifies the amount of RAM the device must have to install the application.
- Find the Install command options.
Some application installers may contain help options. Find help options by running the application file and adding/helpor/?to the end of the file.
The following steps demonstrate how to run these commands.- Find the installer file.

- Hold SHIFT + Right-click the installer file.
- Hold Select Copy As Path.
- Open Command Prompt.

- Paste in the installer file location, adding
/helpor/?to the end. - This should show a dialog box to show supported installation commands.
- Find the installer file.
The results of running the command are shown in the screenshot. This example shows the supported Workspace ONE Tunnel Desktop Application Install parameters.
- Define How to Install.

- Under Deployment Options tab, scroll down to find the How To Install section.
- For the Install Command, enter
Workspace ONE Tunnel 1.2 for Win10_Desktop.exe /Install /Passive. - Ensure Admin Privileges is set to Yes.
- Change Device Restart if required. This example uses User Engaged Restart. This allows the user to reboot the machine to complete the install when the user is ready.
- For Installer Reboot Exit Code, the supported values are
3010and1641. - For Installer Success Exit Code, the supported values are
0and3010.
| Error Code | Value | Description |
| ERROR_SUCCESS | 0 | The action completed successfully. |
| ERROR_SUCCESS_REBOOT_INITIATED | 1641 | The installer has initiated a restart. This message indicates success. |
| ERROR_SUCCESS_REBOOT_REQUIRED | 3010 | A restart is required to complete the install. This message indicates success. This does not include installs where the ForceReboot action is run. |
- Define When to Call Install Complete.

- Click Add.
- Select File Exists for the Criteria Type.
- Enter
C:\Program Files\Omnissa\Workspace ONE Tunnel\OmnissaTunnel.exefor the Path. - Click Add.
- Add the application icon.

- Select the Images tab.
- Select the Icon tab.
- Click the area labeled Click or drag files here.
- Navigate to the folder containing the Application logo, or download the provided image to use.
- Set Terms of Use.
- Select the Terms of Use tab.
- If you decide to have a Terms of Use that your users must accept before installing applications, you can configure that here. For this exercise, select None.
- Click Save & Assign.
- Select Assignments and click Add Assignment.
- Configure the assignment.
- Click Add Assignment.
- Configure application distribution settings.

- Give the application assignment a name.
- Select the Select Assignment Groups search box and select an assignment group, for example, (Acme Corp).
- Select On-Demand for the App Delivery Method.
- Select Show for Display in App Catalog.
- Navigate to the Restrictions Tab.
- Enable for Make App MDM Managed if User Installed.
- Select Save then click Save and Publish.
- Confirm that the application appears in List View.

- On the Internal applications List View, confirm that the Workspace ONE Tunnel Desktop Application is displayed.
You have successfully added the Workspace ONE Tunnel Desktop Application to Workspace ONE UEM for deployment.
Creating Per-App VPN Profile for Windows Desktop
On Windows Desktop, Tunnel can force selected applications to connect through your corporate VPN.
In this exercise, you configure the Windows Desktop profile which configures the tunnel client on the device to allow only designated applications to access content on internal servers.
Log in to the Workspace ONE UEM console to perform the next steps.
- Click Add and click Profile.
- Select Windows.
- Select Windows Desktop.
- Select Device Profile.
- Configure the General settings.

- Select the General tab.
- Enter a Name, for example,
Per App VPN. - Select Assignment type. This example uses Auto, so devices automatically receive the policy.
- Assign the policy to a Smart Group(s).
- Add and configure VPN payload.

