Configuring Web Reverse Proxy and Identity Bridging in Unified Access Gateway
Overview
Omnissa provides this operational tutorial to help you with your Omnissa Workspace ONE UEM environment. In this tutorial, you configure a web reverse proxy instance to access an intranet website using certificate-based authentication on the Unified Access Gateway. You also configure two modes for Identity Bridging; SAML to Kerberos and Certificate to Kerberos.
Audience
This operational tutorial is intended for IT professionals and Workspace ONE UEM administrators of existing production environments.
Knowledge of additional technologies such as network, VPN configuration, Workspace ONE® Intelligence and Workspace ONE® UEM is also helpful.
Configuring Web Reverse Proxy and Device Certificate Authentication
The web reverse proxy feature in Unified Access Gateway enables external access to internal websites.
This section helps you to configure a web reverse proxy instance to access an intranet website using device certificate as authentication method on the Unified Access Gateway.
The exercises cover Unified Access Gateway 3.3.1 deployment and in vSphere 6.5 U1. Procedures include:
- Deploying the Unified Access Gateway appliance.
- Configuring web reverse proxy to access both SSL and non-SSL websites.
- Adding certificate-based authentication to an intranet website.
The steps are sequential and build upon one another, so make sure that you complete each step before going to the next step.
Architecture
The architectural diagram below shows an example environment which emulates a typical environment, including DMZ and internal networks.
In this example, external requests to the vApp are sent to the vPod Router, which directs those requests to the appropriate resource, based on the incoming port. Ports 4000-6500 are reserved for the environment components so all traffic coming in on these ports is forwarded to the appropriate Edge Service for the Unified Access Gateway server. In addition, ports 443 and 9443 are forwarded to the Unified Access Gateway server over the respective ports.
The vApp networks (internal, DMZ, and transit) are created within the vApp. The internal and transit networks are NATed to the SE- UCS-Network for outbound internet connectivity while the DMZ network routes through the vPod Router for inbound and outbound access. Note that the vPodRouter does not have a NIC on the internal network and therefore cannot route external traffic to resources on the internal network.
vPod Router | ESXi01 6.5.0 U1 | Control Center | vCenter Server 6.5 U1 hosted on ESXi01
Architecture Overview Diagram
The following architectural diagram shows an example of two major networks that you can deploy your servers into. For this set of exercises, you deploy the Unified Access Gateway appliance on a DMZ and assign the respective NICs.
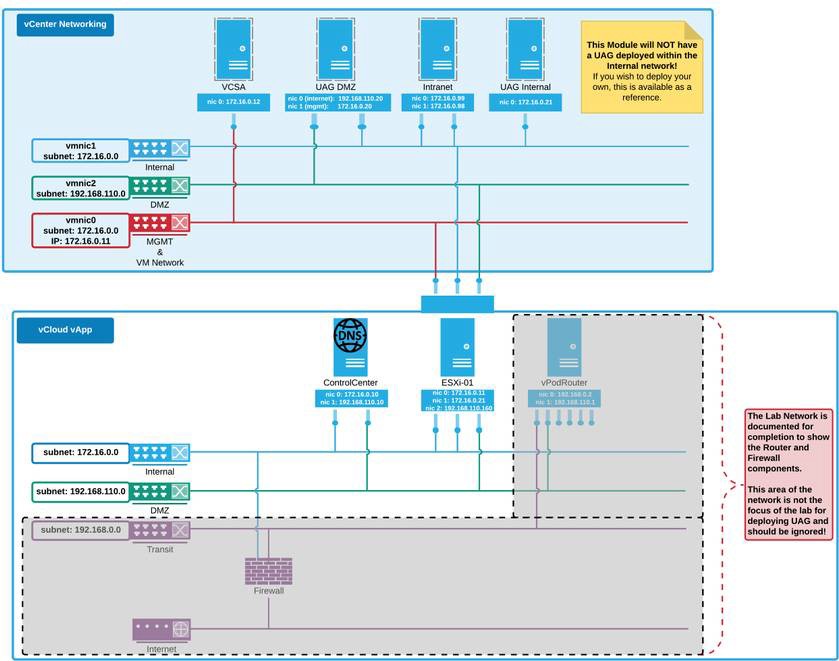
At the top of the diagram is vCenter Networking. At the bottom of the diagram is the vApp network required to support the environment. For these exercises, the focus is on the network hosted on the ESXi, and represented by the following three networks:
- VM Network & Management: Represents the dedicated network to access the Management Console.
- Internal Network: Represents the internal network on 172.16.0.x range. The Control Center, ESXI, and vCenter are part of the internal network.
- DMZ Network: Represents the DMZ network on 192.168.110.x which is where the Unified Access Gateway appliance is to be deployed. The Unified Access Gateway Internet-facing NIC is associated to this network.
Network Interfaces
Unified Access Gateway supports deployments with one, two, or three NICs. This means that the server can be partitioned to receive traffic on a single interface or to route traffic to different interfaces, based on the source of the request. Most often, if you need to implement multiple NICs, you already follow this standard with other web applications in your organization.
You must determine what is appropriate for your environment when selecting the number of NICs during installation. It is important for you to understand the expected behavior when two or three NICs are enabled.
To explore these options, see Deploying Unified Access Gateway: Workspace ONE Operational Tutorial.
General Considerations
In the exercises for deploying the Unified Access Gateway server through vSphere, the vCenter setup is hosted in a nested template. This is not usually the case when working with users in a live environment.
User environments can include multiple networks and can optionally have a Network Protocol Profiles (NPP) that corresponds to the networks to connect to the Unified Access Gateway. Prior to version 3.3, NPP was a requirement. Since version 3.3, NPP is no longer required.
Note: Keep in mind that the Unified Access Gateway requires a netmask, default gateway, and subnet to be defined for each network enabled during deployment.
Prerequisites
Before you can perform the steps in this exercise, you must install and configure the following components:
- Omnissa Workspace ONE UEM SaaS or on-premises latest version.
- vSphere ESX host with a vCenter Server (vSphere 6® and later).
- vSphere data store and network to use.
- PowerShell script running on Windows 8.1 or later machines, or Windows Server 2008 R2 or later.
- Windows machine running the latest PowerShell script with OVF Tool command installed.
- Unified Access Gateway PowerShell script, such as uagdeploy-VERSION.ZIP (download from my.workspaceone.com, and extract the files into a folder on your Windows machine).
- Obtain a Unified Access Gateway virtual appliance image OVA file, such as .euc-access-point-3.3.X.X-XXXXXXXXXXX.ova (see Omnissa Product Interoperability Matrixes to determine which version to download).
- CA Root and Intermediate certificate, and user certificate to configure Device Certificate Authentication.
Logging In to the vSphere Web Client
To perform most of this exercise, you need to log in to the vSphere Web Client.
- Launch Chrome Browser
- Authenticate to the vSphere Web Client
After completing the login, you are presented with the vSphere Web Client.
Preparing Unified Access Gateway INI Settings for Deployment
This section covers the required INI settings to configure Unified Access Gateway appliance during deployment.
Configure the General Deployment Settings
An INI file containing all the configuration settings is required to deploy the Unified Access Gateway appliance. In this exercise, you use the uag-appliance.ini file to provide the respective parameters for your deployment.
You deploy a new Unified Access Gateway appliance called UAG02 in the example, and which has two NICs. NIC1 is Internet-facing and NIC2 is for back end and management.
Open the uag-appliance.ini File for Editing
Navigate to the uag-appliance.ini file. In this example, the INI file is located in UAG Resources.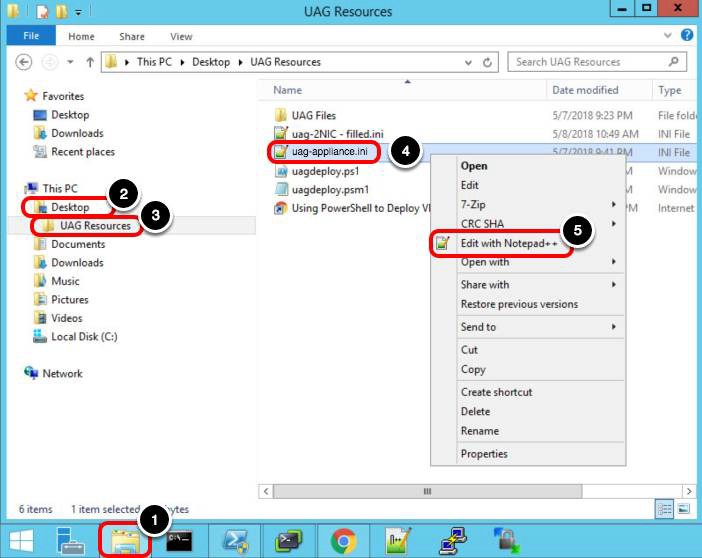
- Click the File Explorer icon on the task bar.
- Click Desktop.
- Click UAG Resources.
- Right-click the
uag-appliance.inifile. - Click Edit with Notepad++.
Configure General Settings (1/2)
In the General section, provide the following settings: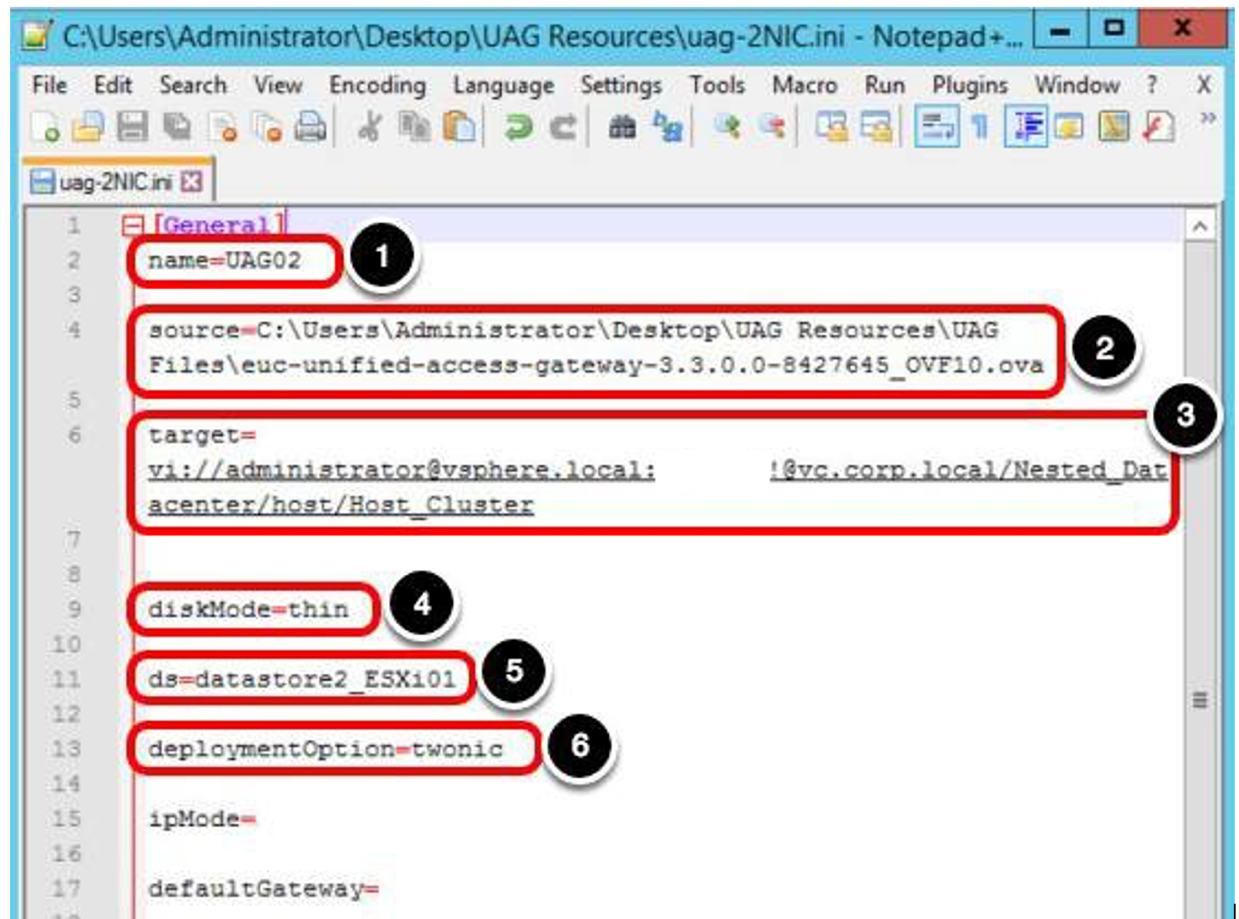
- In the name field, enter a name, such as UAG02 in this example.
