Integrating Workspace ONE UEM and Cisco ISE v3.1 and Beyond
Overview
The Cisco Identity Services Engine (ISE) is a Network Access Control (NAC) solution designed to enhance network security by forcing devices to comply with policies before they are allowed to access a corporate network.
Several Omnissa Workspace ONE UEM customers have been using Cisco networking components to comply with their advanced security requirements, and integrating Workspace ONE UEM with Cisco ISE functionality gives them a more complete network security solution. While using the Workspace ONE UEM solution helps ensure both data and device integrity, additional steps taken at the network layer can further enhance the overall security for utmost protection.
Cisco ISE behavior up to version 3.0 (MAC address)
As a privacy measure, mobile devices and some desktop operating systems increasingly use random and changing MAC addresses for each SSID that they connect to, also operating systems like Android no longer expose the device MAC addresses through their APIs when using Work Profile. Up to Cisco ISE version 3.0, MAC addresses have been used to identify the devices and authenticate whether it is valid (ownership) and compliant.
While MAC address randomization offered substantial privacy advantages, it posed challenges for integrations reliant on consistent MAC addresses for device identification. This is particularly evident in scenarios highlighted below involving Cisco ISE and Workspace ONE UEM:
- Where the same device may present different MAC addresses depending on the SSID used for connection
- Where the same device may present a MAC address depending on the network it was connected to over Wired, Wireless, or VPN
- Where the same device may present the dongle or docking station's MAC address when these devices are connected through them
Consequently, when ISE communicates with Workspace ONE UEM using a MAC address, Workspace ONE UEM may fail to lookup the MAC address as belonging to any valid device. This can result in the device being unable to authenticate and gain access to network resources.
That creates a problem where Cisco ISE and Workspace ONE UEM API servers no longer can obtain the device MAC addresses or access it for the same device depending on which SSID is used to connect to the service. So, when Cisco ISE makes a call to the UEM API server, UEM doesn’t identify the MAC address belonging to any valid device, resulting in the device being unable to authenticate and gain access to network resources.
Cisco ISE behavior version 3.1 and beyond (GUID based)
To solve the problem, Cisco ISE and Workspace ONE UEM came together with an updated integration. Cisco ISE release 3.1 introduces the MDM API version 3 that enables the use of a unique device identifier called GUID (globally unique identifier) instead of MAC addresses to identify devices connecting to the network, in turn, the GUID value is provided by Workspace ONE UEM as part of the client certificate to be used by ISE to query device’s compliance information available into Workspace ONE UEM.
The ISE and UEM integration addresses the problem making the device UUID (GUID) the common identifier between them, removing ISE’s dependency on MAC addresses to query the device’s compliance information in UEM.
Purpose of This Tutorial
This integration ensures that your end user's devices can safely and securely connect and access network resources, so that even when their MAC addresses are randomized; they can connect over Wired, Wireless, or VPN and they can connect via dongle or docking stations, eliminating the dependency on the MAC address. This tutorial takes you through the required steps to integrate Cisco ISE v3 MDM API (released with Cisco ISE 3.1) and Workspace ONE UEM, in addition to configuring certificate lifecycle management on Workspace ONE UEM for certificate-based authentication with ISE using Wi-Fi connectivity as a use case.
Before you perform the configuration steps provided in this tutorial, you must have administrator access to the Cisco ISE and Workspace ONE UEM environments, including knowledge of certificate templates and certificate authority to perform the required configuration.
Audience
This tutorial is intended for IT, network, and security administrators who are familiar with Workspace ONE UEM and Cisco ISE.
Use Case
As a standalone solution, the Cisco ISE ensures mobile devices connected to your corporate Wi-Fi network are compliant with limited policies based on device type and user. The integration with Workspace ONE UEM enables ISE to perform device posture based on a more granular level by using the wealth of mobile device data provided by Workspace ONE. While Workspace ONE UEM can determine device compliance based on an extensive list of attributes, ISE makes the policy decisions using additional context from Workspace ONE UEM and enforces policies on the network.
On the other hand, Cisco ISE takes Workspace ONE UEM’s ability to enable or deactivate Wi-Fi functionality a step further by restricting access to allowlisted websites while a device is connected to the corporate Wi-Fi network. The following table depicts which data elements Workspace ONE UEM and Cisco can manage individually and demonstrates the power of this integrated solution.
|
| Workspace ONE UEM | Cisco ISE |
| Device Type |
|
|
| Device User |
|
|
| Device Details |
|
|
| Device Compromised |
|
|
| Device Compliance |
|
|
| Deactivate Wi-Fi |
|
|
| Restrict Wi-Fi* |
|
|
| Advanced device restrictions |
|
|
* Selectively restrict access to allowlisted websites only.
What are the benefits of integrating UEM and ISE?
Organizations might be in different stages and have not implemented advanced solutions to secure access through their networks, but those can benefit from Workspace ONE UEM and Cisco ISE integration considering the following scenarios.
Enterprises not enforcing mobile and desktop device network security policies
If your company does not enforce security policies on mobile and desktop devices when accessing the internal corporate Wi-Fi network, your infrastructure is potentially exposed to security risks and attacks from the device. Incorporating the Cisco ISE and Workspace ONE UEM allows the devices to connect to the corporate Wi-Fi and VPN safely and securely.
Enterprises not allowing mobile devices on the Network
If your company does not currently allow mobile devices on your internal corporate network, incorporating the Cisco ISE along with Workspace ONE UEM could allow devices onto the corporate Wi-Fi, because both products work together to minimize or remove risks associated with allowing mobile devices onto the Wi-Fi network.
Enterprises currently using Cisco ISE without Workspace ONE UEM
If you already have a Cisco ISE solution, adding Workspace ONE UEM to the architecture enhances the functionality of the Cisco ISE by adding more detail to the mobile device status. When used with your existing Cisco Wireless Networking components and Workspace ONE UEM, you can confirm mobile devices accessing your wireless network are compliant with your security policies.
How does the integration work?
The integrated solution creates a secure method of access for anyone attempting to join your internal corporate Wi-Fi network, ISE will use the GUID of a device to query UEM for the device’s registration, compliance statuses, and other MDM attribute values.
The integration flow requires registration with Cisco ISE and enrollment into Workspace ONE UEM, as described below:
- When an end-user attempts to connect their mobile or desktop device, they initially access a Service Set Identifier (SSID) which prompts them to register with the Cisco ISE and enroll in Workspace ONE UEM.
- Once enrolled, Workspace ONE UEM sends a certificate with a GUID value to the device, including a Wi-Fi profile that uses the certificate for authentication with Cisco ISE.
- When the device connects to the internal SSID, it uses the certificate for authentication with Cisco ISE, which receives the GUID for the device from the certificate.
- ISE first authenticates the Wi-Fi device and after that, it communicates with UEM through REST API leveraging the GUID value to query device information and compliance is checked against assigned policies at regular intervals.
- Additionally, if a device violates an active compliance policy, access is immediately restricted based on the policies defined in ISE, and the user is redirected to the Workspace ONE UEM Self-Service Portal (SSP) for remediation.
All communications between Cisco ISE and UEM can now use the GUID to identify the device, ensuring accuracy and consistency between the two systems.
Integrating Workspace ONE UEM and Cisco ISE
Prerequisites
To take advantage of the new Cisco ISE v3 MDM APIs leveraging GUID as the unique device identifier, ensure you have the following resources available:
- Cisco ISE version 3.1 or later.
- Workspace ONE UEM 2410.
- Certificate Authority integrated with Workspace ONE UEM to issue certificates.
- GUID is only supported when using certificate-based authentication methods, basic authentication methods that only use username and password are not supported.
Customers currently using Cisco ISE prior to version 3.1 will continue to be supported and will not be impacted by this integration.
