Horizon Cloud configuration
This chapter is one of a series that make up the Omnissa Workspace ONE and Horizon Reference Architecture, a framework that provides guidance on the architecture, design considerations, and deployment of Omnissa Workspace ONE and Omnissa Horizon solutions. This chapter provides information about common configuration and deployment tasks for Omnissa Horizon Cloud. It is not intended to replace the product documentation but to reference and supplement it with additional guidance. A companion chapter, Horizon Cloud architecture, provides information about architecture and design.
Identity and access management
You need to configure machine identity by defining the domain information to use for virtual machines. You also need to configure user identity by establishing a trust relationship with an Identity Provider (IdP) to provide user authentication services. You can optionally set up single sign-on to allow users to access virtual desktops and applications, without having to enter credentials a second time.
Configuring machine and user identity
As a part of the onboarding process, Horizon Cloud requires you to configure a trust with an Identity Provider (IdP) to provide authentication services for that customer tenant. You can choose to leverage Omnissa Access or Microsoft Entra ID (formerly Azure Active Directory) as your IdP. More IdP options may be available in future releases.
Note: Make sure to read and understand the design restrictions on Identity Providers as explained in the Horizon Cloud architecture chapter.

Figure 1: Identity management setup
To configure Identity management:
- Machine Identity - Define at least one active directory domain and specify the associated domain bind and join account information. See Setting up your Active Directory Domain.
- If you are planning on using True SSO for single-sign-on, also select the Use Enrollment Service Account option and configure a Primary Domain Enrollment Service account and an Auxiliary Domain Enrollment Service account.
- Single-Sign-on - Optionally add a single-sign-on configuration - See Configuring SSO or Configuring True SSO.
- User Identity - Connect to the chosen identity provider. See Connecting your Identity Provider.
Table 1: Identity management strategy
| Decision | Omnissa Access was used as the identity provider. |
| Justification | Omnissa Access was already in place, used for other Horizon deployments with Workspace ONE Access connectors already connecting to required Active Directory domains. |
Configuring SSO
To enable a single sign-on experience for your users, you can add an SSO configuration to be deployed on the Horizon Edge Gateway. This process sets up the required trust relationship to allow users to authenticate once in Horizon Cloud and then get automatically logged into their desktop or applications without having to enter their credentials a second time at the resource.
Notes:
- The SSO configuration described here, uses the built-in Omnissa Certificate Authority.
- As an alternative you can use True SSO, which uses a Microsoft Certificate Authority. For more information on these options, see Single-Sign-on.
To set up SSO using the Omnissa Certificate Authority, the following steps must be completed.
- Ensure that the active directory domains, that you intend to use for desktops, are defined in the Universal Console.
- Define the SSO Configuration. See Add an SSO Configuration for an Omnissa CA for more information.
- Install and configure the Certificate Authority (CA) role on a Domain Controller. See Install the Certification Authority for more information.
- Download the CA bundle for the SSO Configuration and install it on the domain controller by running the included PowerShell script. For more information, see Publish the Omnissa SSO CA Bundle to the Active Directory Forest.
- Add an internal DNS record for the management interface of the Horizon Edge Gateway service and ensure that desktops can resolve this FQDN to the correct IP address. See DNS for more information.
- Select to use SSO on the Edge Gateways and pool groups. See Enable the SSO Configuration.
Define the SSO Configuration
Define the SSO Configuration in the Horizon Universal Console.
Note: An active directory domain cannot have both a SSO and a True SSO configuration defined on it.
- In the Horizon Universal Console, navigate to Integrations > Identity & Access and click Manage.
- Select the SSO Configurations tab, click the Add button and select Omnissa CA from the drop-down menu.
- Define a Name for this SSO Configuration.
- Select the Certificate authority mode to use.
- Specify the Configuration domain name to determine the configuration naming context of the AD forest for your SSO configuration.
- Select the active directory Domains.
- Click Add.
For more information, see Add an SSO Configuration for an Omnissa CA.
Enable the SSO Configuration
Finally, ensure that SSO is enabled in both the Horizon Edge Gateway and the pool group.
- Make sure that any Horizon Edge Gateway that you want to use SSO, has the Use SSO option enabled and the SSO Configuration you just defined selected.
- When defining a pool group, select the policy set to Use SSO.
