Workspace ONE and Horizon reference architecture overview
This chapter is one of a series that make up the Omnissa Workspace ONE and Horizon Reference Architecture, a framework that provides guidance on the architecture, design considerations, and deployment of Omnissa Workspace ONE and Omnissa Horizon solutions. This chapter includes an executive summary, information about reference architectures, an overview of Workspace ONE and Horizon, architectural overviews and diagrams, general multi-site best practices.
In subsequent chapters of this book, design guidance is given for each product—with a corresponding architecture chapter devoted to each product—followed by best practices for integrating the components into a complete platform. For validation, we built an example environment.
Throughout this book, we listed the design decisions made for this example environment, along with the rationale for each decision and descriptions of design considerations.
Executive summary
Use this reference architecture as you build services to create an integrated digital workspace that addresses your unique business requirements and use cases. You will integrate the components of Workspace ONE and Horizon, as required, including Workspace ONE Unified Endpoint management (UEM), Workspace ONE Intelligence, Horizon 8, and Horizon Cloud Service.
Workspace ONE combines identity and mobility management to provide frictionless and secure access to all the apps and data that employees need to do their work, wherever, whenever, and from whatever device they choose. Additionally, Workspace ONE integrates with Horizon virtual desktops and published applications delivered through Horizon 8 and Horizon Cloud Service. This integration provides fast single-sign-on (SSO) access to a Windows desktop or set of Windows applications for people who use the service.

Figure 1: User workspace with Workspace ONE
The example architecture and deployment described in this guide address key business drivers. The approach taken is, as with any technology solution, to start by defining those business drivers and then identify use cases that need to be addressed. Each use case will entail a set of requirements that need to be fulfilled to satisfy the use case and its respective business drivers.
Once the requirements are understood, the solutions can be defined, and blueprints outlined for the services to be delivered. This step allows you to identify and understand the products, components, and parts that need to be designed, built, and integrated.
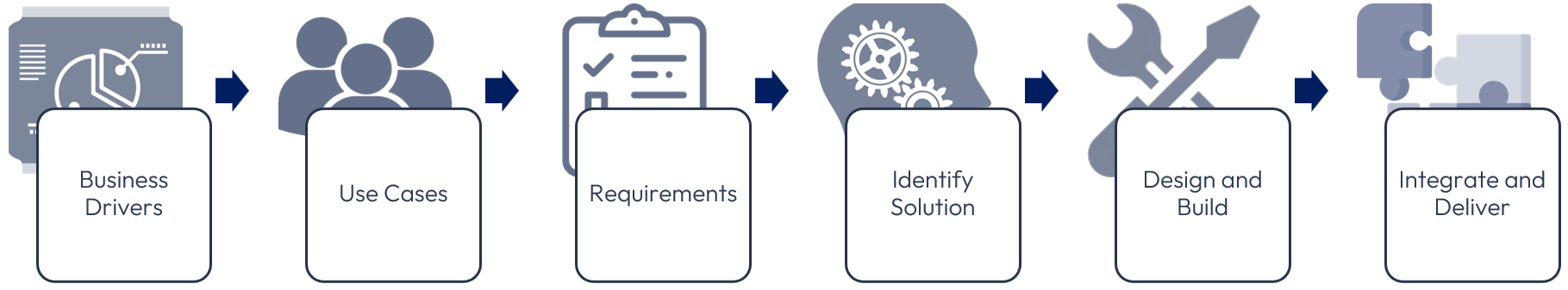
Figure 2: Design approach
To deliver a Workspace ONE and Horizon solution, you build services efficiently from several reusable components. This modular, repeatable design approach combines components and services to customize the end-user experience without requiring specific configurations for individual users. The resultant environment and services can be easily adapted to address changes in the business and use case requirements.
