Horizon Cloud Service compliance with 14 NCSC Cloud Security Principles
Introduction
The UK National Cyber Security Centre (NCSC) guidance for the 14 Cloud Security Principles describes a comprehensive cloud information security program to help enable organizations meet compliance and security obligations within the UK.
For the most up-to-date list of product audits and certifications, navigate to the Omnissa Trust Center. We also publish extensive documentation to familiarize organizations with our products and services on Docs and Tech Zone. Refer to the Cloud Services Guide for detailed descriptions of service components, as well as shared service administration responsibilities between Omnissa and the customer.
Note: You can find the definitions for acronyms used throughout this document in Acronyms used in the Workspace ONE and Horizon Security Series.
Purpose
This document addresses the Omnissa enterprise Information Security Program, as well as policies and procedures in relation to the NCSC guidance for the 14 Cloud Security Principles for the following cloud-hosted services: Omnissa Horizon® Cloud Service Next Gen. Within this whitepaper, these services are collectively referred to as “Horizon Cloud Service.”
Audience
This document is intended for UK-based Horizon Cloud Service commercial cloud administrators. It assumes at least intermediate knowledge of Horizon Cloud Service, and focuses on the policies, processes, and controls supporting the cloud-delivered services. Federal Risk and Authorization Management Program (FedRAMP), on-premises, and third-party offerings are not in scope for this document.
1. Data-in Transit Protection
Table 1: NCSC Guidance for protection of Data-in-Transit
| NCSC Guidance | |
| Principle | User data transiting networks should be adequately protected against tampering and eavesdropping. This should be achieved through a combination of: network protection - denying your attacker the ability to intercept data encryption - denying your attacker the ability to read data |
| Goals | You should be sufficiently confident that:
|
Data within the Horizon Control Plane is encrypted in-Transit via TLS 1.2+ and at-Rest (AES-256). Customers manage encryption of their workload capacities (for example, Omnissa Horizon® Edge), which include VDIs, VMs, multi-session VMs, images, and user data. Customers can also optionally configure the Horizon Cloud Service to communicate to the on-premises, corporate network via a VPN or ExpressRoute connection.
Horizon Cloud Service enforces strong TLS 1.2 encryption in transit to and from the Omnissa cloud environments over the public Internet to protect data against man-in-the-middle attacks. In transit encryption includes traffic between end-user devices and service, the service and other services (such as cloud connectors and customer systems), and internally within the service, where applicable. Firewalls, managed perimeter devices, and strong physical and logical access controls provide layered security within the Omnissa Horizon® Control Plane hosted environments.
2. Asset Protection and Resilience
Table 2: NCSC Guidance for Asset Protection and Resilience
| NCSC Guidance | |
| Principle | User data, and the assets storing or processing it, should be protected against physical tampering, loss, damage or seizure. |
| Goals | The aspects to consider are:
|
Omnissa models our Asset Management program after ISO 27001, NIST 800-53, and PCI-DSS standards, and Horizon Control Plane is hosted on Microsoft Azure globally. Microsoft Azure data centers have undergone PCI-DSS certification, SOC 2 Type 2 audits, and have achieved at least ISO 27001, in addition to ISO 27017 and 27018 certifications. As part of our vendor risk management program, Omnissa validates security controls in the SOC reports and certificates for our data center partners; appropriate agreements and service level agreements (SLAs) are in place.
Note: Microsoft publishes compliance and security information for their services. Reports and attestations can be acquired directly from these providers.
Visit the Omnissa Trust Center for the latest Horizon Cloud Service industry certifications.
2.1 Physical Location and Legal Jurisdiction
Table 3: NCSC Guidance for Physical Location and Legal Jurisdiction
| NCSC Guidance | |
| Principle | In order to understand the legal circumstances under which your data could be accessed without your consent, you must identify the locations at which it is stored, processed, and managed. You will also need to understand how data-handling controls within the service are enforced, relative to UK legislation. Inappropriate protection of user data could result in legal and regulatory sanction, or reputational damage. |
| Goals | You should understand:
|
Data Center Locations
Horizon Cloud Service provides access to the Horizon Control Plane that is hosted in Omnissa-managed Microsoft Azure instances. The Horizon Control Plane contains the Omnissa Horizon® Universal Console, which is also the broker located in the United States, Ireland, and Japan. Horizon Control Plane interacts with Regional Data Shards that store customer data located in the United States, Germany, UK, Ireland, Japan, and Australia. The Horizon Universal Console provides customer administrators access to orchestrate and manage the customer’s Horizon Service workloads.
Processing locations can be found in the sub-processor list available on the Omnissa Legal Center.
Omnissa Support Locations
Omnissa Global Customer Support Team operates in a follow-the-sun model from our locations around the world. Support may be provided from any of these global offices or other locations as our support team continues to expand to meet customer requirements.
