Zero trust regulation and framework
Executive summary
The pandemic moved zero trust from something that was “nice to have” to something that “we need to implement immediately. Like, yesterday!” The old perimeter-based security model is finally starting to die, and we see the transition almost becoming complete in 2022 and high-profile cases like the Colonial Pipeline REvil ransomware gang attacks, SolarWinds breach attack on US agencies — including parts of the Pentagon, the Department of Homeland Security, the State Department, the Department of Energy, the National Nuclear Security Admin, and the Treasury. So were private companies, like Microsoft, Cisco, Intel, and Deloitte, and other organizations like the California Department of State Hospitals, and Kent State University.

Most recently, the Apache Log4j vulnerability, have certainly helped speed up that awareness and drove it into hyper-drive instigating a special White House Open-Source Software Security Summit to look into the national and global supply-chain and was attended by Omnissa’s Office of the CTO (OCTO) to help industry and government have an open dialogue on how best to tackle examples of Log4j, which is just the latest poster child for the real issue: how can we ensure source code, build, and distribution integrity in open source software (OSS)?.
Undoubtedly, zero trust (ZT) is trendy and yes, lots of vendors have hopped on the bandwagon and relabeled their existing security products as being “zero trust/capable/ready.” So, wading through some marketing-hyped terms will be inevitable, but rest assured in 2022 you will see that it’s both real and achievable to begin deployment of ZT and these concepts within episode 4 will help provide takeoff and help better define the true emphasis of the term ‘zero-trust’ from what it truly is, a framework and intrinsic cybersecurity paradigm and architecture, and how best to comply, fund and make the end user's lives better for it!
U.S National Background
In 2020, the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-207, Zero Trust Architecture (ZTA) was released to provide agencies with guidance and detailed recommendations to improve their security posture using the core principles of ZTA. While in 2021, after several high-profile malicious campaigns and attacks against both civilian and government targets, the Executive Order (EO) 14028 “Improving the Nation’s Cybersecurity” was scripted with requirements for all Federal agencies to develop a plan to implement ZTA in an effort to modernize and strengthen cybersecurity standards and detection.
Also, the EO helps demonstrate progressive refinement of requirements as they emanate from NIST, Cybersecurity & Infrastructure Security Agency (CISA), Office of Management & Budget (OMB), and Federal Acquisition Regulations (FAR) changes, and recently, an updated memo was sent with instructions for the Department of Defense (DoD) and intelligence agencies (IC) spelling out how the network requirements for civilian federal agencies included in that order — such as instituting zero-trust security principles — also should apply across National Security Systems (NSS) and culminated with the release this week of the OMB Memorandum requirements within M-22-09 which sets forth a Federal ZTA Strategy, requiring agencies to meet specific cybersecurity standards and objectives by the end of FY24.
Additionally, late last year, the Biden administration tasked NIST to work with industry and other parties to come up with a new framework “to improve the security and integrity of the technology supply chain.” The White House said that NIST’s work will “serve as a guideline to public and private entities on how to build secure technology and assess the security of technology, including open-source software.”
Furthermore, the U.S. FedGov also has its arms around at least some of the same technology supply-chain issues through existing efforts highlighted by CISA. That approach is being made through the Information and Communications Technology (ICT) Supply Chain Risk Management Task Force, which last month had its term extended to July 2023. CISA’s ICT task force is a public-private partnership composed of representatives from large- and small-private sector organizations to identify challenges and solutions for managing risks to the global ICT supply chain. It is chaired by CISA, IT and the Communications Sector Coordinating Councils.
Although NIST is a part of some of the most recognized Zero Trust standards, there are other reference architectures, pillars, and frameworks both nationally and internationally that we’ll touch upon in this document.

Compliance & regulatory breakdown
This section discusses the compliance and regulatory breakdown.