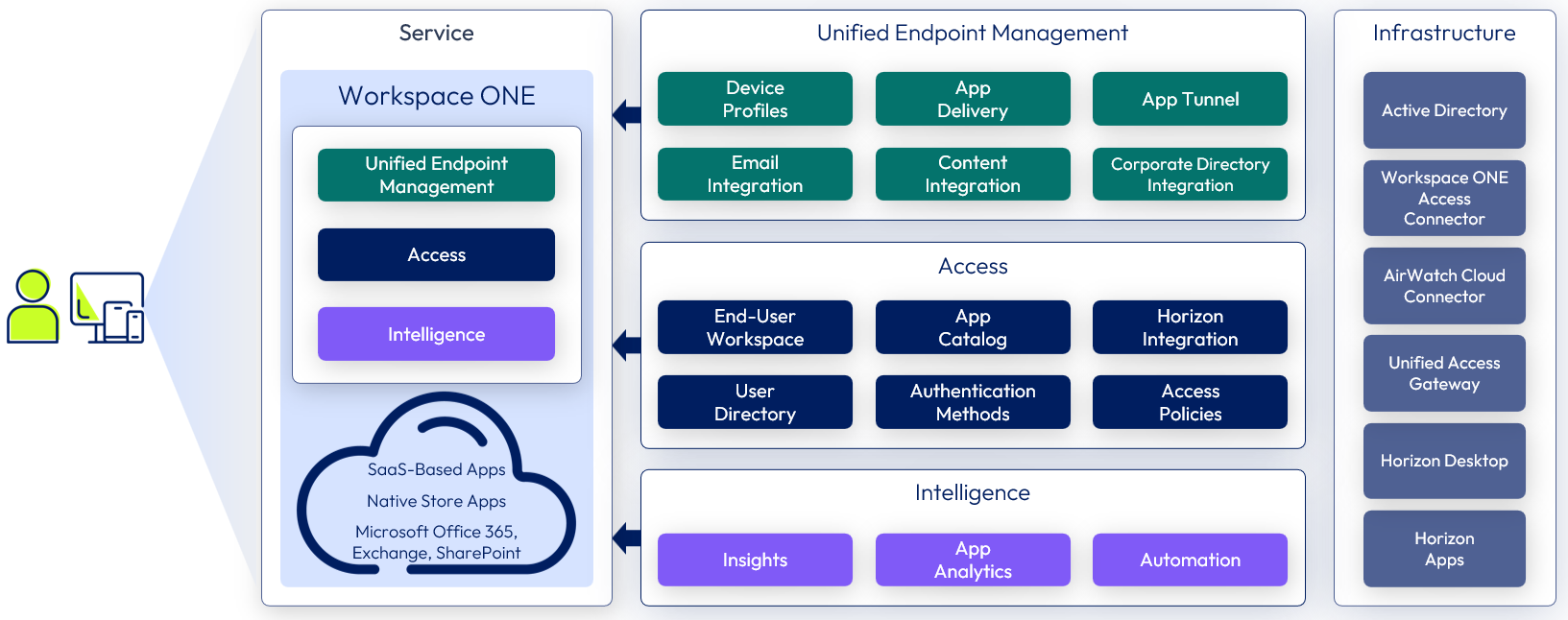
Figure 3: Sample service blueprint
This reference architecture underwent validation of design, environment adaptation, component and service build, integration, user workflow, and testing to ensure that all the objectives were met, that the use cases were delivered properly, and that real-world application is achievable.
This Workspace ONE and Horizon Reference Architecture illustrates how to architect and deliver a modern digital workspace that meets key business requirements and common use cases for the increasingly mobile workplace, using Workspace ONE and Horizon.
Reference architectures
The Omnissa reference architectures are designed and validated to address common use cases, such as enterprise mobility management, enterprise desktop replacement, remote access, and disaster recovery.
This Omnissa Workspace ONE and Horizon reference architecture is a framework intended to provide guidance on how to architect and deploy Omnissa Workspace ONE and Omnissa Horizon solutions. It presents high-level design and low-level configuration guidance for the key features and integration points of Workspace ONE and Horizon. The result is a description of cohesive services that address typical business use cases.
Our reference architectures offer customers:
- Standardized, validated, repeatable components
- Scalable designs that allow room for future growth
- Validated and tested designs that minimize implementation and operational risks
- Quick implementation and reduced costs
This reference architecture does not provide performance data or stress-testing metrics. However, it does provide a structure and guidance on architecting in repeatable blocks for scale. The principles followed include the use of high availability and load balancing to ensure that there are no single points of failure and to provide a production-ready design.
Audience
This reference architecture helps IT architects, consultants, and administrators involved in the early phases of planning, designing, and deploying Workspace ONE, Horizon 8, and Horizon Cloud Service solutions.
You should have:
- A solid understanding of the mobile device landscape
- Deep experience regarding the capabilities and configuration of mobile operating systems
- Familiarity with device-management concepts
- Knowledge of identity solutions and standards, such as SAML authentication
- Understanding of enterprise communication and collaboration solutions, including Microsoft Office 365, Exchange, and SharePoint
- A good understanding of virtualization, in particular any platform used to host services.
- A solid understanding of desktop and application virtualization
- A solid understanding of firewall policy and load-balancing configurations
- A good working knowledge of networking and infrastructure, covering topics such as Active Directory, DNS, and DHCP
Design methodology
To ensure a successful Workspace ONE and Horizon deployment, it is important to follow proper design methodology. To start, you need to understand the business requirements, reasons, and objectives for undertaking the project. From there, you can identify the needs of the users, and organize these needs into use cases with understood requirements. Highlighting the technical details to deliver a distinct use case, such as OS platform and persona, allows you to define a particular scenario for a distinct use case.