Privacy & the UK General Data Protection Regulations (UK GDPR)
Omnissa complies with applicable obligations as a Data Processor. Omnissa enables customers to use services in a manner that enables the Customer to comply with applicable Data Protection Laws, including the UK GDPR, as a Data Controller, or as a Processor with respect to personal data. Omnissa has no direct relationship with the Users whose data it processes in connection with providing the Software and any related services. A User who seeks access, or who seeks to correct, amend, or delete inaccurate data should direct their query to the Customer. If the Customer requests Omnissa to modify or remove the data, we will respond to the Customer’s request in accordance with our data processing agreement with the applicable Customer or as may otherwise be required by applicable law. As the Data Controller, Customers can export solution data at any time from the administrative console. Horizon Cloud Service administration console enables administrators to manage the data from the web-based consoles to help organizations to simplify data protection and privacy within a wider UK GDPR compliance program:
- Access, update, or remove data directly from the consoles at any time.
- Export solution data at any time via CSV, as well as PDF and XLS formats.
See our Data Processing Addendum on the Omnissa Legal Center for more information about data transfers and our standard contractual clauses.
Scoped Data
Horizon Cloud Service gives customers data minimization, accuracy, and audit controls to help administrators protect end-user data. For an overview of the data collected by the service, refer to the Horizon Cloud Service Security Whitepaper.
2.2 Data Center Security
Table 4: NCSC Guidance for Data Center Security
| NCSC Guidance | |
| Principle | Locations used to provide cloud services need physical protection against unauthorized access, tampering, theft or reconfiguration of systems. Inadequate protections may result in the disclosure, alteration or loss of data. |
| Goals | You should be confident that the physical security measures employed by the provider are sufficient for your intended use of the service. |
As part of our vendor risk management program, Omnissa reviews audit reports, such as SOC reports for our data center partners; furthermore, appropriate agreements and service level agreements (SLAs) are in place. Microsoft Azure staff do not have logical access to the data hosted on the Omnissa-managed Horizon Cloud Service components.
Microsoft Azure has undergone various certifications and audits, including PCI-DSS certification, SOC 2 Type 2 audits, and ISO 27001/27017/27018 certifications. Microsoft Azure offers best-in-class physical security, including at ingress and egress points through 24/7/365 on-site monitoring, required badge access, mantraps, and so on.
Horizon Cloud Control Plane is hosted on multiple Availability Zones. Each data center facility is unique in its specific approach to the physical infrastructure, but Microsoft Azure follows the same general principles for power redundancy and physical access controls.
Various power, cooling, and fire suppression measures include redundant power to each component, with dual PDU and power in each cabinet: N+1 PDU and a generator fuel system for power, N+1 cooling and fire detection with early warning tools, and dual interlock pre-action sprinkler systems.
2.3 Data-at-Rest Protection
Table 5: NCSC Guidance for Data-at-Rest Protection
| NCSC Guidance | |
| Principle | To ensure data is not available to unauthorized parties with physical access to infrastructure, user data held within the service should be protected regardless of the storage media on which it’s held. Without appropriate measures in place, data may be inadvertently disclosed on discarded, lost or stolen media. |
| Goals | You should have sufficient confidence that storage media containing your data are protected from unauthorized access. |
Data within the Horizon Control Plane is encrypted at rest (via AES-256). Customers manage encryption of their workload capacities (for example, Horizon Edge), which include VDIs, VMs, multi-session VMs, images, and user data. Data in backup systems is also stored encrypted at rest. Access to all data storage systems is monitored and logged.
2.4 Data Sanitization
Table 6: NCSC Guidance for Data Sanitization
| NCSC Guidance | |
| Principle | The process of provisioning, migrating, and de-provisioning resources should not result in unauthorized access to user data. |
| Goals | You should be sufficiently confident that:
|
Under the shared responsibility model, Microsoft Azure manages hardware sanitization for the underlying systems supporting Omnissa cloud environments. Omnissa environments regularly overwrite or delete hosted customer data according to a defined schedule. The Omnissa Data Processing Addendum (“Deletion of Data”) and the Cloud Services Guide found on the Omnissa Legal Center govern data deletion for standard hosting agreements.
2.5 Equipment Disposal
Table 7: NCSC Guidance for Equipment Disposal
| NCSC Guidance | |
| Principle | Once equipment used to deliver a service reaches the end of its useful life, it should be disposed of in a way which does not compromise the security of the service, or user data stored in the service. |
| Goals | You should be sufficiently confident that:
|
Horizon Cloud Service is hosted on Microsoft Azure, and Omnissa has no access to the underlying hardware. Under the shared responsibility model, Microsoft Azure manages physical security controls, including system maintenance and equipment disposal, as well as physical access credential lifecycles. Microsoft Azure revokes access credentials for the physical hosting spaces as required. Microsoft Azure media destruction and decommissioning procedures are NIST 800-88 Rev 1 compliant.
Note: Azure publishes compliance and security information for their services. Reports and attestations can be acquired directly from Microsoft.
2.6 Physical Resilience and Availability
Table 8: NCSC Guidance for Physical Resilience and Availability
| NCSC Guidance | |
| Principle | Services have varying levels of resilience, which will affect their ability to operate normally in the event of failures, incidents or attacks. A service without guarantees of availability may become unavailable, potentially for prolonged periods, regardless of the impact on your business. |
| Goals | You should be sufficiently confident that the availability commitments of the service, including their ability to recover from outages, meets your business needs. |
Horizon Cloud Service is hosted within Microsoft Azure IaaS environments. Customers fully manage the data, such as routine backups and content, stored or accessed through the Horizon Cloud Service solution. Omnissa provides disaster avoidance and recovery for top-layer and user-management interfaces, which are owned and operated by Omnissa.
