Business drivers, use cases and service definitions
This chapter is one of a series that make up the Omnissa Workspace ONE and Horizon Reference Architecture, a framework that provides guidance on the architecture, design considerations, and deployment of Omnissa Workspace ONE and Omnissa Horizon solutions. This chapter provides information about sample business drivers, typical use cases, and service definitions.
Addressing business requirements
An end-user-computing (EUC) solution based on Omnissa Workspace ONE, Horizon, and Horizon Cloud Service can address a wide-ranging set of business requirements and use cases. In this reference architecture, the solution targets the most common requirements and use cases seen in customer deployments to date.
A technology solution should directly address the critical business requirements that justify the time and expense of putting a new set of capabilities in place. Each and every design choice should center on a specific business requirement. Business requirements could be driven by the end user or by the team deploying EUC services.
The following are sample common key business drivers that can be addressed by the Workspace ONE solution.
Mobile access
Requirement definition: Provide greater business mobility by providing mobile access to modern and legacy applications on laptops, tablets, and smartphones.
Workspace ONE and Horizon solution: Omnissa Workspace ONE provides a straightforward, enterprise-secure method of accessing all types of applications that end users need from a wide variety of platforms.
- It is the first solution that brings together identity, device and application management, a unified application catalog, and mobile productivity.
- Omnissa Horizon Client technology supports all mobile and laptop devices as well as common operating systems.
- Omnissa Unified Access Gateway virtual appliances provide secure external access to internal resources without the need for a VPN.
Fast provisioning and access
Requirement definition: Allow fast provisioning of and secure access to line-of-business applications for internal users and third-party suppliers, while reducing physical device management overhead.
Workspace ONE and Horizon solution: Workspace ONE can support a wide range of device access scenarios, simplifying the onboarding of end-user devices.
- Adaptive management allows a user to download an app from a public app store and access some published applications. If a user needs to access more privileged apps or corporate data, they are prompted to enroll their device from within the app itself rather than through an agent, such as the Omnissa Workspace ONE Intelligent Hub app.
- Omnissa Horizon can provision hundreds of desktops in minutes using Instant Clone Technology. Horizon provides the ability to entitle groups or users to pools of desktops quickly and efficiently. Applications are delivered on a per-user basis using App Volumes.
- Omnissa Horizon Cloud Service delivers feature-rich virtual desktops and applications using a purpose-built cloud platform. This makes it easy to deliver virtualized Windows desktops and applications to any device, anytime. IT can save time getting up and running with an easy deployment process, simplified management, and a flexible subscription model.
- Unified Access Gateway appliances provide a secure and simple mechanism for external users to access virtual desktops or published applications customized using Dynamic Environment Manager.
Reduced application management effort
Requirement definition: Reduce application management overhead and reduce application provisioning time.
Workspace ONE and Horizon solution: Workspace ONE provides end users with a single application catalog for native mobile, SaaS, and virtualized applications and improves application management.
- Workspace ONE provides a consolidated view of all applications hosted across different services with a consistent user experience across all platforms.
- With Horizon and Horizon Cloud Service on Microsoft Azure, Windows-based applications are delivered centrally, either through virtual desktops or as RDSH-published applications. These can be centrally managed, allowing for access control, fast updates, and version control.
- Omnissa Workspace ONE Intelligence gives IT administrators insights into app deployments and app engagement. Analysis of user behavior combined with automation capabilities allow for quick resolution of issues, reduced escalations, and increased employee productivity.
- Omnissa App Volumes provides a simple solution for managing and deploying applications. Applications can be deployed “once” to a single central file and accessed by thousands of desktops. This simplifies application maintenance, deployment, and upgrades.
- Omnissa ThinApp provides additional features to isolate or make Windows applications portable across platforms.
Centralized and secure data and devices
Requirement definition: Centralize management and security of corporate data and devices to meet compliance standards.
Workspace ONE and Horizon solution: All components are designed with security as a top priority.
- Omnissa Workspace ONE UEM (powered by AirWatch) provides aggregation of content repositories, including SharePoint, network file shares, and cloud services. Files from these repositories can be synced to the Workspace ONE Content app for viewing and secure editing.
- Workspace ONE UEM policies can also be established to prevent distribution of corporate files, control where files can be opened and by which applications, and prevent such functions as copying and pasting into other apps, or printing.
- Horizon is a virtual desktop solution where user data, applications, and desktop activity do not leave the data center. Additional Horizon and Dynamic Environment Manager policies restrict and control user access to data.
- Horizon Cloud Service is the platform for delivering virtual desktops or published applications where user data, applications, and desktop activity do not leave the data center. Additional Horizon Cloud and Dynamic Environment Manager policies restrict and control user access to data.
- Workspace ONE Intelligence detects and remediates security vulnerabilities at scale. Quickly identify out-of-compliance devices and automate access control policies based on user behavior.
Comprehensive and flexible platform for corporate-owned or BYOD strategies
Requirement definition: Allow users to access applications, especially the Microsoft Office 365 suite, and corporate data from their own devices.
Workspace ONE and Horizon solution: Workspace ONE can meet the device-management challenges introduced by the flexibility demands of BYOD.
- Workspace ONE and features like adaptive management simplify end-user enrollment and empower application access in a secure fashion to drive user adoption.
- With Horizon 8 and Horizon Cloud Service, moving to a virtual desktop and published application solution removes the need to manage client devices, applications, or images. A thin client, zero client, or employee-owned device can be used in conjunction with Horizon Client. IT now has the luxury of managing single images of virtual desktops in the data center.
- Get insights into device and application usage over time with Workspace ONE Intelligence to enable optimizing resource allocation and license renewals. The built-in automation capabilities can tag devices that have been inactive for specific periods of time or notify users when their devices need to be replaced.
- Horizon 8 and Horizon Cloud Service allow cross-platform access to business-critical applications. As an example, developers, designers, and creatives with macOS can access Windows-native published applications without the need to install and manage a separately installed OS with Boot Camp. In other words, Horizon helps organizations cover the “Mac App gap” without heavy investment into cross-platform re-development of those business-critical apps. Additionally, Horizon improves the user experience by eliminating the need to switch operating systems with Boot Camp.
Reduced support calls and improved time to resolution
Requirement definition: Simplify and secure access to applications to speed up root-cause analysis and resolution of user issues.
Workspace ONE and Horizon solution: Workspace ONE provides single-sign-on (SSO) capabilities to a wide range of platforms and applications. By leveraging SSO technology, password resets are unnecessary.
- Omnissa Workspace ONE Access provides a self-service single point of access to all applications and, in conjunction with True SSO, provides a platform for SSO. Users no longer need to remember passwords or request applications through support calls.
- Both Workspace ONE UEM and Workspace ONE Access include dashboards and analytics to help administrators understand what a profile of application access and device deployment looks like in the enterprise. With greater knowledge of which applications users are accessing, administrators can more quickly identify issues with licensing or potential attempted malicious activities against enterprise applications.
- Workspace ONE Intelligence ensures that end users get the best mobile application experience by keeping an eye on app performance, app engagement, and user behavior. With detailed insights around devices, networks, operating systems, geolocation, connectivity state, and current app version, LOB owners can optimize their apps for their unique audience and ensure an optimal user experience.
Multi-site deployment business drivers
There are many ways and reasons to implement a multi-site solution, especially when deploying components on-premises. The most typical setup and requirement is for a two-data-center strategy. The aim is to provide disaster recovery, with the lowest possible recovery time objective (RTO) and recovery point objective (RPO); that is, to keep the business running with the shortest possible time to recovery and with the minimum amount of disruption.
The overall business driver for disaster recovery is straightforward:
- Keep the business operating during an extended or catastrophic technology outage.
- Provide continuity of service.
- Allow staff to carry out their day-to-day responsibilities.
With services, applications, and data delivered by Workspace ONE and Horizon, which means providing continuity of service and mitigating against component failure, all the way up to a complete data center outage.
With respect to business continuity and disaster recovery, this reference architecture addresses the following common key business drivers:
- Cope with differing levels and types of outages and failures.
- Develop predictable steps to recover functionality in the event of failures.
- Provide essential services and access to applications and data delivered by Workspace ONE and Horizon during outages.
- Minimize interruptions during outages.
- Provide the same or similar user experience during outages.
- Provide mobile secure access.
The following table describes the strategy used for responding to each of these business drivers. In this table, the terms active/passive and active/active are used.
- Active/passive recovery mode – Requires that the passive instance of the service be promoted to active status in the event of a service outage.
- Active/active recovery mode – Means that the service is available from multiple data centers without manual intervention.
Table 1: Meeting business requirements with multi-site deployments
| Business driver | Comments |
| Provide essential services and access to applications and data delivered by Workspace ONE and Horizon during outages. Minimize interruptions during outages. | The highest possible service level is delivered, and downtime is minimized, when all intra-site components are deployed in pairs and all services are made highly available. These services must be capable of being delivered from multiple sites, either in an active/active or active/passive manner. |
| Provide a familiar user experience during outages. | To maintain personalized environments for end users, replicate the parts that a user considers persistent (profile, user configuration, applications, and more). Reconstruct the desktop in the second data center using those parts. Workspace ONE Access provides a common entry point to all types of applications, regardless of which data center is actively being used. |
| Cope with differing levels and types of outages and failures. | This reference architecture details a design for multi-site deployments to cope with catastrophic failures all the way up to a site outage. The design ensures that there is no single point of failure within a site. |
| Develop predictable steps to recover functionality in the event of failures. | The services are constructed from several components and designed in a modular fashion. A proper design methodology, as followed in this reference architecture, allows each component to be designed for availability, redundancy, and predictability. With an effective design in place, you can systematically plan and document the whole end-user service and the recovery steps or processes for each component of the service. |
| Provide mobile secure access.
| Desktop mobility is a core capability in the Horizon platform. As end users move from device to device and across locations, the solution reconnects end users to the virtual desktop instances that they are already logged in to, even when they access the enterprise from a remote location through the firewall. Unified Access Gateway virtual appliances provide secure external access without the need for a VPN. |
Use cases
Use cases drive the design for any EUC solution and dictate which technologies are deployed to meet user requirements. Use cases can be thought of as common user scenarios. For example, a finance or marketing user might be considered a “normal office worker” use case.
Designing an environment includes building out the functional definitions for the use cases and their requirements. We define typical use cases that are also adaptable to cover most scenarios. We also define services to deliver the requirements of those use cases.
Workspace ONE use cases
This reference architecture includes the following common Workspace ONE use cases, as examples.
Table 2: Workspace ONE common use cases
| Use case | Description |
| Mobile task-based worker | Users who typically use a mobile device for a single task through a single application.
|
| Mobile knowledge worker | Many roles fit this profile, such as a hospital clinician or an employee in finance, marketing, HR, health benefits, approvals, or travel.
|
| Contractor | Contractors might require access to specific line-of-business applications, typically from a remote or mobile location.
|
Horizon use cases
This reference architecture includes the following example Horizon or Horizon Cloud Service use cases.
Table 3: Horizon use cases
| Use case | Description |
| Static task worker | These workers are typically fixed to a specific location with no remote access requirement. Some examples include call center worker, administration worker, and retail user. A static task worker:
|
| Mobile knowledge worker | This worker could be a hospital clinician, a company employee, or have a finance or marketing role. This is a catch-all corporate use case. A mobile knowledge worker:
|
| Software developer / IT (power user) | Power users require administrator privileges to install applications. The operating system could be either Windows or a Linux OS, with many applications, some of which could require extensive CPU and memory resources. A power user:
|
| Multimedia designer / engineer | These users might require GPU-accelerated applications, which have intensive CPU or memory workloads, or both. Examples are CAD/CAM designers, architects, video editors and reviewers, graphic artists, and game designers. A multimedia designer:
|
| Contractor | External contractors usually require access to specific line-of-business applications, typically from a remote or mobile location. A contractor:
|
Recovery use case requirements
When disaster recovery is being considered, the main emphasis falls on the availability and recoverability requirements of the differing types of users. For each of the previously defined use cases and their requirements, we can define the recovery requirements.