Cisco ISE Configuration
The following steps are required to enable ISE and UEM communication and will be performed in the Cisco ISE console:
- Import the Workspace ONE UEM SSL Certificate
- Configuration of Workspace ONE UEM as External MDM
- Configuration of the GUID as device identifier
Import Workspace ONE UEM SSL Certificate (Trusted Certificates)
For Cisco ISE to establish trust with Workspace ONE UEM, first it’s required to import the Workspace ONE UEM SSL Certificate into ISE. You can obtain the UEM SSL Certificate through your internet browser, such as Edge, Chrome, Safari, or Firefox using the following procedures:
- Navigate to your Workspace ONE UEM environment (i.e.: https://cnXXX.awmdm.com).
- Click the lock or settings icon next to the URL, click on the menu item Connection is Secure and select the option to show the certificate:
- On the details tab for the certificate, click Export to file (.CER format).
In the Cisco ISE Console, from the Menu icon navigate to Administration > System > Certificates > Trusted Certificates click import to import the UEM certificate in PEM or CRT in base 64 format.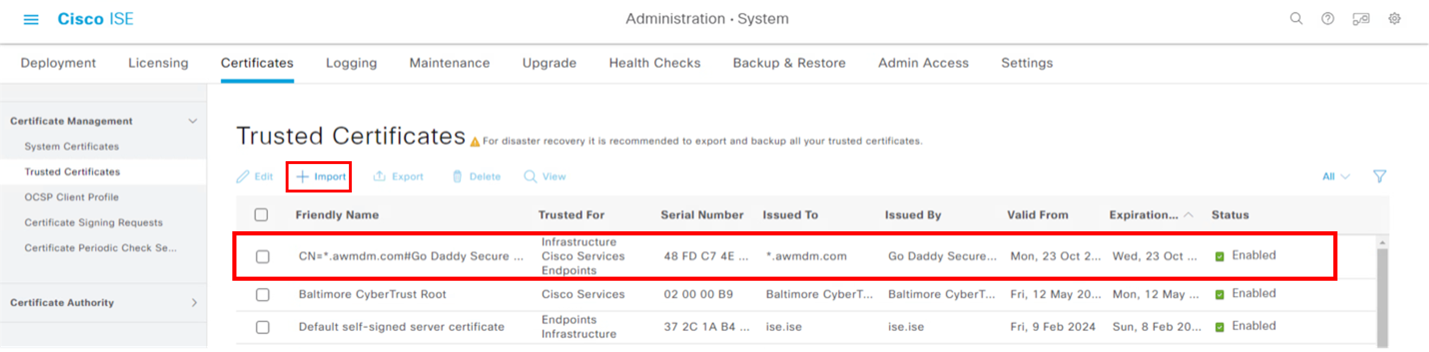
Figure 1: Example of UEM certificate already imported into Cisco ISE.
Import any other certificate chain required to establish trust between ISE and the device client certificate.
Configure Workspace ONE UEM as External MDM
This topic covers the steps to add Workspace ONE UEM as MDM Servers into Cisco ISE.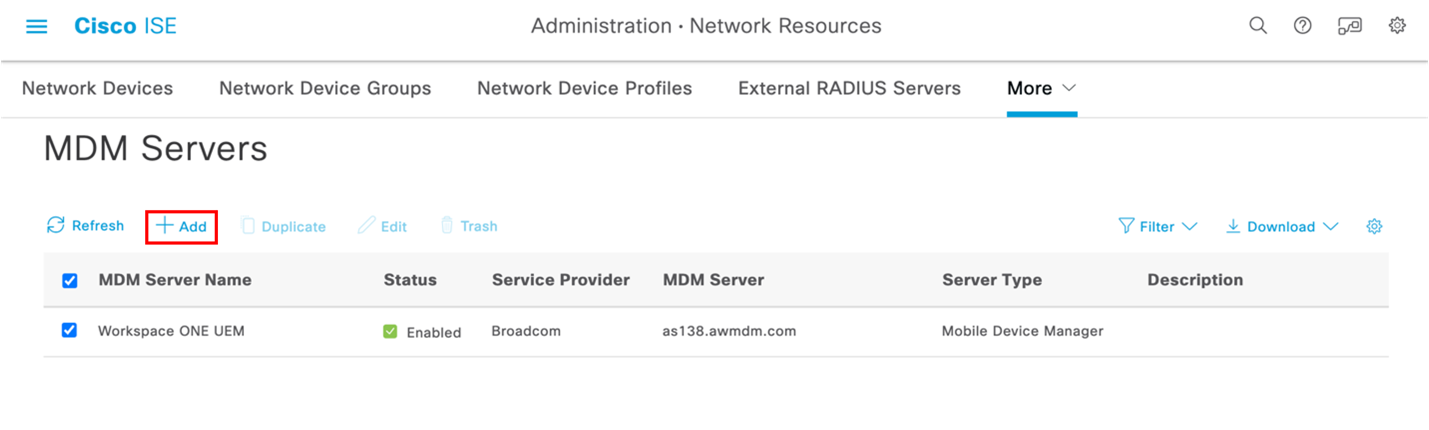
Figure 2: Example of UEM configuration added to Cisco ISE.
Navigate to Administration > Network Resources > External MDM and click the Add button, fill out the fields on the New Server page based on your Workspace ONE UEM instance. Before you proceed, make sure the REST API is enabled on the UEM OG (Organization Group) that will be used to integrate with ISE.
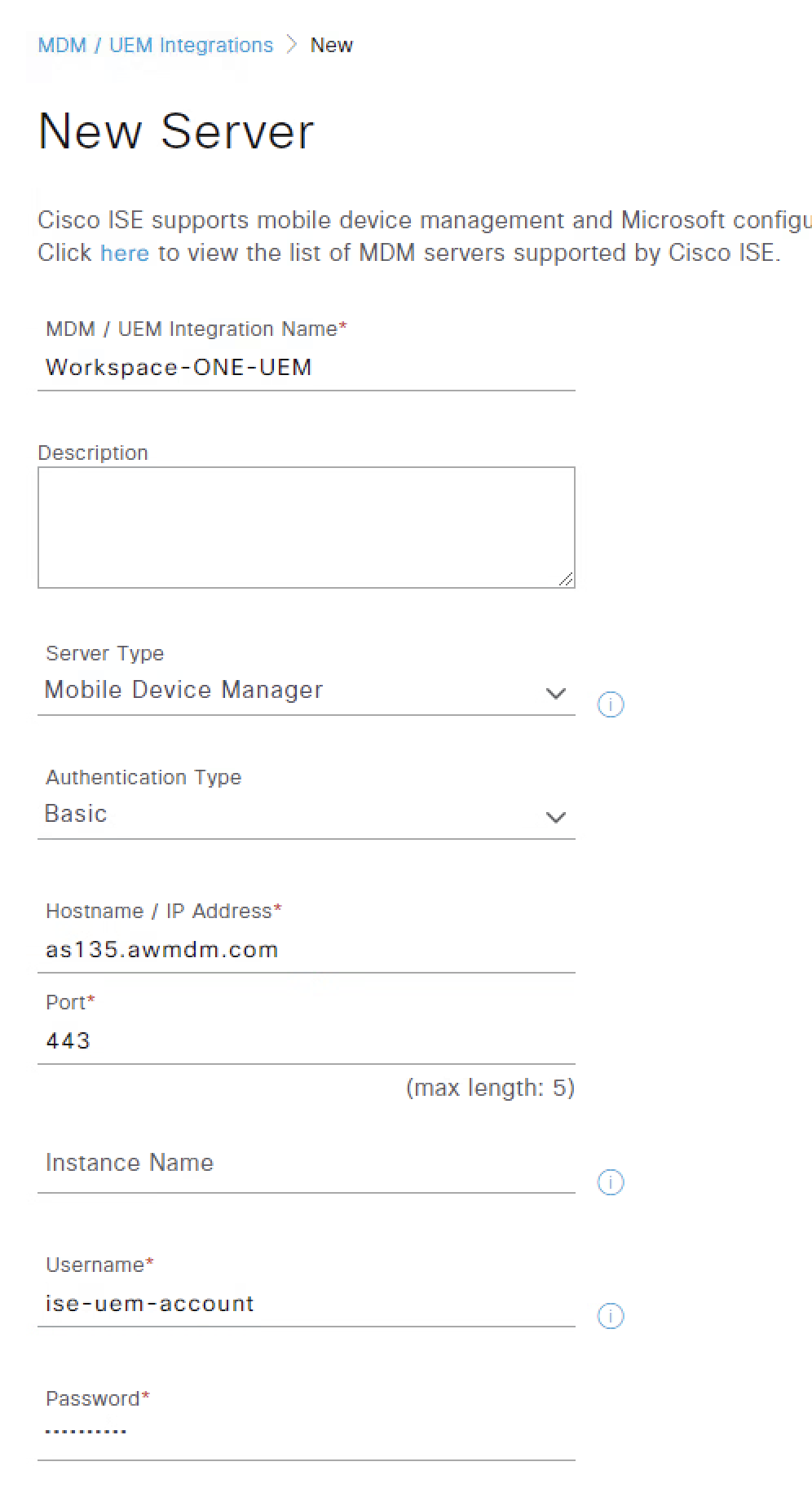
The above values are just examples, ensure to add the correct information related to your UEM environment and set the following fields as:
- Set Server Type to Mobile Device Manager.