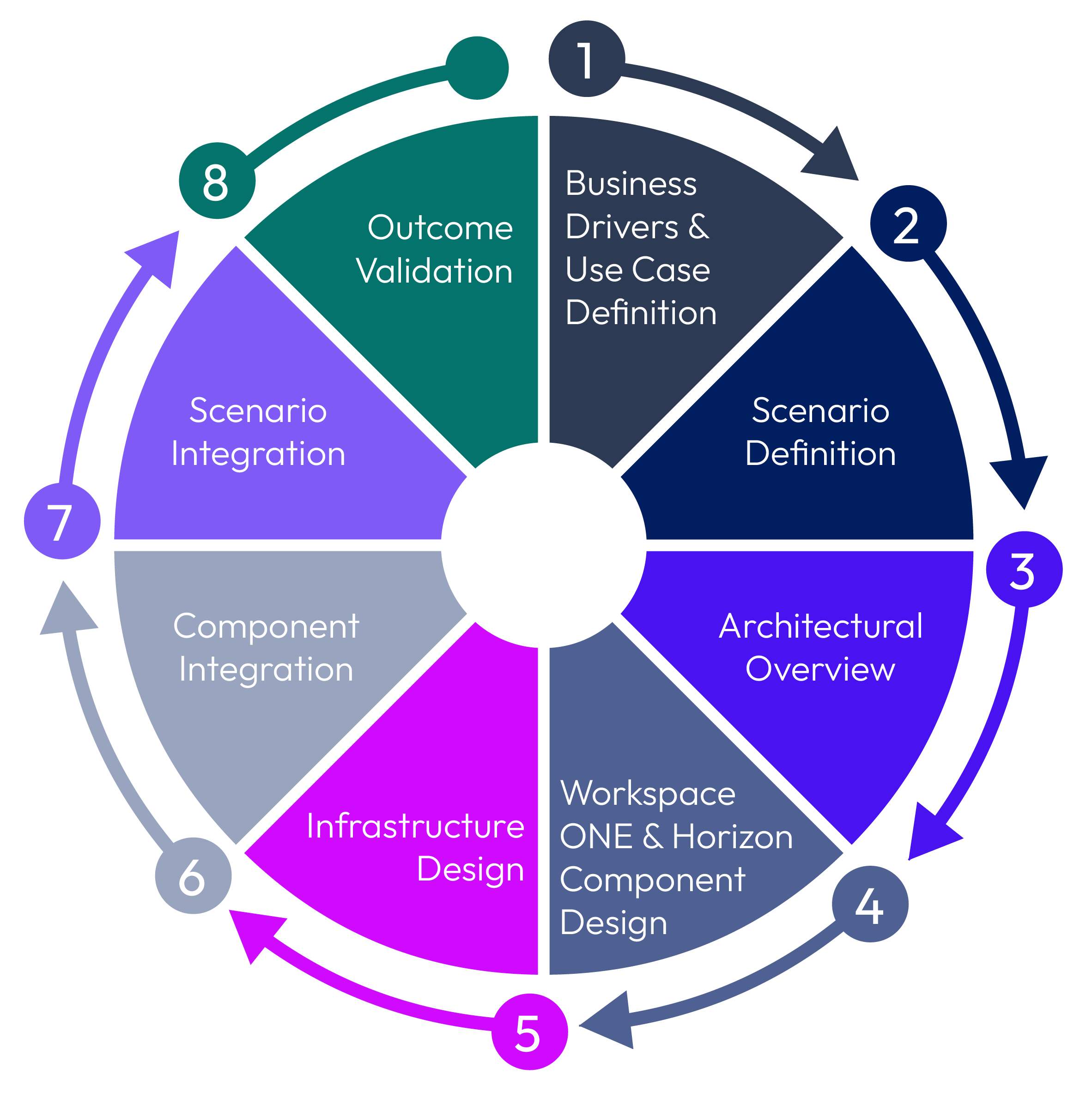
Figure 4: Reference architecture design methodology
A Workspace ONE and Horizon design uses a number of components to provide the services that address the identified use cases and scenarios. Before you can assemble and integrate these components to form a service, you must first design and build the components in a modular and scalable manner to allow for change and growth. You also must consider integration into the existing environment. Then you can bring the parts together to deliver the integrated services to satisfy the scenarios, use cases, business requirements, and the user experience.
As with any design process, the steps are cyclical, and any previous decision should be revisited to make sure a subsequent one has not impacted it.
Design decisions
As part of the creation of this reference architecture, full environments are designed, built, and tested. Throughout the chapters of this book, design decisions are listed that describe the choices we made for our implementation.
Table 1: Design Decision Regarding the Purpose of This Reference Architecture
| Decision | Full production-ready environments were architected, deployed, and tested. |
| Justification | This allows the content of this guide, including the design, deployment, integration, and delivery, to be verified, validated, and documented. |
Each implementation of Workspace ONE and Horizon is unique and will pose distinct requirements. The implementation followed in this reference architecture tries to address the common use cases, decisions, and challenges that need to be addressed in a manner that can be adapted to differing circumstances.
Workspace ONE and Horizon overview
Workspace ONE is a simple and secure enterprise platform that delivers and manages any app on any device. Workspace ONE integrates identity, application, and enterprise mobility management while also delivering feature-rich virtual desktops and applications. The platform is composed of several components— Workspace ONE UEM, Workspace ONE Access, Horizon, and the Workspace ONE productivity apps, which are supported on most common mobile platforms.