When using the cloud-based versions of services, such as Workspace ONE UEM, Workspace ONE Access, and Workspace ONE Intelligence, availability is delivered as part of the overall service SLA.
With solutions that have components deployed on-premises, the availability of both the platform delivering the service to the user and the data they expect to use, must be considered. For Horizon–based services, the availability portion of the solution might have dependencies on applications, personalization, and user data to deliver a full experience to the user in a recovery site. Consider carefully what type of experience will be offered in a recovery scenario and how that matches the business and user requirements.
This reference architecture discusses two common disaster recovery classifications: active/passive and active/active. When choosing between these recovery classifications, which are described in the following table, be sure to view the scenario from the user’s perspective.
Table 4: Disaster recovery classifications
| Use case and recoverability objective | Description |
| Active/passive RTO = medium RPO = medium | Users normally work in a single office location. Service consumed is pinned to a single data center. Failover of the service to the second data center ensures business continuity. |
| Active/active RTO = low RPO = low | Users require the lowest possible recovery time for the service (for example, health worker). Mobile users might roam from continent to continent. Users need to get served from the nearest geographical data center per continent. Service consumed is available in both primary and secondary data centers without manual intervention. Timely data replication between data centers is extremely important. |
With a Horizon–based service, the recovery service should aim to offer an equivalent experience to the user. Usually, the service at the secondary site is constructed from the same or similar parts and components as the primary site service. Consideration must be given to data replication and the speed and frequency at which data from the primary site can be replicated to the recovery site. This can influence which type of recovery service is offered, how quickly a recovery service can become available to users, and how complete that recovery service might be.
The RTO (recovery time objective) is defined as the time it takes to recover a given service. RPO (recovery point objective) is the maximum period in which data might be lost. Low targets are defined as 30- to 60-second estimates. Medium targets are estimated at 45–60 minutes. These targets depend on the environment and the components included in the recovery service.
Service definitions
From our business requirements, we outlined several typical use cases and their requirements. Taking the business requirements and combining them with one or more use cases enables the definition of a service.
The service, for a use case, defines the unique requirements and identifies the technology or feature combinations that satisfy those unique requirements. After the service has been defined, you can define the service quality to be associated with that service. Service quality takes into consideration the performance, availability, security, and management and monitoring requirements to meet SLAs.
The detail required to build out the products and components comes later, after the services are defined and the required components are understood.
Do not treat the list of services as exclusive or prescriptive; each environment is different. Adapt the services to your particular use cases. In some cases, which might mean adding components, while in others it might be possible to remove some that are not required.
You could also combine multiple services together to address more complex use cases. For example, you could combine a Workspace ONE service with a Horizon 8 or Horizon Cloud Service, and a recovery service.

Figure 1: Example of combining multiple services for a complex use case
Workspace ONE use case services
A use case service identifies the features required for a specific type of user. For example, a mobile task worker might use a mobile device for a single task through a single application. The Omnissa Workspace ONE use case service for this worker could be called the mobile device management service. This service uses only a few of the core Workspace ONE components, as described in the following table.
Table 5: Core components of Omnissa Workspace ONE
| Component | Function |
| Workspace ONE UEM | Enterprise mobility management |
| Omnissa Access | Identity platform |
| Workspace ONE Intelligence | Integrated insights, app analytics, and automation |
| Workspace ONE Intelligent Hub | End-user access to apps |
| Horizon | Virtual desktops and Remote Desktop Services (RDS) published applications delivered either through Horizon 8 or Horizon Cloud Service. |
| Workspace ONE Boxer | Secure email client |
| Workspace ONE Web | Secure web browser |
| Workspace ONE Content | Mobile content repository |
| Workspace ONE Tunnel | Secure and effective method for individual applications to access corporate resources |
| AirWatch Cloud Connector | Directory sync with enterprise directories |
| Workspace ONE Access Connector | Directory sync with enterprise directories Sync to Horizon resources |
| Unified Access Gateway | Gateway that provides secure edge services |
Enterprise mobility management service
Many organizations have deployed mobile devices and have lightweight management capabilities, like simple email deployment and device policies, such as a PIN requirement, device timeouts, and device wiping. But they lack a comprehensive and complete management practice to enable a consumer-simple, enterprise-secure model for devices. The following figure shows a high-level illustration of a Workspace ONE Standard deployment and the available components delivering an Enterprise Mobility Management Service
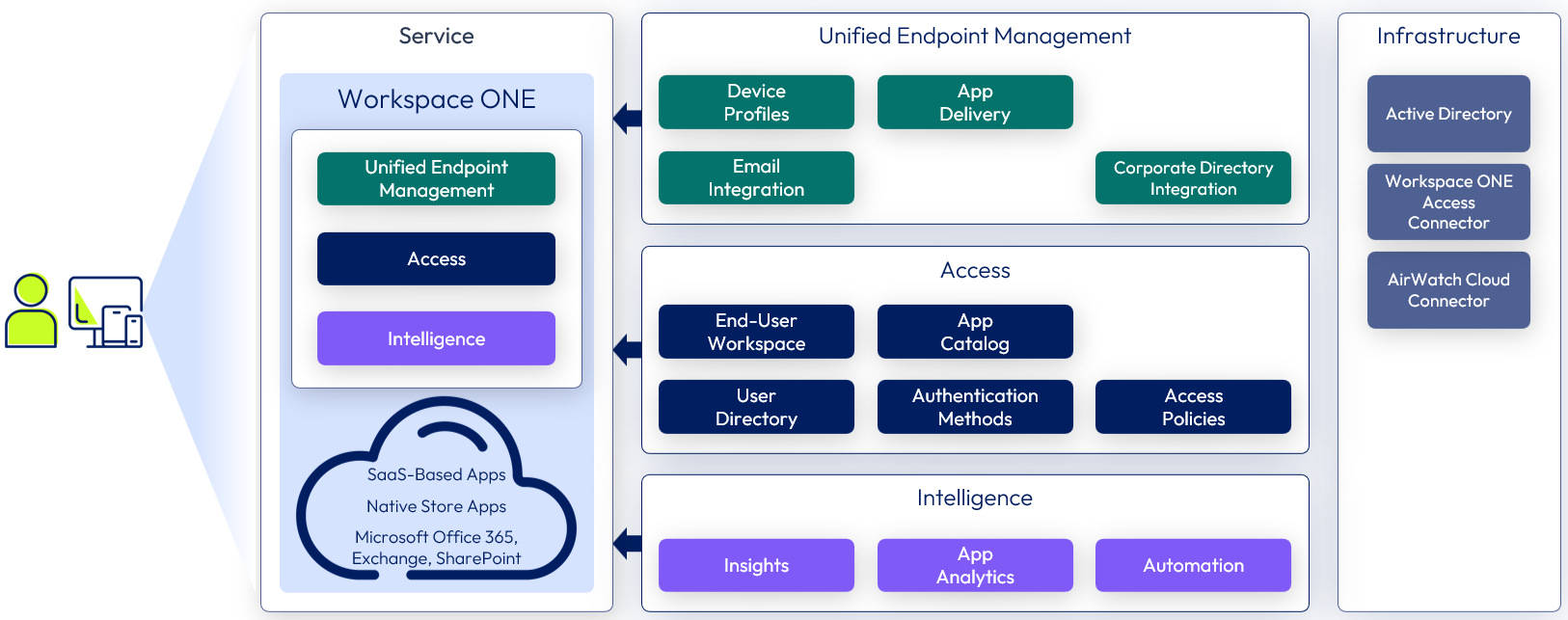
Figure 2: Enterprise mobility management service
Enterprise productivity service
Organizations with a more evolved device management strategy are often pushed by end users to enable more advanced mobility capabilities in their environment. Requested capabilities include single sign-on (SSO) and multi-factor authentication, and access to productivity tools. However, from an enterprise perspective, providing this much access to corporate information means instituting a greater degree of control, such as blocking native email clients in favor of managed email, requiring syncing content with approved repositories, and managing which apps can be used to open files. The following figure shows a high-level illustration of a Workspace ONE Advanced deployment and the available components delivering an Enterprise Productivity Service.
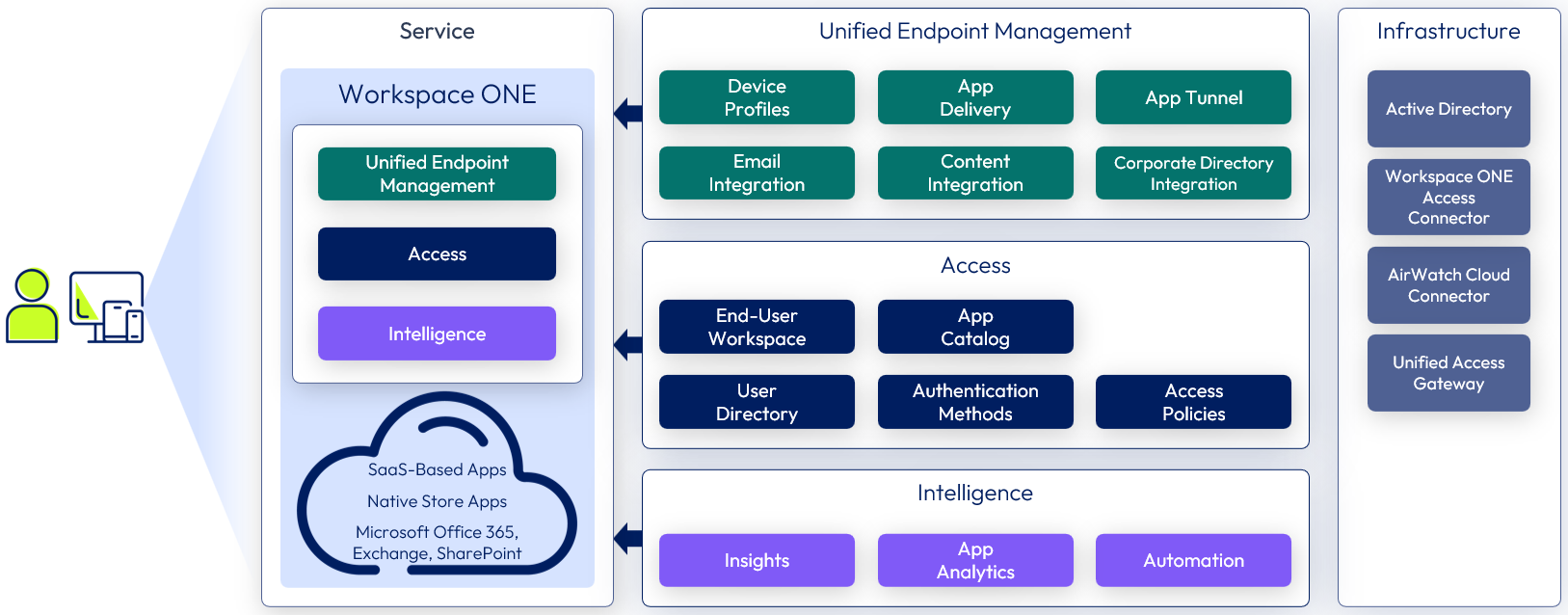
Figure 3: Enterprise productivity service
Enterprise application workspace service
Recognizing that some applications are not available as a native app on a mobile platform and that some security requirements dictate on-premises application access, virtualized applications and desktops become a core part of a mobility strategy. Building on the mobile productivity service, and adding access to Horizon–based resources, enables this scenario.