Disaster Recovery is a shared responsibility between Omnissa and customers for the Horizon Cloud Service.
Omnissa Business Continuity and Disaster Recovery strategies include data and hardware redundancy using Microsoft Azure Availability Zones, network configuration redundancy and backups, and regular testing exercises. Omnissa maintains inventories of critical assets, including asset ownership, and Omnissa maintains an inventory of critical supplier relationships.
Horizon Cloud Service environments meet strict requirements for high availability and redundancy. Omnissa eliminates any single point of failure through Microsoft Azure Availability Zones, network, power, and clustering of key components. Horizon Cloud Service environments are hosted on geographically resilient Microsoft Azure Availability Zones.
Customers can review uptime status, planned maintenance, and historical incident data on a service status page.
3. Separation Between Users
Table 9: NCSC Guidance for Separation Between Users
| NCSC Guidance | |
| Principle | A malicious or compromised user of the service should not be able to affect the service or data of another. |
| Goals | You:
|
Multi-tenancy in Horizon Cloud Service
The Horizon Control Plane is a multitenant component of the service. Customer data is separated at the application layer, and each tenant is encrypted with a per-tenant key.
Regional Data Shards
Data shards are deployed across multiple regions and store customer data. Customers choose a region to store their data upon their first login to the service. This approach not only helps ensure a more secure method of storing customer data but also provides greater levels of scalability. Communications between the Regional Data Shard and Horizon CP VM Hub are conducted over the MQTT protocol, which leverages encryption in transit and at rest.
4. Governance Framework
Table 10: NCSC Guidance for Governance Frameworks
| NCSC Guidance | |
| Principle | The service provider should have a security governance framework which coordinates and directs its management of the service and information within it. Any technical controls deployed outside of this framework will be fundamentally undermined. |
| Goals | You should have sufficient confidence that the service has a governance framework and processes which are appropriate for your intended use. Good governance will typically provide:
|
Information Security Management System (ISMS) Governance
The Omnissa ISMS leverages guidance from industry best practices and regulatory standards, including NIST SP 800-53, PCI-DSS, and ISO 27001. Omnissa maintains written ISMS, and we perform annual reviews and audits of the program to help ensure the integrity of our hosted offering. Our ISMS considers the following objectives:
- The threats, vulnerabilities, and likelihood of occurrence identified by assessment of risks relative to the overall business strategy and objectives.
- The legal, statutory, regulatory, and contractual requirements that Omnissa and relevant and applicable partners, contractors, and service providers must comply with; and
- The principles, objectives, and business requirements for information handling, processing, storing, communicating, and archiving developed by Omnissa to support its business operations.
Omnissa has designated a Chief Information Security Officer to oversee our ISMS. For comprehensive security through the organization, multiple groups within Omnissa have a role in establishing, maintaining, monitoring, and operating the security practices for the ISMS:
- Incident and Vulnerability Management
- Security Engineering and Security Operations
- Human Resource Security
- Legal
- Governance Risk and Compliance
Regulatory Governance
We continuously review laws and regulations to appropriately respond to the evolving legal and privacy landscapes. Our in-house legal department is involved in the establishment and review of privacy policies to review which privacy laws and regulations are applicable to the jurisdictions in which we operate.
5. Operational Security
Table 11: NCSC Guidance on Operational Security
| NCSC Guidance | |
| Principle | The service needs to be operated and managed securely in order to impede, detect or prevent attacks. Good operational security should not require complex, bureaucratic, time consuming or expensive processes. |
| Goals | There are four elements to consider:
|
Omnissa considers configuration and change management, vulnerability management, protective monitoring, and incident management procedures in our ISMS. We strive towards operating and managing all Horizon Cloud Service environments using a consistent ISMS framework. Third-party and internal assessors validate these processes at least annually under the Omnissa ISMS program. These audits are essential to our continuous improvement programs.
For the most up-to-date list of product audits and certifications, navigate to the Omnissa Trust Center.
5.1 Configuration and Change Management
Table 12: NCSC Guidance for Configuration and Change Management
| NCSC Guidance | |
| Principle | You should have an accurate picture of the assets which make up the service, along with their configurations and dependencies. |
| Goals | You should have confidence that:
|
Omnissa maintains a formal configuration management policy based on industry best practices to harden the cloud environment; revisions and exceptions to the configuration management policy are processed through a documented change management policy to help ensure the confidentiality, integrity, and availability of our hosted offering.
Our change management policy defines controlled changes to configurations in our production environments; change processes include required approval, testing, implementation, and contingency plans. Changes undergo standard testing and validation processes, and if, for any reason, a change is unsuccessful or does not pass the required testing phases, our teams execute a fallback plan.
Microsoft Azure manages the underlying hardware asset registers as well as configuration and change management procedures for Omnissa-managed Horizon Cloud Service environments according to PCI-DSS and ISO 27001, 27017, and 27018. Microsoft Azure media destruction and decommissioning procedures are NIST 800-88 Rev 1 compliant.
