Configuring the Tunnel Edge Service: Workspace ONE Operational Tutorial
Workspace ONE UEM 2212Unified Access Gateway 2309
Overview
This operational tutorial is provided to help you with your Omnissa Workspace ONE environment and walks through configuring the Tunnel edge service on Unified Access Gateway.
Audience
This operational tutorial is intended for IT professionals and Workspace ONE UEM administrators of existing production environments.
Knowledge of additional technologies such as network, VPN configuration, Workspace ONE Intelligence, and Workspace ONE UEM is also helpful.
Configuring Tunnel Edge Services on Unified Access Gateway
The Tunnel is an edge service on Unified Access Gateway, which enables Per-App VPN on managed mobile devices to secure access to internal resources. Tunnel allows individual applications to authenticate and securely communicate with back-end resources over HTTP(S) or TCP for Per-App Tunnelling.
This section helps you to configure the Tunnel edge service on Unified Access Gateway.
Procedures include:
- Enrolling a testing per-app VPN on an iOS device
- Deploying Workspace ONE Tunnel
- Configuring Tunnel in the Workspace ONE UEM console
- Deploying Unified Access Gateway and enabling Tunnel edge service through PowerShell
- Defining network traffic rules for Per-App Tunnel
- Configuring VPN profile and deploying Workspace ONE Tunnel client
- Validating access to internal websites based on device traffic rules using an enrolled iOS device
The steps are sequential and build upon one another, so make sure that you complete each step before going to the next step.
Tunnel Components
Before deploying Unified Access Gateway with Tunnel, it is important to understand the Tunnel components available to provide secure internal access to your device fleet.
Tunnel consists of Per-App Tunnel; this component runs independently as a separate service on the Unified Access Gateway appliance to enable internal access for an end-user device.
The Tunnel feature enables an SSL VPN connection on a per-application and full-device basis for any public or internal application. This feature leverages the native Per-App VPN functionality of the operating system such as Android, iOS, macOS, and Windows platforms, and a device-side VPN client application to initiate a VPN connection when an enabled application is started. The Workspace ONE Tunnel client application installed on the user's device maintains an allowlist of applications that should use VPN, handle certificates for enabled applications, and initiate the VPN connection on behalf of the user.
Settings for the Per-App Tunnel features are pushed to the device in a device profile with the VPN payload configured. Each platform offers slightly different variations of the Per-App Tunnel feature, but all platforms require the presence of the Workspace ONE Tunnel client to use Per-App VPN functionality.
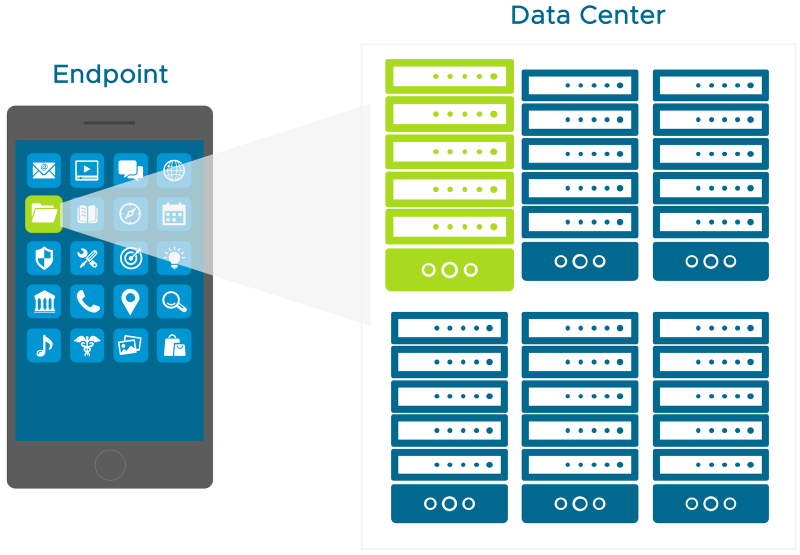
Tunnel Edge Service on Unified Access Gateway
The Tunnel works as an edge service on Unified Access Gateway, and can automatically be configured during deployment using PowerShell, or after deployment, using the Unified Access Gateway administration console.
The Unified Access Gateway appliance OVF template contains several edge services, beyond Tunnel. The template includes Content Gateway, Secure Email Gateway, Web Reverse Proxy, and Horizon. The appliance runs from a standard hardened image.
Tunnel Deployment Model on Unified Access Gateway
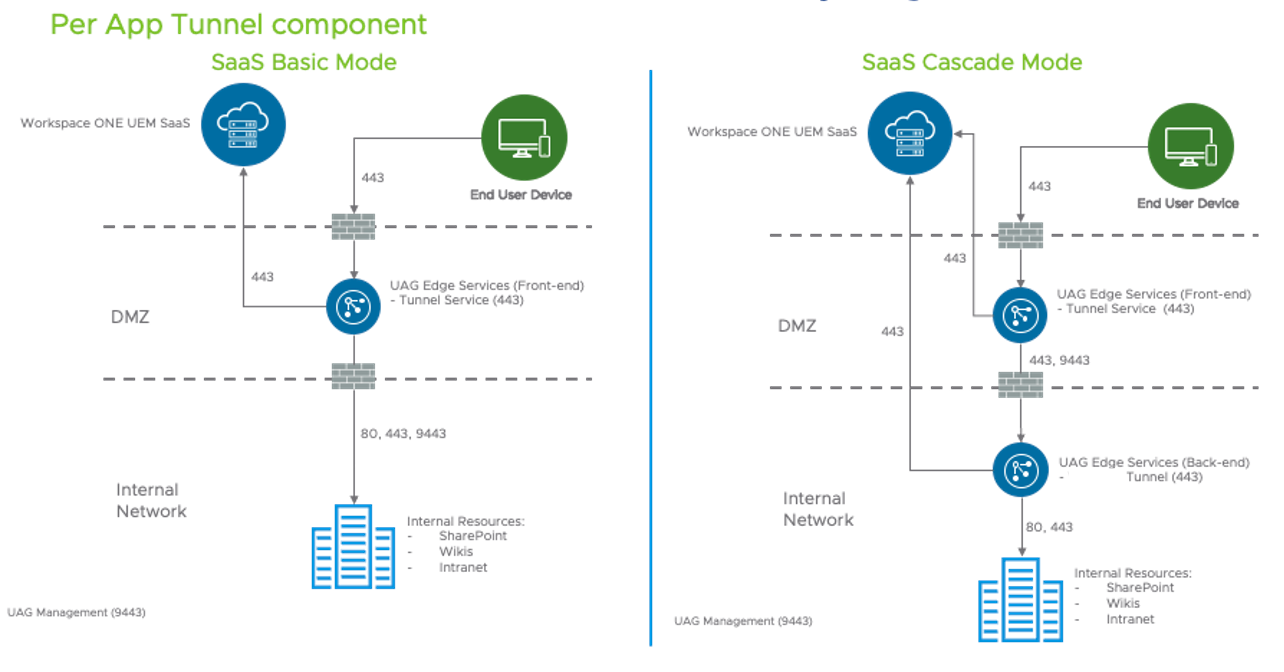
Figure 1: Tunnel edge service on Unified Access Gateway
The Tunnel can be deployed in one of two configurations:
- Basic Mode consists of a single Unified Access Gateway appliance, typically situated in the DMZ, where devices can connect to the appropriate port for each feature, authenticate with a certificate issued from the Workspace ONE UEM Console, and connect to internal sites.
- The Cascade Mode option allows devices to authenticate to the front-end tunnel on the Unified Access Gateway appliance located in the DMZ, then connect to the back-end tunnel enabled on another Unified Access Gateway appliance over a single port and then access internal resources.
TLS Port Sharing
TLS port sharing is an important component of Unified Access Gateway that allows the use of a single port (443) for multiple edge services. It is enabled by default on Unified Access Gateway whenever multiple edge services are configured to use TCP port 443. Supported edge services are Tunnel (Per-App Tunnel component only), Content Gateway, and Web reverse proxy.
When enabling Per-App Tunnel and Content Gateway edge services with TLS Port Sharing, a TLS SNI rule is automatically created to forward incoming traffic on port 443 to the edge service port 10443 for Content Gateway and 8443 for Per-App Tunnel, respectively. After that, the edge service communicates with the internal resource based on the original request.
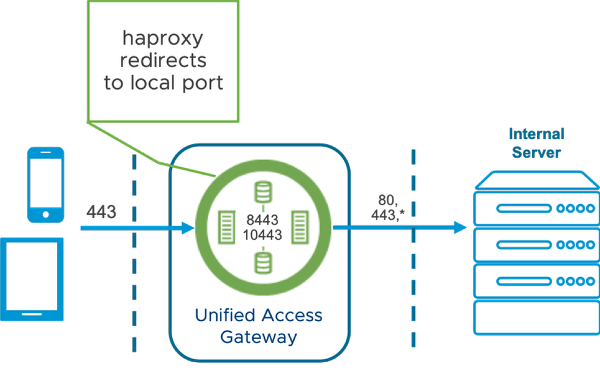
Figure 2: TLS port sharing
Note: To enable port sharing on TCP port 443, ensure that each configured edge service has a unique external host name pointing to Unified Access Gateway. When port sharing is not enabled, each edge service is assigned to a different port and can use the same external name.
Basic Model
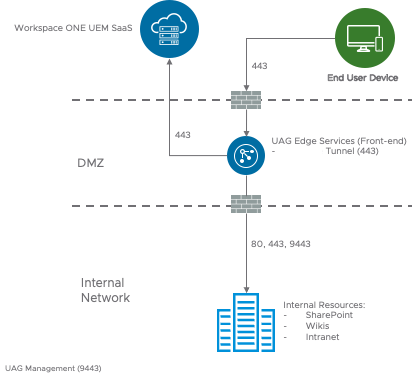
Figure 3: Basic deployment model
The Basic deployment model includes a single Unified Access Gateway appliance, which requires a public host name and a dedicated port for each component.
The default port for Per-App Tunnel is 443. When TLS Port Sharing is deactivated, the Per-App Tunnel default port is 8443.
These ports are secured with a Workspace ONE UEM-issued tunnel certificate, issued from the device root certificate in your Workspace ONE UEM environment or a public third-party SSL certificate.
Note: TLS Port Sharing is enabled by default in Unified Access Gateway 3.3 and later.
Cascade Model
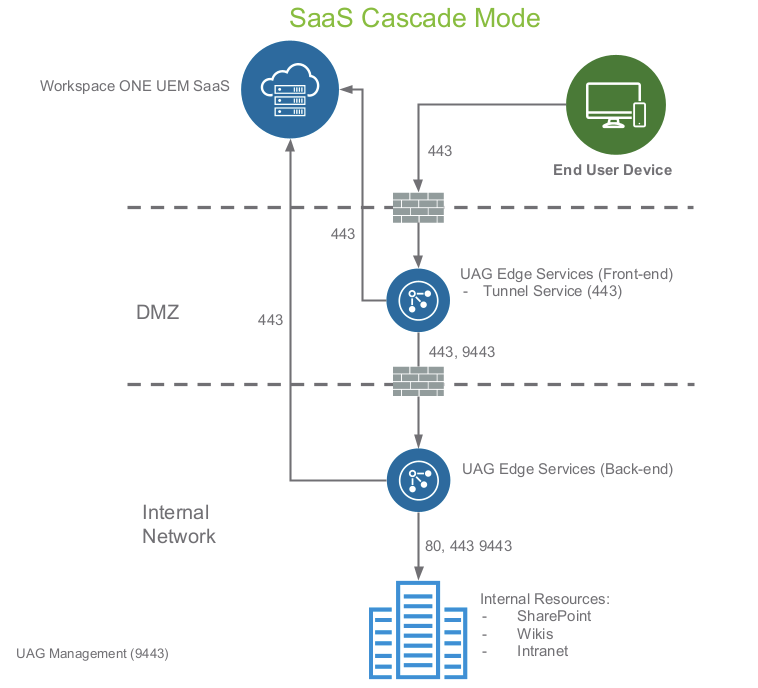
Figure 4: Cascade deployment model
The Cascade deployment model architecture includes two instances of Unified Access Gateway with Tunnel enabled on each. In cascade mode, the front-end server resides in the DMZ and communicates to the back-end server in your internal network.