National
One of the key institutes and though leaders used by both U.S. Federal, State & Local/Education (SLED) is based on the NIST / NCCoE = SP guidance & collaboration consortium & NRA and FARS clause language related to SP 800-207 = compliance: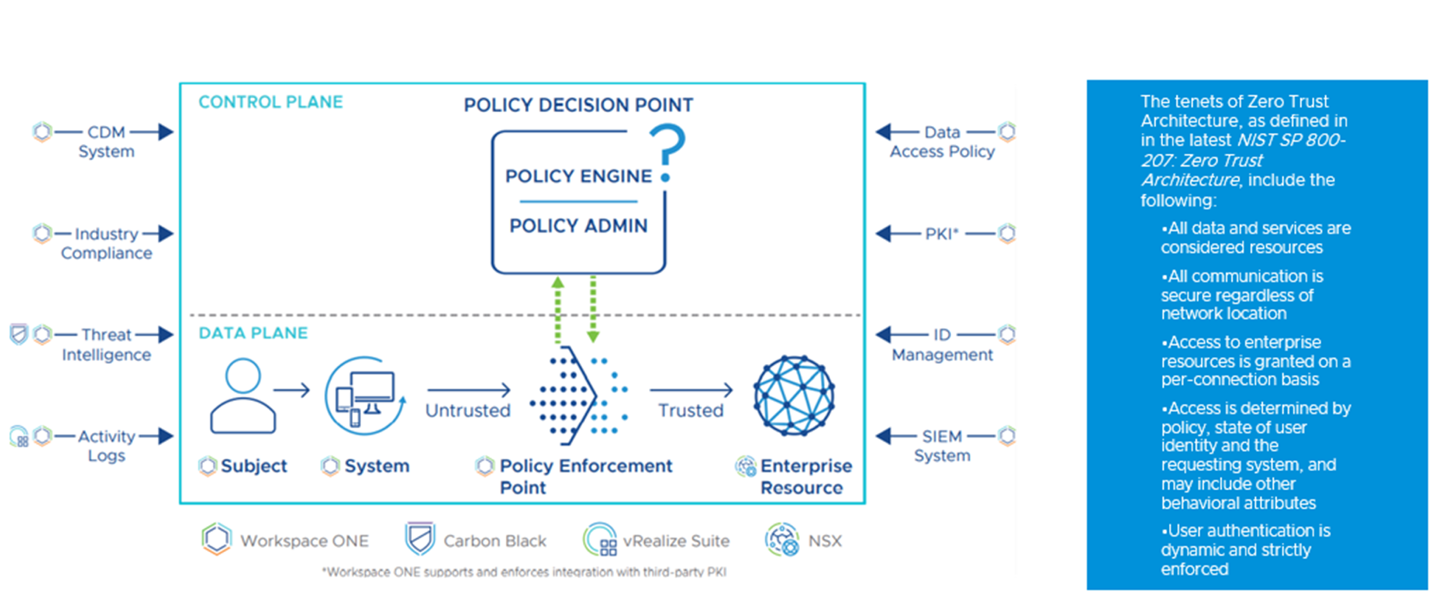
Federal Information Security Modernization Act (FISMA) enhancements with NIST’s SP 800-53v5 and to the FedRAMP; targeted highlights to modernize FISMA that provide clear, coordinated, whole-of-government approach to federal Cybersecurity include:
- Clarify Federal Cybersecurity Roles for Improved Cooperation.
- Advance a Risk-Based Cybersecurity Posture.
- Expand Inventories and Information Sharing for Improved Security.
- Promotes Shared Services and Agency Support.
