Zero Trust in real time
Introduction
Cybersecurity has always been designed with an ‘under a lock-and-key', or moat around the castle mentality. However, in today’s fluid and supply-chain driven risk mitigation realm, the focus on perimeter defenses only ensure that external malicious actors are kept at bay. Unfortunately, these malicious actors are sometimes provided golden keys that land them directly inside the castle without having to fight a single knight or archer. That's where we find ourselves typically in today’s world of interwind supply chain and ecosystem of both custom and OpenSource software distribution, and with the current Apache Log4j vulnerability & Log4Shell Exploitation (as represented in Figure 1 above), providing us a zero-trust in real-time exercise in action at a global scale!
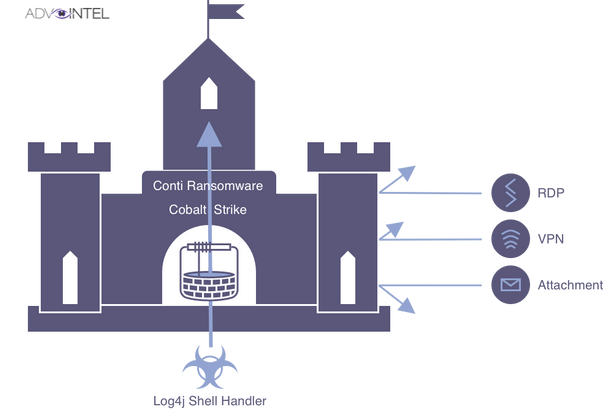
Figure 1: Log4j She'll Handler Infographic (Source Credit: AdvIntel)
Purpose
Audience
This Whitepaper is intended for IT and Cybersecurity administrators and product evaluators who are familiar with Omnissa Workspace ONE and Omnissa Horizon. Familiarity with networking and security practices, such as identity management and endpoint protection is assumed. Knowledge of other technologies, such as Virtual Private Network (VPN) and specific Omnissa solutions including Workspace ONE Intelligence, Access and is also helpful.
Background
Apache’s Log4j is a widely-used, open-source logging library utility exists in the action of the Java Naming and Directory Interface (JNDI), which takes to resolve variables embedded within numerous cloud and enterprise apps including numerous popular cloud-hosted services of the likes of Minecraft, iCloud, Cloudflare and Twitter, to track software activity. affecting Apache’s Log4j library, versions 2.0-beta9 to 2.14.1 (and subsequently versions 2.15>16 as well).
"A weakness in the computational logic (e.g., code) found in SW / HW components that, when exploited, results in a negative impact to CIA-triad e.g. confidentiality, integrity, or availability. Mitigation of the vulnerabilities in this context typically involves coding changes but could also include specification changes or even specification deprecations (e.g., removal of affected protocols or functionality in their entirety)."
And, with the deep ubiquity and integration within these hosting services and servers and Apache tool makes the extent of this zero-day’s potential damage likely wide-reaching and is likely to affect hundreds of millions of devices. Worst, it didn’t take a week to find that not only was there an original vulnerability for which an exploitation could be leveraged for a rogue Command & Control in the distribution of malware or exfiltration of data etc... there was also the risk of a Denial of Service (DoS) attack vector for affected servers/services as well documented in a separate but tangible CVE-2021-45046.
Later, a ‘third’ CVE which was released as well: CVE-2021-45105 with a base CVSS Score of 7.5. The Apache Software Foundation's log4j project then disclosed the new vulnerability identified by CVE-2021-45105; and expressed their belief that this flaw seems to be a non-critical DoS-only as was the 2nd vulnerability, which is much tighter in scope for attack vectors than the previous 2 vulnerabilities.