- In the source field, enter the path, such as C:\Users\Administrator\Desktop\UAG Resources\UAG Files\euc-unified- access-gateway-3.3.0.0-8539135_OVF10.ova, and use File Explorer to verify that the OVA file has the name indicated.
- In the target field, enter the destination path, such as vi://administrator@vsphere.local:password@vc.corp.local/Nested_Datacenter/host/Host_Cluster. Note: You can replace the password with 'PASSWORD' and the script prompts for the password during the PowerShell execution.
- In the diskmode field, enter thin.
- In the ds field (ds refers to data store), enter datastore2_ESXi01.
- In the deploymentOption field, enter twonic.
Configure General Settings (2/2)
Continue with the General section configuration, configure the following parameters in the INI file. Keep in mind that ip0 is the Internet-facing NIC, and ip1 is the internally facing NIC.
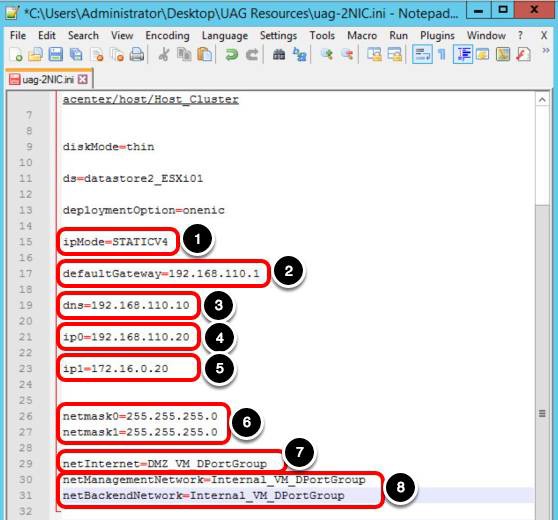
- For ipMode, enter STATICV4.
- For defaultGateway, enter 192.168.110.1 .
- For dns, enter 192.168.110.10.
- For ip0, enter 192.168.110.20.
Note: ip0 is the Internet-facing NIC.
- Enter 172.16.0.20 for the ip1 field.
Note: ip1 is the internally facing NIC.
- For netmask0 and netmask1, enter 255.255.255.0.
- For netInternet, enter DMZ_VM_DPortGroup.
- For netManagementNetwork and netBackendNetwork, enter Internal_VM_DPortGroup.
Configure the TLS/SSL Certificates
SSLCert and SSLCertAdmin contain SSL certificate information for the administration and Internet interfaces.
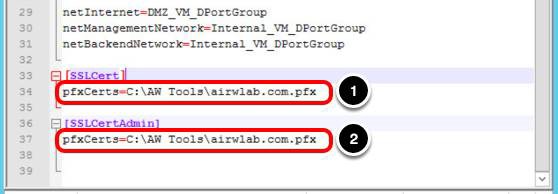
- For pfxCerts under SSLCert, enter
C:\AWTools\airwlab.com.pfx
(this certificate is for the Internet interface). - For pfxCerts under SSLCertAdmin, enter
C:\AW Tools\airwlab.com.pfx
(this certificate is for the administration interface).
The certificate password is requested during the deployment.
Deploying Unified Access Gateway Appliance
After you have configured the INI file for your Unified Access Gateway deployment, the next step is to run the uagdeploy.ps1 PowerShell script passing the INI as a parameter.
Deploy Unified Access Gateway Using PowerShell
Open PowerShell and run the script. The script prompts for input after you run it.
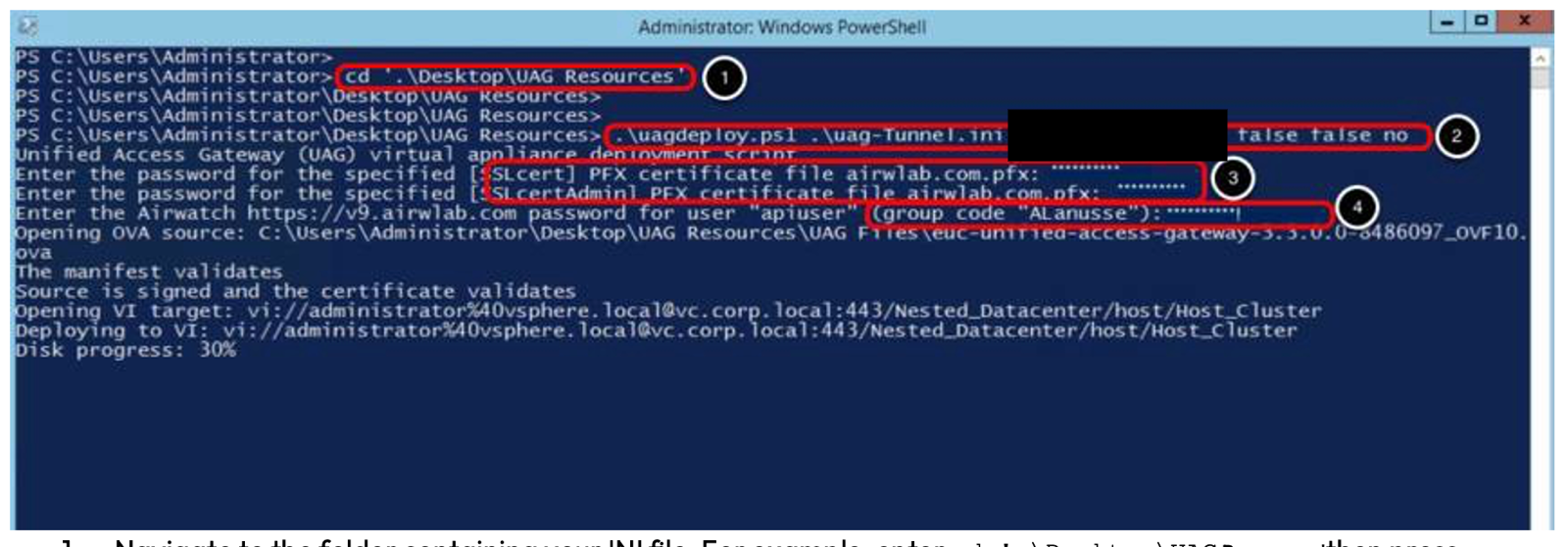
- Navigate to the folder containing your INI file. For example, enter
cd'.\Desktop\UAGResources' then press Enter. - Enter
.\uagdeploy.ps1 .\<uag-tunnel>.ini <password1> <password2> false false no
then press Enter. Replace<uag-tunnel>with your INI file name.
Replace <password1> with the root password for the Unified Access Gateway appliance. Replace <password2> with the administrator password for REST API management access. The first false is to not skip the validation of signature and certificate.
The second false is to not skip SSL verification for the vSphere connection. The no is to not join the CEIP program.
- Enter the password for the SSLcert and SSLcertAdmin fields, for example,
certpassword. - Enter the apiuser password, for example,
apiuserpasswordto allow Unified Access Gateway to obtain the Tunnel settings from Workspace ONE UEM.
To avoid a password request for the certificate, remove the pfxCert values and provide a PEM certificate in the INI file. Set the
pemCerts and pemPrivKey for the SSLCert and SSLCertAdmin sections in the INI file.
The deployment starts and you can follow the progress in the same window or on your vSphere Web Client.
Confirm the PowerShell Script Deployment Completes
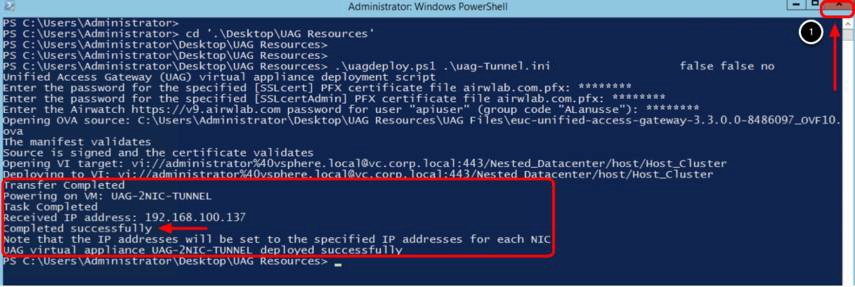
- Confirm the deployment has been completed successfully. The Completed successfully text is shown in the output.
- Click Close.
After a successful deployment, the script automatically powers on the VM UAG-2NIC-TUNNEL.
The Received IP address presented by the script log is a temporary IP; the final IPs for NIC one and NIC two are assigned to the Unified Access Gateway appliance during the first start. Return to the vSphere Web Client and validate the IP address in the next step.
