Best practices for managing Microsoft BitLocker with Workspace ONE UEM
Overview
Omnissa Workspace ONE® UEM empowers administrators to configure BitLocker encryption on managed Windows Desktop devices. Through the Encryption profile, administrators can establish native BitLocker encryption policies, ensuring data security. Additionally, Workspace ONE UEM generates and stores recovery keys within the console, accessible via the self-service portal. Workspace ONE UEM facilitates the configuration of BitLocker To Go, a drive encryption technology for removable data drives.
What Is BitLocker encryption?
Microsoft BitLocker, a volume encryption feature introduced with Windows Vista, has become a crucial security component for many commercial and enterprise organizations. It addresses data loss from stolen, lost, or improperly decommissioned computers by encrypting operating systems and fixed data volumes.
BitLocker can use the following encryption methods:
- AES CBC 128-bit
- AES CBC 256-bit
- XTS AES 128-bit
- XTS AES 256-bit
For more information, see Microsoft Docs: BitLocker Overview.
What is BitLocker To Go?
BitLocker To Go (BL2Go) is a Windows tool that encrypts removable data drives to prevent unauthorized access. BL2Go can use a password, smart card, or a recovery key to decrypt removeable devices, such as:
- USB flash drives
- SD cards
- External hard disk drives
BL2Go can encrypt removable data devices that are formatted using the following file systems:
- NTFS
- FAT32
- FAT16
- exFAT
For more information, see Microsoft Docs: BitLocker To Go FAQ.
Workspace ONE UEM encryption profiles for Windows desktop
Workspace ONE UEM provides a comprehensive set of options for deploying and managing BitLocker on a Windows Desktop device. These options allow administrators to secure devices using native BitLocker encryption. The following settings are available in the encryption payload.
Table 1: Workspace ONE UEM Encryption Profile Settings
| Settings | Description |
| Encrypted Volume | Workspace ONE UEM gives you the option to encrypt all hard disks on the device, or only the system partition. See Configure Hard Drives as a Single Volume Rather than Multiple Volumes for OS and Data for recommendations related to this setting. |
| Encryption Method | This setting identifies the method to be used at the time the hard disk(s) are encrypted. The available options are:
The Default option will use the default encryption method specified by the OEM. |
| Only Encrypt Used Space During Initial Encryption | When this option is selected, BitLocker will only encrypt used space on the hard disk at the time of encryption. |
| Custom URL for Recovery Key | You can specify the URL used by end users to get the recovery key for their device. Because Workspace ONE UEM hosts the recovery keys in the Self-Service Portal, you should consider using that as the URL. |
| Force Encryption | This option will force re-encryption of the device if BitLocker is manually deactivated. See Carefully Consider Options Such as Force Encryption and Always Keep System Encrypted for recommendations on the use of this setting. |
| Keep System Encrypted at All Times | When selected, this option ensures that the device remains encrypted, even during device wipes, profile removals, or disconnects from Workspace ONE UEM. See Carefully Consider Options Such as Force Encryption and Always Keep System Encrypted for recommendations on the use of this setting. |
| BitLocker Authentication Settings: Authentication Mode | End users must authenticate before accessing an encrypted device. This option allows you to select the authentication method to be used. The methods available are:
See Use TPM Instead of Password Protectors for recommendations on this setting. |
| BitLocker Authentication Settings: Require PIN at startup | When selected, this option requires the user to enter a PIN prior to operating system start up or auto-resume from suspend or hibernate mode. |
| BitLocker Authentication Settings: PIN Length | Use this option to specify the required length of the startup PIN. By default, the PIN will be numeric. If additional complexity is required for the PIN, you can configure Allow Enhanced PIN at Startup. |
| BitLocker Authentication Settings: Allow Enhanced PIN at Startup | If you require a more complex PIN, select this option to activate the use of uppercase and lowercase letters, symbols, numbers, and spaces. |
| BitLocker Authentication Settings: Use Password if TPM Not Present | This option will allow a password to decrypt the device if TPM is unavailable. |
| BitLocker Authentication Settings: Suspend BitLocker until TPM is initialized | This option will postpone the encryption of a device until TPM is initialized, which can be useful for Out-of-Box Experience (OOBE) enrollments. |
