Horizon Cloud Service – next-gen Security Overview
Introduction
This document provides an overview of the security controls implemented in the cloud-connected components of Omnissa Horizon® Cloud Service – Next-Gen.
Note: Horizon Cloud Service Next-Gen and Horizon Cloud Service (HCS) throughout the remainder of this document may be used ‘interchangeably’ but are referring to Horizon Cloud Service Next-Gen specifically in this use case, unless otherwise specified.
Note: You can find the definitions for acronyms used throughout this document in: Acronyms used in the Workspace ONE & Horizon Cloud Security Series.
Purpose
The intent is to provide readers with an understanding of how Horizon Cloud Service Next-Gen approaches cloud security, the key mechanisms, and processes that Omnissa uses to manage information security, as well as describing shared responsibilities for providing security in a modern, cloud computing environment.
Audience
This document assumes at least intermediate knowledge of Horizon Cloud Service Next-Gen and focuses on the policies, processes, and controls supporting the cloud-delivered service. U.S. General Services Administration’s (GSA) Federal Risk and Authorization Management Program (FedRAMP) is not in scope for this document.
Data Center Locations
Horizon Cloud Service Next-Gen provides access to the Omnissa Horizon® Control Plane that is hosted in Omnissa-managed Microsoft Azure instances. The Horizon Control Plane contains the Omnissa Horizon® Universal Console which is also the broker located in the United States, Ireland, and Japan. Horizon Control Plane interacts with Regional Data Shards that store customer data located in the United States, Germany, UK, Ireland, Japan, and Australia. The Horizon Universal Console provides customer administrators access to orchestrate and manage the customer’s Horizon Service workloads.
Shared Responsibilities
The end-to-end security of the Horizon Service is shared between Omnissa and our customers. Responsibilities change by the underlying Horizon Service workload.
Omnissa provides security for the aspects of the service offering over which we have sole physical, logical, and administrative level control. Customers are responsible for the aspects of the service offering over which they have administrative-level access or control.
Omnissa leverages Infrastructure-as-a-Service (IaaS) providers globally to support the Horizon Cloud Service Next-Gen offering. These providers maintain physical and environmental security controls for the cloud-delivered service. Specific details regarding these providers can be found in the Horizon Service Sub-Processors Addendum available in the Omnissa Legal Center.
Compliance Reports
Refer to the Omnissa Cloud Trust Center for the latest list of industry certifications by service.
The Omnissa Information Security Program
Maintaining the service and stored customer data confidentiality, integrity, and availability (CIA-Tirad) requires a wide array of tools, processes, and processes that must all be expertly designed to balance customer satisfaction, business needs, product efficiency, product deadlines, revenue, shareholder expectations, regulations, and laws. Omnissa balances these needs with a set of controls and management processes designed to both mitigate risk and enhance our product offerings. Omnissa created controls and processes using a set of driving principles to provide the underlying general rules and guidelines for security within our cloud-delivered services. Overarching principles include:
- Risk – Managing risk by understanding the threat landscape, building a solid platform, and leveraging all decision makers when calculating risk.
- Controls – Establishing a balance of effectiveness and efficiency by implementing the appropriate controls for the associated risk.
- Security – Providing preventative and protective capabilities to ensure a secure service.
The Omnissa Information Security Management System
Omnissa has implemented various information security policies and procedures that are in-line with its overall corporate objectives, which demonstrate a commitment to the management of a formal Information Security Management System (ISMS) that fulfills our obligations to its customers regarding information CIA. Our ISMS reflects the following considerations and objectives:
- The threats, vulnerabilities, and likelihood of occurrence identified by assessment of risks relative to the overall business strategy and objectives.
- The legal, statutory, regulatory, and contractual requirements that Omnissa and relevant and applicable partners, contractors, and service providers must comply with.
- The principles, objectives, and business requirements for information handling, processing, storing, communicating, and archiving developed by Omnissa to support its business operations.
Omnissa personnel are obligated to comply with Omnissa ISMS data protection requirements in their respective roles, processes, projects, and programs. Failure to adhere to these policies and procedures may result in disciplinary action, including possible termination, including civil and/or criminal liability.
Asset Management
Omnissa maintains an asset management program as part of our ISMS to categorize both physical and logical assets. The Asset Management program is reviewed at least annually, and all changes are approved by our Information Security Governance Committee.
Data Center Operations teams maintain an inventory of all production assets including, but not limited to, software license information, software version numbers, component owners, machine names, and network addresses. Inventory specifications may include device type, model, and serial number.
Data Classification and Handling
Omnissa has a comprehensive Data Classification Policy (DCP) and handling and protection standards for all electronic and paper media. Data classification is one of the foundational elements of the Omnissa ISMS. Controls and protections for information are dependent upon identifying proper data classifications. The Omnissa Confidential Data Classification Program (CDCP) provides a matrix of controls arranged by the data lifecycle, from creation of the data to its destruction, and covers all forms of media while in use, in transit or archived, and the program is audited annually by independent third-party auditors.
The policy focuses on data classification sources, status, risks, and categories associated with the normal data lifecycle. Assets are classified in terms of their value, legal requirements, sensitivity, and criticality to Omnissa and our customers. Customer-owned information is classified as “Restricted” which is the most stringent data classification at Omnissa. Data classification and handling policies are audited at least annually by independent third-party auditors.
Physical Security
The Omnissa physical security policy governs security for our offices, data centers, support centers, and other global business locations to safeguard information systems and staff.
Key elements of this policy include controls around physical security perimeters, physical entry controls, physical access, securing offices, rooms and facilities, visitors to facilities, records, preventing the misuse of facilities, protecting against external and environmental threats, working in secure areas, access to restricted areas, delivery and loading areas, equipment siting and protection, supporting utilities, equipment maintenance, removal of assets, security of equipment and assets off-premises, secure disposal or reuse of equipment, unattended user equipment and clear desk and clear screen.
Horizon Cloud Service components are hosted in various third-party data center locations globally. These data center partners maintain physical and environmental security controls for the cloud-delivered service. Refer to the Horizon Cloud Service sub-processor Addendum available on the Omnissa Legal Center for details on our data center partners. Specific information regarding which region is leveraged by component is outlined in the Horizon Cloud Service-Next-Gen Privacy Data Sheet.
