Mobile threat report for U.S. public sector
Executive Summary
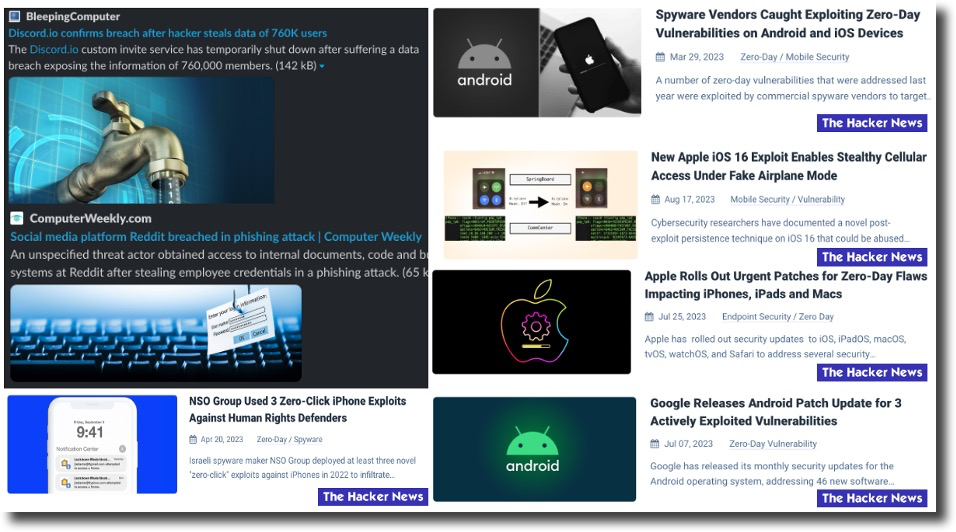
Figure 1: 2023 Mobile-related headlines on vulnerabilities, malicious techniques/tactics & effects
The pandemic moved zero trust from a conceptual framework to something that both public and private sectors needed ‘yesterday’! The old perimeter-based ‘castle-and-moat’ security model was finally starting to show its age, and we're seeing the transition becoming more prevalent in 2023. There were several factors contributing to this paradigm shift, but it was largely by such previous high-profile cases like the Colonial Pipeline REvil ransomware gang and SolarWinds breach attacks on US agencies—including parts of the Pentagon, the Department of Homeland Security, the State Department, the Department of Energy, the National Nuclear Security Admin, and the Treasury but also numerous Defense Industrial Base (DIB) and State, Local & Education (SLED) entities—that were the driving force in doing so.
But today, those attacks and their predecessors are simply the tip of the iceberg regarding malware and malicious actors’ Tactics, Techniques & Procedures (TTPs) and the diverse array of systems they are going after, which includes less thought of areas; things like Cloud, IoT, and ICS but also a steady dose of mobile-enabled efforts. As highlighted in the headlines in Figure 1, these bulletins and notices from companies, related to vulnerabilities and their associated threats to establish the Cyber Kill Chain (CKC), only continue to accelerate into 2023. These mobile-enabled Advanced Persistent Threats (APTs) require advanced techniques to defend, deny, disrupt, and contain data exfiltration from the end-user’s device, the network, or the cloud.
Undoubtedly, zero trust (ZT) is trendy and yes, now as overused as ‘cloud’ with lots of vendors hopping on the bandwagon and relabeling their existing security products as being “zero trust/capable/ready.” So, wading through some marketing-hyped terms will be inevitable, but rest assured in 2023, you will continue to see that it’s both real and achievable to begin deployment of ZT and these concepts can be further reviewed for background on Omnissa’s Tech Zone. These will undoubtedly help provide takeoff and better define the emphasis of the term ‘zero-trust’ from what it truly is, a framework and intrinsic cybersecurity paradigm and architecture, and how best to comply, fund, and make the end-users of both traditional and mobile-enabled endpoints lives better for it!
Although we will most certainly address Zero Trust within this whitepaper, as it is intrinsically tied to the subject, we will focus deeper into the drivers and metrics for both Public Sector organizations within the U.S., but also other security and privacy-focused industries can additionally leverage this whitepaper to serve as guidance as well, such as other global Public Sector institutions, could all glean details from within this report, in order to make informed decisions regarding the threat that exists for their own mobile environment.
Moreover, this document provides details and metrics to establish a baseline on how the threat to mobile-enabled devices faces mounting increases in attacks to the security and privacy of user data; not just to the general public, but more specifically to US Public Sector Government-Furnished Equipment (GFE) / Govt-Owned Personally-Enabled (GOPE A.K.A. COPE) or BYOD-Approved Device(s) (BYODAD). In this whitepaper, we will analyze these metrics in several key areas and provide takeaways on how best to protect those devices.
The ‘Key Findings Methodology’ from 2022>2023 data and trends in this report are based on findings from our Mobile Threat Defense (MTD) partner Lookout’s ever-growing mobile dataset of security telemetry, which is built on graph-based machine intelligence that analyzes data globally from more than 210 million devices, 175 million apps, and ingests four million URLs daily. Additional details are pulled from various sources, including Verizon’s and Mobile Security Index (MSI) Data Breach Investigation Report (DBIR) 2021/22 reports.
U.S. Government background on mobile security
In 2020, the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-207, Zero Trust Architecture (ZTA) was released to provide agencies with guidance and detailed recommendations to improve their security posture using the core principles of ZTA. While in 2021, after several high-profile malicious campaigns and attacks against both civilian and government targets, the Executive Order (EO) 14028 “Improving the Nation’s Cybersecurity” was scripted with requirements for all Federal agencies to develop a plan to implement ZTA in an effort to modernize and strengthen cybersecurity standards and detection.

Figure 2: Gov’t guidance / framework for mobile threats & protection techniques
Although Zero Trust is the new framework for overall guidance on achieving secure user and agent interaction with data, NIST, CISA, and MITRE provide more specific guidance and reference architectures for deploying and monitoring secure mobile frameworks. This guidance, which can be leveraged both nationally and internationally, will be discussed briefly in this document as related to the threat metrics and details regarding real-world tactics that are defined explicating within MITRE Matrices for Mobile Tactics, Techniques & Procedures (TTPs) used by adversaries involving device access and network-based effects:

Figure 3: MITRE ATT&CK matrices for mobile covering TTPs for both AndroidOS & iOS
Compliance & guidance for mobile
One of the key institutes and thought leaders used by both U.S. Federal, State & Local/Education (SLED) is based on the NIST / NCCoE Special Publications (SP) guidance & collaboration consortium & NRA and FARS clause language related to SP 800-207 compliance but more importantly are the implementation guides from other associated institutions such as the DoD and DHS / CISA Technical Reference Architecture and Pillars which reflect the requirements for enhanced endpoint protection that include mobile and the threats presented to each of the domains of mobile including Device, Network, Application & Phishing that are detailed in the MITRE matrices above.
These fundamental security elements are also augmented by additional privacy concerns that are intangible to security, but equally as concerning to those that often process on the device or through it in-Transit data, such as Personally Identifiable Information (PII), Sensitive Personal Information (SPI), Financial Services & Insurance industries (FSI or Protected Health Information (PHI). Assurance that the apps they are operating on or through the mobile web browsers are secure and not leaking or being siphoned is critical to meeting compliance. Organizations such as Open Web Application Security Project (OWASP) provide web-based best practices in the form of their Top 10 and Mobile Application Security Testing Guide (MASTG) as well.
Data privacy and protection laws are now dictated by governments around the world, as well as industries as a whole. Even if an organization isn’t obligated to comply with specific regulations, government initiatives can drive the private sector to evaluate its own cybersecurity standards or in combination, be required duly by both agencies and their respective ‘industrial base’ that is associated with them (e.g., Defense / Health / Finance). These regulations being privacy-related have real-world mobile compliance factors based on susceptibility to intercepts Over-the-Air (OTA), such as in a Machine-in-the-Middle (MitM) attack or through on-device Spyware and Surveillanceware apps.