Many current Horizon users benefit from adding the Workspace ONE catalog capabilities as a single, secure point of access for their virtual desktops and published applications.
The following figure shows a high-level illustration of a Workspace ONE Enterprise Edition deployment and the available components delivering an Enterprise Application Workspace Service.
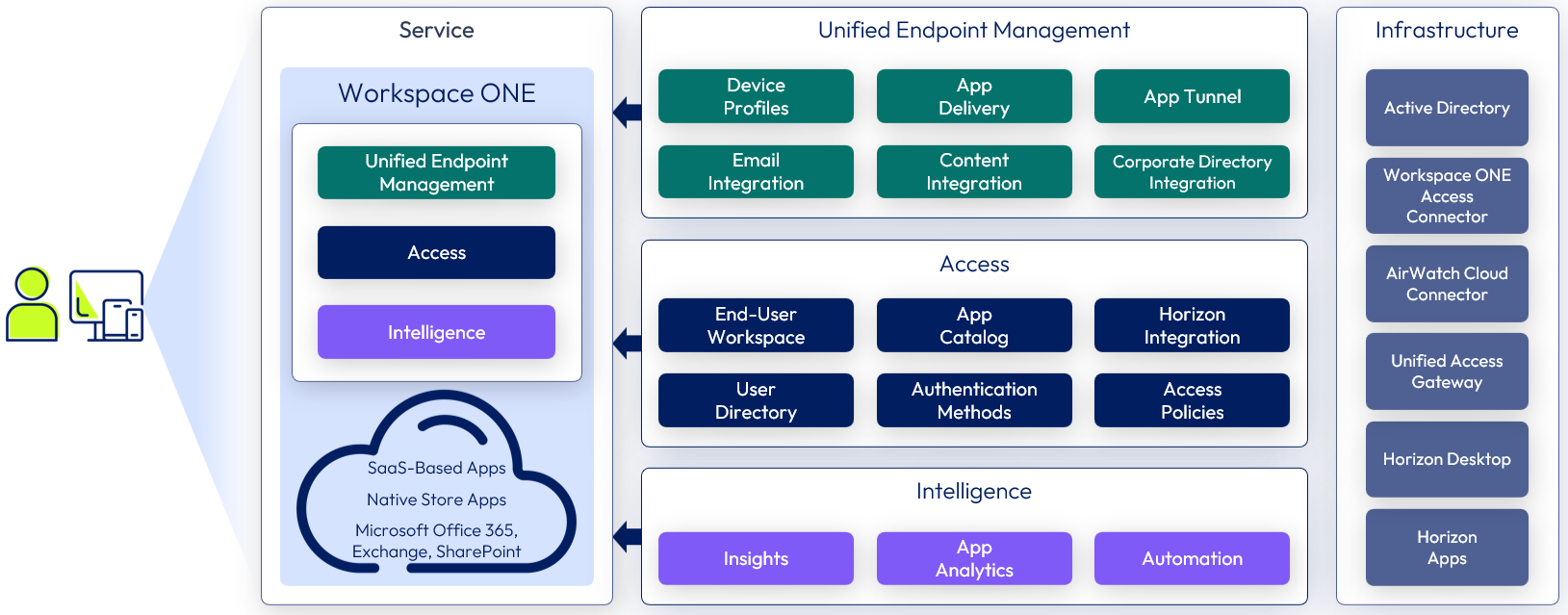
Figure 4: Enterprise application workspace service
Horizon 8 use case services
Omnissa Horizon 8 use case services address a wide range of user needs. The following section illustrates typical services that address common use cases. These can be amended to suit your use cases.
For example, a Published Application service can be created for static task workers, who require only a few Windows applications. In contrast, a GPU-Accelerated Desktop service can be created for multimedia designers who require graphics drivers that use hardware acceleration.
The following components are used across the various use cases.
Table 6: Core components of Omnissa Horizon 8
| Component | Function |
| Horizon 8 | Virtual desktops and RDSH-published applications |
| App Volumes | Application management and deployment |
| Dynamic Environment Manager | User profile, IT settings, and configuration for environment and applications |
Horizon 8 published application service
Windows applications are delivered as published applications provided by farms of Remote Desktop Service Host (RDSH) servers. The RDSH servers are created using instant clones to provide space and operational efficiency. Applications are delivered through App Volumes. Dynamic Environment Manager applies profile settings and folder redirection.
The following figure shows a high-level illustration of a Horizon 8 Published Application Service deployment and the components required to deliver the service.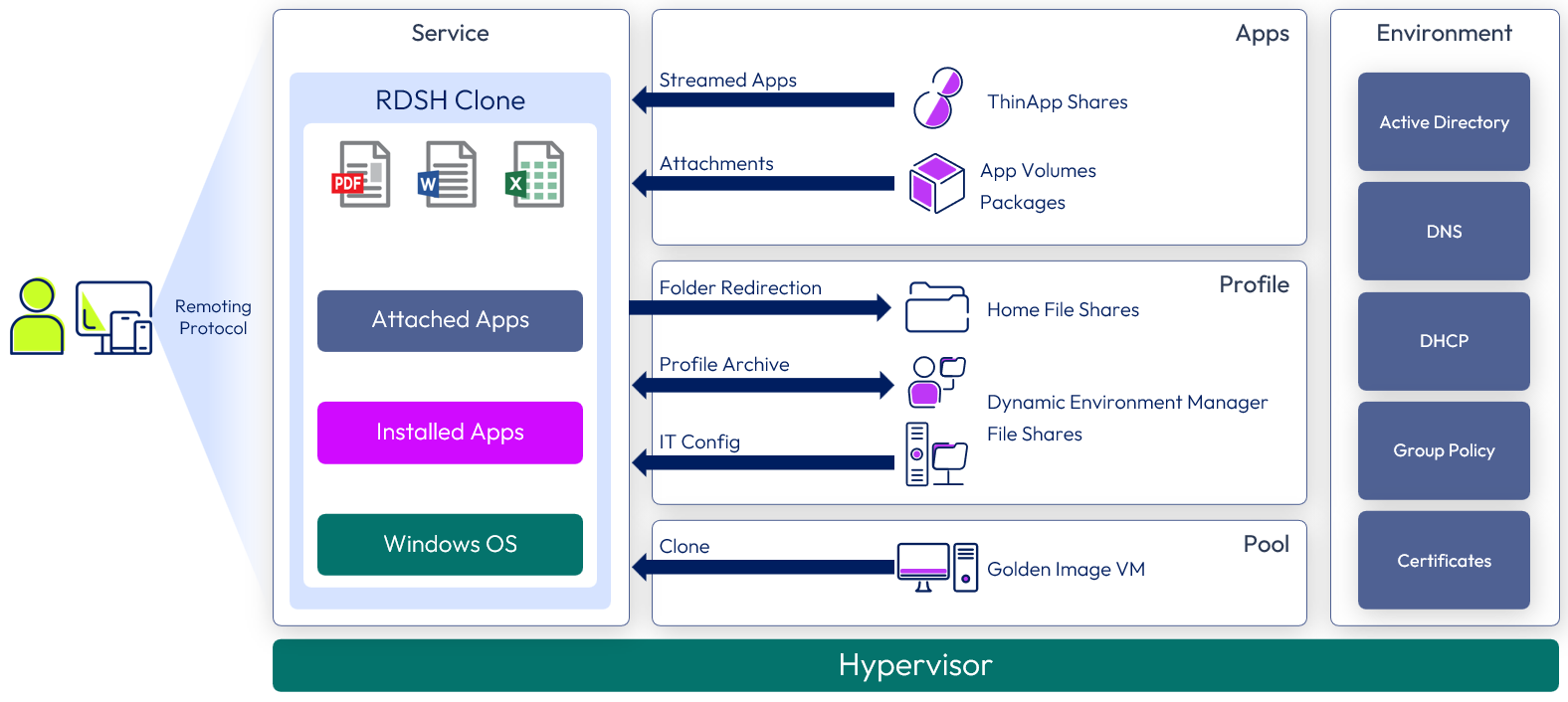
Figure 5: Horizon 8 published application service
Horizon 8 GPU-accelerated application service
Similar to the Horizon 8 Published Application service but has more CPU and memory, and uses hardware-accelerated rendering with NVIDIA GRID graphics cards installed in the vSphere servers (vGPU). Delivering GPU-Accelerated applications using RDSH-published applications is ideal for occasional use of graphical applications where users may only require a small number of apps to be accelerated.
The following figure shows a high-level illustration of a Horizon 8 GPU-Accelerated Application Service deployment and the components required to deliver the service.
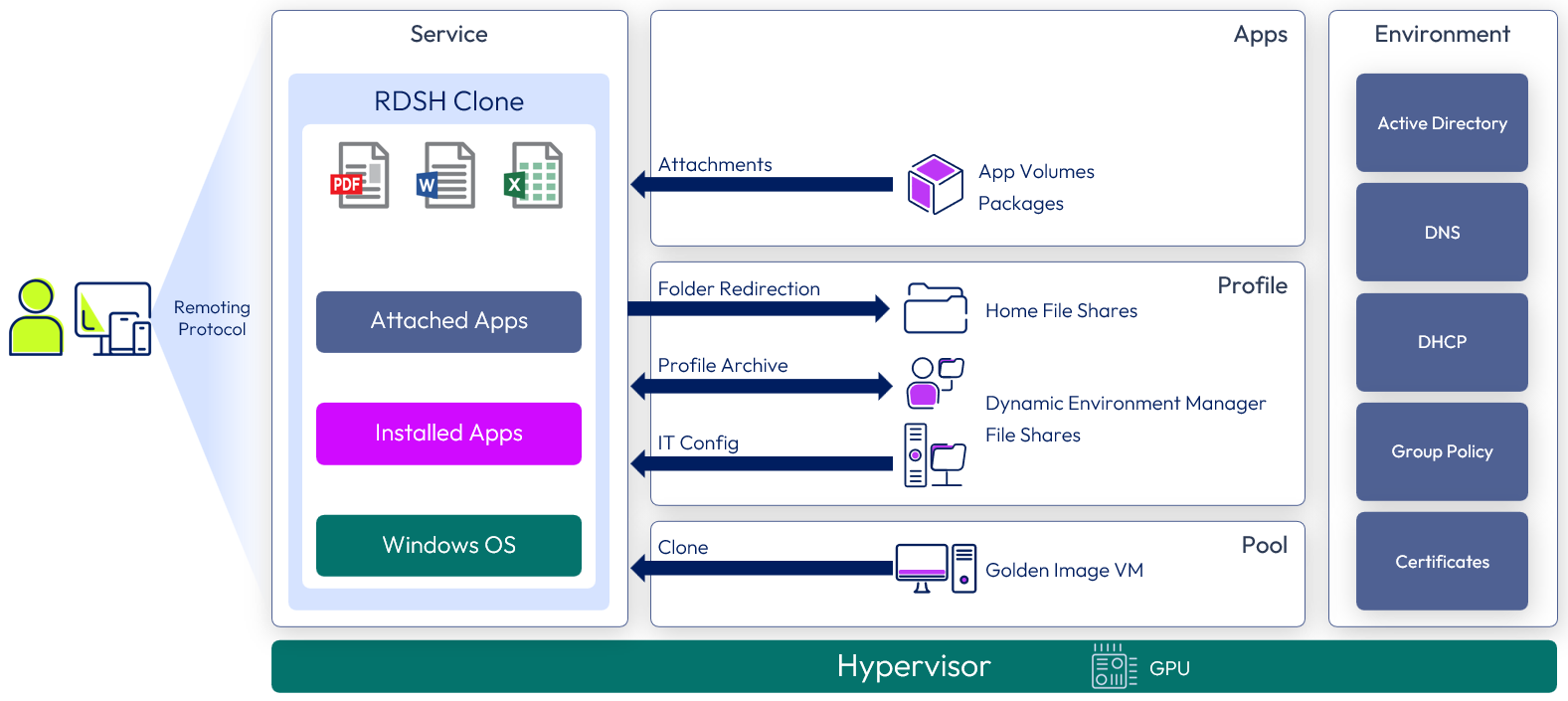
Figure 6: Horizon 8 GPU-accelerated application service
Horizon 8 published apps on demand service
Windows applications are delivered as published applications provided by farms of RDSH servers. The RDSH servers are created using instant clones to provide space and operational efficiency. Applications are delivered through App Volumes. Dynamic Environment Manager applies profile settings and folder redirection.