Note: Azure publishes compliance and security information for their services. Reports and attestations can be acquired directly from Microsoft.
5.2 Vulnerability Management
Table 13: NCSC Guidance for Vulnerability Management
| NCSC Guidance | |
| Principle | Service providers should have a management process in place to identify, triage, and mitigate vulnerabilities. Services which don’t, will quickly become vulnerable to attack using publicly known methods and tools. See our guide on vulnerability management for more detail. |
| Goals | You should have confidence that:
|
Omnissa employs a rigorous Vulnerability Management program as part of our Information Security Program. We follow guidance established in NIST SP 800-30 and PCI-DSS, and we conduct regular risk and vulnerability assessments to identify, assess, and remediate emerging threats. When potential vulnerabilities are discovered, we follow a documented procedure to prioritize and deploy necessary patches within the cloud environment. Remediation efforts are prioritized and applied against critical and high-risk issues.
We identify vulnerabilities and threat-sources through subscribing to relevant mailing lists, conducting interviews with various members of the cloud community, attending conferences, and mapping data to the business landscape. Internally managed scanning tools are regularly updated to help ensure quick detection of emerging threats.
Defined change management procedures help ensure patches are compatible with the production environment. Rollback plans are captured as part of change management processes where required.
5.3 Protective Monitoring
Table 14: NCSC Guidance for Protective Monitoring
| NCSC Guidance | |
| Principle | A service which does not effectively monitor for attack, misuse, and malfunction will be unlikely to detect attacks (both successful and unsuccessful). As a result, it will be unable to quickly respond to potential compromises of your environments and data. |
| Goals | You should have confidence that:
|
Omnissa-managed cloud environments are secured with layered defenses, including but not limited to, access control mechanisms, firewalls, malware controls, auditing mechanisms, and network controls. Intrusion Detection Systems (IDS) monitor network traffic, log suspicious activity, and alert on suspicious network activity within Omnissa cloud environments.
Omnissa Cloud Operations monitor cloud environments 24/7 for alerts or suspicious activity. Omnissa follows the Fault, Configuration, Accounting, Performance, and Security (FCAPS) model to monitor the cloud environment and has configured the system to notify IT personnel if the central processing unit (CPU) utilization is too high, disk space limited, memory issues, key service failures, bandwidth utilization, power consumption, or other defined performance items. IaaS providers offer built-in security and monitoring controls.
In alignment with PCI-DSS standards, Omnissa has enabled full auditing capabilities on all environments to enable the reconstruction of security incidents and events. We have provided a description of incident response management for the following section, 5.4 Incident management and audit capabilities in Principle 12. Audit information for users.
5.4 Incident Management
Table 15: NCSC Guidance for Incident Management
| NCSC Guidance | |
| Principle | Unless carefully pre-planned incident management processes are in place, poor decisions are likely to be made when incidents do occur, potentially exacerbating the overall impact on users. |
| Goals | You should have confidence that:
|
Our Incident Response program plans and procedures are developed in alignment with ISO 27001 and PCI-DSS standards. For the purpose of security and incident management, we maintain contacts with industry bodies, risk and compliance organizations, local authorities and regulatory bodies. Points of contact are regularly updated to ensure direct compliance liaisons have been established and to be prepared for a forensic investigation requiring rapid engagement with law enforcement.
We require staff to report information security events as quickly as possible per corporate policies. At a minimum, these situations include:
- Ineffective security controls or access violations
- Breach of information integrity, confidentiality or availability expectations
- Human errors
- Non-compliances with policies or guidelines
- Breach of physical security arrangements
- Uncontrolled system changes
- Malfunction of software or hardware
Incident Management Plan
Omnissa follows a formal Incident Management Plan that is maintained as part of our overall Information Security Program. Incidents are reported to the appropriate Cloud Operations team for categorization and resolution; issues are escalated to senior management according to a pre-defined protocol. We track issue alerts, responses, and resolutions throughout completion: Incident response teams prepare postmortem report to internal stakeholders and our Information Security Governance Committee for review. We use email announcements to maintain open lines of communication between support staff and customers regarding change management events, incident events, and problem events.

Figure 1: Omnissa Incident Response Cycle
We periodically review incidents and update our incident response program as needed based on: Incident root cause and incident pattern analysis, as well as potential changes in the internal control environment and legislation. Incident response plans are tested at least once annually whether a security incident has occurred or not.
- Results of the quarterly review are reported to management.
- Key metrics are defined, tracked, and reported to senior management on a yearly basis or as needed.
6. Personnel Security
| NCSC Guidance | |
| Principle | Where service provider personnel have access to your data and systems you need a high degree of confidence in their trustworthiness. Thorough screening, supported by adequate training, reduces the likelihood of accidental or malicious compromise by service provider personnel. |
| Goals | You should be confident that:
|
Omnissa maintains formal personnel security procedures as part of our Information Security Program, which includes comprehensive background checks. All employees acknowledge company policies and sign a Non-Disclosure Agreement (NDA). Information security awareness training is mandatory; completion and end-of-course testing are recorded. Annual refreshers are required.