- Set Authentication Type to Basic.
- For Hostname / IP Address provide the UEM API Server hostname.
- For Port set 443, the default for UEM SaaS.
- Update in case you use a custom port for UEM on-premises.
- Leave Instance Name empty.
- UEM Username and Password with access to execute device actions through REST API.
- You can assign the Tunnel Administrator Role permission on UEM to this account.
The following parameters (Polling interval, UEM Device Compliance Timeout and Compliance Cache) are related to the behavior of device compliance, specifically, the polling interval parameter specifies how often ISE will query UEM for changes to device posture. Polling can be deactivated by setting the value to 0 minutes. Polling can be used to periodically check the device compliance posture on UEM. If the device is found to be out of compliance and the device is associated with the network, then ISE will issue a Change or Authorization (CoA) forcing the device to re-authenticate. The device will probably need to remediate with UEM although this will depend on how the ISE policy is configured. Note that UEM compliance requirements are configured on the MDM and are independent of the policy configured on ISE.
Finally, when an endpoint is authenticated or reauthenticated, Cisco ISE uses a cache to get the Workspace ONE UEM variables for that endpoint. If the age of the cached value (Compliance Cache Expiration Time) is higher than the configured value, Cisco ISE sends a new device query to the Workspace ONE UEM to get new values. If the compliance status has changed, then Cisco ISE triggers the appropriate CoA.
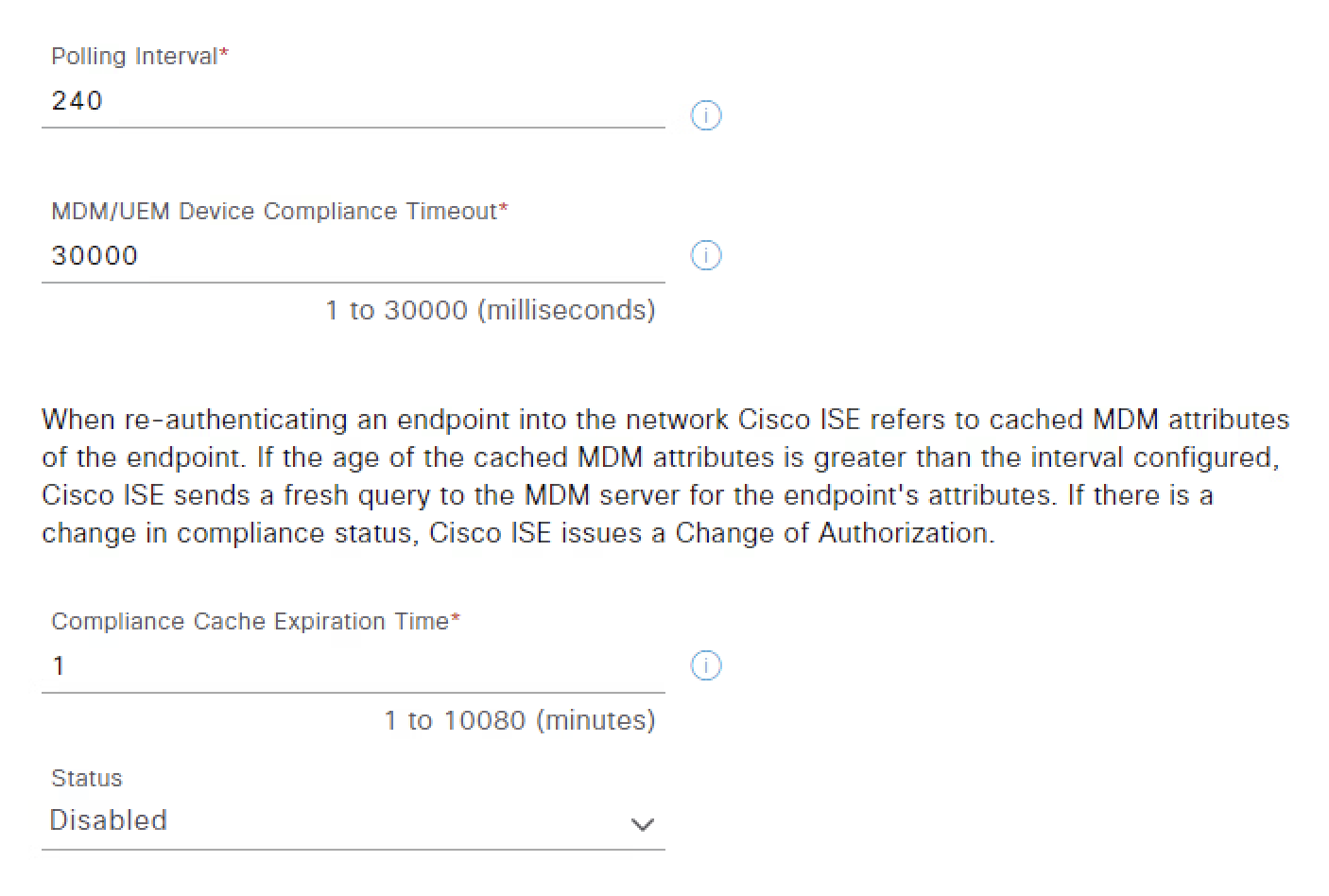
For this tutorial, we are leaving the device compliance-related parameters as default, updating only:
- Status to Enabled
- Click Test Connection
The Test Connection button validates the connectivity with UEM and if it supports the Cisco ISE MDM APIs version 3 that is required to send GUID information. A successful test connection will display the Cisco API version supported by the UEM instance and a new section called Device Identifiers, the identifier options allow ISE to query UEM based on the selected parameters to obtain device information such as compliance status. ISE provides flexibility to select the option to query based on MAC address, GUID, and SAN.
