Device Posture in Entra ID using Intelligence and Graph API
Zero Trust for MS Office 365 Overview
The concept of Zero Trust assumes that any connection to sensitive data is untrusted even coming from a corporate device and requires further checks during authentication and access. The concept specifies 5 pillars that need to be addressed when implementing Zero Trust.
There are different possibilities to achieve Zero Trust and secure access to sensitive data in productivity suites like Office 365, which are discussed in a 3-part tutorial series.
This tutorial is an extension to that series. Parts 1, 2, and 3 walked you through the setup of Authentication, ZTNA-based, and Graph API-based compliance integrations with Office 365.
This extension is closely related to the Graph API integration of part 3 and addresses use cases that can be solved with Workspace ONE Intelligence such as compliance for Hybrid Entra ID joined and Workplace joined Windows devices.
The following topics will be covered:
- Overview of components required for Zero Trust leveraging the Intelligence Custom Connectors together with Microsoft’s Graph API.
- Setting up sensors, Entra ID enterprise app, and Freestyle automation to enable Windows device compliance.
Audience
This tutorial is intended for IT professionals and Omnissa Workspace ONE administrators of existing production environments. Familiarity with Active Directory, identity management, and directory services is assumed. Knowledge of other technologies, such as Entra ID, is also helpful.
If you are new to Workspace ONE, review the Evaluation Guide: Managing Apps and Devices with Workspace ONE Cloud which has step-by-step exercises implementing features like mobile single sign-on (SSO) in UEM and Workspace ONE Access.
Zero Trust through Graph API Integration - Architecture
This guide builds on the previously released Compliance Integration with MS Office 365 using Graph API guide leveraging the product features Partner Compliance and Windows MDM Entra ID integration.
Although Workspace ONE does not support non-OOBE Hybrid AD joined or registered Windows clients natively, you can leverage Workspace ONE Intelligence, sensors, and custom connectors to transmit the compliance state to Entra ID and leverage it in Entra ID Conditional Access as with the other API-based methods.
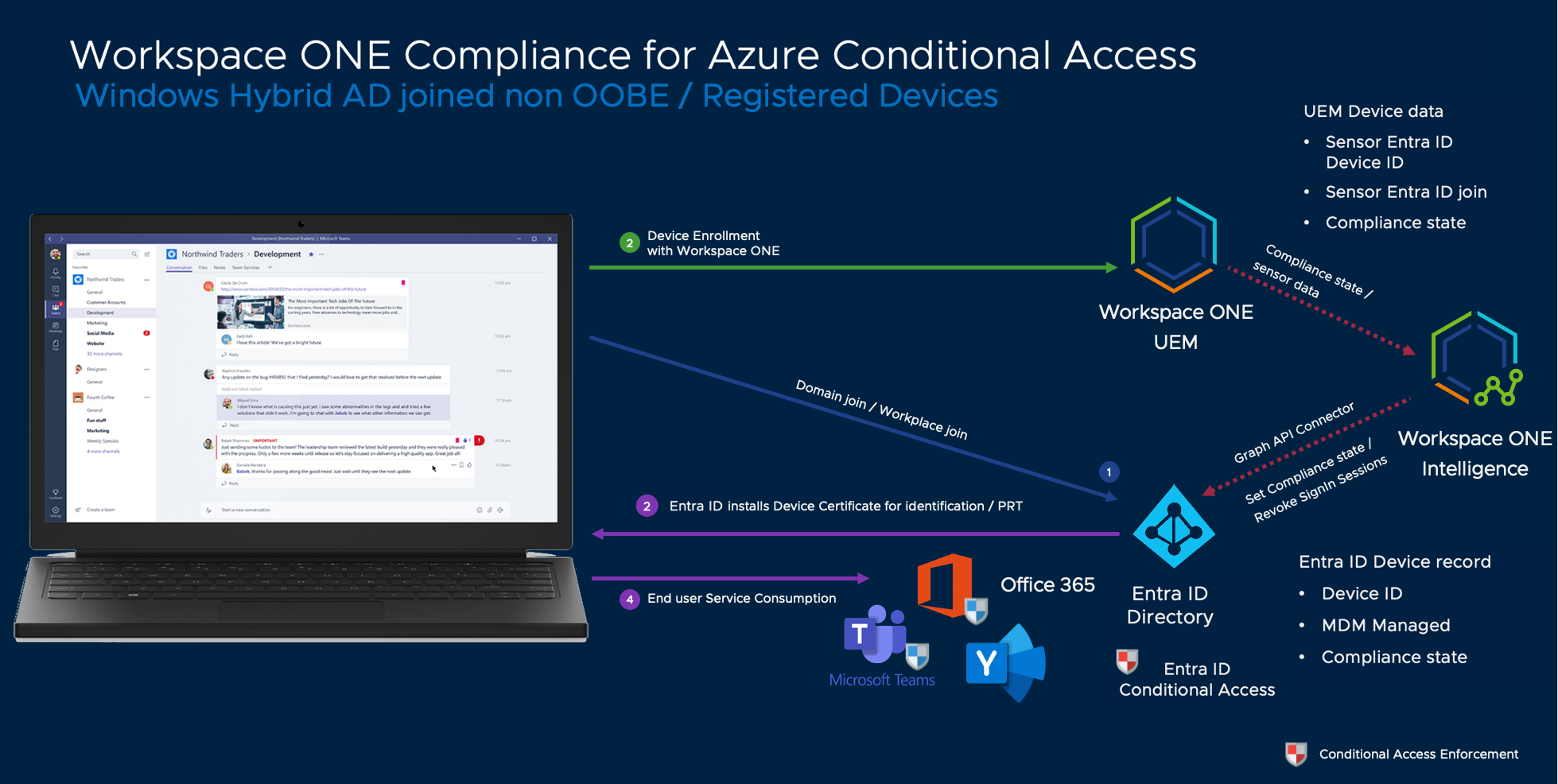
Figure 1: Compliance using Intelligence and Graph API-based integration for Windows 10/11
For a demo of the steps discussed in this tutorial, watch the Device Posture in Entra ID using Omnissa Intelligence video.
Setting Up Workspace ONE for Windows Device Compliance
In this section, we walk through the setup of sensors, Entra ID enterprise app, and Freestyle automation to enable Windows device compliance.
Requirements for Workspace ONE UEM and Graph API
Before you can proceed, you must have the following components installed and configured:
- An existing Workspace ONE environment
- Access to Entra ID Conditional Access Policies
- Rights to add an Entra ID enterprise app and set the required permissions
- Entra ID Premium P1 license
To communicate the device state to Entra ID, we need to know the device identifier used by Entra ID for the device record and save it with our device. We also want to gather how that device is associated with Entra ID; for example, if it is Entra ID joined, Hybrid AD joined, or just registered. The following GitHub repository has all the required sensor definitions for you.
Figure 2: Sensor definitions on Github
For a general overview of sensors, check out Windows Sensor documentation in Omnissa Docs.
Set Up Sensors
Copy the script definition from GitHub and UEM under Resources > Sensors and add the sensors for Windows as a PowerShell script.
For Hybrid joined, you must add sensors to retrieve the variable for domain joined, Entra ID joined, and the Entra ID device ID. For registered or workplace joined devices you must add the sensor definition for workplacejoined status and the workplacejoined device ID which is different from the Entra ID device ID that we can use with Hybrid or Entra ID joined devices.
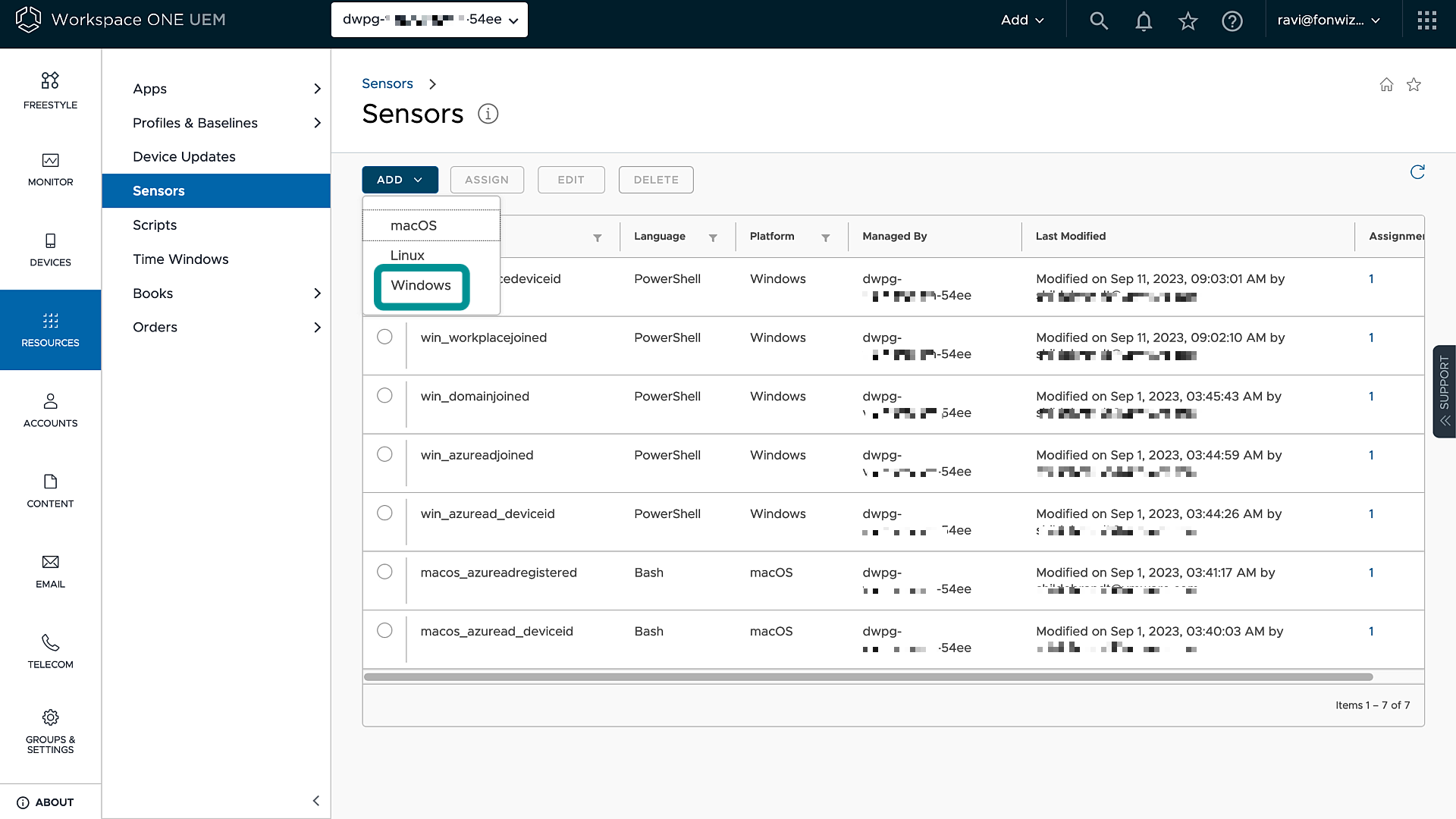
Figure 3: Sensor section in Workspace ONE UEM
Use Automatic Architecture recognition and either System or Current User context. Current User context is only required for Workplace joined devices.