Due to the sensitivity of citizens and the user base in which these regulated domains incorporate, Data privacy regulations typically dictate how personal data is used and stored. These regulations are increasing in scale and scope, such as under the UN Conference on Trade & Development (UNCTAD), which provides a collection of 128 countries with forms of legislation worldwide; here are some other specific examples:
- California Consumer Privacy Act (CCPA) (although state-based, several other U.S. entities using it as a potential blueprint)
- General Data Protection Regulation (GDPR) for the European Union (EU) member nations
- Protection of the liability of user data via Cybersecurity Framework from HITRUST Alliance & Cybersecurity CSF for Global Financial Intuitions
Gov't & regulated industries are lucrative targets
Cybersecurity risk isn’t just an issue for IT and security teams. As more breaches occur, finance and compliance teams are increasingly concerned about what cyber risk means to them. These other elements are both driving Zero Trust and thusly, mobile security as a means to protect these assets that are ‘fiduciary in nature’ and can be assigned a value in these circumstances, and the effects of an attempted or successful breach can be used in evaluation examples:
- The rising cost of cyber-attacks > Cybercrime is estimated to have surpassed $6T in 2021 and is expected to exceed $10T by 2025 <and> Average cost of a data breach is ~= $4.24M per incident causing many organizations to take out hefty Cyber Insurance to mitigate against those potential attacks and successful breaches or face fines and disciplinary actions.
- North Korean state-sponsored actors alone stole an estimated $395 million worth of cryptocurrency last year as part of seven intrusions against virtual currency exchanges and investment firms, up (3) from 2020 (although fewer than the 2018 high of 10 @ $522 million total).
- Mobile-based attacks too have their own set of economic factors that include data exfiltration from apps or stored data, and credentials for privilege escalation to backdoors through Ent VPN client tunnels. These can be used as beachheads to get to more lucrative data assets or on their own. We’ll cover aspects of mobile fiduciary impacts a little later.
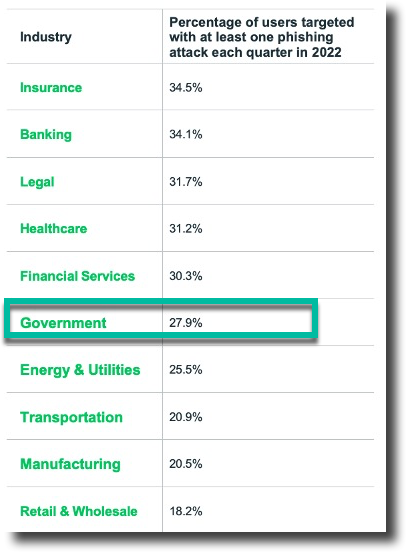
Figure 4: Lookout Industry target analysis
Unsurprisingly, some of the most regulated industries are also frequently targeted. This is likely due to the immense amounts of sensitive personally identifiable information (PII), intellectual property, or financial data that they own. And with a single successful mobile phishing attack, a threat actor could get access to an organization’s infrastructure and sensitive data.
And with increased risk comes increased rewards or costs depending on what side of the fence you're sitting. Risk can be measured in several ways. With how valuable data has become, cyber, compliance, and financial risk are now fully intertwined as data breaches involving sensitive user data seem to be occurring every day. Using the Factor Analysis of Information Risk (FAIR) model of risk analysis, we estimate that the maximum potential financial impact of successful mobile phishing on an organization of 5,000 employees is almost $4,000,000. More on the breakdown of phishing-related expenses are discussed in the next section.
Mobile Top Threats
Agency and Enterprise staff should expect to be able to access the data they need to be productive from any device, location, or network. With that being the case, more apps, data, devices, and networks are being introduced into complex enterprise ecosystems that make planning a security strategy more difficult every day. Attackers are using this to their advantage by targeting employees on mobile devices and apps to steal credentials and gain initial access to an organization’s enterprise infrastructure.
Although there are cases of rogue Wi-Fi Access Points in the form of ‘Pineapples’ or through other cellular network intercepts, they are becoming more challenging for those actors based on access policies being driven on the devices for only connecting to known/protected APs and restricting contact through open, unsecure and unvetted Wi-Fi, etc.
As for compromises due to jailbroken or rooted iOS / Android devices, most Gov't & Regulated institutions or enterprises incorporate strict policy enforcement through Unified Endpoint Management (UEM) solutions, such as Omnissa’s Workspace ONE UEM, in which those controls are placed and enforced on the devices and end-users prior to being allowed access to any such enterprise resource or data.
This section dives into the top threats to mobile devices.
Mobile phishing: Tip of the spear
Thus ‘phishing or spear-phishing’, including those outside of email (e.g., SMSing) have become the preferred tactic of the malicious actor towards Gov't & Enterprise users. Because so many avenues are made available for fake messaging, email filters are no longer adequate to serve as the only line of defense. And true to the security doctrine of Defense-in-Depth (DiD), additional assets like Mobile Threat Defense that provide state-of-the-art Phishing & Content Protection (PCP) detection and protection are required as represented in Figure 5:

Figure 5: Lookout PCP Report, 2023 - 85% of mobile phishing attacks happen outside email
Regarding a comparison of ‘Enterprise to Government’, Figure 6 shows the number of unique URLs accessed by users on enterprise devices from 2020-2022 in an aggregate view of each year. The percentage of enterprise users globally who are interacting with more than (>1) and up to (6) malicious links is increasing each year. This is likely due to attackers getting better at creating convincing phishing campaigns that target both enterprise and personal channels as well as a blurrier line between personal and work usage on mobile devices.
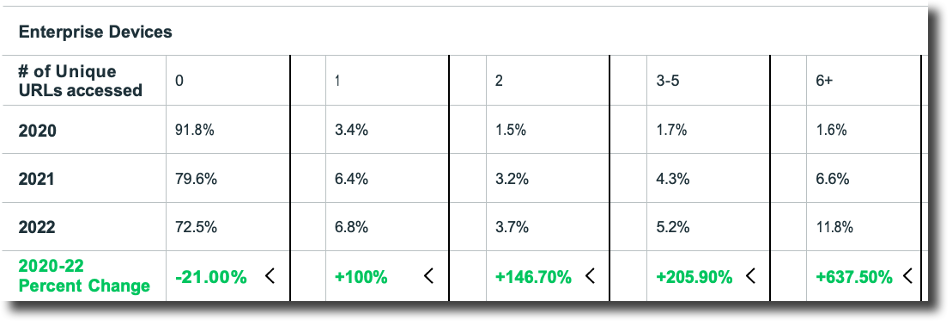
Figure 6: Number of unique URLs accessed by users on enterprise devices
The numbers that stand out the most are the significant increases over time of users on enterprise devices tapping on malicious links. These targeted enterprise-level attacks intend to steal corporate credentials, which the attacker will then try to use across hundreds of known enterprise cloud-based platforms like AWS, Google, Salesforce, or Slack.
Also, they could try to log in to a variety of VPN tunnels, which would give the intruder broad access to the organization’s network resources. Once they’re in, an attacker can do anything from a quick-hitting data exfil to a long-term surveillance campaign where they implement a backdoor to be able to enter and exit the victim’s infrastructure as they please before executing an advanced attack like ransomware.
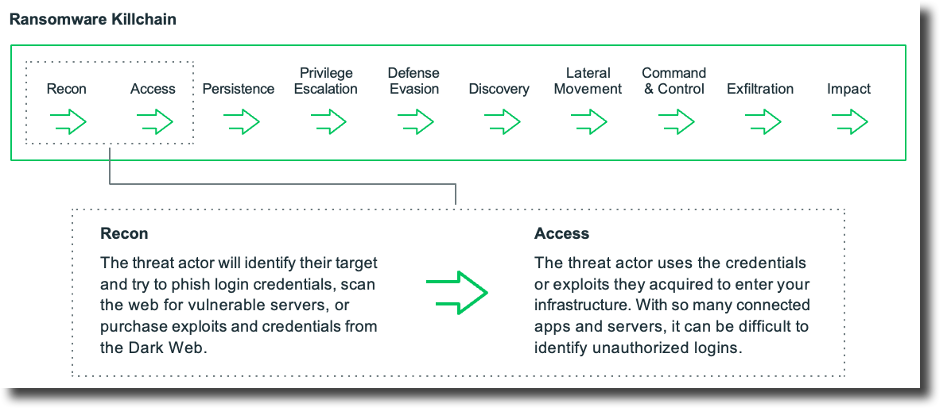
Figure 7: Ransomware killchain
Mobile phishing threat metrics for government
Similar to those stats collected for enterprises, The Lookout Threat Team recently collected specific U.S. Public Sector-based data regarding agent Phishing encounters (PCP) in relation to the same scope of ‘threat URL encounter rates’ from 1Q21 > 4Q22 but with specific Public Sector based data points and are represented in Figure 8. Within those encounter rates are a steady average data set, which can be seen at ~6.75% quarter over quarter for two years. Users are encountering malicious links or phishing URLs for credential harvesting, at a rate of as many as 1 in 20. This trend only once goes down at the end of the cycle, but not before two quarters before it saw heavy campaigns, swelling that number to 1 in 10. In any case, they are on the rise overall even though they had a drop-in activity at the end of the year.