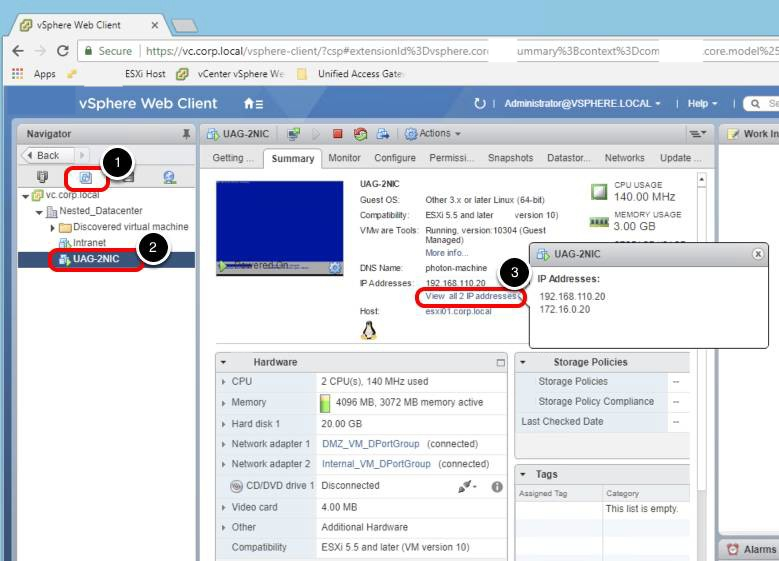
Validate Unified Access Gateway Deployment
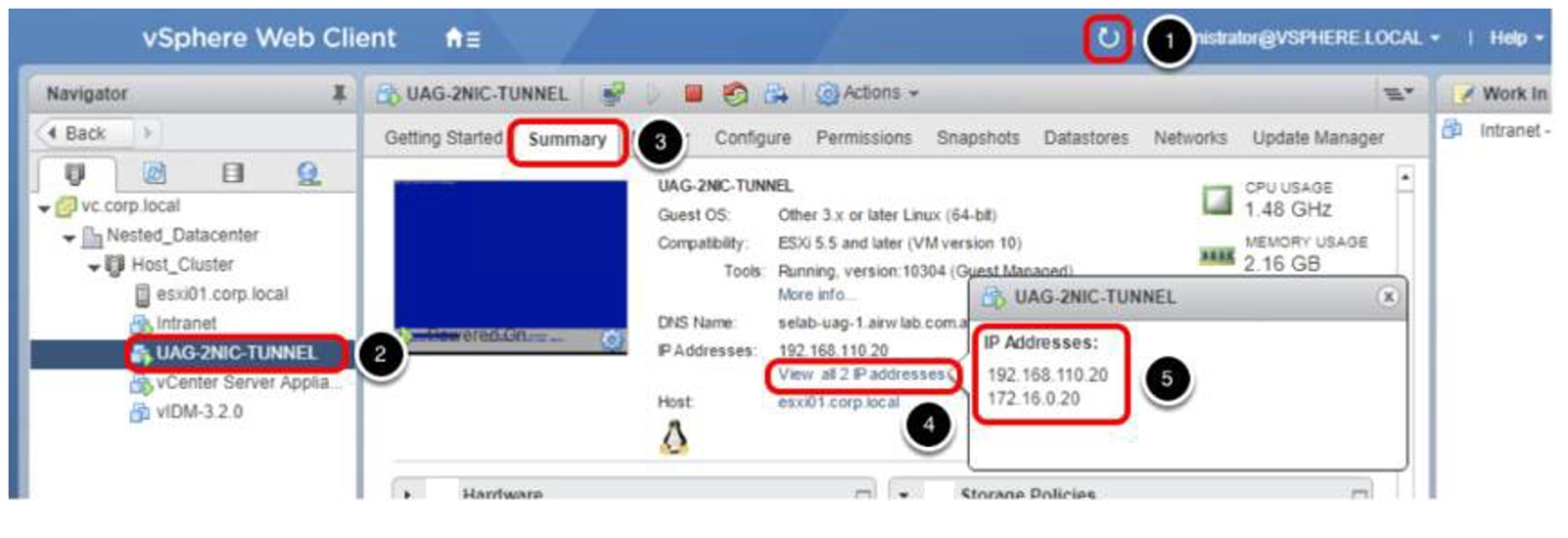
- If you do not see the UAG-2NIC VM under Nested_Datacenter, you may need to click Refresh first.
- Click UAG-2NIC-TUNNEL.
- Click the Summary tab.
- Click View all 2 IP addresses.
- The IP addresses in this example are 192.168.110.20 and 172.16.0.20.
Important: If the Unified Access Gateway appliance does not finalize the configuration during the first startup, you receive an error message from vSphere Web Client. If that happens, wait for the appliance to finalize, and refresh the entire Google Chrome browser.
Log In to Unified Access Gateway Administrator Console
Navigate to the Unified Access Gateway administration console URL (i.e.: https://uagmgt-int.airwlab.com:9443/admin) to perform the web reverse proxy configuration on the following steps.
Confirm Administrator Login to the Internal Network
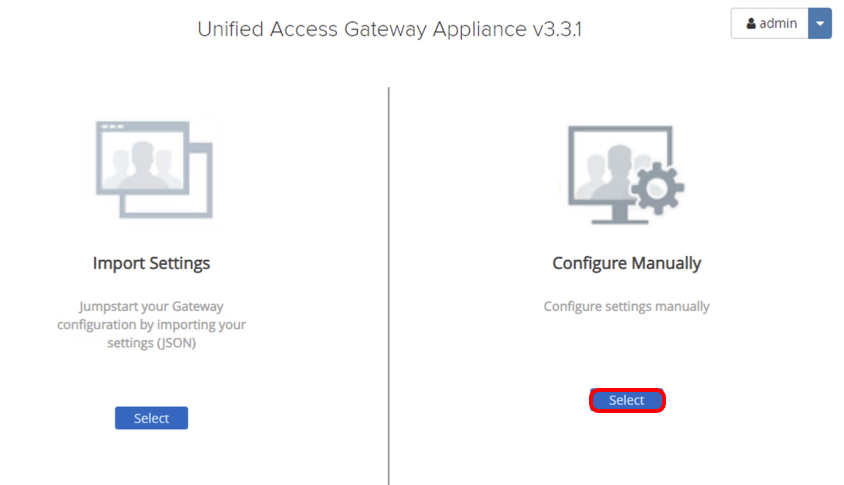
A successful login redirects you to the following screen. Keep this window open as you will return to the administration console later.
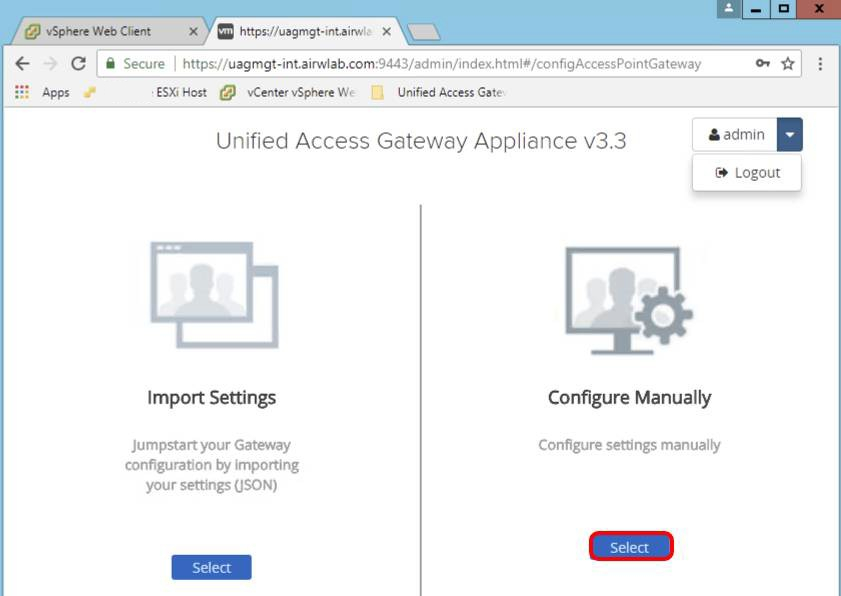
Click Select to configure settings manually.
Configuring Web Reverse Proxy to Access a Non-SSL Website
The Unified Access Gateway is now deployed, and you can access to the Unified Access Gateway administration console to update the appliance configuration.
This section helps you to configure Unified Access Gateway as a web reverse proxy, enabling external access to an internal website (intranet) hosted on an internal server. Communication occurs on HTTP/port 80.
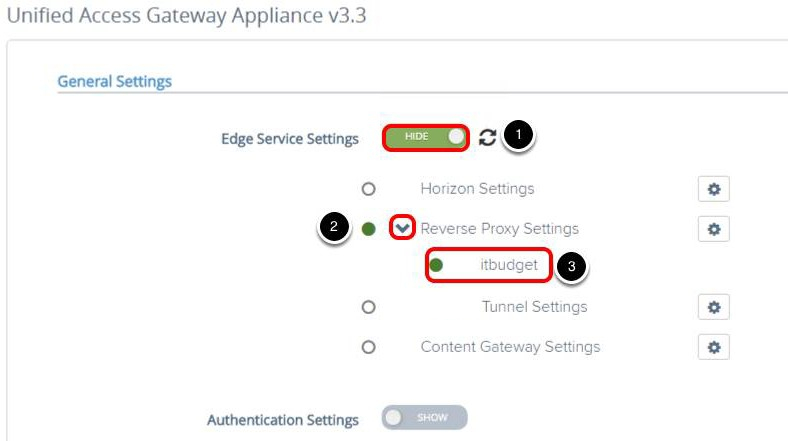
Access the Reverse Proxy Settings
- Click SHOW, after you click SHOW, it changes to HIDE.
- Click the Gear icon next to Reverse Proxy Settings.
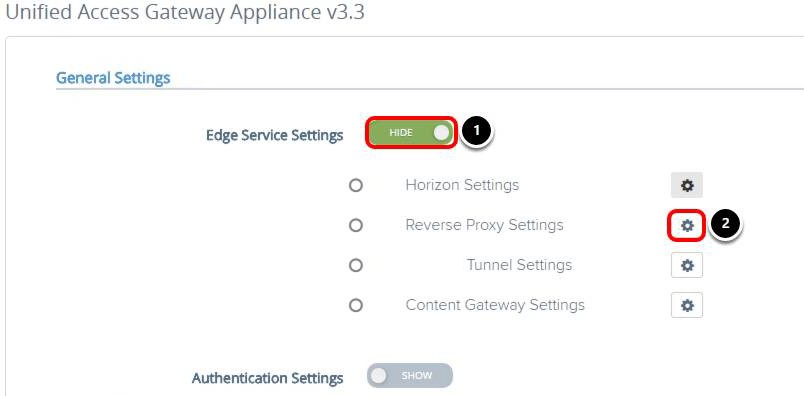
Add Reverse Proxy Settings
Click Add to create a new reverse proxy instance. You configure this new reverse proxy instance to access the intranet.
Define Features Used by Reverse Proxy
Click Enable Reverse Proxy Settings. The toggle changes to YES.
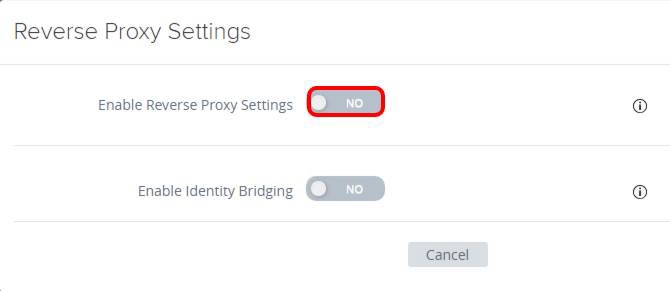
The Unified Access Gateway identity bridging feature can be configured to provide single sign-on (SSO) to legacy web applications that use Kerberos constrained delegation (KCD) or header-based authentication. The identity bridging feature is covered in Getting Started with Identity Bridging: Kerberos Setup.
Configure Intranet Reverse Proxy Settings
Configure the following reverse proxy settings.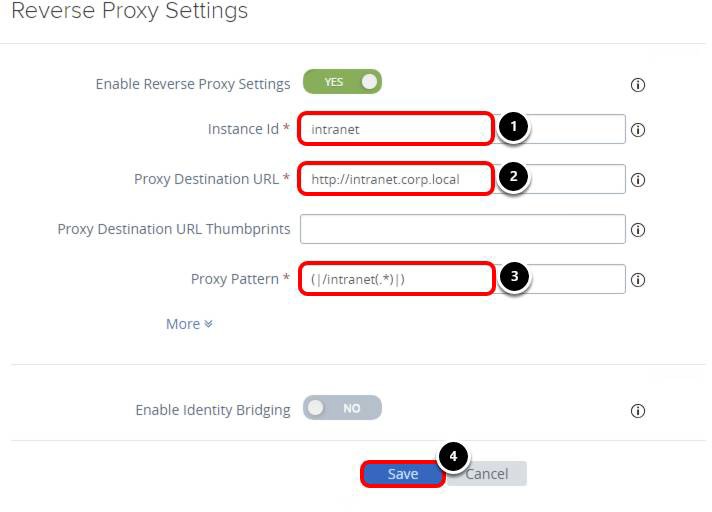
- Enter intranet for the Instance Id, which is a unique name to identify and differentiate a web reverse proxy instance from all other web reverse proxy instances.
