Migrating from Tunnel Proxy to Per-App Tunnel
Overview
As technology evolves and remote access becomes a cornerstone of working culture, customers are moving away from traditional full-device VPNs and are looking more towards app tunnels as the new standard. The Omnissa Workspace ONE Tunnel application has long been enabling customers to have secure access to their internal resources while minimizing the threat vectors to your network.
Omnissa Workspace ONE® has provided two related solutions that are part of the Unified Access Gateway software appliance:
- Tunnel Proxy - enables SDK-built applications to set up an app-level proxy connection to internal sites, leveraging HTTPS encryption and certificate authentication. The Omnissa Workspace ONE Web app embeds Proxy support by default.
- (Per) App Tunnel - enables an SSL VPN connection on a full tunnel and per-app basis for any public or internal application for managed devices. The Workspace ONE Tunnel application resides on a device, and an administrator explicitly specifies which apps are enabled for Tunnel when using per-app capability or all apps when using full tunnel. Workspace ONE also offers a new Tunnel SDK module as part of the Workspace ONE SDK, which serves as a replacement to the Tunnel Proxy solution. The Tunnel solution is more secure, has better performance, and has more features than Proxy.
As such, The Tunnel Proxy component part of Workspace ONE Tunnel is no longer supported. See the Tunnel Proxy End of Support Life announcement. All Tunnel Proxy use cases have been consolidated into the Tunnel gateway, app, and SDK.
Audience
This guide is intended to help Workspace ONE UEM administrators currently using Tunnel Proxy to migrate to unmanaged Tunnel.
Both current and new administrators of existing production environments can benefit from using this guide. Hands-on experience and knowledge of Omnissa Workspace ONE® UEM, Omnissa Tunnel gateway deployment through Unified Access Gateway or standalone method and Workspace ONE Tunnel app configuration is assumed.
Tunnel SDK use cases
The use of the Tunnel SDK module is primarily designed for native mobile applications on unmanaged devices that require communication with a resource on the internal network, like internal websites, REST API servers, desktops, and others.
Organizations that cannot manage end-user devices (such as contractors or BYOD) through mobile device management (MDM) and require access to corporate information through native mobile applications, can leverage:
- Workspace ONE Web app to enable access to internal websites.
- Workspace ONE SDK embedded into the company internal applications, to enable access to internal resources.
How Tunnel SDK module works
This section covers how the Tunnel module works.
Tunnel module (aka Tunnel SDK) on Workspace ONE SDK
A new Tunnel module was added to the Workspace ONE SDK to enable native mobile apps to perform app tunneling on unmanaged iOS and Android devices without the need for the Workspace ONE Tunnel application.
The Tunnel SDK leverages Device Traffic Rules defined in Omnissa Workspace ONE® UEM. When App Tunnel Mode is set to Workspace ONE Tunnel as part of the default SDK security policies, a compatibility option is available to support apps that have not yet migrated from Proxy to Tunnel.
Starting with version 7.6, the Workspace ONE Web app now comes equipped with the Workspace ONE SDK, featuring the new Tunnel module. This enhancement enables seamless use of Workspace ONE Web with Per-App Tunnel, enhancing security and connectivity.
When using the Tunnel SDK, the Workspace ONE Tunnel app and assignment of a Per-App VPN profile to the app are not required, which enables the use of unmanaged devices (MAM mode).
Enrollment method considerations
In MAM mode use cases, you must deploy SDK-based apps through the HUB app to receive the SDK configuration to perform app tunneling.
On devices managed through MDM, use a VPN profile payload and Workspace ONE Tunnel to achieve app tunneling.
Requirements
This section covers server, certificate, and application requirements.
Server
- Workspace ONE UEM 1905 and later.
- Omnissa Tunnel (Per-App) configured in Workspace ONE UEM with the following configuration for certificate authentication:
- Client Authentication for Tunnel only supports AirWatch CA; third-party CAs are not currently supported.
- Server Authentication may use either a public SSL certificate or an AirWatch CA.
- Omnissa Unified Access Gateway 2412 and above.
Application
Application requirements:
- Default SDK profile assigned to the mobile applications; custom SDK profiles are not currently supported.
- For internal applications that leverage Workspace ONE SDK, you must work with your development team to update the SDK to the latest version.
For more information, see:
When using Workspace ONE Web, version 7.6+ of the app is required.
Architecture
This section covers architecture and network considerations, and benefits.
Architecture and network considerations
Assuming you already have the Omnissa Tunnel (Per-App component) edge service enabled on the Unified Access Gateway appliance, nothing changes from an architecture perspective.