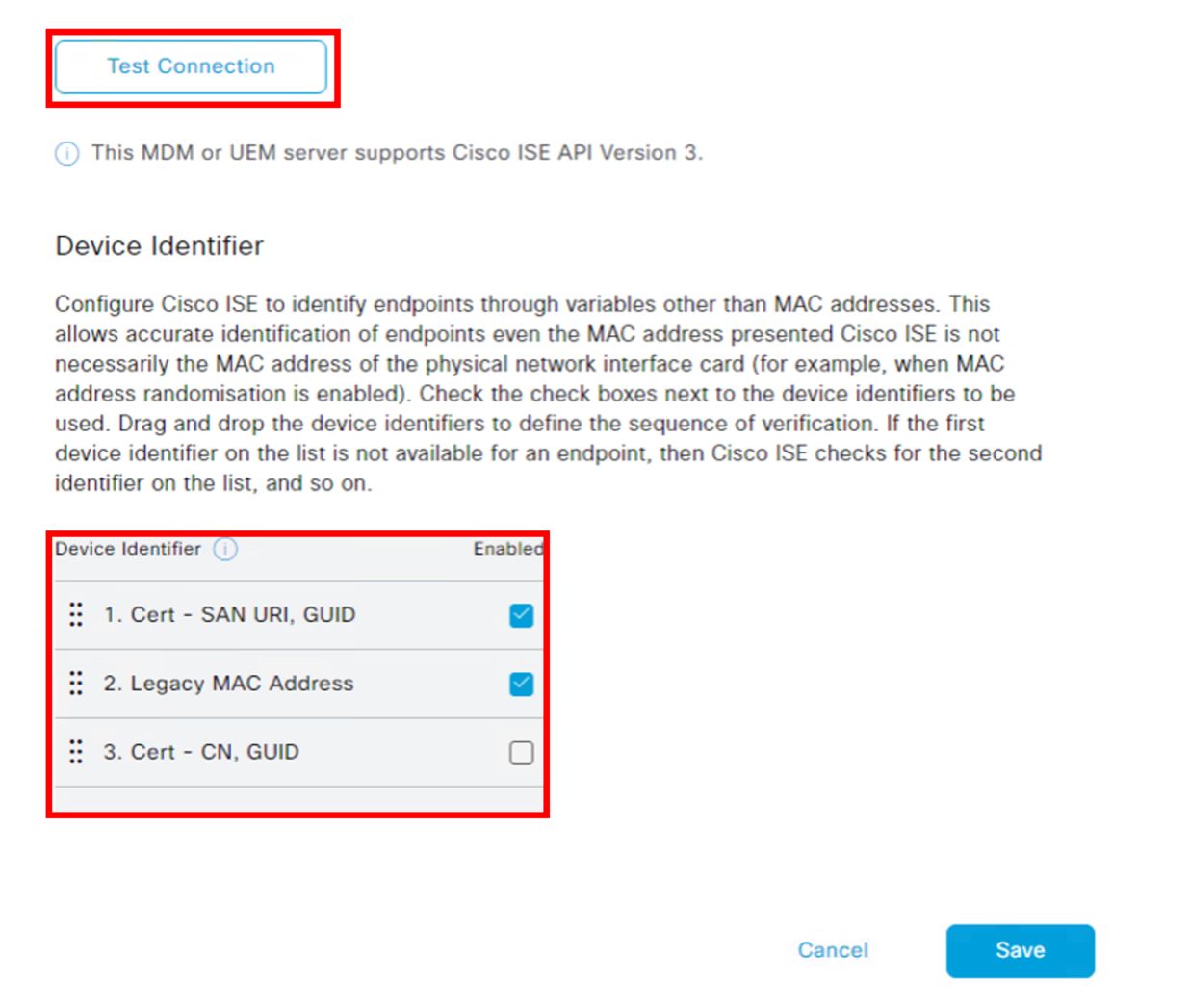
In the above example, Cisco ISE will first query a device on UEM using the GUID attribute on the SAN URI, If the requested attributes are not available, Cisco ISE will query against UEM using the device’s MAC address. For devices that randomize MAC addresses it is recommended not to select 'Legacy MAC address' from the list of Device Identifiers from ISE.
You must configure the "Cert - SAN URI, GUID" based integration to ensure ISE doesn’t rely solo on MAC address to identify the device connecting to the network.
- Select the check box for Cert - SAN URI, GUID.
- In case you select additional identifiers, make sure to keep Cert - SAN URI, GUID as the first one in the list using the drag and drop option.
- Note: Some Certificate Authorities integrated with Workspace ONE UEM may not currently support the SAN URI field. In such instances, it’s recommended that you continue using MAC addresses for device identification.
Workspace ONE UEM Configuration
To establish the integration between Workspace ONE UEM and Cisco ISE 3.1+ using GUID as a method for device identification, the company’s network must use certificate-based authentication. Because of this, UEM must be integrated with a certificate authority to streamline the issuing and delivery of certificates to the devices, and the certificate must contain a specific attribute required by ISE.
More specifically, when configuring the certificate template, one of the Subject Alternative Name (SAN) URI fields within the network authentication certificate must have the following designated value ID:WS1UEM:UUID:{DeviceUuId}, where Workspace ONE UEM will replace the {DeviceUuId} lookup field with actual device UUID when the certificate is issued to the device, either through SCEP or Credentials profile. When the device presents this certificate to authenticate into the network, Cisco ISE uses this UUID to identify the device instead of its MAC address.
Follow the steps below to prepare the certificate template and the device’s Wi-Fi profile for certificate authentication against ISE.
Certificate-based authentication with ISE
The configuration of certificate-based authentication with ISE is beyond the purview of the document. Check the following Cisco ISE documentation Configure EAP-TLS Authentication with ISE.
Step 1. Prepare Certificate Template for ISE
On the certificate authority that will issue the certificate to be used on the device for network authentication, create a new template for ISE.
In case you are using Microsoft CA, duplicate the User Template and provide a new name, such as “UserISEv3”, to ensure that Client Authentication and Server Authentication are included as part of the Application Policies extensions.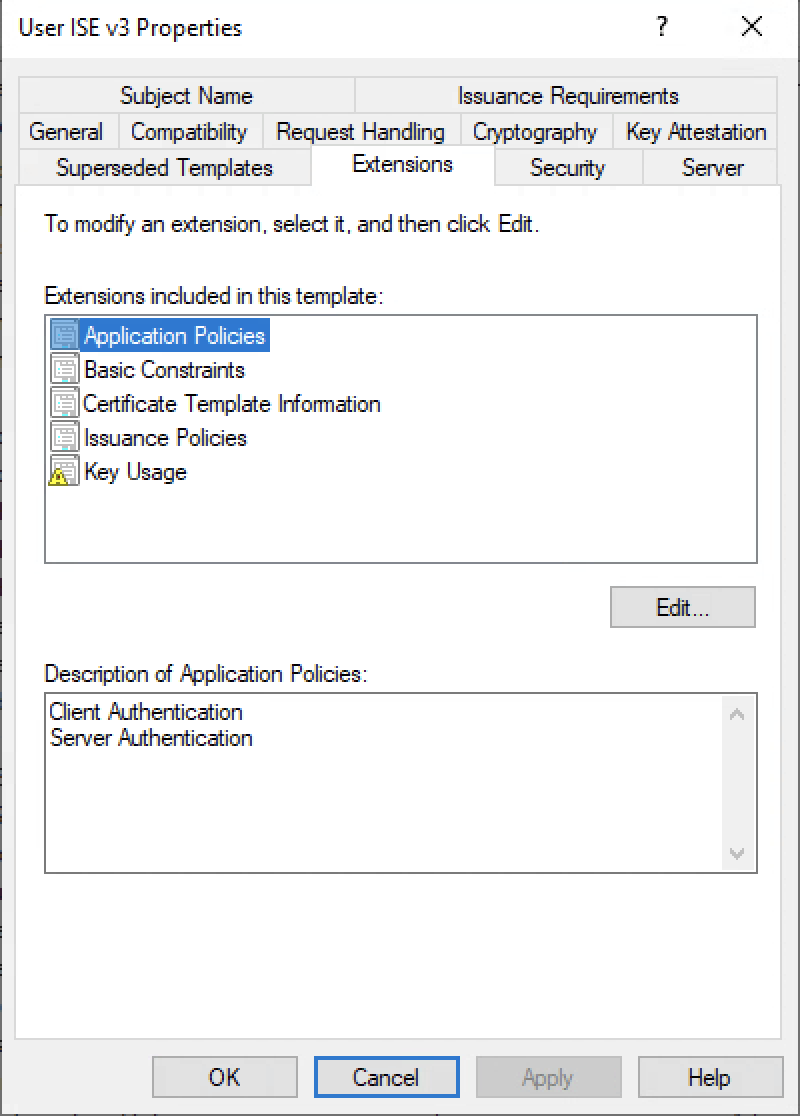
Figure 3: Extensions configuration required for ISE templates.
In the Workspace ONE UEM console, create a new certificate by navigating to Groups & Settings > Configurations > Certificate Authorities:
- Click the Certificate Authority that will be used to issue the certificate.