Data Center Security
Omnissa partners with third-party IaaS providers to host applicable components of Horizon Cloud Service - Next-Gen (for example, to host Horizon Control Plane). The IaaS providers have undergone SOC 2 Type 2 audits and have achieved at least ISO 27001 certification. Physical addresses for Horizon Cloud Service Next-Gen hosting locations are confidential and on-site visits are forbidden.
Our data center providers are required to follow the same minimal requirements for redundancy and physical access control, including:
- Ingress and egress points are secured with devices that require individuals to provide multi-factor authentication (MFA) before granting entry or exit through a minimum combination of badge access, biometrics, and mantraps.
- Physical access is controlled at building ingress points by 24x7, on-site professional security staff utilizing surveillance, detection systems, and other electronic means.
- Door alarming devices are configured to detect instances where an individual exits or enters a data layer without providing MFA.
- Physical access points to data centers are recorded by Closed Circuit Television Camera (CCTV). Recordings are retained according to legal and compliance requirements.
- Environmental control systems are equipped minimally with N+1 power, cooling, and fire suppression measures to ensure continuous operations.
Data center locations depend on the customer’s use of Horizon Cloud Service – Next-Gen. Specific details regarding the current location based on the component in question are shown in the Horizon Cloud Service Next-Gen section of the Uptime status page.
Omnissa Offices
All Omnissa offices deploy physical and environmental security measures to safeguard Omnissa facilities, staff, and assets. Omnissa uses a combination of building design, environmental controls, security systems, and designated security personnel, in conjunction with corresponding procedures, and physical and environmental controls, to restrict access to information services and information assets. Controls include, but are not limited to:
- Implementing entry controls to secure Omnissa facilities.
- Maintaining and monitoring an audit trail of all access to the site through badge and visitor logs.
- Requiring visitor sign-in with date and time of entry and departure, and supervising visitation.
- Performing regular access rights reviews to secure areas and updating or revoking these rights as necessary.
- Revoking all access rights to Omnissa facilities and restricted areas immediately while deactivating access codes known by the staff upon personnel termination.
Human Resources and Personnel Security
Human Resource considerations include processes for background screening, employment agreements, training, and employee termination.
Employee Background Screening
Pursuant to local laws, regulations, ethics, and contractual constraints, all employment candidates, contractors, and involved third parties are subject to background verification. Omnissa conducts criminal background checks, commensurate with the employee position and level of access to the service.
Confidentiality Agreements
Omnissa personnel and alternative workforce (AWF) are required to sign confidentiality agreements. Additionally, upon hire, personnel are required to read and accept the Acceptable Use Policy and the Omnissa Business Conduct Guidelines. Employees who violate Omnissa standards or protocols are subject to appropriate disciplinary action.
Employee Training
In alignment with the ISO 27001 standard, all Omnissa personnel and AWF are required to complete annual business conduct and security awareness training. Personnel with access to cloud production environments receive additional training as they assume job roles and responsibilities. Omnissa periodically validates that employees understand and follow the established policies through compliance audits.
Omnissa uses an enterprise Learning Management System (LMS) to deliver required onboarding and annual security awareness training. The LMS records successful completion and reports are reviewed during ISMS review meetings. This training must be completed before authorizing access to production systems.
Awareness training topics include, but are not limited to:
- Secure system configuration.
- User account management policies.
- Environmental control implementation and operation.
- Incident Response plans and procedures.
- Disaster Recovery plans and procedures.
- Physical Security controls.
Employee Termination
Omnissa terminates access privilege(s) to systems when an employee leaves the company. An employee who changes roles within the organization will have access privilege(s) modified according to their new position. Both departing and terminated employees are also required to return assets during this access privilege redaction term.
Business Continuity
This program implements appropriate security controls to protect its employees and assets against natural or man-made disasters. As a part of the program, a runbook system automates policy review, and policy updates made available to appropriate individuals. Additionally, these policies and procedures include defined roles and responsibilities supported by regular workforce training. Omnissa determines the impact of any disruption to the organization by identifying dependencies, critical products, and services.
Our business continuity plans are reviewed annually to determine which business processes are most critical and what resources – people, equipment, records, computer systems, and office facilities – are required for operation. All documented plans follow an annual standard maintenance, assessment, and testing schedule. Service operations teams also maintain service-specific business continuity plans to address the unique needs of each cloud application.
Risk Management
In alignment with the ISO 27001 standard, Omnissa maintains a Risk Management program to mitigate and manage risk companywide. We perform risk assessments at least annually to help ensure appropriate controls implementation to reduce the risk related to the confidentiality, integrity, and availability of sensitive information.
Omnissa cloud management has a strategic business plan to mitigate and manage risks which requires management to identify risks within its areas of responsibility and to implement appropriate measures designed to address those risks. Omnissa cloud management re-evaluates the strategic business plan at least bi-annually.
Our Risk Management Program includes:
- Identifying and characterizing threats.
- Assessing the vulnerability of critical assets to specific threats.
- Determining the risk (that is, the expected likelihood and consequences of specific types of attacks on specific assets).
- Identifying ways to reduce those risks.
- Prioritizing risk reduction measures based on a strategy.
Vendor Risk Management
Omnissa has a comprehensive vendor procurement and risk management program to choose providers that meet identified security baseline requirements. Supplier agreements ensure that providers comply with applicable laws, security, and privacy obligations.
Sub-processors
Omnissa leverages sub-processors to provide certain services on our behalf. Refer to the Horizon Cloud Services Sub-Processors Addendum available on the Omnissa Legal Center for a list of sub-processors used globally. Omnissa is responsible for any acts, errors, or omissions of our sub-processors that cause us to breach any of our obligations. Omnissa enters into an agreement with each sub-processor that obligates the sub-processor to process the Personal Data in a manner substantially similar to the standards set forth in the Omnissa Cloud Services Exhibit available on the Omnissa Legal Center, and at a minimum, at the level of data protection required by applicable Data Protection Laws. Refer to the Omnissa Data Processing Addendum available on the Omnissa Legal Center for additional information.
Change Management
Omnissa maintains a detailed Change Management policy that defines controlled changes to production environments. Changes are processed through a formal program that includes approval, testing, implementation, and roll-back plans.
Third-party and internal audits of these processes are performed at least annually under the Omnissa ISMS program and are essential to the Omnissa continuous improvement programs.