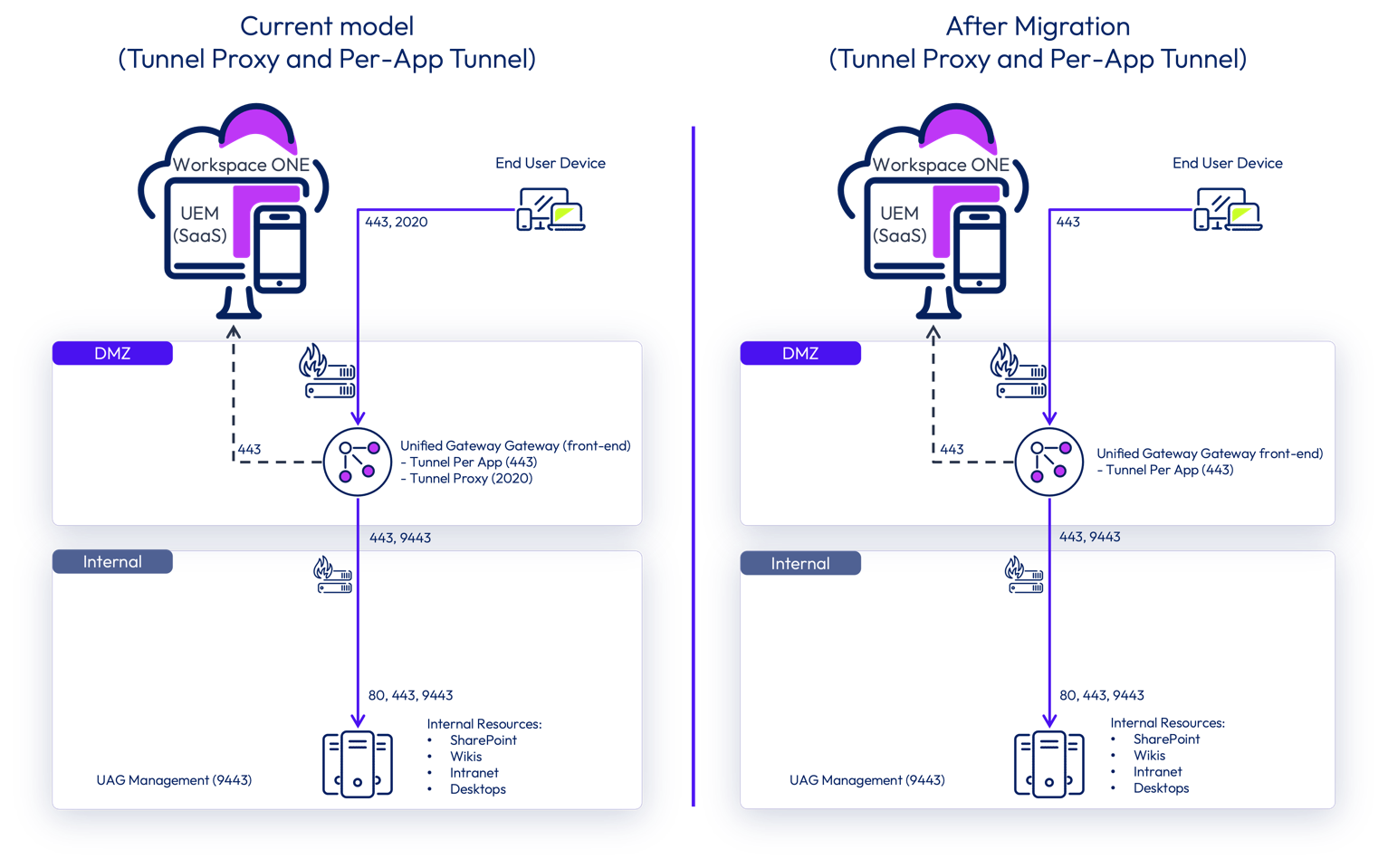
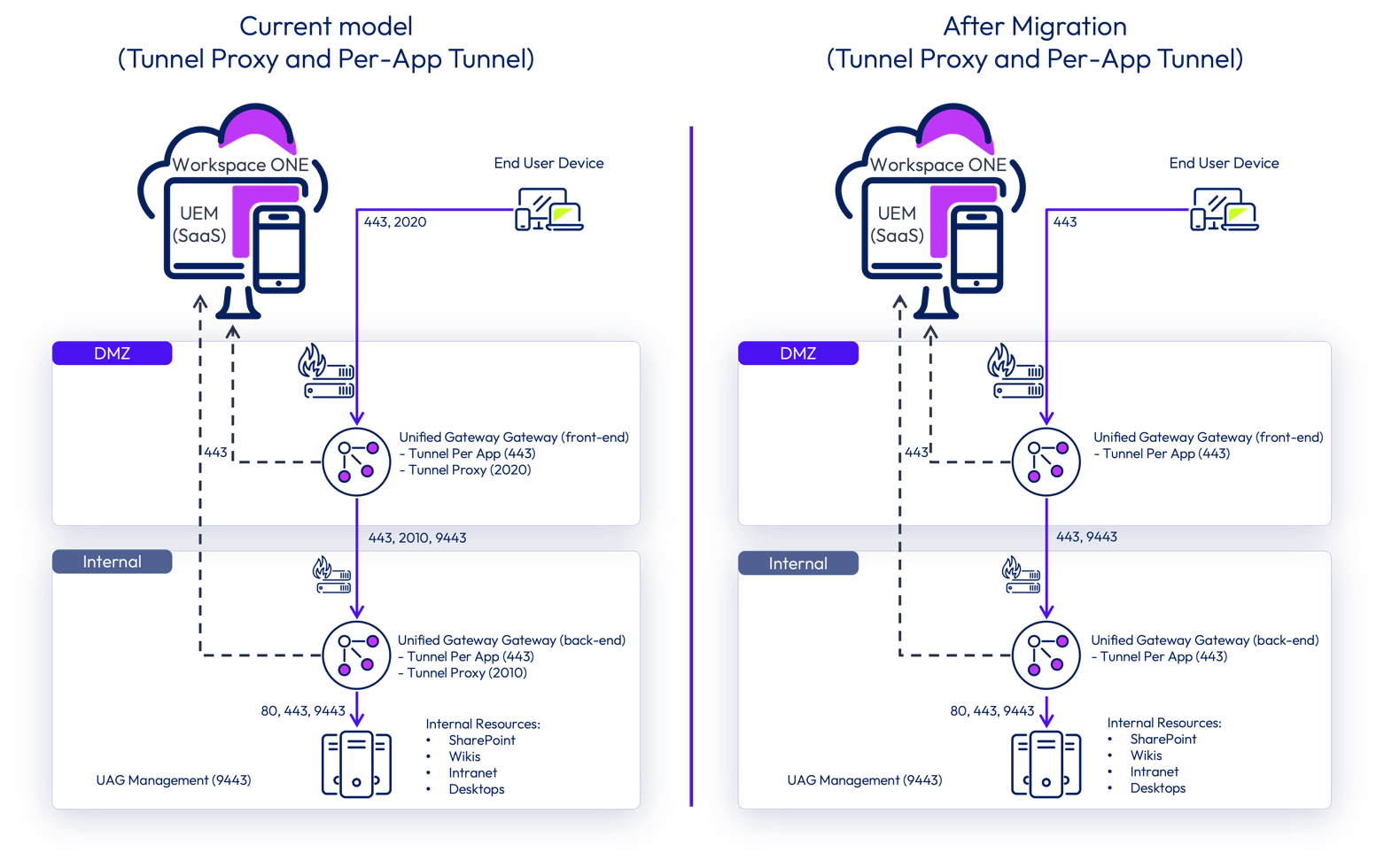
The current model requires two open ports for Tunnel edge service in each appliance (basic versus cascade mode):
- Tunnel Proxy requires 2020 on front-end appliance and 2010 on the back-end appliance when deploying in cascade mode.
- Per-App Tunnel most likely configured on 443 or 8443 for the front-end appliance, also on the back-end appliance when using cascade mode deployment.
When you complete the migration steps, the only change to consider is from a network perspective. Only the Per-App Tunnel port must be open on the DMZ. Remove the firewall rules allowing access through TCP 2010 and 2020; they are no longer required.
Basic mode configuration
The following diagrams illustrate the architecture required by the current model versus how the architecture will look after the migration based on Tunnel basic mode configuration, which is a single Tunnel Gateway deployed on DMZ.
Cascade mode configuration
The next diagrams illustrate the same architecture comparison but now based on Tunnel cascade mode configuration. In cascade mode, traffic from the application on the device to the internal network flows through a front-end appliance deployed on DMZ, followed by another tunnel gateway deployed on the Internal Network.
Architecture benefits
The consolidation of all use cases under a single Tunnel service brings some additional benefits:
- Reduces the number of non-standard ports opened on DMZ.
- When deployment Tunnel with Unified Access Gateway:
- Enables the use of Unified Access Gateway High Availability component to load balance Tunnel traffic on port 443.