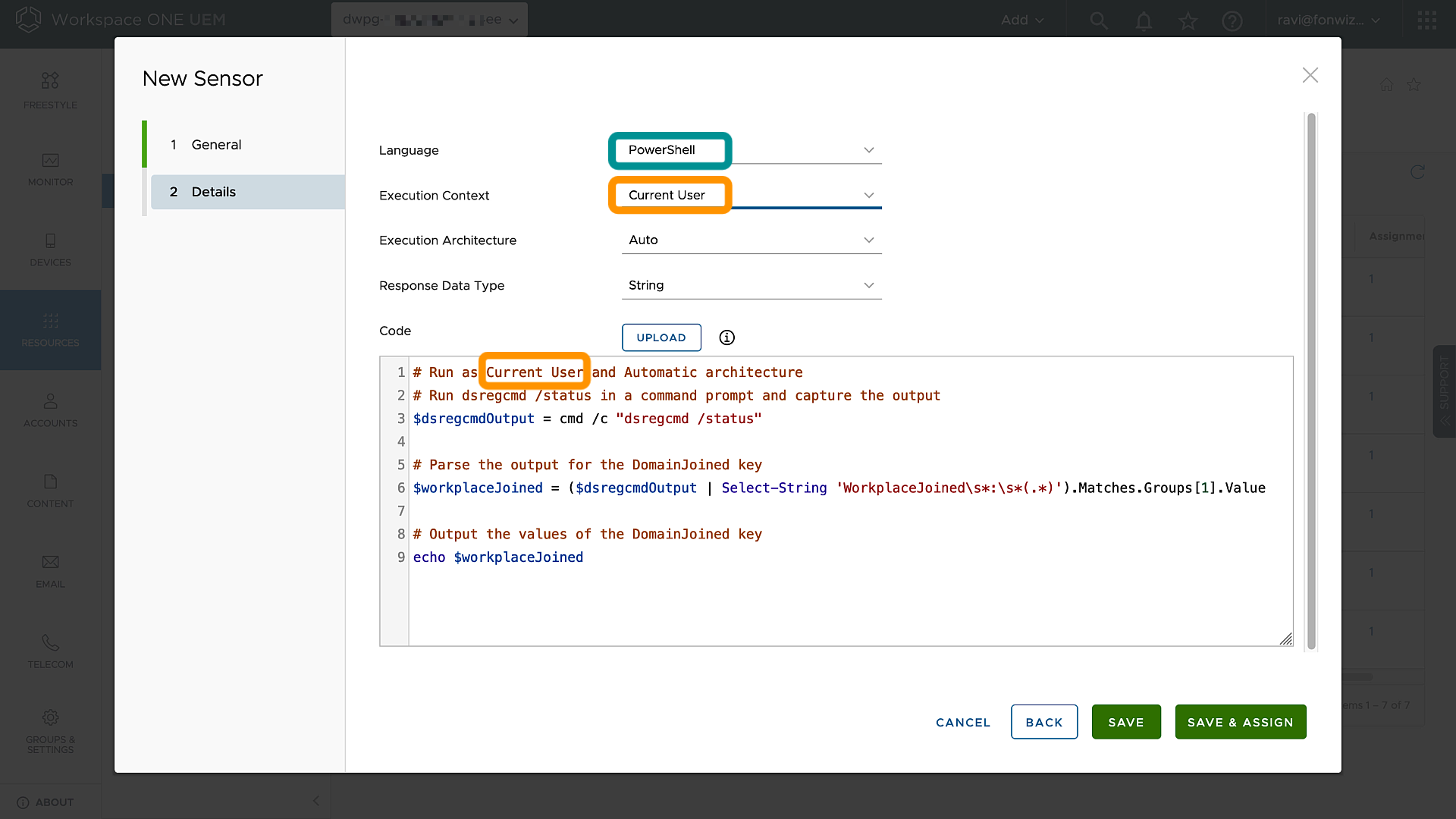
Figure 4: Sensor details
Then assign the sensor to the smart group for the devices you want to target and choose the right deployment type such as Schedule for system context and Event for user context type sensors.
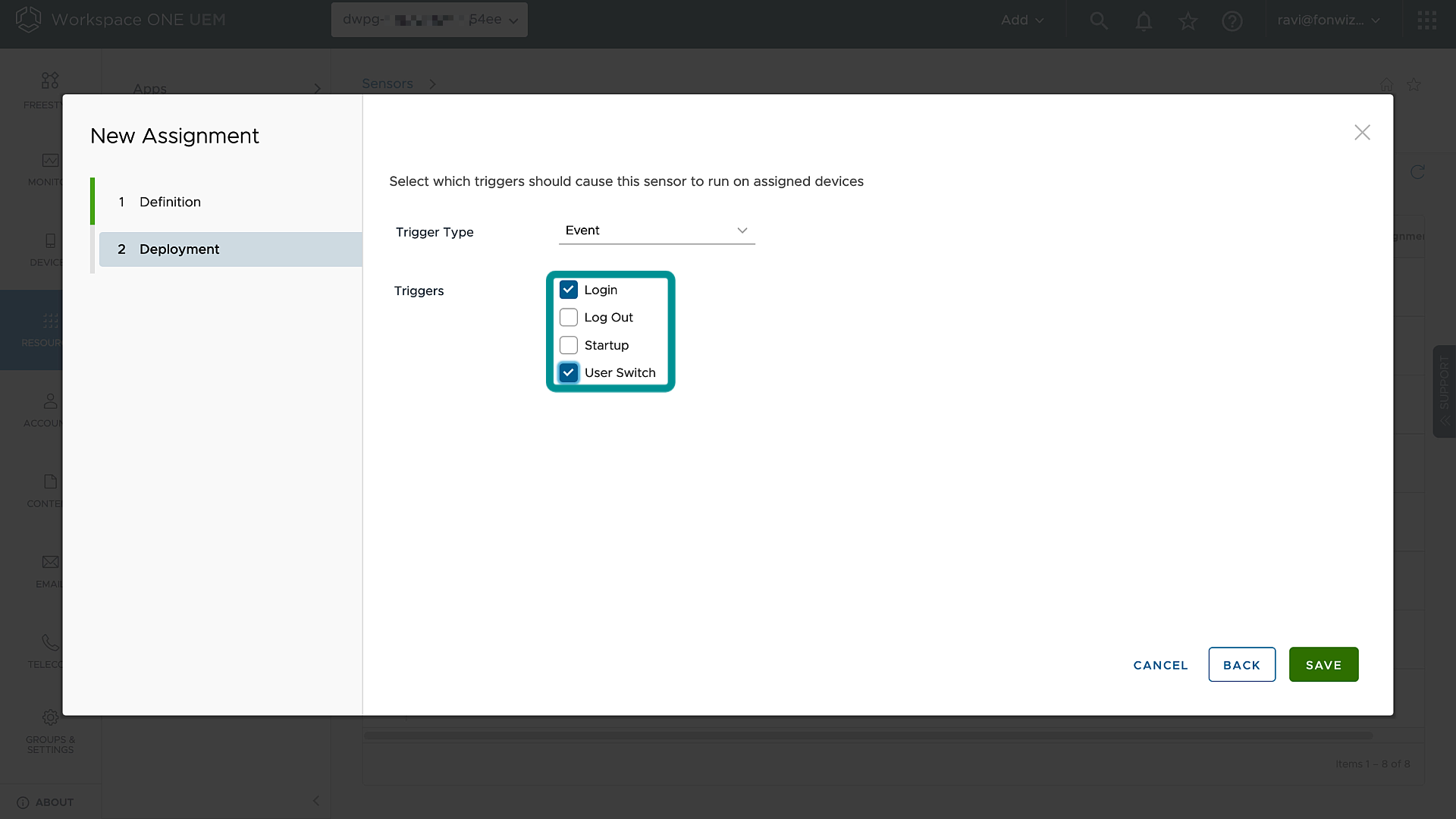
Figure 5: Sensor assignment deployment settings
After adding all the sensors that you want to use, wait for the devices to retrieve the definitions and report back the sensor data. You can see the sensor data in the device details for Workspace ONE UEM cloud environments or you might need to check Intelligence for on-premises UEM environments.
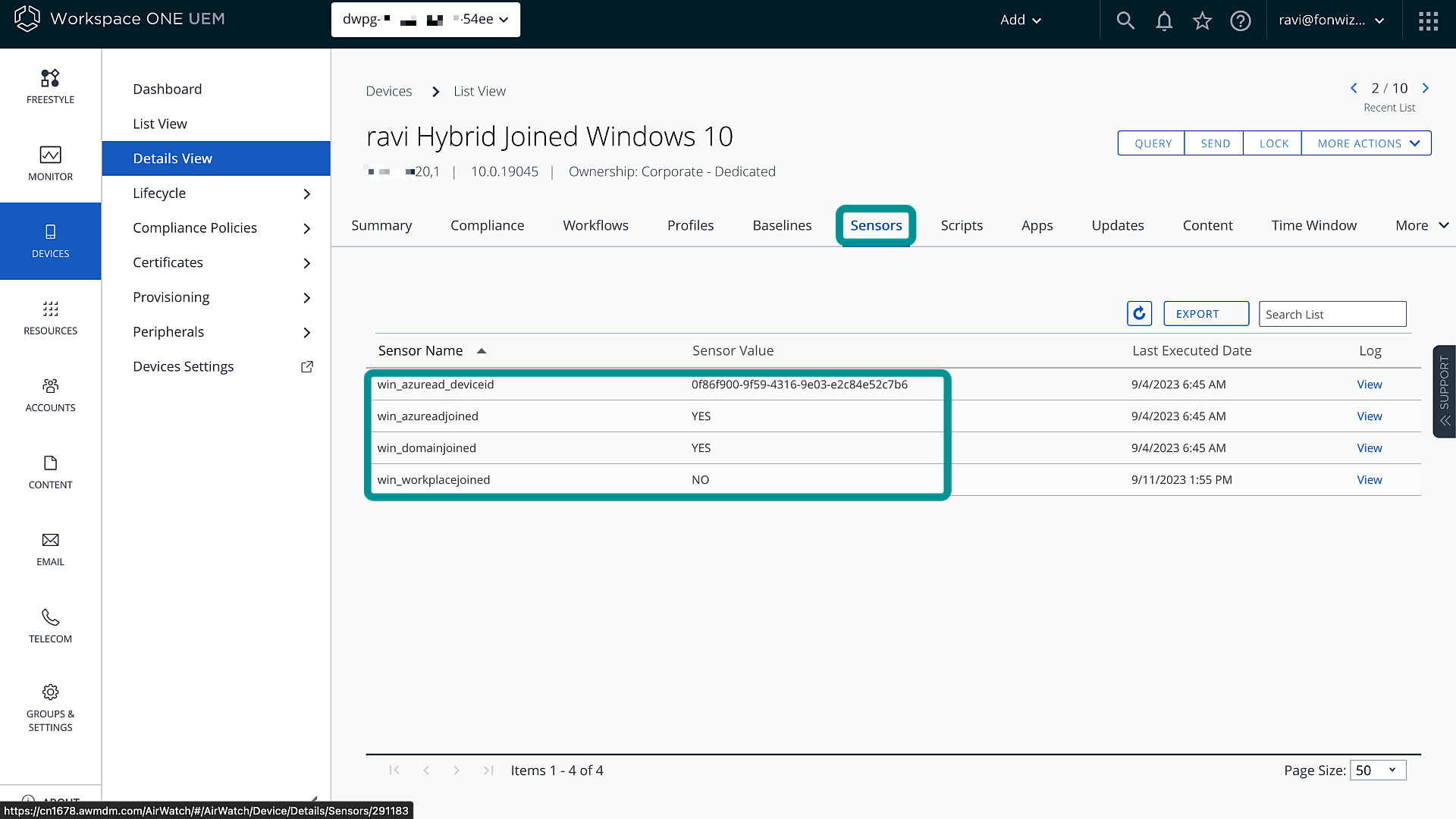
Figure 6: UEM device details Hybrid joined
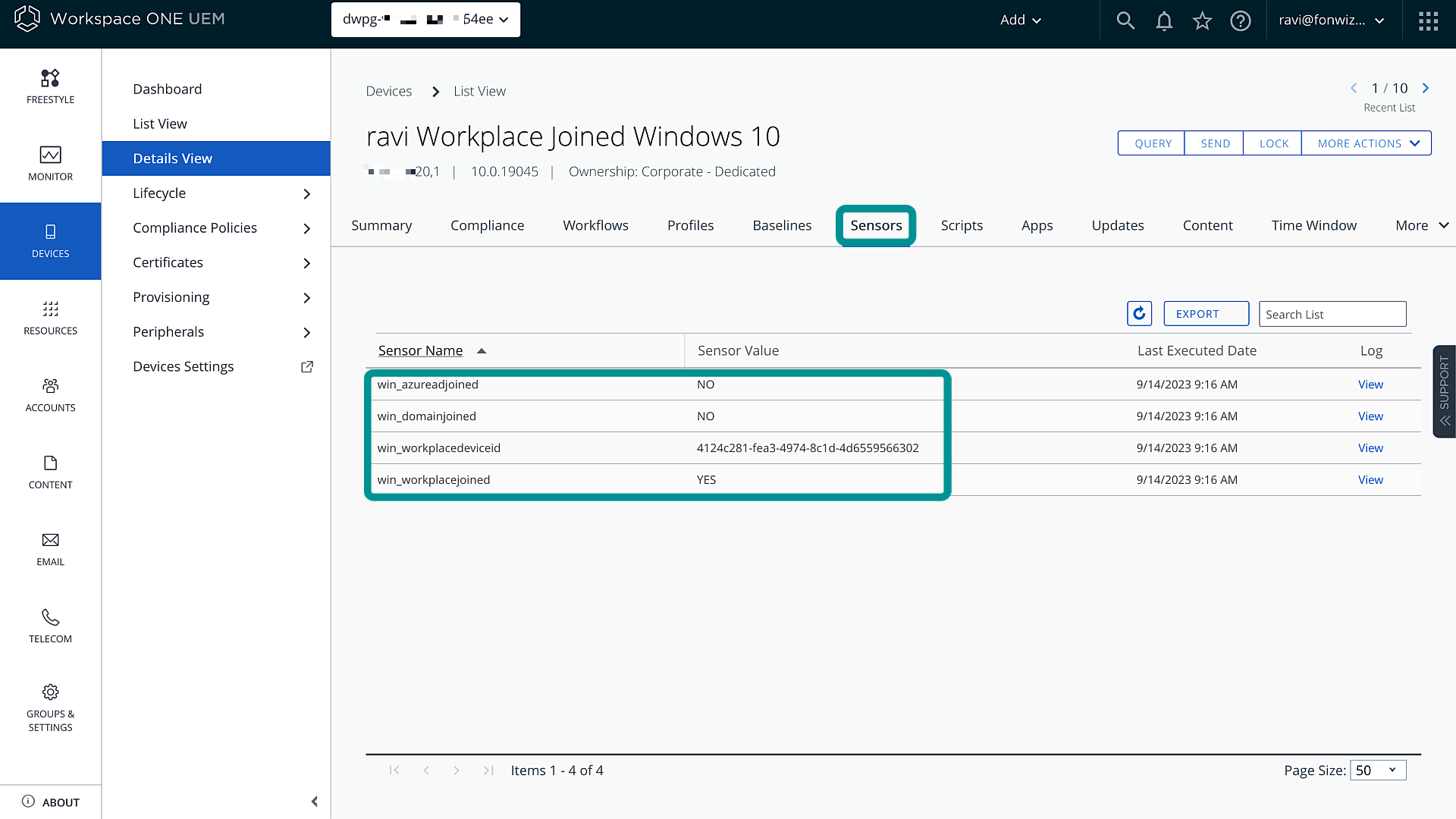
Figure 7: UEM device details for workplacejoined
Set Up Entra ID Enterprise App
Now, we have all the device information from UEM to build Freestyle automations and target the correct device in Entra ID.
