Omnissa Product Security
Introduction
Omnissa understands that the integrity of its cloud services and products (herein, “products”) is paramount to our customers. In recognition of the ever-evolving threat landscape and the potential risks to critical infrastructure, intellectual property, and sensitive information, Omnissa has proactively designed a set of comprehensive and stringent software security assurance programs and procedures for the sole purpose of identifying and mitigating potential product security risks during product planning, development, and delivery phases demonstrating the integrity of our products and mitigating potential vulnerabilities. These specialized programs and practices support the development of secure products, and solutions, and drive security awareness across the enterprise.
Purpose
This whitepaper provides an overview of how our commitment to building trust with our customers is present in every facet of our comprehensive, risk-based software assurance process and dedication to driving customer success and satisfaction through our trust programs.
This whitepaper focuses on the following topics of the Omnissa approach to product and information security:
- Designing our Security Development Lifecycle
- Protecting Product Source Code
- Providing Secure Product Support Services
Audience
This document is intended for current and prospective customers of Omnissa Workspace ONE® and Omnissa Horizon® Cloud Service software and services. It assumes at least intermediate knowledge of software development best practices and focuses on the policies, processes, and controls supporting the Omnissa software and security development lifecycle.
Note: You can find the definitions for acronyms used in this document in: Acronyms used in this Whitepaper for it and other Workspace ONE and Horizon Cloud related terms.
Product Security Development Lifecycle
The Omnissa Software Product Lifecycle (SDLC) includes the framework, governance, and set of executive checkpoint reviews, tools, artifacts, and guidance that enables Omnissa to help ensure business readiness during product availability and throughout the product lifecycle. Central to the framework is an integrated and predictable approach to product and process cross-functional planning, release/program management, measurement, risk management, and decision-making at each phase of the product lifecycle.
The Omnissa Security Development Lifecycle (SDL) is a set of processes, tools, and practices that Omnissa uses to reduce the likelihood that security vulnerabilities are introduced into and persist in Omnissa products and cloud services.
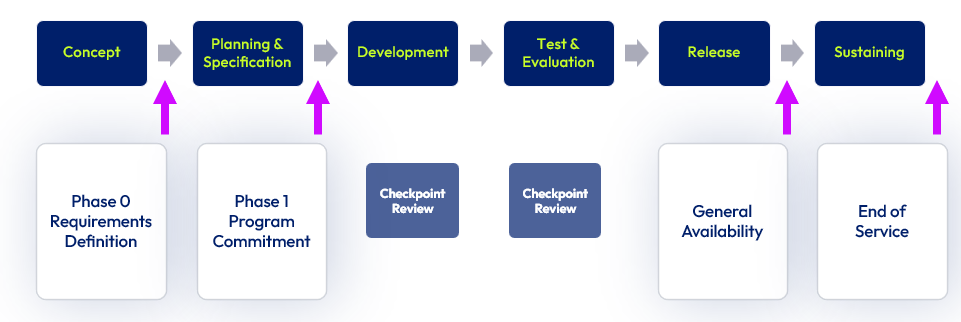
Figure 1: Enterprise Product Lifecycle Management Workflow
Building Security into Omnissa Products and Practices
Omnissa has established programs and practices that identify and mitigate security risks throughout a designed software development process. Through these activities, Omnissa delivers secure products and solutions for its customers.
Based on industry-recognized best practices and established standards, combined with trusted industry consultants and participants, our programs and practices focus on:
- Building secure software.
- Protecting intellectual property (IP) related to software products.
- Managing software security supply chain risks.
- Managing technology partner and ecosystem risks.
- Delivering secure product support.
Product Security
The Omnissa Product Security group develops and drives software security initiatives across our R&D organizations to reduce and mitigate software security risks. Their goals and practices are to oversee a product development process utilizing a comprehensive approach to assist with the planning, development, and delivery of secure products. Product Security plays a pivotal role in identifying, addressing, and responding to security threats and vulnerabilities to help ensure security for our customers. The teams and efforts described in this section represent our commitment to promoting a security mindset culture to foster positive cross-functional collaboration with a strong emphasis on security.