The flow is as follows:
- The Per-App Tunnel requests originate from port 443 when TLS Port Sharing is enabled on the front-end Unified Access Gateway.
- The internal Unified Access Gateway redirects the request to HAProxy, which redirects the request to Tunnel edge service on port 8443.
- Tunnel authenticates the device and forwards the request to the back-end tunnel, which redirects to the specific internal resource port.
Architecture
The architectural diagram below shows an example environment that emulates a typical environment, including DMZ and internal networks.
In this example, external requests to the vApp are sent to the vPod Router, which directs those requests to the appropriate resource based on the incoming port. Ports 4000-6500 are reserved for the environment components so all traffic coming in on these ports is forwarded to your Unified Access Gateway appliance's appropriate edge service. In addition, ports 443 and 9443 are forwarded to the Unified Access Gateway appliance over the respective ports.
The vApp Networks (internal, DMZ, and transit) are created within the vApp. The internal and transit networks are NATed to the SE-UCS-Network for outbound internet connectivity while the DMZ network routes through the vPodRouter for inbound and outbound access. Note that the vPodRouter does not have a NIC on the Internal network and therefore cannot route external traffic to resources on the internal network.
vPod Router | ESXi01 6.5.0 U1 | Control Center | vCenter Server 6.5 U1 deployed in the ESXi01
1. Architecture Overview Diagram
The following architectural diagram shows an example of two major networks which you can deploy your servers into. For this set of exercises, you deploy the Unified Access Gateway appliance on a DMZ and assign the respective NICs.
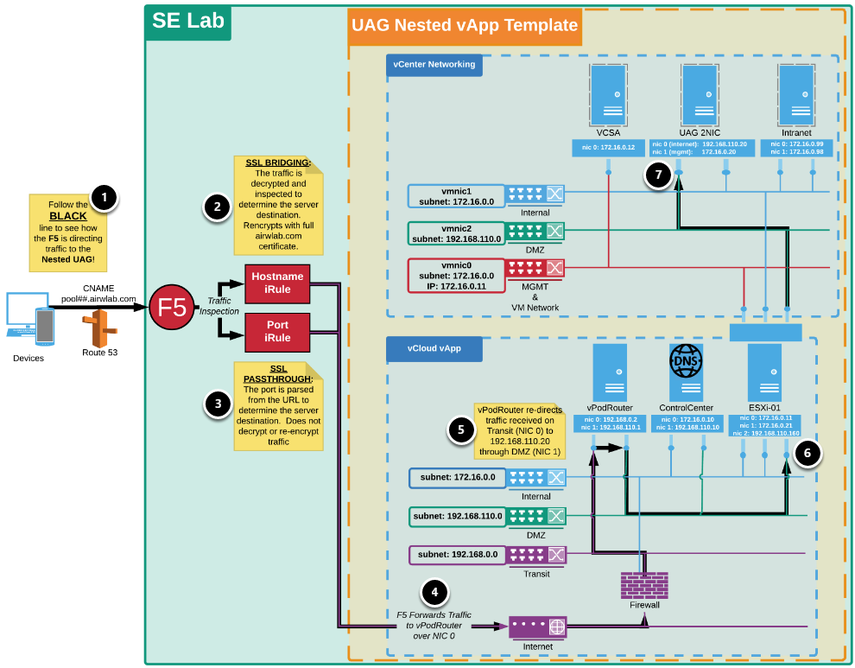
At the top of the diagram is vCenter Networking. At the bottom of the diagram is the vApp network required to support the environment. For these exercises, the focus is on the network hosted on the ESXi, and represented by the following three networks:
- VM Network & Management: Represents the dedicated network to access the Management Console
- Internal Network: Represents the internal network on 172.16.0.x range. The Control Center, ESXI, and vCenter are part of the internal network.
- DMZ Network: Represents the DMZ network on 192.168.110.x which is where the Unified Access Gateway appliance is to be deployed. The Unified Access Gateway Internet-facing NIC is associated to this network.
High-level Overview of Traffic Routing
The architectural diagram is based on two ports and two host names that route through the F5 load balancer. In this example, non-standard ports are used for these services in the 6000 - 6500 port range, due to F5 configuration for an internal network.
The next steps detail how the traffic is routed:
- The host names (tunnel-pt.airwlab.com) are CNAMEs that point to the external IP of the F5. When these host names are resolved, they are routed to the F5 to be inspected and forwarded to the internal networks.
- If the request includes only the host name ( tunnel-pt.airwlab.com), the F5 uses the Hostname iRule. This Hostname iRule inspects inbound traffic to the F5 over port 443 (HTTPS). The traffic is decrypted using the *.airwlab.com SSL certificate and chain. The Hostname iRule then inspects the traffic, re-encrypts the traffic using the SSL certificate and chain, and then routes the inbound request to the appropriate destination server based on the host name of the request. This process is known as SSL Bridging, which is not supported by Per-App Tunnel.
- If the request includes the host name and port (tunnel-pt:airwlab.com:6000), the F5 uses the Port iRule. This Port iRule inspects inbound traffic to the F5 over non-443 ports. Unlike the Hostname iRule, the Port iRule parses the request for the port number and then routes the inbound request to the appropriate destination server based on the port of the request. This process does not involve decrypting or re-encrypting the traffic; it forwards the request to the desired destination. This process uses SSL Passthrough.
- From the F5 Hostname or Port iRules, the traffic is forwarded to the configured IP address.
- The vPodRouter is configured to forward Unified Access Gateway traffic to the 192.168.110.20 IP address over the DMZ Network.
- The Nested DMZ Network (192.168.110.0 on vmnic2) is provided by NIC 2 on the ESXi-01 Host (192.168.110.160).
- The request reaches the nested Unified Access Gateway appliance deployed on 192.168.110.20.
Avoid SSL Bridging
In this example, non-443 ports are used for Tunnel and Content Gateway to avoid decrypting and re-encrypting the traffic because this is not supported with Per-App Tunnel. In other scenarios, you would use the standard ports where possible. This exercise demonstrates that the ports for both services can be configured to work within the architecture.
2. Network Interfaces
Unified Access Gateway supports deployments with one, two, or three NICs. This means that the server can be partitioned to receive traffic on a single interface or to route traffic to different interfaces, based on the source of the request. Most often, if you need to implement multiple NICs, you already follow this standard with other web applications in your organization.
You must determine what is appropriate for your environment when selecting the number of NICs during installation. You need to understand the expected behavior when two or three NICs are enabled.
To explore these options, see Deploying Unified Access Gateway: Workspace ONE Operational Tutorial.
3. General Considerations
In the exercises for deploying the Unified Access Gateway server through vSphere, the vCenter setup is hosted in a nested template. This is not usually the case when working with users in a live environment.
User environments can include multiple networks and can optionally have a Network Protocol Profiles (NPP) that corresponds to the networks to connect to the Unified Access Gateway. Prior to version 3.3, NPP was a requirement. Since version 3.3, NPP is no longer required.
Note: Keep in mind that the Unified Access Gateway requires a netmask, default gateway, and subnet to be defined for each network enabled during deployment.
Prerequisites
Before you can perform the steps in this exercise, you must install and configure the following components:
- Workspace ONE UEM 2310 or later
- vSphere ESX host with a vCenter Server (vSphere 7 and later)
- vSphere data store and network to use
- PowerShell script running on Windows 10 and later machines, or Windows Server 2016 and later
- Windows machine running the PowerShell script with OVF Tool command installed (see OVR Tool Software Download to install the latest OVF Tool)
- Unified Access Gateway PowerShell script, such as uagdeploy-VERSION.ZIP, available at my.workspaceone.com; after download, extract the files into a folder on your Windows machine
- iPhone, iPad, and iPod Touch devices running iOS 17+ and later
- Android 10+ and later
Network prerequisites for Unified Access Gateway can be found here: - UAG prerequisites (Select the Tunnel & Gateway tab.)
Ensure the following settings are enabled in the Workspace ONE UEM console:
- Organization Group created and set as Customer Type
- Device Root Certificate issued
- REST API Key generated at the Organization Group where Tunnel will be enabled
To perform most of this exercise, you need:
- Admin access to the vSphere administration console
- Admin access to the Workspace ONE UEM console
Creating an API Account and Setting Permissions in Workspace ONE UEM
Unified Access Gateway requires access to the Workspace ONE UEM API Server to retrieve the Tunnel configuration and configure the Tunnel Edge Service. Unified Access Gateway uses an API account configured during deployment, after that the communication is based on certificates.
The API account does not require full administrator permissions, instead, it only requires read access to the Enterprise API Integration.
Create API Role Permission
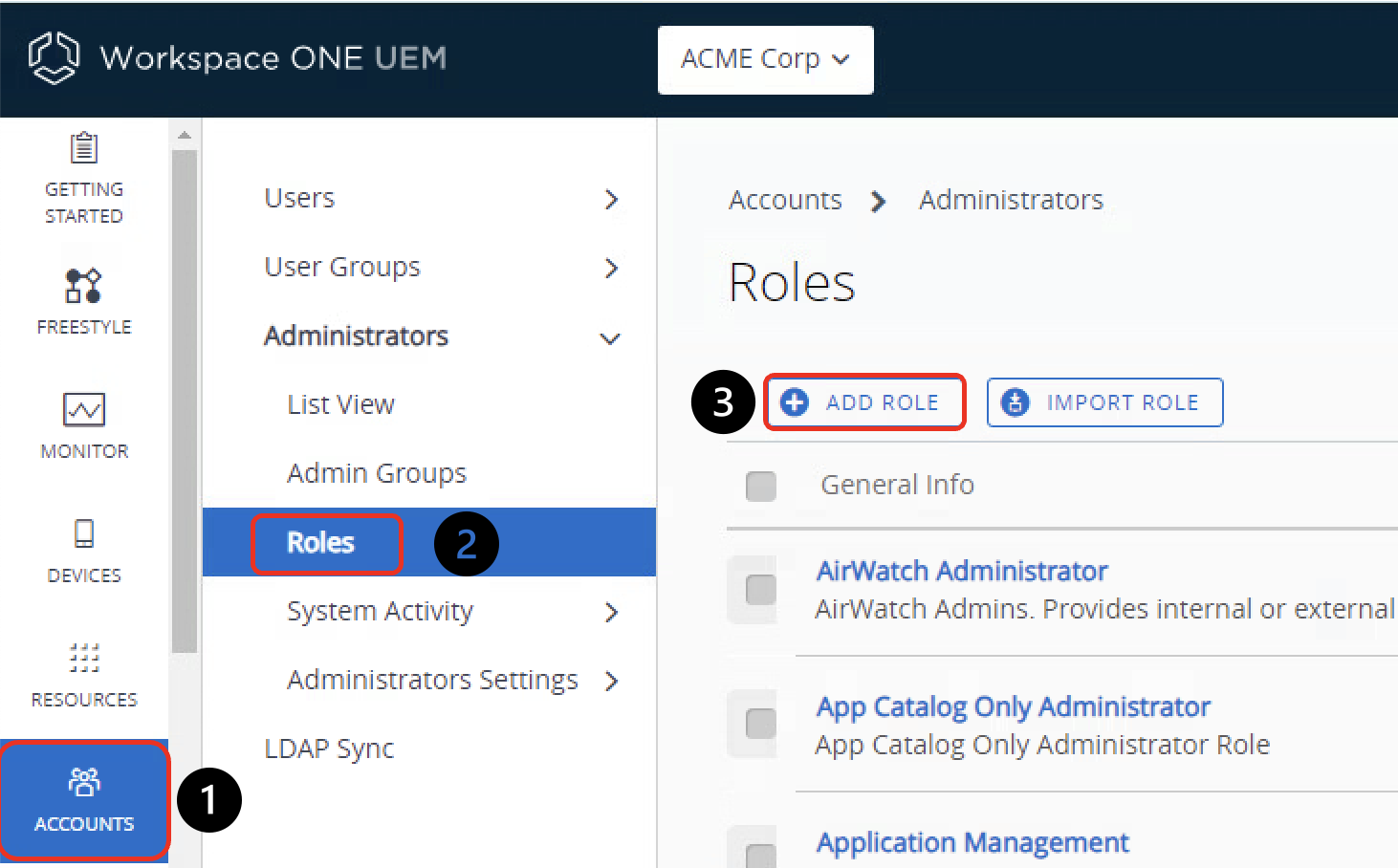
- Select Accounts.