Configuring True SSO
Omnissa True SSO provides users with SSO to Horizon desktops and applications regardless of the authentication mechanism used. See the True SSO section in Horizon Cloud architecture for more details.
Notes:
- The True SSO configuration described here, uses a Microsoft Certificate Authority. As an alternative you can use SSO which uses the built-in Omnissa Certificate Authority. For more information on these options, see Single-Sign-on.
- The True SSO configuration covered here is different from the True SSO configuration for Horizon 8 pods. For details on Horizon 8 configuration, see Setting Up True SSO in the Horizon Configuration chapter.
The high-level steps that need to be completed to deploy True SSO, for a Horizon Edge Deployment, are:
- Deploy at least one Horizon Edge. This is required to perform the discovery of the Microsoft Certificate Authority environment. See Deploying a Horizon Edge for instruction.
- Ensure that the active directory domains, that you intend to use for desktops, are defined in the Universal Console and have the Use Enrollment Service Account option configured.
- Install and configure the Microsoft Certificate Authority service on one or more suitable domain member servers.
- Setup an active directory security group.
- Create and issue a True SSO certificate template.
- Create and issue an Enrollment Agent certificate template.
- Select to use SSO on the Horizon Edge Gateways and the pool groups.
For more information on how to install and configure True SSO, see the following documentation pages:
- Horizon Cloud True SSO Requirements for Microsoft Enterprise Certificate Authority and Required Certificate Templates
- Add an SSO Configuration to Use True SSO with Horizon Edges.
Set Up a Microsoft Certificate Authority
- Prepare a Windows Server for each Certificate Authority instance and join it to the active directory domain that the desktops will be joined to.
- Add the Active Directory Certificate Services Server role using the Add Roles and Features Wizard. The only role service required is Certification Authority.
- Once installed, configure Active Directory Certificate Services using the following values.
Table 4: Settings for Active Directory Certificate Services
| Configuration Item | Setting |
| Role Services | Certification Authority |
| Setup Type | Enterprise CA |
| CA Type | Root CA or Subordinate CA, depending on your preference for PKI deployments. Choose Root CA if you are not integrating into an existing PKI. |
| Private Key | Create a new private key |
| Cryptology | Key length: 2048 (recommended) Hash algorithm: SHA384 (recommended) |
| CA Name | Change if desired. |
| Validity Period | Leave as default of 5 years. |
- The final configuration is done by opening a command prompt, as an Administrator, and running the following commands:
- Enable non-persistent certificate processing and help reduce the CA database growth rate:
certutil -setreg DBFlags +DBFLAGS_ENABLEVOLATILEREQUESTS
- Ignore offline CRL (certificate revocation list) errors on the CA:
certutil -setreg ca\CRLFlags +CRLF_REVCHECK_IGNORE_OFFLINE
- Restart the Certificate Authority Service so that these changes can take effect.
sc stop certsvc
sc start certsvc
Repeat these steps on each Certificate Authority server.
Create an Active Directory group
Create an active directory security group. This will be used to assigned permissions to issue certificates on behalf of users from the Microsoft Certificate Authority.
- Create an Active Directory universal security group.
- Add the user accounts that you defined as the Primary Domain Enrollment Service account and the Auxiliary Domain Enrollment Service account when you added the active directory domain for machine identity.
Create and issue a True SSO certificate template
The Microsoft Certificate Authority Server issues a smartcard certificate that is used to log the user onto the virtual machine. Follow the instructions below to define a suitable certificate template that will be used generate the certificates.
- Create a new True SSO certificate template by first opening the Certification Authority administrative tool.
- Expand the tree in the left pane, right-click Certificate Templates and select Manage.
- Right-click the Smartcard Logon template and select Duplicate Template.
- Do not click OK until you have completed all the configurations listed in the following table.