- Enables the use of multiple edge services (Web Reverse Proxy, Content Gateway, Secure Email Gateway) on the same appliance using a single port (443).
Migration
The following steps help you to perform the required changes in Workspace ONE UEM for SDK-based apps to start using Per-App Tunnel features and deactivate the Tunnel Proxy.
Obtaining App Tunnel URLs for Tunnel Proxy
Before you begin, make sure that Tunnel Proxy is deployed in your Workspace ONE UEM environment. Take note of all App Tunnel URLs that are defined for Tunnel Proxy and configured under SDK Security Policies in the Workspace ONE UEM Console.
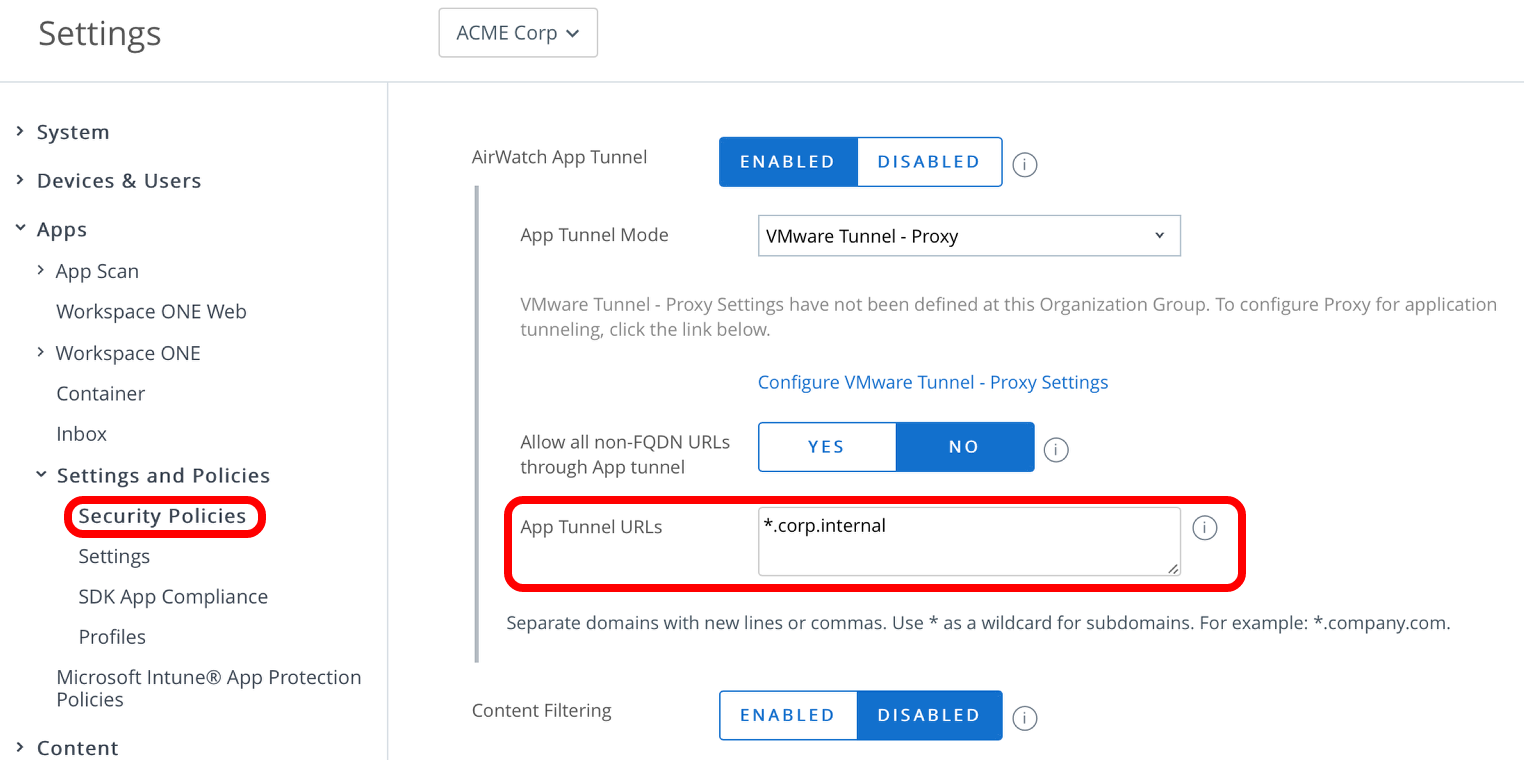
Tunnel SDK will no longer look for the URLs based on the Security Policy configuration. Instead, you will configure the URLs under Device Traffic Rules.