- Navigate to Administrators > Roles.
- Click Add Role.
Set API Role Permission
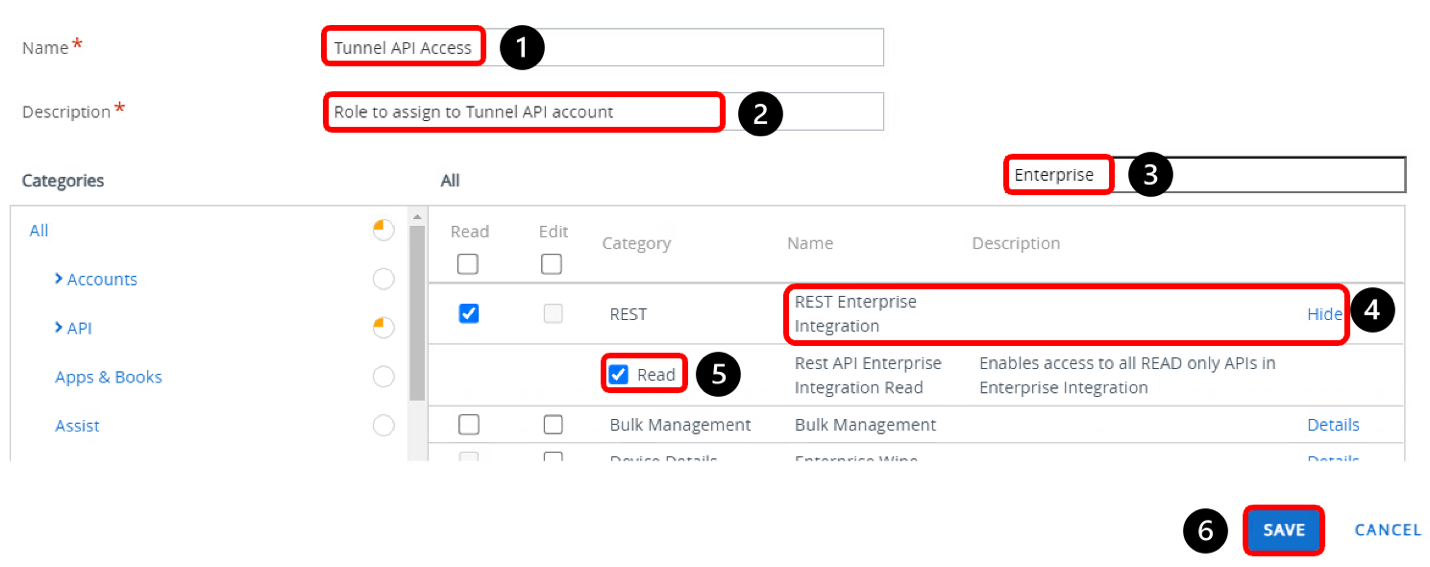
- Enter Tunnel API Access for the Role Name.
- Provide a description.
- Enter Enterprise in the search box.
- Confirm that you can see REST Enterprise Integration and click Details.
- Select Read.
- Click Save.
A Role with permission to read the Tunnel configuration has been created.
Create API Administrator Account
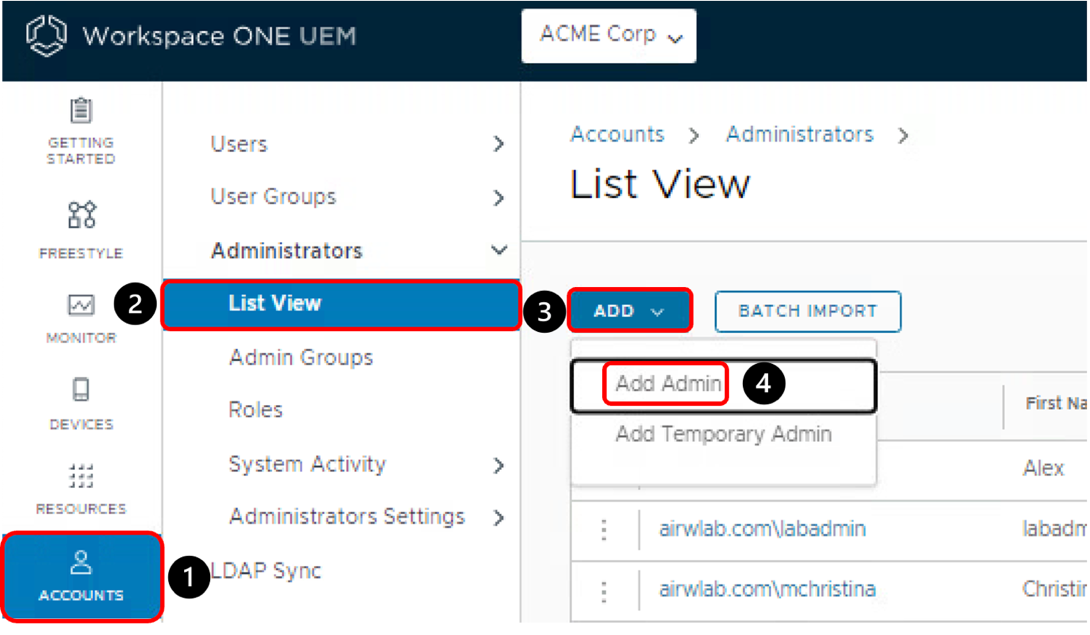
- Click Accounts.
- Navigate to Administrators > List View.
- Click Add.
- Select Add Admin.
Select the Admin Type
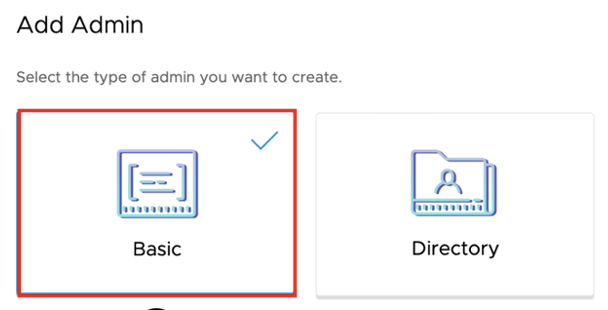
- Select Basic or Directory.
- Click Next.
Add API Admin
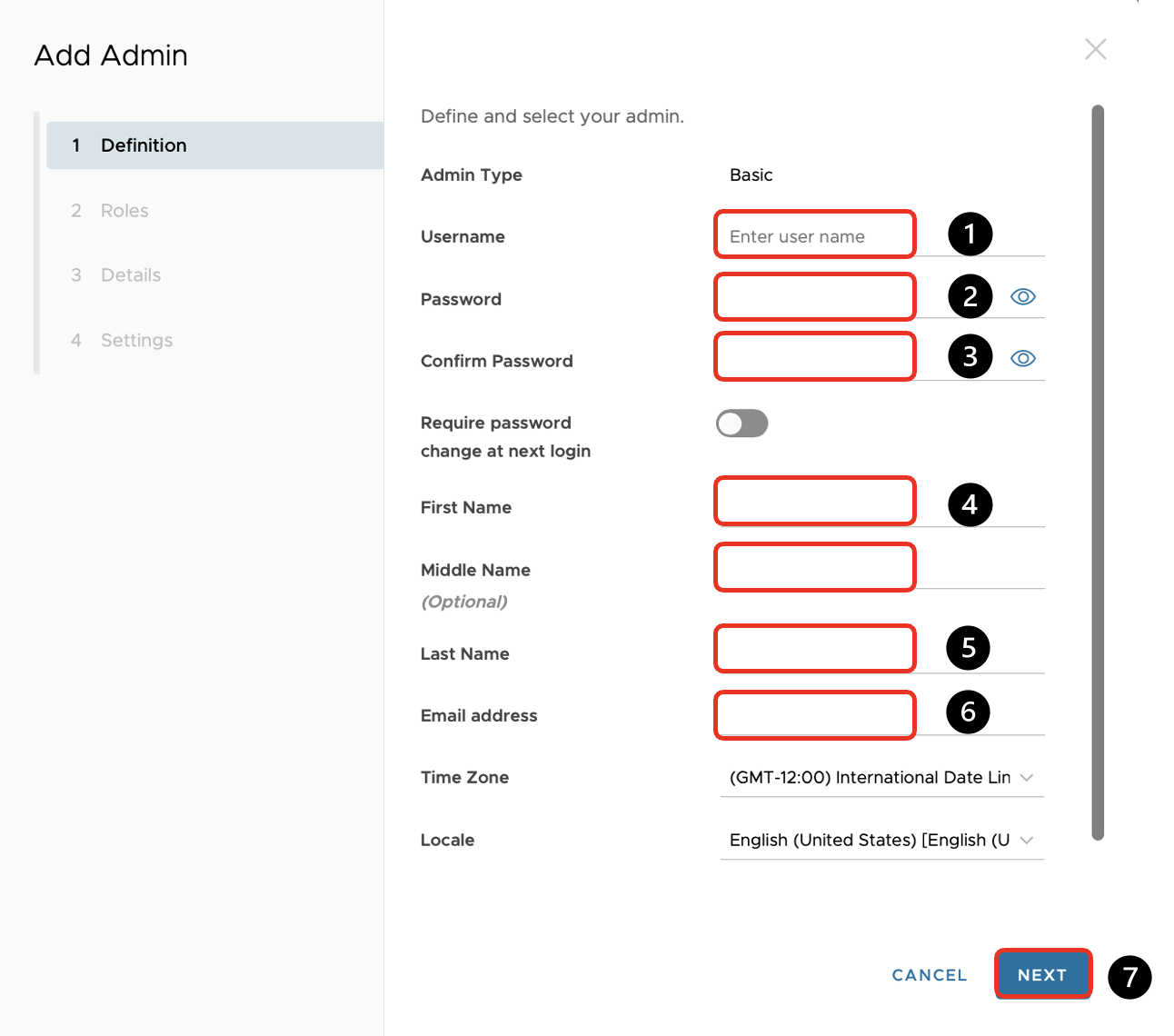
- Enter a Username.
- Enter a Password.