- Security Engineering: The Security Engineering team focuses on building secure products and solutions from the ground up. They work closely with the product development teams to integrate security best practices into the entire software development lifecycle. This includes conducting threat modeling, performing code reviews, and implementing secure coding guidelines. By proactively addressing security concerns during the development process, Security Engineering helps minimize potential vulnerabilities in our offerings.
- Communications: The Communications team is responsible for transparently communicating security-related information to stakeholders, including customers, partners, and the cybersecurity community. In the event of a security incident, they ensure timely and accurate notifications and guidance on mitigations and fixes. Additionally, the Communications team maintains open channels for reporting security concerns and facilitates a coordinated response to emerging threats.
- Response: The Omnissa Security Response team handles the incident response (IR) process in case of high-risk vulnerabilities. They are well-versed in handling security concerns efficiently and effectively, coordinating with internal teams and external industry organizations as required. The Response team follows established protocols to investigate, contain threats, and implement remediation plans to restore the security and integrity of affected systems.
- Compliance: Omnissa has a mature security certification program to drive critical products through targeted security certifications such as Common Criteria, FIPS 140-2, and DISA STIG.
- Security Evangelism: Omnissa has developed a program to raise security awareness and competency within the broader Omnissa R&D community through formal and informal training.
Omnissa establishes a robust security ecosystem by integrating Security Engineering, Communications, and Response functions to proactively protect its products and customers. This integrated approach enables Omnissa to respond to security challenges swiftly and maintain transparent communication with stakeholders while continuously enhancing product security. Through these efforts, Omnissa reaffirms its commitment to building and sustaining trust with customers, helping to ensure that their data and operations remain safeguarded in the face of evolving cybersecurity threats.
Security Development Lifecycle Overview
The Omnissa SDL program is designed to identify and mitigate security risks during Omnissa software product planning and development phases. The development of our SDL has been heavily influenced by industry best practices and organizations such as SAFECode (Software Assurance Forum for Excellence in Code) and SAMM (Software Assurance Maturity Model).