Configuration Management
Omnissa maintains a detailed Configuration Management policy based on industry best practices to harden the cloud environment; revisions and exceptions to the Configuration Management policy are processed through the Change Management policy to help ensure the confidentiality, integrity, and availability of our hosted offering.
Omnissa-managed components Horizon Cloud Service Next-Gen are configured to meet PCI-DSS requirements, such as:
- Disabling unnecessary ports, services, and protocols.
- Inbound and outbound network controls.
- Reviewing server builds for gaps prior to image configuration.
- Hardening server configurations using secure images
Time Synchronization
Time synchronization is in place to help ensure system times are accurate per PCI-DSS requirements.
Vulnerability and Patch Management
Omnissa employs a rigorous Vulnerability Management program as part of the Omnissa ISMS. Risk analysis and acceptance activities are performed on vulnerabilities to confirm the vulnerability and to determine the appropriate means of addressing the vulnerability.
System Monitoring
Omnissa Cloud Operations is staffed 7x24x365 and the team deploys several commercial and custom purpose-built tools to monitor the performance and availability of all hosted solution components. Components include the Omnissa-managed Horizon Cloud Service underlying infrastructure servers, storage, networks, portals, services, and information systems.
Vulnerability Scanning
Vulnerability scans are performed at least monthly on internal and external systems. System and application owners are required to address critical and high vulnerabilities with a plan of corrective action after vulnerability discovery. Other vulnerabilities are addressed with a plan of corrective action within a reasonable period.
Code Security Development Lifecycle Principles
The Omnissa SDL program is designed to identify and mitigate security risks during Omnissa software product planning and development phases. The development of the Omnissa SDL has been heavily influenced by industry best practices and organizations such as SAFECode (the Software Assurance Forum for Excellence in Code) and Software Assurance Maturity Model (SAMM). SAFECode and SAMM are two prominent initiatives in the software security industry that aim to improve software security practices and help organizations enhance the security of their software development lifecycle.
The Omnissa SDL is periodically assessed for its effectiveness at identifying risk, and new techniques are added to SDL activities as they are developed and mature. The program is supported by a security engineering team that performs security design reviews and thorough security testing.
Omnissa encourages continuous employee training through programs that subsidize certification attempts (for example, ISC2’s Certified Information Systems Security Professional (CISSP) and Certified Cloud Security Professional (CCSP)), relevant conference passes, training classes, and subscriptions to leading online training platforms for enhancing technical and business acumen. Additionally, employees can use job rotation programs designed to reignite and broaden employee work experience.

Figure 1: Omnissa SDLC Process
Penetration Testing
Penetration testing includes testing of Omnissa and third parties and customer penetration testing.
Omnissa and Third-Party Testing
The Omnissa Penetration Testing Program is a rigorous set of processes that include automated tooling built into the Omnissa Security Development Lifecycle (SDL), Omnissa Red Team penetration testing, and third-party internal and external testing initiatives all in alignment with industry best practices, standards, and frameworks such as NIST and PCI-DSS. Red Team and third-party tests are performed at least once per calendar year and include testing at the web application, network, logging, and infrastructure layers.
The penetration tests focus on identifying high-impact vulnerabilities that could lead to exploitation, theft of data, or overall privilege escalation. Tests follow a method intended to simulate real-world attack scenarios and threats that could critically impact data privacy, integrity, and overall business reputation. Experienced internal security engineering staff and penetration testing vendors use their industry expertise to develop a risk-informed threat model based on the criticality of resources and data and any specific areas of concern.
To increase the efficiency of testing and to achieve more meaningful results, tests are performed using a white box testing approach – during which the tester has access to source code. For third-party tests, vendors provide daily status updates during the testing period. Any critical or high findings are communicated to Omnissa immediately so they can be resolved during the testing period and be re-tested by the vendor prior to the project close-out.
Remediation Approach
The Omnissa Red Team uses the industry standard Common Vulnerability Scoring System (CVSS) 3 Scoring system, which takes the base score of the vulnerability and applies environmental and other considerations unique to Omnissa to arrive at a true risk score appropriate for our environment. Our policy mandates all vulnerability findings must be remediated with SLA.
As such, we have a standard notification and escalation process to help ensure we secure Omnissa assets. If the user performs remediation within the SLA, then no escalation is necessary. If the user exceeds the SLA time period and does not have an exception approval, we will go through an escalation process to inform management of any non-compliant environments.
Findings from third-party testing are remediated according to a risk-based approach. Each finding is evaluated for probability and impact and is remediated accordingly. Omnissa remediation timelines are dependent upon several factors such as severity, complexity, impact, product life cycle, and location of finding (internal vs. external resource).
We believe this is an important step towards reducing our exposure to risk from vulnerabilities and protecting the availability of our infrastructure. During annual compliance assessments, third-party auditors inspect tickets to determine that identified findings are documented and tracked for remediation.
Customer Penetration Testing
Customer-initiated penetration testing, port and vulnerability scanning, spoofing, web application scanning, protocol flooding, denial of service attacks, installation of malware, attempts to decompile source code or any other actions that may disrupt the cloud-hosted production environment are explicitly forbidden in the Omnissa Cloud Services Exhibit available on the Omnissa Legal Center (see Acceptable Use).
Cloud Environment Monitoring
Omnissa Cloud Operations is staffed 7x24x365 and deploys several commercial and custom purpose-built tools to monitor the performance and availability of all hosted solution components. Components include the underlying infrastructure servers, storage, networks, portals, services, and information systems used in the delivery of Omnissa-managed service components.
Intrusion Detection & Prevention
Omnissa deploys several mechanisms to detect intrusions and help protect against distributed denial of service (DDoS) attacks of the Horizon Control Plane. These mechanisms range from real-time Intrusion Detection/Prevention Systems (IDS/IPS) technologies, internal logs and tools, and external intelligence (for example, Open-Source Intelligence (OSINT)) data sources. Omnissa monitors for security events involving the underlying infrastructure servers, storage, networks, information systems, and upstream providers used in service delivery. As part of our Software Development Lifecycle (SDLC), Horizon applications are also assessed against the Open Web Application Security Project (OWASP) Top Ten to identify potential application code to identify and remediate potential errors that could lead to unauthorized access and Denial of Service (DoS). In alignment with PCI-DSS, Horizon Cloud Service uses file integrity monitoring to detect malicious behavior or changes in system files or libraries. Additionally, Horizon Cloud Next-Gen implements a web application firewall (WAF) and file integrity monitoring (FIM) in alignment with PCI-DSS requirements.