Workspace ONE
Workspace ONE features provide enterprise-class security without sacrificing convenience and choice for end users:
- Real-time app delivery and automation – Taking advantage of new capabilities in Windows, Workspace ONE allows desktop administrators to automate application distribution and updates. This automation, combined with virtualization technology, helps ensure application access as well as improve security and compliance. Provision, deliver, update, and retire applications in real time.
- Self-service access to cloud, mobile, and Windows apps – After end users are authenticated through either the Workspace ONE Intelligent Hub app, they can instantly access mobile, cloud, and Windows applications with one-touch mobile single sign-on (SSO).
- Choice of any device, employee or corporate owned – Administrators can facilitate adoption of bring-your-own-device (BYOD) programs by putting choice in the hands of end users. Give the level of convenience, access, security, and management that makes sense for their work style.
- Device enrollment – The enrollment process allows a device to be managed in a Workspace ONE UEM environment so that device profiles and applications can be distributed and content can be delivered or removed. Enrollment also allows extensive reporting based on the device’s check-in to the Workspace ONE UEM service.
- Adaptive management – For some applications, end users can log in to Workspace ONE and access the applications without first enrolling their device. For other applications, device enrollment is required, and the Workspace ONE app can prompt the user to initiate enrollment.
Administrators can enable flexible application access policies, allowing some applications to be used prior to enrollment in device management, while requiring full enrollment for apps that need higher levels of security.
- Conditional access – Both Workspace ONE Access and Workspace ONE UEM have mechanisms to evaluate compliance. When users register their devices with Workspace ONE, data samples from the device are sent to the Workspace ONE UEM cloud service on a scheduled basis to evaluate compliance. This regular evaluation ensures that the device meets the compliance rules set by the administrator in the Workspace ONE UEM Console. If the device goes out of compliance, corresponding actions configured in the Workspace ONE UEM Console are taken.
Workspace ONE Access includes an access policy option that administrators can configure to check the Workspace ONE UEM server for device compliance status when users sign in. The compliance check ensures that users are blocked from signing in to an application or using SSO to the Workspace ONE Access self-service catalog if the device is out of compliance. When the device is compliant again, the ability to sign in is restored.
Actions can be enforced based on the network that users are on, the platform they are using, or the applications being accessed. In addition to checking Workspace ONE UEM for device compliance, Workspace ONE Access can evaluate compliance based on network range of the device, type of device, operating system of the device, and credentials.
- Unified application catalog – The Workspace ONE Access and Workspace ONE UEM application catalogs are combined and presented on either the Workspace ONE app’s Catalog tab or the Workspace ONE Intelligent Hub app, depending on which is being used.
- Secure productivity apps - Workspace ONE Boxer, Web, Content, People, and PIV-D Manager – End users can use the included mail, calendar, contacts, browser, content, organization, and authentication capabilities, while policy-based security measures protect the organization from data leakage by restricting the ways in which attachments and files are edited and shared.
- Mobile SSO – One-touch SSO technology is available for all supported platforms. The implementation on each OS is based on features provided by the underlying OS. For iOS, one-touch SSO uses technology known as the key distribution center (KDC). For Android, the authentication method is called mobile SSO for Android. And for Windows 10, it is called cloud certificate.
- Secure browsing – Using Workspace ONE Web instead of a native browser or third-party browser ensures that access to sensitive web content is secure and manageable.
- Data loss prevention (DLP) – This feature forces documents or URLs to open only in approved applications to prevent accidental or purposeful distribution of sensitive information.
- Resource types – Workspace ONE supports a variety of applications exposed through the Workspace ONE Access and Workspace ONE UEM catalogs, including SaaS-based SAML apps, Horizon apps and desktops, Citrix virtual apps and desktops, ThinApp packaged apps delivered through Workspace ONE Access, and native mobile applications delivered through Workspace ONE UEM.
Workspace ONE platform integration
Workspace ONE UEM delivers the enterprise mobility management portion of the solution. Workspace ONE UEM allows device enrollment and uses profiles to enforce configuration settings and management of users’ devices. It also enables a mobile application catalog to publish public and internally developed applications to end users.
Workspace ONE Access provides the solution’s identity-related components. These components include authentication using username and password, two-factor authentication, certificate, Kerberos, mobile SSO, and inbound SAML from third-party Workspace ONE Access systems. Workspace ONE Access also provides SSO to entitled web apps and Windows apps and desktops delivered through either Horizon or Citrix.
Workspace ONE Intelligence
Workspace ONE Intelligence is a service that gives organizations visualization tools and automation to help them make data-driven decisions for operating their Workspace ONE environment.
By aggregating, analyzing, and correlating device, application, and user data, Workspace ONE Intelligence provides extensive ways to filter and reveal key performance indicators (KPIs) at speed and scale across the entire digital workspace environment. After information of interest has been surfaced by Workspace ONE Intelligence, IT administrators can:
- Use the built-in decision engine to create rules that take actions based on an extensive set of parameters.