- Select VPN from the payload menu and click Configure.
- Enter a Connection Name for the policy, for example,
Corp VPN. - Select Workspace ONE Tunnel from the Connection Type drop-down menu.
- Choose the Device Traffic Rule Set (as configured in Configuring Device Traffic Rules for Windows 10) to be assigned via this Profile Payload.
- Select Enable for Desktop Client - This enables the Workspace ONE Tunnel Desktop Application, otherwise it will use the Windows UWP client, no longer recommended.
- Configure Custom Configuration XML as needed. Refer to Custom Configuration XML for Windows Desktop for additional details on the list of Custom Configuration parameters available.
- Select Enable for the Enhanced Domain Resolution located under DNS Resolution via Tunnel Gateway.
- Click Save & Publish.
- Click Publish to publish the VPN profile.
Custom Configuration XML for Windows Desktop
Custom Configuration allows the administrator to determine the behavior of the Tunnel Client on the device, from initialization process, UI elements and network behavior.
For example, the following XML configuration allows the end user to turn on/off (ToggleTunnelFeature) the Tunnel from the tray icon, and change the Tunnel connection (OnDemand) from an on-demand basis to always connected.
<?xml version="1.0" encoding="utf-16"?>
<CustomConfiguration>
<ToggleTunnelFeature>true</ToggleTunnelFeature>
<OnDemand>false</OnDemand>
</CustomConfiguration>
The result of this XML configuration reflects on the UI of the Tunnel Windows Client showing an option to enable/deactivate the Tunnel Client, and for the OnDemand connection, it determines the Tunnel internal behavior as always connected.
Several other parameters can be customized to change the Tunnel behaviour; the following table lists the custom configuration parameters supported and their respective Tunnel Mode. For additional information, visit the Configure Tunnel Profile for Windows Desktop Client in the product documentation.
| Custom Configuration XML tag syntax | Description | Tunnel Mode |
| Format
For Wildcard Certificate For SAN Certificates mention the complete Subject Alternate Name | Required when using Third-Party SSL certificate for the Tunnel Server Certificate. This applies only to the SAN Certificate and Wildcard certificate. To retrieve the subject CN name: 1. Open the certificate on a Windows machine. 2. Select the Details tab. 3.The Subject row contains the CN of the cert. | Per-App and Full Device |
| | List of DNS search domains in comma-separated values | Per-App and Full Device |
| | List of probe URLs used by the Desktop client to consider if it is connected to a trusted network based on the reachability. Supported schemes: http:// & https:// or IP Addresses http://10.0.0.1 | Per-App and Full Device |
| | Comma separated list of hostnames whose resolution should not be tunneled | Per-App |
| | Default is false. When set to true, users will be given an option to Enable and Disable tunnel client service OnDemand from the system tray icon. The Tunnel Client Service will be up when the user deactivates from the tray icon, but the Tunnel client will not intercept any traffic. When the user enables the Tunnel Client from the tray icon the tunnel client will be ready to intercept the traffic and tunnel the requests. | Per-App and Full Device |
| | Default is true. When set to true, Tunnel Client will connect when required based on incoming requests from the apps, like user trying to browser. If there is not traffic for 5 minutes, Tunnel Client will disconnect automatically. When set to false, Tunnel Client will be always connected. | Per-App and Full Device |
| | Default is false. Use this attribute to enable the Tunnel service to start before you log in. This parameter is useful for specific domain authentication scenarios, such as dropship provision where Tunnel needs to start before the user logon. | Per-App and Full Device |
| | Use this attribute to prefer external DNS response over internal DNS response when DNS response is received from both. | Per-App and Full Device Note: Use the PreferInternalDNS or PreferExternalDNS XML code in the Configuration XML. If both the XML codes are used in the Configuration XML, then the PreferInternalDNS XML code takes precedence. |
| | Use this attribute to prefer internal DNS response over external DNS response when DNS response is received from both. |
Testing Per-App Tunnel on Windows
Now that the enrolled device has received the settings configured in the Workspace ONE UEM Console, you are ready to begin testing the Per-App VPN functionality. The Workspace ONE Tunnel Desktop Application should be installed on your device.
In this exercise, you learn how to:
- Launch an internal website with an authorized application.
- Launch an internal website with an unauthorized application.
- Launch a defined application and demonstrate blocked domains.