To build out that part of the integration, we must add an enterprise application in Entra ID which we can give the correct permissions to update the device. Add the app through app registrations and set the permissions.
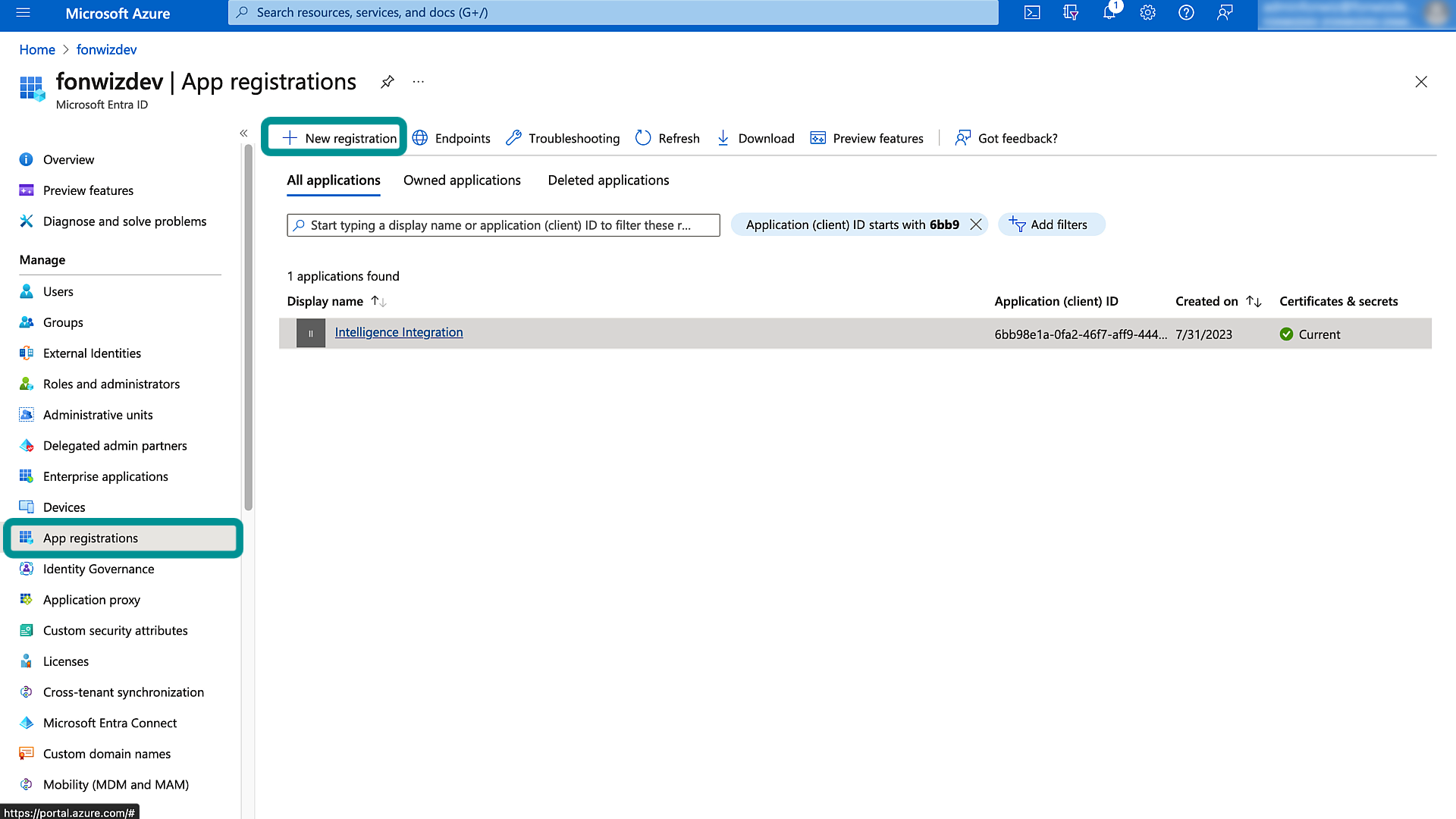
Figure 8: Entra ID App registration
We want to achieve two main actions with the integration:
- Revoke the user session – we need the Microsoft Graph User Read Write All permission.
- Update the device managed and compliance state – we require the Microsoft Graph Device Read Write All permission.
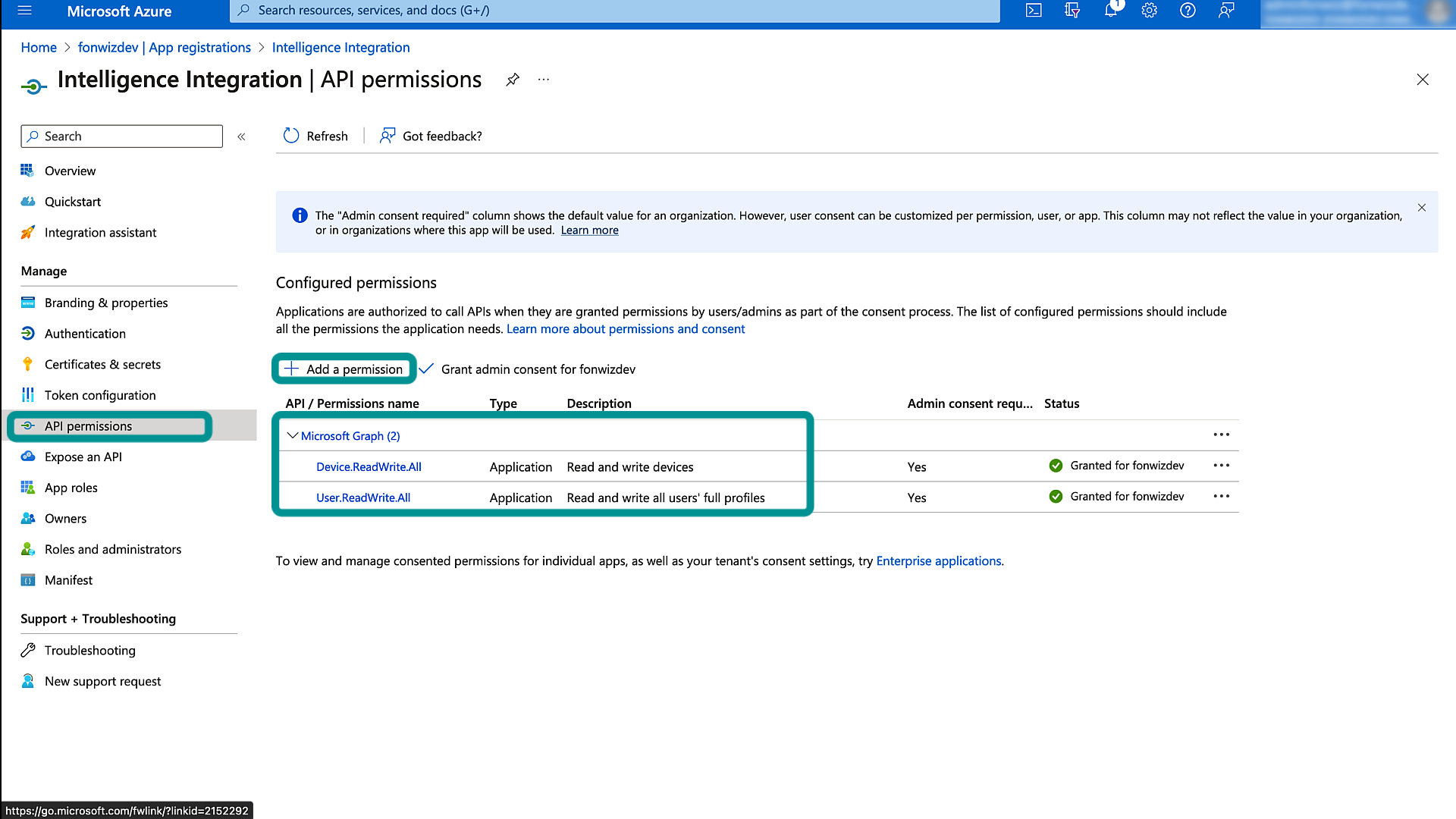
Figure 9: Entra ID App API permissions
Intelligence must authorize with Entra ID (now known as Entra ID) to perform the required API calls for the automation. To achieve this, we require the Application (Client) ID and must create a secret to use as client credentials to request authorization in the form of OAuth Access tokens.