Antivirus & Antimalware
Omnissa implements industry best practices for both administrative and technical controls to prevent, detect, and respond to viruses and malware, including ransomware. As part of our annual security training programs, Omnissa operates a quarterly Phishing Prevention Program to help train our employees to recognize threats. Social engineering topics (such as tailgating, badge access, and vishing) are also covered in our annual security training.
As our employees moved to a remote work model during the global pandemic, Omnissa created a Working from Home security guide that covers topics such as mobile device security, securing home Wi-Fi, phone/email scams, and securing homes for natural disasters.
In alignment with PCI-DSS, Omnissa has deployed and centrally manages antivirus and endpoint protection on all employee workstations which is configured to scan for updates to antivirus definitions and update clients continuously. Additionally, the software performs on-demand virus scans of any attachments or content introduced into the workstation.
Systems settings prohibit end users from disabling endpoint protection software. All corporate-owned and personal devices are also enrolled in a Omnissa-managed instance of Workspace ONE UEM. Note that employees are prohibited from accessing Horizon Cloud Service Next-Gen production environments using personal devices.
Log Management
Omnissa-managed Horizon Cloud Service Next-Gen services leverage a robust, centralized Security Information & Event Management (SIEM) infrastructure per PCI-DSS requirements. All critical systems and privileged access, firewall, and ID/PS logs are logged and monitored. Cloud service system security logs and events are centrally aggregated and monitored in real-time 7x24x365 by the Omnissa Security Operations Center (SOC). Logs forwarded to the Omnissa SOC are retained for one year and up to five years in archive.
Incident Management & Response
The Omnissa Incident Response program plans, and procedures have been developed in alignment with the ISO 27001 and PCI-DSS standards. Omnissa maintains contacts with industry bodies, risk and compliance organizations, local authorities, and regulatory bodies. Points of contact are regularly updated to ensure direct compliance liaisons have been established and prepared for a forensic investigation requiring rapid engagement with law enforcement. Under the Omnissa ISMS program, the incident response plan is tested at least once annually, whether or not a security incident has occurred.

Figure 2: Omnissa Incident Response Cycle
Omnissa Security Operations Center (SOC)
The Omnissa SOC is staffed and monitors alerts on security anomalies 7x24x365. The SOC leverages multiple log capture, security monitoring technologies, and intrusion detection tools to look for unauthorized access attempts, monitor for incoming threats, and detect activity from malicious insiders.
Incident Reporting
All staff are responsible for reporting information security events as quickly as possible. At a minimum, these situations include:
- Ineffective security controls or access violations.
- Breach of information integrity, confidentiality, or availability expectations.
- Human errors.
- Non-compliance with policies or guidelines.
- Breach of physical security arrangements.
- Uncontrolled system changes.
- Malfunction of software or hardware.
Breach Notification
In the case of a confirmed data breach of a Omnissa-managed service component, Omnissa shall without undue delay notify affected customers of the breach in accordance with applicable laws, regulations, or governmental requests.
Identity and Access Management
Managing identity and access includes access of both customers and Omnissa to production environments, as well as Omnissa access to customer networks detailed below.
Customer Access to Production Environment
Customers manage applicable access to the application Horizon Cloud Service Next-Gen application administrative interfaces, such as the Horizon Universal Console and Horizon Cloud Service Next-Gen application programming interfaces (APIs). Identity is tied to either your Omnissa account credentials or if your account is federated, your corporate account credentials.
Customer administrators can configure role-based access controls (RBAC) to restrict the depth of access and user management information and features available to each Horizon Administrative Portal user. Horizon Cloud application administrator changes are retained for review within the console event log. Refer to Omnissa Docs for additional information.
Omnissa Access to Production Environments
Horizon Cloud Service Next-Genis a multi-tenant cloud service. Service systems are accessed for maintenance and support purposes only. Omnissa does not request prior approvals to access service systems. Access privileges are enforced using role-based access control, separation of duties, and the principle of least privileges. Access privileges to Omnissa-managed Horizon Cloud Service components are enforced using role-based access control, separation of duties, and the principle of least privileges.
Production environment access is secured through an allowlist of source addresses, multi-factor authentication, and VPN; and access is restricted to authorized members of applicable teams. Network Access Control Lists (ACLs) and NAT policies forward authorized inbound traffic. Logs are in place to review support staff access to all systems and environments per PCI-DSS requirements.
Omnissa Access to Customer Consoles
The Horizon Control Plane is a multi-tenant cloud service. Service systems are accessed for maintenance and support purposes only. Omnissa does not request prior approvals to access service systems. Access privileges are enforced using role-based access control, separation of duties, and the principle of least privileges. Production environment access is secured through a combination of VPN, IP address allow listing or jump servers using Multi-factor Authentication (MFA) and directory credentials.
In accordance with ISO 27001 and PCI-DSS, access is restricted to authorized members of applicable teams, and system sessions are set to an idle timeout of 15 minutes. Logs are in place to review support staff access to all systems and environments. Quarterly User Access Reviews are conducted to review privileged access and to remove or deactivate accounts with 90 days of inactivity.
Omnissa Access to Customer Networks
Horizon Cloud Service Next-Gen integrates with customer resources using optional customer-managed on-premises connectors. Horizon Cloud services, therefore, do not require direct access to internal customer networks, and Omnissa support personnel do not have access to customer internal networks.
Horizon Cloud Service Next-Gen Architecture
Horizon Cloud Service Next-Genis a modern cloud-first, multi-cloud Desktop-as-a-Service (DaaS) deployment with Thin Edge Infrastructure (TEI). The service provides customers with a global view of their desktops and applications spanning across on-premises and cloud environments. For an overview of Horizon Cloud Service – Next-Gen, refer to the Horizon Cloud Service Next-Gen Privacy Data Sheet, which offers details regarding architectural components, functionality, and geographic location.
Data Center and Horizon Cloud Service Next-Gen Data Processing Locations
Data center locations depend on the customer’s use of Horizon Cloud Service. Specific details regarding the current location based on the component in question are shown in the Horizon Cloud Service Next-Gen section of the Uptime status page.