SAMM and SAFECode are two prominent initiatives in the software security industry that aim to improve software security practices and help organizations enhance the security of their software development lifecycle.
Omnissa SDL is periodically assessed for its effectiveness at identifying risk, and new techniques are added to SDL activities as they are developed and mature.
The program is supported by a security engineering team that performs security design reviews and thorough security testing.
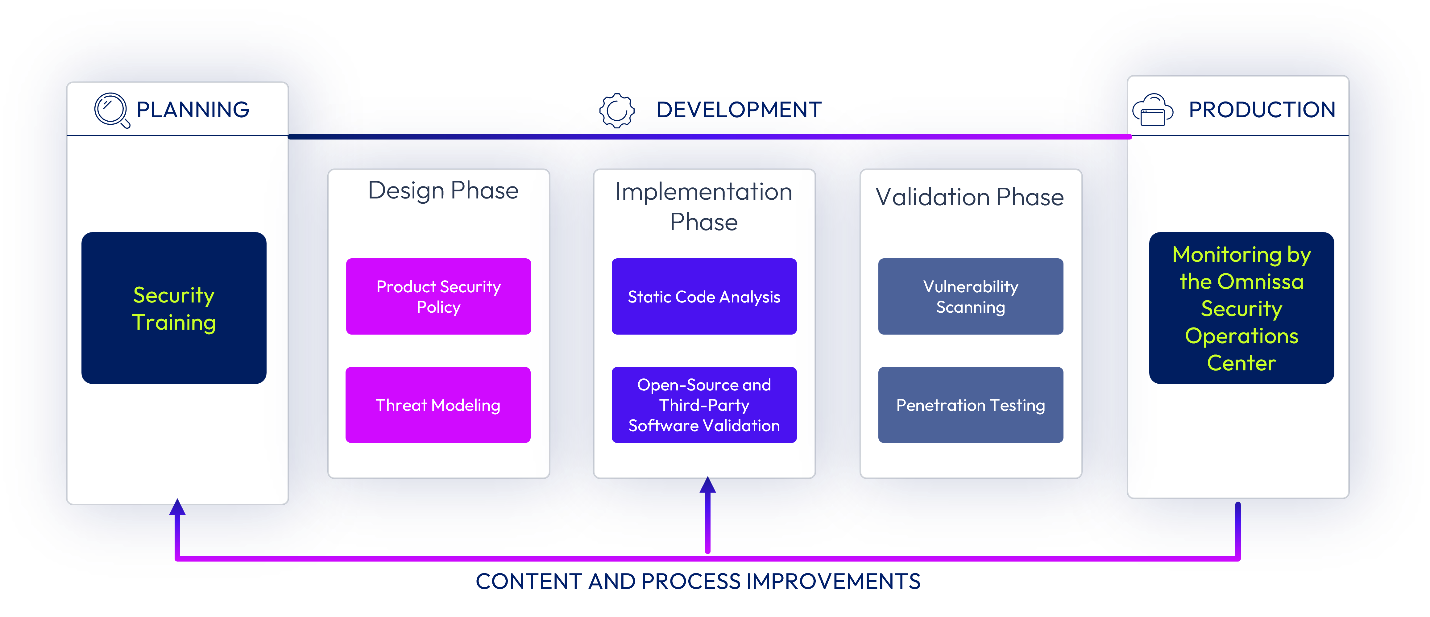
Figure 2: Omnissa Security Development Lifecycle
Current Omnissa SDL activities include:
- Security Training: Omnissa maintains role-based technology-specific product security and privacy training curricula in our central learning management system. It also provides recommendations and pointers to external security-focused training.
- Security Planning: SDL planning early in the development lifecycle forms the basis for the later Security Review activity when a product's security profile is evaluated at development milestones.
- Threat Modeling: This activity identifies security flaws and incorrect design assumptions present in the architecture of a product.
- Open-Source Software and Third-Party Software (OSSTPS) Validation: This activity highlights OSS/TP software components with known vulnerabilities for mitigation before being included in a product release.
- Static Code Analysis: Also known as Static Application Security Testing (SAST), this activity uses automated tools to detect implantation defects and security flaws in code.
- Vulnerability Scanning: This activity uses automated tools to detect security vulnerabilities in running systems.
- Penetration Testing: This activity attempts to circumvent security controls and uncover implementation weaknesses.
- Security Review: This activity collects and examines the results of all prior activities.
The Omnissa Product Security group owns the definition and practice of SDL processes. The SDL is the secure software development methodology used to help our product development groups identify and mitigate security issues early in the lifecycle before release.
The SDL's end-to-end set of lifecycle processes aims to help product development groups achieve these goals:
- Reduce their component's risk profile and attack surface.
- Identify and remediate costly security-related design flaws early in the development process before the bulk of coding has taken place.
- Discover and remediate security vulnerabilities before their broad availability.
- Educate teams on security issues and security best practices.