DHS / CISA = Technical Reference Architecture and Model Pillars:
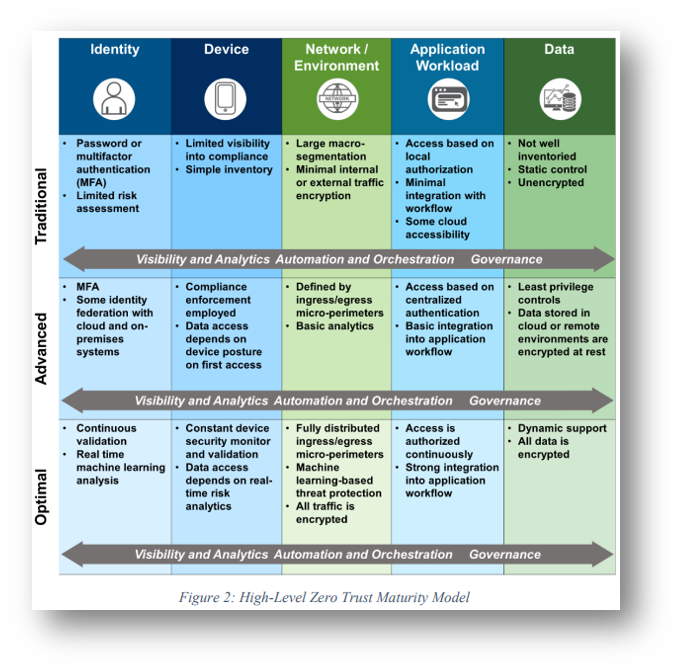
DISA / DoD = Reference Architecture’s ZT controls and ‘Maturity Levels’: 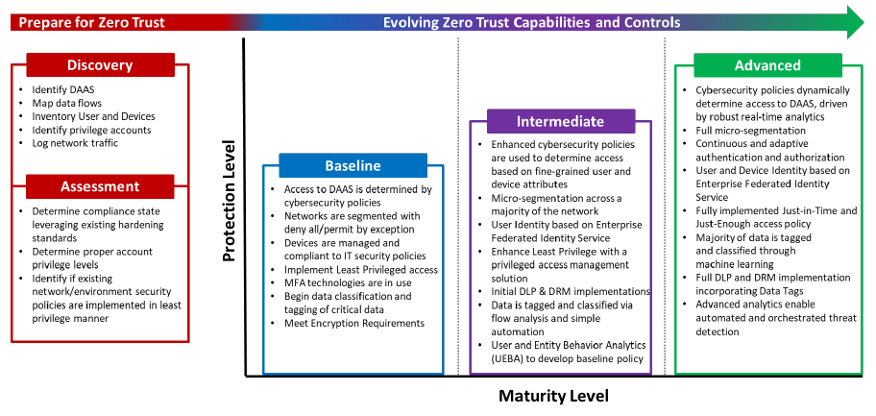
Exec / OMB = EO 14028 & principal guidance M-22-05 for ZT requirements= targeted through FY24:
- From within the Executive Order (EO) 14488, agencies must be moving to a zero-trust architecture and need to implement specific zero trust security goals by the end of Fiscal Year (FY) 2024, organized around (5) pillars:
- Identity: Agency staff use an enterprise-wide identity to access the applications they use in their work. Phishing-resistant multi-factor authentication (MFA) protects those personnel from sophisticated online attacks.
- Devices: The Federal Government has a complete inventory of every device it operates and authorizes for government use, and can prevent, detect, and respond to incidents on those devices.
- Networks: Agencies encrypt all Domain Name System (DNS) requests and HTTP traffic within their environment and begin executing a plan to break down their perimeters into isolated environments.
- Applications and Workloads: Agencies treat all applications as internet-connected, routinely subject their applications to rigorous testing, and welcome external vulnerability reports.
- Data: Agencies are on a clear, shared path to deploy protections that make use of thorough data categorization. Agencies are taking advantage of cloud security services to monitor access to their sensitive data and have implemented enterprise-wide logging and information sharing.
- Other elements:
Automation: FISMA data collection has long remained an overly manual process that often leads agencies to create complicated spreadsheets and internal processes to respond to questions. As the Federal information security apparatus matures, so should its reporting mechanisms. OMB is emphasizing automation and the use of machine-readable data to speed up reporting, reduce agency burden, and improve outcomes. This memorandum directs development of a strategy to enable agencies to report performance and incident data in an automated and machine-readable manner.