Horizon Cloud Service Next-Gen Architecture Overview
Horizon Cloud Service Next-Genis a modern cloud-first, multi-cloud Desktop-as-a-Service (DaaS) deployment with Thin Edge Infrastructure. The service provides customers with a global view of your desktops and applications spanning across on-premises and cloud environments. Regardless of the location of customer desktop and application deployments, Horizon Cloud Service Next-Gen enables customers to consistently manage and monitor them. A description of each component, such as VM Hub and Data Shards can be found below.
Horizon Cloud Next-Gen Architecture Diagram

Figure 3: Visual representation of key components within Horizon Cloud Service – Next-Gen
Note: Locations and available regions may change as the service grows.
Horizon Control Plane
Horizon Control Plane is a multi-tenant cloud service that has been built with security in mind. An organization is paired with only one Horizon Control Plane instance at any time.
The Horizon Control Plane is a distributed, cloud-based control plane that contains the containerized services that deliver Horizon Cloud Service – Next-Gen. It is used for all administrative functions and policy management and to provide user services. The Horizon Control Plane provides the ability to deploy and manage the Omnissa Horizon® Edge from a single, centralized user interface. With Horizon Cloud Service Next-Genthe Horizon Console, the connection server/brokering function, App Volumes management servers, and associated databases are all included in the Horizon Control Plane.

Figure 4: The relationship between the Horizon Control Plane and the Horizon Edge
Horizon Edge
A Horizon Edge defines an instance of Horizon capacity as registered in the Horizon Control Plane. It is based in a single physical location or region and can be divided into multiple blocks to provide scalability. There are different implementations of a Horizon Edge, depending on what type of Capacity Provider is being used for the instance (for example, Native Microsoft Azure vs. Omnissa Horizon® 8). More information on each use case is provided in the respective sections below.
Control Plane Virtual Machine Hub
Endpoints correspond to regional data shards to help optimize connectivity between the Horizon Agent and Horizon Control Plane. The communication between the Horizon Agent and the Horizon Control Plane Virtual Machine Hub leverages the Message Queuing Telemetry Transport (MQTT) protocol which is encrypted and leverages Azure Private Link for communication.
Regional Data Shards
Data shards are deployed across multiple regions and store customer data. Customers choose a region to store their data upon their first login to the service. This approach not only helps ensure a more secure method of storing customer data but also provides greater levels of scalability. Communications between the Regional Data Shard and CP VM Hub are conducted over the MQTT protocol which leverages encryption in transit and at rest.
Capacity Providers
Capacity Providers are Omnissa-supported hypervisors and cloud platforms that provide the necessary resource capacity to deliver desktops and applications to end users. A single provider should have infrastructure sourced from a single physical location or data center.
There are two different types of providers:
- Primary Provider – The provider that contains the Horizon Edge deployment (Horizon Edge Gateway & Unified Access Gateways). The primary provider can be dedicated to the Horizon Edge and Unified Access Gateways or can also contain virtual desktops and shared hosts for published applications.
- Secondary Provider - Additional providers are used to expand a Horizon Edge beyond the number of virtual machines (VMs) supported by the primary provider. You can add up to (3) secondary providers to a single Horizon Edge. See Single Horizon Edge Scaling. Secondary providers can be either added to a Horizon Edge during deployment or added later.
Each Horizon Edge must be configured to use a provider. Only one Horizon Edge can be deployed per provider.
Note: Currently, only Microsoft Azure-based Capacity Providers are supported.
Horizon Cloud Service Next-Gen Use Cases
Horizon Cloud Service Next-Gen delivers virtual desktops and applications across multiple deployment options across two main use cases:
- Use Case 1: Deploying Horizon Cloud Service Next-Gen with Microsoft Azure DaaS service.
- Use Case 2: Using the Horizon Cloud Service Next-Gen Control Plane for connecting to on-premises Horizon 8 and providing optional common SaaS services.
Horizon Edge Secure Connectivity to the Horizon Control Plane
The Horizon Edge makes outbound calls to the Horizon Control Plane over the Internet via a secure connection. There is no inbound management connectivity from the Horizon Edge Gateway. Data is transmitted between the Horizon Control Plane and the Horizon Edge, over the public Internet, via Transport Layer Security (TLS) 1.2+ and is authenticated with strong, periodically rotated keys and authentication tokens. The connection to the Horizon Control Plane allows access to the Horizon Edge and CP VM Hub to facilitate the following actions:
- Configuration changes.
- Live state queries.
- Supportability requests, including interactive support, log fetching, and component health queries.
- Brokering a connection between the Horizon Control Plane and the regional data shards.

Figure 5: Interaction between Horizon Edge and Horizon Control Plane
Use Case 1: Horizon Cloud Service Next-Gen on Native Microsoft Azure
Horizon Cloud Service Next-Gen on Native Microsoft Azure is a DaaS platform that can be deployed into a customer's existing Microsoft Azure tenant. The service makes it easy and cost-effective to deliver virtualized Windows desktops and applications to any device, anytime.
Prior to Next-Gen, Horizon Cloud Service required components to reside in a customer’s Microsoft Azure subscription, in addition to the Azure PostgreSQL service. The components generated additional Azure consumption costs each month per Azure subscription, each of which could handle 2,000 users. With Horizon Cloud Next-Gen, most Horizon infrastructure components are moved away from the customer’s responsibility to the Horizon Control Plane, which reduces costs and increases scalability from 2,000 to 5,000 users per Azure subscription.
Placing these resources in the Omnissa-managed Horizon Control Plane also reduces the impact of updates and patches and gives Omnissa more visibility into the day-to-day operations so we can resolve issues before they affect the customer’s environment.
Customer-Managed Microsoft Azure and the Horizon Edge
In Horizon Cloud Service Next-Gen on Microsoft Azure, customer workloads, desktops, virtual desktop instance (VDI) sessions, along with the Horizon Agent and the Horizon Edge, reside inside of customer-managed Azure subscriptions. The Horizon Agent in conjunction with Horizon Edge components is leveraged to communicate with the Horizon Control Plane.

Figure 6: The Horizon Edge and Virtual Desktops/Apps are hosted in the customer's Azure subscription
Secure Credential Storage
The Horizon Cloud Service Next-Gen on native Microsoft Azure service stores the following credentials for each Horizon Cloud subscription account:
- Active Directory domain bind and domain bind aux username and password.