Table 5: Configuration settings for the True SSO certificate template
| Configuration Item | Setting |
| Compatibility | Certification Authority: Windows Server 2008 R2 Certificate recipient: Windows 7 / Server 2008 R2 |
| General | Template display name: Edge True SSO Template name: EdgeTrueSSO Validity period: 1 hour Renewal period: 0 hours |
| Request Handling | Purpose: Signature and smartcard logon Select For automatic renewal of smart card certificates. Select Prompt the user during enrollment. |
| Cryptography | Provider category: Key Storage Provider Algorithm name: RSA Minimum key size: 2048 Select the Requests can use any provider available on the subject's computer radio button. Request hash: SHA384 Can be different depending on the security standards. |
| Subject Name | The defaults should have the following selected. The Build from this Active Directory information radio button is selected. The Subject name format: Fully distinguished name The User principal name (UPN) check box is selected. |
| Server | Select Do not store certificates and requests in the CA database. De-select Do not include revocation information in issued certificates. |
| Issuance Requirements | Select This number of authorized signatures with a value of 1 Policy type required in signature: Application policy Application Policy: Certificate Request Agent Require the following for reenrollment: Valid existing certificate |
| Security | Add the group you created for the domain enrollment accounts and give this read and enroll permissions. |
- Switch back to the Certificate Authority console and issue the True SSO certificate.
- Right-click Certificate Templates and select New > Certificate Template to Issue.
- Select the new True SSO template you just created. (Note that you might need to wait for replication to complete before the new template appears in the list).
- This step is required for all certificate authorities that issue certificates based on this template. Repeat the issuance on all certificate authority servers that you intend using with True SSO.
Create and issue an enrollment agent template
- Create a new Enrollment Agent certificate template by first opening the Certification Authority administrative tool.
- Expand the tree in the left pane, right-click Certificate Templates and select Manage.
- Right-click the Enrollment Agent template and select Duplicate Template.
- Do not click OK until you have completed all the configurations listed in the following table.
Table 5: Configuration Settings for the Certificate Template
| Configuration Item | Setting |
| General | Template display name: True SSO Enrollment Agent Template name: TrueSSOEnrollmentAgent |
| Security | Add the group you created for the domain enrollment accounts and give this read and enroll permissions. |
- Switch back to the Certificate Authority console and issue the Enrollment Agent certificate template.
- Right-click Certificate Templates and select New > Certificate Template to Issue.
- Select the new Enrollment Agent template you just created.
- This step is required for all certificate authorities that issue certificates based on this template. Repeat the issuance on all certificate authority servers.
Define the True SSO configuration
Once the Microsoft Certificate Authority servers are setup, and the True SSO and Enrollment Agent templates are configured and issued, you can define the SSO Configuration in the Horizon Universal Console.
Note: An active directory domain cannot have both a SSO and a True SSO configuration defined on it.
- In the Horizon Universal Console, navigate to Integrations > Identity & Access and click Manage.
- Select the SSO Configurations tab, click the Add button and select Microsoft CA from the drop-down menu.
- Define a Name for this SSO Configuration.
- Select at least one Horizon Edge Gateway to use for discovery of the Microsoft Certificate Authority environment.
- Select the active directory Domains and click Discover.
- Choose the TrueSSO template that you created and issued.
- Choose the Enrollment agent template that you created for use with True SSO.
- Make sure that the correct Certificate authorities you want to be used are listed.
- Click Add.
Enable the True SSO configuration
Finally, ensure that SSO is enabled in both the Horizon Edge Gateway and the pool group.
- Make sure that any Horizon Edge Gateway that you want to use True SSO, has the Use SSO option enabled and the True SSO Configuration you just defined selected.
- When defining a pool group, select the policy set to Use SSO.
Deploying a Horizon Edge
The Universal Console in the Horizon Control Plane can be used to define, deploy, and manage Horizon Edges to supported cloud-native provider capacity. Before deploying your first Horizon Edge, complete the onboarding tasks to assign roles, launch Horizon Cloud for the first time, and select a region for Horizon Cloud services metadata. See Onboarding to Horizon Cloud for more information.