Configuring device traffic rules based on App Tunnel URLs
You must migrate the App Tunnel URLs used by Tunnel Proxy to device traffic rules and assign them to the applications that leverage the Workspace ONE SDK.
Client authentication
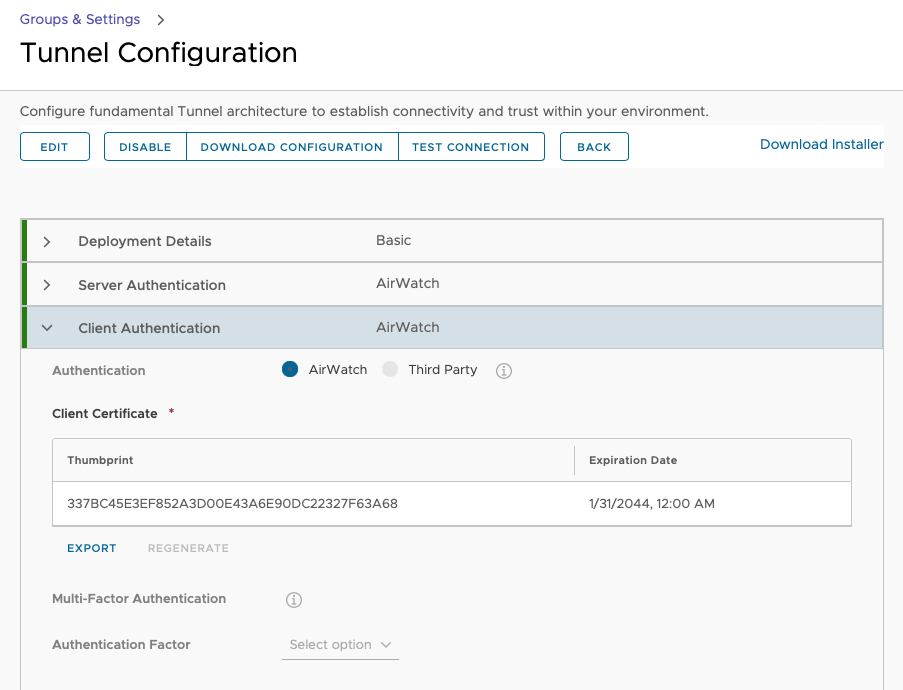
Ensure client authentication is configured to use AirWatch CA. Third-party SSL certificates are not supported on unmanaged devices with Tunnel SDK.
Device traffic rules
Adding Tunnel URLs to the device traffic rules allows SDK-based apps to identify which URLs to proxy the traffic through the Tunnel Service on Unified Access Gateway, leveraging app tunnelling.
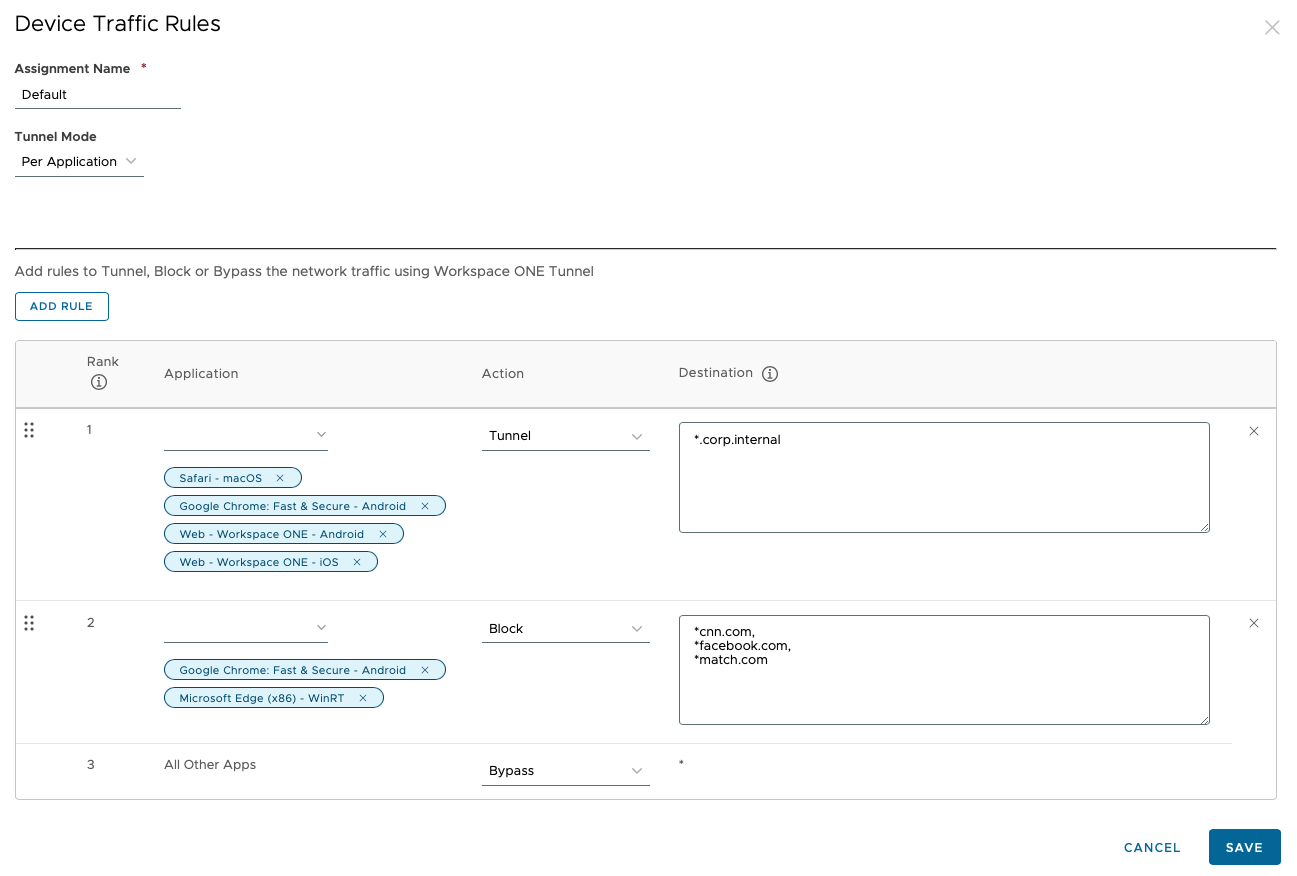
The example shown uses Workspace ONE Web because it is integrated with Workspace ONE SDK.