- Create policies that take automated remediation actions based on context.
With Workspace ONE Intelligence, organizations can easily manage complexity and security without compromising a great user experience.
Horizon 8
Horizon 8 offers simplicity, security, speed, and scale in delivering on-premises virtual desktops and applications with cloud-like economics and elasticity of scale.
Horizon 8 allows components of a desktop or RDSH server to be decoupled and managed independently in a centralized manner yet reconstituted on demand to deliver a personalized user workspace when needed. Horizon 8 is supported with both on-premises and cloud-based Horizon deployments, providing a unified and consistent management platform regardless of your deployment topology. This approach provides several key benefits, including simplified desktop and RDSH image management, faster delivery and maintenance of applications, and elimination of the need to manage “full persistent” desktops.
- Just-in-Time Desktops – Leverages Instant Clone Technology coupled with App Volumes to accelerate the delivery of user-customized and fully personalized desktops. Dramatically reduce infrastructure requirements while enhancing security by delivering a brand-new personalized desktop and application services to end users every time they log in.
- Reap the economic benefits of stateless, nonpersistent virtual desktops served up to date upon each login.
- Deliver a pristine, high-performance personalized desktop every time a user logs in.
- Improve security by destroying desktops every time a user logs out.
- App Volumes – Provides real-time application delivery and management.
- Quickly provision applications at scale.
- Dynamically attach applications to users, groups, or devices, even when users are already logged in to their desktop.
- Provision, deliver, update, and retire applications in real time.
- Provide a user-writable volume, allowing users to install applications that follow them across desktops.
- Dynamic Environment Manager – Offers personalization and dynamic policy configuration across any virtual, physical, and cloud-based environment.
- Provide end users with quick access to a Windows workspace and applications, with a personalized and consistent experience across devices and locations.
- Simplify end-user profile management by providing organizations with a single and scalable solution that leverages the existing infrastructure.
- Speed up the login process by applying configuration and environment settings in an asynchronous process instead of all at login.
- Provide a dynamic environment configuration, such as drive or printer mappings, when a user launches an application.
For more information, see Horizon 8.
Horizon Cloud Service
Horizon Cloud Service- next-gen delivers virtualized desktops and apps to just about any endpoint device you can think of. Devices can include Windows, Mac, and Linux desktop computers and laptops, Chromebooks, tablets, smartphones, and thin and zero clients. The difference is that Horizon Cloud – next-gen is a cloud-based managed service, that delivers and maintains all the critical management tools used in a Desktops-as-a-Service (DaaS) deployment for use with your choice of capacity, from on-premises platforms, or cloud-based infrastructure platforms.
For more information, see Horizon Cloud Service.
Architectural overview
A Workspace ONE design uses several complementary components and provides a variety of highly available services to address the identified use cases. Before you can assemble and integrate these components to form the desired service, you first need to design and build the infrastructure required.
The components in Workspace ONE, such as Workspace ONE Access, Workspace ONE UEM, and Horizon are available as on-premises and cloud-hosted products.
For this reference architecture, both cloud-hosted and on-premises Workspace ONE UEM and Workspace ONE Access are used separately to prove the functionality of both approaches. These are shown in the cloud-based and on-Premises logical architecture designs described in this chapter.
Note that other components, such as Horizon 8 or Horizon Cloud Service, can be combined with either a cloud-based or an on-premises Workspace ONE deployment.
Workspace ONE logical architecture
The Workspace ONE platform is composed of Workspace ONE Access and Workspace ONE UEM. Although each product can operate independently, integrating them is what enables the Workspace ONE product to function.
Workspace ONE Access and Workspace ONE UEM provide tight integration between identity and device management. This integration has been simplified in recent versions to ensure that configuration of each product is relatively straightforward.
Although Workspace ONE Access and Workspace ONE UEM are the core components in a Workspace ONE deployment, you can deploy a variety of other components, depending on your business use cases. For example, and as shown in the figure in the next section, you can use Unified Access Gateway to provide the Workspace ONE Tunnel or VPN-based access to on-premises resources.
For more information about the full range of components that might apply to a deployment, refer to the Workspace ONE UEM documentation.
Cloud-Based logical architecture
With a cloud-based architecture, Workspace ONE is consumed as a service requiring little or no infrastructure on-premises.
- Workspace ONE UEM SaaS tenant – Cloud-hosted instance of the Workspace ONE UEM service. Workspace ONE UEM acts as the mobile device management (MDM), mobile content management (MCM), and mobile application management (MAM) platform.
- Workspace ONE Access SaaS tenant – Cloud-hosted instance of Workspace ONE Access. Workspace ONE Access acts as an identity provider by syncing with Active Directory to provide single sign-on (SSO) across SAML-based applications, Horizon–based apps and desktops, and ThinApp packaged apps. It is also responsible for enforcing authentication policy based on networks, applications, or platforms.