- Under Request Template click Add Request Template.
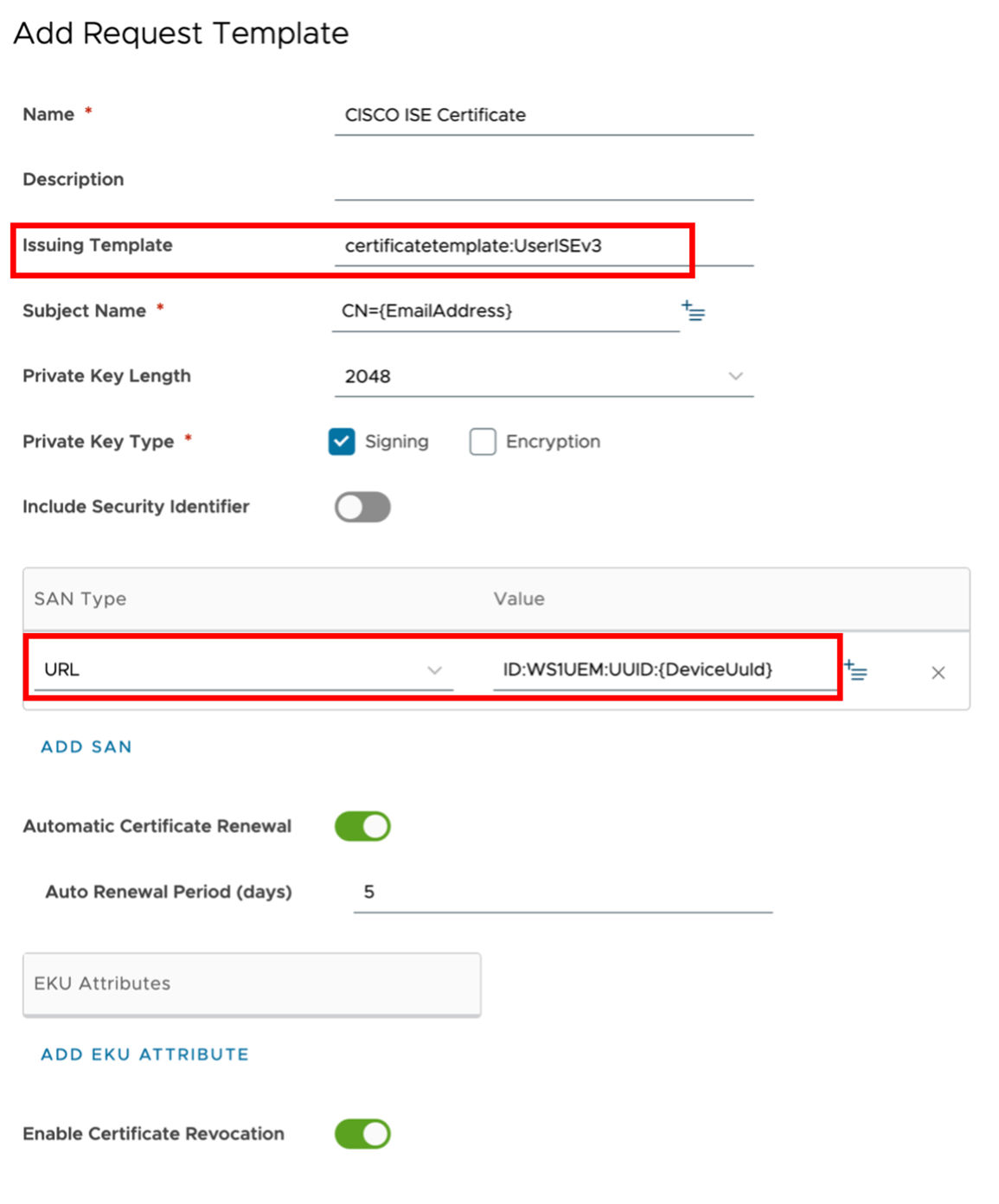
Figure 4: Example of certificate template for network authentication with Cisco ISE.
Configure the certificate template as above updating the respective fields:
- Set the Issuing Template for the respective name of the template created on your internal CA, in this example named UserISEv3.
- Add a SAN item, setting SAN Type as URL and value ID:WS1UEM:UUID:{DeviceUuId}.
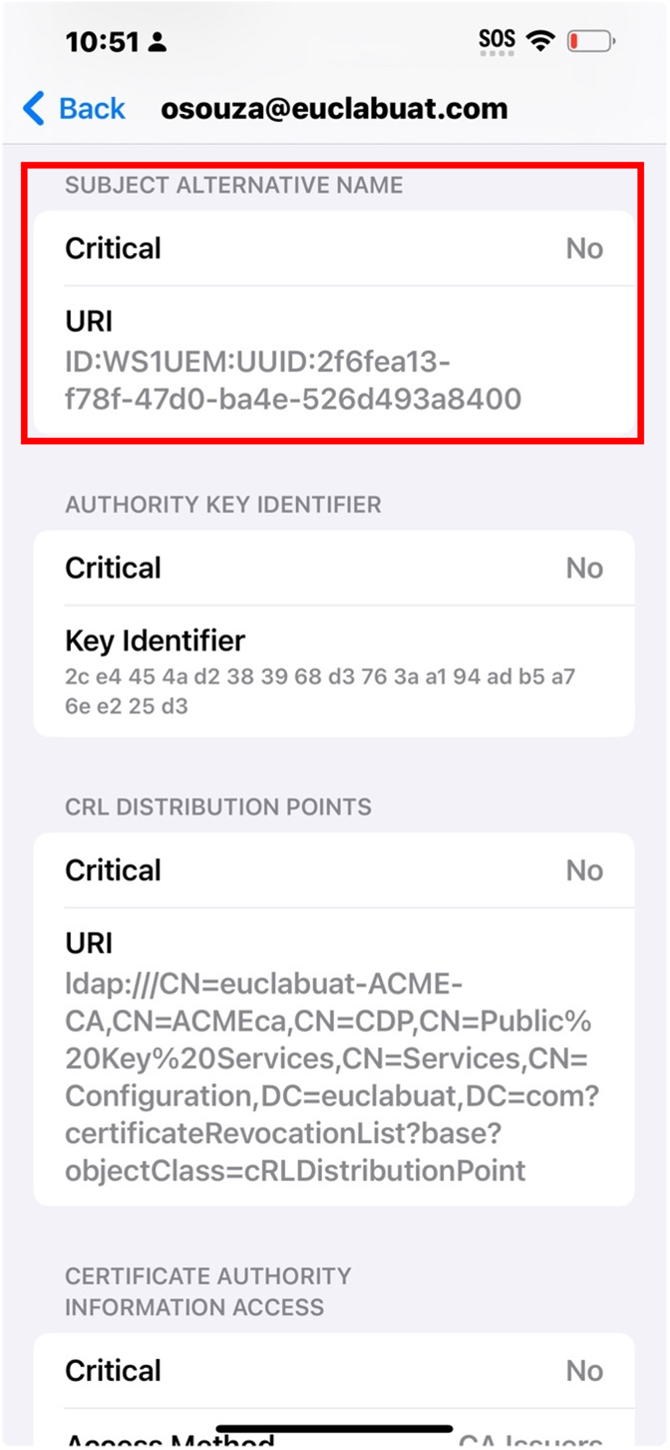
After finalizing all the configuration and enrolling a device, the certificate issued by the CA will contain the device UUID as part of the Subject Alternate Name. The device UUID format should look like the following screenshot.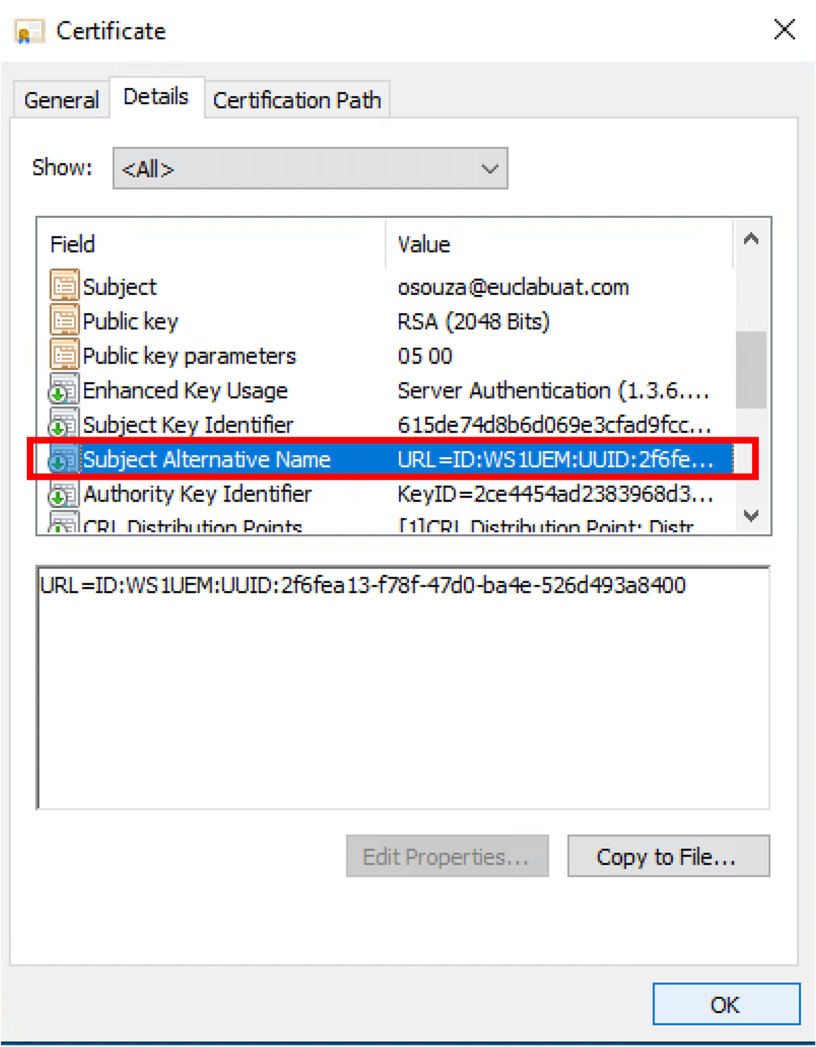
Figure 5: Example of certificate including the unique device identifier that will be used by Cisco ISE.
On iOS devices, you can access Settings > General > VPN & Device Management > Device Manager > More Details > Certificates. In the list of certificates, select the ISE certificate delivered by Workspace ONE UEM, under the Subject Alternative Name you will find the device GUID.
Step 2. Configure Profile’s Certificate and Wi-Fi payload
Automating the Wi-Fi and certificate deployment creates a silent configuration, seamless user experience, and ensures that all ISE requirements are properly configured on the device.