- Enter a Proxy Destination URL, for example, http://intranet.corp.local. This URL represents the web application address on the internal network.
- Enter (|/intranet(.*)|) for Proxy Pattern, which specifies the value in regular expression format that matches the URIs that are related to the intranet URL (proxyDestinationUrl). For the intranet server, a forward slash intranet (/intranet) is the value used to access the intranet home page when using the Unified Access Gateway appliance.
- Click Save.
Additional parameters can be configured for this type of reverse proxy. For more details, see Configure Reverse Proxy with Workspace ONE Access in the Omnissa Unified Access Gateway Documentation.
Validate Reverse Proxy Configuration
Click Close to close the reverse proxy settings and then validate configuration.
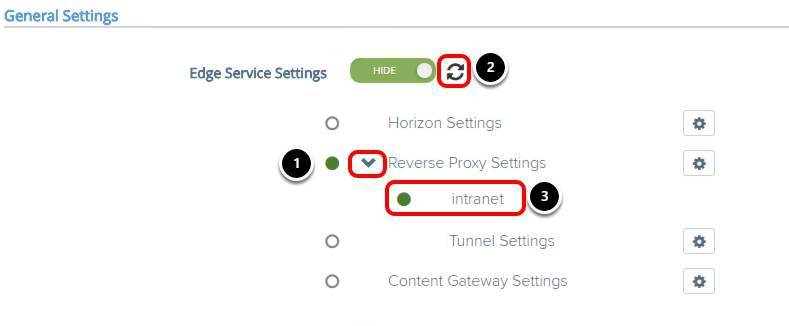
- Click the arrow for Reverse Proxy Settings.
- Click the refresh icon for the Edge Service Settings.
- Confirm the intranet proxy status is green.
After you add the reverse proxy settings for intranet, the Unified Access Gateway appliance tests the communication between the appliance and intranet. The status turns green if a connection is possible, otherwise, it turns red.
Note: It may take a few minutes for the intranet proxy to show as green. Click the refresh icon until the status changes to either green or red.
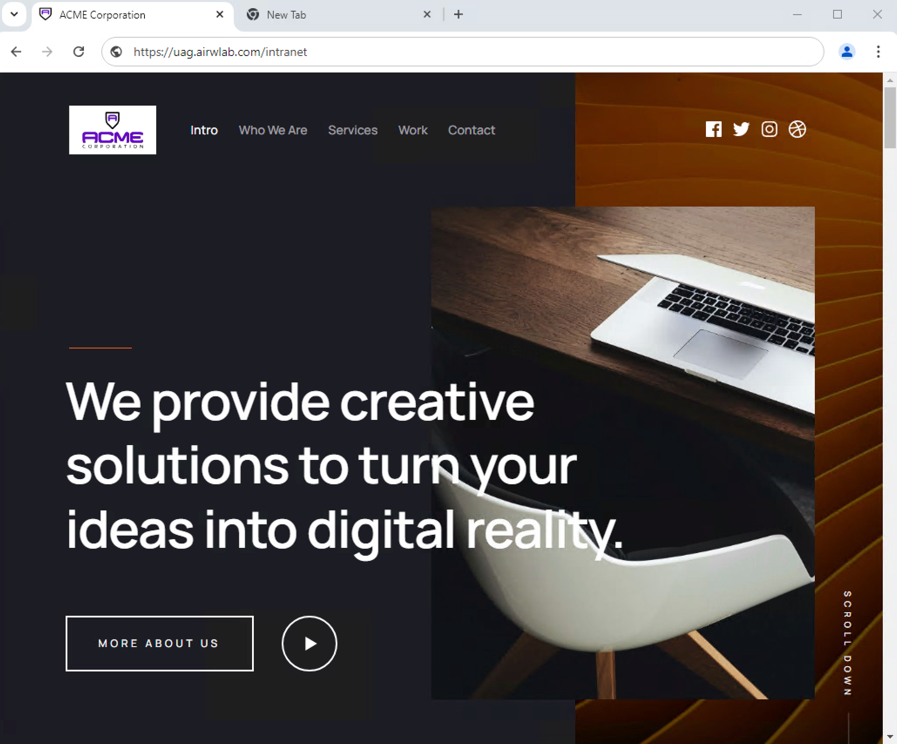
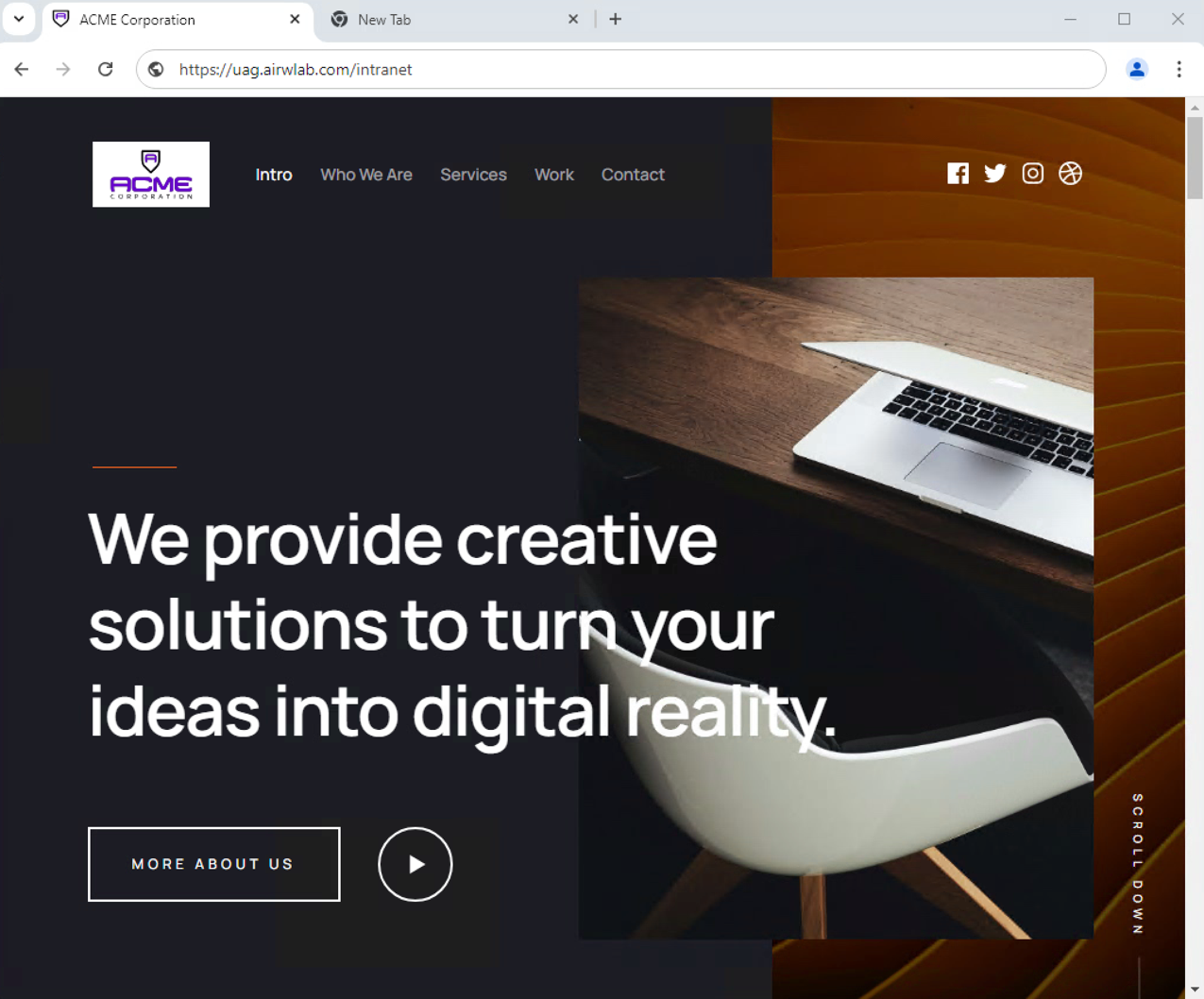
Access Intranet Through Reverse Proxy
- Click the New Tab button.
- Enter an intranet address, for example, https://uag.airwlab.com/intranet in the address bar and press Enter.

In this example, the result is a sample intranet page hosted on an internal IIS server.
- Access to the intranet is through Unified Access Gateway port 443, as result of the TLS port sharing configuration enabled by default during deployment.
- Access to the Unified Access Gateway administration console is through Unified Access Gateway port 9443 and IP 172.168.0.20, associated to the internal NIC.
Configuring Web Reverse Proxy to Access an SSL Website
To access an internal SSL website, additional configuration is required to establish trust between Unified Access Gateway and the internal website. This section helps you to configure the existing intranet reverse proxy instance to access an SSL website. Communication occurs on HTTPS/port 443.
Access the Reverse Proxy Settings
In the Unified Access Gateway administration console, click the Gear icon next to Reverse Proxy Settings.
Add Reverse Proxy Settings
Click the Gear icon to update the intranet configuration settings.
Configure Intranet Reverse Proxy Settings
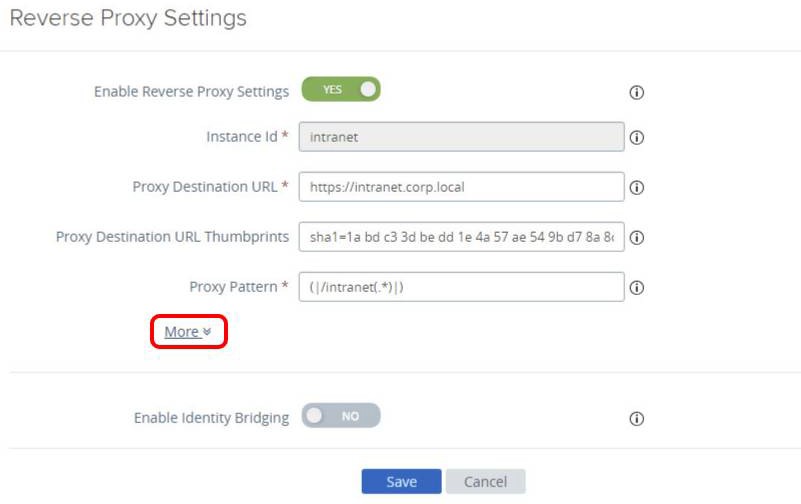
- Change the Proxy Destination URL to include https, for example,
https://intranet.corp.local. - Enter the Proxy Destination URL Thumbprints, for example,
sha1=1abd c3 3d be dd1e 4a 57 ae 549b d7 8a 8c 20cb
40 a5 59. This value represents the list of acceptable SSL server certificates.
- Click Save.
Note: A thumbprint is in the format [alg=]xx:xx, where alg can be sha1, the default, or md5. The xx values represent hexadecimal digits. The : separator can also be a space or omitted. If you do not configure the thumbprints, the server certificates must be issued by a trusted CA.