- Traffic to *.corp.internal is tunneled for the Remote Desktop and Workspace ONE Web applications on iOS and Android. However, the behavior will differ because both applications do not use Workspace ONE SDK.
- The Workspace ONE Web app has been added to the rule without assigning a VPN profile. This ensures that the Tunnel SDK dynamically detects the destination URL to securely tunnel traffic, while also enabling seamless functionality on unmanaged devices.
- If your Workspace ONE Web app has a VPN profile assigned, it will function exclusively on managed devices and require the Workspace ONE Tunnel app to securely route traffic.
- If you click Save at this point, it will not migrate the SDK-based apps from tunnel proxy to app tunnelling.
Deactivating Tunnel Proxy in Workspace ONE UEM
After you have completed the required device traffic rules configuration, the next step is to switch off the Tunnel Proxy component for the SDK-based apps on Workspace ONE UEM console.
Set App Tunnel Mode to Workspace ONE Tunnel
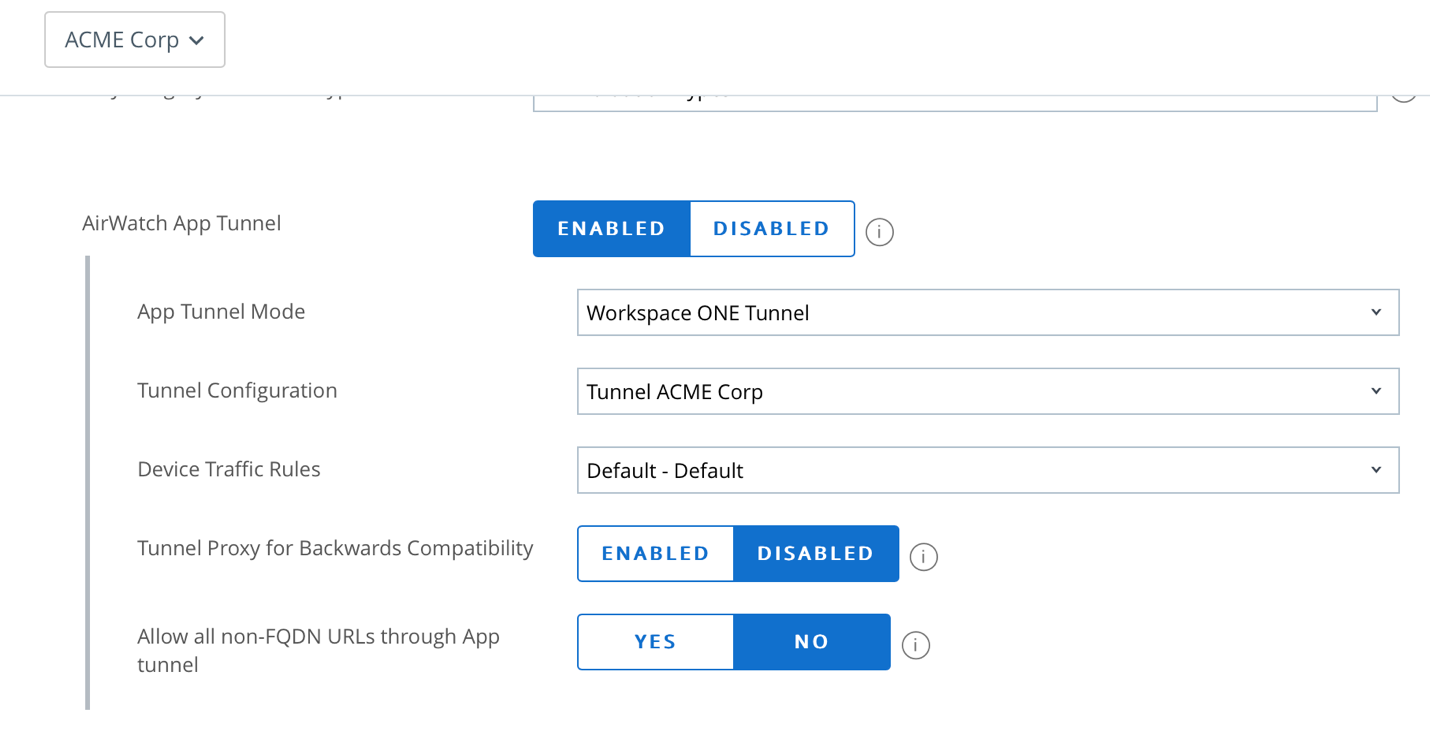
- Return to the SDK Security Policies configuration and change the App Tunnel Mode to Workspace ONE Tunnel.
- Save the configuration.
Switching the configuration tells Workspace ONE SDK which configuration the SDK-based apps will get next time the SDK checks in.
Note: In case the apps do not have the new Tunnel SDK module, you can enable the Tunnel Proxy for Backwards Compatibility option to fetch the existing proxy configuration.
Deactivate Tunnel Proxy
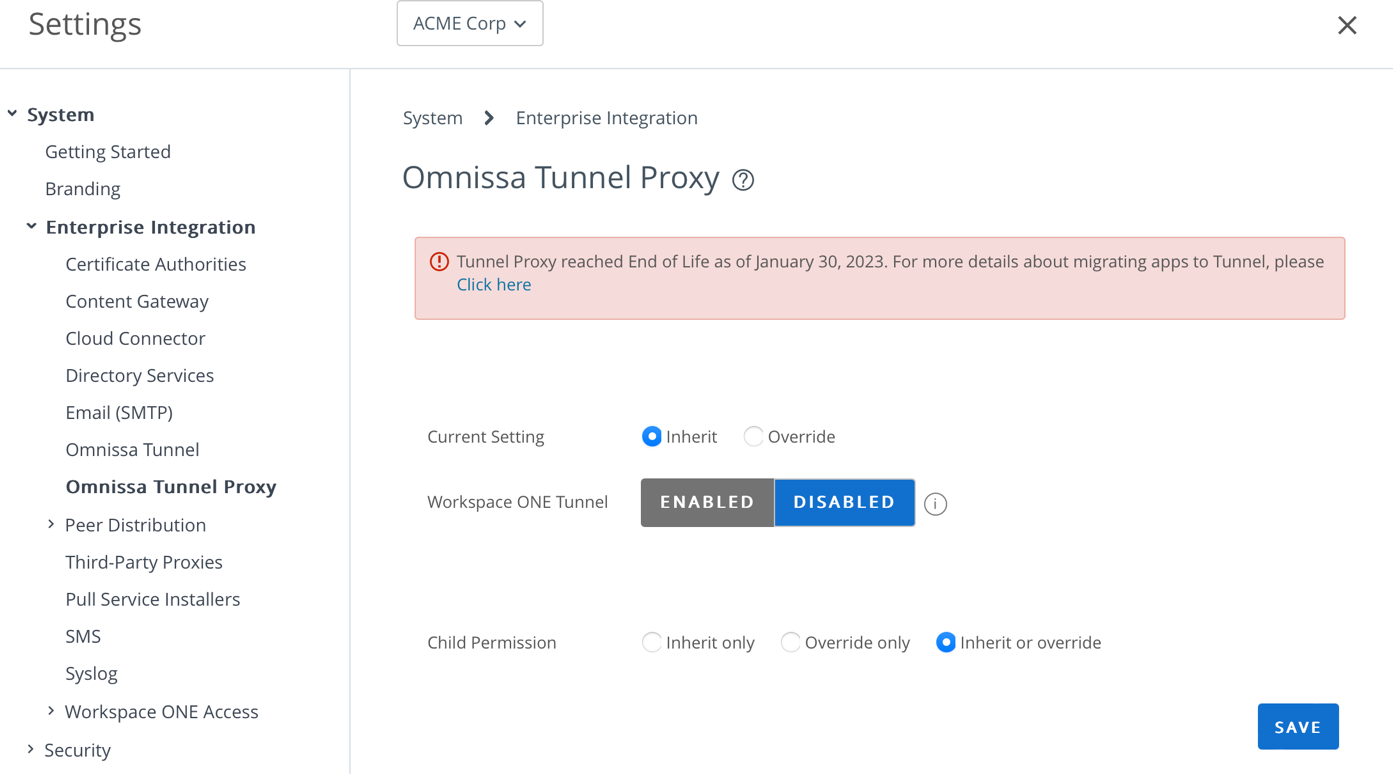
If your environment does not require backward compatibility with Tunnel Proxy, perform the following steps to deactivate the Tunnel Proxy configuration.