Background checks are performed in accordance with pre-employment background check protocols applicable to the region and are subject to local laws and regulations. As a general matter, Human Resources (HR) Operations initiate and oversee the background check process. Results are treated as confidential personnel records, made available only to those outside HR Operations with a business reason to review or be consulted regarding the results.
Subject to applicable law, we typically perform the following background checks:
- A verification of the applicant’s recent work history
- Confirmation of highest degree obtained, and professional qualifications required for the position
- Review of certain criminal records, consistent with availability of records and limitations imposed by applicable law
All employees are responsible for maintaining company sensitive information confidentiality, storing, and managing passwords appropriately, being aware of customer privacy concerns, and remaining vigilant for security threats (such as social engineering, phone impersonations) always. Violations of the information security policies are subject to disciplinary proceedings, including termination and legal action, as necessary.
- We require staff to report information security events as quickly as possible per corporate policies to help detect external threat actors or malicious insiders. At a minimum, these situations include:
- Ineffective security controls or access violations
- Breach of information integrity, confidentiality, or availability expectations
- Human errors
- Non-compliance with policies or guidelines
- Breach of physical security arrangements
- Uncontrolled system changes
- Malfunction of software or hardware
- Bring your own (BYO) devices are not used to maintain cloud environments. Corporate-issued mobile devices are subject to automatic compliance policies that require and specify approved OS, patches, and applications. BYO devices must be enrolled in Workspace ONE UEM to access corporate information and are subject to additional corporate-mandated security controls.
- Access to production environments is secured through a combination of VPN and bastion servers using MFA and directory credentials. Production environment access is monitored and logged.
Initial and annual information security awareness is delivered through a Learning Management System (LMS). The LMS electronically records training proof of completion for employees. Cloud Operations personnel receive additional, specialized training as they assume job roles and responsibilities within 30 days of beginning work; training must be completed before authorizing access to cloud environment systems.
Topics include:
|
|
7. Secure Development
Table 16: NCSC Guidance for Secure Development
| NCSC Guidance | |
| Principle | Services should be designed and developed to identify and mitigate threats to their security. Those which aren’t, may be vulnerable to security issues which could compromise your data, cause loss of service or enable other malicious activity. |
| Goals | You should be confident that:
|
The Omnissa SDL program is designed to identify and mitigate security risks during Omnissa software product planning and development phases. The development of the Omnissa SDL has been heavily influenced by industry best practices and organizations such as SAFECode (the Software Assurance Forum for Excellence in Code) and Software Assurance Maturity Model (SAMM). SAFECode and SAMM are two prominent initiatives in the software security industry that aim to improve software security practices and help organizations enhance the security of their software development lifecycle.
The Omnissa SDL is periodically assessed for its effectiveness at identifying risk, and new techniques are added to SDL activities as they are developed and mature. The program is supported by a security engineering team that performs security design reviews and thorough security testing.
Omnissa encourages continuous employee training through programs that subsidize certification attempts (for example, ISC2’s Certified Information Systems Security Professional (CISSP) and Certified Cloud Security Professional (CCSP)), relevant conference passes, training classes, and subscriptions to leading online training platforms for enhancing technical and business acumen. Additionally, employees can use job rotation programs designed to reignite and broaden employee work experience.
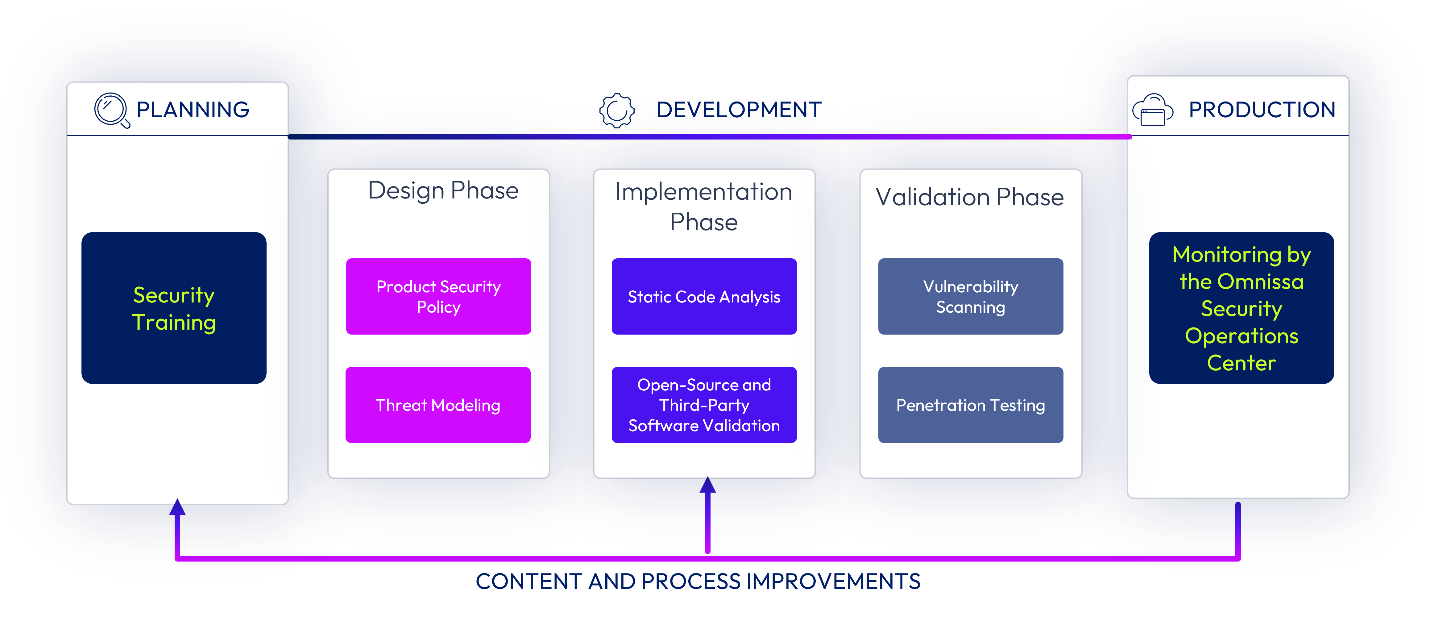
Figure 2: Omnissa SDLC Process
To securely deliver continuous product improvements, we have incorporated DevOps processes into our SDL where applicable. Continuous Delivery (CD) pipelines have logging enabled. Development teams can push code as a check-in, and this process requires multiple code reviews in parallel with unit and integration testing. After successful completion of pass/fail tests, code is deployed into the internal environment and then to UAT and hosted production environments.