- Confirm the Password.
- Enter a First Name, for example, API.
- Enter a Last Name, for example, User.
- Enter your email for Email Address.
- Click Next.
Assign Role
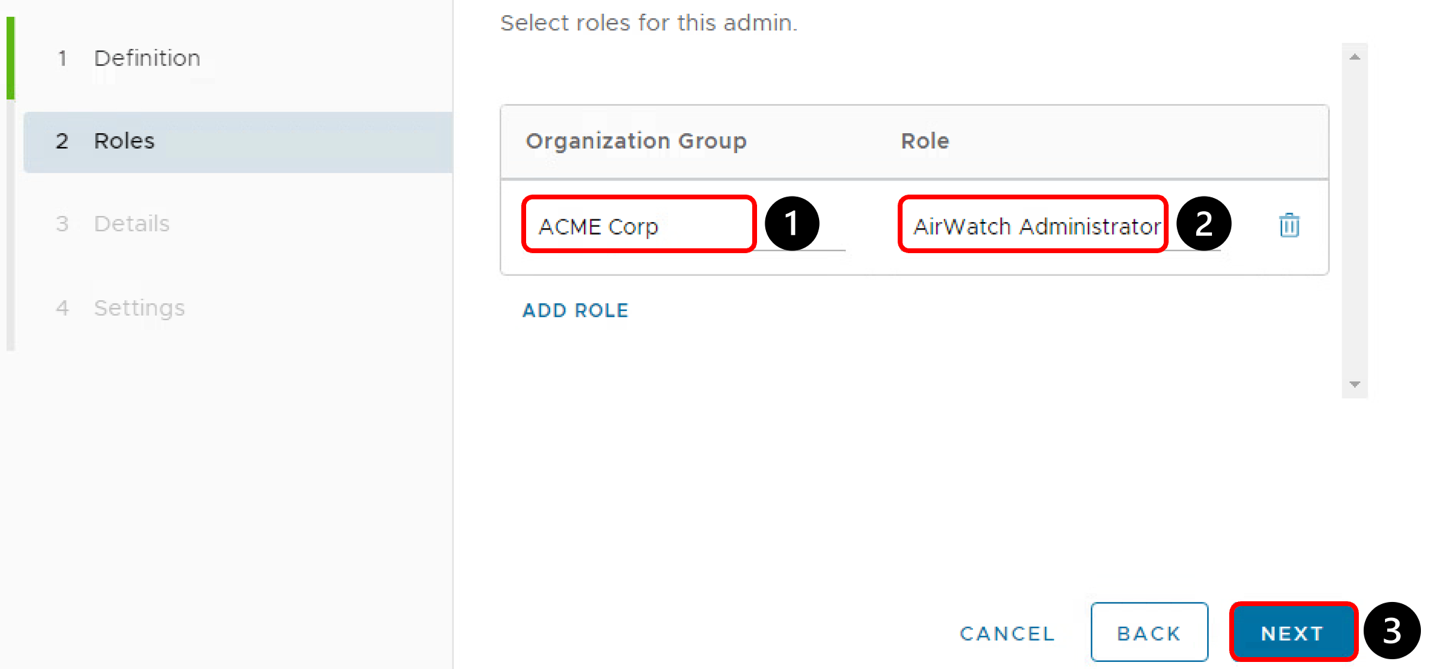
- Select the Organization Group in the drop-down menu.
- Select the Role we created for Tunnel API Access.
- Click Next and Save.
An API account with minimum permissions to obtain the Tunnel configuration is ready to be used in the Unified Access Gateway configuration.
Enrolling an iOS Device
In this section, enroll your iOS device in Workspace ONE UEM by installing the Workspace ONE Intelligent Hub. A Group ID is required to complete enrollment. See Identify your Group ID from Workspace ONE UEM Console.
- Download and install Workspace ONE Intelligent Hub from the App Store (if needed).
Note: Checked-out devices will likely have the Workspace ONE Intelligent Hub already installed. You may skip this step if your device has the Workspace ONE Intelligent Hub installed.
At this point, if you are using your own iOS device or if the device you are using does not have the Workspace ONE Intelligent Hub Application installed, then install the application from the App Store.
To install the Workspace ONE Intelligent Hub application from the App Store, open the App Store application and download the free Workspace ONE Intelligent Hub application.
- Launch the Intelligent Hub app on the device.
Note: if you have your own iOS device and would like to test, you must download the Workspace ONE intelligent hub app first. - Enter the Server URL and tap Next.
- Tap the Server Details button.
- Enter your Group ID.
- Tap the Next button.
Note: If you are using an iPhone, you may have to close the keyboard by tapping Done to tap the Next button. - Now, provide user credentials to authenticate to Workspace ONE UEM.
- Enter your Username.
- Enter your user Password.
- Tap the Next button.
Redirect to Safari and Enable MDM Enrollment in Settings
The Workspace ONE Intelligent Hub prompts you to enable Workspace Services to enroll your device into Workspace ONE UEM.
- Tap Next to begin.
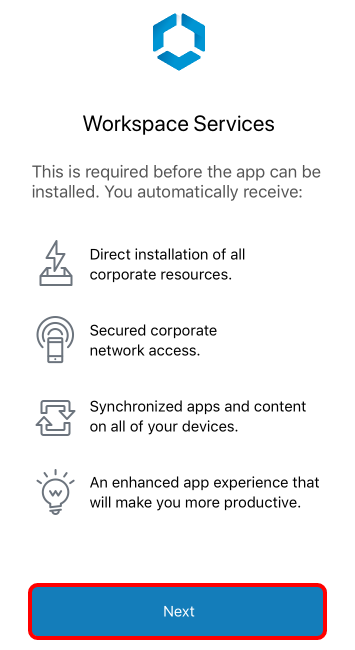
- Allow the Website to open settings (if needed). If you are prompted to allow the website to open Settings, tap Allow.
Note: If you do not see this prompt, continue to the next step. This prompt occurs only for iOS devices on iOS 10.3.3 or later.
- Install the Workspace ONE MDM Profile. Tap Install in the upper-right corner of the Install Profile dialog box.
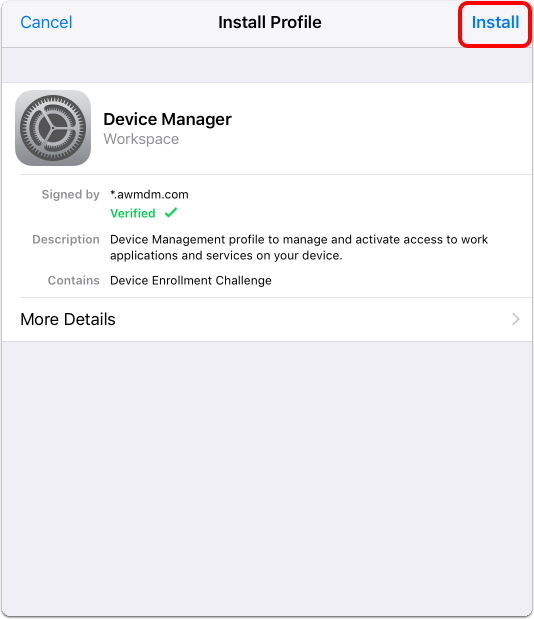
- Install and Verify the Workspace ONE MDM Profile. Tap Install when prompted on the Install Profile dialog.
- Review iOS MDM Profile Warning.
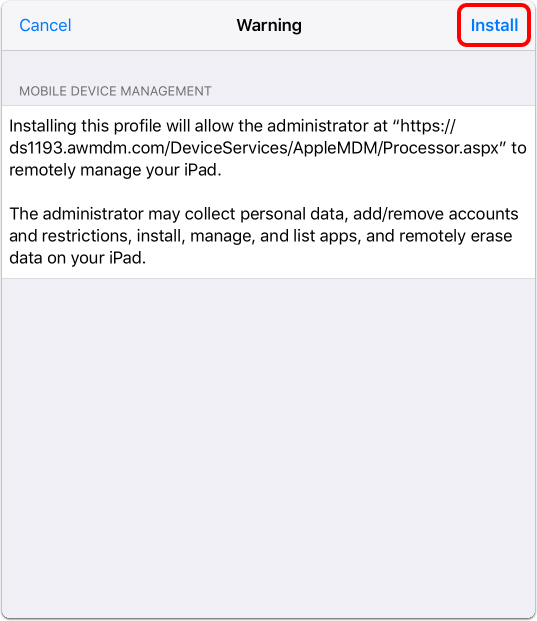
- You should now see the iOS Profile Installation warning explaining what this profile installation will allow on the iOS device.
Tap Install in the upper-right corner of the screen.
- Trust the Remote Management Profile.
- You should now see the iOS request to trust the source of the MDM profile.
- Tap Trust when prompted at the Remote Management dialog.
- You should now see that the iOS Profile was successfully installed.
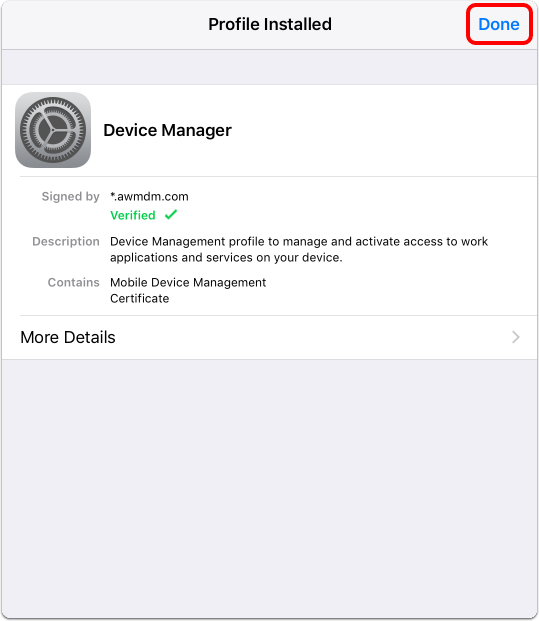
- Tap Done in the upper-right corner of the prompt.
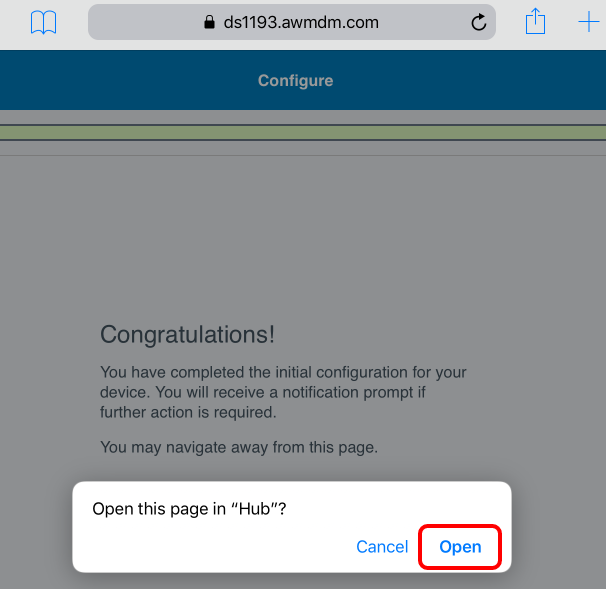
- Your Workspace ONE UEM enrollment is now complete. Tap Open to navigate to the Workspace ONE Intelligent Hub.