- Active Directory domain join, and domain join aux username and password.
- File share username and password.
- Azure subscription credentials.
These user credentials are protected with AES 256-bit encryption when stored in the cloud. The credentials are accessible by the Horizon Cloud Service when performing operations on behalf of the account or distributing to components that need access.
Customers manage encryption of their workload capacities Horizon Edge, which include VDI Desktop VMs, multi-session VMs, images, and user data. Customers can also optionally configure the Horizon Cloud Service to communicate to the on-premises, corporate network via a virtual private network (VPN) or ExpressRoute connection.
As the Capacity Providers available with Horizon Cloud Service Next-Gen expands, we will continue to update published documentation for details regarding how the service is secured and configured to enable customers to leverage each component.
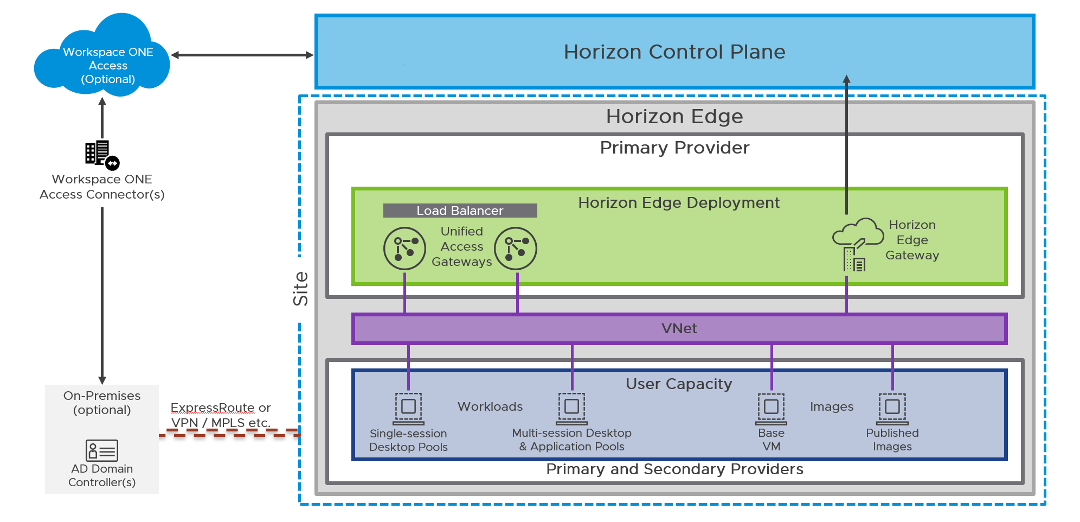
Figure 7: Horizon Cloud Service Next-Gen architecture
Horizon Edge Networking Components
A Microsoft Azure Virtual Network (VNet) is required for each Horizon Edge. In the primary Capacity Provider for each Horizon Edge, the VNet should contain at least three different subnets for management components of the service, a demilitarized zone (DMZ), and desktop capacity. These subnets are used for the Horizon Gateway Appliances and customer-managed workload. Network security group (NSG) policies are applied on the VNet, to allow and disallow traffic in and out of that VNet and to segregate that network into subnets.
Horizon Cloud Next-Gen deployed Edges require three subnets for the delivery of the service:
- DMZ – Enables inbound traffic from the Internet to the external Unified Access Gateways. NSGs that are a feature of Microsoft Azure are used to control inbound access and allow only the required ports and protocols to the external Unified Access Gateways.
- Management – An internal management network that allows the Azure Kubernetes Service (AKS) clusters on the Edge to update the Unified Access Gateways and provides an outbound Internet channel for connection to the Horizon Control Plane and the Azure API.
- Desktop – Customer-controlled network for the VDI desktops and Remote Desktop Session Host (RDSH) Farms (supporting both multi-session desktops and applications), and internal Unified Access Gateways.
Visit the networking section of Horizon Cloud Next-Gen Architecture for additional insight into how the subnets can be used in the implementation of the service.
Azure Kubernetes Service (AKS) Cluster
The AKS cluster deployed as part of the delivery of the Horizon Cloud Next-Gen service is deployed as a fully private cluster. This approach helps ensure the AKS cluster on the customer’s Horizon Edge is not able to be accessed via the public Internet. Instead, the cluster being stored within the customer’s VNet is secured and only accessible via Azure APIs.
Communication via API enables the Horizon Control Plane services and customer Horizon Edge to communicate with one another. The API Server is fully managed by Microsoft and is not accessible directly by Omnissa. Additionally, communication between nodes is secured by leveraging open service mesh to help ensure that no other system (VMs and so on) on the management subnet can intercept the traffic between the nodes.
Kubernetes profiles leverage virtual internet protocol (IP) addresses for most services which helps ensure the security of the Horizon Edge, even if the IP address was compromised. Any service requiring external communications leverages TLS to encrypt communications.
Any communication requiring an outbound connection can be secured through either Network Address Translation (NAT) gateways or via a firewall configuration (user-defined routes). Refer to the following resources for insight into how to configure this approach. This will need to be determined at the time of initial setup.
While both NAT gateway and firewall configuration approaches are supported, the firewall configuration approach offers more granular control regarding content filtering.
Horizon Edge Updates and Troubleshooting
As part of the initial deployment, Omnissa deploys a Kubernetes cluster inside the customer’s Horizon Edge deployment on Microsoft Azure. This AKS cluster facilitates the creation of the external Unified Access Gateway (UAG) in a dedicated Azure Virtual Network (VNet) and any subsequent updates to the UAG.
In the event of troubleshooting or diagnosing an issue, Omnissa can:
- Obtain log files and crash reports from the Horizon Cloud Pod (made available as “Support Bundle”), which will show usernames, times when users have accessed the system, and other environment information, including IP addresses and hostnames.
- Obtain other files, such as configuration files, from the deployed infrastructure VMs within the Horizon Edge.
- Have real-time access to the current operational health status of the Horizon Edge.
- Have interactive shell access on the AKS cluster for troubleshooting and support.
Additional Horizon Edge Monitoring
Customers may optionally leverage Microsoft Defender for Cloud within the customer’s Horizon Edge component which enables intrusion detection at the network level. Due to the different ways this tool can be leveraged (Detection Mode vs. Protection Mode) testing by the customer is advised to help ensure the solution continues to function as expected.