In this topic, we will review the steps to create a new profile based on an iOS platform. The profile configuration for other OS platforms follows the same steps with a similar configuration for the Wi-Fi payload.
Note: Important to take into consideration for this step:
- It’s recommended to create a new profile for this step; later it will make the validation and troubleshooting process easier, as minimizing any disruption on existing devices that are already configured to connect through Cisco ISE.
- When updating a profile already deployed in production, you must republish the profile for the devices to be able to receive the new certificate.
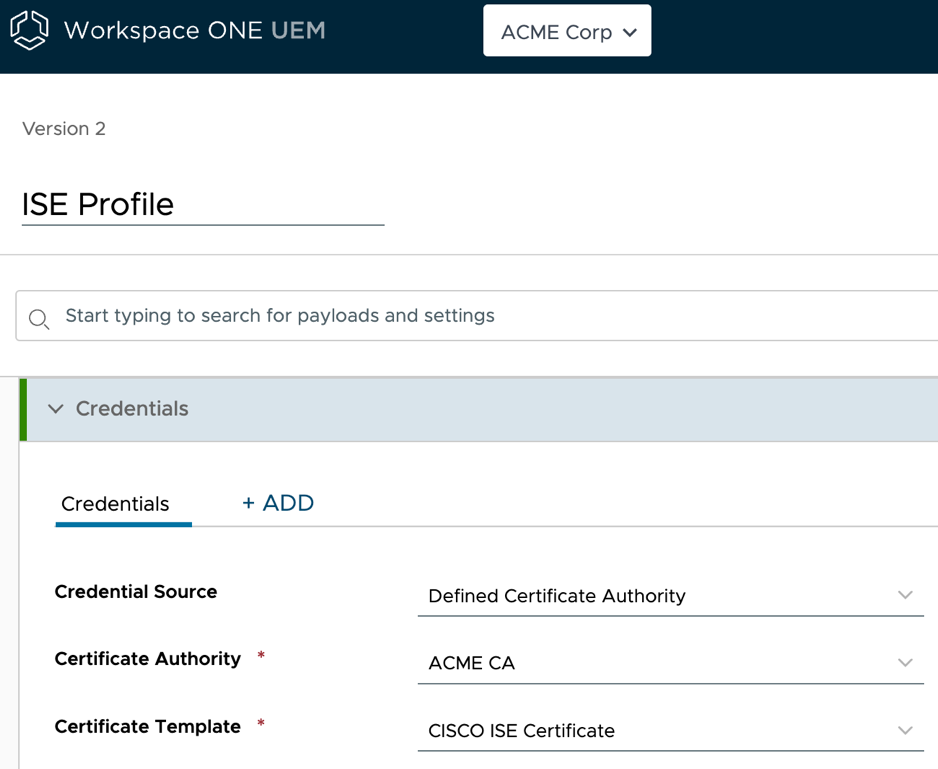
Figure 6: Example of an iOS profile configuration for Cisco ISE certificate based on credentials payload.
Create a new profile to set up either Credentials or SCEP payload to be sent to the devices that you plan to enable Wi-Fi certificate-based authentication through Cisco ISE.
- Add a Credentials payload and fill out the Certificate Source, Authority, and Template fields based on the template defined in Step 1.
On the same profile, add a Wi-Fi payload that will contain the configuration for the device to connect to the corporate Wi-Fi and authenticate into the network.