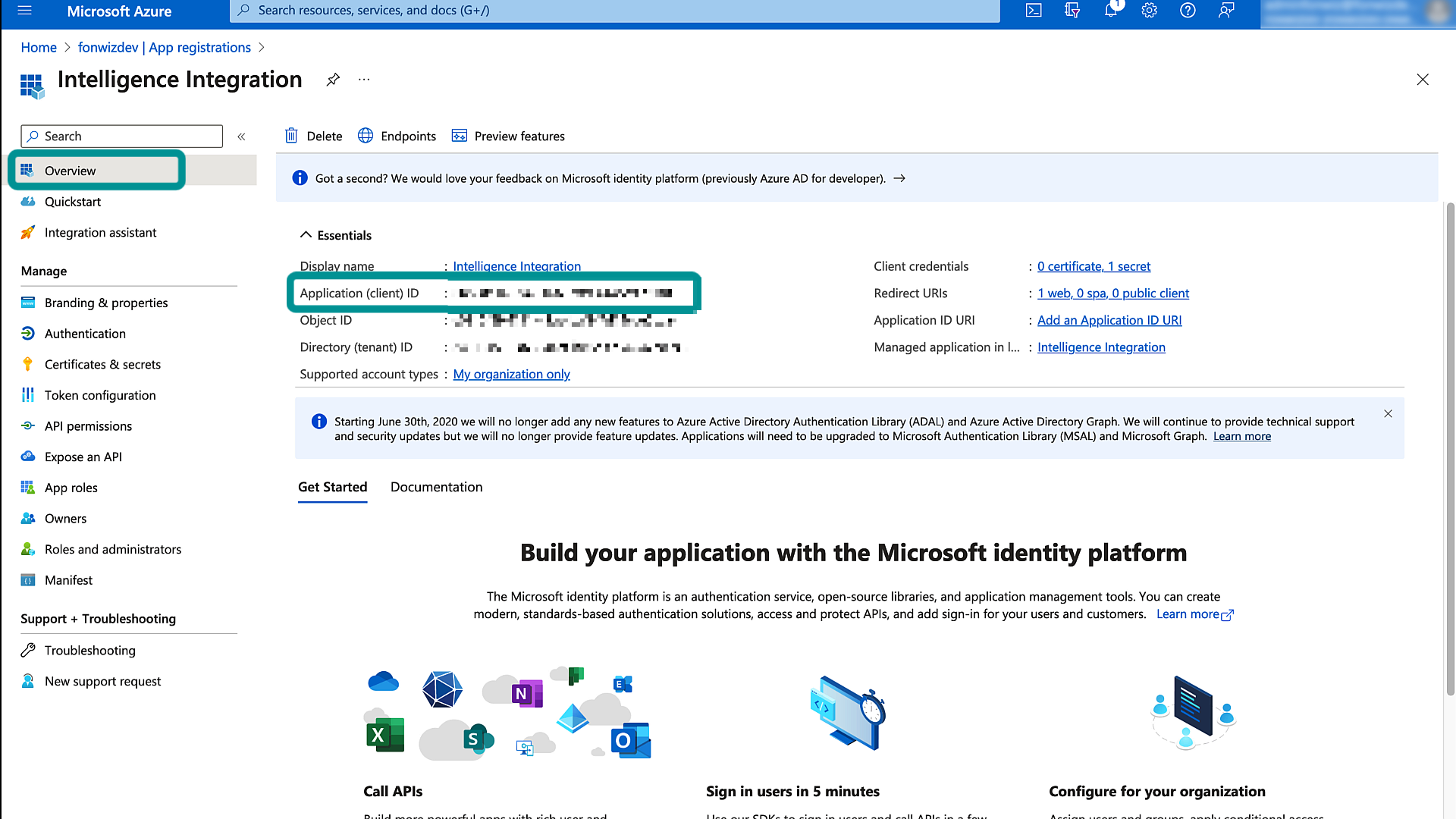
Figure 10: Entra ID Application ID
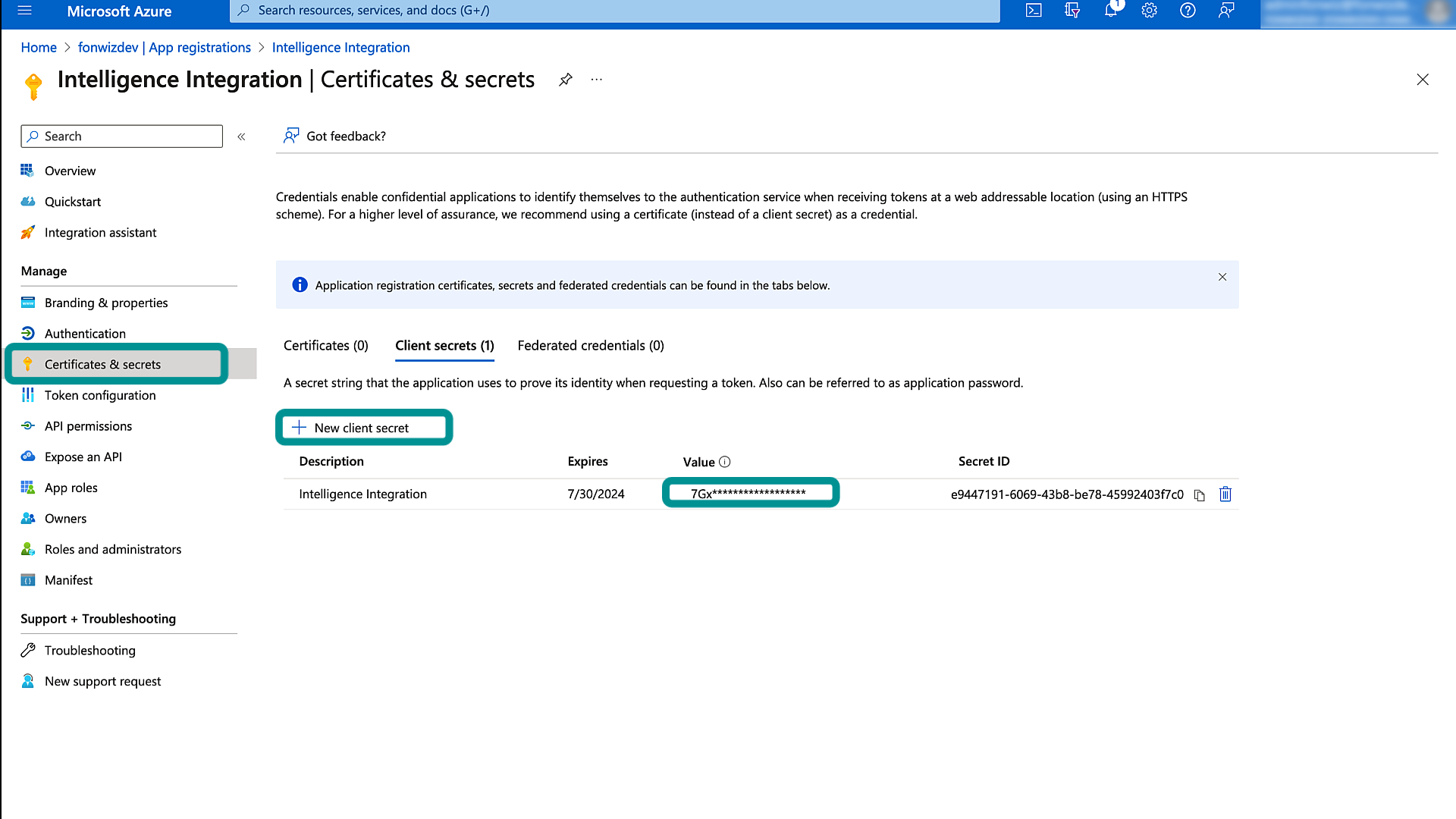
Figure 11: Entra ID App Secret
Set Up Freestyle Automation
Now that the application is set up, go to Intelligence to add a custom connector integration under Integrations > Workflow Connectors.
For more information, see Intelligence Custom Connector documentation in Omnissa Docs.
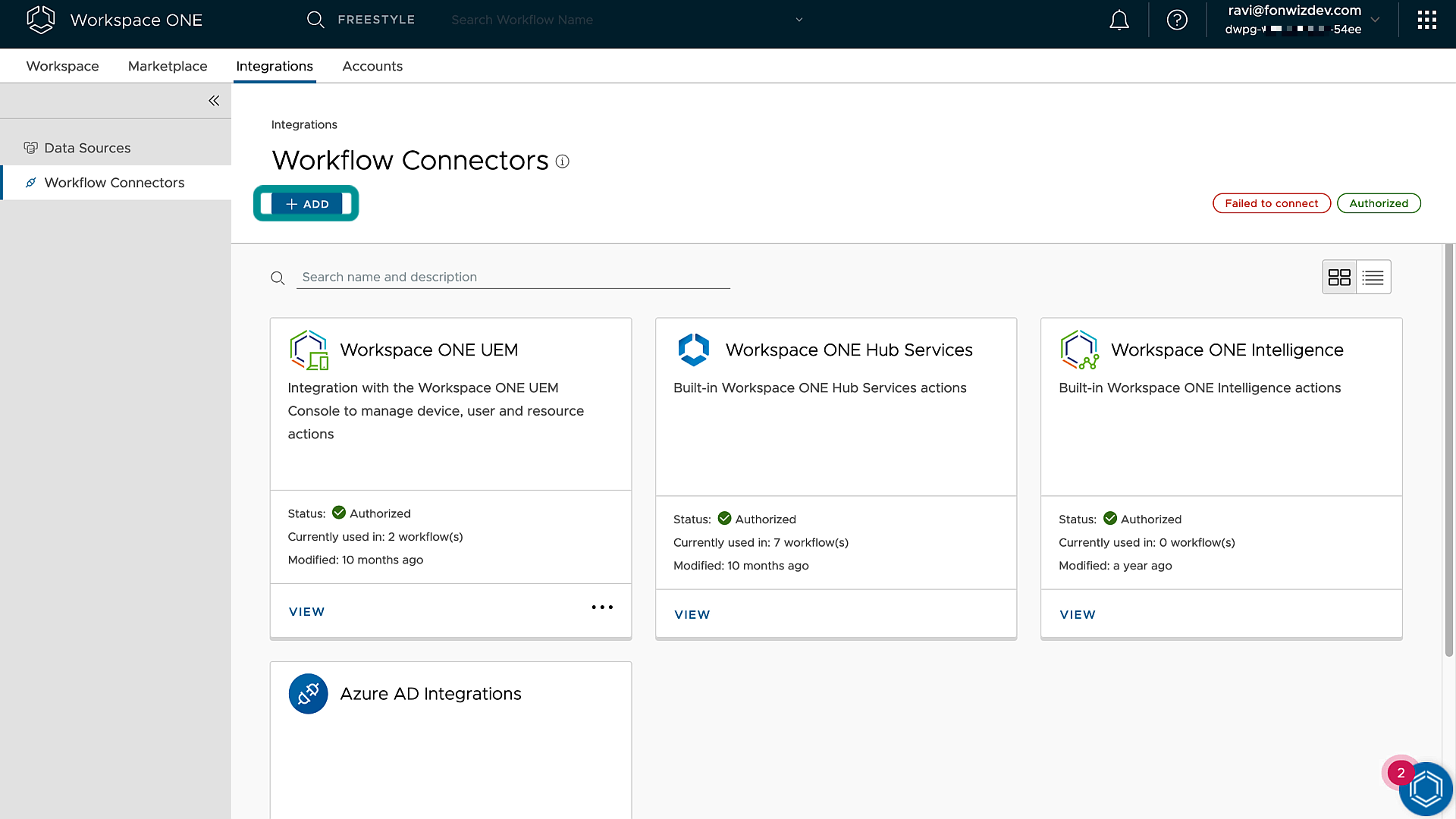
Figure 12: Intelligence Custom Connector
Add a connector and add the required details for authorization with the Microsoft Graph API. Use the following table as guidance.
| Base URL | |
| Auth Type | OAuth2 Authentication |
| Client ID | Application ID |
| Client Authentication Location | Send client credentials in body |
| Grant Type | Client Credentials |
| OAuth2 Token URL | https://login.microsoftonline.com/EntraIDTenantID/oauth2/v2.0/token |
| Client Secret | Client Secret |
| Scope |
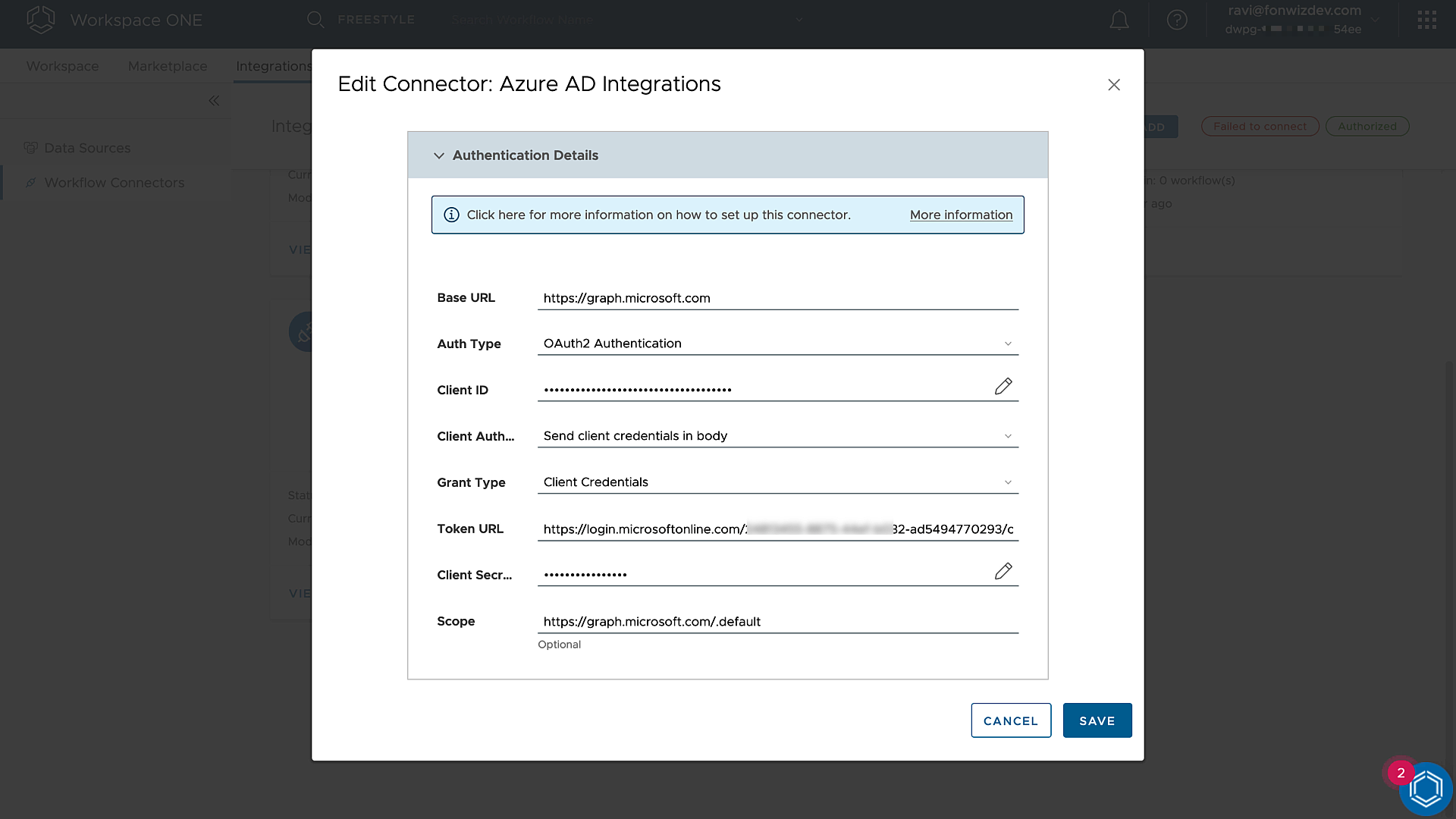
Figure 13: Intelligence Custom Connector Authorization
Now we have the connector, but we must specify which Microsoft Graph API calls to perform. Intelligence custom connectors use Postman (a RestAPI testing tool) exports called collections as blueprints for the calls. The collection we want to use has calls to set the isCompliant and isManaged flag as well as a call to revoke the current user sessions.