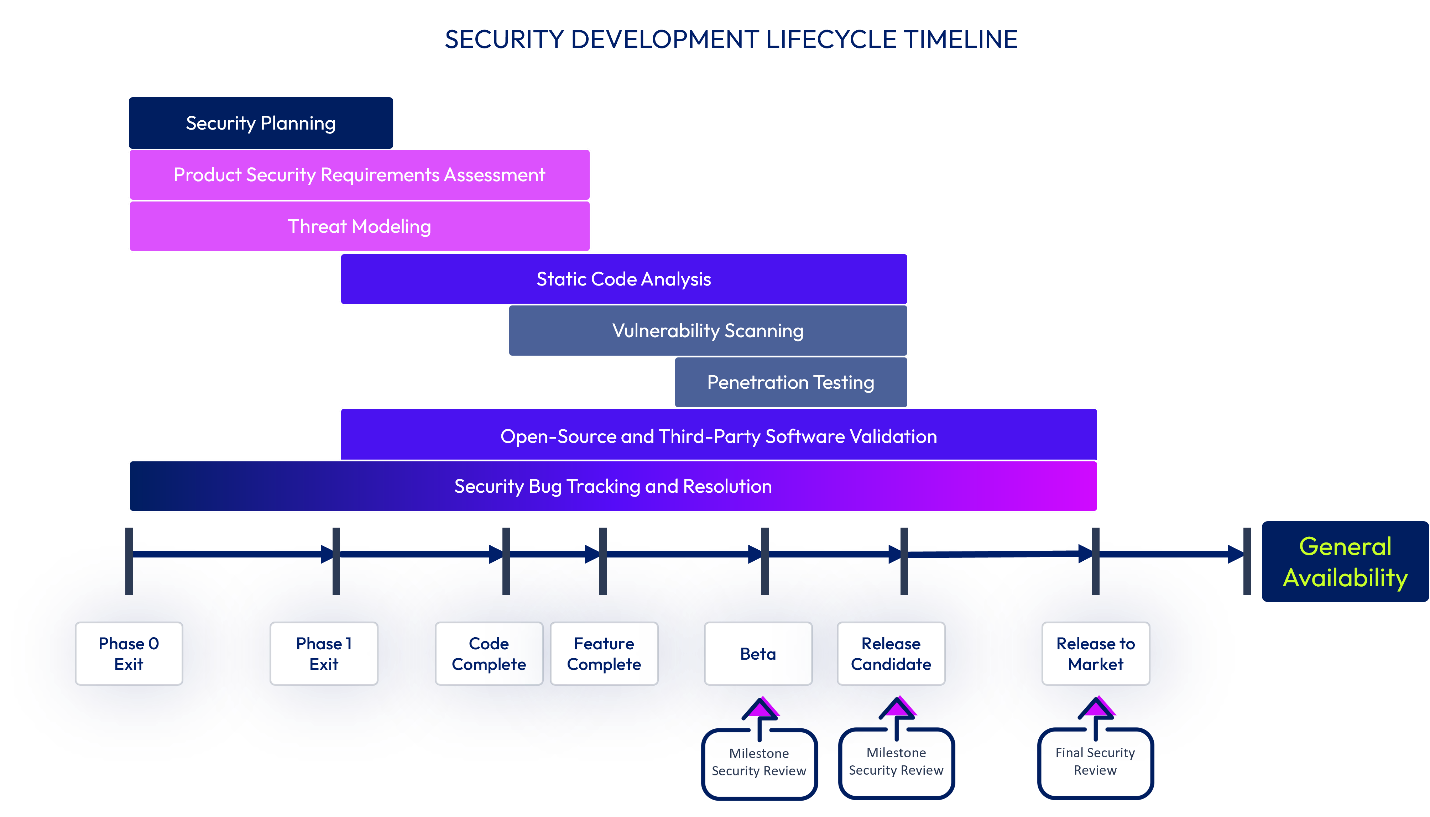
Figure 3: Timeline of SDL activities and product release milestones
The SDL processes include these activity phases: Planning, Design, Implementation, Validation, Security Review, and Production.
Planning
During this phase, the development team documents its security plan (strategy, risks, initial schedule, and so on) for the release, utilizing the Security Development Lifecycle workflow.
As part of our abiding commitment to helping ensure support around security early in the development process, we offer courses for managers, developers, and quality engineers in:
- Security concepts
- Security design and testing
- Secure coding techniques for specific languages
- Various security tools
Design
During this phase, the development team utilizes the Omnissa product security requirements to identify and remediate security issues in Omnissa products before release.
Additionally, the development team formally develops a threat model that identifies potential security flaws and incorrect design assumptions present in the architecture of the application or component. Threat modeling occurs early in the development process and thus allows adequate time for teams to remediate any design-related security issues.