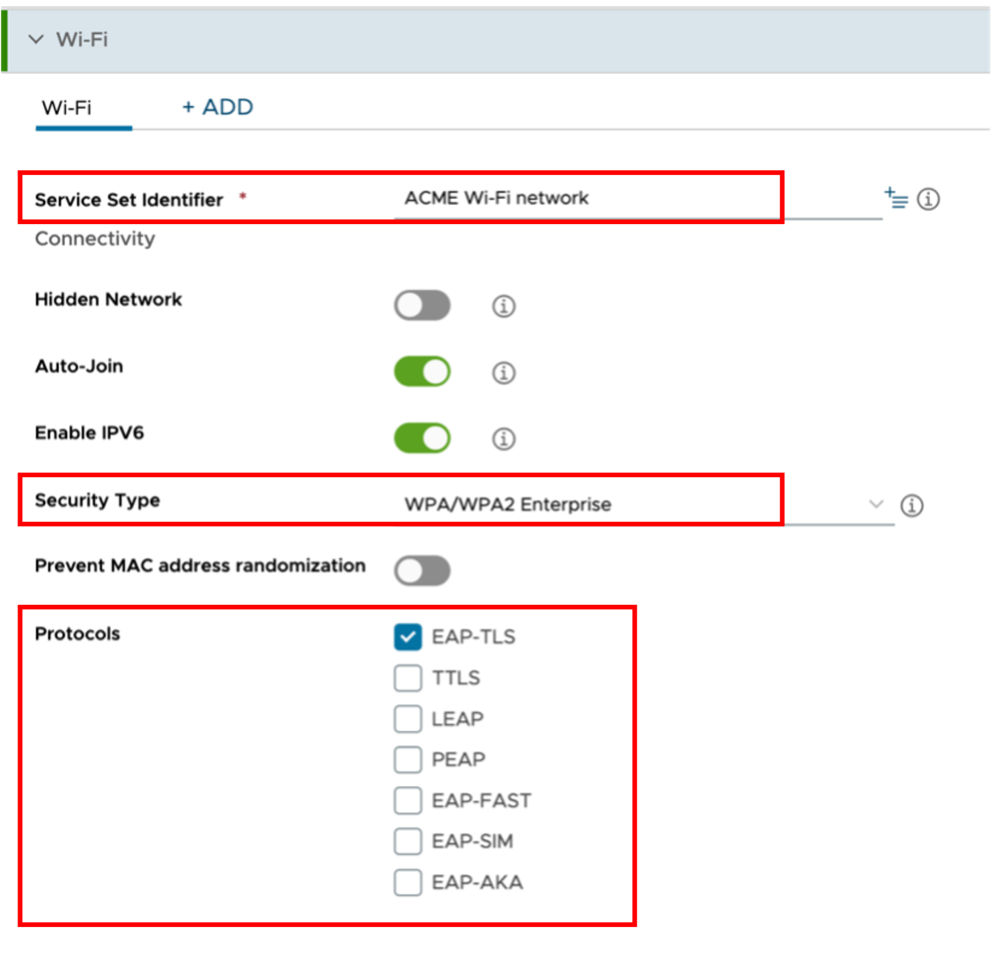
Configure the Wi-Fi attributes based on your network configuration, such as:
- Service Set Identifier
- Security Type
- Protocols
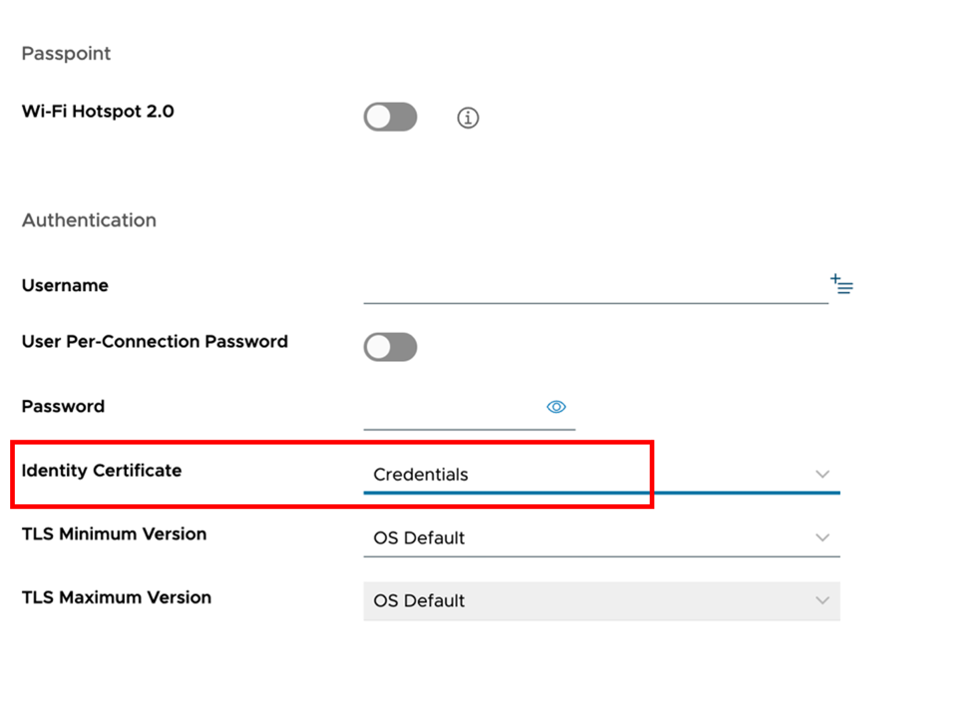
Under Authentication, set the Identify Certificate field to the credentials payload defined on this profile.
The certificate will be used during the network authentication against Cisco ISE, ISE will read the certificate to obtain the Device UUID (GUID) and query device information such as compliance status into Workspace ONE UEM.
Important: The certificate chain must be imported to Cisco ISE to ensure trust with the certificate clients used for the authentication. Review the steps described in Import Workspace ONE UEM SSL Certificate (Trusted Certificates).
Troubleshooting
The UEM and ISE integration leverages multiple parts, which requires troubleshooting multiple components in different places. The following is a list of common resources you can access to perform the troubleshooting.
Device and Certificate Troubleshooting
To troubleshoot issues related to the device’s certificate configuration and deployment:
- Navigate to Device > List View and locate the device, under Device Detail Page ensure:
- Under the Profile tab confirm that the Wi-Fi Profile is installed.
- Under the Certificate tab confirm that the Status of the certificate is Installed.
- When the certificate status is not installed, navigate to the More > Troubleshooting page and look for the Module “Certificate Management”, An error related to the certificate will be available under that category, and the event data column will provide additional error details.
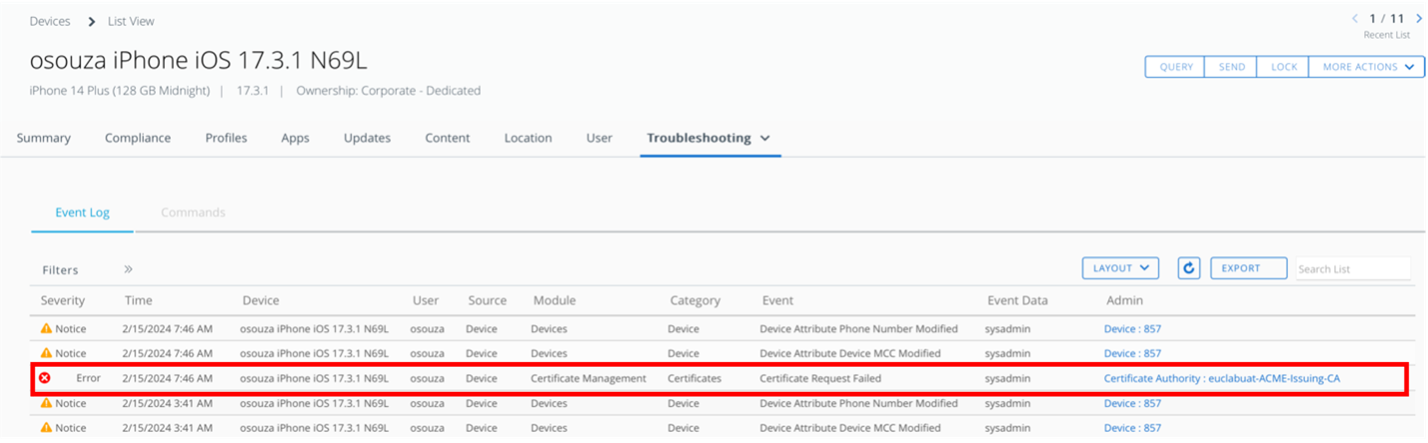
Figure 7: Device Troubleshooting page in Workspace ONE UEM.