| BitLocker Authentication Settings: Minimum Password Length | Use this option to set the minimum number of required characters for a password. |
| BitLocker Static Recovery Key Settings: Create Static BitLocker Key | This option activates a static recovery key that is shared across a group of devices. |
| BitLocker Static Recovery Key Settings: BitLocker Recovery Password | Click the Generate icon to create a new recovery key. |
| BitLocker Static Recovery Key Settings: Rotation Period | Use this option to specify the number of days for recovery key rotation. |
| BitLocker Static Recovery Key Settings: Grace Period | This option configures the number of days that the previous recovery key will continue to work after rotation. |
| BitLocker Suspend: Activate BitLocker Suspend | The setting activates BitLocker Suspension, which suspends BitLocker encryption during specified times such as scheduled updates. BitLocker Suspension allows the device to reboot without the need for an encryption PIN or password. |
| BitLocker Suspend: Suspend BitLocker Type | With this option, you can select to either activate BitLocker Suspension on a recurring schedule or specify a Custom day and time. |
| BitLocker Suspend: BitLocker Suspend Start Time | This option allows you to specify the start time for BitLocker Suspend. |
| BitLocker Suspend: BitLocker Suspend End Time | Use this option to specify an end time for BitLocker Suspend. |
| BitLocker Suspend: Scheduled Repeat Type | With this option, you can set the type of recurrence for BitLocker Suspend. You select daily or weekly. |
Purpose of this tutorial
The purpose of this guide is to provide recommendations and considerations for how to best configure BitLocker settings and policies on Windows Desktop devices managed by Workspace ONE UEM. The best practices outlined in this document are based on customer experiences and engineering feedback.
Audience
This guide is intended for IT professionals and Workspace ONE UEM administrators of existing production environments who manage Windows Desktop devices with Intelligent Hub.
Knowledge of additional technologies such as encryption, Windows Desktop device management, and Omnissa Workspace ONE® UEM is also helpful.
Best practices and considerations
The following items should be considered before creating and configuring an encryption profile for Windows Desktop devices in Workspace ONE UEM.
Use TPM instead of password protectors
BitLocker can encrypt the Windows operating system on a computer lacking a Trusted Platform Module (TPM) version 1.2 or later. However, it’s advisable to use TPM whenever feasible. With the release of Windows 8, BitLocker can protect the operating system volume on a TPM-less computer using either a USB startup key or an operating system volume password. Nevertheless, neither option offers the system integrity verification BitLocker provides when TPM is present. Setting TPM as the authentication mode for BitLocker ensures the most secure option for device encryption.

Figure 1: BitLocker Authentication Mode in Workspace ONE UEM
Configure hard drives as a single volume rather than multiple volumes for OS and data
When Workspace ONE UEM sends a BitLocker Profile to a computer with multiple volumes, the operating system partition is assigned a newly created numerical protector. The additional volumes are assigned Auto Unlock protectors that will unlock the volumes with the OS volume. Although Workspace ONE UEM maintains recovery keys for all hard drives, recovering multiple logical volumes on a single hard disk can introduce additional complexities. Therefore, it is recommended to configure a single volume per hard disk for the OS, applications, and data.
Allow Workspace ONE UEM to manage the full BitLocker lifecycle
Microsoft provides several mechanisms for enabling and managing BitLocker on computers, including Microsoft Intune, Endpoint Configuration Manager, and Microsoft BitLocker Administration and Monitoring (MBAM). For managed Windows Desktop devices, the recommended approach is to create a device profile in Workspace ONE UEM to activate BitLocker. This involves enrolling the device in Workspace ONE UEM before enabling BitLocker and allowing UEM to manage BitLocker settings. Introducing BitLocker GPO settings, other management tools, or manual enablement can lead to unintended complexities and issues in the environment.
When a BitLocker-encrypted Windows Desktop device is enrolled in Workspace ONE UEM and a device profile for managing BitLocker is applied, new UEM-specific protectors are added to the existing ones. If the encryption profile is removed, all protectors are removed from the device.