Horizon Cloud Service Next-Gen can optionally communicate with on-premises, corporate network resources via VPN or ExpressRoute connection. This connection may be required if the Active Directory or user data and applications are located on-premises. Typically, internal end users connect to the Horizon Edge over this connection. To help ensure data is secure, the Horizon Control Plane uses strong in-transit encryption (TLS 1.2+) over the public Internet as prescribed by the PCI-DSS Standard.
For detailed, up-to-date information about the protocols and ports for the service, review the product documentation and detailed diagrams are available in a TechZone article entitled Omnissa Horizon Cloud Service on Microsoft Azure Network Ports Diagrams.
Use Case 2: Horizon 8 and Horizon Cloud Service – Next-Gen
Using Horizon Cloud Service – Next-Gen, customers can choose to leverage an on-premises software-defined data center (SDDC) or VMC on AWS to host their pools of desktops. As part of the pairing process, the Horizon Edge deployment comprised of the chosen Capacity Provider, networking elements and user capacity to the Horizon Cloud Control Plane to manage the Horizon subscription license and other services. Omnissa does not have access to customer-managed components of the Horizon 8 Edge, such as their VDI sessions. See the Omnissa Cloud Services Guide in the Omnissa Legal Center for more details.

Figure 8: Horizon Cloud Service Next-Gen connects to on-premises Horizon 8 instances using the Horizon Edge
Horizon Cloud Service Next-Gen Data Processing
Data processing controls include data collection, data separation, data encryption, and key management.
Data Collection: Thin Edge Deployments
How the service interacts with data varies depending on which type of deployment is set up that have been correlated below in Table 1.
Table 1: Horizon Cloud Service Next-Gen Data Collection
| Control Plane Instance | Edge Hub |
| In thin Edge Architecture deployments of the service, the Control Plane Instance (CPI) communicates with Regional Data Shards via API. CPI contains the Horizon Portal which acts as a Broker as well as the Universal Console. The CPI collects the following elements for the delivery of the service. | In thin Edge Architecture deployments of the service, the Edge Hub resides in the same location as the CPI. The Edge Hub manages Internet of Things (IoT) Hub devices and modules for Horizon Edges. |
| Data Collected | Data Collected |
|
|
| Control Plane VM Hub | Regional Data Shards |
| The Control Plane VM Hub only stores data transiently. | The Regional Data shard is where the majority of customer content that the service leverages resides. This information communicates with the CPI via API. |
| Data Collected | Data Collected |
| Customer Content
Accounts
|
Active Directory Permission Requirements
The Horizon Cloud Service uses customer Active Directory (AD) for user management and entitlements. There are two types of Active Directory accounts required by the service that have been correlated in Table 2:
Table 2: Active Directory Permission Requirements
| Active Directory Account | Permission Requirements | Bind Type |
| Domain bind and domain bind aux account | | Generic Security Service Application Program Interface (GSSAPI) and NT LAN Manager Security Support Provider (NTLMSSP) binds are used for these accounts. Optionally toggle Microsoft Group Policy Object (GPO) of “Require Signing.” |
| Domain join and domain join aux account | Active Directory domain join and domain join aux account that has additional permissions to perform Sysprep operations and join computers to the domain, create new accounts, and more. | Only GSSAPI binds are used for these accounts. |
Horizon Cloud Service Next-Gen on Microsoft Azure uses an industry-standard approach/design to securely communicate with Microsoft Active Directory using Generic Security Services Application Program Interface -Generic Security Services Application Program Interface (SASL-GSSAPI). All communication with Active Directory is encrypted using Kerberos (SASL-GSSAPI); this is referred to as a “signed and sealed” connection. With SASL-GSSAPI, customers can help ensure that they can continue to follow Microsoft best practices to reject unsigned/unencrypted Lightweight Directory Protocol (LDAP) Requests, by having the LDAP “Require Secure Signing Policy” enabled on the Active Directory Servers with Horizon Cloud on Microsoft Azure.
Data Processing: Horizon 8 Deployments
How the service interacts with data varies depending on which type of deployment is set up. Table 3 is representative of a Horizon 8 Deployment:
Table 3: Data Processing Details for Horizon Next-Gen Horizon 8 Deployment
| What | Where | Who | Privacy Notes |
| End User Data | |||
| Data created by end users, for example, files, user settings, and user-installed applications. | This is stored only in the VDI desktops, which you deploy and configure. Omnissa has no access to this data. | End users access this data from within their VDI desktop sessions or RDSH app and desktop sessions. Omnissa does not have access, nor does it manage this data Customers manage access to the VMs or external file services that are under your control. | Because this data is authored by end users, it may contain personal data. You have full control of where this data is stored. The disk images storing this information may be encrypted. |
| Horizon Cloud Account Data | |||
| In a Horizon 8 implementation of Horizon Cloud Next Gen, this type of data would entail the following information:
| Certain Telemetry Data and Splunk credential data are stored encrypted in the Control Plane Instance (CPI) or Edge Hub Personally Identifiable Information data persists in the Regional Data Shard for Data Sovereignty considerations. | You own this data and manage it through the Administration Console. Omnissa can access this data to provide support and understand the service usage. The service itself can use the supplied information to facilitate certain functionality.
| The following personal data is stored:
The main use of the personal data is to identify the entitlement of end users to services (VDI desktops, remote applications, AV applications, Workspace ONE UEM policies), and the assignment of end users to resources (for example, linking an end user to a specific VDI desktop VM in a dedicated assignment). In addition, IT administrators are identified and given rights within the system. |
| IT Administrator | |||
| Data about your usage of the system, for example, login times, and audit information tracking changes to service configuration and operations. | Stored in the Regional Data Shard | You can see audit data. Omnissa can access this data to provide support and understand the service usage. | The following data is stored:
Audit and log data for system changes will identify the IT administrator who caused the change. |
| Licensing Data | |||
| Stored in the Regional Data Shard | You can see this data when you log in to the Horizon Cloud Administrative Console Omnissa can access this data to provide support and understand service entitlement. | This data enables customers to compare what they have chosen to how they are using the solution on a day-to-day basis This data enables Omnissa to help ensure the correct allocation of resources to customers as well as support other license-related activities. |
Data Separation
The Horizon Control Plane is a multitenant component of the service. Customer data is separated at the application layer and each tenant is encrypted with a per-tenant key. Refer to the other areas of this document for an overview of how data residency is achieved (such as customer data which resides within regional data shards).