Additional parameters can be configured for this type of reverse proxy. For more details, see Configure Reverse Proxy with Workspace ONE Access in the Omnissa Unified Access Gateway Documentation.
Validate Reverse Proxy Configuration
Close the Reverse Proxy Settings and validate configuration.
- Click the arrow for Reverse Proxy Settings.
- Click the refresh icon for Edge Service Settings
- Confirm the intranet proxy status is green.
After you add the reverse proxy settings for intranet, the Unified Access Gateway appliance tests the communication between the appliance and intranet. The status turns green if a connection is possible, otherwise, it turns red.
Note: It may take a few minutes for the intranet proxy to show as green. Click the refresh icon until the status changes to either green or red.
Access Intranet Through Reverse Proxy
- Click the New Tab button.
- Enter a https address, for example, https://uag.airwlab.com/intranet in the address bar and press Enter.
In this example, the result is a sample intranet page hosted on an internal IIS server. However, Unified Access Gateway is now connecting to the intranet on port 443 using HTTPS.
- Access to the intranet is through Unified Access Gateway port 443, as result of the TLS port sharing configuration enabled by default during deployment.
- Access to the Unified Access Gateway administration console is through Unified Access Gateway port 9443 and IP 172.168.0.20, associated to the internal NIC.
Adding Certificate-Based Authentication to the Intranet Website
All users can access the intranet based on the current web reverse proxy configuration. You can restrict access to the intranet to some users by adding device certificate as the authentication method on the Unified Access Gateway appliance.
This section helps you to add certificate-based authentication and grant access to the intranet only for users who have a certificate installed on their device. The user certificate must match the root certificate set on the Unified Access Gateway appliance.
- Enable X.509 Certificate Settings.

In the Unified Access Gateway administration console:
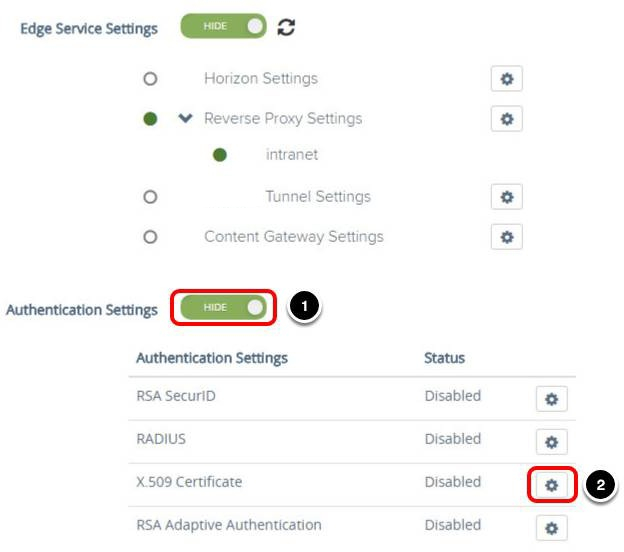
- Click SHOW next to Authentication Settings.
- Click the Gear icon next to X.509 Certificate.
Upload Certificate to Unified Access Gateway Appliance
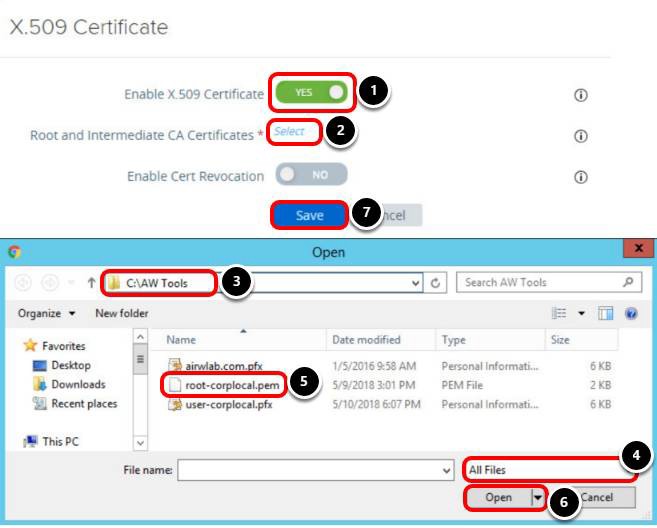
- Click NO to enable X.509 Certificate; after you click NO, it changes to YES.
- Click Select to upload the Root and Intermediate CA Certificates.
- Enter the path to your certificates, for example, C:\AW Tools and press Enter.
- Click the combo box and select All Files.
- Select your certificate, for example, root-corplocal.pem.
- Click Open.
- Click Save.

After you click Save, the message Configuration saved successfully appears. The certificate has been uploaded and added to the Unified Access Gateway Appliance certificate store.
Important: In this example, only the ROOT certificate is used during the authentication process. In a production environment, you will have ROOT and INTERMEDIATE certificates available, and you must upload both to the Unified Access Gateway appliance.
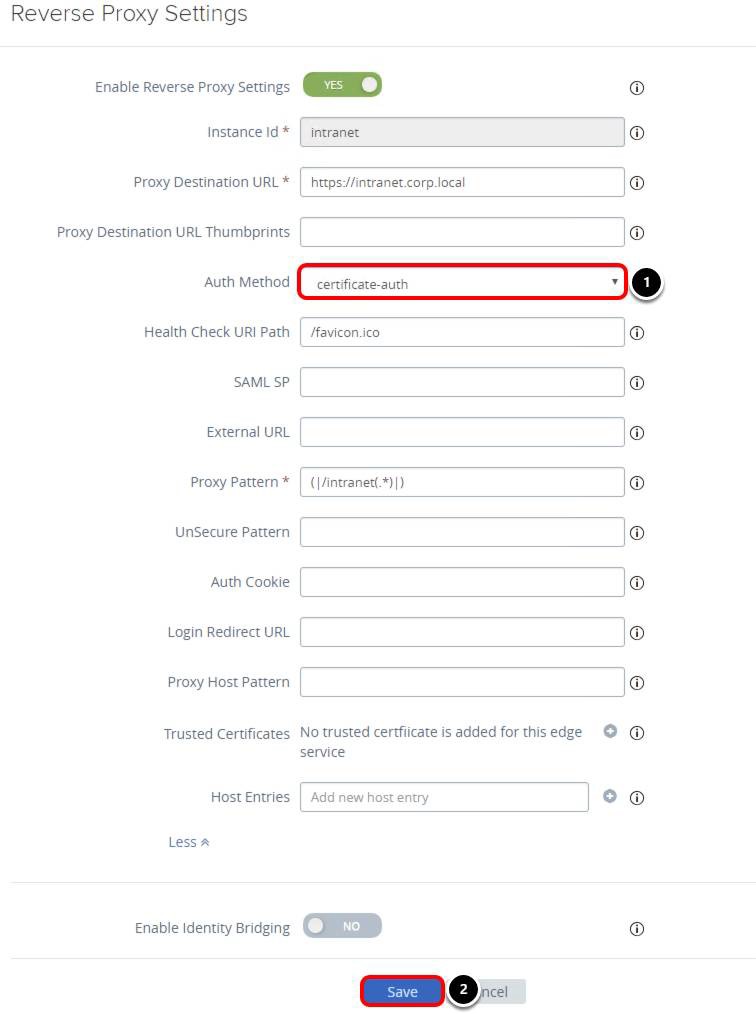
Enable Certificate Authentication for Intranet Website
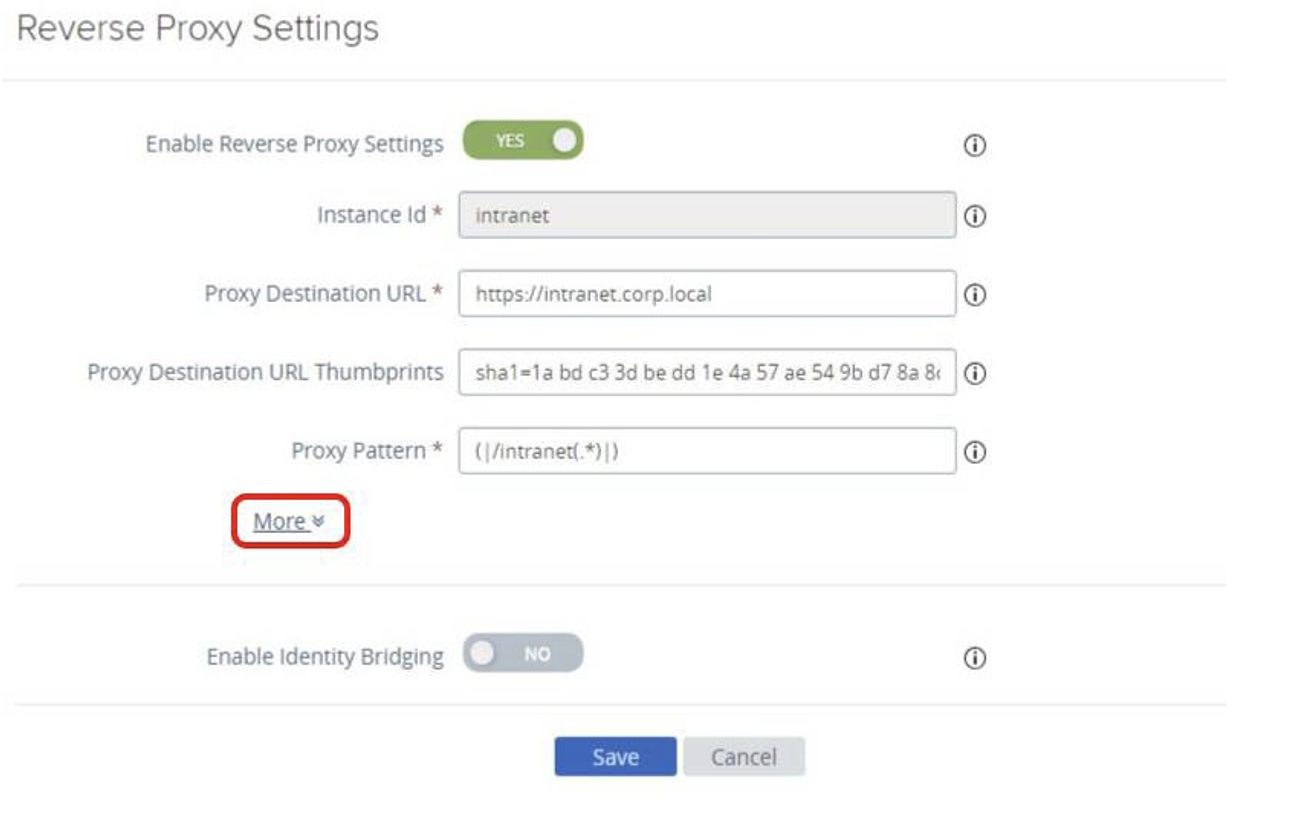
The next step is to configure Unified Access Gateway to require certificate authentication for intranet access. Select the Gear icon for Reverse Proxy Settings.
- Edit the Intranet Reverse Proxy Settings.
- Select the Gear icon for the intranet Instance.
- Configure Intranet Reverse Proxy Settings.
- Click More.

- Click More.
Configure the Authentication Method
- Select certificate-auth for Auth Method.
- Click Save.

Close the Reverse Proxy Settings
Click Close for the Reverse Proxy Settings.