The RDSH farm is associated with an App Volumes instance and the App Volumes packages are attached to the RDSH servers in real-time, as a user requests an application.
The following figure shows a high-level illustration of a Horizon Apps on Demand Service deployment and the components required to deliver the service.
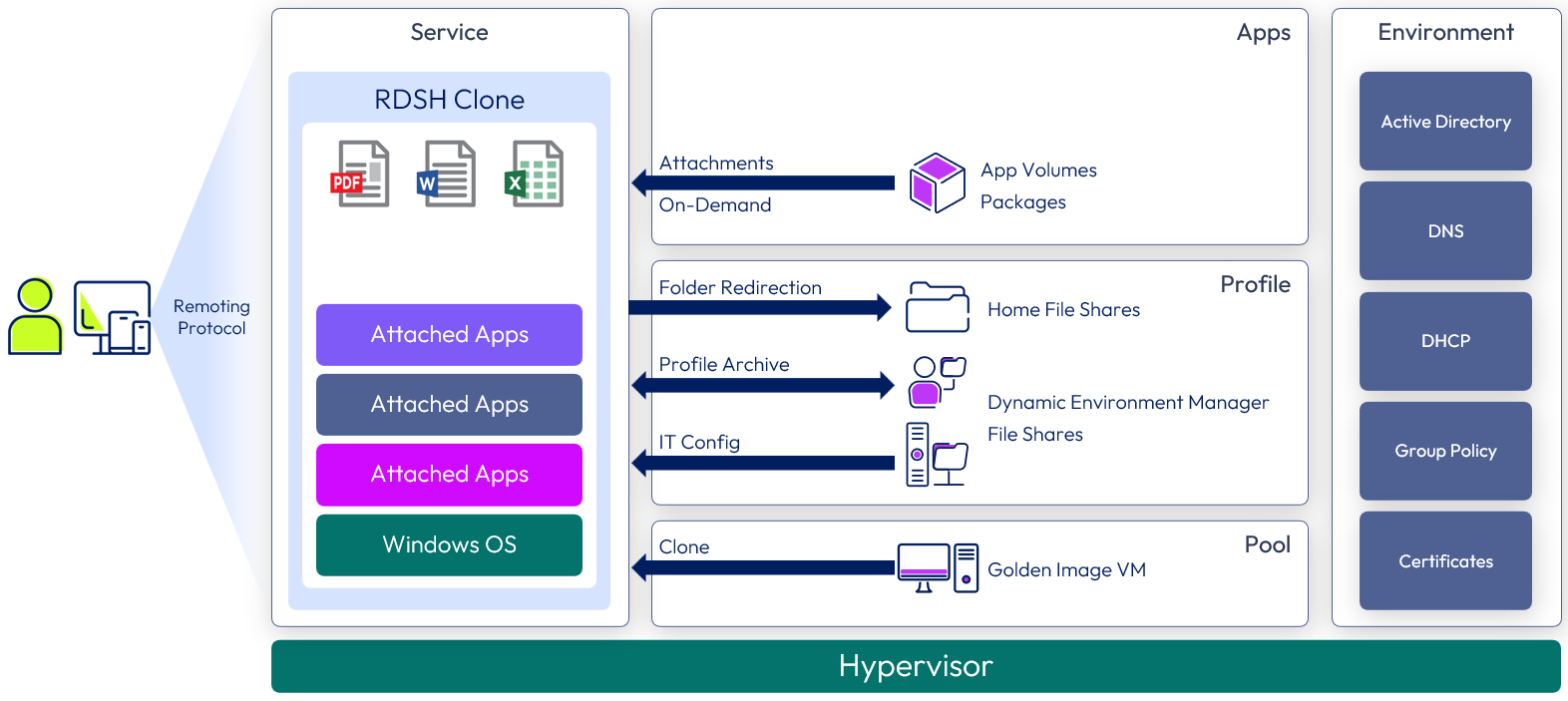
Figure 7: Horizon 8 published apps on demand service
For more information, see Horizon Published Apps on Demand.
Horizon 8 desktop service
The core Windows 11 or Windows 10 desktop is an instant clone, which is kept to a plain Windows OS, allowing it to address a wide variety of users.
The majority of applications are delivered through App Volumes, with core and different departmental versions. Individual or conflicting applications are packaged with ThinApp and are available through the Workspace ONE Access catalog. Dynamic Environment Manager applies profile settings and folder redirection.
The following figure shows a high-level illustration of a Horizon 8 Desktop Service deployment and the components required to deliver the service.
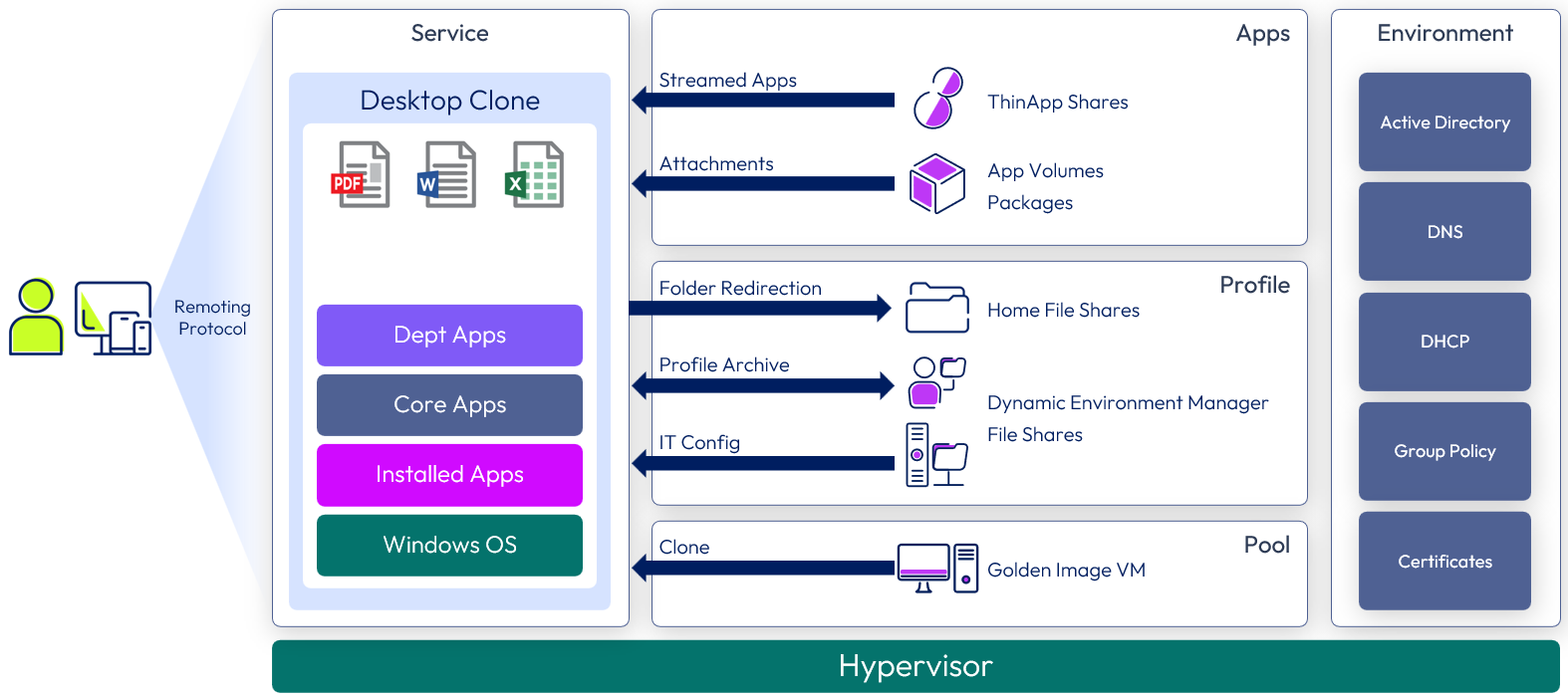
Figure 8: Horizon 8 Desktop Service
Horizon 8 desktop with user-installed applications service
Similar to the construct of the Horizon 8 Desktop service, with the addition of an App Volumes writable volume. Writable volumes allow users to install their own applications and have them persist across sessions. One typical use case is for software developers or IT power users.
The following figure shows a high-level illustration of a Horizon 8 Desktop with User-Installed Applications Service deployment and the components required to deliver the service.
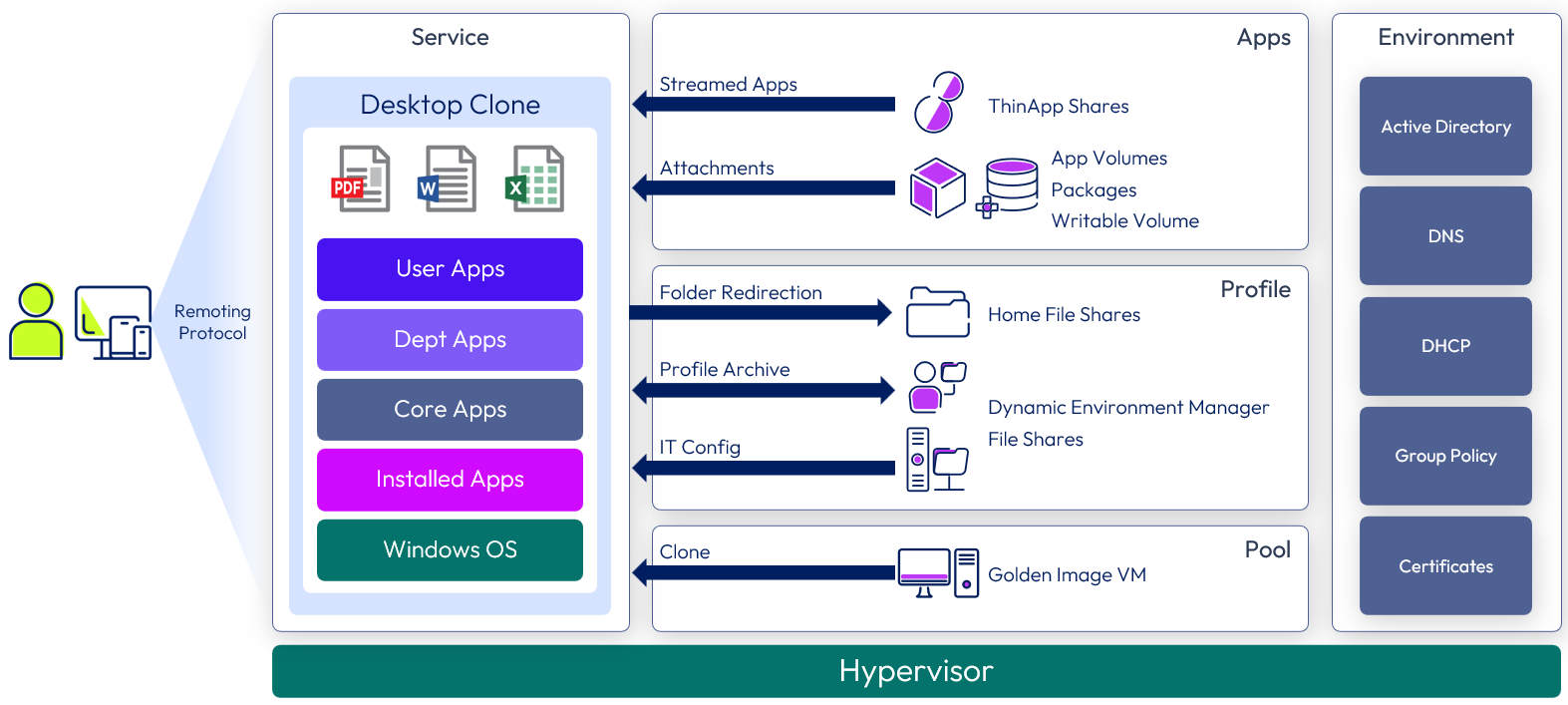
Figure 9: Horizon 8 desktop with user-installed applications service
Horizon 8 GPU-accelerated desktop service
Similar to the Horizon 8 Desktop Service or the Horizon Desktop with User-Installed Applications service but has more CPU and memory and can use hardware-accelerated rendering with NVIDIA GRID graphics cards installed in the vSphere servers (vGPU).