- Launch an RDP session and connect to the machine on the internal network.
- Connect to an SMB share to access file shares inside the corporate network.
Launch Internal Website with an Authorized Application
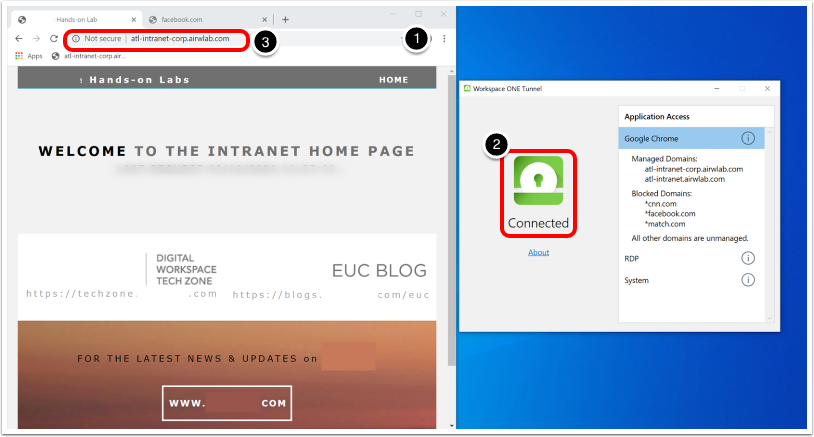
- Launch Chrome as a browser. Chrome was the application specified to Tunnel traffic.
- The Workspace ONE Tunnel Desktop Application is connected and an internal web page is displayed.
- The address used –
atl-intranet-corp.airwlab.com– is specified in the Device Traffic Rules in the previous exercise.
This web page is accessible only to applications (in this use case, Chrome) defined in the policy.
Launch Internal Website with an Unauthorized Application
Next, open another web browser, such as Microsoft Edge, and navigate to an internal web page. For example, atl-intranet-corp.airwlab.com.
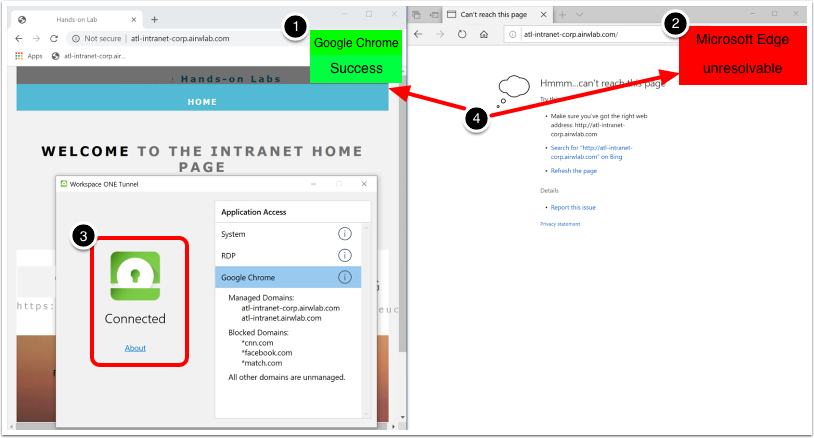
- Launch Chrome - this is the authorized application.
- Launch another browser - for example, Microsoft Edge.
- The Workspace ONE Tunnel Desktop Application is connected and an internal web page is displayed.
- The address
atl-intranet-corp.airwlab.comcan be resolved in Chrome, but not in Microsoft Edge.
Launch a Defined Application to Demonstrate Blocked Domains
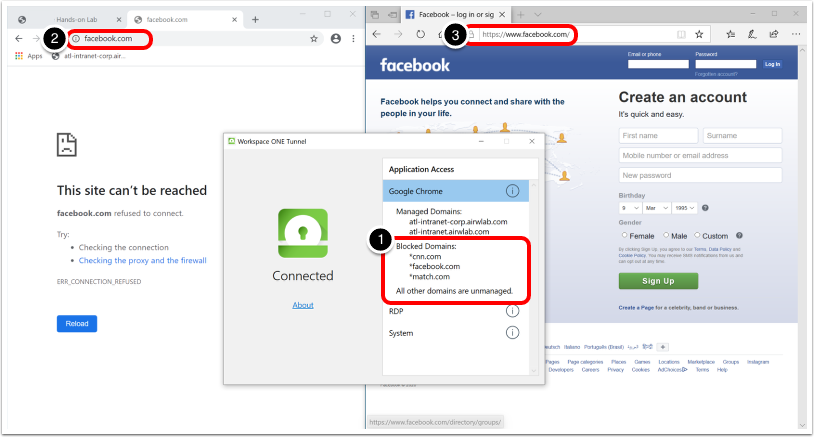
- In the Application access rules, certain websites are blocked. These were listed in the Device Traffic Rules.
- Websites blocked are
cnn.com,facebook.com, andmatch.com.
- Websites blocked are
- Open Chrome and navigate to one of these websites. This example uses
facebook.com.- When trying to resolve the DNS name, the browser displays an error as this website is blocked.
- Launch another browser, in this case, Microsoft Edge. Facebook.com is accessible, as the policy is configured for Chrome only.
Test RDP Connections
Sometimes, you may need to RDP into desktop sessions that are located back in the office.
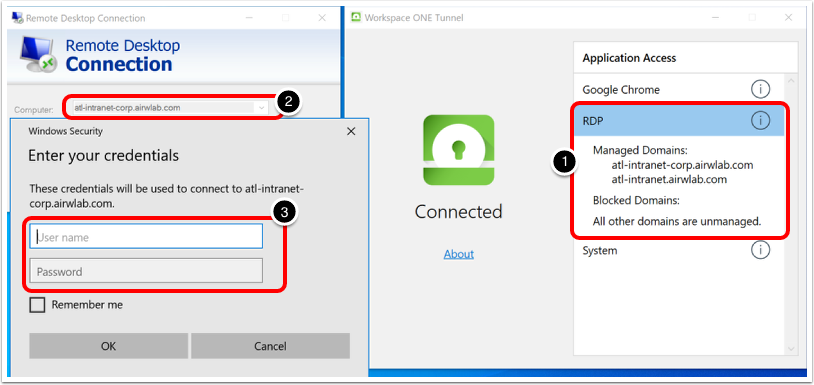
- In the Application access rules, confirm the domain configuration for Remote Desktop Client access.
Note: The RDP application is not from the Windows Store. - Launch the RDP application and enter the machine name. In this example, you connect to the machine atl-intranet-corp on the domain airwlab.com.
- Workspace ONE Tunnel Desktop Application resolves this address, and you should be prompted for authentication.
Test SMB Share Connections
Workspace ONE Tunnel Desktop Application allows remote Windows users to connect to file shares located behind the corporate firewall. This can be team shares, individual shares, or connecting to a specific machines' C drive, for example.
This example uses the host atl-intranet-corp and connects to its C: drive.
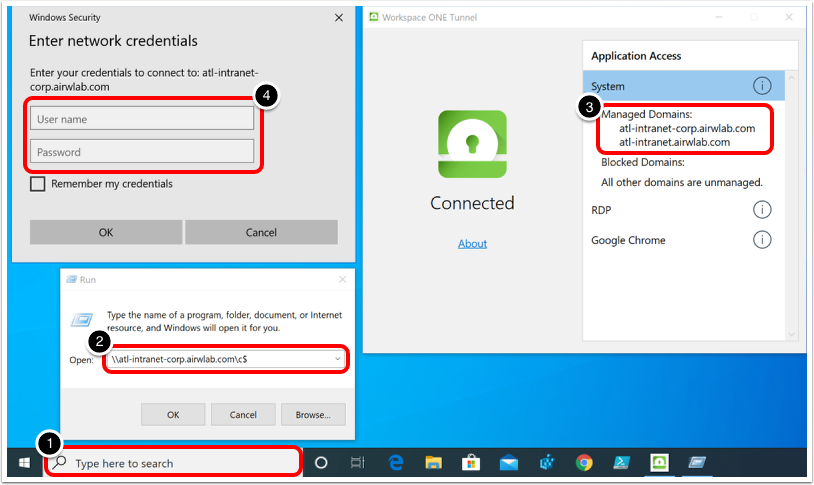
- In the search bar, enter Run and press the return key.
- Enter the address of the file share you would like to connect to. For example,
\\atl-intranet-corp.airwlab.com\c$. - In the Application access rules, confirm the domain configuration for System resource access.
- Launch the SMB share. Tunnel will resolve this address, and you should be prompted for authentication to the SMB share.
Troubleshooting Workspace ONE Tunnel on Windows
If a Per-App Tunnel problem occurs on Windows Desktop, you can check a number of places to troubleshoot. This section of the operational tutorial covers where to troubleshoot on Windows Desktop at a high level. Depending on the problem, there may be steps that should be performed on the Unified Access Gateway. However, troubleshooting the Unified Access Gateway is outside the scope of this tutorial. Workspace ONE UEM administrators should contact our support for assistance when troubleshooting Per-App Tunnel, Workspace ONE Tunnel, or the Unified Access Gateway.
This section is divided into two and covers the following high-level set of initial troubleshooting steps.
- Workspace ONE Tunnel Desktop Application Installation Troubleshooting.
- Checking Workspace ONE UEM console for application install status.
- Locating Workspace ONE Tunnel desktop application installer logs.
- Checking device registry for Workspace ONE Tunnel desktop application install status.
- Checking Workspace ONE UEM console for Policy install status.
- Checking device registry for Per-App VPN Profile.
- Workspace ONE Tunnel Desktop Application Connectivity Troubleshooting.
- Confirming the Workspace ONE Tunnel status when Tunnel is connected.
- Confirming the Workspace ONE Tunnel status when Profile is not installed.
- Confirming Application Access and Tunnel Service.
- Checking the Workspace ONE Tunnel certificate.
- Enabling Workspace ONE Tunnel debug logging.
- Locating Workspace ONE Tunnel logs.
- Confirming Workspace ONE Tunnel DNS Resolution.
Troubleshoot Workspace ONE Tunnel Installation
In this section, check issues that may arise from the Workspace ONE Tunnel desktop client application installation.
- Check Workspace ONE UEM console for application install status.