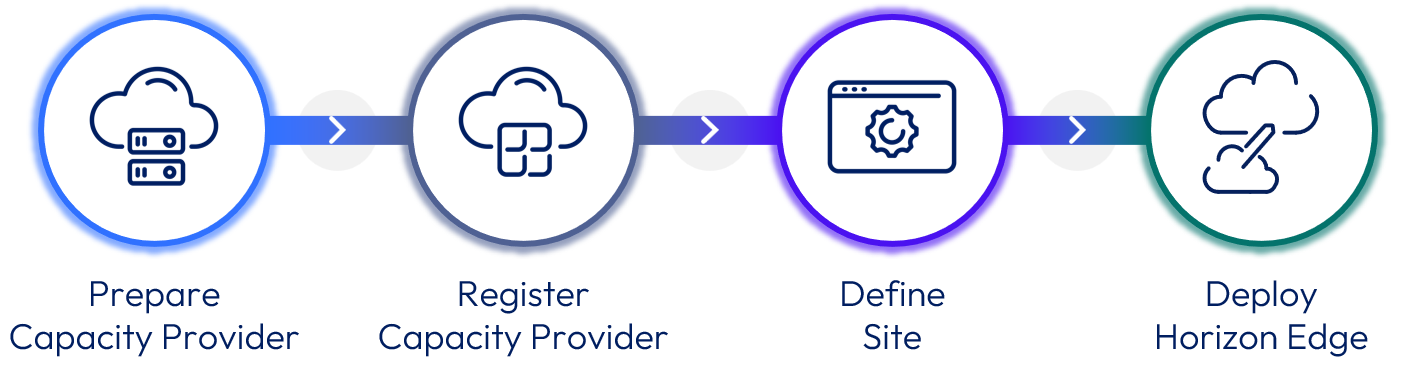
Figure 2: Deploying a Horizon Edge
To deploy a new Horizon Edge:
- Prepare the capacity provider.
- For Azure - See Preparing Microsoft Azure.
- Register a new capacity provider to use.
- Define a site (if not using an existing site).
- Deploy the Horizon Edge.
Steps 2 and 3 can also be done as part of the Horizon Edge deployment wizard.
Note: Before deploying a Horizon Edge, you should configure identity management, including domain information, and single-sign-on configuration (if being used). See Configuring Machine and User Identity for an overview of the process.
Certificates
When deploying a Horizon Edge, you need to supply a TLS/SSL certificate. The certificate is applied to the Unified Access Gateways when the Horizon Edge deploys them.
The certificate can be in either PEM or PFX format. The certificate should match the FQDN of the Unified Access Gateway as defined when deploying the Horizon Edge.
DNS
Two DNS records are required as part of the Horizon Edge deployment. One facilitates user connections and a second is used as part of the single sign-on configuration.
Load balancer for Unified Access Gateways
To allow user connections to resources, you need to create a DNS record to the load balanced FQDN of the Unified Access Gateways.
Create a DNS record for the load balanced address of the Unified Access Gateways.
- The name should match Unified Access Gateway FQDN.
- The IP address is the load balancer IP in the Unified Access Gateway section.
- You should create a DNS record in your external DNS. If you use split DNS (where the internal domain name matches the internal domain name, also create a record in your internal DNS system).
The Unified Access Gateway FQDN and load balancer IP address are listed in the Horizon Edge detail which can be found by navigating to Resources > Capacity, clicking the name of the Horizon Edge, and then locating within the Unified Access Gateway section.
Horizon Edge Gateway
As part of the single sign-on (SSO) configuration, you must set up a DNS record for the Horizon Edge gateway service. Desktops should be able to resolve the FQDN of the Horizon Edge Gateway to the IP address allocated to it in the Management subnet used for deployment.
Create a DNS record for the Horizon Edge Gateway service.
- The name should match the Horizon Edge Services FQDN.
- The IP address is the load balancer IP in the Horizon Edge Gateway section.
- Create this DNS record in your internal DNS or the DNS system the desktops use for their DNS lookups.
The Horizon Edge Services FQDN and Load Balancer IP address are listed in the Horizon Edge detail which can be found by navigating to Resources > Capacity, clicking the name of the Horizon Edge, and then locating within the Horizon Edge Gateway section.
Preparing Microsoft Azure
To deploy a Horizon Edge to a Microsoft Azure IaaS provider, the Azure subscription must first be prepared.