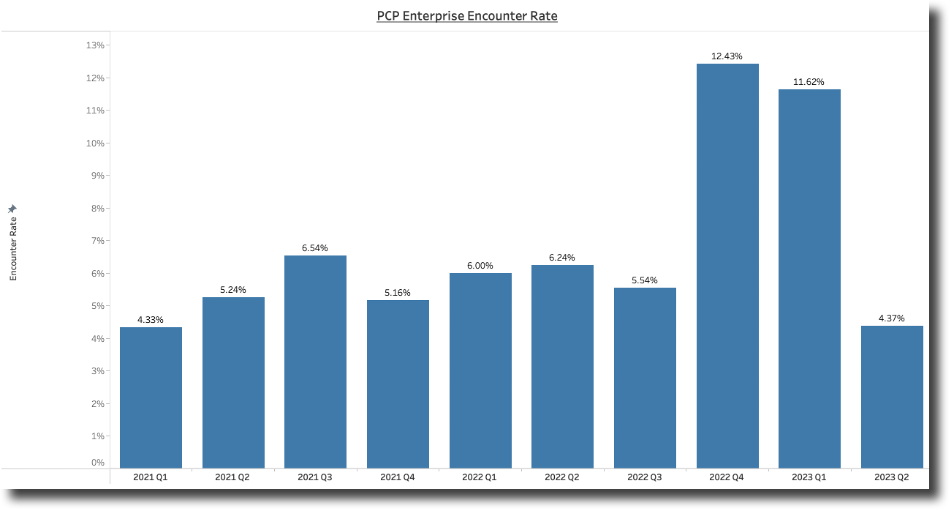
Figure 8: Combined percent of agents on Gov't devices accessing malicious & credential harvesting phishing URLs per quarter
Business impacts of mobile phishing
Cybersecurity risk isn’t just an issue for IT and security teams. As more breaches occur, finance and compliance teams are increasingly concerned about what cyber risk means to them.
Potential financial repercussions
As the risk of mobile phishing increases every year, so does the potential impact on an organization’s bottom line. Below is a calculated estimation of the potential financial risk due to mobile phishing attacks on an annual basis.
To calculate this estimation, we can consider (3) key factors extracted from the Lookout Security Graph highlighted in Figure 8 over a two-year period from January 1st, 2021, thru December 31, 2022:
- Average number of phishing attempts per device,
- Likelihood of a phishing attack getting through, and
- Average impact per event
The Threat Capability estimate, which is the likelihood of an attack reaching the target, is based on research that about 20% of people will open a phishing message, and about 67% of them will click the link and enter their credentials on the malicious webpage. Multiplying these numbers together gives a threat capability of 13.34%. This is confirmed by the National Council of Identity Theft Protection who indicates that it’s possible that as many as 13.4% of agents would submit their passwords to a phishing website.
This would indicate an organization with 5,000 devices could potentially face 2,501 phishing attacks each year. It should be noted that without proper security controls, these attacks could all have a direct impact.
Finally, the impact numbers are pulled from the Ponemon 2021 Cost of Phishing report, which surveyed 591 IT and IT security practitioners. Of those surveyed, the average organization size was 9,576 employees and the average costs incurred directly from phishing, ransomware, business email compromise or credential loss was $10,545,645. The average costs of business disruptions were extrapolated to be ~ $4,280,572. Adding those two numbers together and dividing by 9,576 employees shows that the average cost = $1,550 / per incident.
Application risk management for mobile
Most iOS and Android apps are not malicious but may violate security or regulatory requirements by exhibiting unsafe behaviors or containing vulnerabilities. Omnissa's Workspace ONE Mobile Threat Defense also provides comprehensive visibility into these app risks within an organization’s mobile fleet, enabling administrators to monitor and set policies against apps that are at risk of violating internal and regulatory requirements.
If we were to put apps on a spectrum in terms of risk, there would be harmless apps on one end and malicious apps on the other. What remains between them is a gray area of apps that are not outright malware but violate the security posture of the organization or specific industry/regional regulations like GDPR.
One of the prevailing trends is collecting data in lieu of payment. Lookout’s Threat Team are now seeing a proliferation of free apps because user data has become the new currency. Developers of these grey apps (and the companies they work for) are selling this harvested to data brokers, ad networks, and other third-party vendors – leaving your staff and potentially your organization’s data at risk.
Understanding app risks for mobile
Organizations have (3) main categories of risk ranging from ‘No sensitive behaviors’ to ‘Some’ to the worst, ‘Malicious Behavior’. Within this set of app risk categories, enterprises need to be aware of and take steps to manage, including but not limited to these other criteria:
- External threats that come from criminals, competitors, and countries through modified or hidden code.
- Vulnerabilities within apps and devices, where these defects, flaws, or weaknesses in software or hardware (as in the case of firmware/processor or memory or a network controller) can be exploited by malicious actors.
- User behaviors and the way they’ve potentially configured their devices (depending on the device type and policy allowances), could allow apps to access sensitive information about users and organizations.
In the realm of malicious actions for credential harvesting, there are (4) main ways in which a malicious actor can compromise user credentials and data in a mobile app:
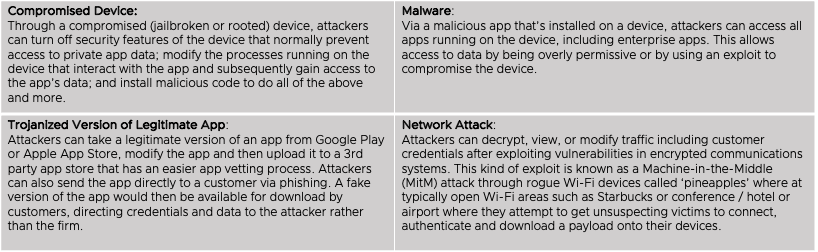
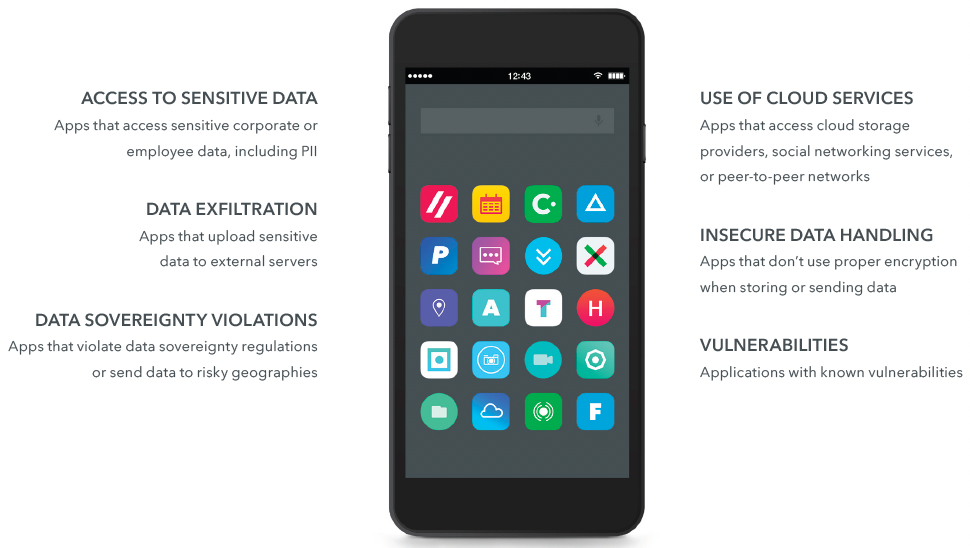
Figure 9: Sensitive mobile app behaviors
Mobile threats, app vulnerabilities, user behaviors, and configurations all create risks, such as loss of sensitive data, leading to breaches of regulations and compliance rules which are highlighted graphically in Figure 9. Any of which could harm your users, organization, and your brand. This leads us to the next set of use cases regarding app development (AppDev) and those that comply with good security standards. For example, those who abide by or practice the framework examples, those in the aforementioned OWASP Mobile Application Security framework, and those who simply don’t take the appropriate time to properly incorporate good Cyber hygiene into their DevOps program, leaving gaps in those apps which can be taken advantage of by those external threats <or> from our next group, are required to provide legally collected data from its user base for potential government espionage.