The following figure shows a high-level illustration of a Horizon 8 GPU-Accelerated Desktop Service deployment and the components required to deliver the service.
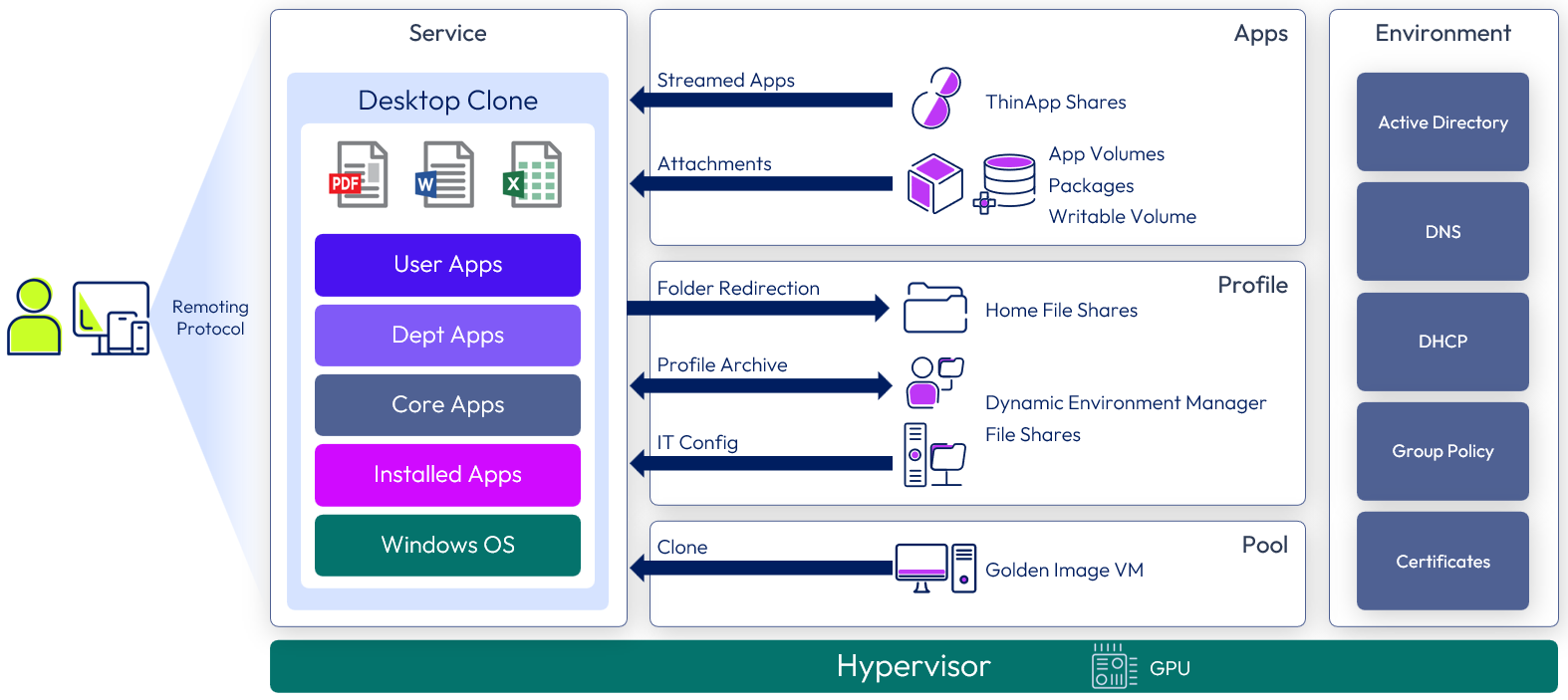
Figure 10: Horizon 8 GPU-Accelerated Desktop Service
Horizon 8 Linux desktop service
The core desktop is an instant clone of Linux. Applications can be pre-installed into the golden image VM.
The following figure shows a high-level illustration of a Horizon 8 Linux Desktop Service deployment and the components required to deliver the service.
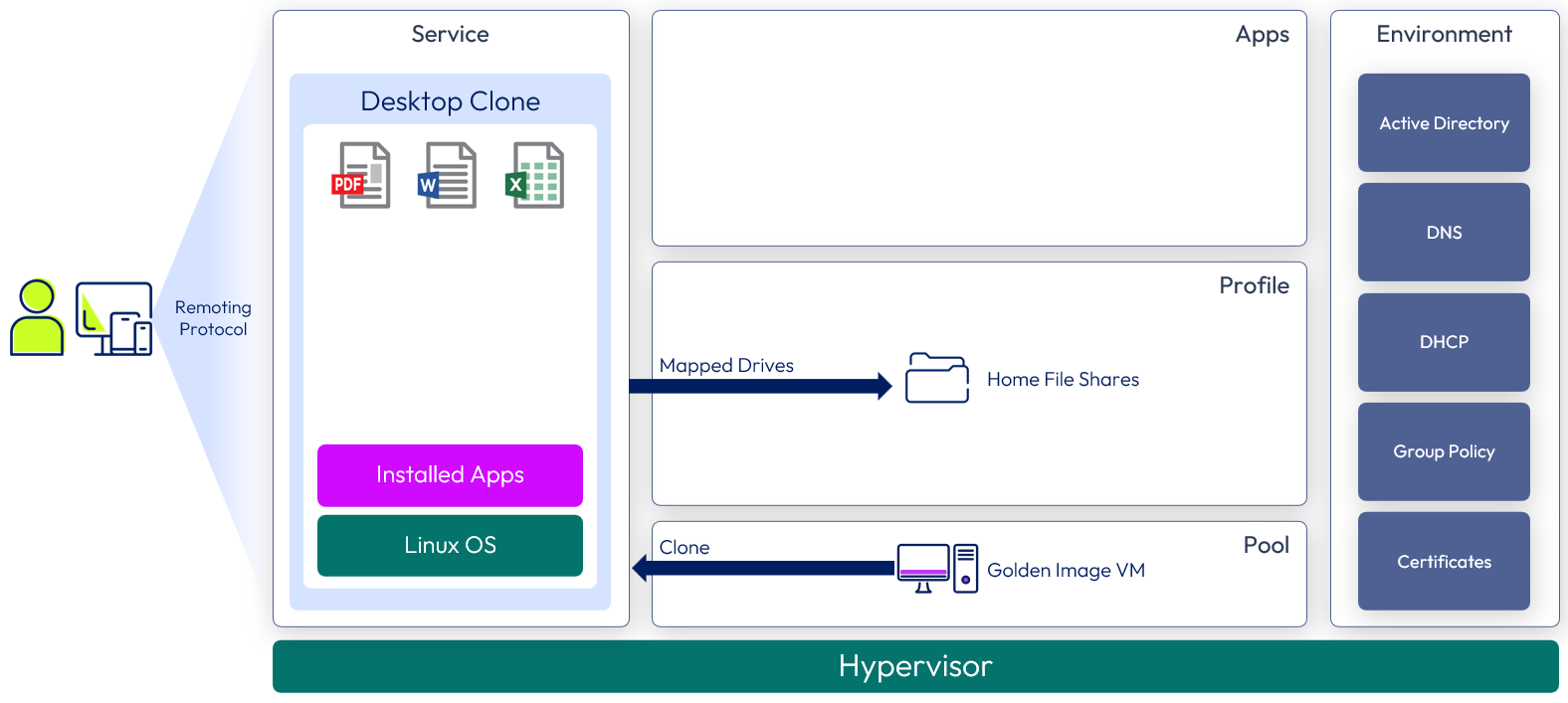
Figure 11: Linux desktop service
Horizon Cloud Service use case services
These services address a wide range of user needs. For example, a published application service can be created for static task workers, who require only a few Windows applications. In contrast, a secure desktop service could be created for users who need a larger number of applications that are better suited to a Windows desktop–based offering.
The following core components are used across the various use cases.
Table 7: Core components of Omnissa Horizon Cloud Service next-gen
| Component | Function |
| Horizon Cloud Service | Virtual desktops, shared desktops and RDSH-published applications |
| Dynamic Environment Manager | User profile, IT settings, and configuration for environment and applications |
| Cloud Capacity Provider E.g. Microsoft Azure | Infrastructure platform |
Horizon Cloud Service shared desktop service
Windows desktop experiences are delivered using Windows 10 multi-session desktops. Windows multi-session functionality is currently a feature only available for use on Microsoft Azure based infrastructure. These desktops are optionally available in the catalog and through the Workspace ONE app or web application. Dynamic Environment Manager applies profile settings and folder redirection.