- Navigate to the Details view of the device.
- Select the Apps tab.
- Confirm that the App Status for the Tunnel Installer is Installed.
- Confirm that the App Status for Workspace ONE Tunnel shows the correct version. In this example, Workspace ONE Tunnel 1.2.0.18 is installed.
- Locate Workspace ONE Tunnel desktop application installer logs.

By default, the Workspace ONE Tunnel Desktop Application Installer logs are found in %TEMP%.
Two logs should exist:- Workspace_ONE_Tunnel_<date>.log
- This is the Bootstrapper log which usually does not yield very important errors unless any dependency programs fail on install, for example, .NET.
- Workspace_ONE_Tunnel_<date>_000_OmnissaTunnelClientInstaller.log
- This is the Tunnel Installer log which shows any failures during the Workspace ONE Tunnel desktop application installation.
- Workspace_ONE_Tunnel_<date>.log
- Check device registry for Workspace ONE Tunnel install status.
Check the location of the registry installation settings for the Workspace ONE Tunnel desktop application. These values should match the values in the Workspace ONE UEM console.
On the computer that should have the Workspace ONE Tunnel desktop application installed, open the Windows Registry or runregedit.msc.
- Navigate to Computer > HKEY_LOCAL_MACHINE > SOFTWARE > AirWatchMDM > AppDeploymentAgent > S-1-5-18.
- Click the GUID of the application. For example,
{3A7FE2DB-8AE4-4DBA-A9D3-042C88F53A50}. - Click the Registry key to show IsInstalled.
Tip: The Application GUID should match the value in the Workspace ONE UEM Console.
- Confirm application ID in the Workspace ONE UEM console.

- In the Workspace ONE UEM console, navigate to Resources > and select the Workspace ONE Tunnel Application from List View.
- In the App Details View, the Application ID (GUID) should match the registry value in the previous screenshot.
For more information on troubleshooting Windows Applications, see Troubleshooting Windows Devices: Workspace ONE Operational Tutorial.
- Check Workspace ONE UEM console for policy install status.

After you have confirmed that the application is installed, make sure the policy is installed on the device.- In the Workspace ONE UEM console, navigate to the Details View of that device.
- Select the Profiles tab.
- Confirm that the Status of the Per App VPN Profile is successful.
- Check device registry for per-app VPN profile.
On the computer that should have the Tunnel policy installed, open the Windows Registry or runregedit.msc.
- Navigate to
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Omnissa\Omnissa Tunnel. - Click TunnelConfiguration.
- This displays the Tunnel Policy applied to that machine.
Tip: If no policy is shown in the registry, re-push the policy from the Workspace ONE UEM console and perform a Device Query on that device from the Workspace ONE UEM console.
- Navigate to
Troubleshoot Workspace ONE Tunnel Client Connectivity
After you have successfully installed the Workspace ONE Tunnel, the next step is to test the Per-App Tunnel connectivity by attempting to access one of the internal resources through the domains defined on the Device Traffic Rules.
- Confirm the Workspace ONE Tunnel status when Tunnel is connected.
- When the Tunnel Client has reached a successful connection, the Tunnel Client UI displays
Connected.
- When the Tunnel Client has reached a successful connection, the Tunnel Client UI displays
- Confirm Workspace ONE Tunnel status when profile is not installed.

- If the Workspace ONE Tunnel Client has installed, but the configuration settings have not, the Tunnel client status is
Not Configured.
Tip: To resolve, ensure the Per-App VPN profile is assigned to the device, and ensure it is successfully installed.
- If the Workspace ONE Tunnel Client has installed, but the configuration settings have not, the Tunnel client status is
- Confirm application access and Tunnel service.
- Problem: The Workspace ONE Tunnel Client status is
Disconnected. - Solution: Confirm that the Application is defined in Application Access and that the application is running.
- Problem: The Workspace ONE Tunnel Client status is
Disconnected. - Solution: Confirm that the Workspace ONE Tunnel Service is running in Windows Services. If the service is not started, start the service.
To check the Tunnel service:
- On the Windows machine, open Services and locate the Omnissa Workspace ONE Tunnel Service.
- Ensure that the Startup type is set to Automatic.
- Ensure that the Service is running.
- Check the Workspace ONE Tunnel desktop application certificate.
- Authentication for the Tunnel Client can be configured to use Enterprise Certificates or internally-signed certificates. If no certificate is present, the Tunnel UI status displays
Not Configured -Authentication Certificates are not present. - If there is no certificate present, you may want to push the policy again to the device. By re-pushing the policy, the Tunnel certificate should be installed.