Omnissa performs extensive penetration tests against our applications and services. The penetration tests are generally divided into three different phases, focusing on identifying high-impact vulnerabilities that could lead to exploitation, theft of data, and overall privilege escalation. The tests typically follow a method intended to simulate real-world attack scenarios and threats that could critically impact the data privacy, integrity, and overall business reputation. Our third-party penetration testers hold numerous certifications ranging from OCSP to SANS certifications.
In alignment with PCI-DSS requirements, we encourage continuous employee training through annual training in up-to-date secure coding techniques, including how to avoid common coding vulnerabilities. Additionally, employees can participate in job rotation programs designed to reignite and broaden employee work experience.
8. Supply Chain Security
Table 17: NCSC Guidance for Supply Chain Security
| NCSC Guidance | |
| Principle | The service provider should ensure that its supply chain satisfactorily supports all the security principles which the service claims to implement. |
| Goals | You understand and accept:
|
Omnissa engages sub-processors to provide hosting services for the Horizon Cloud Service environments. We enter into agreements with our sub-processors to meet baseline security requirements and to adhere to applicable data protection laws. We work with reputable service providers and perform software validation for OSS/TP to safeguard against known vulnerabilities prior to incorporation within our products and services.
Horizon Cloud Service environments are deployed in Microsoft Azure and MongoDB. Sub-processors are outlined per service in the Sub-processors Addendums available in the Omnissa Legal Center.
We have also established compliance standards and service expectations with our data center providers and regularly audit data center controls, procedures, and independent assessments to assess and minimize service provider risk:
- SLAs are in place with our data center providers that stipulate baseline compliance standards and security requirements.
- We also review published SOC reports and PCI-DSS/ISO certifications, DR plans, and other applicable policies (such as access control policies, physical and environmental plans) of the processor.
- Additional information concerning data center sub-processors is outlined in Principle 2. Asset protection and resilience.
9. Secure User Management
Table 18: NCSC Guidance for Secure User Management
| NCSC Guidance | |
| Principle | Your provider should make the tools available for you to securely manage your use of their service. Management interfaces and procedures are a vital part of the security barrier, preventing unauthorized access and alteration of your resources, applications and data. |
| Goals | The aspects to consider are:
|
Omnissa shares the responsibility for securing Horizon Cloud user management with customer or partner administrators.
- Horizon Cloud customer administrators manage end-user and administrator accounts through the web consoles. Customers can use their existing Active Directory infrastructure for user authentication and management. For added security, customers can integrate with two-factor authentication solutions, such as RSA SecurID and RADIUS, and smart card authentication solutions. Additionally, configure single sign-on using SAML, Kerberos, or True SSO. Using Horizon Cloud with the Unified Access Gateway also supports integration with Okta and Ping. Omnissa applications are subject to continuous testing to confirm control efficiency.
- We additionally implement strong access controls in accordance with role-based access control, separation of duties, and the principle of least privileges. Production environment access is secured through a combination of VPN and bastion servers using MFA and directory credentials. System sessions are set to an idle timeout of 15 minutes. Logs are in place to review support staff access to all systems and environments. Quarterly User Access Reviews are conducted to review privileged access and to remove/deactivate accounts with 90 days of inactivity.
9.1 Authentication of Users to Management Interfaces and Support Channels
Omnissa Internal Support Channels
Omnissa employees use an internal web ticketing system, dedicated support line, or self-service password tool to reset credentials. Users are verified prior to credential reset or temporary password delivery. Where temporary credentials are issued, users will be required to change passwords upon initial login. Cloud environment privileged credentials are reset and fully tracked through an internal ticketing system.