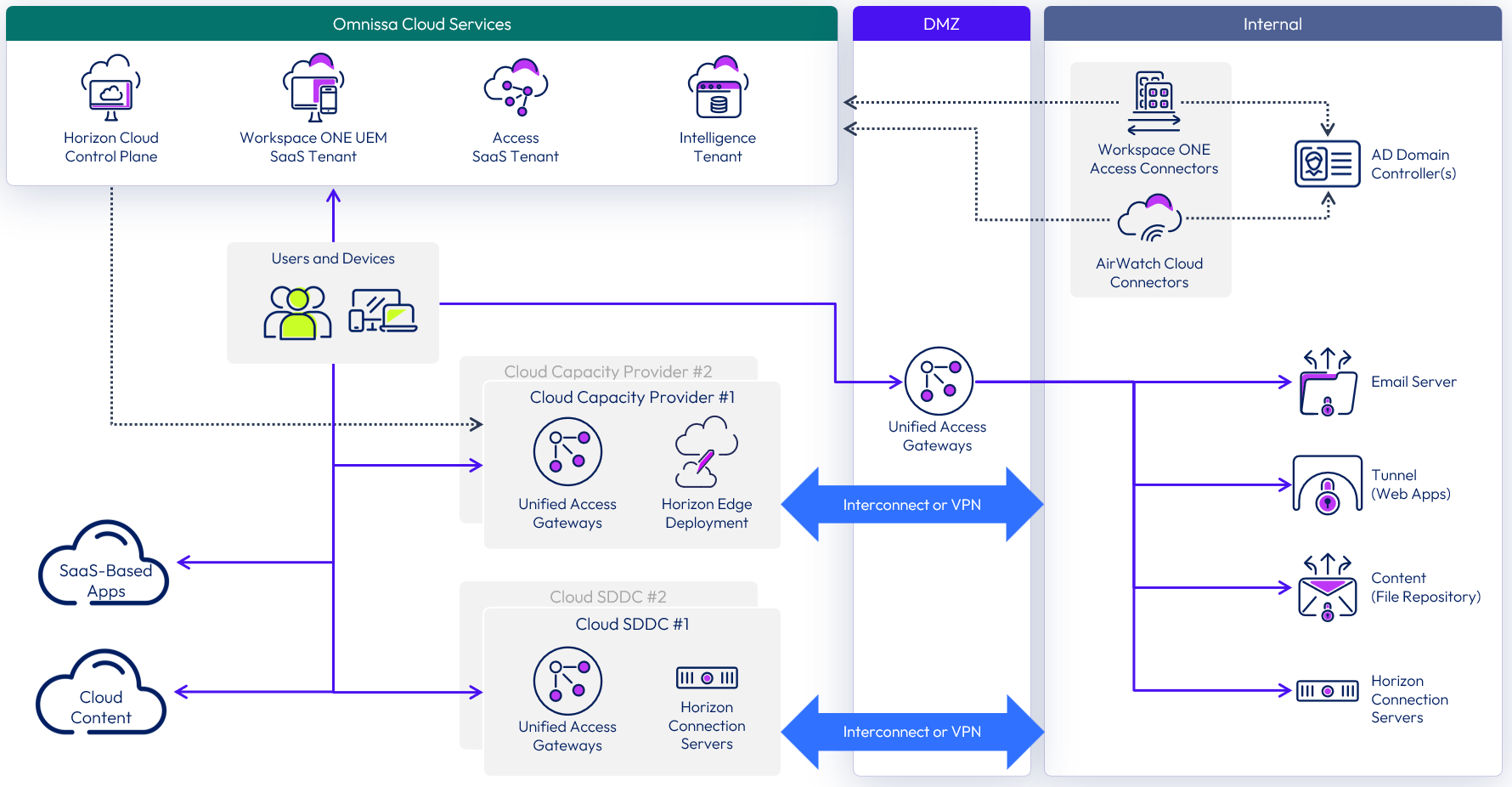
Figure 5: Sample Workspace ONE cloud-based logical architecture
On-Premises logical architecture
With an on-premises deployment of Workspace ONE, both Workspace ONE UEM and Workspace ONE Access are deployed in your data centers.
- Workspace ONE UEM – On-premises installation of Workspace ONE UEM. Workspace ONE UEM consists of several core components, which can be installed on a single server. Workspace ONE UEM acts as the MDM, MCM, and MAM platform.
- Workspace ONE Access – Acts as an identity provider by syncing with Active Directory to provide SSO across SAML-based applications, Horizon–based applications and desktops, and ThinApp packaged apps. Workspace ONE Access is also responsible for enforcing authentication policy based on networks, applications, or platforms.