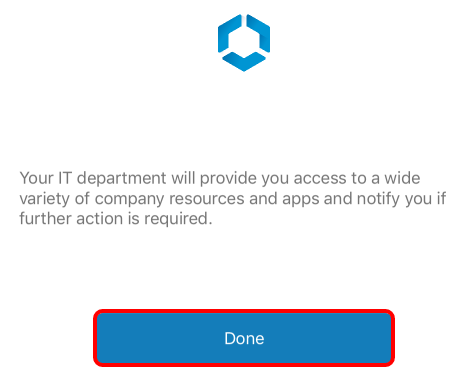
- Accept the Workspace ONE Intelligent Hub Notice. Tap Done to confirm the notice and continue.
- Accept Notifications for Hub (if needed). Tap Allow if you get a prompt to allow notifications for the Hub app.
- Accept the App Installation (if needed). You may be prompted to install a series of applications. If prompted, tap Install to accept the application installation.
- Confirm the Privacy Policy. Tap I Understand.
- Accept the Data Sharing Policy. Tap I Agree for the Data Sharing policy.
- Confirm the Device Enrollment in the Hub App.
Confirm that the Hub app shows the user account that you enrolled with.
You have now successfully enrolled your iOS device with Workspace ONE UEM. Continue to the next step.
Enabling Tunnel in the Workspace ONE UEM Console
When the Tunnel edge service is enabled on the Unified Access Gateway appliance, it retrieves the Tunnel configuration from Workspace ONE UEM. Therefore, the Tunnel must be configured first in the Workspace ONE UEM console, prior to deployment of the Unified Access Gateway appliance.
This section helps you to configure Tunnel in the Workspace ONE UEM console.
Open Tunnel Configuration
- Select Groups & Settings.
- Select Configurations.
- Enter Tunnel in the search field and press Enter.
- Select Tunnel on the result list.
Configure Tunnel Settings
First, configure the host name and port details.
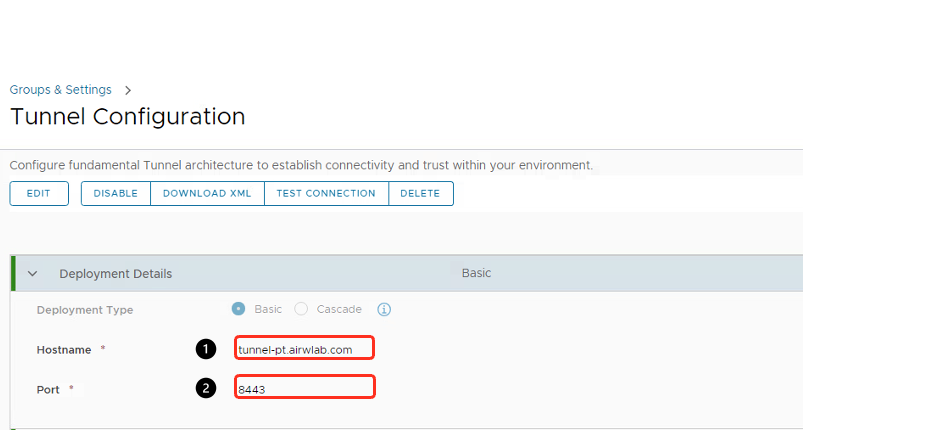
- Enter the Tunnel server host name for Hostname.
- Enter a Port number.
- Click Next.
Configure Tunnel SSL certificate
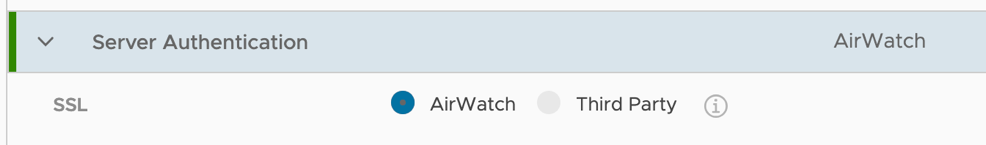
Select AirWatch as the certificate.
If you want to use your own SSL Public Certificate, select Third Party and upload the certificate using the console.
Confirm Tunnel Settings
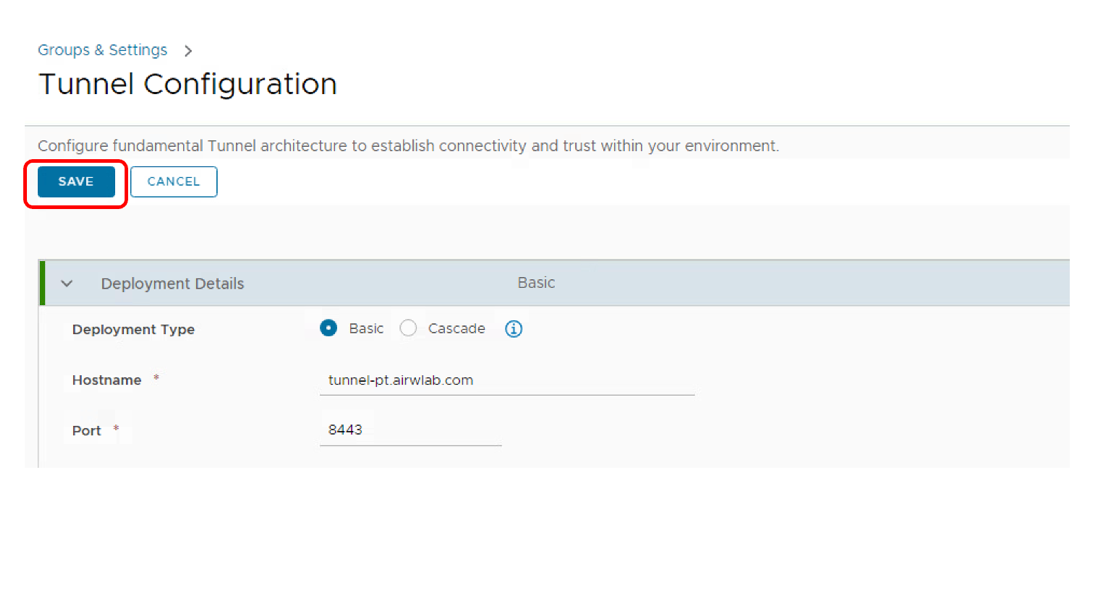
Verify that the configuration summary is correct. Click Save to continue.
Download the Unified Access Gateway Appliance
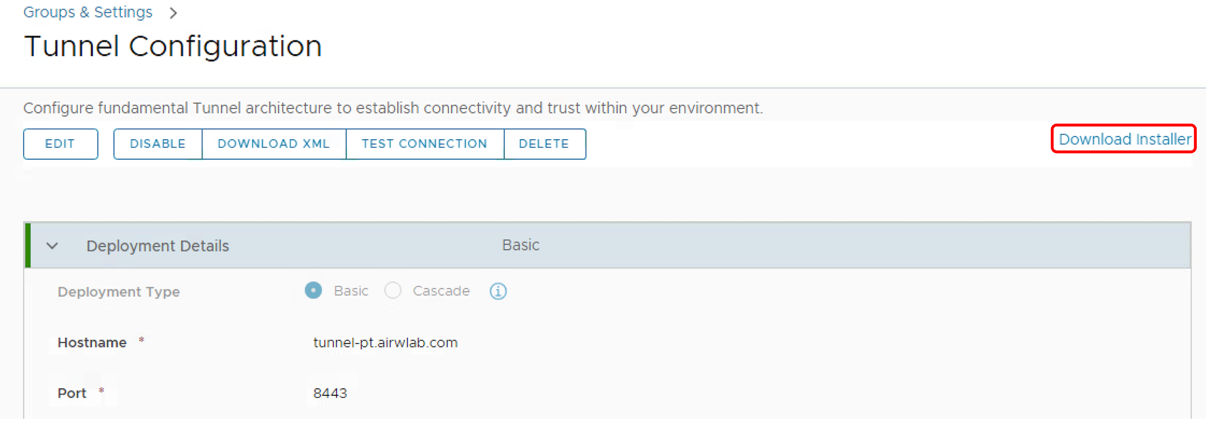
After the configuration is saved, click Download Installer to download the Unified Access Gateway virtual appliance. Extract the ZIP file on the Windows machine where you will install Unified Access Gateway.
The next section helps you to deploy the Unified Access Gateway appliance OVF through PowerShell and configure Tunnel edge services based on the settings configured in Workspace ONE UEM.
Preparing the Tunnel INI Settings for Deployment
This section covers the required INI settings to enable the Tunnel edge service during the Unified Access Gateway appliance deployment. Ensure you are logged in to the machine where you will install Unified Access Gateway. Extract the contents of the Unified Access Gateway ZIP file on this machine.
Configure the General Deployment settings
The INI file contains all the configuration settings required to deploy the Unified Access Gateway appliance.
This exercise uses the uag-Tunnel.ini file and is configured for a Unified Access Gateway appliance called UAG-TUNNEL, which has two NICs—NIC one is set to internet facing and NIC two for back end and management.
The INI file template is located in the Unified Access Gateway installer ZIP package downloaded in the previous exercise. Edit the INI file and start configuring the General and network settings.
In the INI example below, the settings are already filled out. The General section includes details such as deployment location and network configuration for the Unified Access Gateway appliance.
[General]
name= uag-tunnel
uagname=uag-tunnel
adminPasswordExpirationDays=365
source=C:\UAG Deploy\euc-unified-access-gateway-23.09.0.0-22617266_OVF10-001.ova
target=vi://<VCENTER HOST>/HOL-DC/host/Cluster1/
ds=XT02-HOL-3
netInternet=DPG-VMs_Mgmt1_52
netManagementNetwork=DPG-VMs_Internal_60
netBackendNetwork=DPG-VMs_Internal_60
defaultGateway=192.168.55.254
deploymentOption=twonic
ip0=192.168.52.200
netmask0=255.255.252.0
ip1=192.168.60.100
netmask1=255.255.254.0
dns=192.168.52.10
[AirwatchTunnelGateway]
apiServerUsername=apiuagsvc
organizationGroupCode=intel
apiServerUrl=https://ws1.airwlab.com
airwatchServerHostname=tunnel-pt.airwlab.com
[SSLCert]
pfxCerts=C:\UAG Deploy\rui_pwd.pfx
[SSLCertAdmin]
pfxCerts=C:\UAG Deploy\rui_pwd.pfx
The SSLCert and SSLCertAdmin sections contain SSL certificate locations for the administrator and Internet interfaces.
Configure Tunnel Settings
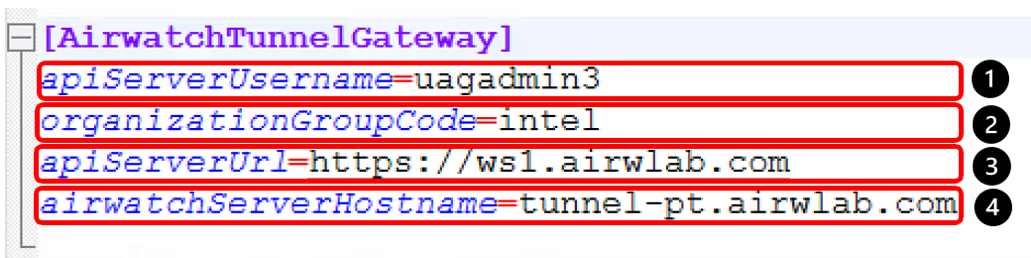
The AirWatch section contains the required parameters to enable the Tunnel edge service on your Unified Access Gateway appliance.
- Enter the apiServerUsername, for example, uagadmin3.
Note: This account only requires READ access to REST API Enterprise integration, full Administrator permission is not required. - Enter your Group ID for the Organization Group.
- Enter the apiServerUrl, for example, https://ws1.airwlab.com.
- Enter the airwatchServerHostname, for example, https://tunnel-pt.airwlab.com.