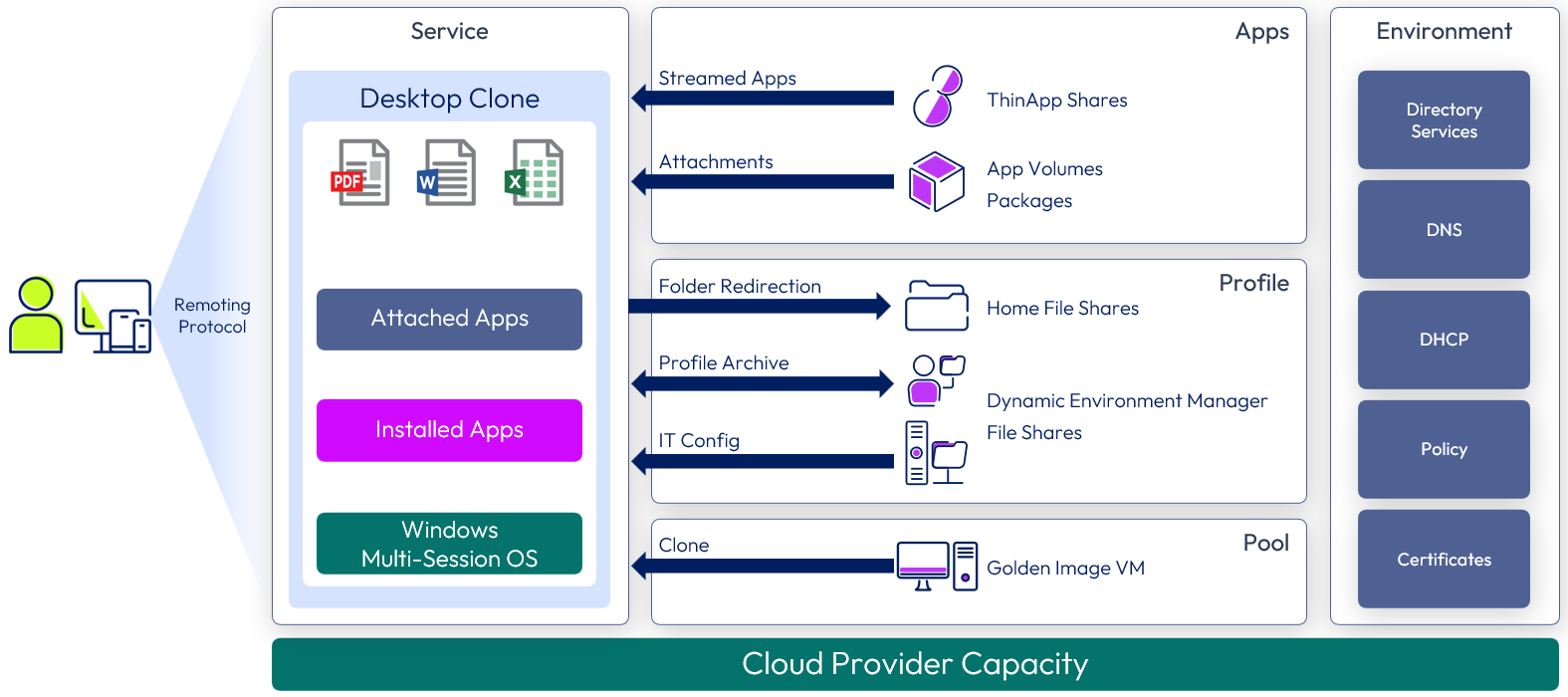
Figure 12: Horizon Cloud Service shared desktop service
Horizon Cloud Service published application service
Windows applications are delivered as published applications provided by farms of RDSH servers or Windows 10/11 multi-session hosts. These applications are optionally available in the catalog and through the Workspace ONE app or web application. Dynamic Environment Manager applies profile settings and folder redirection.
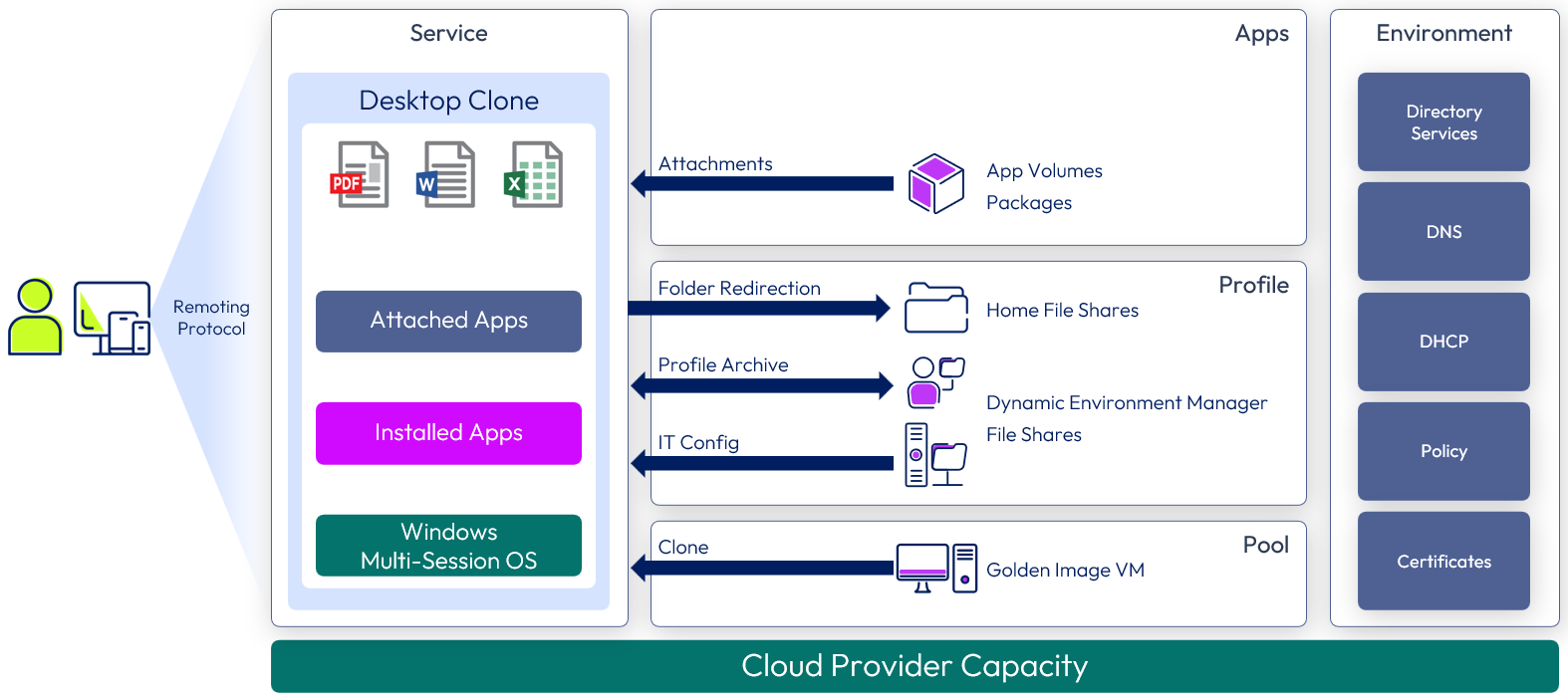
Figure 13: Horizon Cloud Service published application service
Horizon Cloud Service GPU-accelerated application service
Overview: Similar to the Horizon Cloud Service Published Application service, but this service uses hardware-accelerated rendering with NVIDIA GRID graphics cards available through Microsoft Azure. The Windows applications are delivered as published applications provided by farms of RDSH servers.
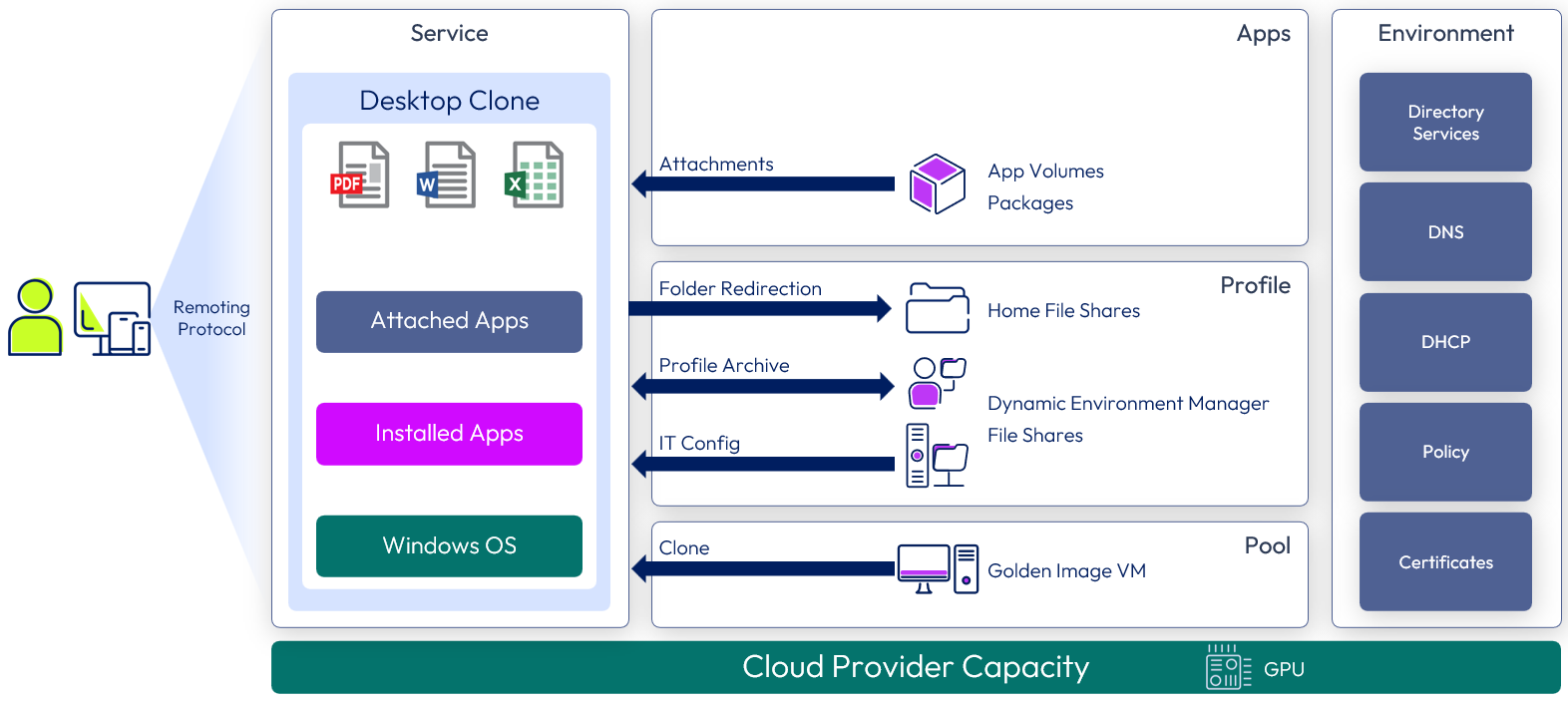
Figure 14: Horizon Cloud Service GPU-accelerated application service
Horizon Cloud Service desktop service
This service uses a standard Windows 10/11 desktop that is cloned from a golden image VM. Dynamic Environment Manager applies the user’s Windows environment settings, application settings, and folder redirection. Desktop and application entitlements are optionally made available through the Workspace ONE Access catalog.