Import the User Certificate to the Local Windows Store
- In Google Chrome, click the three dots next to the URL address bar.
- Click Settings.
- Access the Certificate Settings.
- Enter Certificate in the search text box
- Select Manage Certificates
- Choose Import Certificate.

- Click Import under the Personal tab.
- Click Next to start the import wizard.
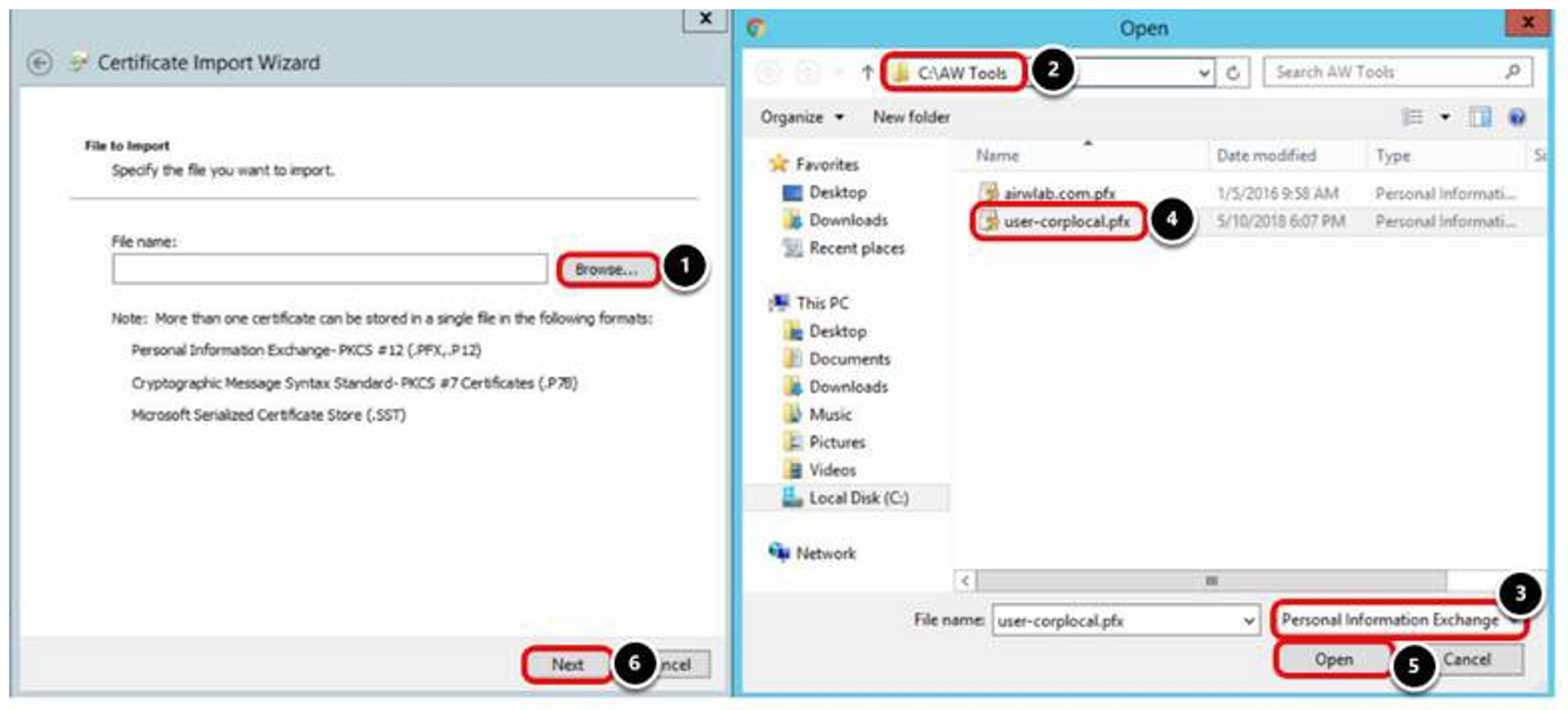
Select the User Certificate
- Click Browse.
- Enter the certificate path, for example, C:\AW Tools and press Enter.
- Click the combo box and select Personal Information Exchange (*.pfx).
- Select the user certificate, for example, user-corplocal.pfx. This user certificate should match the root certificate previously uploaded to the Unified Access Gateway appliance.
- Click Open.
- Click Next.

Enter the User Certificate Password
- Enter a Password.
- Click Next.
Choose the Personal Certificate Store
Keep the default selection and click Next.
The certificate will be imported to the Personal store.
Complete the Certificate Import Wizard
Click Finish to complete the wizard and then confirm that the import was successful.
Click OK. The list of certificates is refreshed and the user certificate is listed as part of the Personal Store. You have now imported the user certificate. The next step is to import the root certificate.
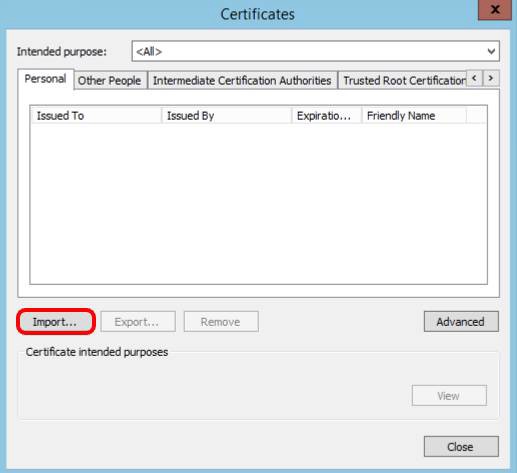
Import the Root Certificate to the Local Windows Store
Import the Root certificate to complete the client-side configuration.
- Select Trusted Root Certification Authorities.
- Click Import.
Start the Certificate Import Wizard
Click Next to start the wizard.
Choose the Root Certificate
- Click Browse.
- Enter the path to your root certificate, for example, C:\AW Tools and press Enter.
- Click the combo box and select All Files (*.*).
- Select the root certificate that was uploaded to the Unified Access Gateway appliance, for example, root-corplocal.pem.
- Click Open.
- Click Next.
Choose the Trusted Root Certification Authorities Store
Click Next to confirm that you want to import the certificate under the Trusted Root Certification Authorities Store.
Complete the Certificate Import Wizard
Click Finish.
Confirm the Certificate Warning and Install (If Prompted)
Click Yes to confirm the installation of the certificate.
Confirm the Certificate was Imported
Click OK.

Confirm the Root Certificate was Imported
- Confirm that your certificate is listed under Trusted Root Certification Authorities.
- Click Close.
Test the Certificate Authentication
- On Google Chrome, click the three dots next to the URL address bar.
- Click New incognito window.
- Navigate to the Intranet site.
- Enter an intranet address, for example, https://uag.airwlab.com/intranet/ and press Enter.
Select the User Certificate
All the certificates in the Personal store that match the root certificates installed on the Unified Access Gateway appliance, are shown on the certificate list. In this exercise, only one root certificate was uploaded for the domain intranet.corp.local, and there is only one certificate on the key store that matches this root. Therefore, only one certificate is listed.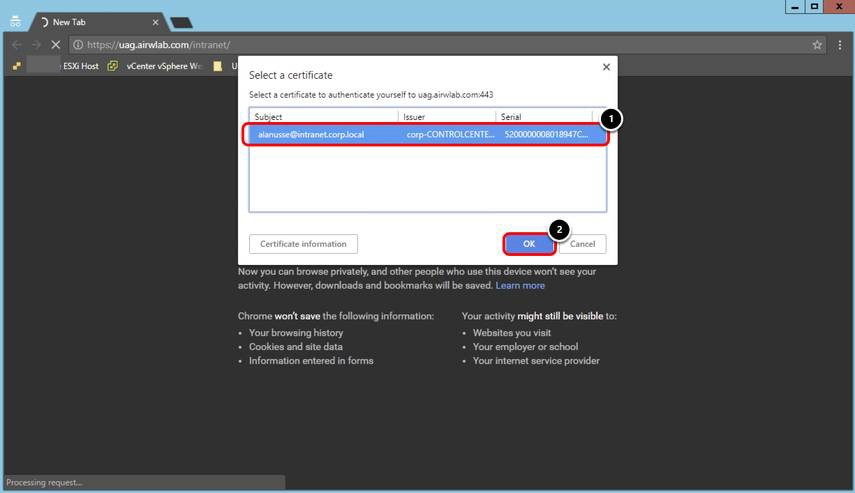
- Select the certificate.
- Click OK.
Confirm Certificate Authentication was Successful
The intranet page is displayed and is only accessible from external networks to users that have the correct certificate. Click Close.
Conclusion
In this set of exercises, you have learned how to:
- Deploy the Unified Access Gateway on a two-NIC configuration using PowerShell script
- Configure Web reverse proxy to access internal Web sites through HTTP and HTTPS protocols
- Configure device certificate authentication to secure and restrict access to internal websites through Web reverse proxy configuration
For more information, see the Omnissa Unified Access Gateway documentation.
Getting Started with Identity Bridging: Kerberos Setup
Today's workforce depends on mobility and organizations must enable their workforce through multiple ways—this enablement can lead to a review of internal procedures, technologies, IT security requirements, and so on. As part of this process, providing external access to internal web applications is one of the top priorities for IT leaders to enable the workforce. Security is the primary requirement; providing the best user experience without compromising security is key.
Unified Access Gateway allows secure access to internal applications through multiple edge services. This section demonstrates how identity bridging can provide external access and single sign-on to internal legacy applications (non-SAML applications) using Kerberos constrained delegation (KCD).
Identity bridging on Unified Access Gateway acts as a proxy that sits in front of web applications and translates the user identity to Kerberos. The user provides their identity through SAML or a certificate, and Unified Access Gateway translates that identity and uses KCD to perform the authentication against the internal applications.
The identity bridging mode can be configured with Workspace ONE in the cloud to authenticate users. When a user requests access to a legacy Web application, the identity provider (IdP) applies the applicable authentication and authorization policies.
This section guides you through the entire process on how to configure identity bridging and covers all the requirements. These exercises cover Kerberos configuration on Windows Server 2016.
Procedures include:
- Understanding Kerberos Delegation
- Configuring Internet Information Server (IIS) to support Kerberos Authentication
- Configuring Kerberos Delegation on the Service Account
After you complete the initial identity bridging configuration, you can configure one of two options:
- Configure SAML to Kerberos Option in Identity Bridging
- Configure Certificate to Kerberos Option in Identity Bridging
The steps are sequential and build upon one another, so make sure that you complete each step before going to the next step.
Architecture
The architectural diagram below shows an example environment which emulates a typical environment, including DMZ and internal networks.
In this example, external requests to the vApp are sent to the vPod Router, which directs those requests to the appropriate resource, based on the incoming port. Ports 4000-6500 are reserved for the environment components so all traffic coming in on these ports is forwarded to the appropriate Edge Service for the Unified Access Gateway server. In addition, ports 443 and 9443 are forwarded to the Unified Access Gateway server over the respective ports.
The vApp networks (internal, DMZ, and transit) are created within the vApp. The internal and transit networks are NATed to the SE- UCS-Network for outbound internet connectivity while the DMZ network routes through the vPod Router for inbound and outbound access. Note that the vPodRouter does not have a NIC on the internal network and therefore cannot route external traffic to resources on the internal network.
vPod Router | ESXi01 6.5.0 U1 | Control Center | vCenter Server 6.5 U1 hosted on ESXi01
Architecture Overview Diagram
The following architectural diagram shows an example of two major networks that you can deploy your servers into. For this set of exercises, you deploy the Unified Access Gateway appliance on a DMZ and assign the respective NICs.