Figure 10: Chinese Gov't backed firms required by law to comply
App behaviors and configuration risks
Unsafe app behaviors can lead to the leakage of enterprise data accessed by certain apps. Examples include apps that access sensitive enterprise data and public cloud-based storage services not under enterprise control and apps that access data with compliance requirements such as credit card numbers or personally identifiable information, and don’t have adequate protection for the use, transmission, and storage of that data. In the first 6 months of 2020, over 30,000 enterprise iOS devices in the metrics collection encountered sideloaded applications.
Apps within the mobile community, especially those within the Android ecosystem have had a linage of data collection, extraction, or even flat-out eavesdropping on both the end-user system for its local data and other apps residing on the device. Typically, this has been achieved by simple user compliance, known as T/Cs acceptance (Terms & Conditions). Most who download and accept these when installing an app like TikTok onto their device rarely, if ever bother to take the time to examine exactly what the app is requesting access to or is allowed to do, e.g., turn on microphone / camera / photo roll.
Across tens of millions of devices in which the Lookout Threat Team has access to aggregate around app threat metrics, 37% of apps access user location, 27% access local storage, 21% access the camera, 16% access the address book, 12% access text messages, and 5% access the microphone.
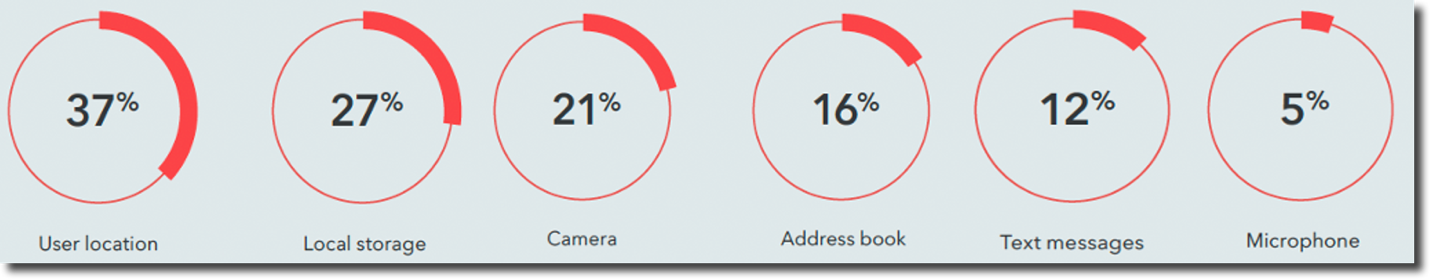
Figure 11: Apps with access to user data
Combined with this powerful access and new Chinese laws, it has introduced a new level of vulnerability for software and Apple and Samsung mobile device applications by Chinese-based AppDev firms, such as popular social media apps, or fitness wearables/trackers and other devices that can provide location and other data to the Chinese government.
With their implicit compliance now mandatory, the risk of user data, trends, and usage are most likely in the hands of the government and being processed in order to better provide their offensive capabilities in the cyberwarfare domain more accurate and damaging when and if used; this could take spear-phishing to a whole new level? However, TikTok is not alone when it comes to National Security concerns.
This is why in 2020 through 2023, governments including the U.S. federal and state levels began requiring the removal of the app on any GFE or GOPE-enabled device, where government data or apps would reside. However, we need to be careful not to over-index on that threat alone, as for the most part, we should remember that TikTok’s business model is essentially a company whose revenue comes from advertising, as are any of the social media giants, such as LinkedIn, X, Facebook, or Snapchat to name a few.
There are a lot of ad-based networks, and they all work the same way, tracking users across many different apps and websites. TikTok is just so much more visible because of its enormous popularity and user-base and the wealth of data it has at its disposal from such a large group of youth across the globe. Yet what makes it so dangerous goes back to its origins as a Chinese-backed state company which must comply with all data requests made of them.
As highlighted in Figure 10, Kaspersky and Huawei have been in the news for many years for similar reasons - too much information flowing into the hands of a potential adversary to the Western government’s users and their citizens' privacy and security. Two more to think about: Temu and Shein, which are at the top of shopping apps in the US and abroad and are among the most downloaded apps on both the Apple App Store as well as Google Play. And while they have slightly different business models, you can think of them as Chinese versions of an Amazon eRetailer, but the parent companies Pinduoduo & PDD Holdings have been known to have supported the use of spyware, embedded into other apps they developed and distributed discussed in the article below:
Additionally, recent discoveries about the popular Chinese e-commerce app Pinduoduo have proven that there can be outright malicious functionality hidden in apps developed by legitimate organizations. Pinduoduo was recently removed from Google Play after researchers discovered its off-store versions, which were predominantly used for the Chinese market, could exploit zero-day vulnerabilities and take over devices in various ways.
After the news came out about Pinduoduo, researchers from our partner’s Lookout Threat Lab, decided to take a look at Temu, which is another wildly popular e-commerce app developed by the same parent company. The Threat Lab found some code in Temu that was removed after the Pinduoduo discoveries were made.
Most alarmingly, versions 1.55.2 and before had a patching capability through a home-built framework known as “Manwe,” which is an unpacking and patching tool that was also found in the malicious versions of Pinduoduo.
Manwe could enable PDD holdings to patch the app on the device, rather than through the Apple App Store or Google Play Store. This is against app store policies, as it could enable the developer to push unauthorized code via updates to user devices.

Figure 12: APT43 (Kimsuky) – Apple Zombie
App threats
Malicious mobile apps can harm you in many different ways, including stealing information, physically damaging your device and monitoring a user’s or organization’s activities. Common ways apps can become unsafe include injecting malicious code into a legitimate app and asking for permissions that are beyond what the app needs to function. Many organizations think that by having Mobile Device Management (MDM) solution means they’re protected from app threats.
The reality is that users can easily install apps that are not approved by the App Store or the Google Play Store onto their phone. Prevalence of app threats in the 2nd quarter of 2020, 1 in 380 enterprise mobile devices within the metrics analysis collection encountered an app-based threat. These app threats include riskware, device hacking tools, spyware, surveillanceware, trojans, adware, and remote code execution. Some recent editions to this collection can be traced to nation-state operators, such as the (DPRK) where several malicious apps were used:
- Android surveillanceware family uploaded to Google Play’s testing enclave
- Uses stolen credentials to synchronize features to automatically install Apple Zombie to victims
- Targeted users in NATO-based countries, such as Turkey, United States, and South Korea
- Various application titles were used to hide the surveillanceware:
- i.e., KISA, Security, Security Plugin, NAVER, DAUM, Google Plugin
App threat metrics for government
In the past two years, Lookout has collected a volume of data metrics related to app threat and vulnerability encounter rates amongst Gov't customers. As can be seen in the charts, there is a great disparity between iOS and Android-based app threats and vulnerabilities for quarterly encounter rates, nearly 10x in any given quarter. This is still a legacy effect of the flexibility in development from a DevOps standpoint within the Android community, as well as downloading or hosting apps from off-Google Storefronts but has been improving over time. However, one other interesting note on those encounter rates for both app platforms is having a striking resemblance in increasing or decreasing rates per month almost mirroring one another, which could be attributed to active campaigns that were leveraging apps on either platform?