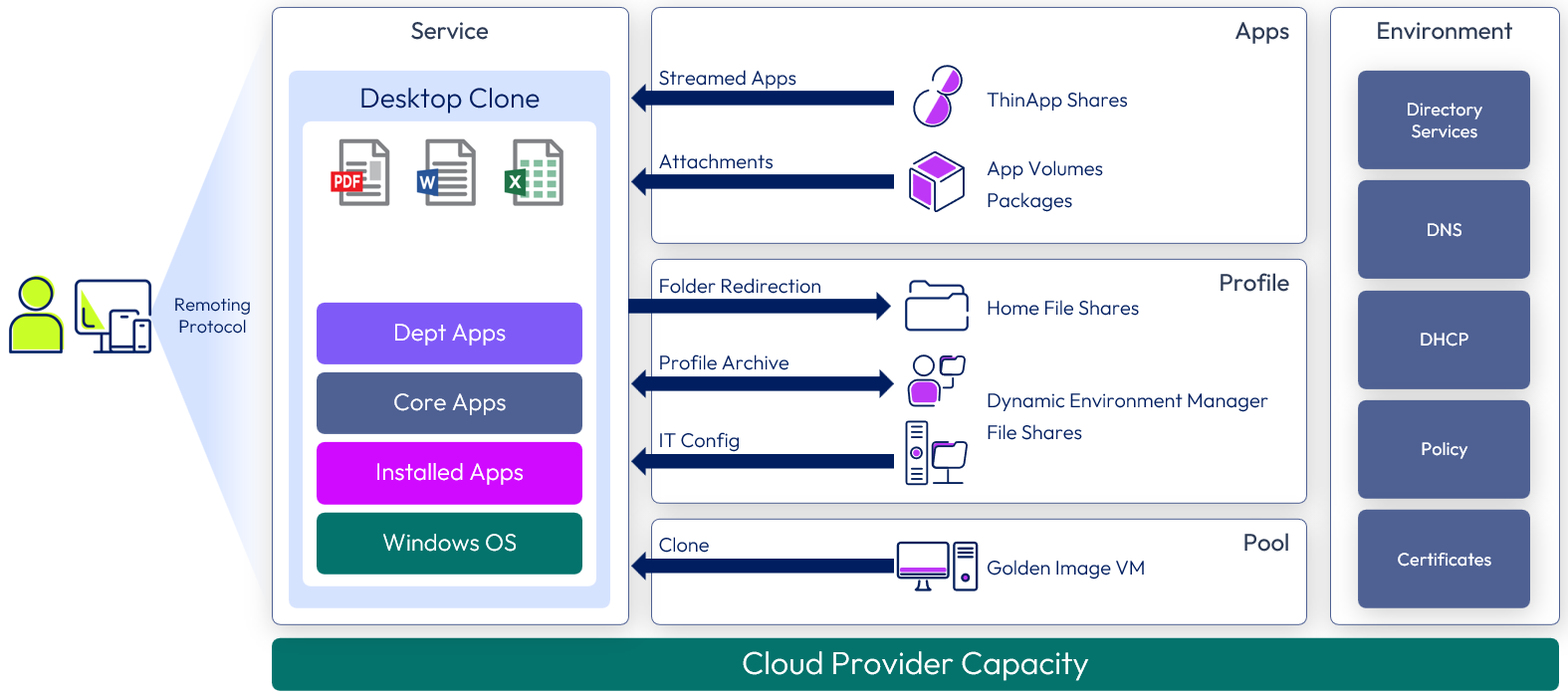
Figure 15: Horizon Cloud Service desktop service
Recovery services
To ensure availability, recoverability, and business continuity, the design of the services also needs to consider disaster recovery. We can define recovery services and map them to the previously defined use-case services.
Recovery services can be designed to operate in either an active/active or an active/passive mode and should be viewed from the users’ perspective.
- In active/passive mode, loss of an active data center instance requires that the passive instance of the service be promoted to active status for the user.
- In active/active mode, the loss of a data center instance does not impact service availability for the user because the remaining instance or instances continue to operate independently and can offer the end service to the user.
In the use cases, a user belongs to a home site and can have an alternative site available to them. Where user pinning is required, an active/passive approach results in a named user having a primary site they always connect to or get redirected to during normal operations.
Also, a number of components are optional to a service, depending on what is required. Service definitions for multi-site Workspace ONE Access, App Volumes, and Dynamic Environment Manager data are detailed after the main active/passive and active/active recovery services.
For guidance and considerations for Horizon, see Providing Disaster Recovery for Horizon.
Workspace ONE Access Recovery Service - on-premises
Workspace ONE Access can also be consumed as a cloud-based service or deployed on-premises. When deployed on-premises, it is important to provide resilience and failover capability both within and between sites to ensure business continuity. Workspace ONE Access can be architected in an active/passive manner, with a failover process recovering the service in the standby site.

Figure 16: Workspace ONE Access recovery
Horizon 8 active-passive recovery service
Requirement: The service delivered to a set of users is run from a specific data center but can be failed over to a second data center in the event of an outage.
Overview: The core Windows desktop is an instant clone or linked clone, which is preferably kept to a vanilla Windows OS, allowing it to address a wide variety of users. The core could also be a desktop or session provided by an RDSH farm of linked clones or instant clones.
Although applications can be installed in the golden image OS, the preferred method is to have applications delivered through App Volumes, with core and department-specific applications included in various packages. Individual or conflicting applications are packaged with ThinApp and are available through the Workspace ONE Access catalog.
If the use case requires the ability for users to install applications themselves, App Volumes writable volumes can be assigned.
Dynamic Environment Manager applies the profile, IT settings, user configuration, and folder redirection.
The following table details the recovery requirements and the corresponding Horizon component that addresses each requirement.
Table 8: Active/passive recovery service requirements
| Requirement | Comments |
| Windows desktop or RDSH available in both sites | Horizon 8 pools or farms are created in both data centers. Golden image VM can be replicated to ease creation. Universal Broker or Cloud Pod Architecture (CPA) is used for user entitlement and to control consumption. |
| Native applications | Applications are installed natively in the base Windows OS. No replication is required because native applications exist in both data center pools. |
| Attached applications (optional) | Applications contained in App Volumes packages are replicated. |
| User-installed applications (optional) | App Volumes writable volumes. RTO = 60–90 minutes RPO = 1–2 hours (array dependent) |
| IT settings | Dynamic Environment Manager IT configuration is replicated to another data center. RTO = 30–60 seconds RPO = Approximately 5 minutes |
| User data and configuration | Dynamic Environment Manager user data is replicated to another data center. RTO = 30–60 seconds RPO = Approximately 2 hours |
| SaaS applications | Workspace ONE Access is used as a single-sign-on workspace and is present in both locations to ensure continuity of access. |
| Mobile access | Unified Access Gateway, Blast Extreme |
At a high level, this service consists of a Windows environment delivered by either an instant-clone desktop or RDSH server, with identical pools created at both data centers. With this service, applications can be natively installed in the OS, provided by App Volumes packages, or some combination of the two. User profile and user data files are made available at both locations and are also recovered in the event of a site outage.
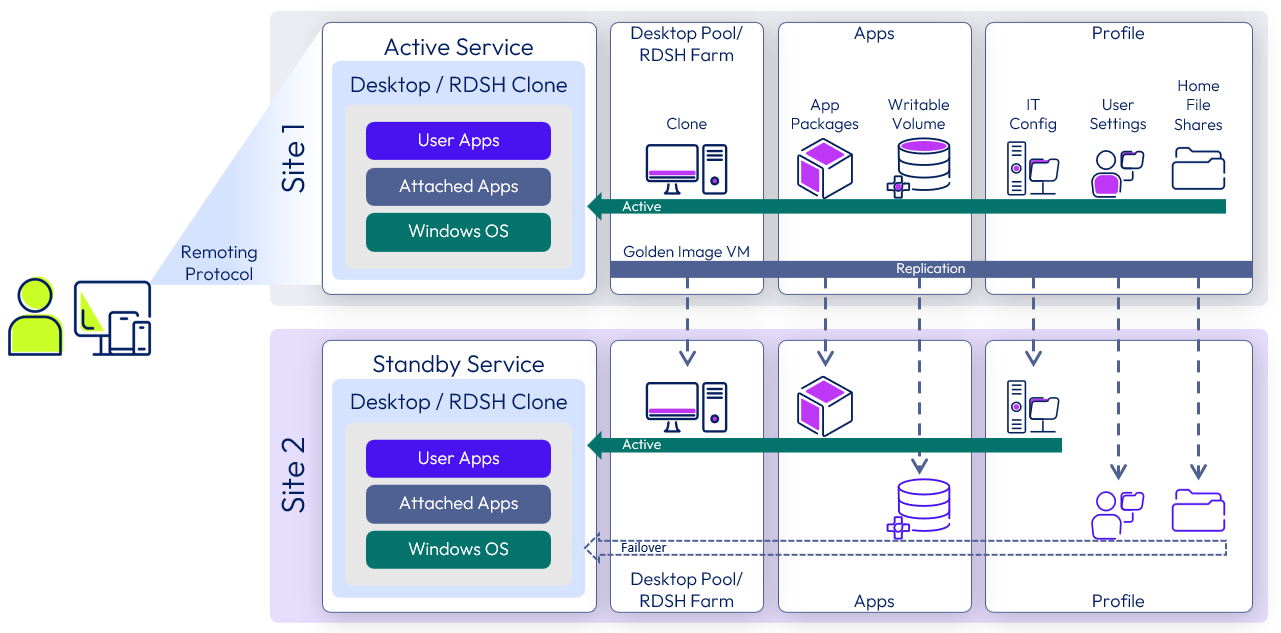
Figure 17: Horizon 8 active/passive recovery service
Horizon 8 active-active recovery service
Requirement: This service delivered to a set of users is available from multiple data centers without manual intervention.
Overview: Windows applications are delivered as natively installed applications in the Windows OS, and there is little to no reliance on the Windows profile in case of a disaster. Dynamic Environment Manager provides company-wide settings during a disaster. Optionally, applications can be delivered through App Volumes packages, with core and department-specific applications included in various packages.
This service generally requires the lowest possible RTO, and the focus is to present the user with a desktop closest to his or her geographical location. For example, when traveling in Europe, the user gets a desktop from a European data center; when traveling in the Americas, the same user gets a desktop from a data center in the Americas.
The following table details the recovery requirements and the corresponding Horizon component that addresses each requirement.
Table 9: Active/active recovery service requirements
| Requirements | Products, Solutions, and Settings |
| Lowest possible RTO during a disaster | No reliance on services that cannot be immediately failed over. |
| Windows desktop or RDSH server available in both sites | Horizon desktop and application pools are created in both data centers. Golden image VM can be replicated to ease creation. Universal Broker or Cloud Pod Architecture (CPA) is used to ease user entitlement and consumption. |
| Native applications | Applications are installed natively in the base Windows OS. No replication is required because native applications exist in both data center pools. |
| Attached applications (optional) | Applications contained in App Volumes packages are replicated using App Volumes storage groups. |
| IT settings | Dynamic Environment Manager IT configuration is replicated to another data center. The following RTO and RPO targets apply during a data center outage when a recovery process is required: RTO = 30–60 seconds RPO = 30–60 seconds |
| User data and configuration (optional) | Dynamic Environment Manager user data is replicated to another data center. The following RTO and RPO targets apply during a data center outage when a recovery process is required: RTO = 30–60 seconds RPO = Approximately 2 hours |
| Mobile access | Unified Access Gateway, Blast Extreme |
At a high level, this service consists of a Windows environment delivered by a desktop or an RDSH server available at both data centers. With this service, applications can be natively installed in the OS, attached using App Volumes packages, or some combination of the two. If required, the user profile and user data files can be made available at both locations and can also be recovered in the event of a site outage.

Figure 18: Horizon 8 active/active recovery service
App Volumes active-passive recovery service
Although applications can be installed in the base OS, they can alternatively be delivered by App Volumes packages. A package is used to attach applications to either the Horizon desktop or the RDSH server that provides Horizon-published applications.
Applications are attached either to the desktop, at user login, or to the RDSH server as it boots. Because packages are read-only to users and are infrequently changed by IT, packages can be replicated to the second, and subsequent, locations and are available for assignment and mounting in those locations as well.
App Volumes writable volumes are, by contrast, used for content such as user-installed applications, and are written to by the end user. Writable volumes must be replicated and made available at the second site. Due to the nature of the content, writable volumes can have their content updated frequently by users. These updates can affect the RPO and RTO achievable for the overall service. Operational decisions can be made as to whether to activate the service in Site 2 with or without the writable volumes to potentially reduce the RTO.
For design guidance on multi-site App Volumes deployments, see Multi-site Design in App Volumes Architecture.