During the Unified Access Gateway deployment, the PowerShell script prompts you for the apiServerUsername password.
Deploying Unified Access Gateway Appliance
After you have configured the INI file for your Unified Access Gateway deployment, the next step is to run the PowerShell script passing the INI as a parameter.
Open PowerShell
- Click the PowerShell icon and run it using Admin Privileges.
- Run
Set-ExecutionPolicy –Scope Process –ExecutionPolicy Bypassprior to executing the command. (To ensure no restrictions block the execution of the PowerShell script).
Deploy Unified Access Gateway using PowerShell
After you run the script, it prompts for input.
- Navigate to the folder containing your INI file.
- Enter the following command line, and replace the INI filename with the one you have used.
.\uagdeploy.ps1 .\uag-tunnel.ini
-rootPwd <PASSWORD>
-adminPwd <PASSWORD>
-disableVerification false
-noSSLVerify false
-ceipEnabled yes
-awAPIServerPwd <password>
-rootPwd - set the root password for the Unified Access Gateway appliance.
-adminPwd - set the admin password for the REST API management access.
-disableVerification - perform validation of signature and certificate.
-noSSLVerify - perform SSL verification for the vSphere connection.
-ceipEnabled - Join the Customer Experience Improvement Program ("CEIP") program.
-awAPIServerPwd - API password for the respective configured API user under the AirWatch section of the INI file.
Note: You might get prompted to enter the password related to the certificates defined on the SSLcert and SSLcertAdmin settings. Certificates can be passed in PEM format using the pemCerts and pemPrivKey settings for the SSLCert and SSLCertAdmin sections of the INI file.
If the -awAPIServerPwd is incorrect, you will get prompted to enter the correct password for the UEM API account.
The deployment starts and you can follow the progress on the same window or on your vSphere Web Client, which you opened at the beginning of this tutorial.
Note: Tunnel can be configured on the INI using the [AirwatchTunnelGateway] and the same settings, when using this section you must use the -awAPITunnelGatewayAPIServerPwd to inform the API password and not the -awAPIServerPwd.
Confirm that the PowerShell Script Deployment Completes
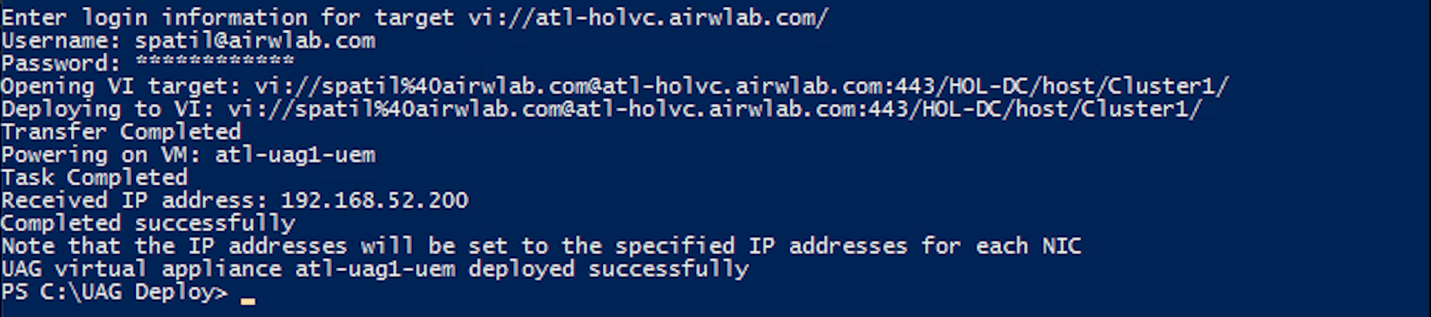
- Confirm the deployment has been completed successfully. The Completed successfully text is shown in the output.
- Click Close.
- After a successful deployment, the script automatically powers on the VM UAG-2NIC-TUNNEL.
The Received IP address presented by the script log is a temporary IP; the final IPs for NIC one and NIC two are assigned to the Unified Access Gateway appliance during the first start. Return to the vSphere Web Client and validate the IP address in the next step.
Validate Unified Access Gateway Deployment
- Click VM and Templates.
- Click your VM, for example, UAG-2NIC.
- Click View all 2 IP addresses.
Important: If the Unified Access Gateway appliance does not finalize the configuration during the first startup, you receive an error message from vSphere Web Client. If that happens, wait for the appliance to finalize, and refresh the entire Google Chrome browser.
Validating Tunnel Settings on the Unified Access Gateway Appliance
The Tunnel is now enabled and running based on the INI settings that you provided during the Unified Access Gateway deployment.
As an alternative to deploying the Tunnel using PowerShell, you can use the Unified Access Gateway administration console, which allows you to enable or change the current Tunnel settings.
This section helps you to validate the Tunnel settings using the Unified Access Gateway administration console.
Log in to the Unified Access Gateway Administration Console
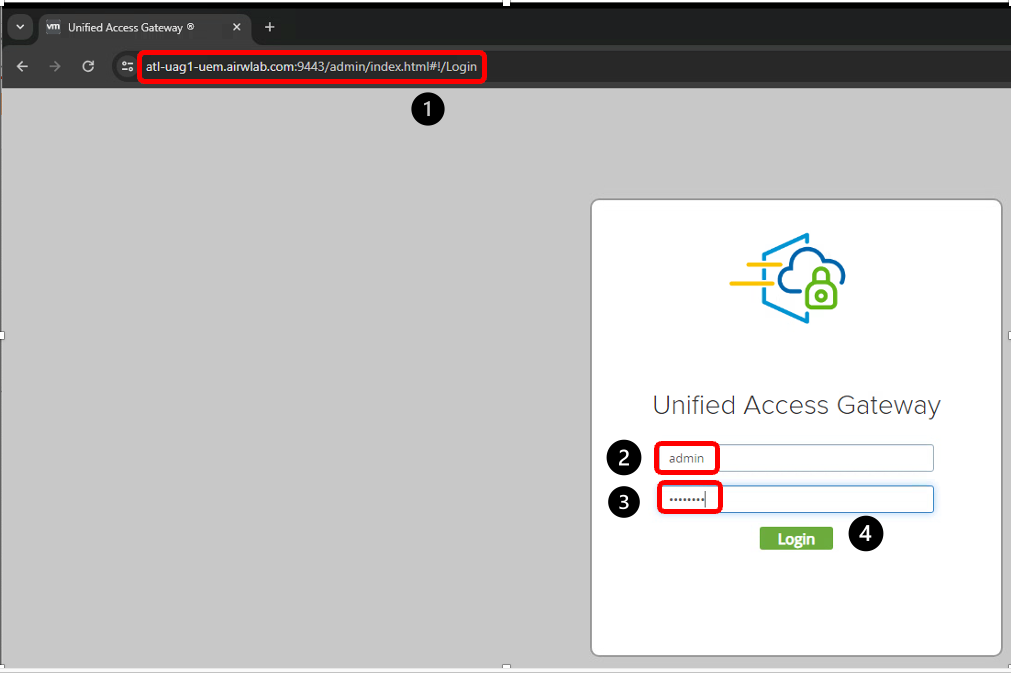
- Click the New Tab button and navigate to the Unified Access Gateway administration console URL, for example, https://<UAG_hostname>:9443/admin.
- Enter the username.
- Enter the password defined during deployment.
- Click Login.
Validate Configuration settings
A successful login redirects you to the following screen. Keep this window open as you will return to the administration console later.
Click Select to configure settings manually.
Access Tunnel Settings
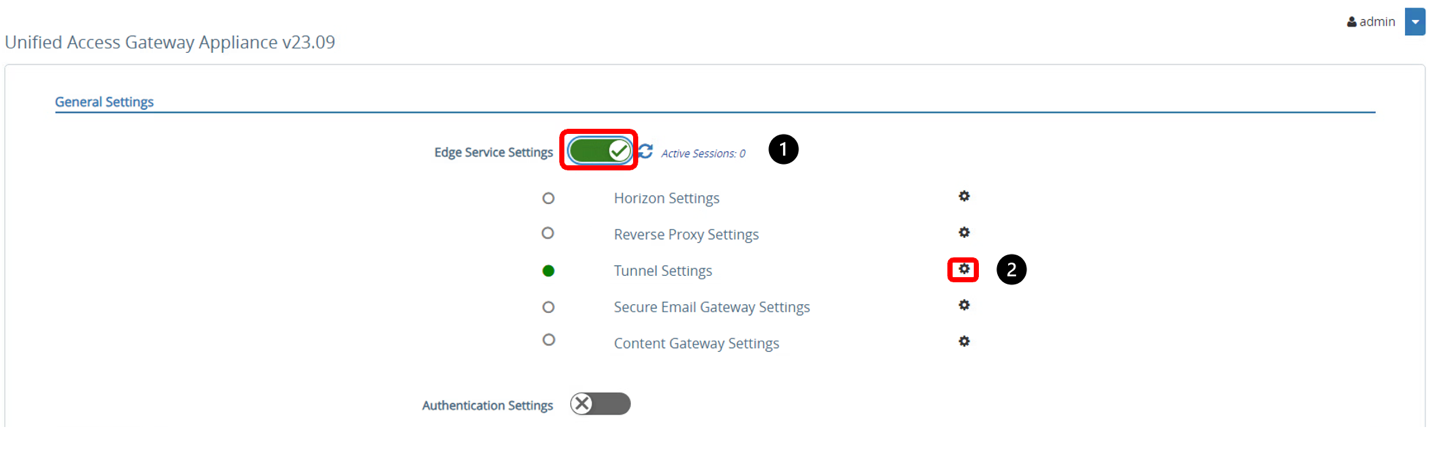
- Click SHOW. After you click SHOW, it changes to HIDE.
- Click the gear icon next to Tunnel Settings. The circle should be green, which means the Unified Access Gateway appliance and Workspace ONE UEM console can communicate.
Validate the Tunnel settings on Unified Access Gateway
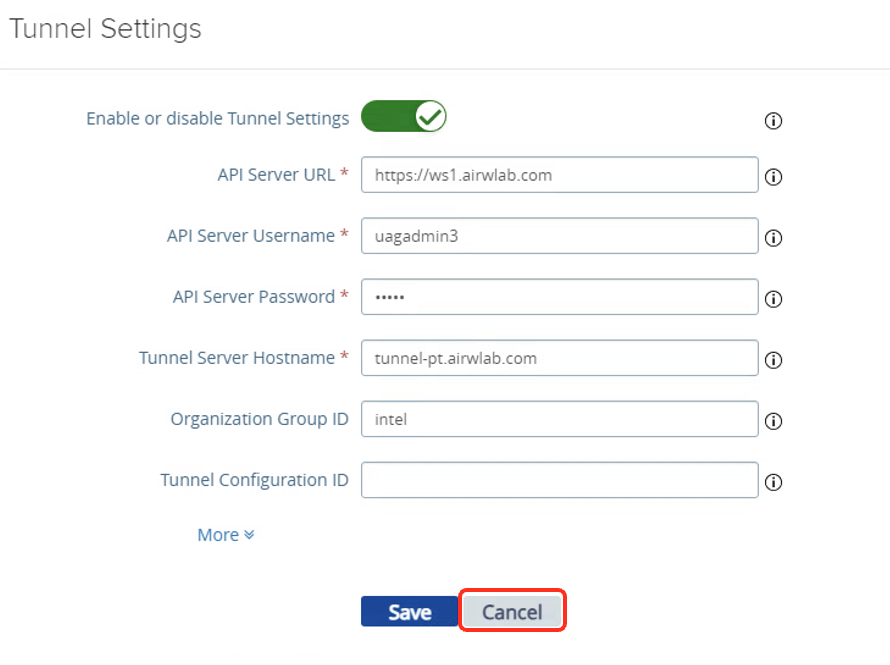
The Tunnel edge service is enabled based on the configuration defined in the INI file.