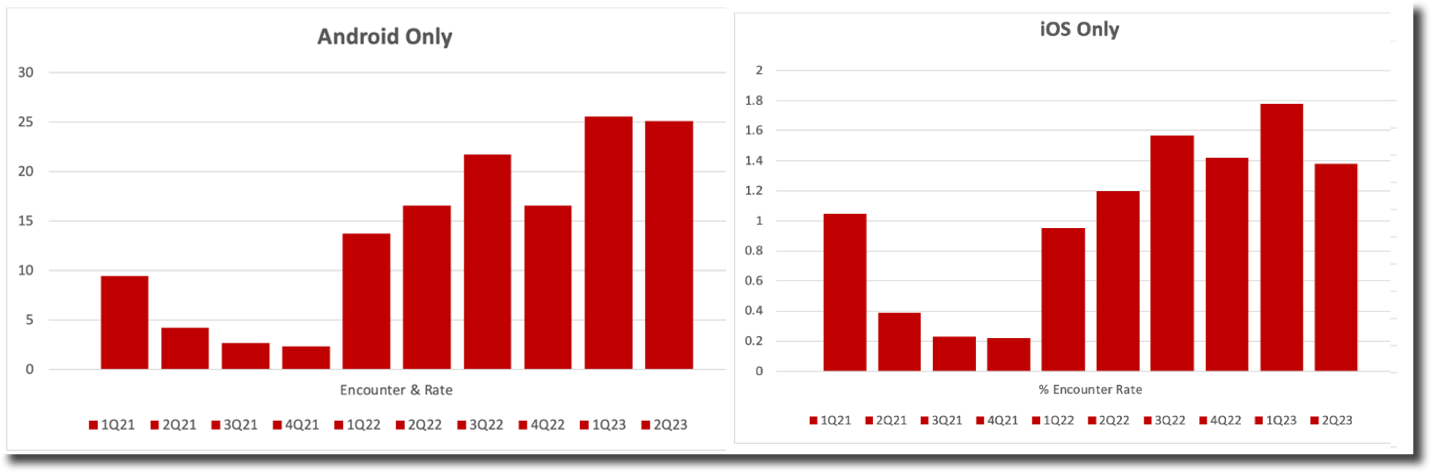
Figure 13: App threats & vulnerabilities quarterly encounter rates for each OS-type separately
Let’s look at another observation from metrics related to the Public Sector focused App Threats & Vulnerabilities Quarterly Encounter Rates. Figure 14 below shows a breakdown of the percent encounter rates for Public Sector customers based on App Threat Devices by Classification (excluding the more prevalent riskware). Here you can see that over time several different techniques are employed by malicious actors to gain access or extraction of sensitive data from the enterprise or the device’s user themselves.
The most prevalent app threat classification by far in the Gov't realm is ‘Riskware’ including adware, spam, and chargeware comprised over 65% of the encounter rates over the span.
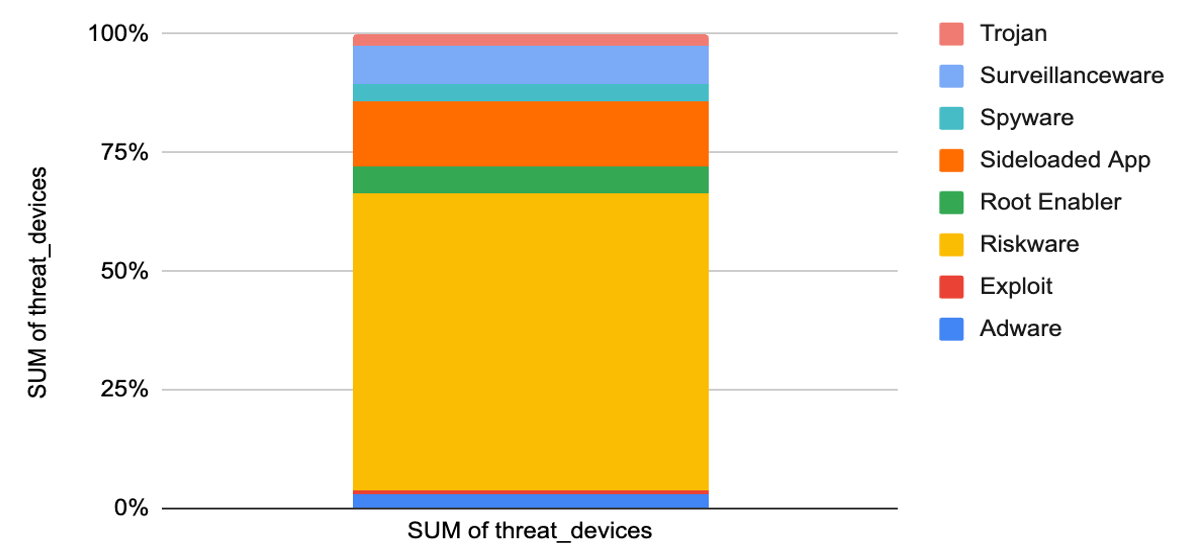
Figure 14: Combined OS - app threats by classification over 2-year span
Outside of riskware, three other different techniques are seen often throughout the 2-year span, Adware / Root Enabler & Trojan; although, a total of (8) different major categories of app threats were seen, confirming the adversarial flexibility, including the last quarter where spyware is exclusively being leveraged.
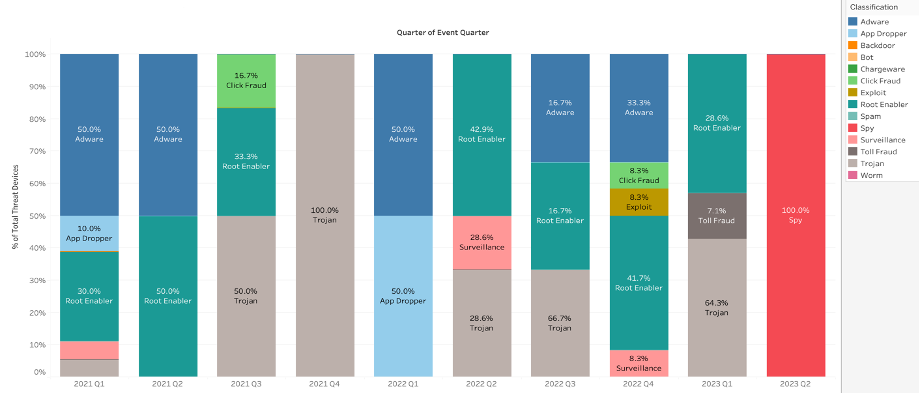
Figure 15: App threat devices by classification (excluding riskware)
Figure 15 provides insight into a six-month view of encounter rates showing the changes between the different methodologies being tracked for Public Sector institutions. Although it can be assumed that ‘Riskware’ would dominate the quarters, there are surges in different sub-areas of risks and vulnerabilities regarding app threats, including OS vulnerabilities for 3Q22 as the leader encounter rate of threat risk, typically phishing is and continues to be the prevalent way Public Sector devices are attacked.
However, as can be correlated from the data, IT staff resting on the assumption that malicious actors will only utilize a small spectrum of tools or that other previously un-tasked elements are not relevant would present a danger and enhanced risk as can be seen from several of the other quarters whereby different methods and rates do fluctuate. The simple lesson that can be extracted is that Public Sector agencies and enterprises must stay up with risk mitigation and take all categories seriously, even if the trend seemingly suggests that one area is more important than another; the winds of change can bring a new threat factor to the forefront!
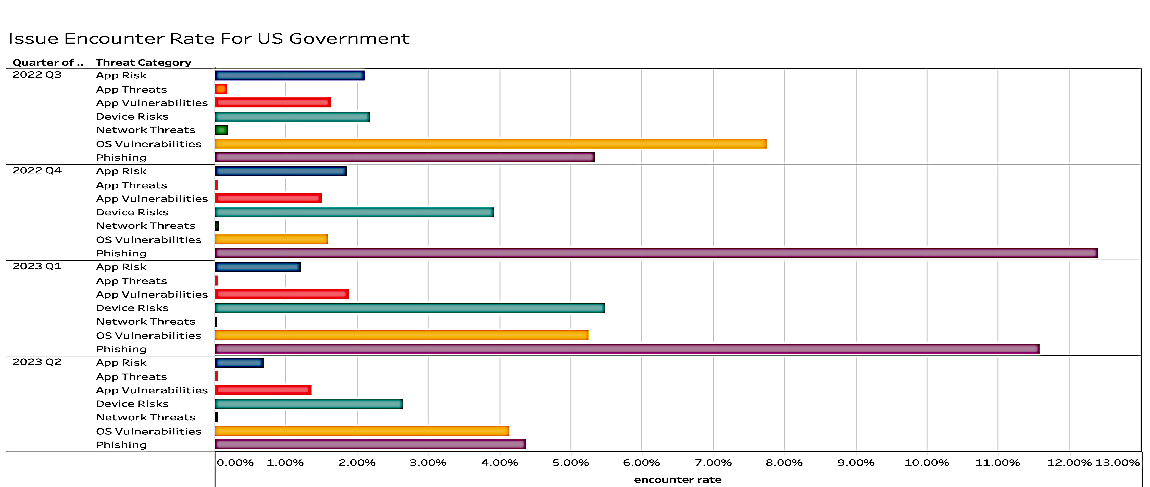
Figure 16: App threat devices by classification (excluding riskware)
Summary of Mobile Threats for Government
Regardless of whether agents use enterprise-issued, personal devices or those based on Gov't-Owned Personally-Enabled, every iOS, iPadOS, and Android device needs to be protected against mobile phishing. Now more than ever, empowering agents and end-users to use mobile devices is a critical piece of boosting productivity. But with one in eight agency devices and over half of personal devices being exposed to at least one mobile phishing attack every quarter and 85% coming from outside agency E-Mail, agency decision makers need to be aware of the risks they pose to your users and data. It’s critical to take adequate steps to treat the mobile device like other endpoints worth protecting in your environment.