Visibility: CISA is continuing to work with Federal agencies and the public to mitigate potential exposure, and also renewing calls for a Software Bill of Materials (SBOM) to aid in system visibility and inventory management, which was called for in cybersecurity EO 14028 – as a way to make remediation of similar vulnerabilities easier in the future, providing essentially a list of components that comprise a given piece of software or application. Furthermore, to provide a better-automated way to understand if those assets are exposed to a given vulnerability and then quickly pivot to remediation; thus, driving down the response time that an adversary has potentially to exploit it (as was in the case of the Apache Log4j). Those agencies/businesses that had an SBOM in place were able to get to the root of those integrations/dependencies far better than those that did not.
Additional details within the OMB M-22-05 requirement Incident Reporting:
- Reporting Major Incidents to OMB and CISA:
- Agencies must report to CISA and the OMB OFCIO within one hour of determining a major incident occurred and should update OMB OFCIO and CISA within (1) hour of determining that an already-reported incident or breach is a major incident.
- Pursuant to Presidential Policy Directive-41 (PPD-41), U.S. Cyber Incident Coord, if a cyber incident is a major incident, it is also a "significant cyber incident." Thus, would also trigger the coordination mechanisms outlined in PPD-41 and potentially require participation and actions from a Cyber Unified Coordination Group.
- Don’t have to be a federal agency to comply with the NIST framework (CSF) or take actions on the EO:
- A recent survey, conducted ironically by SolarWinds, interviewed 100 state, local officials and 100 education-sector officials, found that 67% are “somewhat likely” to adopt practices and activities outlined in EO 14028 while another 19% said they are “very likely” to do so.
- Commercial firms, vendors and providers in order to comply as a part of the larger ecosystem and supply chain will also have to comply and invoke this framework to assure viability to not only the Public Sector but also the private firms for which they do business.
- Examples of standards and compliance bodies for ZT foundations include:
- Nat'l Cyber Security Centre NCSC for UK (ZT FW pub) / Canada / New Zealand
- EU NIS2 Directive/ENISA Certification (5G & Cybersecurity market certs)
- Germany DEUmilSAA / BSI / Cloud Telkom - C5
- International Standards Organization (ISO) 27001 , 27017/18 & 27701
- Australian Cyber Security Centre (ACSC) InfoSec Manual
- APACJ – InfoSec Mgt & Assessment Program (ISMAP)
- 3rd Generation Partnership Project (3GPP) = 5th Gen (5G)
Other factors include the following:
- Data privacy regulations > dictating how personal data is used and stored are increasing as the UN Conference on Trade & Development (UNCTAD) provides a collection of 128 countries with forms of legislation worldwide; some examples:
- California Consumer Privacy Act (CCPA)
- General Data Protection Regulation (GDPR)
- Protection of the liability of user data
- Cybersecurity Framework from HITRUST Alliance & Cybersecurity CSF for Global Financial Intuitions
- The rising cost of cyber-attacks > Cybercrime is estimated to have surpassed $6T in 2021 and is expected to exceed $10T by 2025 <and> Average cost of a data breach is ~= $4.24M per incident
- North Korean state-sponsored actors alone stole an estimated $395 million worth of cryptocurrency last year as part of seven intrusions against virtual currency exchanges and investment firms, up (3) from 2020 (although fewer than the 2018 high of 10 @ $522 million total)
Note: No one single vendor will meet the full spectrum of a ZTA
- North Korean state-sponsored actors alone stole an estimated $395 million worth of cryptocurrency last year as part of seven intrusions against virtual currency exchanges and investment firms, up (3) from 2020 (although fewer than the 2018 high of 10 @ $522 million total)
- Multiple vendors and solutions within the ecosystem will be required
- Omnissa too will not be a ‘single source’ to achieve all elements of a complete ZTA <but> can offer a unique guide for deploying a model that with a collection of assets/services/solutions could meet these 1st phases and provide a foundation for the future evolution of ZTS etc.
