Leveraging Dynamic Environment Manager to enhance security for Zero Trust
Overview
Omnissa Dynamic Environment Manager (DEM) helps with user profiles, dynamic & smart policies, settings, and more when users connect to Horizon Virtual Desktop Infrastructure (VDI) sessions. Policies dynamically adjust to changing circumstances, such as whether the user is accessing a session from an office or while traveling. All devices are supported, including cloud-hosted, virtual, and physical desktops. In this tutorial, we will address the following:
- How to provide dynamic security enforcement based on profile parameters set within DEM for a Horizon session leveraging ‘Smart Policies’.
- Leveraging DEM’s profile configuration management within Smart Polices to trigger enforcement.
- Providing security for allowed network access and functions within a Horizon session.
Purpose of This Tutorial
This tutorial takes you through the steps in procedures 1 and 2 below and will help guide you in the use of DEM’s Policy Configuration to enable dynamic security enforcement for Horizon Virtual Desktop Infrastructure (VDI) sessions. Before you implement your own Policy Configuration design, you must first set up a reference-architecture environment. For more information, see the Omnissa documentation page for DEM.
Furthermore, you’ll learn how to avoid creating complex log-on scripts and instead use pre-configured settings that dynamically apply end-user security policies for both personal and environmental settings, as well as network & application mapping for a seamless log-on. This means your end-users will have access from any type of device, from any secure approved location based on what the policy provides; by using DEM, you get to manage where users’ access originates based on a dynamic security profile and to what resources they’re allowed to access and enable fundamental aspects of Zero Trust Architecture (ZTA) pillars.
Audience
This tutorial is intended for IT administrators and product evaluators who are familiar with and have knowledge of the core technologies of Omnissa Horizon. Also, familiarity with networking and storage in a virtual environment, Active Directory, identity management, directory services, and is assumed and is also helpful.
This Operational Tutorial covers specific use cases for Zero Trust and Best Practices for Security to include:
- Public Sector, both FedGov & SLED agencies, and other regulated industries, such as Critical Infrastructure, Healthcare & Finance
- Best practices and guidance on deployment, as well as tips and tricks on this use case
- Links to relevant sections of the other DEM guides and Horizon Reference Architecture
Enhance Security with Dynamic Environment Manager
National Institute of Standards & Technology (NIST) and Cybersecurity Information Sharing Act (CISA) have both provided guidance and best practices regarding Cyber Security Framework (CSF), as well as Zero Trust Architecture and a Zero Trust Maturity Model (ZTMM). Both provide established requirements to enlist in an organization’s data assurance, including Identification, Protection, and Detection from the CSF and establishing protection specifically for the Data pillar and ‘Data Access’ from the ZTMM. We will focus on the pillars of the User, and Network but also what can help provide a foundation in support of others, such as ‘Automation and Visibility’.
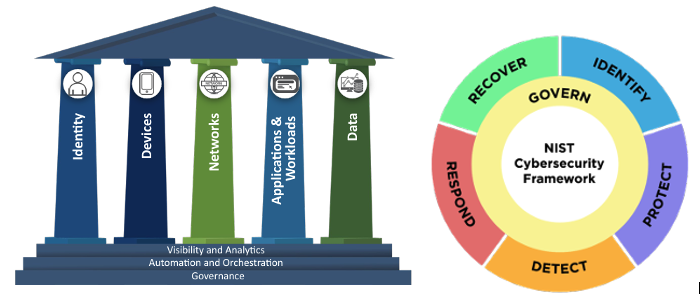
This exercise helps you to enable these controls that reside within the framework of both CSF and a ZTA. The steps are sequential and build upon one another, so make sure you complete each step before going on to the next.
Demo Video for Procedure’s 1 and 2 below:
Procedure 1 - Parent topic: Import ADMX templates containing the policies you want to configure. See Import ADMX Templates.
Procedure 1: Security Profile Configuration for Secure Network Domain
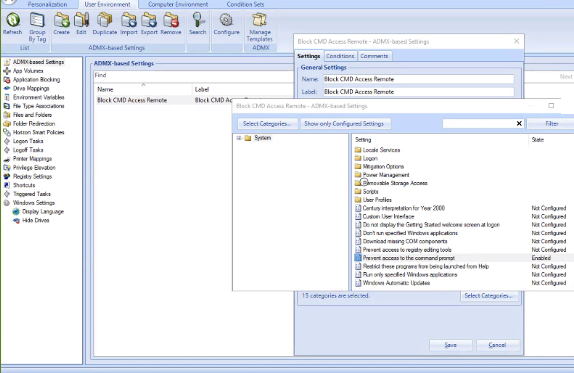
- Start the Dynamic Environment Manager Management Console.