Customer Support Channels
To validate customer support requests, Omnissa assigns a unique customer number to each customer contact for the purpose of technical support. The customer number is created for users either when users create an Omnissa Customer Connect profile themselves, or when a new order is placed for users that do not have an Omnissa Customer Connect profile. Customer numbers are unique to individuals (similar to a personal identification number).
9.2 Separation and Access Control within Management Interfaces
Customer Managed Users – Overview
Horizon Cloud Service administrators can manage Horizon Cloud from any web browser, anywhere in the world, by simply logging into secure consoles. These consoles do not need to be downloaded, installed or configured, saving their IT department time and resources. Horizon Cloud Service portals may include:
- Horizon Cloud Service Administrator Console
- Omnissa Access Administrator Console
Administrative and end-user portals fully encrypt data in transmission with TLS over the public Internet, in alignment with PCI-DSS standards.
Horizon Cloud and the associated administrative portals undergo rigorous internal and third-party penetration and vulnerability assessments as a crucial step of our SDL. Issues, where uncovered, are tracked through remediation and prioritized according to criticality.
Customer Managed Users – Creation
Horizon Cloud Service integrates with directory services to inherit existing identity permission structures and credentials. Horizon Cloud Service integrates with Omnissa Access to extend existing directory infrastructure and provide a seamless Single Sign-On (SSO) experience to web, mobile, cloud, and legacy applications.
Customer Managed Users – Role-based Access Controls
Each administrative console records activity and provides detailed application-level logs of the events or actions taking place. The solution maintains and displays this information to authorized users for auditing and reporting purposes. In the process of authenticating to the cloud-based administrative console, after authenticating to the initial login screen using an Omnissa Customer Connect account, the individual from a customer organization enters their Active Directory user account credentials in the second login screen, according to the Active Directory domain they have registered with the environment. The system provides predefined roles that they can assign to the various Active Directory groups. These Active Directory domain-related roles control which areas of the console are viewable and enabled or viewable and deactivated, as the logged-in person navigates through the console.
Horizon Cloud Service Administrative Console and Omnissa Access Console include numerous built-in roles with varying levels of access.
Navigate to Omnissa Docs for full descriptions of available pre-configured and customizable administrator roles across the Horizon Cloud Service platform.
10. Identity and Authentication
Table 19: NCSC Guidance for Identity and Authentication
| NCSC Guidance | |
| Principle | All access to service interfaces should be constrained to authenticated and authorized individuals. Weak authentication to these interfaces may enable unauthorized access to your systems, resulting in the theft or modification of your data, changes to your service, or a denial of service. |
| Goals | You should:
|
Omnissa Authentication Policies
Access privileges are enforced using role-based access control, separation of duties, and the principle of least privileges. Production environment access is secured through a combination of VPN and bastion servers using MFA and directory credentials. In accordance with ISO 27001 and PCI-DSS, access is restricted to authorized members of applicable teams, and system sessions are set to an idle timeout of 15 minutes. Logs are in place to review support staff access to all systems and environments. Quarterly User Access Reviews are conducted to review privileged access and to remove/deactivate accounts with 90 days of inactivity. Passwords:
- Cannot be from a dictionary word
- Cannot be a name
- Cannot be repeated over a given period
Customer-Managed Authentication Policies
Horizon Cloud Service integrates with directory services to inherit existing identity permission structures and existing credentials. Omnissa Access uses SAML 2.0 assertions to federate users with existing credentials. There are multiple authentication mechanisms available for customers to access their virtual desktops to include directory integration, MFA, and SSO with SAML via Omnissa Access.
11. External Interface Protection
Table 20: NCSC Guidance for External Interface Protection
| NCSC Guidance | |
| Principle | All external or less trusted interfaces of the service should be identified and appropriately defended. If some of the interfaces exposed are private (such as management interfaces) then the impact of compromise may be more significant. You can use different models to connect to cloud services which expose your enterprise systems to varying levels of risk. |
| Goals | You:
|
For customers using Omnissa Access to facilitate identity federation, Omnissa Access enforces TLS data encryption between cloud environments and service clients (such as web consoles and user endpoints) over the public Internet. To protect Omnissa Access, we use Amazon Web Service (AWS) Virtual Private Clouds (VPCs), security groups, and subnets to connect systems in different security domains. All external traffic passes through firewalls before reaching proxy servers. For more information on the security controls used by Omnissa Access cloud service, see the Workspace ONE Cloud Services Security Overview.
Omnissa Access to Production
Access privileges are enforced using role-based access control, separation of duties, and the principle of least privileges. Production environment access is secured through a combination of VPN and bastion servers using MFA and directory credentials. In accordance with ISO 27001 and PCI-DSS, access is restricted to authorized members of applicable teams, and system sessions are set to an idle timeout of 15 minutes. Logs are in place to review support staff access to all systems and environments. Quarterly User Access Reviews are conducted to review privileged access and to remove/deactivate accounts with 90 days of inactivity.
Horizon Service Authentication
Horizon Cloud Service web interfaces and user endpoints are secured with TLS 1.2 for data in transit over the public Internet. See Principle 9 and Principle 10 for an overview of service components and security. Note that customer administrators access and manage the Horizon Cloud Service platform from web-based consoles and do not directly manage the cloud environment.