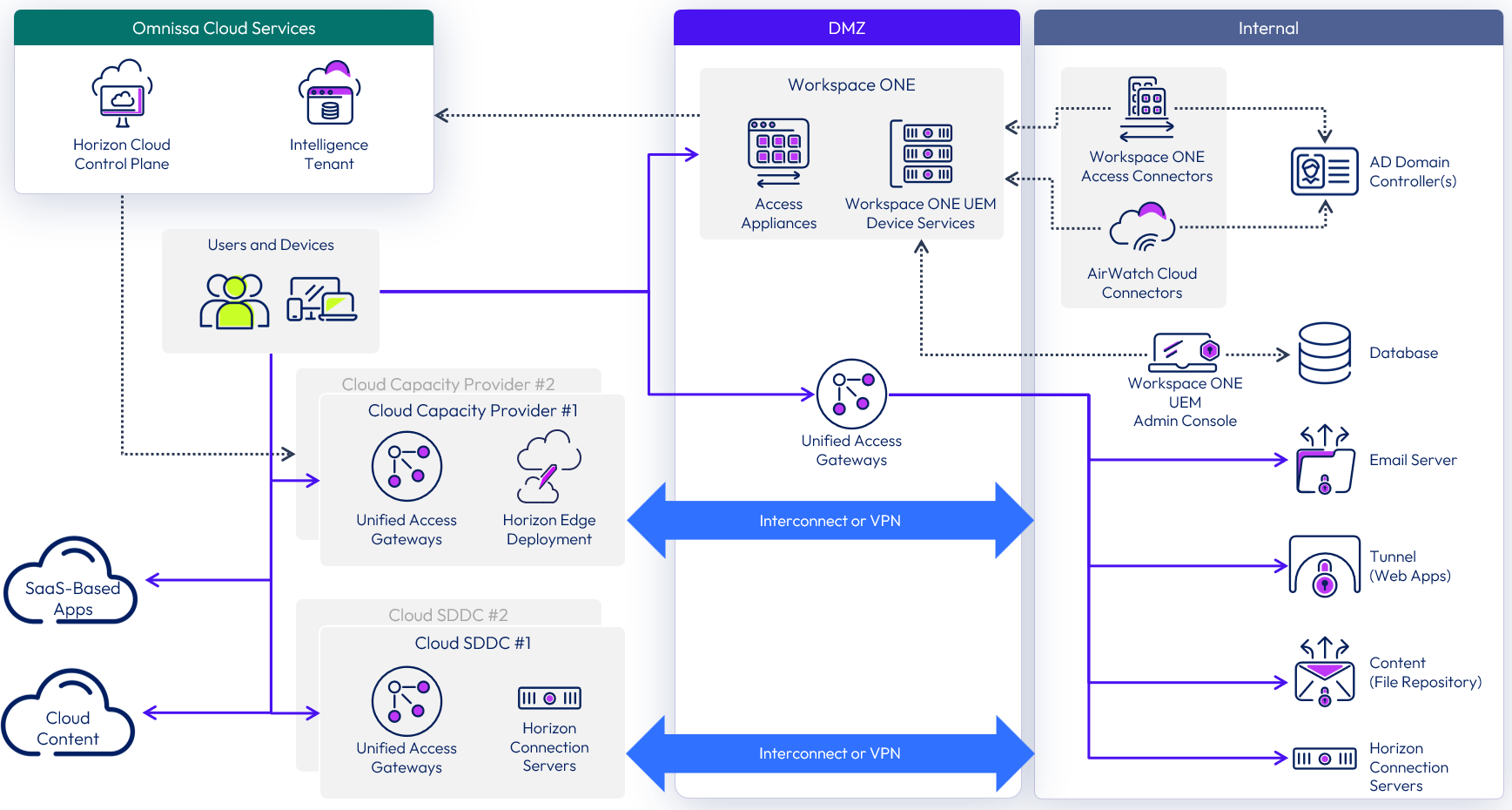
Figure 6: Workspace ONE sample on-premises logical architecture
Common components
A number of optional components in a Workspace ONE deployment are common to both a cloud-based and an on-premises deployment.
- AirWatch Cloud Connector (ACC) – Runs in the internal network, acting as a proxy that securely transmits requests from Workspace ONE UEM to the organization’s critical backend enterprise infrastructure components. Organizations can leverage the benefits of Workspace ONE UEM MDM, running in any configuration, together with those of their existing LDAP, certificate authority, email, and other internal systems.
- Workspace ONE Access Connector – Performs directory sync and authentication between an on-premises Active Directory and the Workspace ONE Access service.
- Unified Access Gateway – Virtual appliance that provides secure edge services and allows external access to internal resources.
Horizon virtual desktops and published applications
Both Horizon 8 and Horizon Cloud Service can be combined and integrated into a Workspace ONE deployment, regardless of whether you use a cloud-based or on-premises deployment.
- Horizon 8 – Manages and delivers virtualized or hosted desktops and applications to end users.
- Connection Servers – Broker instances that securely connect users to desktops and published applications running on hypervisor VMs, physical PCs, blade PCs, or RDSH servers. Connection Servers authenticate users through Windows Active Directory and direct the request to the appropriate and entitled resource.