- Authentication for the Tunnel Client can be configured to use Enterprise Certificates or internally-signed certificates. If no certificate is present, the Tunnel UI status displays
To check the certificates:
- On the Windows machine, search MMC, and open the Certificates snap in.
- Navigate to Local Computer > Personal > Certificates.
- Confirm that the certificate for certificate authentication to the Tunnel service is listed.
- Retrieve the device UDID from the Workspace ONE UEM console.
- Navigate to Devices > List View > Summary and confirm that the device UDID matches the Certificate request as shown in the previous screenshot.
- Enable Workspace ONE Tunnel debug logging.

- On the Windows machine, navigate to the system tray. You should see the Tunnel icon.
- Right-click the Tunnel client.
- Select Enable debug logging.
- Debug logging levels are from 0-4 - Enabling debug logging will set the log level to 4.
You can also check the Workspace ONE Tunnel log level in the device registry.
- On the computer that should have the Tunnel installed, open the Windows Registry or run
regedit.msc. - Navigate to Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Omnissa\Omnissa Tunnel.
- Under the LogLevel entry, you should see a value from 0-4. In this example, the value is 0.
- You cannot change the value in the registry. You must follow the steps to Enable Workspace ONE Tunnel Debug Logging.
- Locate Workspace ONE Tunnel logs.
- By default, the Workspace ONE Tunnel Client Installer logs are located in
C:\ProgramData\Omnissa\Omnissa Tunnel.
- By default, the Workspace ONE Tunnel Client Installer logs are located in
Two logs should exist:
- win_tunnel – This log file shows connectivity issues with the Workspace ONE Tunnel desktop application.

- win_tunnelui – This log file shows User Interface changes within the Workspace ONE Tunnel desktop application.

- Confirm Workspace ONE Tunnel desktop application DNS resolution.

After you have confirmed Tunnel connectivity, check the DNS resolution.
Sometimes, the Workspace ONE Tunnel Client may be in good working order. For example, the profile is installed, the application is installed, the service is running, and the status is Connected. However, the DNS resolution is still failing. In this case, general networking troubleshooting can assist greatly.
You can check the Name Resolution Policy Table (NRPT).
On the Windows machine, open PowerShell and enter Get-DnsClientNrptRule. This command retrieves the Name Resolution Policy Table (NRPT) for the device. For more information, see Microsoft PowerShell Docs - Get-DnsClientNrptRule.
Deploying Workspace ONE Tunnel for Android
Per-App Tunneling helps users to access critical information using applications on their devices from their devices. Mobile flows help users perform business-critical tasks from a single app — streamlining the user experience.
Leveraging Per-App Tunnel allows you to control which applications are on a device and what internal resources the applications have access to by automatically activating or deactivating Per-App VPN access, based on which applications are active. By enabling remote access, you no longer need to provide a device-wide VPN on your devices, which can allow unintended or unauthorized apps or processes to access your VPN. In this tutorial, you configure and deploy Workspace ONE Tunnel to enable the Per-App Tunnel component on managed devices.
These exercises involve the following components:
- Workspace ONE Tunnel – The app used on the device to securely connect to the Unified Access Gateway to provide Per-App Tunnel functionality, also referred to as Tunnel Client.
- Unified Access Gateway – The virtual appliance where the Tunnel edge service is installed, and to which the tunnel client connects.
- Per-App Tunnel – Component of Tunnel edge service for connecting to a secure tunnel channel on a per-application basis, which is controlled and configured by the VPN profile payload and Device Traffic Rules.
- Per-App VPN Profile and Device Traffic Rules – The Workspace ONE UEM configuration is pushed to the device that contains the Per-App Tunnel configurations. Every time a specified application is opened, the Workspace ONE Tunnel client evaluates the Device Traffic Rules assigned to it before making any routing decisions and establishes a Per-App tunnel connection with the Unified Access Gateway based on the Per-App VPN Profile configuration.
High-Level Architecture
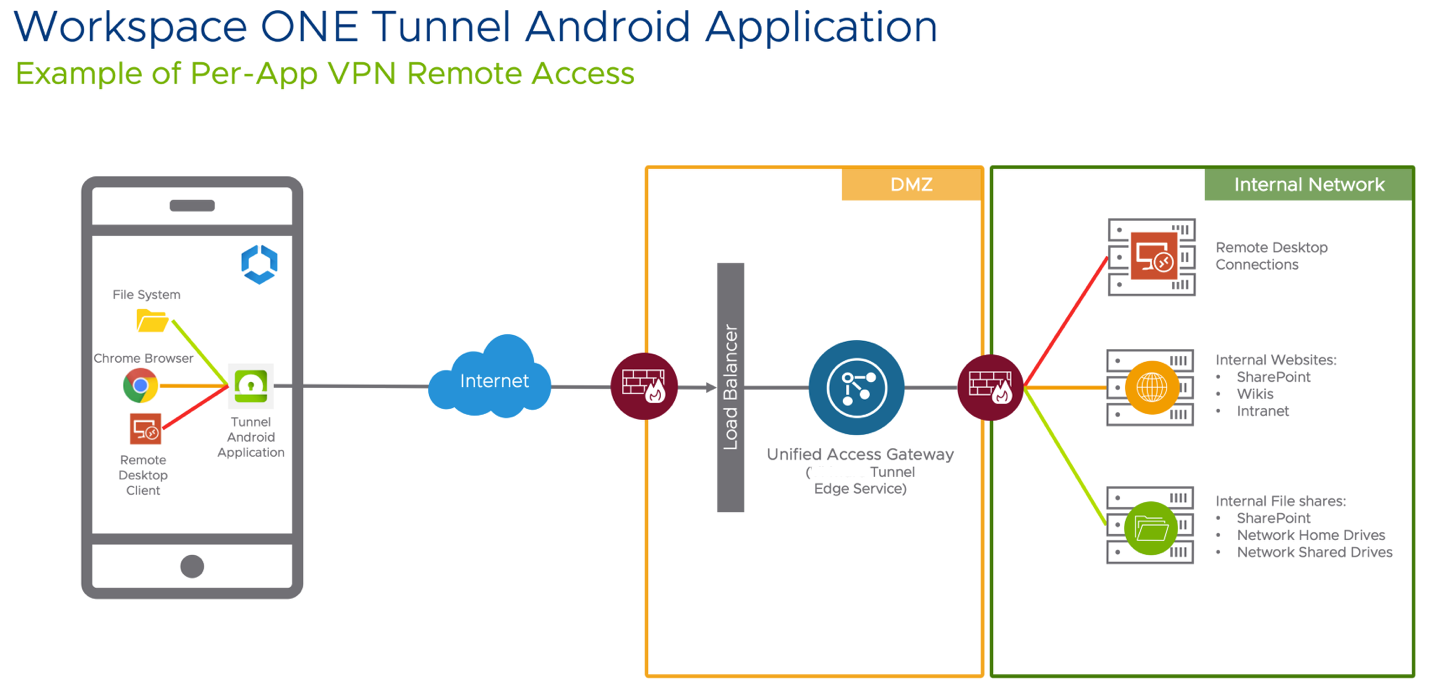
The device contains the applications required by the end-user to perform their daily job. Some applications require access to internal resources to function. Those applications, based on Per-App VPN configuration, use Workspace ONE Tunnel which communicates with the Tunnel Service on Unified Access Gateway hosted on the DMZ, to validate if the device requesting access is in compliance or not before authorizing access through the internal resource.
Prerequisites
Before you can perform the steps in this exercise, you must have the following components installed and configured:
- Workspace ONE UEM version 2203 and later
- Android 10.0+ enrolled in Workspace ONE UEM
- The latest version of Workspace ONE Tunnel app from the Google Play Store
- Deploy Workspace ONE Tunnel using Android Enterprise
Configuring Device Traffic Rules for Android
In this exercise, you configure device traffic rules for Android.
Note: Domain values used in this section are examples only. Your values will differ.
In the Workspace ONE UEM console:
- Navigate to Groups & Settings > Configurations.
- Select Tunnel.