- In comments made this previous week, shortly after the Zero-Day release, CISA expected all kinds of attackers to exploit the vulnerability, from cryptominers to ransomware and nation-state actors/groups. CISA’s Director told industry leaders Monday that along with the vulnerability (VUL) and scope, among other factors, makes the ranking among vulnerabilities as "one of the most serious I've seen in my career, if not the most serious. “At the time, there was no evidence of an active of supply-chain attack…”
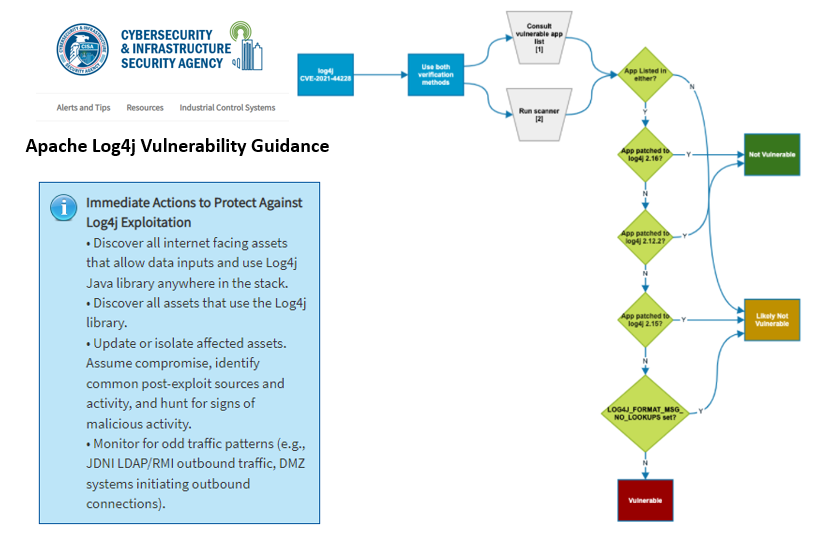
Figure 2: CISA Log4j Guidance Infographic
Reflective of this dialogue and through actualization of the current expanding scope and spiraling escalation of these vulnerabilities, CISA and its partners, through the ‘Joint Cyber Defense Collaborative’ in response, also created a rare, specific webpage (see summary above), to track updates for Apache’s Log4j vulnerability and an updated resource to provide guidance and will actively maintain a community-sourced GitHub repository of publicly available tools, including a scanner and vendor-supplied advisories regarding the Log4j vulnerability. CISA provided continual updates for both of those webpages and the GitHub repository. They’ve also included an updated government-wide Emergency Directive (ED 22-02) directing federal agencies to mitigate the Apache Log4j vulnerability.
Situation
Setup
Below is the situational setup of the Log4j vulnerability:
- The Common Vulnerabilities & Exposures (CVE) rating for this event was a ’10.0’ out of 10 <and> what started as a 3.7 ramped up to a 9.0 within a week for the secondary CVE respectively and now a 3rd rated at 7.5.
- Continued potential for additional follow-on CVEs related to the original vulnerability (e.g. 2nd and now 3rd CVE related to Log4j) was ‘high’.
- Not only did it provide a level of numeric scale to the severity of the issue, but also the speed in which it changed dynamically, and thus the criticality of the problem facing the overall community at large.
Scope
Below is the situational scope of the Log4j vulnerability:
- Apache’s service was and still is very broadly used in a variety of consumer and enterprise services, websites, and applications including numerous popular cloud-hosted services of the likes of Apple’s iCloud, Minecraft, Cloudflare and Twitter—as well as, in operational technology (OT) products—to log security and performance information:
- An unauthenticated remote actor could exploit this vulnerability to take control of an affected system and provide them a C2 e.g. malware / phishing campaigns or simply exfiltration e.g. $ or info
- The 2nd flaw has been found in the same logging utility, one that could crash websites & serve as a DoS
Actions
Below is the situational actions required from the Log4j vulnerability:
- Scale to find what apps have vulnerable versions of Log4j
- Discover which apps have the vulnerability
- Halt attacks against it today, don’t wait for a patch or WAF signature updates, and lastly…
- Future-proof your code and protect against the zero-day vuls as they come to pass
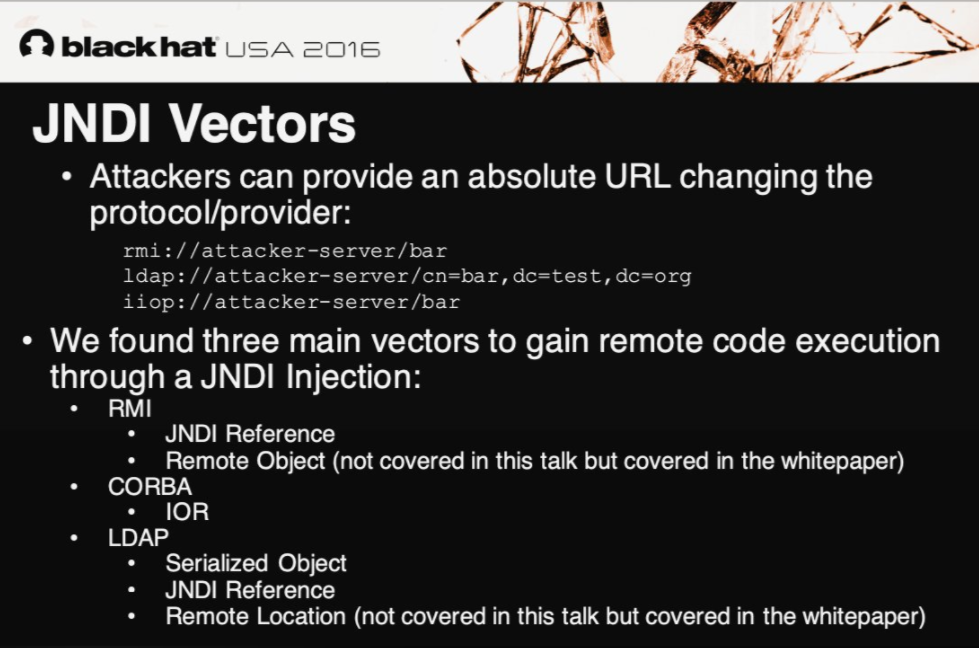
Figure 3: Source Credit: Black Hat USA Infographic
Solution: Zero Trust the next Battlefield

Figure 3: Source Credit: Black Hat USA Infographic
Setup: Battlefield
- Breadth & Depth; unknown, undocumented and unseen? This had been in making for years…
- How long must you play on a given battlefield?! This issue will be around for some time, as are other vulnerabilities and their malicious variants and actors developing against them ex. Mirai / SolarWinds / Spectre-Meltdown
Scope: Land & Expand
- Where’s the beachhead? How do you stop an attack that is already inside your walls, within your fabric of operations and doesn’t need sophisticated threat actor involvement?