- On the Computer Environment tab, select ADMX-based Settings.
- Click Create. This will give you access to choose the settings to apply. In this example, we are blocking the command (CMD) prompt to comply with best practice principles to limit unnecessary risks to system changes in the event of a compromise and provide an agency automation for application access decisions to adhere to least privilege principles.
- Enter a name, label, and a tag for the settings definition.
- Click Select Categories.
- Select the categories you want to manage with this definition and click OK.
Note: If you see any Orphaned nodes within the Category tree, ensure to import these missing templates. For more information, see Import ADMX Templates. - Click Edit Policies and configure the necessary policies.
- Click Conditions to add any variable check that you want to consider like Endpoint IP address ranges, AD groups, or users. In this case, we are setting the IP range for the internal network.
Note: This helps establish external access prevention policies against potential malicious access to the organization from outside the range defined.
- Click Save.
For more information, see Horizon Smart Policy Settings Admin Guide.
Procedure 2 - Parent topic: Configuring ADMX-Based Computer Settings
Procedure 2: Compromised Remote Session Pre-Mitigation & Detection
When a session from a user has a ‘low bandwidth’ quality, Horizon can detect it based on an algorithm of the client’s communication with the agent. This calculation can produce a measurable threshold whereby an administrator can use DEM to set a ‘Low-speed WAN’ connection trigger. With Smart Policies, you can use the Bandwidth profile policy setting to configure a profile for PCoIP or Blast sessions on remote desktops in order to enable a security compliance policy based on the following linked reference of bandwidth profiles. These can be configured by performing the following steps, in this order:
- Start the Dynamic Environment Manager Management Console.
- On the Computer Environment tab, select Horizon Smart Policies.
- Click Create. In this example, we are detecting a slow network connection and limiting access to things like USB, Drives, and Copy/Paste.
Note: Often when nefarious actors attempt to compromise a system, a leading Indicator of Compromise (IoC) can often be associated with ‘lower bandwidth session values’ that can indicate access from a foreign entry point and with this information, we can take steps to block or limit controls to the environment; thus, further assisting with deployment expansion of endpoint and application profile isolation mechanisms to more of agency network architecture with ingress/egress micro-perimeters and service-specific interconnections within the ZTMM.
- Enter a name, label, and a tag for the settings definition.
- Click Bandwidth Profile under Horizon Smart Policy Settings.
- Select Low-Speed WAN.
Note: In the following steps, we are going to show an example of configuration for Data Loss Prevention (DLP). Below we will first disallow a user’s ability to select a local drive. Next, we will allow a copy function into the agent, but <not> out of it the local machine. Next, we will disallow the user’s ability to add a USB-enabled device, such as a memory stick, further assisting agencies with automation of data inventory and tracking enterprise-wide, covering all applicable agency data, with DLP strategies based upon attributes and/or labels for compliance with ZTMM.
- Scroll down to the redirection section.
- Select Client drive and select Disabled.
- Select Clipboard and set to Allow copy from client to agent.
- Select USB and select Disabled.
- Click Save.
For more information, see Horizon Smart Policy Settings Admin Guide.
Summary and Additional Resources
Conclusion
This operational tutorial provided the steps to perform Security Profile Configuration for Secure Network Domain for session connectivity, as well as to secure against a potentially compromised remote session with pre-mitigation steps and for breach detection.
For more operational tutorials and other training, educational, or informational assets on Dynamic Environment Manager see Tech Zone, as well as the ‘Additional Resources’ below.
For versions of Dynamic Environment Manager, DEM is available in both Standard and Enterprise editions.
- DEM Enterprise Edition is the full-featured version that is included in Horizon 8, which provides a multi-cloud VDI (Virtual Desktop Infrastructure) app solution
- FedGov markets can run on-premises, in private data centers or a variety of private or public clouds — to provide sovereign cloud deployment models — and that can broker virtual and physical desktops with a best-in-class, NIAP and NSA CSfC Authorized end-user experience.
Additional Resources
For more information about Dynamic Environment Manager & Horizon VDI including Public Sector resources, you can explore the following resources:
- Tech Zone: DEM Architecture Guide
- Tech Zone: What is DEM?
- Tech Zone: Tech Intro & Features for DEM
- Tech Zone: DEM Configuration Guide
- Tech Zone: Managing Profiles & Policies for Windows with DEM
- Tech Zone: Public Sector Portal
- Docs: DEM Installation Guide
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2024/11/21 |
|
| 2024/03/22 |
|
About the Author and Contributors
- Andrew Osborn, Omnissa alumni.
- Joe Graziano, Sr. Solution Engineer, Omnissa.
Feedback
For questions or feedback, send to tech_content_feedback@omnissa.com.