- From the Device Traffic Rules tile, click Edit.
- Click Add or the Default assignment to manage the device traffic rules.

Administrators can create multiple Device Traffic Rules that will be assigned to the Per-APP VPN profile and will deploy to the devices based on the smart group assigned to the Profile. The first device traffic rule assignment created will be set as default. - Observe the default device traffic rule.

- Update the Assignment Name with the name of your choice.
- Observe (or modify) the default action which applies to all Android applications selected to use Per-App VPN:
- Tunnel – All apps, on the device configured for Per-App Tunnel send network traffic through the tunnel. For example, set the Default Action to Tunnel to ensure all configured apps without a defined traffic rule use the Workspace ONE Tunnel for internal communications.
- Block – Blocks all apps, on the device configured for Per-App Tunnel from sending network traffic. For example, set the Default Action to Block to ensure that all configured apps without a defined traffic rule cannot send any network traffic regardless of destination.
- Bypass – All apps, except Safari, on the device configured for Per-App Tunnel bypass the tunnel and connect to the Internet directly. For example, set the Default Action to Bypass to ensure all configured apps without a defined traffic rule bypass the Workspace ONE Tunnel to access their destination directly.
- Click ADD RULE.
- Build the device traffic rule.

- Click ADD RULE.
- Click the down arrow to display the Application list.
- Select one or more triggering applications to control with this rule. Alternatively, on the drop-down select All Applications to apply the rule to all Android applications listed in the drop-down, which are the ones that you assigned the Per-App VPN profile.
- Enter one or more comma-separated fully qualified domain names as destinations to which Workspace ONE Tunnel should apply the Device Traffic Rule. A single asterisk (*) can be used as a wildcard for subdomains.
- Select the Appropriate Action for Workspace ONE Tunnel to perform on traffic from the selected apps:
- Tunnel – Sends app network traffic for specified domains through the tunnel to your internal network.
- Block – Blocks all traffic sent to specified domains.
- Bypass – Bypasses the Workspace ONE Tunnel so the application accesses specified domains directly.
- Proxy – Redirect traffic to the specified HTTPS proxy for the listed domains. The proxy must be HTTPS and must follow the correct format:
https://example.com:port.
- If necessary, adjust the Device Traffic Rules rank in the list. Lower-numbered rank is the highest priority.
- Click Save.
The example shown blocks access to Facebook, Tinder, and Utorrent domains for all applications available on the Android device.
For more information on the formats (wildcards, IP, ports) allowed into the Destination field, see the Device Traffic Rules Destination formats supported chapter.
Distributing Workspace ONE Tunnel for Android
In this exercise, you deploy an application configured to use the Per-App VPN tunnel on Android.
- Click Add and click Public Application.

- Search for Workspace ONE Tunnel.