Continuous Testing
In alignment with PCI-DSS, Omnissa performs extensive internal and external network penetration tests at least annually. The penetration tests are generally divided into three different phases, focusing on identifying high-impact vulnerabilities that could lead to exploitation, theft of data, and overall privilege escalation. The tests typically follow a method intended to simulate real-world attack scenarios and threats that could critically impact the data privacy, integrity, and overall business reputation.
12. Secure Service Administration
Table 21: NCSC Guidance for Secure Service Administration
| NCSC Guidance | |
| Principle | Systems used for administration of a cloud service will have highly privileged access to that service. Their compromise would have significant impact, including the means to bypass security controls and steal or manipulate large volumes of data. |
| Goals | You should:
|
Omnissa secures highly privileged access to the Horizon Cloud Service through a layered defense model that requires strong authentication prior to performing service management functions. Personnel must use Omnissa-owned equipment when accessing production environment systems. Omnissa centrally manages patching, antivirus, and data loss prevention (DLP) software on corporate endpoints through Workspace ONE UEM as our internal end-user device management platform.
Access to Omnissa cloud environments is restricted to approved employees with MFA. Employees are prohibited from transferring customer data from the production environment. All access is logged and monitored. Omnissa Cloud Operations personnel use separate user accounts for administration and normal user activities. Note that customer administrators access and manage the Horizon Cloud Service platform from web-based consoles and do not directly manage the Cloud environment.
13. Audit Information for Users
Table 22: NCSC Guidance for Audit Information for Users
| NCSC Guidance | |
| Principle | You should be provided with the audit records needed to monitor access to your service and the data held within it. The type of audit information available to you will have a direct impact on your ability to detect and respond to inappropriate or malicious activity within reasonable timescales. |
| Goals | You should be:
|
Omnissa Managed Systems
Omnissa has security controls in place to reduce the risk of unauthorized access to sensitive information in the production environment. Horizon Cloud Service environments have intrusion detection mechanisms in place. The service continuously collects and monitors the environment logs, which are correlated with both public and private threat feeds, to spot suspicious and unusual activities.
Omnissa has a formal Security Incident Response team that facilitates all Incident Response activities that comply with industry standards for legally admissible chain of custody management processes and controls. Omnissa has a formal Incident Response team that facilitates all Incident Response activities, which uses legally admissible forensic data collection and analysis techniques. Customers can request access to restricted audit data through the Omnissa Customer Connect support ticketing systems.
Application Logging
Horizon Cloud Service and Omnissa Access application logs accessible by customers are retained for 90 days.
- The Activity Logs page within the Horizon Console tracks both administrator and end-user activity.
- The Omnissa Access admin console provides audit event reports for resource entitlements for groups and users. Audit events include time, date, and identity of administrative changes to permissions and app access.
14. Secure Use of the Service
Table 23: NCSC Guidance for Secure Use of the Service
| NCSC Guidance | |
| Principle | The security of cloud services and the data held within them can be undermined if you use the service poorly. Consequently, you will have certain responsibilities when using the service in order for your data to be adequately protected. |
| Goals | You:
|
Customers manage users, data, and configurations associated with the Horizon Cloud Service platform as well as on-premises connectors (for example, Horizon Cloud Connector) and integration points. Omnissa clearly outlines shared responsibilities with clients. Refer to the applicable details within the Cloud Service Guide available in the Omnissa Legal Center.
Note: Roles and responsibilities for products and services licensed through partners may differ depending on the purchasing model.
Documentation
Customers can access a comprehensive and easily accessible catalog of training resources on Omnissa Docs, Omnissa Customer Connect, and Omnissa Knowledgebase, which provides varying levels of product knowledge and technical expertise, depending on the administrator role.
Training
After implementation, access self-guided training resources, including product documents, instructional videos, and our knowledge base – all available 24/7.
- Product Documents – Getting started articles, configuration guides, and technical whitepapers that cover key topics and address common challenges
- Instructional Videos – Our video library consists of succinct instructional videos organized by training curriculum, topic, and experience level to help you manage your own training schedule
- Knowledge Base – Access valuable tips and tricks written by product experts, product documents, and the latest webinars and announcements
Customers can also leverage Omnissa Learning for training and certification programs designed to grow our customers’ skills and validate their ability to leverage all the opportunities made possible by Omnissa solutions.
Summary and Additional Resources
This whitepaper documents alignment with the 14 NCSC Cloud Security Principles for Omnissa Horizon Cloud Service. The NCSC describes a comprehensive cloud information security program to help enable organizations meet compliance and security obligations within the UK.
Additional Resources
For more information about Horizon Cloud Service, you can explore the following resources:
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 11/20/2024 |
|
About the Author and Contributors
The following people contributed their knowledge and assistance with this document:
- Andrea Smith, Sr. Program Manager, Customer Security Assurance.
- Andrew Osborn, Omnissa alumni.
Feedback
Your feedback is valuable.
To comment on this paper, contact Omnissa Technical Marketing at tech_content_feedback@omnissa.com.