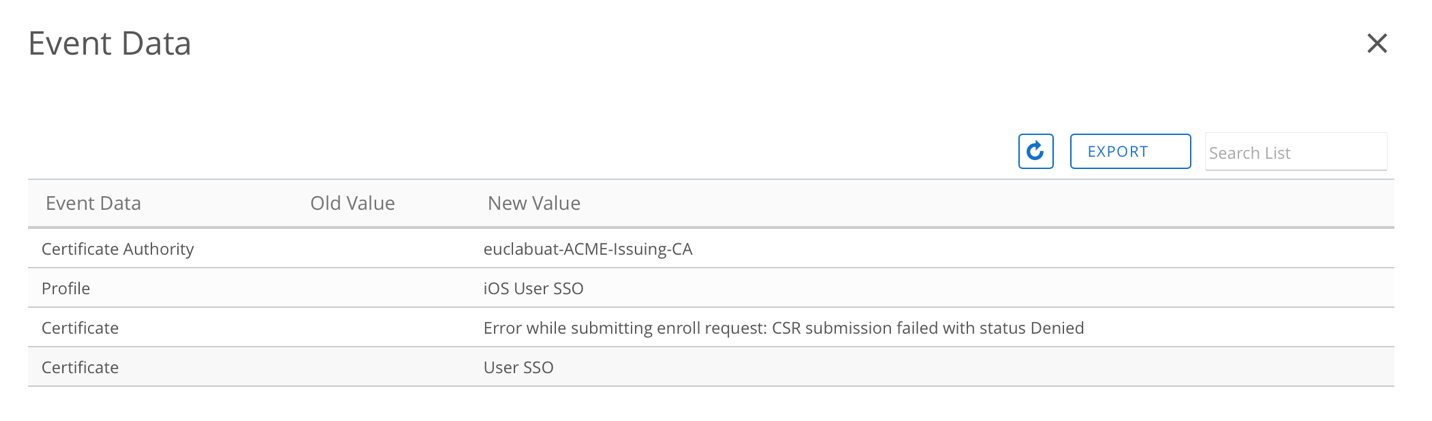
Figure 8: Event details to the specific error log.
- When using the Certificate Authority through AirWatch Cloud Connector (ACC), the ACC logs located at
C:\Omnissa\AirWatch\Logsof the server where it is deployed can provide additional details regarding the certificate issuing process. - In case the ACC log information is not sufficient, connect to your Certificate Authority and look for Failed Requests which will provide the ultimate reason why a certificate request failed.
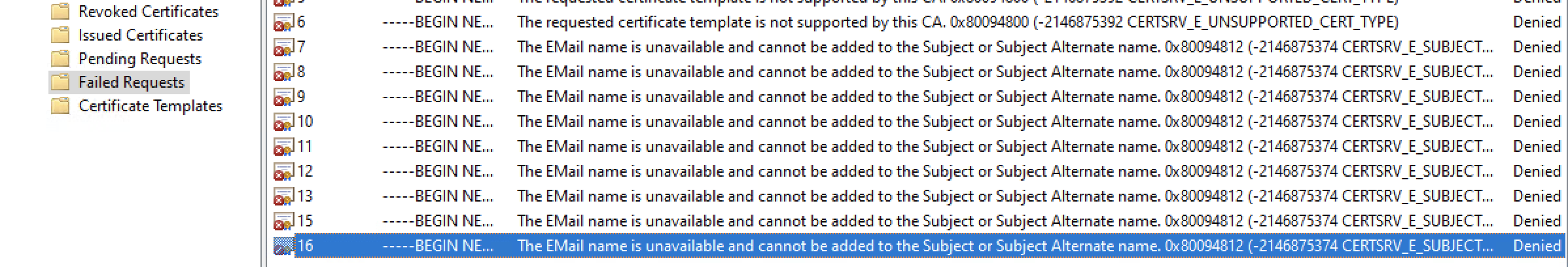
Figure 9: List of certificate failed requests on Microsoft CA reporting the Status Error Code.
GUID Certificate Troubleshooting
The certificate issued by the CA must contain the device UUID (GUID) as part of the Subject Alternate Name, otherwise authentication on Cisco ISE will fail. This can be validated by looking for the details of the certificate on the device and checking the Subject Alternative Name values. The steps and screenshots to perform this check on Windows and iOS devices are as follows:
- On Windows, you can find the certificate by accessing the Certificate Store (
certmgr), the certificate path installation depends on the configuration defined on the Wi-Fi profile.
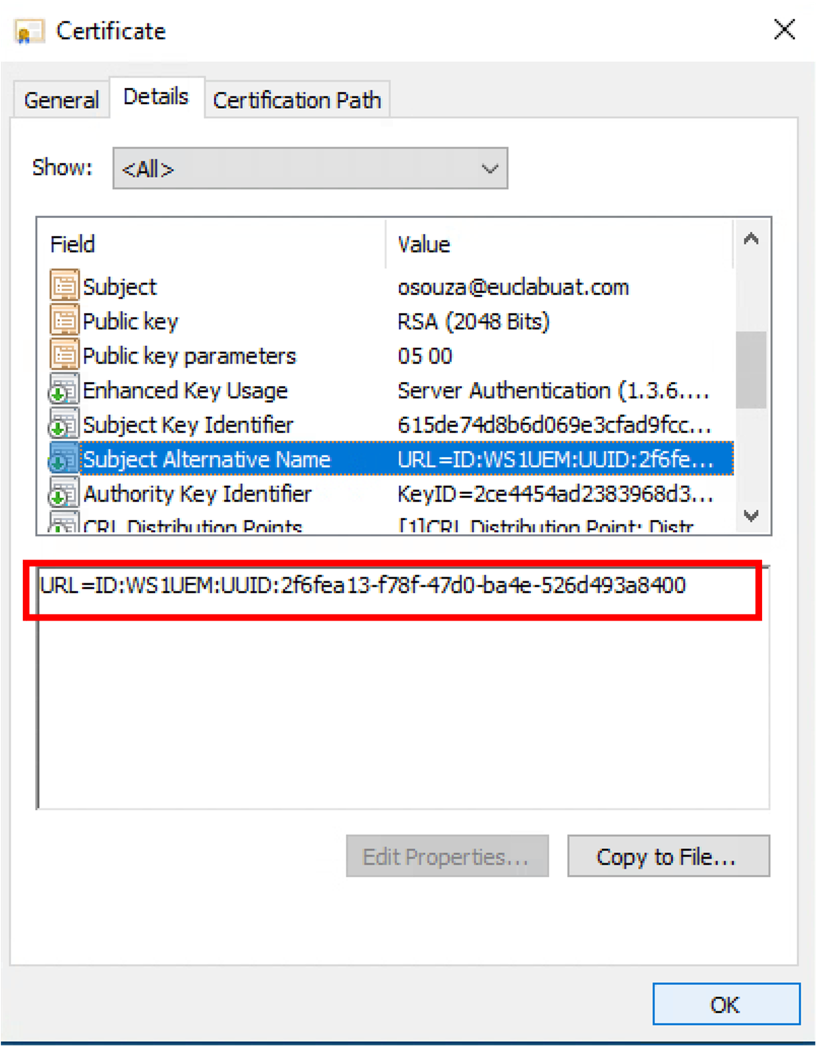
Figure 10: Example of Windows certificate including the unique device identifier that will be used by Cisco ISE.
- On an iOS device, navigate to Settings > General > VPN & Device Management > Device Manager > More Details > Certificates and locate the ISE certificate delivered by Workspace ONE UEM, the device GUID can be located under the Subject Alternative Name item.

In case the GUID is not set correctly, check the certificate template in Workspace ONE UEM as described in Step 1. Prepare Certificate Template for ISE.
Network Troubleshooting
In case you have network connectivity issues, or other ISE-related issues and have already verified that the profile and certificate are properly set up on the device, refer to the following Cisco Identity Services Engine Administrator Guide, Release 3.3 and Cisco Troubleshooting Technotes.
Summary and Additional Resources
Workspace ONE UEM and Cisco ISE integration increases network security to corporate networks, allowing organizations to leverage device compliance information to determine access to corporate networks, as well as address recent limitations caused by MAC address randomization and device level API restrictions implemented by several operating systems. The new integration enables Cisco ISE to leverage a unique device identifier provided by Workspace ONE UEM to continue to query device compliance information and no longer rely on MAC addresses.
Additional Resources
To learn more about Workspace ONE UEM and Cisco ISE integration, you can explore the following resources:
- Enforcing password rotation on API accounts used for Cisco ISE integration
- Streamlining Device Compliance and Tags with Workspace ONE UEM
- Cisco Identity Services Engine Administrator Guide, Release 3.3
- Workspace ONE UEM Resource Page
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2025/01/06 | Update UEM version requirements for Cisco ISE Integration. |
| 2024/03/20 | Guide was published. |
About the Author and Contributors
This document was written by:
Feedback
Your feedback is valuable.
To comment on this paper, either use the feedback button or contact us at tech_content_feedback@omnissa.com