At the top of the diagram is vCenter Networking. At the bottom of the diagram is the vApp network required to support the environment. For these exercises, the focus is on the network hosted on the ESXi, and represented by the following three networks:
- VM Network & Management: Represents the dedicated network to access the Management Console
- Internal Network: Represents the internal network on 172.16.0.x range. The Control Center, ESXI, and vCenter are part of the internal network.
- DMZ Network: Represents the DMZ network on 192.168.110.x which is where the Unified Access Gateway appliance is to be deployed. The Unified Access Gateway Internet-facing NIC is associated to this network.
Network Interfaces
Unified Access Gateway supports deployments with one, two, or three NICs. This means that the server can be partitioned to receive traffic on a single interface or to route traffic to different interfaces, based on the source of the request. Most often, if you need to implement multiple NICs, you already follow this standard with other web applications in your organization.
You must determine what is appropriate for your environment when selecting the number of NICs during installation. It is important for you to understand the expected behavior when two or three NICs are enabled.
To explore these options, see Deploying Omnissa Unified Access Gateway Tutorial.
General Considerations
In the exercises for deploying the Unified Access Gateway server through vSphere, the vCenter setup is hosted in a nested template. This is not usually the case when working with users in a live environment.
User environments can include multiple networks and can optionally have a Network Protocol Profiles (NPP) that corresponds to the networks to connect to the Unified Access Gateway. Prior to version 3.3, NPP was a requirement. Since version 3.3, NPP is no longer required.
Note: Keep in mind that the Unified Access Gateway requires a netmask, default gateway, and subnet to be defined for each network enabled during deployment.
Prerequisites
To perform the steps in this exercise, the following prerequisites are required. The following steps focus only on Kerberos configuration and there is no need to download any Omnissa software:
- AD account with administrator privileges to configure Kerberos delegation.
- Administrator access to the IIS Web Server to perform Kerberos configuration on the websites that will be accessible through Unified Access Gateway.
Kerberos Delegation Overview
Kerberos delegation allows a configured system and user to request Kerberos tokens on behalf of another user.
Because Unified Access Gateway is not joined to the domain, you must add Active Directory (AD) domain Kerberos support to Unified Access Gateway. This process is done with a keytab file, which contains necessary security tokens/hashes for Unified Access Gateway to interact with AD. The keytab file also contains information about the user delegated to request Kerberos tokens on another user’s behalf.
Microsoft recommends that each internal web application has its own delegated user and therefore different keytab files. It is possible to have one delegated user and one keytab file for many different internal apps, but if the keytab file is compromised, you risk access to all internal apps. When you have one user and keytab file per application this allows you to deactivate access to only one system at a time.
Although creating the user and keytab file for each application requires more administration, there are clear security benefits.
A Kerberos realm is the domain over which a Kerberos server has the authority to authenticate. A realm is your trust boundaries. In AD Kerberos, your trust boundaries are your clients, AD servers, and application servers all joined to the domain. Each one trusts the other because they are all part of the same Kerberos realm.
This exercise uses the following environment configuration:
- AD Domain / Kerberos realm CORP.LOCAL
- Internal web server computer name — INTRANET
- Internal web server URL — http://it.corp.local
- Internal web application (Kerberos enabled) — http://it.corp.local/itbudget
- URL used in Workspace ONE Web to access the internal web site through Unified Access Gateway—
- https://uag.airwlab.com/itbudget
- User for Kerberos delegation: iis_it (UPN: iis_it@CORP.LOCAL)
Authentication Flow
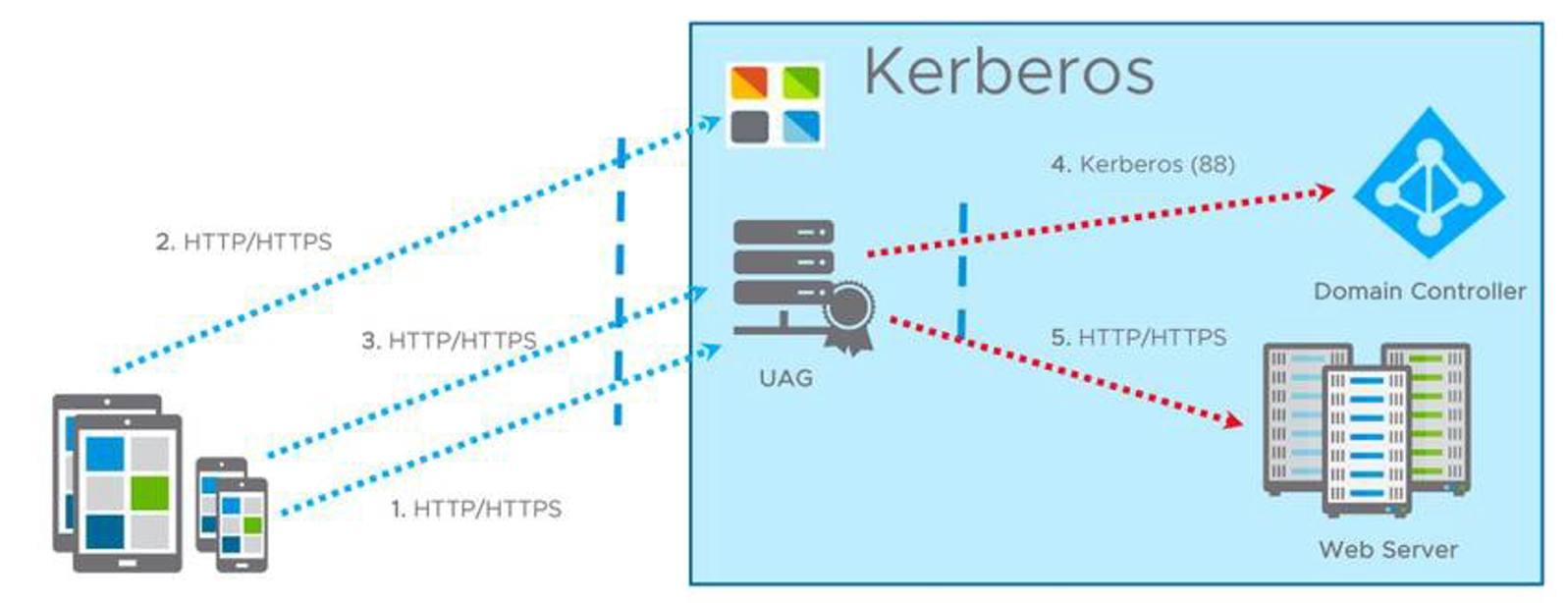
The following diagram describes all the steps used by identity bridging with SAML to Kerberos authentication on Unified Access Gateway. Understanding Kerberos is critical to successfully configure identity bridging.
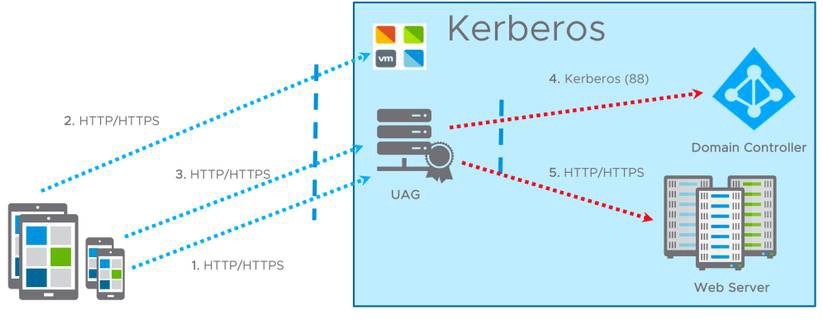
- Client navigates to the application URL (https://uag.airwlab.com/itbudget).
- Client is redirected to the IdP (Workspace One) for authentication (https://vidm.airwlab.com). The IdP issues a SAML assertion upon authentication.
- Client passes the SAML assertion to Unified Access Gateway (http://uag.airwlab.com). Unified Access Gateway validates that the SAML assertion is from a trusted IdP.
- Unified Access Gateway extracts the client’s username from the SAML assertion and requests a Kerberos ticket from Active Directory (CORP.LOCAL) on behalf of that user.
- Unified Access Gateway authenticates against the internal web server (https://it.corp.local) using the Kerberos ticket obtained from AD.
Configuring Kerberos Delegation
This exercise helps you to configure Kerberos delegation for the IIS IT service account that has been assigned to handle Kerberos delegation for the IIS website.
Configure Service Account in Active Directory
Confirm that your service account (CORP\IIS_IT) is available in Active Directory Users and Computers management console. This example uses the CORP\IIS_IT (IIS IT) account. Click the Active Directory Users and Computers icon from the taskbar.
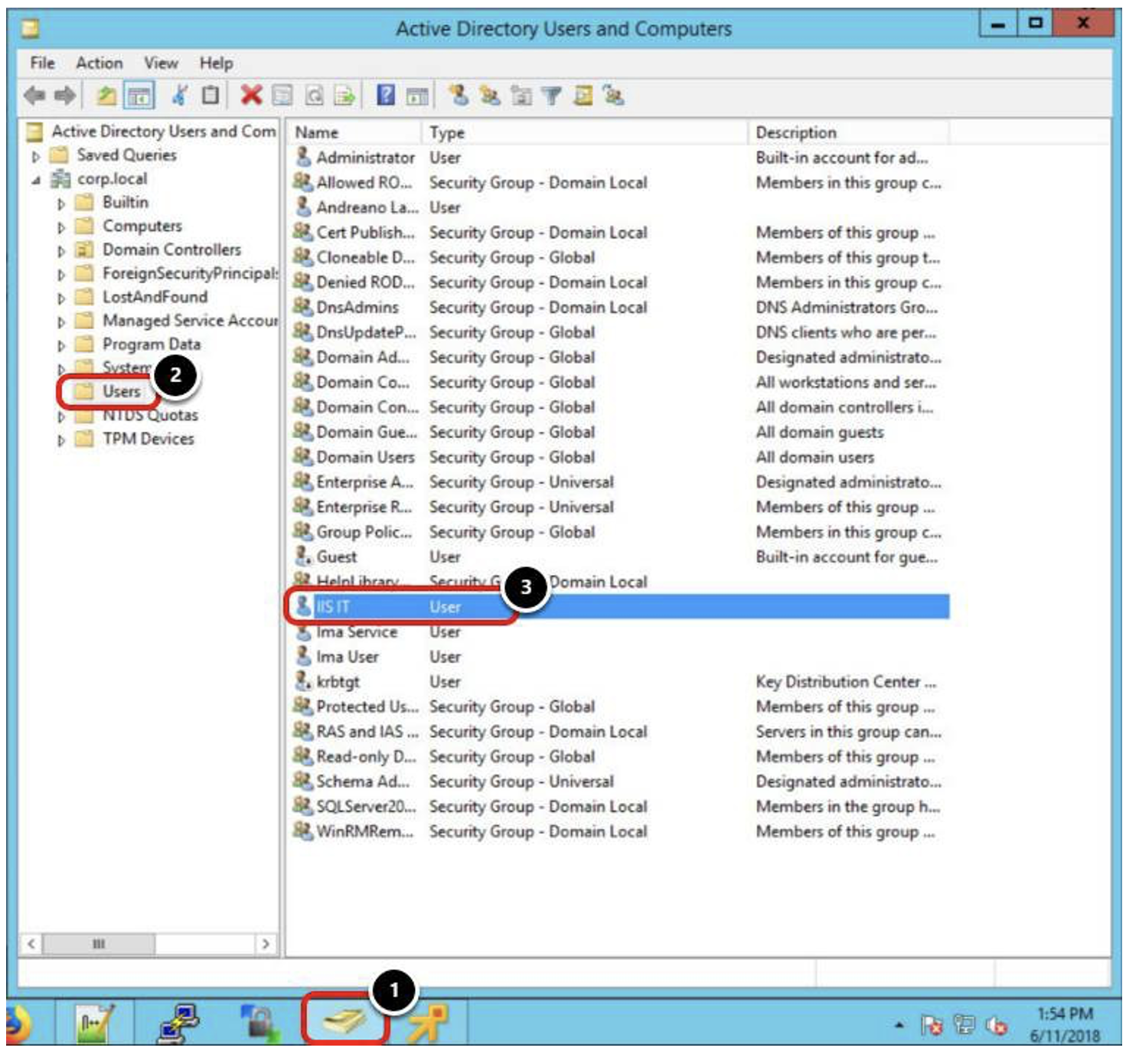
- Navigate to Users.