Protect against mobile phishing and secure data content
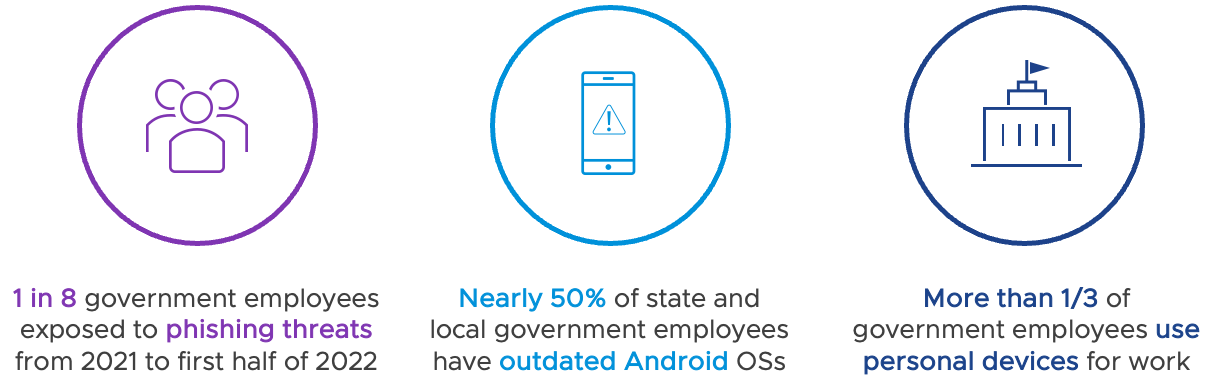
Figure 17: Rise in mobile phishing credential theft targeting U.S. Pub Sector – U.S. Govt Threat Report by Lookout, 2023
The significant increase in phishing attacks on both corporate and personal mobile devices through 2022 as well as the hefty potential financial risk show that continuously modernizing security is critical to both the technical and business side of any organization. IT and security teams need to think about how they can adapt their own strategies to be able to dynamically visualize, detect, and minimize data risks posed by these devices. We anticipate that many private organizations will take the lead from government initiatives to ensure that mobile device security and detection and response capabilities are extended to include mobile devices.
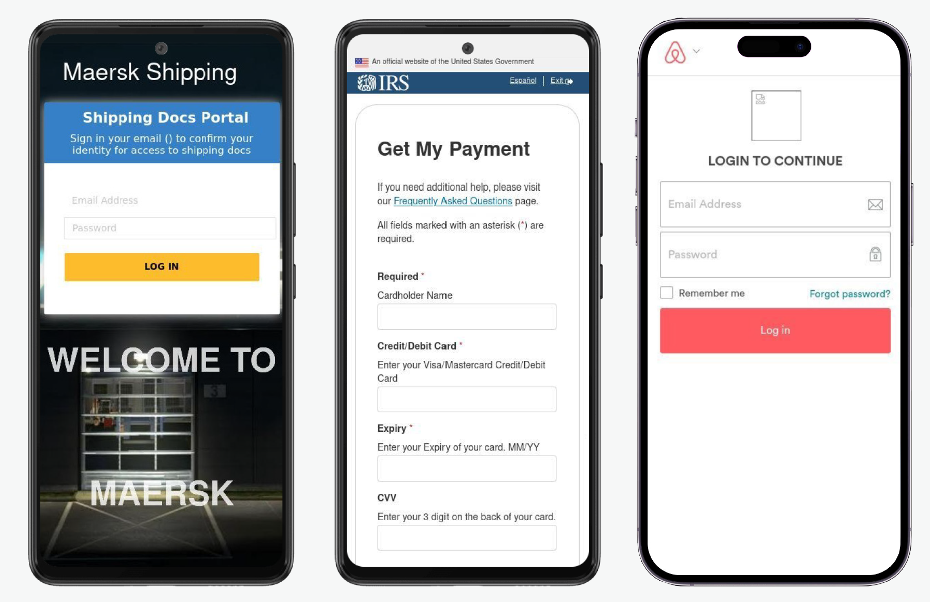
Figure 18: Phishing is real (These pages are fake)
Credential compromise is frequently the first step in an attack as it grants the malicious actor direct access to the target’s infrastructure. We have even observed attackers taking advantage of MFA fatigue explicitly on mobile devices — which allows the attacker to not only compromise an employee’s credentials but allows them to compromise systems that are protected with a password and MFA. Supplementing that with the ability to detect anomalous activity across all platforms, apps, and networks rounds out a holistic endpoint-to-cloud strategy necessary to protect enterprise data against today’s evolving threat landscape.
Prevalence of app vulnerabilities
Lookout researchers have performed many in-depth analyses on numerous popular Android and iOS productivity and business applications. We identified a diverse range of vulnerabilities with varying sophistication and impact. On the high-risk, high-sophistication end of the spectrum, we discovered flaws that would allow adversaries to compromise not only the information a user viewed in an app but also their cloud service account and all data tied to that account.
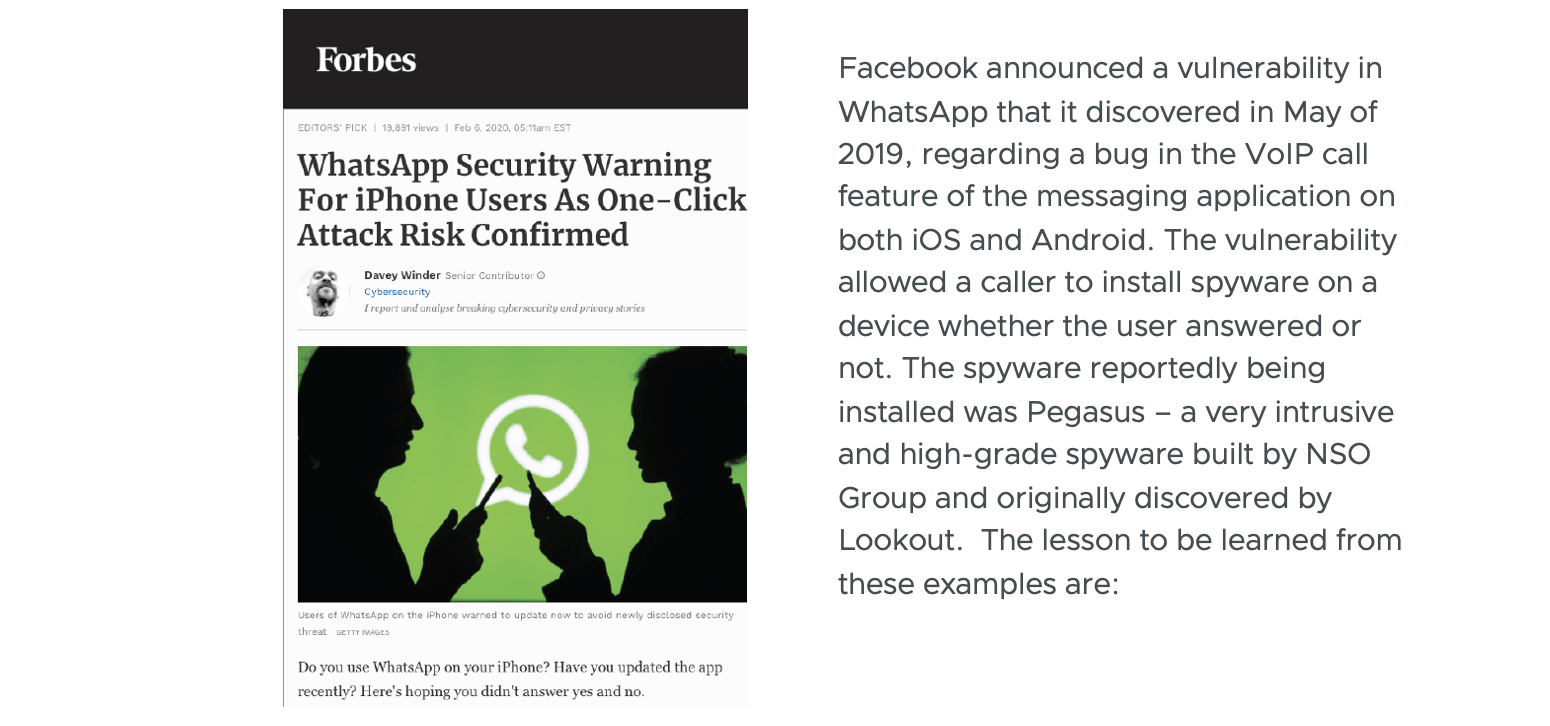
- Zero-day bugs will always be lurking in the wings which threat actors can leverage.