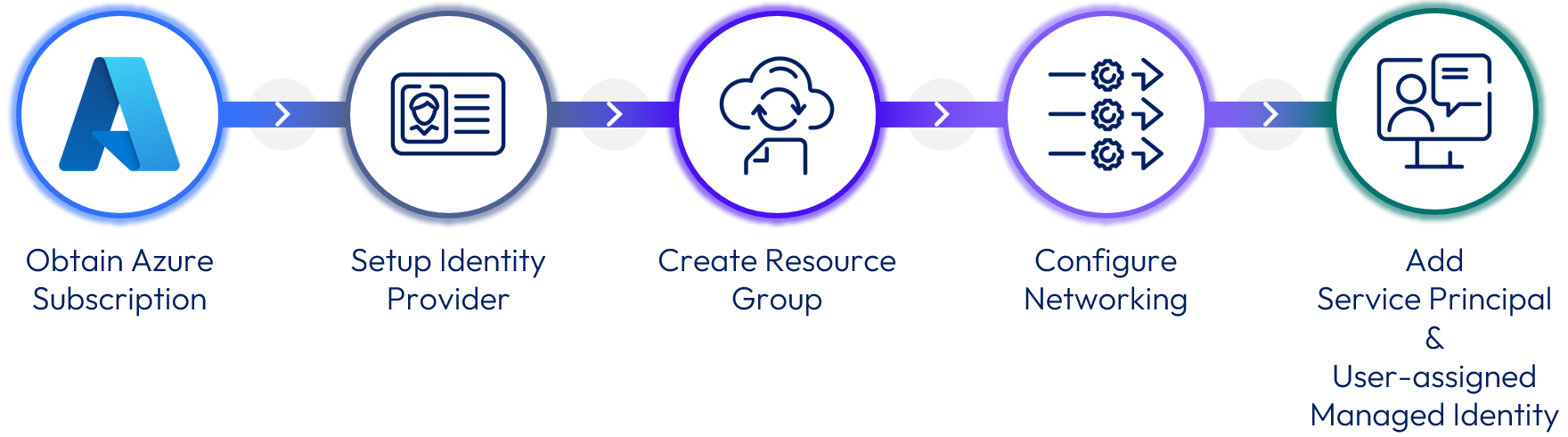
Figure 3: Preparing Azure for a Horizon Edge deployment
To prepare an Azure subscription for a new Horizon Edge deployment:
- Obtain an Azure subscription with suitable capacity.
- Set up an identity provider - See Setting Up Your Identity Provider.
- Either Microsoft Entra ID or Omnissa Access
- Microsoft Entra ID (Azure Active Directory or Azure AD)
- Install Microsoft Entra Connect on an on-premises active directory server to link Microsoft Entra. See Integrate on-premises Active Directory domains with Microsoft Entra ID for more information.
- Omnissa Access
- Configure user attributes.
- Enable the people search feature in Omnissa Access.
- Create Active Directory domain bind and domain join accounts. A main account and an auxiliary are required for each of these.
- Create a Resource Group in the target Azure region – See Manage Azure resource groups by using the Azure portal for more information.
- Configure Networking – See the Networking Requirements section of Requirements Checklist for Deploying a Microsoft Azure Edge and Configure Network Settings for Microsoft Azure Regions for more information.
- Setup a new VNet or configure an existing VNet to be used for the Horizon Edge deployment.
- Define subnets for DMZ, management, and desktop VMs.
- Add NAT Gateway to the management subnet. The Horizon Edge Gateway needs a NAT Gateway for outbound connectivity. For guidance on creating an Azure NAT Gateway, see Quickstart: Create a NAT gateway using the Azure portal.
- Configure any required virtual network peering between VNets. For example, between the target VNet and other VNets that contain supporting infrastructure such as Active Directory domain controllers, or DNS servers.
- Create Service Principal and User-assigned Managed Identity
- Add a Service Principal for the Azure subscription – Service Principals can be defined using the Azure Portal in Azure Active Directory > App registrations. See Azure Service Principals and Create a Service Principal for the Microsoft Azure Subscription for more information and the process.
- Add a User-assigned Managed Identity to the Azure subscription. See Azure Managed Identities and Manage user-assigned managed identities for more information and the process.
For more details on preparing Azure infrastructure for a Horizon Edge deployment, please review the Evaluation Guide for Horizon Cloud, which includes videos that help walk you through a basic configuration of the platform.
Creating desktops and apps on cloud-native deployments
After a Horizon Edge has been deployed to a cloud-native provider, such as Microsoft Azure, you can import images, use them to create pools, pool groups, and entitle users to desktops and applications.