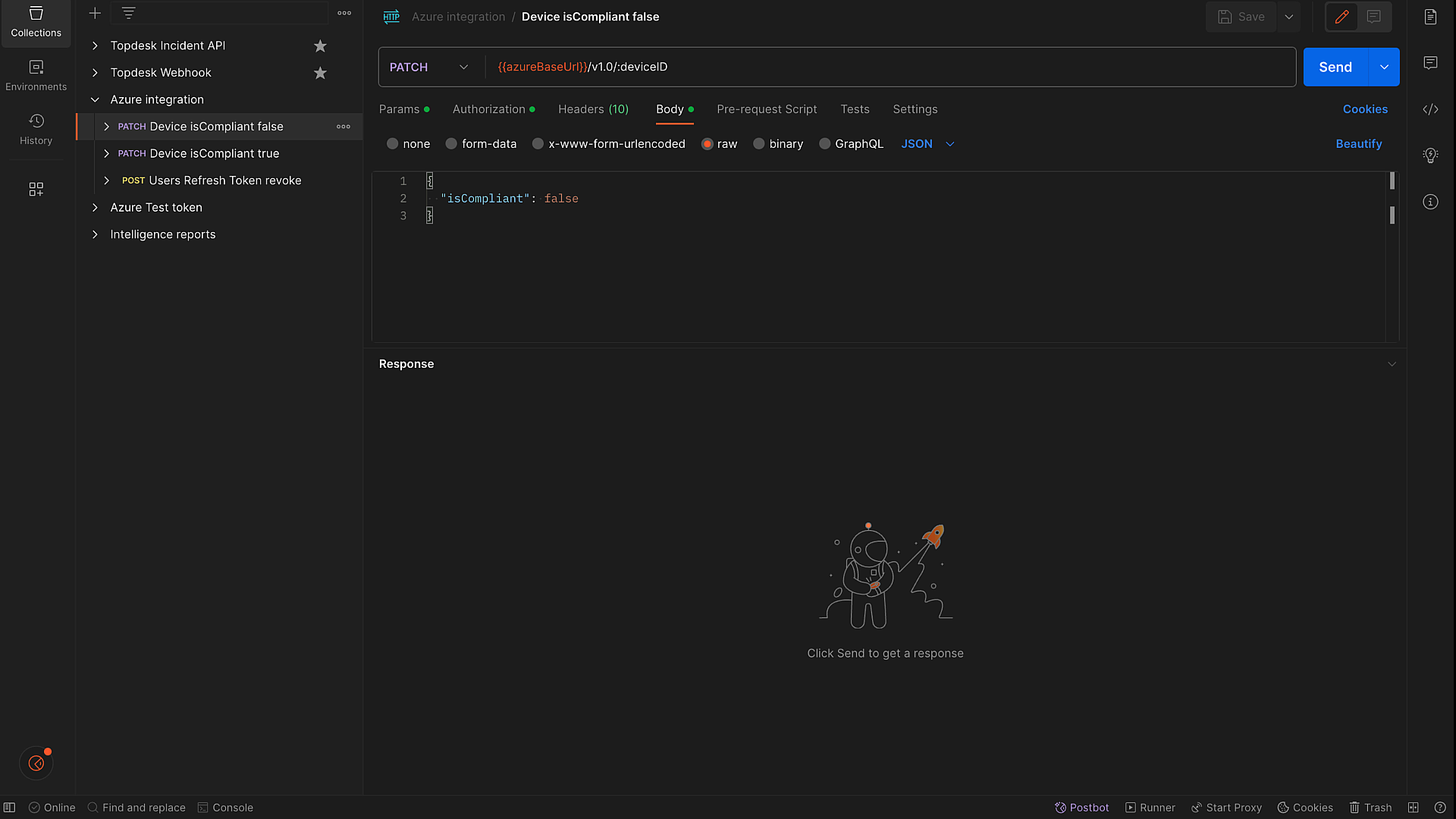
Figure 14: Postman Entra ID Integration collection
Again, on GitHub, I saved a Postman collection export with the API calls to set the device compliance state and revoke the user session.
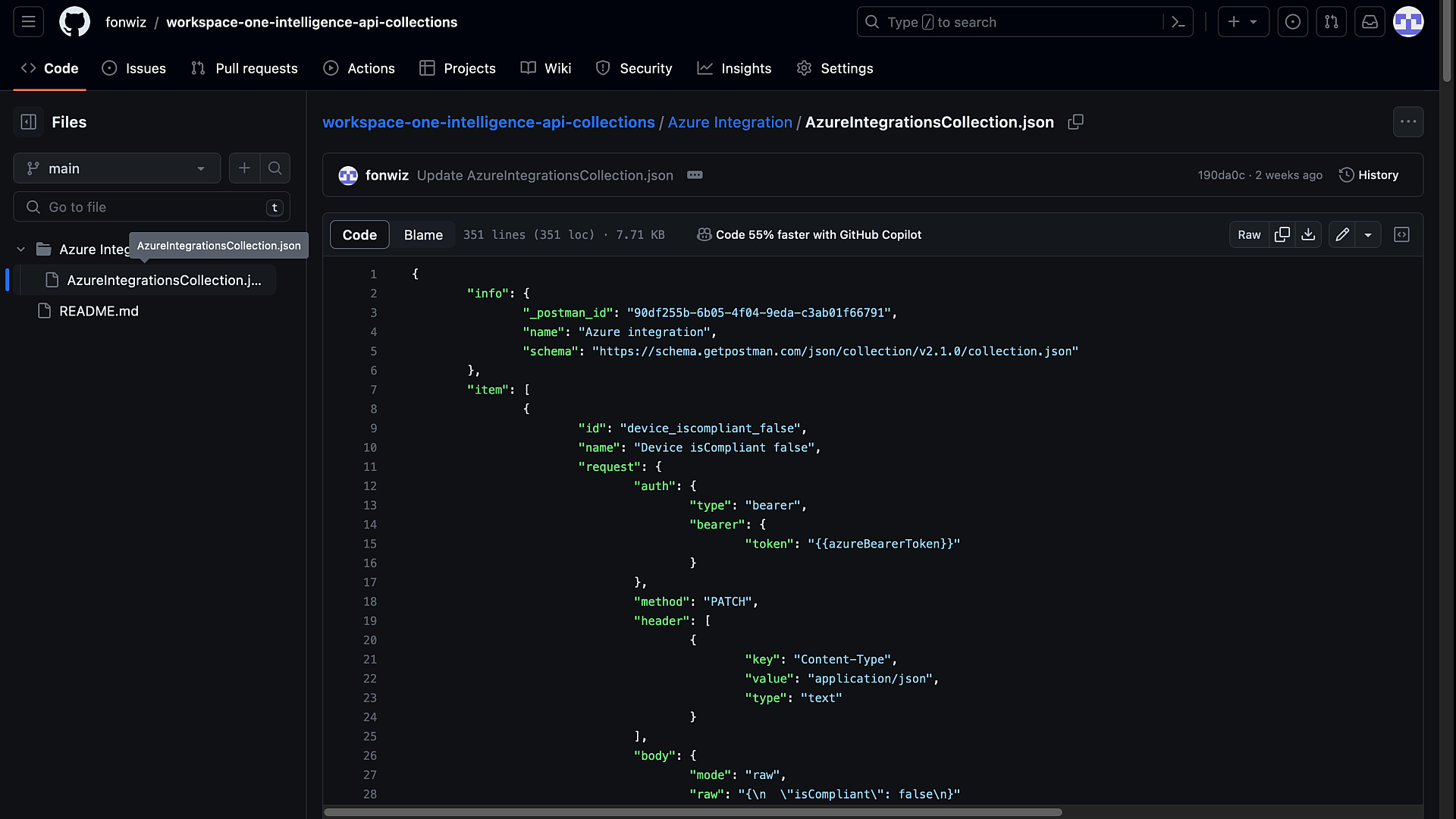
Figure 15: GitHub Postman Entra ID Integration collection
That collection can be imported under Import Actions in the custom connector and, with that, we have set up custom actions to use inside Freestyle workflows.
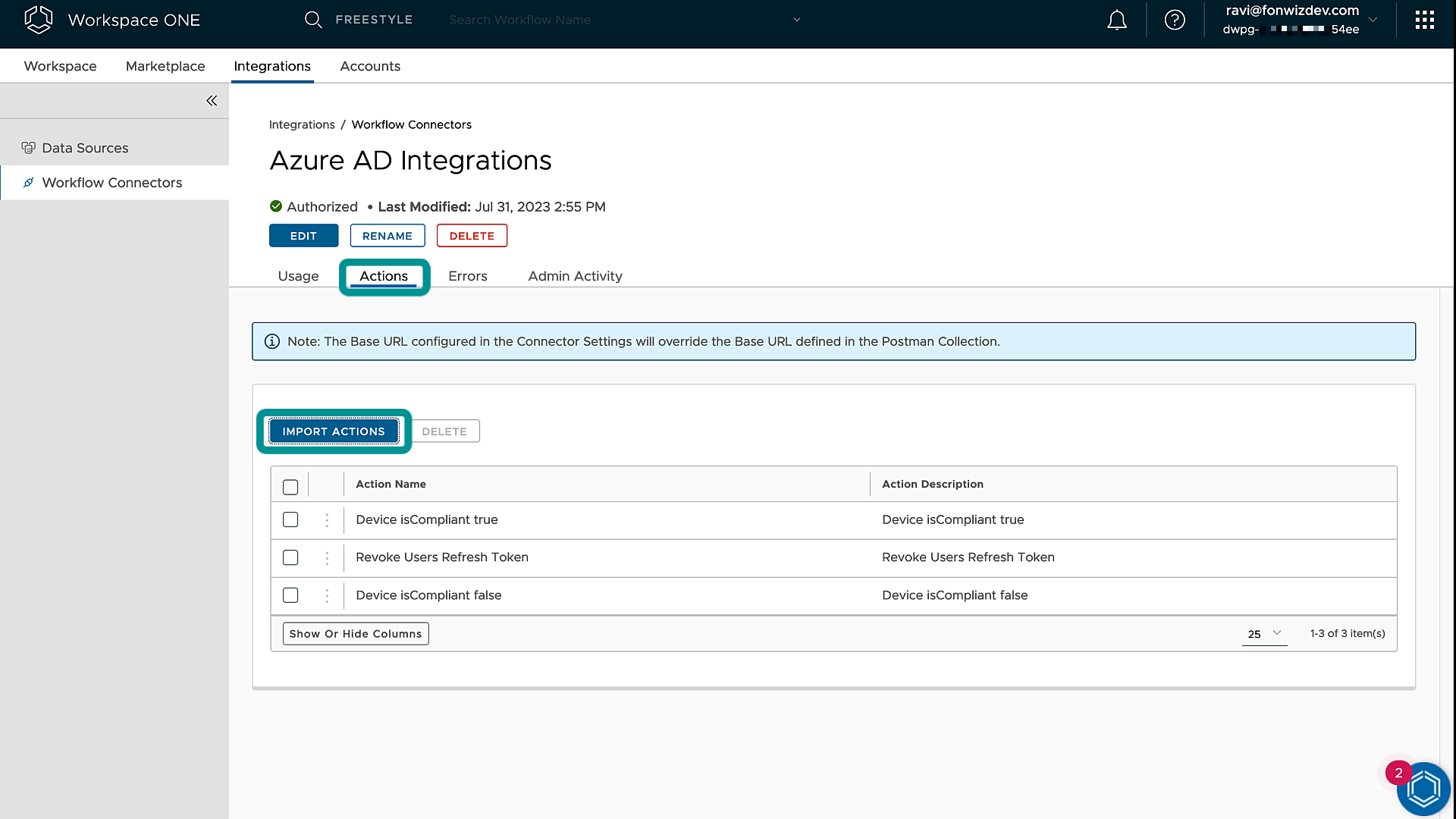
Figure 16: Intelligence Custom Connector Import Action
The next step is to build the automation under Workspace > Freestyle in Intelligence. For more information, see Intelligence Freestyle Orchestrator documentation in Omnissa Docs.