Data Encryption
Data within the Horizon Control Plane is encrypted in-Transit via TLS 1.2+ and at-Rest (AES-256). Customers manage encryption of their workload capacities (for example, Horizon Edge), which include VDIs, VMs, multi-session VMs, images, and user data. Customers can also optionally configure the Horizon Cloud Service to communicate to the on-premises, corporate network via a VPN or ExpressRoute connection.
Key Management
Policies and procedures for key management for Horizon Cloud Service Next-Gen are in place to guide personnel on proper encryption key management in alignment with PCI-DSS requirements. Access to cryptographic keys is restricted to named personnel and all access is logged and monitored.
Backup Retention and Data Destruction
The backup process includes the destruction of data, both logical and physical.
Retention
Application logs for Horizon Cloud Service Next-Gen are stored for (90) days. Daily backups are stored for (30) days, and monthly backups are stored for (60) days.
The Horizon Control Plane is hosted within Microsoft Azure IaaS environments. Customers fully manage the data, such as routine backups and content, stored or accessed through Horizon Cloud Service. Omnissa provides disaster avoidance and recovery for top-layer and user-management interfaces which are owned and operated by Omnissa.
Logical Destruction
Refer to the Omnissa Cloud Services Guide available on the Omnissa Legal Center for our obligations regarding data retention and deletion at termination.
Physical Destruction
Omnissa partners with IaaS and managed service providers to support Horizon Cloud Service Next-Gen environments globally; these providers manage physical media destruction processes according to ISO 27001 and PCI-DSS requirements.
Disaster Recovery Shared Responsibilities
Horizon Control Plane services are hosted within Microsoft Azure IaaS environments. Customers fully manage the data, such as routine backups and content, stored or accessed through the Horizon Cloud Service on Microsoft Azure solution. Omnissa provides disaster avoidance and recovery for top-layer and user-management interfaces which are owned and operated by Omnissa.
Disaster Recovery is a shared responsibility between Omnissa and customers for the Horizon Cloud Service.
Customer Responsibility
Backups managed by Omnissa are only accessible to applicable members of Omnissa. Omnissa does not provide disaster recovery and backup processes for customer-hosted infrastructure and customer-managed data, such as desktops and virtual machine image data.
Horizon Control Plane Service Resiliency
Horizon Control Plane uses multiple Availability Zones in available regions. The Horizon Control Plane stores data in a fully replicated cluster across multiple fault domains in the service’s region. Furthermore, explicit offline backups of the data are taken and stored in the region for disaster recovery and high availability.
The infrastructure is designed to help ensure that customers will typically not notice a disruption during a component or system failure. Horizon Cloud Service Next-Gen provides region failover, in country, to account for a disaster. Furthermore, explicit offline backups of the data are taken and stored in the region for disaster recovery and high availability.
For example, data for customers hosted in the Horizon Control Plane in the U.S. is stored in backups also located in the U.S.
DR plans are rigorously tested against various disaster scenarios, including IaaS disasters within the region as well as tabletop exercises.
DR strategies include but are not limited to:
- The use of multiple Availability Zones in Active-Active configuration
- The use of Multiple Regions, in country, in Active-Passive configuration, in the event a full region outage occurs.
- Backups are encrypted in transit (TLS 1.2) and at rest (AES-256).
- Support staff review backup processes to help ensure data integrity.
Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO)
All Omnissa-managed Horizon Cloud Service components are covered by disaster recovery and business continuity processes; we have defined applicable RTO and RPOs in the table below. Omnissa does not provide disaster recovery and backup processes for customer-hosted infrastructure and customer-managed data.
Table 4: Horizon Cloud Service RTO and RPO
| Horizon Cloud Service | RTO | RPO |
| Horizon Control Plane | 4 hours | 4 hours |
| Horizon Cloud Service on Microsoft Azure – VMs and images | Data is customer-managed | Data is customer-managed |
| Horizon Subscription – VMs and images | Data is customer-managed | Data is customer-managed |
Roles and Responsibilities with Horizon Service
Horizon Cloud Next Gen follows a shared responsibility model between the three parties involved in the service. As prescribed by PCI-DSS standards, a Roles and Responsibilities Matrix is available and can be shared upon request.
Release Management and Maintenance
Omnissa has defined applicable Horizon Service uptime SLAs in the Omnissa Horizon Service SLA. Updates are a shared responsibility between Omnissa and our customers as outlined in the Omnissa Cloud Services Guide. SLA documentation and the Cloud Services Guide are available on the Omnissa Legal Center.
Release Schedules
Omnissa communicates feature releases and service announcements through Omnissa Docs, Omnissa Customer Connect, and by email.
Routine Maintenance
Occasionally, it is necessary for Omnissa to perform maintenance that has the potential to impact the availability of customer environments outside of scheduled maintenance windows, and Omnissa reserves the right to do so. A minimum of five days’ advance notice is given for routine maintenance.
Emergency Maintenance
Emergency maintenance is defined as potentially impactful maintenance activity that must be executed quickly due to an immediate, material threat to the security, performance, or availability of the Service Offering. Every attempt will be made to provide as much advance notice as possible, but notice depends on the severity and critical nature of the emergency maintenance.
Summary and Additional Resources
The intent is to provide readers with an understanding of how Horizon Cloud Service Next-Gen approaches cloud security, the key mechanisms, and processes that Omnissa uses to manage information security as well as describing shared responsibilities for providing security in a modern cloud computing environment.
Additional Resources
For more information about Horizon Cloud Service Next-Gen, you can explore the following resources:
- Horizon Cloud Service Compliance with 14 NCSC Cloud Security Principles
- Horizon Cloud Service Next-Gen Alignment with the ACSC ISM
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| November 21, 2024 | Updated for rebranding to Omnissa |
| August 7, 2024 | Whitepaper updates |
About the Author and Contributors
The following people contributed their knowledge and assistance with this document:
- Kevin Shaw, Sr. Program Manager, Customer Security Assurance
- Andrea Smith, Sr. Program Manager, Customer Security Assurance
- Andrew Osborn, Staff Technical Architect, Product