- Select Android for the Platform.
- Enter an application Name. For example,
Workspace ONE Tunnel. - Click Next.
- Select Tunnel – Workspace ONE Tunnel.

- Click Approve for the Workspace ONE Tunnel app and for any following requests.
- Click Save and Assign.
- Click Add Assignment.
- Configure Assignment settings.

- Click the Selected Assignment Groups field to display the list of created Assignment Groups. Enter
All Devices, and select the All Devices (your@email.shown.here) group. - Select Auto for the App Delivery Method.
- Click the Selected Assignment Groups field to display the list of created Assignment Groups. Enter
- Configure Policies.

- Scroll down to find the Policies section.
- Select Enabled for Managed Access.
- Click Add.
- Confirm that your assignment is displayed and click Save and Publish.

- Preview your assigned devices and click Publish.
Android Considerations
Note the following for Workspace ONE Tunnel on Android:
- After installing Workspace ONE Tunnel for Android, end users must run the application at least once and accept the connection request.
- The key icon in the notification center displays on the device because there is an application installed that uses the Per-App Tunnel functionality. This icon does not indicate an active connection or session with the Tunnel Service. The key icon displays even if you are not actively browsing.
- Certain Android devices allow end users to disable the VPN on an OS level. This prevents the Tunnel from working on the device.
Creating Per-App VPN Profile for Android
Per-App VPN profile allows you to force selected applications to connect through your corporate VPN. Your VPN provider must support this feature, and you must publish the applications as managed applications.
In this exercise, you create the Android profile which configures the Workspace ONE Tunnel client on the device to allow only designated applications to access content on internal servers.
Log in to the Workspace ONE UEM console to perform the next steps.
- Click Add and click Profile.
- Select Android.
- Configure the General settings.

- Select the General tab.
- Enter a Name, for example,
Per App VPN. - Select the name of your device's assignment group, and select that group. For example, select All MDM Enrolled Devices (ACME Corp) as the Assigned Smart Group.
- Add and configure VPN payload.

- Select VPN from the payload menu and click Configure.
- Select Workspace ONE Tunnel from the Connection Type drop-down menu.
- Select the Default traffic rule previously created for Device Traffic Rule Sets.
- Click Save & Publish.
- Click Publish to publish the VPN profile.
Configuring Workspace ONE Web for Per-App Tunnel
Workspace ONE Web is part of the secure productivity app suite from Workspace ONE UEM. Administrators can deploy Workspace ONE Web when data loss and copy/paste restrictions are critical to the business use case.
In this exercise, you distribute and configure Workspace ONE Web for Per-App Tunnel on Android.
- Add application.

- In the Workspace ONE UEM console, click Resources.
- Select Native under Apps.
- Select Public and click Add Application.
- Search for Workspace ONE Web on Google Play Store.

- Select Android for the Platform.
- Enter an application Name. For example,
Workspace ONE Web. - Click Next.
- Select Workspace ONE Web app and approve.

- Click Save and Assign.
- Click Add Assignment.
- Assign Per-App VPN profile to Workspace ONE Web.

- Select All Devices on Assignment Groups.
- Select Auto for App Delivery Method.
- Enable Managed Access.
- Enable App Tunneling
- On Android, select the Per-App VPN Profile that you previously created.
- Click Add.
- Click Save and Publish.
Testing Per-App Tunnel on Android
Now that the enrolled device has received the settings configured in the Workspace ONE UEM Console, you are ready to begin testing the Per-App Tunnel functionality. The applications assigned in the previous exercises should push down during enrollment. The Tunnel and Workspace ONE Web applications should be installed on your device.
In this exercise, launch Workspace ONE Web and access the internal website. Then verify that, although the VPN connection is active, other applications on the device are not able to access the tunnel or internal resources.
- Open Workspace ONE Tunnel.

Press the Home button on your device to return to the Launchpad. Swipe right to see the downloaded applications, if needed.
Tap the Workspace ONE Tunnel icon to launch the application. If prompted, select OK to allow Workspace ONE Web to send your device push notifications.
After the application has been opened, accept the privacy prompts and tap Continue.
Note: On Android, the Workspace ONE Tunnel Client must be launched once to silently route traffic for future occurrences. - Tap I Understand to accept the Privacy Prompt.
- Tap I agree to accept the Data Sharing Prompt.
- Confirm Tunnel connectivity.
After the Tunnel Client has been opened, you can see three areas.
- Device VPN Configuration
- The Profile or Policy that is delivered from Workspace ONE UEM. It shows a list of apps that will use the VPN Tunnel.
- Internet
- Displays whether the device has internet connectivity or not.
- Enterprise Server
- Displays whether the device has connectivity to the Tunnel edge service.
- Device VPN Configuration
- Launch Workspace ONE Web.

Press the Home button on your device to return to the Launchpad. Swipe right to see the downloaded applications, if needed.
Tap the Workspace ONE Web icon to launch the application. If prompted, tap OK to allow the Web to send your device push notifications. - Access the internal website with Workspace ONE Web.

- After the application launches, enter the URL for your intranet website, such as
https://atl-intranet-corp.airwlab.com. - Confirm that the VPN icon appears, indicating the connection is active. The application now connects to Workspace ONE UEM and retrieves the settings for your Organization Group.
- The website should load. In this example, it displays a Welcome message.
- Select and copy the internal URL. In the next step, you test entering this URL into another browser.
- After the application launches, enter the URL for your intranet website, such as
- Paste the URL into another browser.