Figure 17: Intelligence Freestyle Workflow Add
We build a flow for Workspace ONE UEM device data and the automation should trigger automatically based on the trigger rules we apply.
In our case, we want to check on all Windows devices that are enrolled and for which we get sensor values of “YES” for domain joined and Entra ID joined, and where the compliance state is “compliant”.
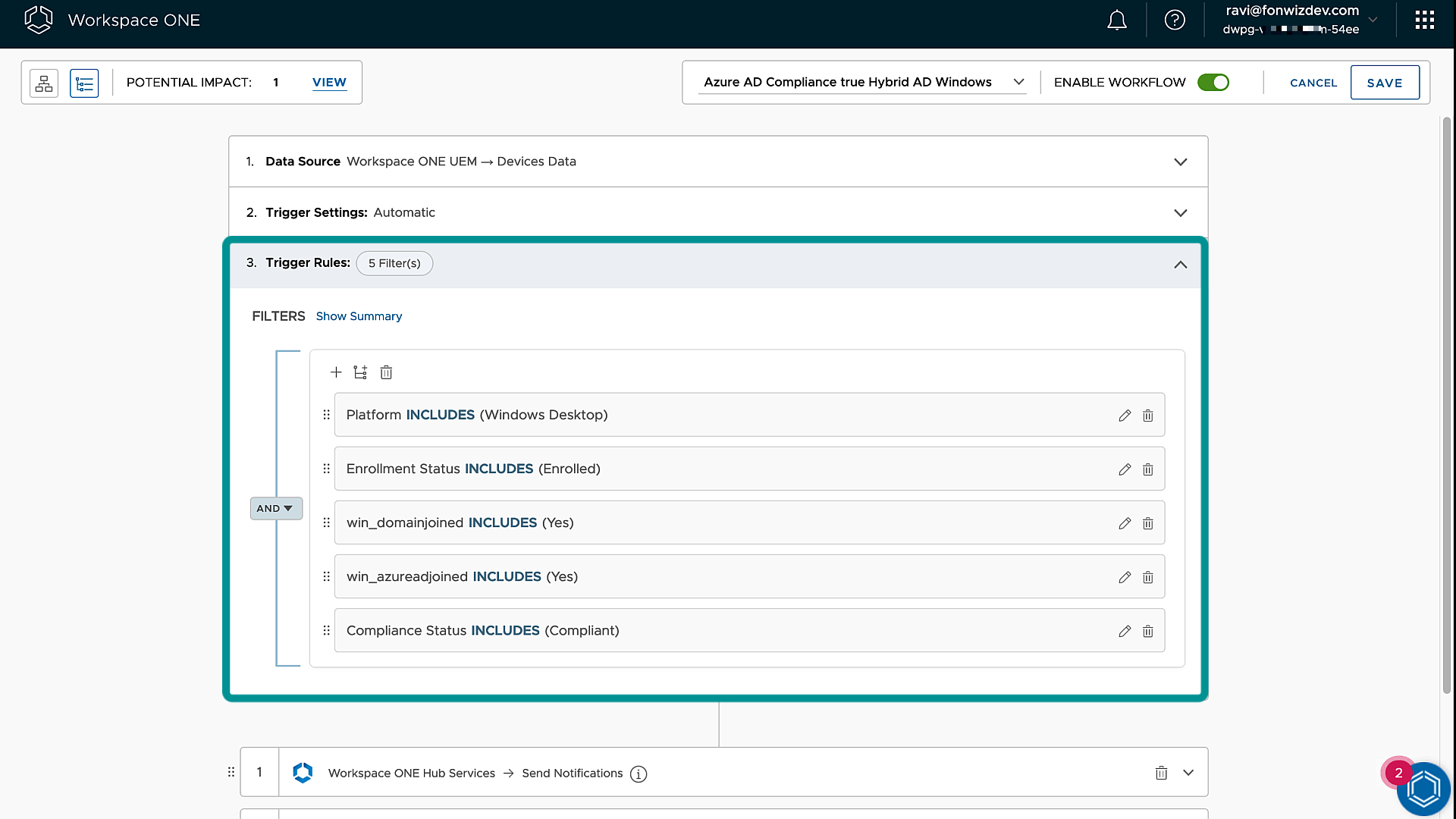
Figure 18: Intelligence Freestyle Workflow Trigger rules
The following table provides an overview of what Entra ID join scenario can be identified by which sensor value and which sensor will give you the correct device ID. You must build the trigger accordingly to target the right device type.
| Sensor value / Scenario | Entra ID Joined | Hybrid Entra ID joined | Workplace Joined/Registered |
| win_azureadjoined | YES | NO | Not used |
| win_domainjoined | YES | YES | Not used |
| win_workplacejoined | Not used | Not used | YES (User specific) |
| win_azuread_deviceid | Device GUID | Device GUID | Not used |
| win_workplacedeviceid | Not Used | Not Used | Device GUID (User specific) |
To build out the actions, we first send out a notification to let the user on the device know that, for compliant devices, the user will have access to Office 365 or other Entra ID federated resources.
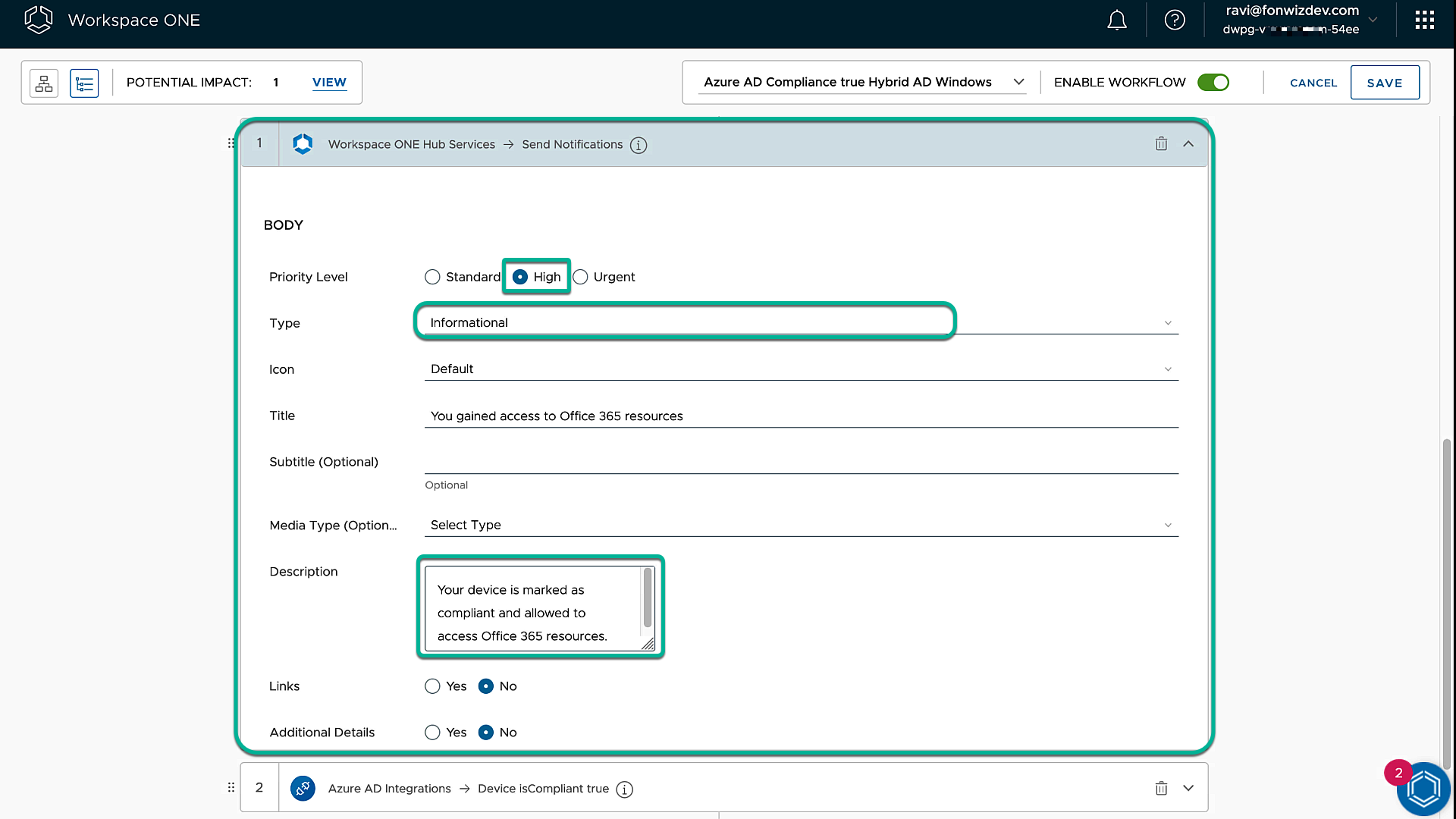
Figure 19: Intelligence Freestyle Workflow action notification
Next, we add the action for the Microsoft Graph API call which targets the right device by using the sensor data we received as a parameter in the call. You can add the variable with the + sign. Make sure the rest of the path_variable looks like the default value.
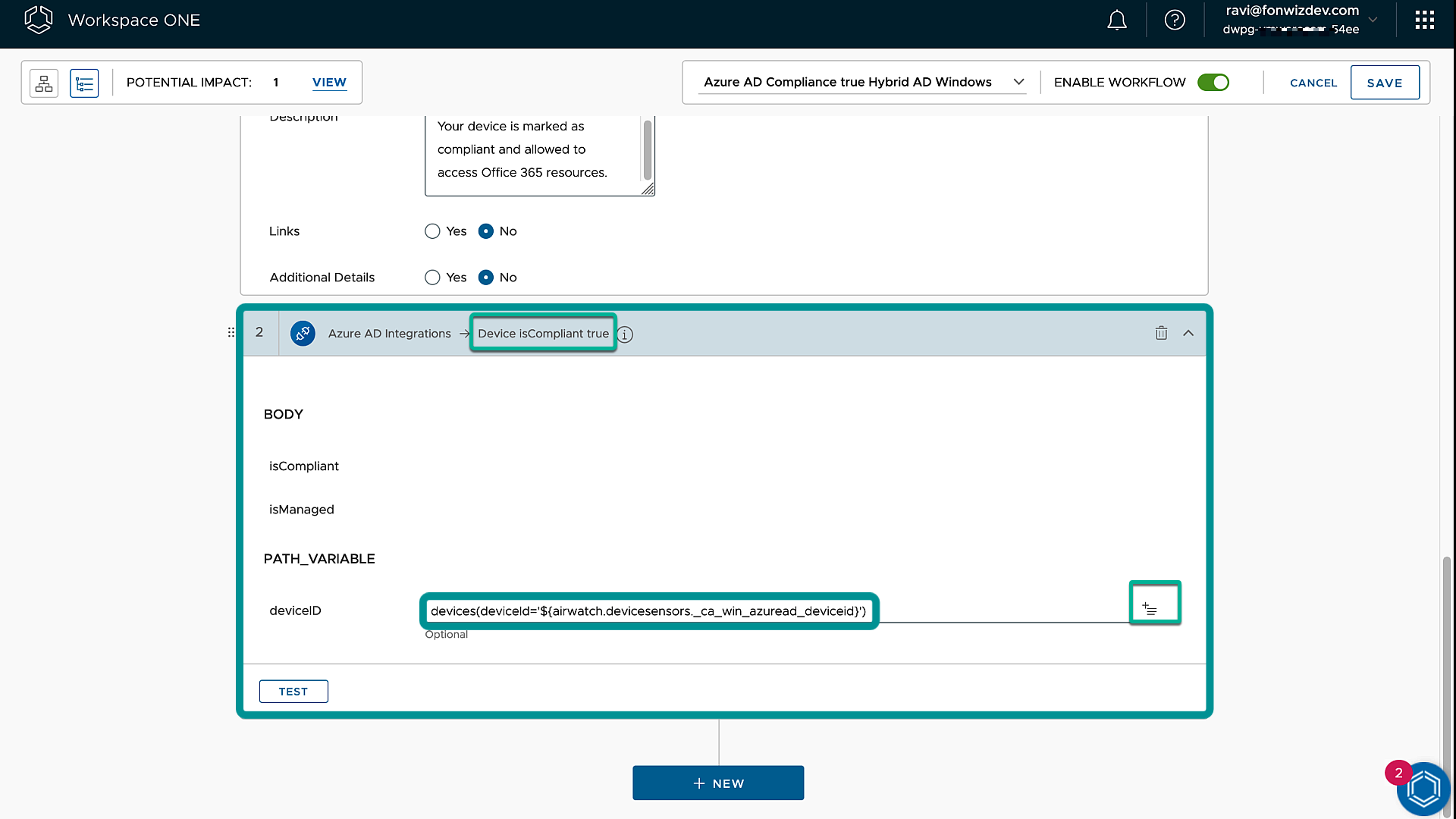
Figure 20: Intelligence Freestyle Workflow action Graph API call
Check how many devices are potentially affected then save the workflow and run once to apply the current state to Entra ID.