Implementation
During this phase, the development team utilizes SAST and Software Composition Analysis (SCA) to detect defects, including security flaws, in third-party software components.
Validation
During this phase, the development team employs automated Vulnerability Scanning processes to identify security vulnerabilities in computing systems running in a network to determine the specific ways in which systems can be threatened and/or exploited.
Security Review
The Security Review establishes whether the software has undergone the required SDL activities adequately to identify security risks and address these risks deeming the software suitable for release to customers.
While the data that the Security Review evaluates is monitored throughout the entire security development lifecycle of the software, formal Security Reviews occur before the Beta, Release Candidate (RC), and Release to Market (RTM) milestones.
Production
When an Omnissa product has reached the general availability milestone, it enters the production stage of its lifecycle and remains in production until it reaches the end-of-life milestone.
Protecting Product Source Code
Product source code managed by R&D follows processes designed to safeguard the integrity of our product-related intellectual property while providing engineers access to source code required to develop and maintain products.
Code Integrity
Code integrity is the trustworthiness and reliability of software code throughout its lifecycle. Code Integrity helps to ensure that the code remains unchanged and unaltered from its original, intended state, protecting it from unauthorized modifications, tampering, or insertion of malicious code.
The following controls allow code integrity problems to be identified and remediated promptly.
Source Code Management
Omnissa uses Source Code Control Management or Version Control to protect the security and integrity of written, developed, tested, and evaluated code. Source control covers code creation, modifications, deletion, and incorporation of the code into more significant parts. Audit controls within the source control system automatically track what changes have been made, who made them, when a change was made, and other consequences of those changes. The product source code is stored on centrally managed servers in a secure area and protected behind a network firewall.
Code Signing
Omnissa requires code to be signed using cryptographic signatures to verify the authenticity and integrity of software code. This helps to ensure that the code has not been tampered with or altered since it was signed by the original author or publisher.
Access Controls
Omnissa enforces Access Controls and Privileges to restrict access to code repositories and to help ensure only authorized employees can view or make changes, thereby reducing the risk of unauthorized modifications. Access to source code is controlled by network access protocols on a per-user basis through user permissions and roles.
Monitoring
Omnissa implements Monitoring and Logging mechanisms that allow code maintainers and administrators to detect suspicious activities that may indicate code tampering or unauthorized access.
Secure Delivery
Several procedures are necessary for Omnissa to maintain security when distributing any on-premises software to a customer's site. For a valid delivery, the product received must correspond precisely to the product master copy without tampering with or substitution of a false version. The delivery procedures help ensure that the integrity and authenticity of the product are maintained and verifiable by the customer and Omnissa after delivery has been completed. The product is delivered via our websites by electronic distribution. The end user is supplied with the product, documentation, and license.
Issue Remediation
Customers report security issues to the Omnissa Product Security group by submitting a support request to Omnissa Customer Service. When a problem is encountered with normal product operations. Product issues are also reported, captured, and filed through our global Customer Service team. Issue details are captured and entered in our issue/bug tracking systems to track security-related bugs.
Any bug discovered during product development, design change, testing, or by a customer must be triaged, and documented, and a solution offered before the bug report can be closed. These bugs include suspected and/or confirmed security flaws.
Providing Secure Product Support Services
The delivery of secure products and services is of utmost importance to Omnissa, which is why we implement industry best practices for securing customer data across all our support service teams, including global support, vulnerability management, and incident response.
Global Customer Service
The Omnissa Global Customer Service organization is global and part of standard practice and engages the necessary global resources when needed. Omnissa has established a variety of processes and procedures to protect data while working to resolve customer support issues, including role-based access, data handling procedures, logging, and monitoring of customer consoles and production systems.
Vulnerability Management
Omnissa has a Vulnerability Management program backed by approved and tested policies and procedures. Vulnerability scans are performed regularly on Omnissa developed products and cloud services.