- There are always gaps in patching and deployment of fixes to them causing a window of exposure.
- Malicious actors are typically more than one step ahead of IT and DevOps, let alone end-users in discovering them and incorporating them into their tools.
- Dynamic protection from a Mobile Threat Defense, just as in the cases with traditional endpoint security agents are not a ‘nice to have’ but a requirement for both good cyber-hygiene as it is guidance within Zero Trust frameworks.
How does Omnissa’s Mobile Threat Defense mitigate these risks?
Risk is always in the eye of the beholder; an app like TikTok or WhatsApp or any other social media, gaming or shopping app may be deemed risky for one FedGov organization, whereas it may be perfectly tolerable to an Educational Institution. That’s why we do not give each app a risk score. Instead, we show the app’s capabilities in the context of an organization’s overall fleet of apps, allowing the admin to make simple, actionable decisions about them. When a risky app is found, the admin can blocklist that app directly from the console. However, blocklisting one-off apps each time does not scale, as apps may update to new versions as much as 10 times per year. Regardless of your policies, Omnissa has protection for all the Device, Network, Application & Phishing elements of these risks.
Key Enhancements with Workspace ONE Mobile Threat Defense
Let’s look at some of the key enhancements of Workspace ONE Mobile Threat Defense.
Phishing & Content Protection (PCP) built into Workspace ONE MTD
Workspace ONE Mobile Threat Defense helps address the risk of threat actors sidestepping security controls—including agency profiles on personal devices—by integrating PCP with the Workspace ONE platform. With MTD, customers will be better able to protect against potential phishing activity across email, SMS, general web content, messaging, and social apps. PCP is applied to all traffic, both external and internal, leveraging a unique integration with Workspace ONE Tunnel that is used to intercept the network URL traffic when clicked on the device and compare it with any malicious URLs identified within the Lookout Security Graph engine (LSGe).
However, Omnissa’s MTD PCP does not inspect the content or data packets itself, so users’ network traffic is not being redirected or tunneled when the VPN is configured in this mode, thus creating a better experience for end-users while providing security and privacy at the same time and minimizing device and agency configured network connection conflicts of previous industry MTD version.
Integration with Workspace ONE Intelligent Hub
By integrating mobile security protection into Hub, security becomes easier to deploy across devices. Hub-integrated protection addresses vulnerabilities, behaviors and configurations, and threats including malware, zero-day, and MitM attacks.
Workspace ONE Intelligent Hub integration can detect issues and notify users of remediation actions to take without the deployment of additional security applications to mobile devices as reflected in Figure 19. This integration is available via Workspace ONE Intelligent Hub enrolled and registered modes, simplifying the delivery of protection to both corporate and personal devices.
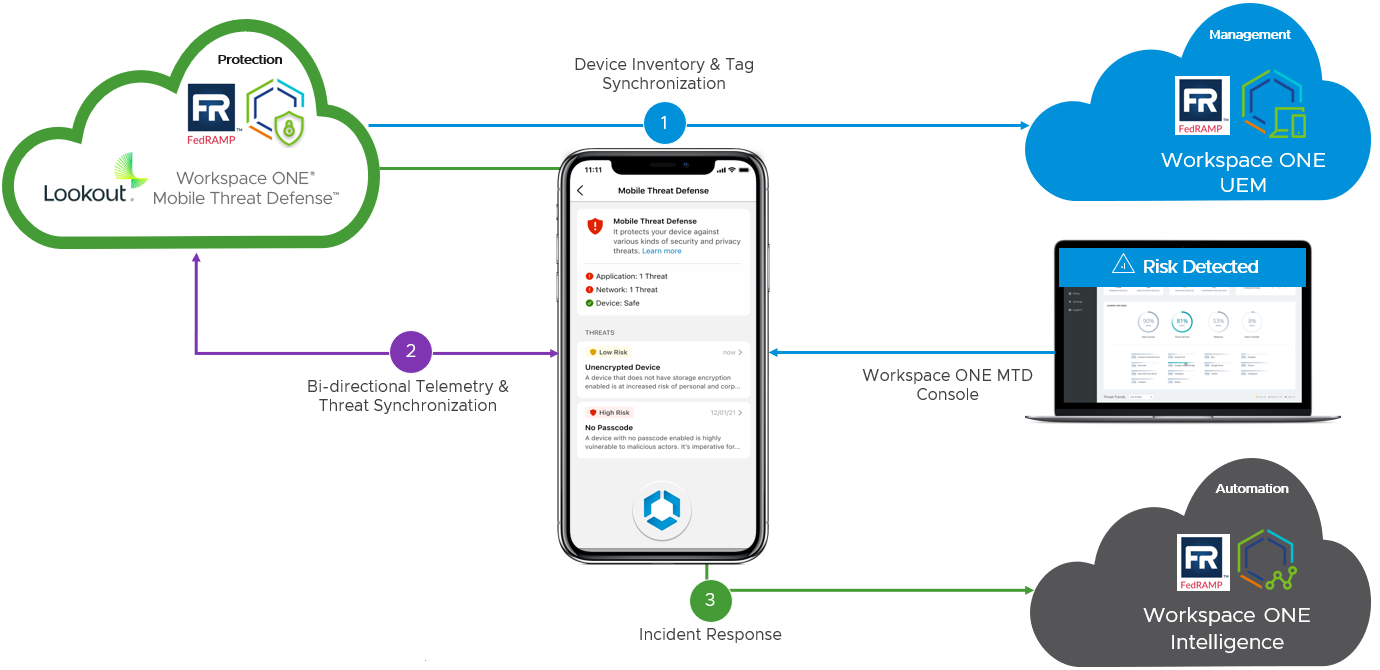
Figure 19: Omnissa’s MTD integration with UEM & Intelligence
Manage app risk at scale with custom policies
Omnissa’s Workspace ONE MTD gives admins the ability to blocklist individual apps, but that’s not a scalable solution when apps may update as much as 10 times a year. That’s why we empower admins to blocklist app behaviors by setting custom policies with flexible remediation actions. This reduces the need to manually vet each application while still preventing data leakage. With Omnissa Workspace ONE MTD, agencies can set custom policies to protect enterprise data from malicious apps and data leakage, strengthening their ability to meet governmental, internal, and regulatory compliance requirements for their mobile endpoints. Also, domains can be filtered for app traffic in ‘Denylisted Content’ policy, e.g., *.ru / *.cn / *.dk / *.ir / *.sy.
Scan and validate mobile apps before deploying
Users can be targeted in app-based attacks through non-malware apps and scanning from the storefronts of Google and Apple only protects users from app threats in those storefronts, not apps outside of them or those that don't pose a particular security risk at the time of scanning. These threats could leave corporate data vulnerable or not provide protection against these non-security threats related to more stringent privacy or policy concerns e.g., in the case of Apps that send data offshore or outside their region’s borders. Apps with the following behaviors can be classified as having elevated risk exposure. Examples include apps that:
- Monitor location changes.