Follow the same steps to add a flow for non-compliant devices and change the trigger to target non-compliant or devices that are just unenrolled.
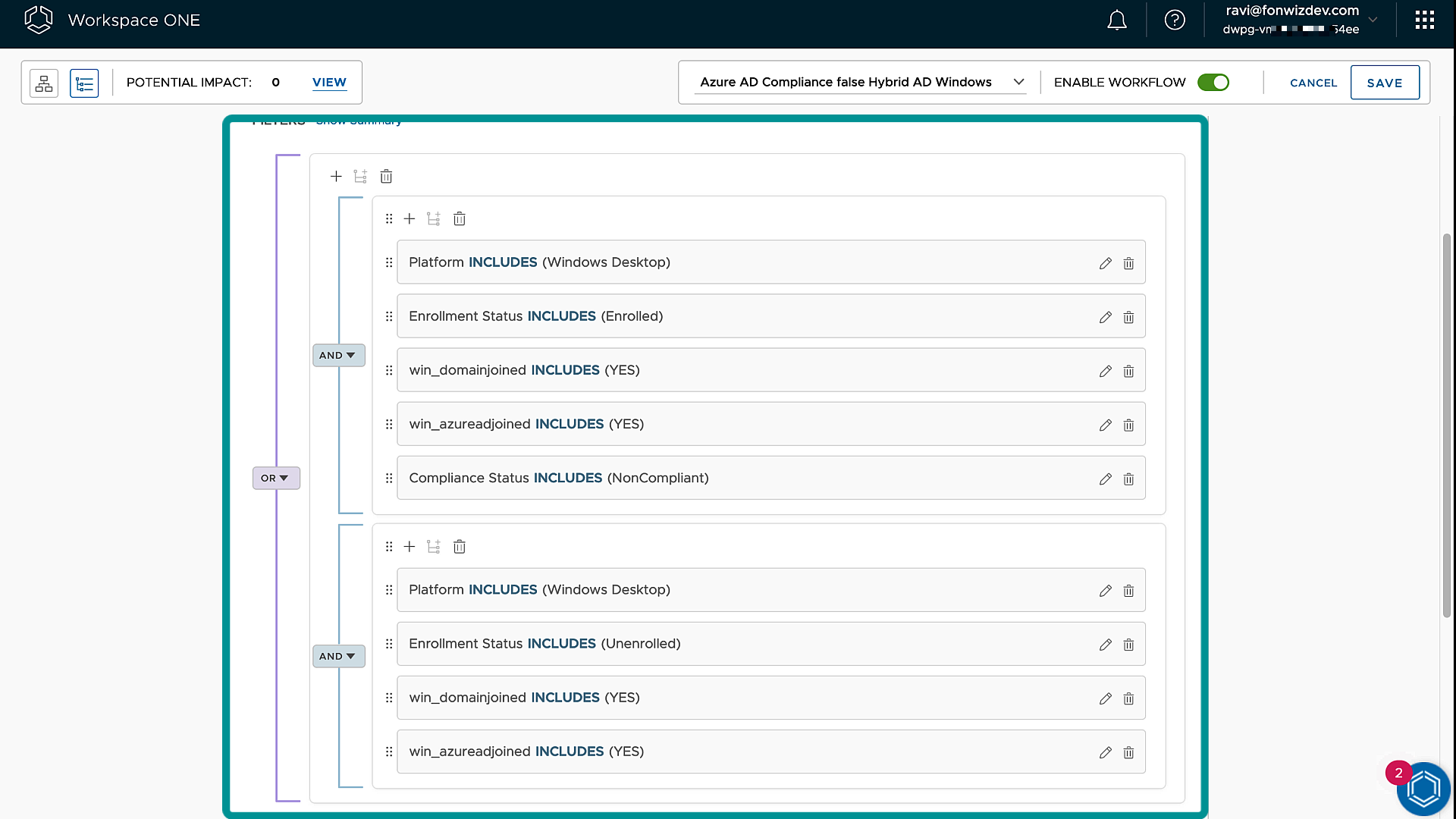
Figure 21: Intelligence Freestyle Workflow Non-Compliant trigger rules
Again, we inform the user that, because of compliance violations, the device cannot access Office 365 resources. Add actions to revoke the user sessions and set the device to noncompliant in Entra ID.
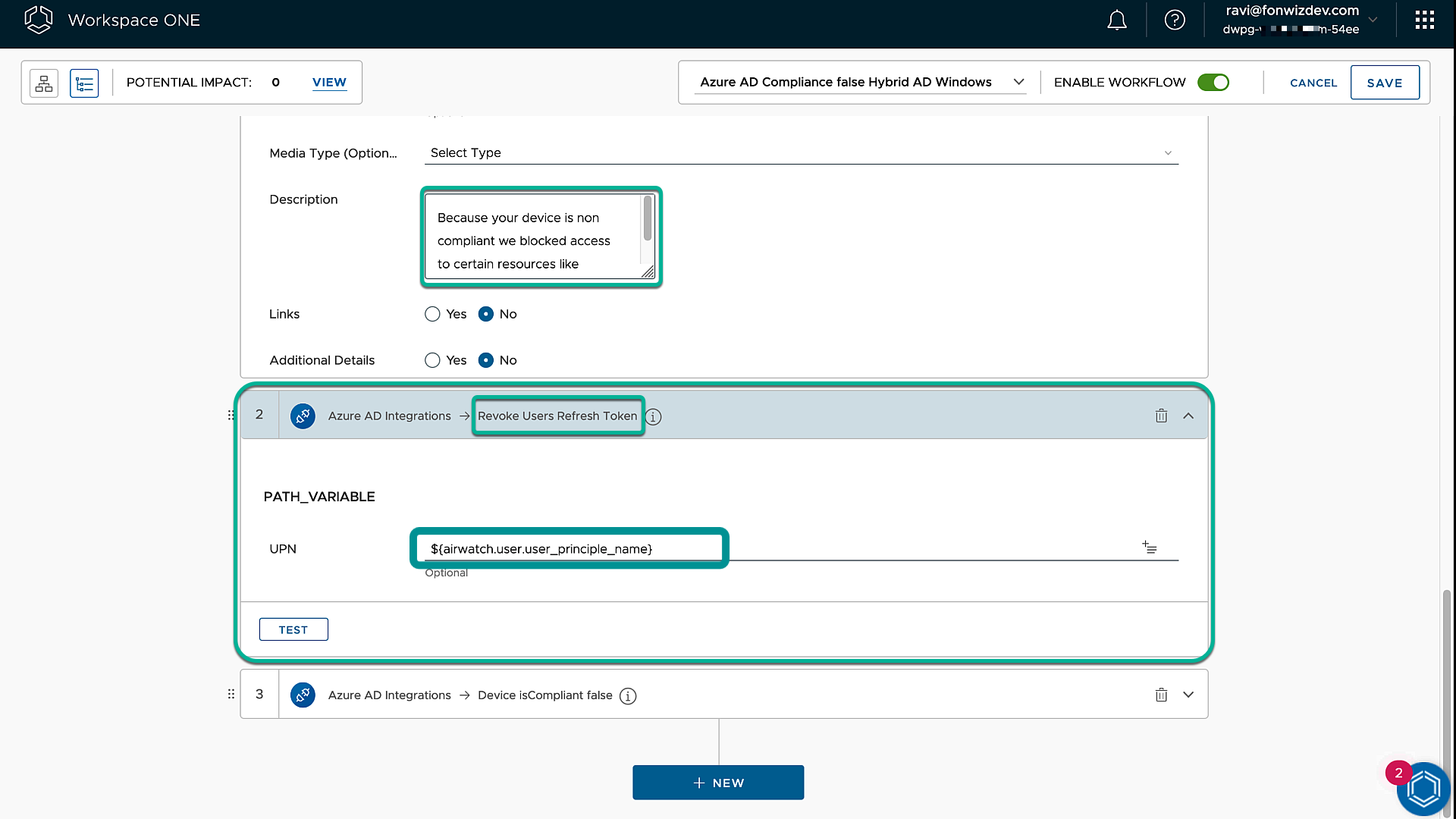
Figure 22: Intelligence Freestyle Workflow Non-Compliant actions notification and session revocation
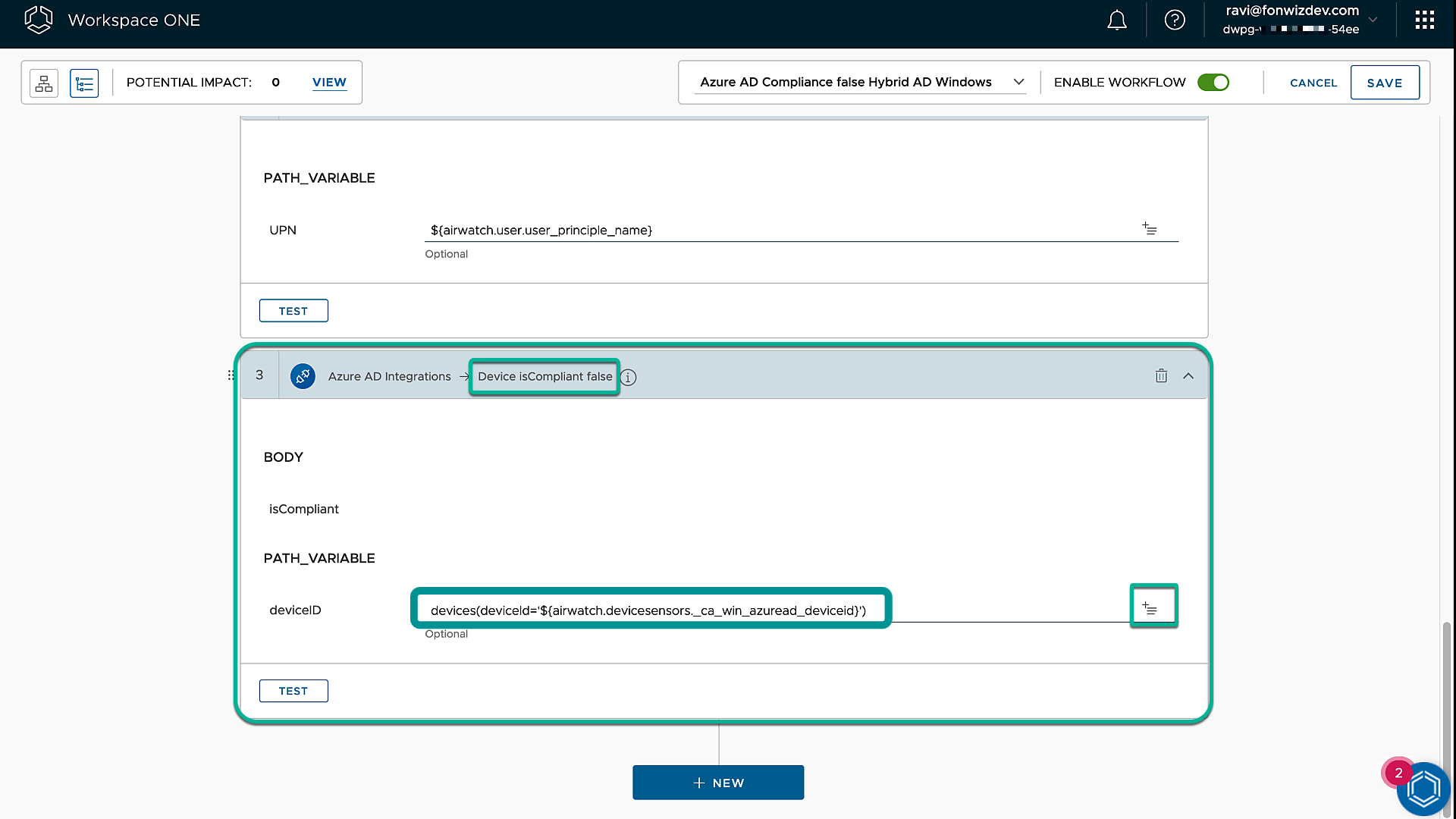
Figure 23: Intelligence Freestyle Workflow Non-Compliant actions compliance false
You can already see a change in Entra ID > All Devices; devices that already reported back the sensor data are now set to the respective compliance state from UEM.