- Mapping to the NIST Cybersecurity framework e.g. Identify, Detect, Protect, Respond & Recover <and> zero-trust framework 7 pillars is a baseline step to providing an initial roadmap for planning and execution (ex. GSA provides for such an acquisition mapping against its (8) pillars of ZT (user, device, network, infrastructure, app, data, visibility & analytics, orchestration & automation): GSA: ZTA Acquisition & Adoption
- Additionally, the DHS Continuous Diagnostics & Mitigation (CDM) Program, although not a fully developed ZTA does provide for funding of numerous elements of the pillars of ZTA: Continuous Diagnostics & Mitigation (CDM) Program
User/customer/employee experience
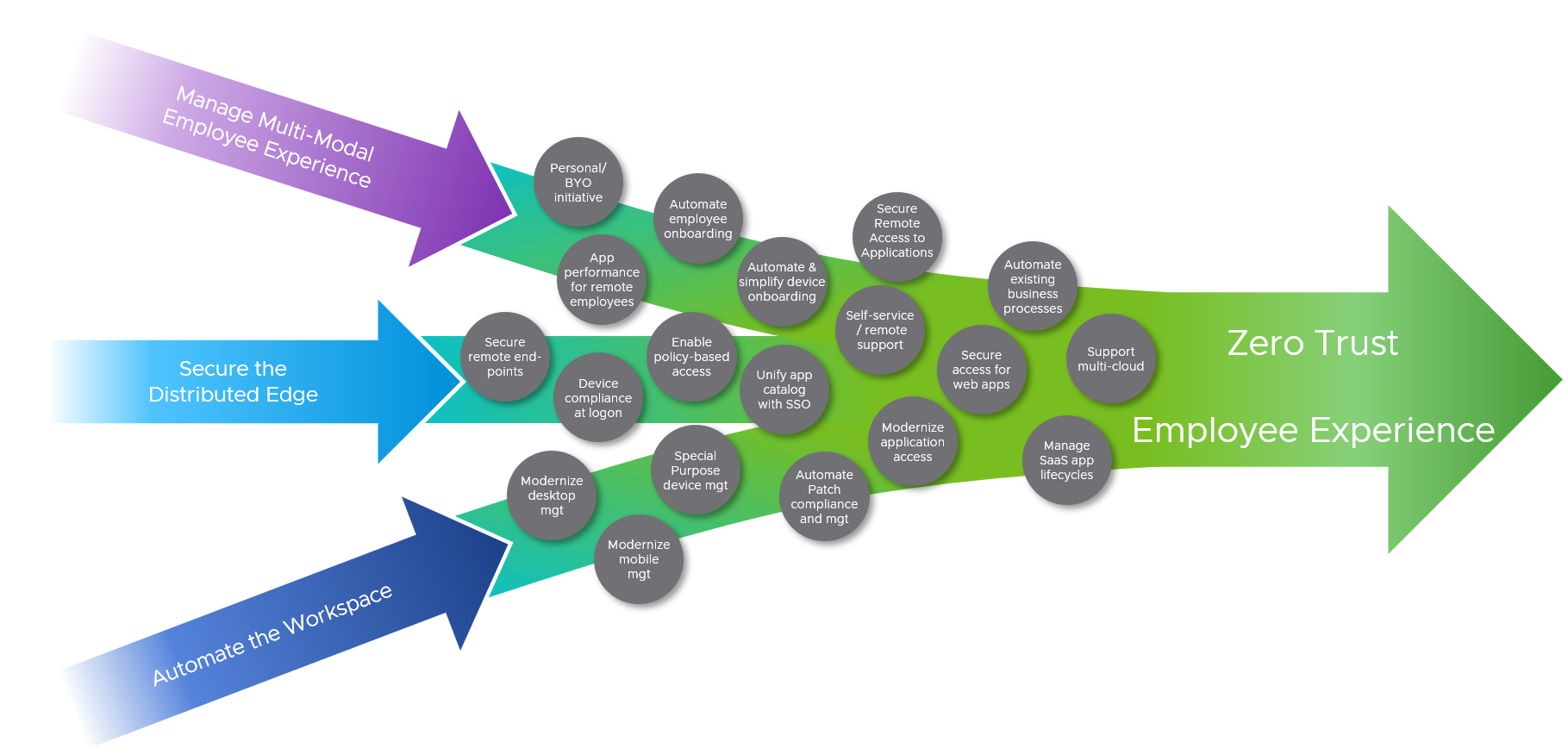
It’s been that the pandemic took 10-15 years of progress (in everything, not just IT) and condensed it down into 1-2 years. We absolutely agree. You probably noticed that nothing on our list of predictions for 2022 was “new” per se. Rather, it’s more about things that have been things for a while that we’ll see becoming more mainstream in 2022.