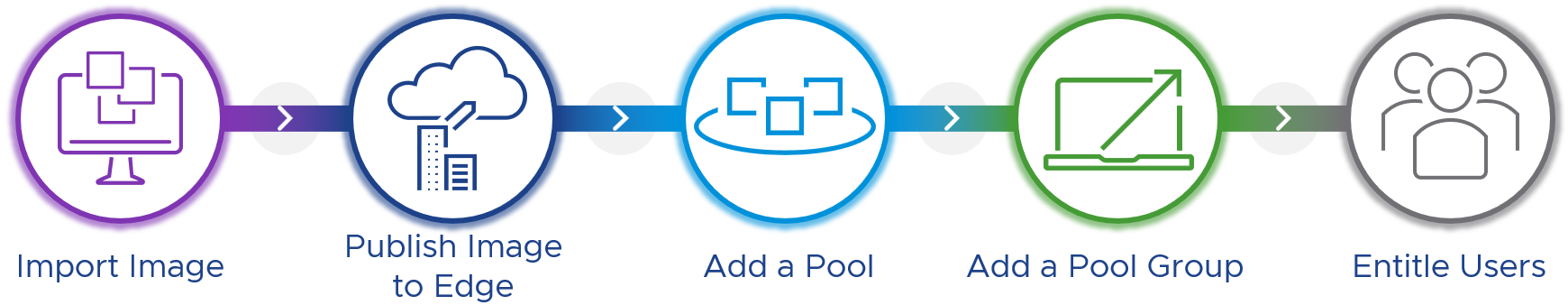
Figure 4: Import images, add pools, add pool groups, and entitle users
The process involves the following steps:
- Import a virtual machine (VM) image. This image becomes a golden virtual machine image that is used to create individual VM clones.
- Publish the image to the Horizon Edges that you want to use it on.
- Create a pool to use the published image.
- Create a pool group to apply policy to the consumption of one or more pools.
- Entitle users to allow access to the resources.
Golden image
With Horizon Edge deployments on a cloud-native provider, such as Microsoft Azure, you can import, customize, and prepare a suitable golden image. You can then publish the image to the Horizon Edges where this is to be used. See Image Management Service for more information.
Pool
A pool uses a published image to create a collection of virtual machines within the selected Azure provider.
Table 2: Cloud-native deployment pool settings
| Component | Settings |
| Destination | Site – Select the site which you want this pool to be associated with. Horizon Edge – Select the Horizon Edge. This list will be populated with the Horizon Edges associated with the chosen site. Provider – Select the provider to use. |
| Image | Azure VM Generation type – V1 or V2 Image – Select an image that has previously been published to the Horizon Edge being used. The capabilities of the image must match the type of pool being created (for example, single-session or multi-session). Marker – Select which marker on the image to use. Version – Select the desired version of the published image to use. Windows license – Confirm that you have eligible Windows licensing. |
| VM Details | Model – Choose the VM model to use. Disk type - Select a supported disk type from the available options. Disk type options are based on the VM model selected, and the Microsoft Azure subscription and region. Disk size – Size of disk in GB Encrypt disks – Choose whether hard disks should be encrypted or not. |
| Domain | Domain - Select the active directory domain to use. Computer OU – Define the Active directory organization unit (OU) where the computer objects should be created. This is the distinguished name of the target OU. |
| Provisioning | Provision VMs on-demand or all at once – Choose whether the total number of VMs defined should be created when the wizard completes, or on-demand, as they are needed by users. Minimum provisioned VMs - The minimum number of spare VMs. Must be less than or equal to maximum VMs to avoid frequent capacity updates. Only applicable if provisioning VMs on demand. Maximum provisioned VMs - The maximum number of spare VMs. Must be greater than or equal to minimum VMs to avoid frequent capacity updates. Only applicable if provisioning VMs on demand. Total VMs - The maximum number of VMs that can be provisioned. Sessions per VM – For multi-session pools, set the total number of sessions to allow per virtual machine. |
| Properties | VM name prefix – Define a prefix for the VMs and the computer objects that will be created. Desktop admin username - Create a username for the local admin account to access the image's operating system, and to use during the image conversion process. Desktop admin password – Define the password to set for the desktop admin account. Outbound proxy – Choose whether to route outbound requests to the Internet through a proxy server. If selected define the proxy host, port, and any IP addresses that should bypass the proxy. |
| Networks | Select which VNets and subnets to create this pool in. Note that after the pool is saved, the networks cannot be edited or changed. |
| Dynamic Environment Manager | When defining a pool, you can optionally select a Dynamic Environment Manager configuration that you have previously defined. See Dynamic Environment Manager. |
For more information, see Create a Pool.