- Navigate to Enterprise Integration > Omnissa Tunnel Proxy.
- Select Disabled for Workspace ONE Tunnel.
- Click Save.
Deactivating App Tunnel Mode effectively transitions the apps to use Per-App Tunnel the next time the end-user relaunches the app. However, the Tunnel Proxy still runs as part of the Tunnel edge service on Unified Access Gateway.
The next topic discusses the options to deactivate Tunnel Proxy on Unified Access Gateway.
Deactivating Tunnel Proxy in Unified Access Gateway
When you deactivate the Tunnel Proxy configuration in the Workspace ONE UEM Console, it does not automatically shut down the Tunnel Proxy component on Unified Access Gateway until you restart the Tunnel edge service.
You can force a restart of the Tunnel edge service using one of the following options:
- Access vSphere Web Client and restart the Unified Access Gateway appliance.
- Open the Tunnel edge service settings using the Unified Access Gateway Admin UI and re-save the configuration.
As a result of the restart, Tunnel edge service communicates with Workspace ONE UEM through API. The service identifies that Tunnel Proxy is deactivated and does not retrieve configuration for the Tunnel Proxy component.
Make sure that you remove the firewall rules that were allowing TCP traffic through ports 2020/2010; they are no longer necessary. The SDK-based apps will communicate through the port configured for Per-App Tunnelling.
Summary and additional resources
This guide provided steps to migrate from legacy Tunnel Proxy to modern Per-App Tunnel.
By leveraging Per-App Tunnel, you can now enable users from managed and unmanaged devices to access internal applications from their mobile devices. IT administrators can leverage advanced features from Unified Access Gateway such as TLS Port Sharing. That eliminates the requirement to open non-standard ports on DMZ and increase TCO leveraging the High Availability component.
It also provides an extra layer of security to your corporate resources by ensuring that non-authorized apps and devices are unable to connect to your VPN, creating the beginnings of a Zero Trust model for application access.
Additional resources
For more information about Per-App tunneling, explore the Deploying Workspace ONE Tunnel and Configuring the Tunnel edge service tutorials on the Unified Access Gateway page, which provides step-by-step guidance to help you level-up in your Workspace ONE knowledge. You will find everything from beginner to advanced curated assets in the form of articles, videos, and labs.
Discover the new Tunnel standalone deployment method, now container-based for simplified deployment and management of the Tunnel Gateway. For a deeper dive, check out our blog post: "Omnissa’s New Standalone Tunnel Deployment Method: Embracing Modern Software Architecture"..
Additionally, you can check out the Workspace ONE and Horizon Reference Architecture which provides a framework and guidance for architecting an integrated digital workspace using Omnissa Workspace ONE and Omnissa Horizon.
Changelog
The following updates were made to this guide:
| Date | Description of changes |
| 2025/02/05 | Update architecture diagrams and requirements |
| 2024/07/11 | Update links |
| 2023/03/28 | Added link to the Omnissa Tunnel Proxy End of Support Life Announcement |
| 2020/04/16 | Guide was published |
About the author and contributors
This guide was written by:
- Andreano Lanusse, Omnissa alumni.
Feedback
Your feedback is valuable.
To comment on this paper, contact Technical Marketing at tech_content_feedback@omnissa.com.