- Customer product compliance assurances:
- As previously mentioned, this required an updated emphasis on automation of compliance, exceptions and reporting via OMB M-22-05 which drove FISMA enhancements with NIST’s SP 800-53v5 and to the FedRAMP cloud hosting security control requirements of the industry.
- Enhanced Identity Management (IdM) and single sign-on (SSO) > for a passwordless experience
- Simplifying End User Onboarding and Access including user-owned or BYOD
- Remote onboarding is one of the trends that emerged during the pandemic was that areas such as End-User Computing (EUC) and HR will be coming closer together as they continued to partner to deliver all the HR capabilities remotely.
- That’s worked as well as could be expected, but it also exposed that the labor and hiring laws in many places are old and weird.
- Regulations are getting updated, with various digital and remote methods being implemented to streamline the onboarding and employment verification process.
- However just because the laws are changing doesn’t mean that all the companies are implementing these new technologies.
- Remote onboarding is one of the trends that emerged during the pandemic was that areas such as End-User Computing (EUC) and HR will be coming closer together as they continued to partner to deliver all the HR capabilities remotely.
- More secure access via SASE (pervasive, seamless, flexible), with multiple tunnel / secure connectivity options (unlike VPN) e.g., split tunnel / per-app / multi-cloud
- The reality is that during the pandemic, people realized that their VPNs were one of their most vulnerable areas and that they can no longer just provide broad access back to the entire corporate network to their remote users.
- Micro-perimeters, continuous policy enforcement, and the wide availability of SASE offerings are moving everyone past VPNs nowadays.
- Better broadband to augment both the remote and cloud experience (speed, resilience, security (consumer devices (ex. NIST MUD (Manufacturer’s Usage Description)))
- Robust Device trust and validation:
- Continuous Policy Enforcement (CPE), although not a single product, rather a mode of operation that could apply to devices, app sessions, network sessions, or even the ability to use a client device.
- ex. a device only allowed to be used in one specific location, so if the user disables that device’s location services, the device immediately locks itself.
- Many of today’s leading security solutions include some form of CPE but will be paramount to device trust and the ZTA solution.
- Threat Defense and Endpoint Protection (MTD/EPP) solutions already can provide this visibility and controls on all sorts of end-user devices, including traditional, mobile and IoT.
- Continuous Policy Enforcement (CPE), although not a single product, rather a mode of operation that could apply to devices, app sessions, network sessions, or even the ability to use a client device.
- Another trend that emerged from the pandemic is that people are finally starting to look at the broad, end-to-end, true end-user “experience.” It’s no longer good enough to just tell users, “Get your own home broadband, here’s the URL for the apps, good luck!”.
- With so many workers scattered out of the office, and with so many variables, including device specs, what else is running on the devices, home Wi-Fi contention, local ISP congestion, the tubes, VPN saturation, etc., IT departments have realized that they need to get a better picture of what the experience is actually like from the end user’s perspective.