- How quickly is the next Cyber / supply chain or infrastructure attack going to take this time?
Action: Campaign
- In the initial hours, CISA and others tracking this had not identified any ‘active campaigns
- Within days, several campaigns have already been detected in the wild ex. several were putting ransomware and remote-access-Trojans on Windows machines with Java installed.
- Malicious actors will continue to sequence the vulnerability as detailed via MITRE’s cyber threat actor’s tactics and techniques as represented below.
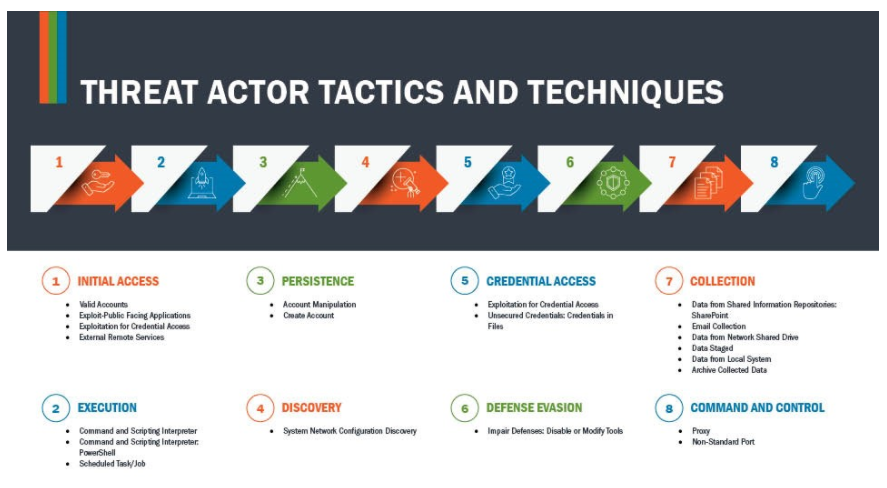
Figure 4: MITRE’s cyber threat actor T&Ts Infographic
Solution: Zero Trust Resilience
How does the protection and mitigation work in taking aim at futureproofing against the incarnation of the next versions of a Log4j vulnerability and attack? By deploying a sound set of Zero Trust Architecture foundations that can start with levels of existing controls and expanding to include more advanced features as defined in the Zero Trust Maturity Model (ZTMM) that can help organizations reference as they transition towards a ZTA. The maturity model aims to assist all orgs in the development of zero trust strategies and implement plans to present ways malicious actors can attack them.
Zero Trust Tenets/Pillars (deployed at every level):
- Because Zero Trust assumes that the exploiter is already inside the perimeter, a supply chain exploit can go after this vulnerability from the inside, gaining Remote Code Execution (RCE) in the logging asset, with its privilege; thus, data isolation and segmentation is crucial along with new dynamic security controls.
Granular Isolation (e.g. microservice, container, app), data):
- Limit the compromised behavior to only intended, tested aspects with least privilege & least capability actions available to the least amount of data.
Continuous Enforcement (on ‘every transaction’):
- Exploit will need to mirror the allowed actions of the component only, without any access to the policy, guessing right at every move, for every hop; thus, dynamic conditional access policies are needed at all phases.
Inline & Realtime Verification:
- Any anomalous action outside of those intentions would be blocked that would be blocked by continuous enforcement and verification, at a point outside of the component failure domain.
Universal Coverage & End-to-End Coverage:
- All subjects and objects are identified and access restricted, so many malicious behaviors will be disallowed.