You can change the configuration at any time or choose not to configure settings in the INI file and later enable the settings through the Unified Access Gateway administration console.
Each time you change the configuration and Save, the changes are applied to the configuration files and the Tunnel edge service restarts automatically. Devices cannot communicate with the service during the restart.
Click Cancel.
Configuring Network Traffic Rules for Per-App Tunnel
From the Workspace ONE UEM console, you can define network traffic rules to granularly control how the Tunnel and Workspace ONE Tunnel app directs traffic from devices.
The configuration in this exercise applies to the Per-App Tunnel component. Device traffic rules control how devices handle traffic from specified applications and server traffic rules manage network traffic when you have third-party proxies configured.
Device traffic rules force the Workspace ONE Tunnel application to:
- Send traffic through the tunnel
- Block all traffic to specified domains
- Bypass the internal network straight to the Internet
- Send traffic to a HTTPS proxy site
The device traffic rules are created and ranked to give an order of execution. Every time a specified application is opened, the Workspace ONE Tunnel application checks the list of rules to determine which rule applies to the situation. If no set rules match, Workspace ONE Tunnel applies the default action. The default action—set for all applications except Safari—applies to domains not mentioned in a rule. If no rules are specified, the default action applies to all domains. The created device traffic rules apply to all VPN Tunnel profiles in the organization group where the rules are created.
Server traffic rules enable you to manage the network traffic when you have third-party proxies configured in your network. These rules apply to traffic originating from the Tunnel. The rules force the Tunnel to send traffic to specific destinations either through the proxy or to bypass it.
Open Tunnel Configuration
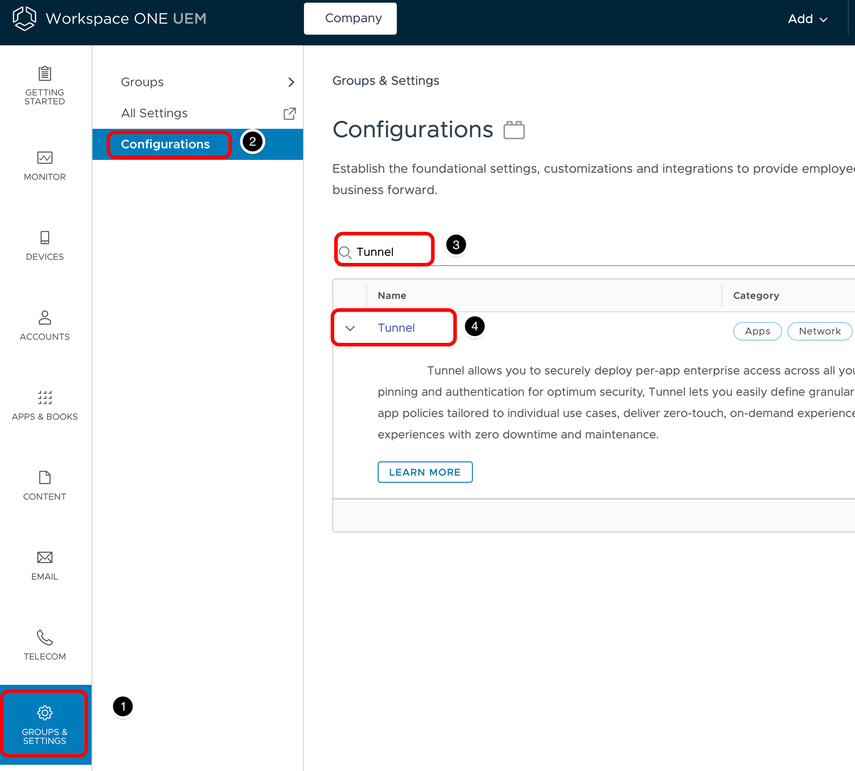
- Select Groups & Settings.
- Select Configurations.
- Enter Tunnel in the search field and press Enter.
- Select Tunnel on the result list.
Edit Device Traffic Rules Set
- In Device Traffic Rule Sets, click Edit.
- Click Default assignment.
Define Device Traffic Rules
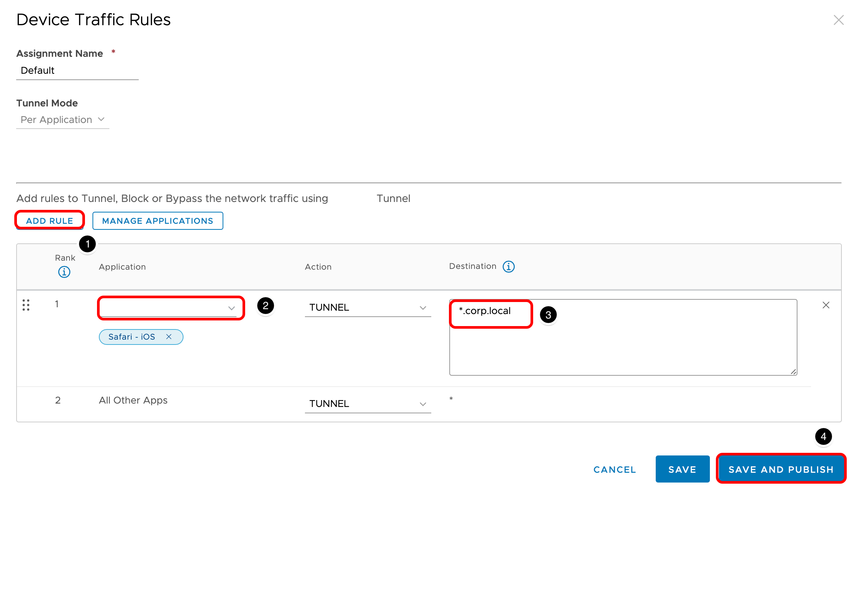
In this step, you create a specific rule that is applied only to Safari; any requests to *.corp.local are routed through the Tunnel. All other requests are not routed through Tunnel.
- Click Add Rule.
- Select Safari-iOS.
- Enter a Destination Hostname.
- Click Save & Publish and then OK on the next dialog box to confirm.
Configuring VPN Profile and Workspace ONE Tunnel Client
To provide Per-App VPN capability on the devices, you must send a VPN profile and Workspace ONE Tunnel client to the devices.
Configure Device Profile
This exercise helps you to create and push the VPN Profile to the device.
Add Device Profile
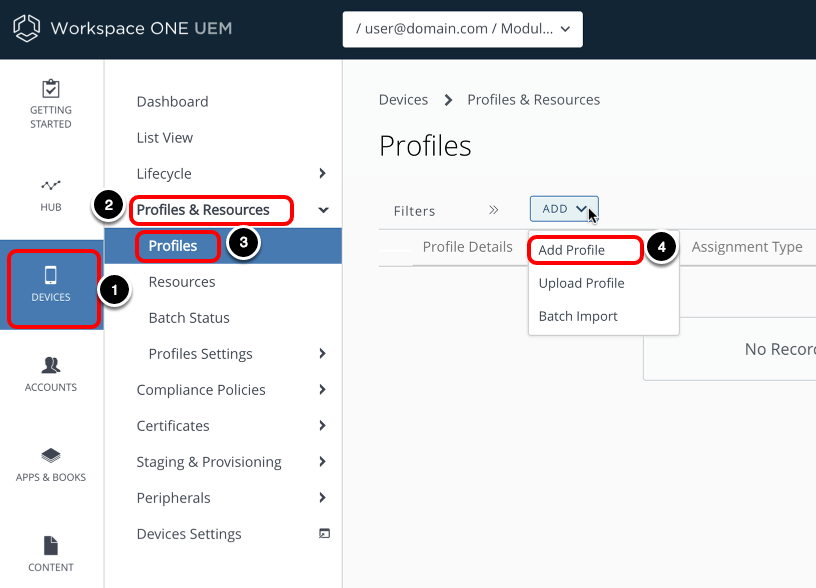
- Select Devices.
- Select Profiles & Resources.
- Select Profiles.
- Click Add, then click Add Profile.
Define Profile Platform

Select Apple OS.
Configure General Profile Settings
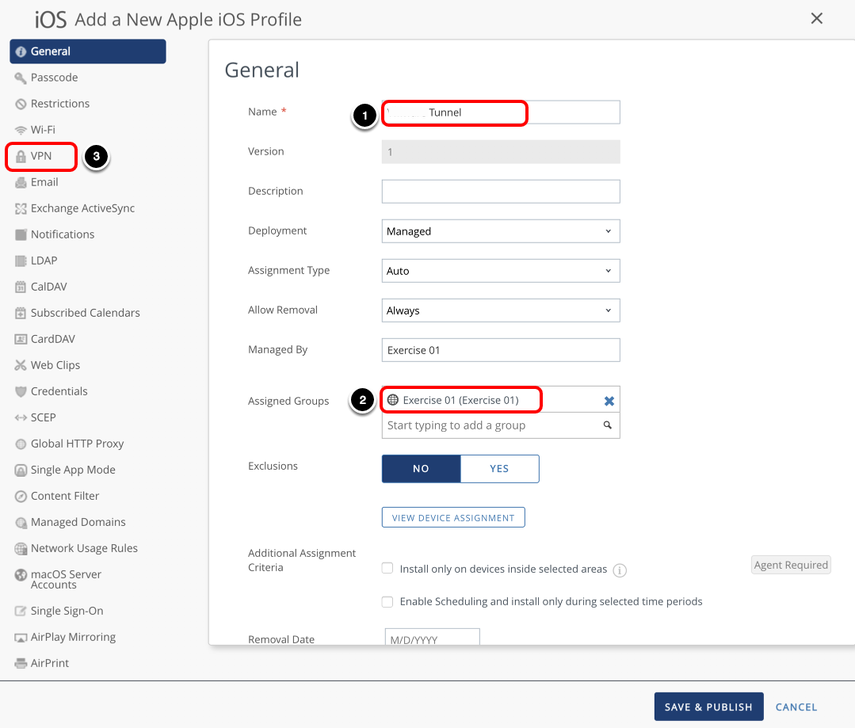
- Enter a Name.
- Select an Assigned Group.
- Select the VPN payload and click Configure.