- Luckily there are plenty of tools to help with this, from SaaS performance management tools to the Digital Employee Experience (DEX) capabilities in Workspace ONE, and we see 2022 as the year that these capabilities go mainstream, and IT departments get serious about managing “the last mile.”
Examples of financial fulfillment for public sector
This section lists examples of financial fulfillment.
- Technology Modernization Fund (2017) > a US Federal tech modernization initiative that gives agencies additional ways to deliver services to the American public more quickly, better secure sensitive systems and data, and use taxpayer dollars more efficiently.
- The GSA TMF Program Management Office (PMO) provides support to agencies applying to receive funds from the TMF to support their modernization efforts at every stage of the proposal development process, from initial concept development to final award.
- American Rescue Plan (2021) > $1.9T that was provided thru the U.S. Treasury Department and allows state and local governments that received funds under last year’s Act to spend that money more easily on cybersecurity upgrades and broadband construction, bringing relief to officials who said the original law was too restrictive.
- Under the relief fund, $350 billion was allocated (of which roughly $105B is still left of the fund), such that states, and localities are set up to receive are now more flexible to spend on Cyber & Cybersecurity than those funds allocated in the 2020 CARES Act — which limited relief money to programs that directly addressed COVID-19.
- The final rule, set to take effect April 1, also broadens what the Treasury considers “government services” that relief funds can fund. While state and local governments could already use their awards on IT upgrades, the new rule specifically names ‘cybersecurity modernization and broadband infrastructure constructions’ as acceptable uses of relief funds, including hardware and software expenditures.
- Infrastructure Investment & Jobs Act (2021) > $1.2T infrastructure spending bill that includes, among many measures, a new cybersecurity grant program and record-setting investments in broadband development.
- $1 billion to set up a four-year grant program inside the Department of Homeland Security to assist state and local governments with cybersecurity funding. The grants, which are to be administered by the Federal Emergency Management Agency — with the Cybersecurity and Infrastructure Security Agency serving in an advisory role.
- The grant plans — particularly the cybersecurity program — will require states to submit detailed plans for how they plan to use any money they might receive. State officials can hone their visions by focusing on a few key subjects, like interoperability and resilience and pick a standard or standardized approach.
- But all arenas of the infrastructure bill will have some ‘Cyber’ tie to them and thus need Cybersecurity planning involved for their procurement and deployment, monitoring, and protection.
- In conjunction with these, enhancements to Federal Acquisition Regulations (FAR) require vendors to comply & be required to conform with NIST SP 800-207 Zero Trust framework <or> will be required to be mitigated or an authorization waiver from an ATO / AO to be deployed without doing so.
- All current FedRAMP cloud environments are already being driven to the newer NIST 800-53 v5 controls to enable these 207 baselines for adoption
- Also includes $65 billion for broadband deployment, the single largest federal investment in high-speed internet access (which should enhance the end-user experience for cloud adoption.)
- $1 billion to set up a four-year grant program inside the Department of Homeland Security to assist state and local governments with cybersecurity funding. The grants, which are to be administered by the Federal Emergency Management Agency — with the Cybersecurity and Infrastructure Security Agency serving in an advisory role.
Summary and additional resources
This document discussed Zero Trust Regulation & Framework, how to get funding or accommodate Zero Trust in the budget, and how to provide a great Zero Trust user experience.
Additional resources
For further Zero-Trust assets, see:
Changelog
Create a new row at the top of the table, and enter a summary of relevant changes. Don’t include reformatting changes, minor rebranding, and other internal changes.
The following updates were made to this guide:
| Date | Description of Changes |
| 2024/11/22 |
|
| 2022/01/21 |
|
About the author
This document was authored by:
Feedback
Your feedback is valuable.
To comment on this paper, contact Omnissa Technical Marketing at tech_content_feedback@omnissa.com.