However, there are situations where existing protectors cannot be used with Workspace ONE UEM, such as password protectors on an operating system volume.
Considering these potential complexities, it is recommended to manage the entire lifecycle of BitLocker through Workspace ONE UEM, including profile installation, encryption, management, and decryption during decommissioning.
Avoid end user pre-encryption prior to enrollment
End users can activate BitLocker on their devices through the Control Panel applet in Windows. However, as mentioned earlier, pre-enrollment BitLocker encryption can cause issues after a device is enrolled in Workspace ONE UEM and a BitLocker device profile is applied. Therefore, it’s advisable to avoid pre-enrollment BitLocker encryption and let Workspace ONE UEM manage the entire BitLocker lifecycle.
When removing encryption profiles, avoid rebooting the PC until the decryption process is complete
When an encryption profile is removed from a Workspace ONE UEM-managed Windows Desktop device, BitLocker initiates the decryption process of the protected volumes. However, before the release of version 2206 of the Workspace ONE UEM console, there was a potential risk of data loss if a Windows device was rebooted during the decryption process. In such a rare scenario, the Auto Unlock protector and numerical password protector were removed from the device when the decryption commenced. If the device was rebooted before the decryption process was complete, there would be no active recovery keys available.
To address this issue, Workspace ONE UEM introduced a change with version 2206, ensuring that the protectors remain on the device until the decryption process is fully completed. Nevertheless, it is still advisable to refrain from rebooting the Windows Desktop device until the decryption process is finished. This precaution ensures the integrity of the data on the volumes being decrypted.
Carefully consider options such as Force Encryption and Always Keep System Encrypted
When activated, the Force Encryption option in BitLocker monitors for attempts to manually deactivate encryption on the Windows Desktop device. This can happen if the user has administrative privileges and deactivates BitLocker from the Control Panel applet. If a status change is detected, Force Encryption will automatically re-activate encryption. However, this feature may cause complications during operations where system processes expect BitLocker to be suspended, such as BIOS updates, hardware changes, Windows Updates, and device wipes and resets. Version 2206 of Workspace ONE UEM has resolved this issue regarding device wipes, but users with prior console and hub version combinations may still be affected. Users without administrative privileges on the Windows Desktop device don’t need Force Encryption activated.

Figure 2: Force Encryption setting in the Encryption Payload
The Always Keep System Encrypted option ensures that the Windows Desktop device remains encrypted even if actions occur that remove device profiles, such as wiping, resetting, removing Intelligent Hub, or disconnecting from the work/school account. Any of these events can remove device profiles, including profiles that activate BitLocker. When activated, the Always Keep System Encrypted option prevents the volume from being decrypted, and the Workspace ONE UEM console retains the recovery keys. While this feature provides data security in case of device wiping due to loss or theft, it can be problematic if Intelligent Hub is intentionally removed for troubleshooting purposes.
Figure 3: Keep System Encrypted at All Times setting in the Encryption Payload
Use caution when using Group Policy to manage BitLocker on devices enrolled in Workspace ONE UEM
BitLocker settings can be managed in various ways, including using Active Directory Group Policy (GPO). Workspace ONE UEM device profiles include a subset of the settings available in Group Policy. However, when using both Group Policy and device profiles to manage BitLocker, there’s a risk of GPO settings being unintentionally overridden by those in Workspace ONE UEM device profiles, and vice versa. This potential conflict can lead to unexpected system behaviors that may affect access to encrypted volumes.
Therefore, it’s crucial to be aware of the BitLocker configurations in both GPOs and device profiles and carefully consider their impact on each other. By doing so, you can minimize the potential impact caused by conflicting policies.
BitLocker To Go password complexity and minimum length requirements are not displayed in the graphical user interface
BitLocker To Go (BL2Go) provides drive encryption for removable data drives, such as USB flash drives, SD cards, and external hard disk drives. When the BL2Go feature is activated, a password screen appears when a removable drive is attached to the Windows device. The graphical user interface (GUI) for BL2Go indicates that the minimum character requirement for the password is eight (8). The GUI does not, however, indicate if additional complexity or character length requirements have been set through local policy or group policy. This can result in potential user experience issues if additional complexity is required of which the user is unaware.