System and application owners must address critical and high vulnerabilities with a corrective action plan. The vulnerability severity drives the level of responsiveness requirements. Risk analysis and acceptance tests are performed on vulnerabilities to confirm the vulnerability and to determine the appropriate means of addressing the vulnerability.
Penetration Testing
Omnissa uses trained and experienced internal security engineering staff to periodically perform penetration testing of critical systems and applications. Results from penetration testing are handled in the same manner as vulnerabilities, as discussed above. Executive summaries of penetration tests performed against Workspace ONE and Horizon Cloud Service can be provided upon request.
Omnissa uses white box testing to achieve more meaningful test results. White box testing means all the source code will be made available to the testers. The white box method enables the security engineer performing the penetration test to have source code available to assist with penetration testing. This results in a more robust set of tests because the penetration testers can achieve deeper and broader results since they spend less time breaking into targeted assets. In alignment with our compliance initiatives, internal and external network pen tests and web app pen tests are performed at least annually (once per calendar year) on Workspace ONE and Horizon Cloud Service.
Security Evangelism
The Security Evangelism team's long-term goal is to increase software security awareness and competency within the Omnissa R&D community. This allows the SDL process to scale effectively. The team uses several programs to achieve this:
- An R&D-wide, role-based, technology-specific online software security training program.
- Participation as speakers at Omnissa annual offsite conferences.
- Software security challenges, competitions, and hackathons focused on Omnissa products.
- Borathons/Hackathons are one of the many innovation programs at Omnissa where employees can build upon their creative roots and work collaboratively on new features, workflows, and proof of concepts.
Third-Party Vendor Risk Management
With the global expansion of the software industry, security concerns have increased that a product or service could be compromised by malicious code introduced during product development or maintenance. Technological innovation and changes in sourcing and supply chain strategies have made software supply chain security a global challenge. Threats ranging from risks associated with using third-party code and open-source components to IP theft have dramatized the vulnerability of this new risk domain. Omnissa actively engages in proactive measures to minimize the occurrence of these risks and has several initiatives to address the security of our supply chain.
Managing Supply Chain Risk
Omnissa uses a Third-Party Risk Management program that focuses on secure sourcing and software integration relating to building solutions. It includes the use of an approved vendor list and open-source software reviews prior to use. Each vendor Omnissa engages undergoes an extensive onboarding process that includes both security and privacy reviews. Supplier agreements require that providers comply with applicable laws, security, and privacy obligations.
Our R&D team includes specific resources responsible for testing, updating, and reviewing the open-source material used in the product. Management of third-party software in Omnissa products adheres to our Secure Development Policy which includes Open-Source/Third-Party Security Scanning also known as Software Composition Analysis (SCA).
Any software deemed “Security Critical” must be appropriately vetted, tested, and maintained. The respective development team incorporating third-party software in their product(s) and services is responsible for the support and fixing of defects and security vulnerabilities, whether they get such support from a vendor contract, or perform this function themselves.
Summary and Additional Resources
Omnissa strives to build products that its customers trust in the most critical operations of their enterprises. To promote this, Omnissa has established oversight procedures that identify and mitigate potential product security risks during development and has instituted programs and practices that drive software security initiatives and awareness across the enterprise.
Our focus on product security strategy and our security development lifecycle ensures our ability to continuously protect sensitive customer information from product vulnerabilities.
In closing, this document represents our innovative, cooperative approach to security for our end user computing software products and solutions.
Additional Resources
For more information about the cloud security of Omnissa services, you can explore the following resources:
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 28 August 2024 | Document branding updated to Omnissa |
About the Author and Contributors
The following people contributed their knowledge and assistance with this document:
- Andrea Smith, Sr. Program Manager, Customer Security Assurance
- Morey Straus, Sr. Manager, Product Security
- Andrew Osborn, Staff Technical Marketing Architect, Technical Marketing
Feedback
Your feedback is valuable.
To comment on this paper, contact Omnissa Technical Marketing at tech_content_feedback@omnissa.com.