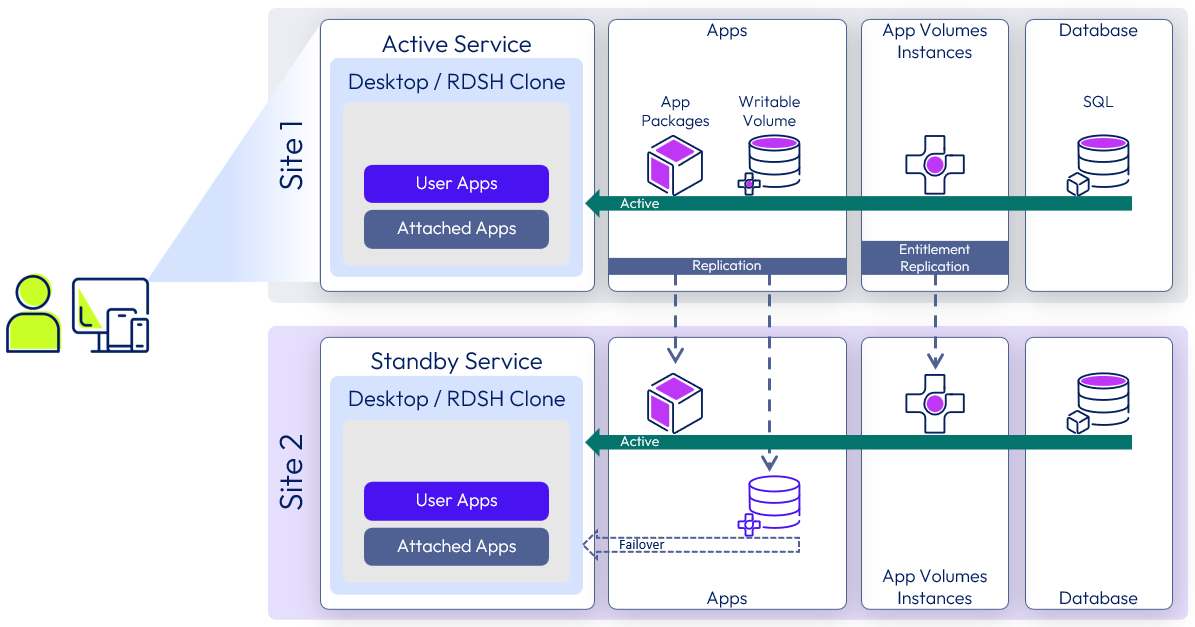
Figure 19: App Volumes active/passive recovery
App Volumes active-active recovery service
As can be seen in the active/passive App Volumes service, App Volumes packages can be replicated from one site to another and made available, actively, in both because packages require read-only permissions for the user. The complication comes with writable volumes because these require both read and write permissions for the user. If a service does not include writable volumes, the App Volumes portion of the service can be made active/active.

Figure 20: App Volumes active/active recovery
Dynamic Environment Manager profile data recovery service
Dynamic Environment Manager provides profile management by capturing user settings for the operating system, applications, and user personalization. The captured settings are stored on file shares that need to be replicated to ensure site redundancy.
Although profile data can be made available to both data centers, there is a failover process in the event of the loss of Site 1 that can impact the RTO and RPO.
Operational decisions can be made in these scenarios as to whether the service in Site 2 would be made available with reduced functionality (for example, available with the Windows base, the applications, and the IT configuration but without the user-specific settings).
For design guidance on multi-site Dynamic Environment Manager deployments, see Multi-site Design in Dynamic Environment Manager Architecture.
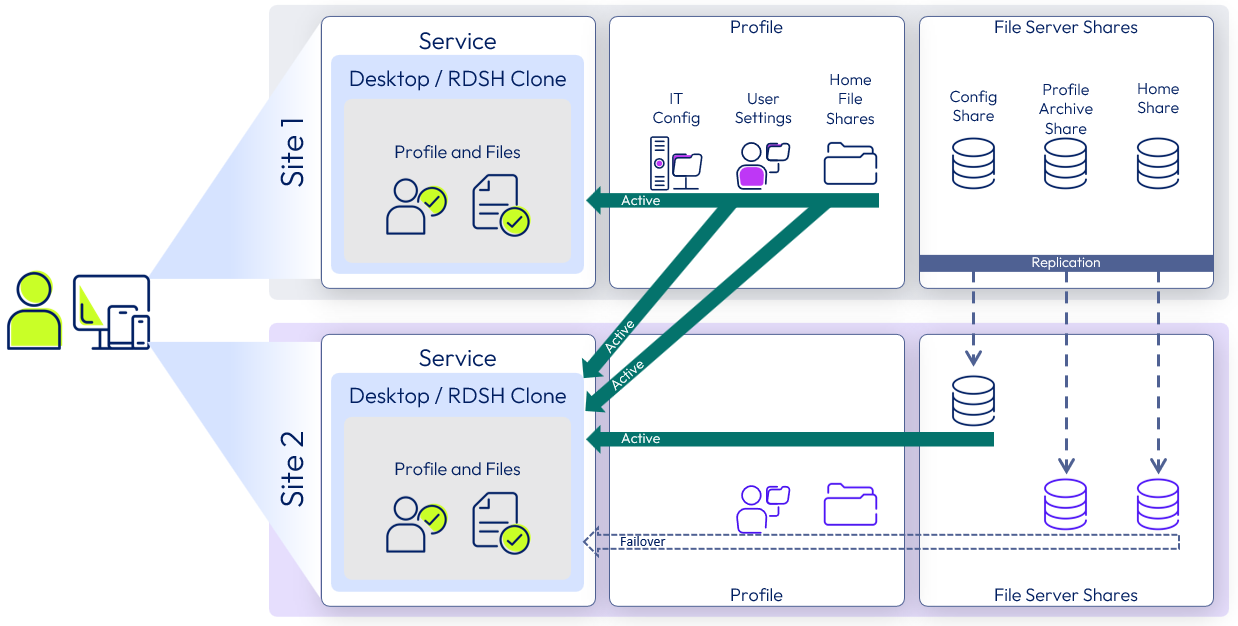
Figure 21: Dynamic Environment Manager profile recovery
Horizon Cloud Service active-passive recovery service
Requirement: The use case service is run from a specific Azure region. An equivalent service can be provided from a second Azure region.
Overview: The core Windows desktop or RDSH server is a clone of a golden image VM. Dynamic Environment Manager applies the profile, IT settings, user configuration, and folder redirection.
Table 10: Horizon Cloud Service Active/Passive Recovery Service Requirements
| Requirement | Comments |
| Windows desktop or RDSH server available in both sites | Horizon desktop pools or RDSH server farms are created in both data centers. |
| Native applications | Applications are installed natively in the base Windows OS. |
| IT settings | Dynamic Environment Manager IT configuration is replicated to ensure availability in the event that the primary Azure region becomes unavailable. |
| User data and configuration | Dynamic Environment Manager user data is replicated to ensure availability in the event that the primary Azure region becomes unavailable. |
At a high level, this service consists of a Windows environment delivered by either a desktop or an RDSH server, with equivalent resources created at both data centers. User profile and user data files are made available at both locations and are also recovered in the event of a site outage.
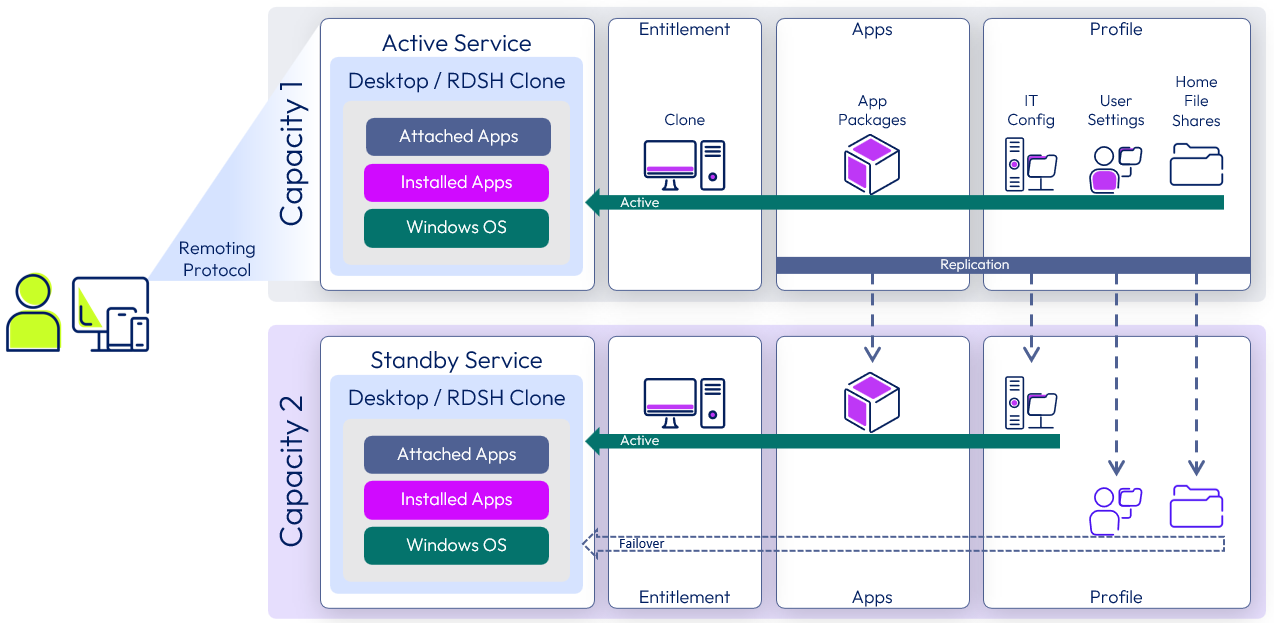
Figure 22: Horizon Cloud Service active/passive recovery service
Dynamic Environment Manager provides profile management by capturing user settings for the operating system, applications, and user personalization. The captured settings are stored on file shares that need to be replicated to ensure site redundancy.
Although profile data can be made available to both regions, there is a failover process in the event of the loss of the environment hosted in Capacity 1 that can impact the RTO and RPO.
Operational decisions can be made in these scenarios as to whether the service in hosted in Capacity 2 should be made available with reduced functionality (for example, available with the Windows base, the applications, and the IT configuration but without the user-specific settings).
Summary and additional resources
Now that you have come to the end of this chapter, you can return to the reference architecture landing page and use the tabs, search, or scroll to select further chapter in one of the following sections:
- Overview chapters provide understanding of business drivers, use cases, and service definitions.
- Architecture chapters give design guidance on the Omnissa products you are interested in including in your deployment, including Workspace ONE UEM, Access, Intelligence, Workspace ONE Assist, Horizon Cloud Service, Horizon 8, App Volumes, Dynamic Environment Manager, and Unified Access Gateway.
- Integration chapters cover the integration of products, components, and services you need to create the environment capable of delivering the services that you want to deliver to your users.
- Configuration chapters provide reference for specific tasks as you deploy your environment, such as installation, deployment, and configuration processes for Omnissa Workspace ONE, Horizon Cloud Service, Horizon 8, App Volumes, Dynamic Environment Management, and more.
Changelog
Date | Description of Changes |
|---|---|
| 2025-04-02 |
|
| 2024-10-07 |
|
| 2024-05-16 |
|
| 2024-02-29 |
|
| 2023-07-26 |
|
| 2023-02-24 |
|
Authors and contributors
- Graeme Gordon, Senior Staff Architect, Omnissa.
Feedback
Your feedback is valuable. To comment on this paper, either use the feedback button or contact us at tech_content_feedback@omnissa.com.