Pool group
A pool group collects together one or more pools. The pools consumed by a pool group can be from any Azure provider.
A Pool Group allows:
- A common set of policies to be applied to the pools that define how users will consume the resources of the pools.
- Users to be entitled to resources in the pool group and therefore consume resources from the pools that are members of that pool group.
The policies that you define on a pool group include the following.
Table 17: Pool group policies
| Component | Policies |
| Client | Default protocol – Select the default protocol for end-user sessions. Currently, only Blast Extreme is supported. You can also select whether to Allow users to select protocol. Allow users to select protocol Preferred client type – Select whether to launch assignments in Horizon Client or a browser. |
| Brokering | Scope – Select whether to search for available desktops on any site or only within the end-user's site. Site connection affinity – Select the default site that end users will connect to. Options are Nearest Site or Home Site. Home site restriction – Restrict users to accessing the assignment only through the assignment home site override, or through the user's home site if an override is not designated. If not selected, the nearest site will be used. Only selectable when site connection affinity is set to Home Site. |
| SSO (Single sign-on) | Use SSO – Defines whether to use SSO for the pool. To enable SSO for the pool, SSO must be enabled on the Horizon Edge Gateway and SSO configuration set up as detailed in Single Sign-On. |
| Power Management | Minimum VMs - The minimum percentage of VMs to keep powered on relative to the total VMs in a pool at any point in time. Power management mode – Select the threshold of virtual machine utilization for this assignment at which a new virtual machine is spun up and drained respectively. Choose from Optimized for performance, Balanced, or Optimized for cost. This setting is only available for a multi-session pool.
Power off protect time - Enter the number of minutes (from 1 to 60) a VM is protected from powering off after powering on due to a headroom error. The default is 30. Power management schedule – Optionally, set up a schedule for power management. |
For more information, see Create a Single-Session Pool Group and Create a Multi-Session Pool Group.
Dynamic Environment Manager
Dynamic Environment Manager offers personalization and dynamic policy configuration for end-user desktops and applications. For Azure-based Horizon Edge deployments:
- Install and configure Dynamic Environment Manager to a file share – See the deployment guidance in the Dynamic Environment Manager Product Page on TechZone.
- Add a Dynamic Environment Manager Configuration – See Configuring Dynamic Environment Manager for more information.
- Select the Dynamic Environment Manager Configuration when defining the Pool – See Create a Pool for more information.
For more guidance on architecting Dynamic Environment Manager, see Dynamic Environment Manager Architecture. For guidance on configuring Dynamic Environment Manager, see Dynamic Environment Manager Configuration.
Summary and additional resources
Now that you have come to the end of this integration chapter on Omnissa Horizon Cloud, you can return to the reference architecture landing page and use the tabs, search, or scroll to select further chapter in one of the following sections:
- Overview chapters provide understanding of business drivers, use cases, and service definitions.
- Architecture chapters give design guidance on the Omnissa products you are interested in including in your deployment, including Workspace ONE UEM, Access, Intelligence, Workspace ONE Assist, Horizon Cloud, Horizon 8, App Volumes, Dynamic Environment Manager, and Unified Access Gateway.
- Integration chapters cover the integration of products, components, and services you need to create the environment capable of delivering the services that you want to deliver to your users.
- Configuration chapters provide reference for specific tasks as you deploy your environment, such as installation, deployment, and configuration processes for Omnissa Workspace ONE, Horizon Cloud, Horizon 8, App Volumes, Dynamic Environment Management, and more.
Additional resources
For more information about Horizon Cloud, you can explore the following resources:
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2025-12-17 |
|
| 2024-10-16 |
|
| 2024-05-30 |
|
| 2023-11-21 |
|
| 2023-10-05 |
|
| 2023-07-24 |
|
| 2023-06-27 |
|
Author and contributors
This chapter was written by:
- Graeme Gordon, Senior Staff Architect, Omnissa
- Rick Terlep, Staff Technical Marketing Architect, Omnissa.
Feedback
Your feedback is valuable. To comment on this paper, either use the feedback button or contact us at tech_content_feedback@omnissa.com.