Exploitation of App Workloads/Services Limitation:
- Similarly, unlike the many exploits with specific mitigations that are being discussed right now in the industry, it is important to remember that remediation, and the speed of that remediation in the forms of detection and response will be paramount under the concept that it isn't if, but when a breech will occur.
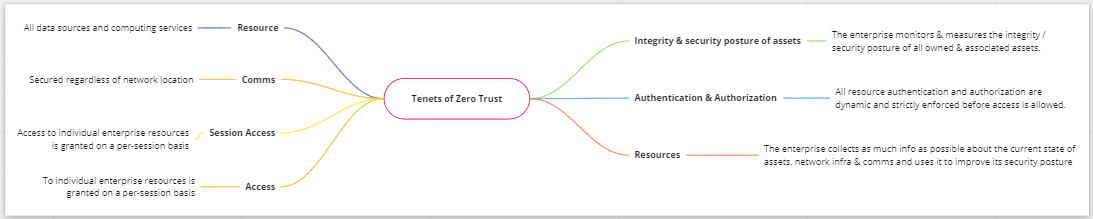
Figure 5: The seven ZT Tenets from NIST SP 800-207 ZTA
Implementation: Zero Trust
- Unified Management:
- Streamline device management, ensuring uniform policies across all platforms from traditional windows systems to iOS, Android or ChromeOS based.
- Manage a broad range of operating systems, from iOS, Android, ChromeOS to Mac OS, Windows, WinServer, and Linux-based systems, through a single, intuitive admin console.
For more information see: Omnissa Workspace ONE on TechZone
- Access Controls:
- Provide conditional access policies to apply policies restricting access based on a large host of environmental data, while ensuring control of your data only from trusted users, in trusted locations, on trusted devices.
- Leverage role-based access controls (RBAC) to tailor permissions based on geographic function, role, and location.
For more information see:
Zero Trust Secure Access to Traditional Apps thru Omnissa <and>
- Identity Management:
- Assist Identity Management (IdM) with Identity Providers (IdPs) by integrating Omnissa’s identity broker solution - Workspace ONE Access for both traditional and mobile platforms.
- Leverage Workspace ONE Access to provide authentication and authorization policies to enforce conditional access, as well as provide a layer of passwordless and phishing-resistance.
For more information see: Omnissa Access on Tech Zone
- Advanced Security Measures:
- Utilize FIPS 140-2 validated modules for enhanced device security, including AES 256-bit Data-at-Rest (DaR) and TLS 1.3 for Data-in-Transit (DiT).
- Employ an automated compliance engine to enforce security settings tailored to specific functions.
For more information see: Omnissa Security & Compliance on Tech Zone
- Scalable Architecture:
- Support a multi-tenant architecture capable of scaling with your organization's needs.
- Ensure seamless management and distribution of both internal and public apps for official use.
For more information see: Omnissa Workspace ONE & Horizon Architecture on Tech Zone
- Comprehensive Data Protection:
- Maximize data loss prevention (DLP) and secure content collaboration.
- Encrypt and containerize email communications, providing a secure alternative to native email clients.
For more information see: Workspace ONE UEM Mgmt Modes on Tech Zone
- Intelligence
- Dashboards
- Reporting
- AI learning of baselines.
For more information see: Workspace ONE Intelligence on Tech Zone
Summary and Additional Resources
Summary
The value of built-in resilience is as a ‘complement’ to the rest of security! The aim and goal should be preserving security resiliency during times of zero-day notification, through exploitation activities and the advancements or updated versions of attacks from the vector by deploying these Zero Trust framework based on NIST’s 7 tenets, strategies, and tools of Zero Trust that extend through the CISA pillars and the Zero Trust Maturity Model (ZTMM). At Omnissa, we have a three-pronged approach to mitigate endpoint security challenges by:
- Enabling Risk-based Secure Access by mitigating endpoint risk with a proactive remediation within conditional access implementation
- Building a smart and extensible platform capable of enhancing endpoint compliance and device remediation scope and speed
- Accelerating information sharing with integrated partner’s solutions to reduce exposure
Additional Resources
And for further Zero-Trust assets on Tech Zone, see:
- Workspace ONE UEM Architecture
- Omnissa Access Architecture
- Omnissa Access Architecture
- Workspace ONE Assist Architecture
- Zero Trust Regulation and Framework
- Omnissa TechZone Public Sector Portal
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2024/11/22 |
|
| 2022/09/08 |
|
About the Author and Contributor
The following people contributed their knowledge and assistance with this document:
- Andrew Osborn, Omnissa alumni.
Feedback
Your feedback is valuable.
To comment on this paper, contact Omnissa at tech_content_feedback@omnissa.com.