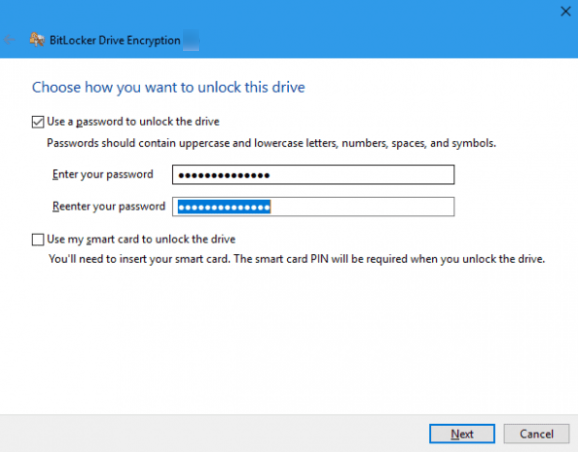
Figure 4: BitLocker to Go password screen
Use Single Use Recovery Keys for BitLocker
Recovery keys for encrypted volumes are stored in the Workspace ONE UEM console and can be accessed through the self-service portal or by contacting the organization’s helpdesk. Because of the static nature of the recovery key, it is possible for a user to save the key and re-use it later to unlock the volume. If the user keeps the key in an unsecure place, such as taped to the bottom of the Windows Desktop device, the device can be compromised if stolen, and information on the volume can be accessed. This can create a significant security vulnerability for an organization. To remediate this security risk, it is recommended that you use Single Use Recovery Keys for BitLocker.
As of Workspace ONE UEM version 2210, you can configure a Single Use Recovery Key for BitLocker. When using the Single Use Recovery Key option, Intelligent Hub detects when a volume is unlocked with a recovery key and generates a new recovery key which it sends back to the Workspace ONE UEM console for safe keeping. This ensures the integrity of the encrypted system by forcing the rotation of the recovery key and ensures that the user cannot re-use the existing recovery key later. The current recovery key remains active on the device until Intelligent Hub can confirm that the Workspace ONE UEM console has received the new recovery key. A successful rotation of the recovery key is noted in the console troubleshooting log allowing administrators to monitor ongoing operations.
Summary and additional resources
This tutorial provided several best practices and considerations for managing BitLocker on Windows Desktop devices with Workspace ONE UEM.
The best practices and considerations discussed include:
- Using TPM instead of password protectors for BitLocker encryption
- Configuring hard drives as single volumes rather than multiple volumes for OS and data
- Allowing Workspace ONE UEM to manage the full BitLocker lifecycle
- Avoiding end user pre-encryption prior to device enrollment into Workspace ONE UEM
- Avoiding reboots after device encryption profiles removal until the decryption process completes
- Careful consideration when using options such as Force Encryption and Always Keep System Encrypted
- Being cautious when using Group Policy to manage BitLocker on devices enrolled in Workspace ONE UEM
- Being aware that BitLocker to Go password complexity and minimum length requirements are not displayed in the graphical user interface
- Utilizing Single Use Recovery Keys for BitLocker
For more operational tutorials on Workspace ONE UEM, check out the Tech Zone.
Additional resources
For more information about Workspace ONE UEM, you can explore the following resources:
- Enabling BitLocker Encryption to Remote Windows Devices
- Omnissa Workspace ONE UEM: BitLocker Encryption – Feature Walk-through
- Workspace ONE UEM Production Documentation – Encryption Profile (Windows Desktop)
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 01/20/2026 |
|
| 08/06/2024 |
|
| 10/18/2022 |
|
About the author and contributors
This tutorial was written by:
- Michael Bradley, Senior Product Specialist, Omnissa
With significant contribution by:
- Kevin Sheehan, Omnissa Alumni.
Questions and feedback
For questions or feedback, send to tech_content_feedback@omnissa.com.