- Open another browser, such as Chrome.
- Copy and paste the URL from the previous step.
- Confirm that only the defined applications can access internal resources.
Note: This example used a Work Managed Device. Work Managed devices provide separation from personal and corporate data. With Per-App Tunnel, you can isolate traffic to only those applications that need it rather than all corporate resources. This example shows Chrome inside the Work Profile attempting to access internal resources.
Troubleshooting Workspace ONE Tunnel on Android
If a Per-App Tunnel problem occurs on Android, you can check a number of places to troubleshoot. This section of the operational tutorial covers where to troubleshoot the Workspace ONE Tunnel client for Android at a high level.
Depending on the problem, there may be steps that should be performed on the Unified Access Gateway. However, troubleshooting the Unified Access Gateway is outside the scope of this tutorial.
Workspace ONE UEM administrators should contact our support for assistance when troubleshooting Per-App VPN, Workspace ONE Tunnel, or the Unified Access Gateway.
This section is divided into three parts and guides you through high-level steps to troubleshoot the Workspace ONE Tunnel installation and connectivity.
- Troubleshooting Device Connectivity
- This section displays where to search for Tunnel Client connectivity issues.
- Collecting logs automatically
- This step is useful for recreating issues and retrieving the Workspace ONE Tunnel Client log file.
- Advanced: Collecting logs manually on an Android Device
- This step is for advanced cases where you may need to see how the device's VPN stack is behaving. This step should be used only for test devices; it is not recommended to leave Developer Options turned on.
Troubleshoot Device Connectivity
- Open the Tunnel Application and tap the Diagnostics menu option.

- Any issues related to connectivity issues with the Tunnel server or a Proxy server are shown on the UI.

- Tap the email option in the upper-right corner to send these logs to your administrator.
Collect Logs Automatically
- Open the Tunnel Application and tap the Diagnostics menu option.
- Activate the Enable debug logs toggle.

- After the issue is reproduced, go to your internal storage and open the
AirWatchLogsfolder. - This folder contains a set of log files that, if required, can be shared with the Workspace ONE support teams.
Advanced: Collect Logs Manually on Android
- To collect logs manually, you must enable developer options on the mobile device.
- Navigate to Settings > About page on the device and tap the build number more than 7 times to enable developer options.
- Enable USB debugging in Settings > Developer Options.
- Connect the device via a USB cable to a laptop and install the device drivers.
- Check whether the device is getting detected in the laptop by running
adb devicesin the command prompt. The device should be listed with a Unique id. - adb is a tool part of the
android-sdkwhich you must download fromhttp://developer.android.com.
- Check whether the device is getting detected in the laptop by running
- After the device is detected (keep the device connected) run
adb logcat –v threadtime > TunnelLogs.log. Logs will continuously dump to the file. - After the issue is reproduced, logging can be stopped either by disconnecting the device or using Ctrl + c command.
- If required, share the
TunnelLogs.logwith the Workspace ONE support teams.
Summary and Additional Resources
This operational tutorial provided steps to leverage native Per-App Tunnel capabilities across mobile platforms, Android and iOS, and desktop platforms, macOS and Windows.
By publishing Per-App VPN profiles to your devices, you can ensure that only authorized apps are accessing authorized applications through the Tunnel. This eliminates the user requirement to manually start and end a network connection like traditional VPN solutions based on the apps they are accessing.
It also provides an extra layer of security to your corporate resources by ensuring that non-authorized apps are unable to connect to your VPN, creating the beginnings of a Zer- Trust model for application access.
Additional Resources
For more information about Workspace ONE, explore the Workspace ONE UEM product page on Tech Zone. You will find everything from beginner to advanced curated assets in the form of articles, videos, and labs.
Additionally, you can check out the Workspace ONE and Horizon Reference Architecture which provides a framework and guidance for architecting an integrated digital workspace using Workspace ONE and Horizon.
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2024-10-18 | Provide additional information on how Trust Network detection works. |
| 2024-10-10 | Update platform support for Workspace ONE Tunnel application. |
| 2024-05-29 | Update links and references to latest documentation. |
| 2024-04-04 | Updated platform support for Full Device mode on Managed Devices. |
| 2023-09-07 | Updated requirements for Workspace ONE UEM. Referenced new documentation links. |
| 2023-3-28 | Updated supported platform matrix for Workspace ONE Tunnel. Updated list of Custom XML Configuration for Windows Desktop. Updated requirements for Windows deployment. Added Windows 11 support. |
| 2022-12-05 | Updated the Trust Network Detection chapter: added DNS resolution details when Trust Network Detection is enabled. Updated platform support and features availability matrix. Added details on the new Device Traffic Rules sync process for Android. |
| 2021-07-09 | Updated the Device Traffic Rules chapter adding a detailed explanation of default action rule per platform. Added supported custom configuration parameters for Windows 10. Added details for Trusted Network Detection based on probe URL. |
| 2021-06-30 | Updated Device Traffic Rules with an explanation about the new Full Device Tunnel Mode. Added Device Traffic Rules Guidelines for use of the asterisk, IP, and port range. Added steps to deploy Workspace ONE Tunnel for iOS as Public App (App Store) using Workspace ONE UEM. |
| 2020-11-13 | Added Trusted Network Detection chapter. Updated Device Traffic Rules topic, adding support to manage traffic assignments based on multiple Device Traffic Rules sets. Update Profile configuration for all platforms to support device traffic rule configuration via profile. |
| 2020-3-26 | Added Windows, Android, and macOS Platforms. Edited iOS Platform. |
About the Author and Contributors
This tutorial was written by:
- Andreano Lanusse, Omnissa alumni.
Feedback
Your feedback is valuable.
To comment on this paper, either use the feedback button or contact us at tech_content_feedback@omnissa.com.