- Are authorized to access the camera.
- Access the clipboard.
- Execute commands in separate processes.
- Use common RNG seed (Android).
Omnissa’s enhanced application protection built into Workspace ONE MTD, will not only continue to protect against the entire spectrum of mobile risk, but through the enhanced app vetting for enterprise developed by Omnissa’s partnered and integrated solution can provide app security testing to determine app behavior for enterprise compliance (or regulatory and governmental compliance) initiatives. App security evaluation and scanning ensures continuous conditional access to corporate resources, which only happens when there is an acceptable level of risk, and the device follows policy, as well as used in the Google’s App Defense Alliance, but also incorporated as manual tools for administrators in order to submit apps as *.IPA & *.APK files for additional analysis of those elevated risk exposure case above, within the Workspace ONE Mobile Threat Defense console prior to deployment by IT, Security or DevOps staff prior to deployment to end users.
Eliminate silos, automate reporting & remediation with the Workspace ONE platform
Interconnecting security and management can help eliminate silos, speed time to value of information, and address risk in real time. Workspace ONE Mobile Threat Defense can help management and security teams glean value from telemetry and threat information by aggregating data, applying AI and machine learning, then triggering alerts and remediation.
Workspace ONE Intelligence makes it possible to associate telemetry data from endpoints, applications, and users with threat information from Workspace ONE Mobile Threat Defense. Reporting and insights can be displayed in aggregate for team review. Specific conditions can trigger auto remediation via Workspace ONE UEM so that risks are addressed in real time. Users can be automatically notified of issues that require self-remediation; users and devices can also be flagged for follow up. These are again core to the 3rd element of the Executive Order requirements and those fundamental to the MITRE ATT&CK for Mobile matrices mentioned previously.
An integrated Workspace ONE suite
Workspace ONE is built on Omnissa's Workspace ONE UEM technology that provides for the standard aspects of Mobile Device Management (MDM), Mobile App Management (MAM), including a Unified Application Catalog. Workspace ONE integrates with virtual desktop application delivery via Omnissa Horizon on a common identity framework with Workspace ONE Assist to complete a full End-User-Computing (EUC) suite that can leverage Baselines as a key feature of enrollment, onboarding, and compliance:
Each of the components, along with the MTD, brings an integrated and secure Zero Trust Architecture (ZTA) solution that is partnered under a CRADA with the National Cybersecurity Center of Excellence (NCCoE). Together within Omnissa Anywhere Workspace, this solution builds trust to empower the government’s anywhere workforce with secure and frictionless experiences by:
- Providing enhanced NextGen endpoint security with Endpoint Protection through MTD.
- Enabling Zero Trust Network Access (ZTNA) with remote support for any device (BYO, 3rd party or Omnissa-managed) in a true hybrid workforce and providing a Security Operations Center (SOC) / Information & Technology support team the tools and telemetry for Indicator of Compromise (IoC) on mobile.
- Facilitating flexible deployment options to obtain immediate value for prioritized use cases, so you can scale at your own pace to harness the full potential of an integrated platform.
- Optimizing security and experience through an integrated approach that combines market-leading technologies essential for hybrid work; this integrated approach provides connected visibility and context, ensuring broader security coverage.
Zero Trust Security mapped into Omnissa’s Mobile Security Solutions
It’s not enough today to simply provide security for a domain, such as mobile, but equally important to enable both a secure means of doing business for the end-user and also ensuring that the complex challenges of ZT aren't being ignored. The right tools and resources must be in place along with a sound phased approach to meet the requirements of a Zero Trust Architecture. After reviewing and planning for a ZTA for the mobile-enabled environment, agencies will need to ensure that a robust device trust and validation utility exists that provides for:
- Continuous Policy Enforcement (CPE), although not a single product, rather a mode of operation that could apply to devices, app sessions, network sessions, or even the ability to use a client device. e.g.
- A device is only allowed to be used in one specific location, so if the user deactivates that device’s location services, the device immediately locks itself.
- Many of today’s leading security solutions include some form of CPE but will be paramount to device trust and the ZTA solution.
- Threat Defense and Endpoint Protection (MTD/EPP) solutions already can provide this visibility and controls on all sorts of end-user devices, including traditional, mobile, and IoT.
- Device, Network, Application & Scanning & Protection ensuring that the software and hardware ecosystem used for the supply chain risks of the mobile hardware and software ecosystem providing compliance validation for each of these domains.
Securing those endpoints and their complex ecosystem of software and hardware takes specialized and honed tools, such as those incorporated into Omnissa’s End-User Computing suite = Workspace ONE UEM and Horizon VDI below providing a robust set of Zero Trust enabled solutions:
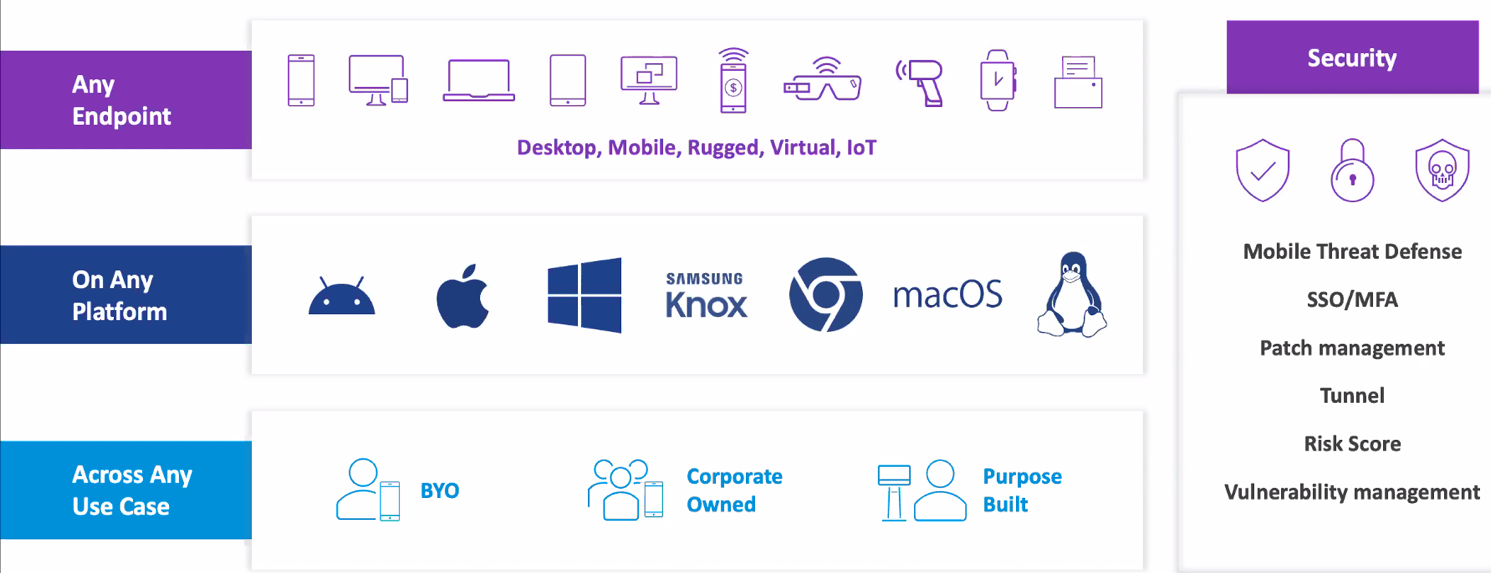
Figure 21: Omnissa Workspace ONE Mobile Security Solution overview
Additional Resources
For further Zero-Trust assets on Tech Zone, see:
- Tech Zone: Security Portal
- Tech Zone: Omnissa Security Products
- Tech Zone: Workspace ONE MTD Configuration Video Library
For additional referenced materials, see:
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2024/11/22 | Updated for Omnissa docs, KB, and Tech Zone links. |
| 2023/08/24 | Guide was published. |
About the Author
Andrew Osborn, Omnissa alumni.
Feedback
Your feedback is valuable. To comment on this paper, either use the feedback button or contact Omnissa at: tech_content_feedback@omnissa.com.