- Horizon Administrative Console – An administrative console that allows configuration, deployment, management, and entitlement of users to resources.
- For more information on the architecture and design of Horizon 8, see Horizon 8 Architecture.
- Horizon Cloud Service – A multi-tenant, cloud-scale next-generation hybrid DaaS platform. Allows you to modernize virtual desktop and app delivery, enabling you to choose where virtual desktops and apps reside, while reducing costs.
- Horizon Control Plane – A distributed cloud-based control plane that contains the containerized services that deliver Horizon Cloud Service – next-gen. It is used for all administrative functions and policy management and to provide user services.
- Horizon Universal Console – Administrative user interface that manages all services and functions provided by the Horizon Cloud Service.
- Capacity Providers - Providers are supported hypervisors and cloud platforms that provide the necessary resource capacity to deliver desktops and applications to end users. Each individual provider of capacity should have infrastructure sourced from a single physical location or data center.
- For more information on the architecture and design of Horizon Cloud Service – next-gen, see Horizon Cloud Service - next-gen Architecture.
General multi-site best practices
There are numerous ways to implement a disaster recovery architecture, but some items can be considered general best practices.
Components that must always run with a primary instance
Even with an active/active usage model across two data centers, meaning that the service is available from both data centers without manual intervention, one of the data centers may hold the primary active instance for some services, while the second site holds a secondary passive instance. The following components must run with a primary instance in a given site:
- On-premises Workspace ONE UEM
- On-premises Workspace ONE Access
- User profile and data shares containing Dynamic Environment Manager user data
- Microsoft Active Directory flexible single master operations (FSMO) roles, specifically, Primary Domain Controller (PDC) Emulator, because it is required to make changes to domain-based DFS namespaces
- Microsoft SQL Server Always On availability groups (if used)
Be sure to secure those resources that are primary and secondary by nature or that cannot be failed over automatically. Procedures must be put in place to define the steps required to recover these resources.
For this reference architecture design, we chose to place the primary availability group member in Site 1 as well as all AD FSMO roles on a domain controller. We made this choice because we had a good understanding of the failover steps required if either Site 1 or Site 2 failed.
Component replication and traveling users
Use Workspace ONE and Horizon components to create effective replication strategies and address the needs of users who travel between sites:
- Create a disaster plan up front that defines what a disaster means in your organization. The plan should specify whether you require a 1:1 mapping in terms of resources, or what portion of the workforce is required to keep the organization operational.
- Understand what user data will need to be replicated between sites to allows users to be productive. The quantity, speed, and frequency of replication will affect the time it takes to present a complete service to a user from another site.
- Replicate Horizon desktop and server (RDSH) golden image templates between sites to avoid having to build the same templates on both sites. You can use the Image Management Service from Horizon Cloud Service, or a vSphere content library, or perform a manual replication of the resources needed across the whole implementation.
- With Horizon, use Universal Broker or Cloud Pod Architecture.
- Avoid using a stretched storage cluster unless you have a persistent desktop model in the organization that cannot easily be transformed into a nonpersistent-desktop use case.
- With regard to initial user placement, even with a traveling worker use case, a given user must be related to user profile data (Dynamic Environment Manager user data), meaning that a relationship must be established between a user account and a data center. This also holds true when planning how users in the same part of the organization (such as sales) should be split between sites to avoid an entire function of the company being unable to work should a disaster strike.
- For a traveling worker use case, where Dynamic Environment Manager is used to control the user profile data, recommends that FlexEngine be used whenever possible in combination with folder redirection. This keeps the core profile to a minimum size and optimizes login times in the case where a profile is loaded across the link between the two data centers.
- Use Microsoft SQL Server failover cluster instances and Always On availability groups for on-premises Workspace ONE UEM and Workspace ONE Access where possible. This is not required for the Connection Server event database.
Summary and additional resources
Now that you have come to the end of this chapter, you can return to the reference architecture landing page and use the tabs, search, or scroll to select further chapter in one of the following sections:
- Overview chapters provide understanding of business drivers, use cases, and service definitions.
- Architecture chapters give design guidance on the Omnissa products you are interested in including in your deployment, including Workspace ONE UEM, Access, Intelligence, Workspace ONE Assist, Horizon Cloud Service, Horizon 8, App Volumes, Dynamic Environment Manager, and Unified Access Gateway.
- Integration chapters cover the integration of products, components, and services you need to create the environment capable of delivering the services that you want to deliver to your users.
- Configuration chapters provide reference for specific tasks as you deploy your environment, such as installation, deployment, and configuration processes for Omnissa Workspace ONE, Horizon Cloud Service, Horizon 8, App Volumes, Dynamic Environment Management, and more.
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2025-04-02 |
|
| 2024-10-07 |
|
| 2024-05-16 |
|
| 2023-11-13 |
|
| 2023-07-25 |
|
Authors and contributors
This chapter was written by:
- Graeme Gordon, Senior Staff Architect, Omnissa.