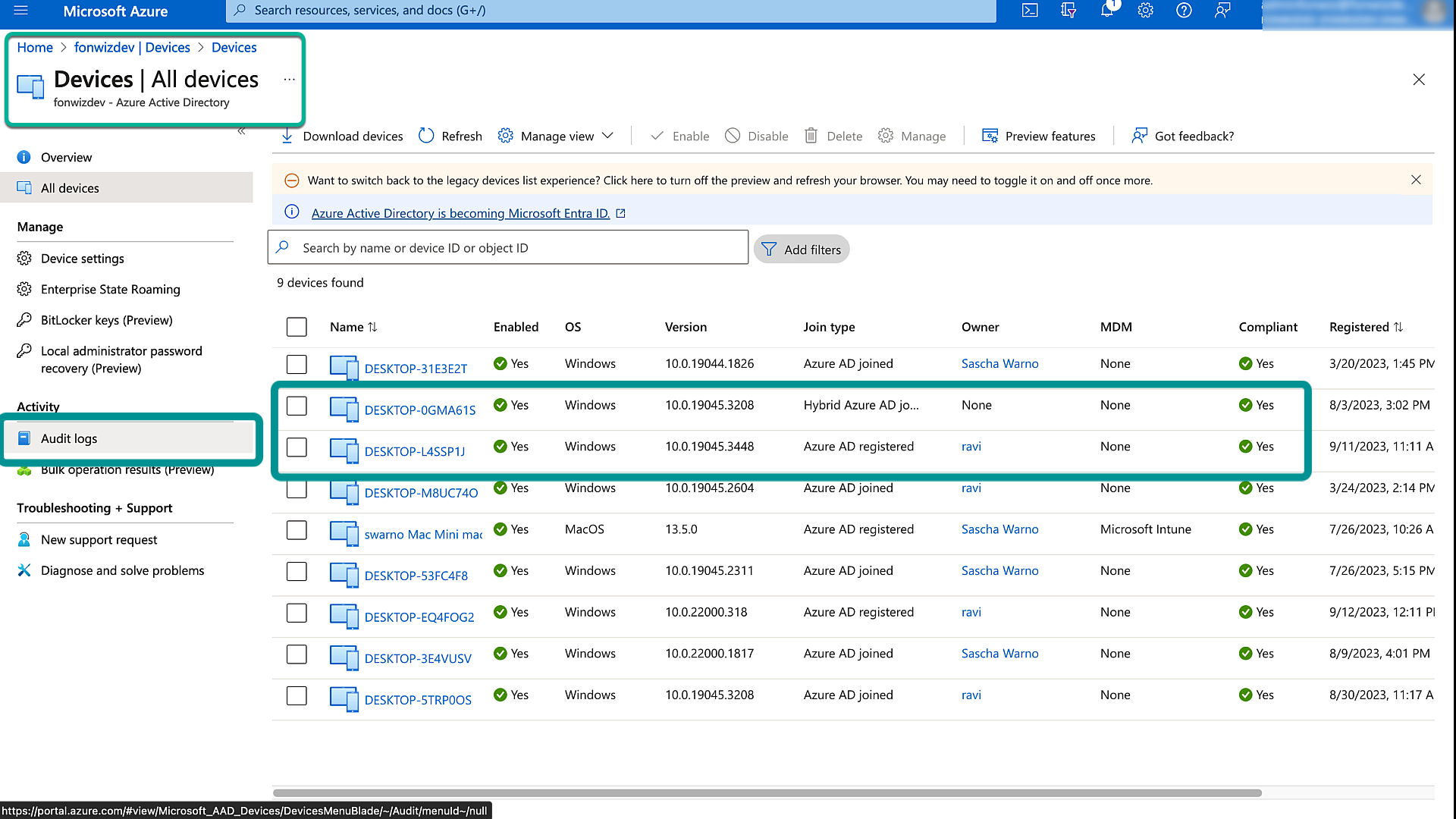
Figure 24: Entra ID All Devices compliant set
In the audit data, you should see that the state was updated by our enterprise app created for the integration. In the details, you can see the fields that got updated on the device object, isManaged and isCompliant.
Similarly, you can see the update for non-compliant devices where the iscompliant state was set to false.
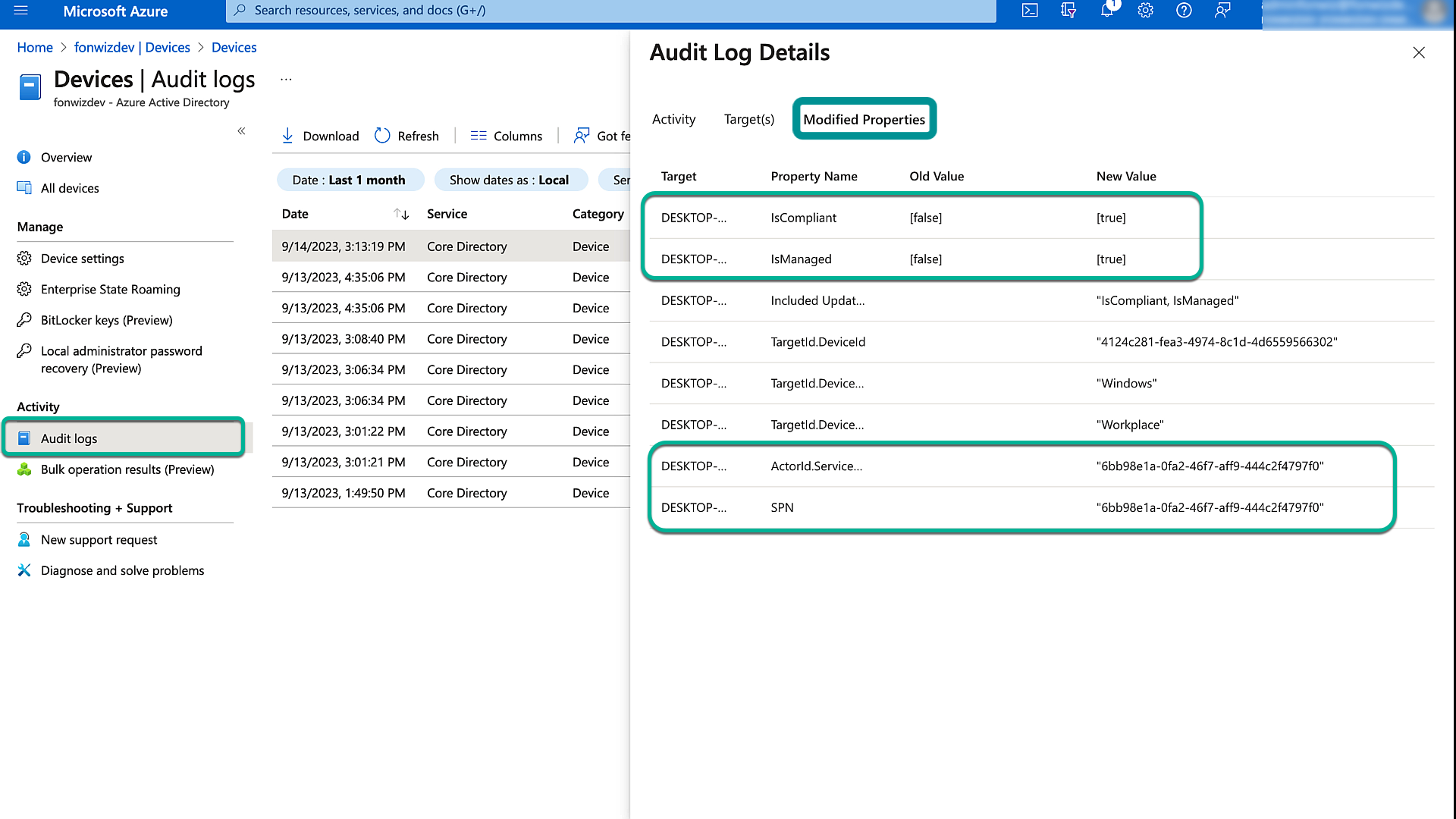
Figure 25: Entra ID All Devices audit logs
Now, we can go into the Entra ID Conditional Access policies and apply a rule for all Windows devices and users that require compliant devices. This setup is covered in previous articles and videos: Setting up Entra ID Conditional Access rules.
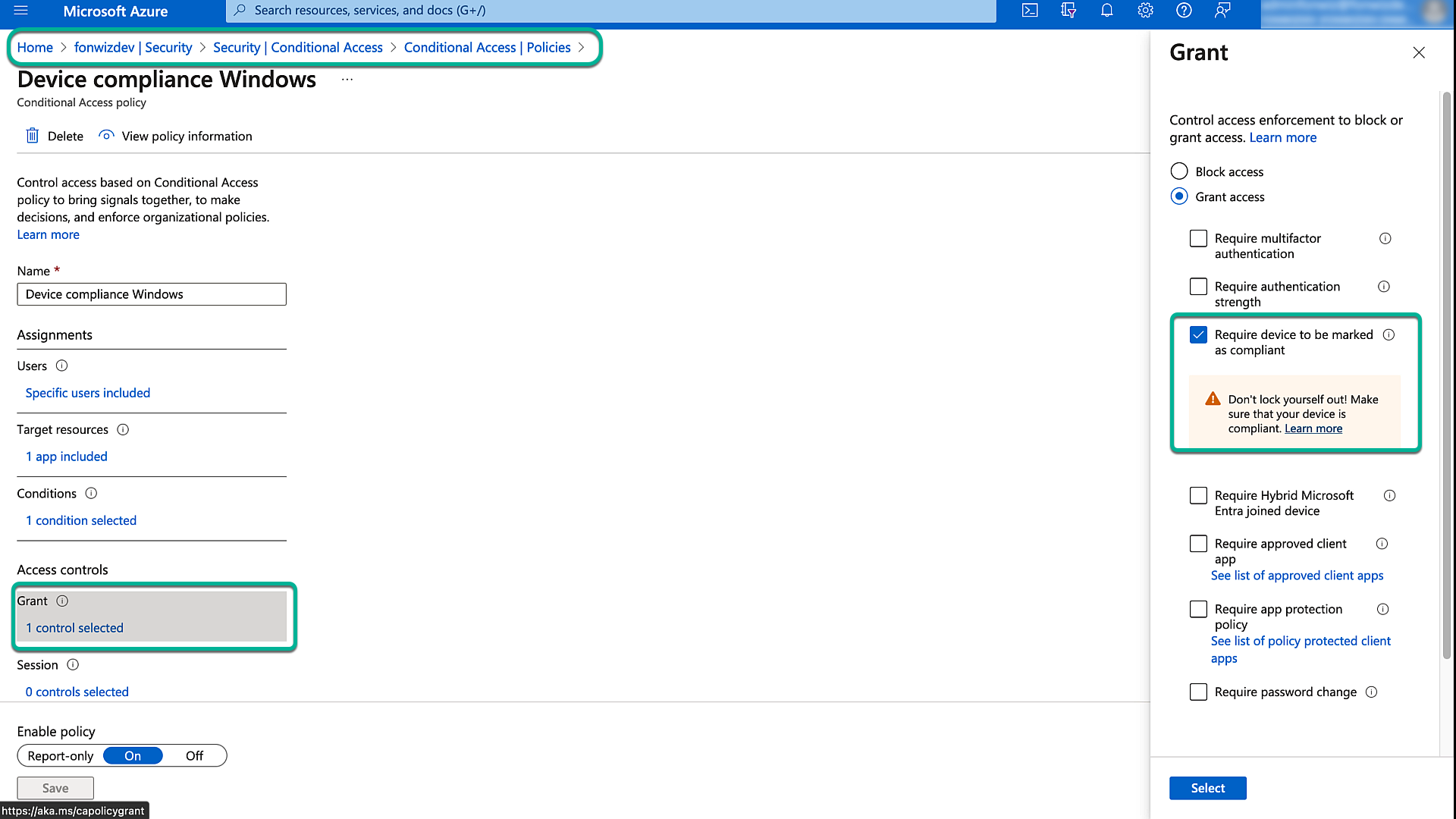
Figure 26: Entra ID Conditional Access policy
This concludes the setup of the integration. The accompanying video, Device Posture in Entra ID using Omnissa Intelligence, shows the different components in action and follows through with the workflow. This demo also depicts the end-user experience including messages they can expect to see on their device.
Summary and Additional Resources
This extension of our series on Workspace ONE compliance integrations into Entra ID and Office 365, provides a solid overview of how to leverage automation orchestrators, like Workspace ONE Intelligence Freestyle with exposed APIs such as Microsoft Graph, to build a custom integration using the device state or other data to, in our case, enhance the security of your end-user solutions.
We welcome your feedback—comment on other integrations you would like us to work on or solutions you have already implemented.
Additional Resources
For more information about Zero Trust, you can explore the following resources:
- Device Posture in Entra ID using Omnissa Access [part 1]
- Device Posture in Entra ID using Workspace ONE Tunnel [part 2]
- Device Posture in Entra ID using API [part 3]
- Device Posture in Okta
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2024/11/6 |
|
| 2023/10/13 |
|
About the Author
This document was written by:
- Sascha Warno, Staff Architect Identity & Security Solutions, EUC Technical Marketing, Omnissa
Feedback
Your feedback is valuable.
To comment on this paper, contact Omnissa End-User-Computing Technical Marketing at tech_content_feedback@omnissa.com .