Configure VPN payload Settings
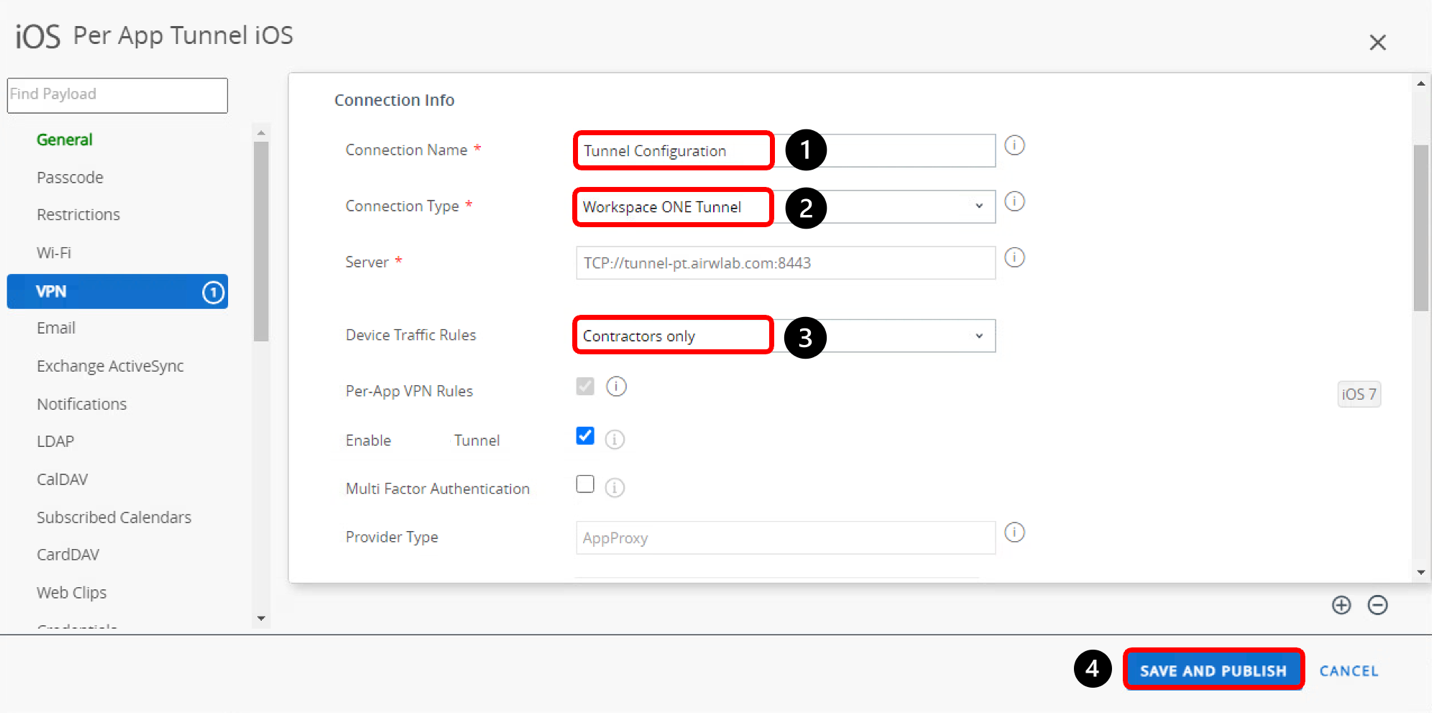
- Enter a name for the VPN payload configuration
- Select Workspace ONE Tunnel.
- Select the Device Traffic Rule like Contractor only.
- Click Save & Publish and on the next screen, click Publish.
Configure Workspace ONE Tunnel Client Application for Deployment
To configure the Workspace ONE Tunnel client application to be deployed to your device through Workspace ONE UEM, follow the chapter Deploying Workspace ONE Tunnel for iOS which is part of Deploying Workspace ONE Tunnel: Workspace ONE Operational Tutorial.
Configure Google Chrome Application for Deployment
Repeat the steps in this exercise, this time for the Google Chrome application.
Google Chrome is used later in this exercise to confirm that Safari is the only browser authorized to access internal websites.
Validating Tunnel Implementation for Per-App VPN
After enrollment is complete, ensure that the Workspace ONE Tunnel and Google Chrome applications are installed on your iOS device.
Launch and Enable the Workspace ONE Tunnel Client

On your iOS device, tap Tunnel to start the Workspace ONE Tunnel client.
Start Workspace ONE Tunnel for the First Time.
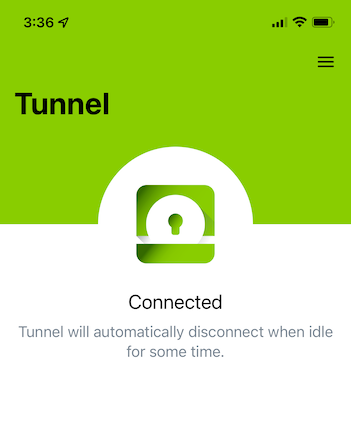
This step enables the newly installed Workspace ONE Tunnel client to initiate a VPN connection automatically on behalf of the user whenever an enabled application is launched. You perform this step only once.
Tap Continue to enable the Workspace ONE Tunnel application as a VPN client on the device.
Access Public Website from Safari
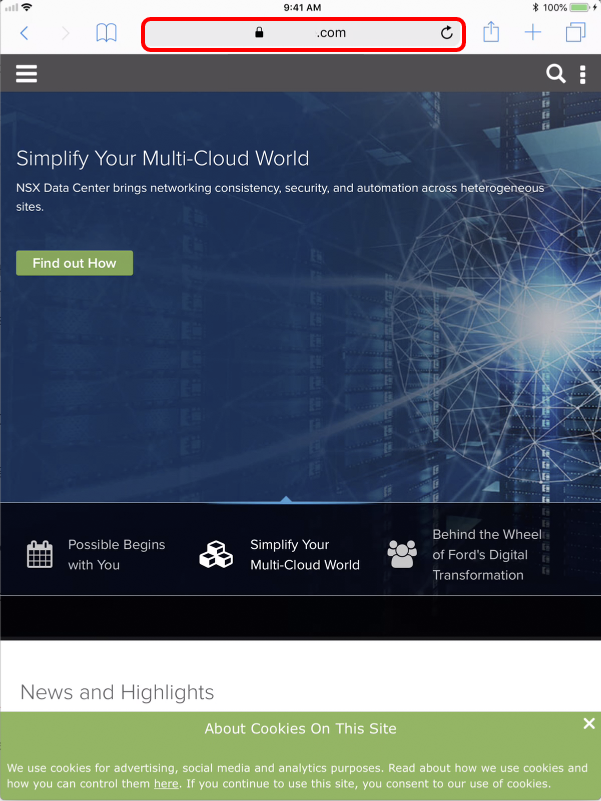
- Open the Safari browser and navigate to an external website.
- You can access the external website and no VPN is requested.
Access Intranet Website with Safari
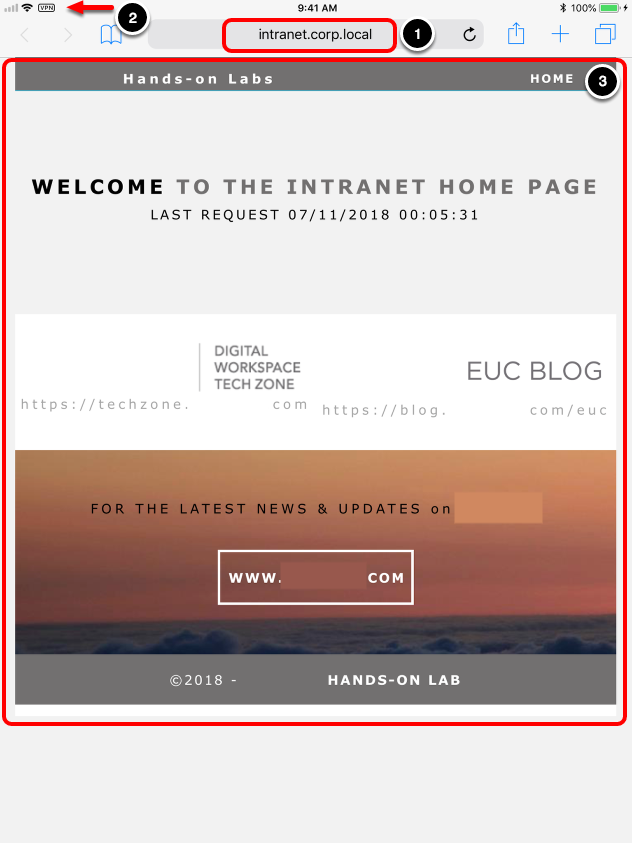
- Navigate to an internal website, for example,
http://intranet.corp.local/intranet. - You should see a VPN icon, indicating the connection is active. The Workspace ONE Tunnel client application identified a rule that applies to this situation, which you created in Define Device Traffic Rules.
- The website should load successfully.
Attempt to Access Intranet Site from Google Chrome
Next, verify that you cannot access the intranet from other browsers, even though the VPN connection is active for Safari.
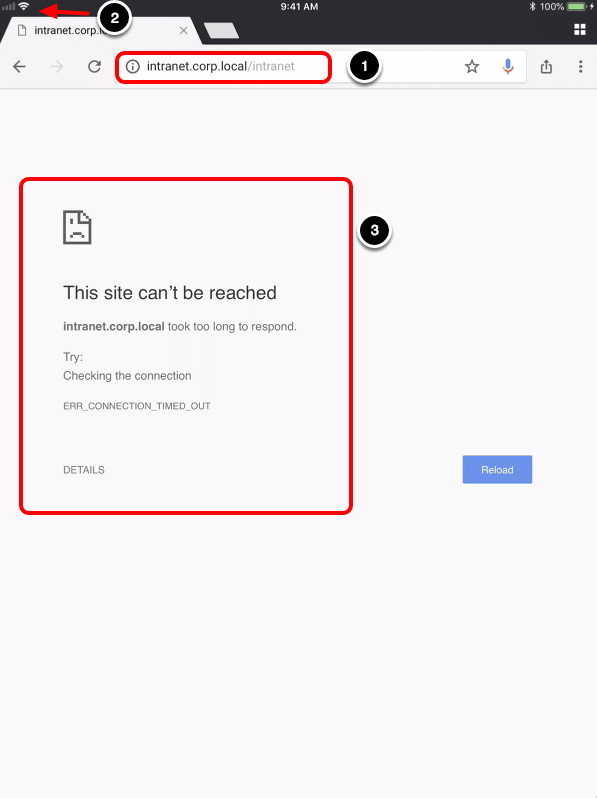
- Open Google Chrome and navigate to an internal website.
- Note that VPN is not active.
- You should see an error message stating This site can't be reached.
The website is published to an internal DNS that can only be accessed when using the VPN connection. The website does not load for Google Chrome because the device traffic rule configured allows access to the internal domain only through the Safari browser. Safari is enabled to initiate Per-App VPN Tunnel only for the domains configured in the device traffic rules.
Deploying Workspace ONE Tunnel on Other Platforms
Now that you have deployed the Tunnel Service with Unified Access Gateway, you can learn how to configure the Workspace ONE Tunnel client to enable access to the internal applications. Visit the following tutorial Deploying Workspace ONE Tunnel to obtain guidance and best practices to configure and deploy Workspace ONE Tunnel across mobile and desktop platforms.
Summary and Additional Resources
This operational tutorial provided steps to configure the Tunnel edge service for Unified Access Gateway in a Workspace ONE UEM environment.
The following procedures were included:
- Configure Tunnel in the Workspace ONE UEM console
- Deploy Unified Access Gateway enabling Tunnel edge services through PowerShell
- Define network traffic rules for Per-App Tunnel
- Configure VPN Profile and deployment Workspace ONE Tunnel client
- Validate access to internal websites based on device traffic rules
Additional Resources
For more information about Workspace ONE, explore the Workspace ONE UEM Product Page.
Additionally, you can check out the Workspace ONE and Horizon Reference Architecture which provides a framework and guidance for architecting an integrated digital workspace using Workspace ONE and Horizon.
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2024/05/29 |
|
| 2024/01/15 | Updated the following sections:
|
| 2021/09/16 | Updated the following sections:
|
| 2021/07/15 |
|
| 2020/10/06 |
|
| 2019/10/28 |
|
About the Author and Contributors
This tutorial was written by:
- Andreano Lanusse, Omnissa alumni.
With additional contributions from:
- Siddesh Patil, Senior Architect, Technical Marketing, Omnissa.
Feedback
Your feedback is valuable.
To comment on this paper, either use the feedback button or contact us at tech_content_feedback@omnissa.com.