- Confirm your IT user exists.
Configure Service Principal Name (SPN) for Service Account
The next step is to assign a Service Principal Name (SPN) entry for the name the website has to respond to, for example, IT.CORP.LOCAL.
The SPN can be associated with a web server machine name or service account under which the application pool's web server will be running. It can be a Local System, Network Service, or a domain account; the SPN must be unique.
If the IIS website only needs to be available by the server’s name on which it is located, you would not need to create additional SPN entries as these already exist in the server account INTRANET in Active Directory. In this example, the DNS name is IT.CORP.LOCAL and the web server machine is INTRANET, and you create an SPN entry HTTP/IT.CORP.LOCAL for the user account CORP\IIS_IT.
Important: For Kerberos authentication to succeed in a load-balanced scenario, the web servers must use an alternate credential that is shared by all members of the array. The credential must also be associated with the array-specific SPNs. This shared credential may be either a computer account or a service account and must be known by every web server within the array.
Load balancing is outside the scope of this exercise, however, for more information, see the Microsoft article: Using Kerberos with a Client Access Server Array or a Load-Balancing Solution.
Assign Service Principal Name to Service Account
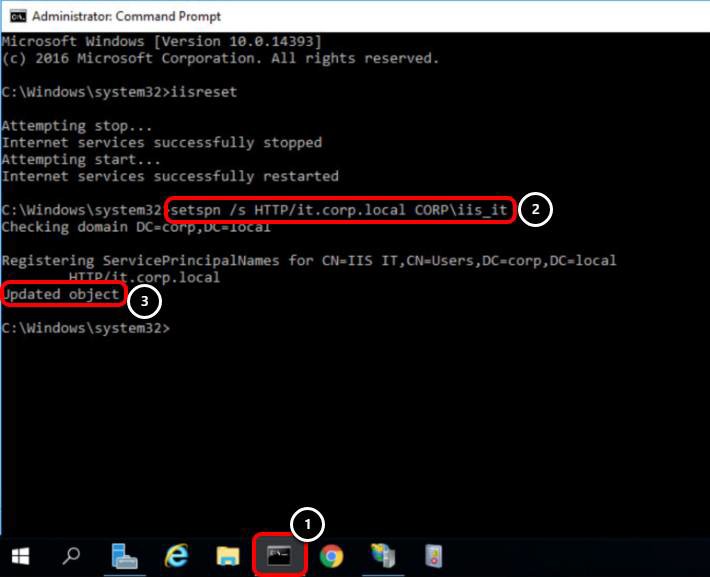
- Click the Command Prompt icon from the taskbar on the intranet VM.
- Enter the command setspn /s HTTP/it.corp.local CORP\iis_it and press Enter. Replace it.corp.local with your DNS name and CORP\iis_it with your IT service user.
- Confirm that the command was successful, noted by the Updated object output.
With this command, you are giving permission to the user, CORP\IIS_IT, to decrypt Kerberos tickets, when users access these addresses and authenticate sessions.
Assign Delegation Rights to the Service Account
Return to the Active Directory Users and Computers management console.
- Click the Active Directory Users and Computers icon from the taskbar.
- Right-click your user, for example, IIS IT.
- Click Properties.
Update Delegation Settings
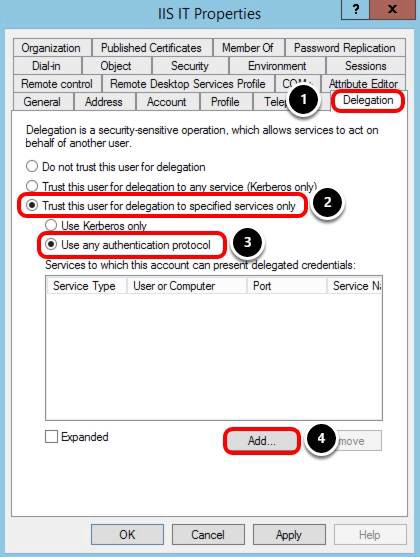
- Select the Delegation tab.
- Select Trust this user for delegation to specified services only.
- Select Use any authentication protocol.
- Click Add.
Search for Computer
Click Users or Computers.
Search for the Intranet Object Name
- Enter your machine name, for example, intranet.
- Click OK.
Select the HTTP Service
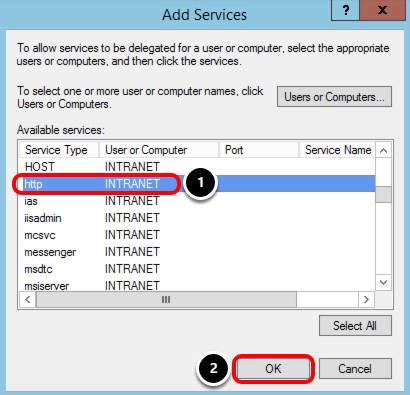
- Select http for INTRANET computer in the Available services list.
- Click OK.
Add HTTP Service for the Delegation
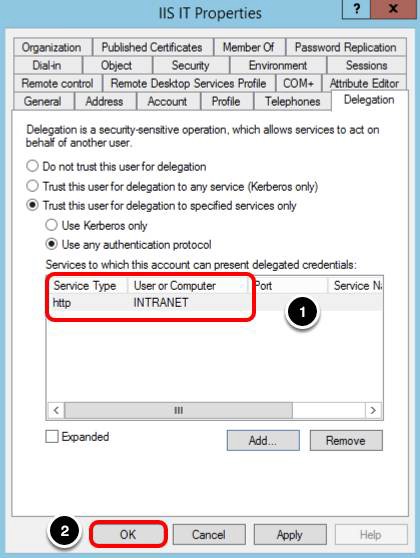
- Confirm that http for INTRANET computer was added to the list of services to which the IIS_IT account can present delegated credentials. The computer value refreshes the next time you select the Delegation tab; instead of INTRANET, you should see INTRANET.CORP.LOCAL.
- Click OK.
You have now authorized a specific user (IIS_IT) to delegate the user logged in credentials to any HTTP service on the INTRANET machine. This setting varies depending on the type of SPN you have registered and might fall under any one of the below categories.
Create a Keytab File
The keytab file is the token used to connect to Active Directory and request an authentication ticket without a login password. Keytab can only be generated through Windows Server OS.
Service names are not case sensitive for Active Directory, but they are case sensitive for Kerberos. However, you may use the following conventions:
- Kerberos realms (and Active Directory Domains) are written in uppercase.
- Hostnames are written in lowercase.
- Database lookups are case sensitive.
Note: The case-sensitive constraint means that the principal names expressed in the mappings must be written using the same case as those returned by a domain-name lookup. The Active Directory is not case sensitive, while Kerberos is case sensitive.
Ensure you are logged in to your domain controller to generate the keytab file. This example illustrates the best practice for the components of the SPN:
- HTTP—All uppercase letters.
- it.corp.local—All lowercase letters.
- CORP.LOCAL—All uppercase letters.
- Open Command Prompt.
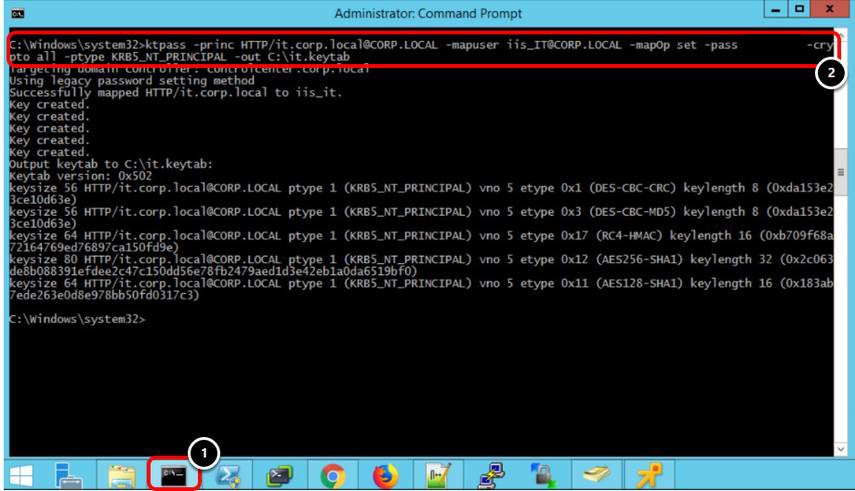
- Enter the following command and press Enter:
ktpass /princ HTTP/it.corp.local@CORP.LOCAL /mapuser iis_IT@CORP.LOCAL /mapOp set /pass [PASSWORD] /crypto all
/ptype KRB5_NT_PRINCIPAL /out C:\it.keytab
- Replace HTTP/it.corp.local@CORP.LOCAL with your service principal name.
- Replace iis_IT@CORP.LOCAL with your service account user.
- Replace [PASSWORD] with your password.
This command creates a file named it.keytab in C:\ — This file will be used to configure identity bridging on Unified Access Gateway.
The following list describes the ktpass tool parameters.
- /princ — Specifies the principal name in the form HTTP/it.corp.local@CORP.LOCAL that you created in Assign Service Principal Name to Service Account. - Caution: This parameter is case-sensitive.
- Caution: This parameter is case sensitive and there is no validation to see if the parameter matches the exact case of the
- userPrincipalName – attribute value when generating the keytab file.
- /mapuser — Maps the name of the Kerberos principal, which is specified by the princ parameter, to the specified domain account.
- /mapOp — Specifies how the mapping attribute is set, in this case, -Set sets the value for Data Encryption Standard (DES) only encryption for the specified local username.
- /crypto — Specifies the keys that are generated in the keytab file.
- /ptype — Specifies the principal type; KRB5_NT_PRINCIPAL is the general principal type (recommended).
- /out — Specifies the name of the Kerberos version 5 keytab file to generate
Configuring Kerberos Authentication on IIS Website
In this exercise, you connect to a machine in your intranet and configure Kerberos authentication on Internet Information Services (IIS). This example uses a VM called Intranet VM.
Log In to the Intranet VM
Enter your credentials on your intranet machine.
- Enter your password.
- Click the Login button, or press Enter.
Launch IIS
Click the IIS Manager icon from the toolbar.![]()
Configure IIS Website
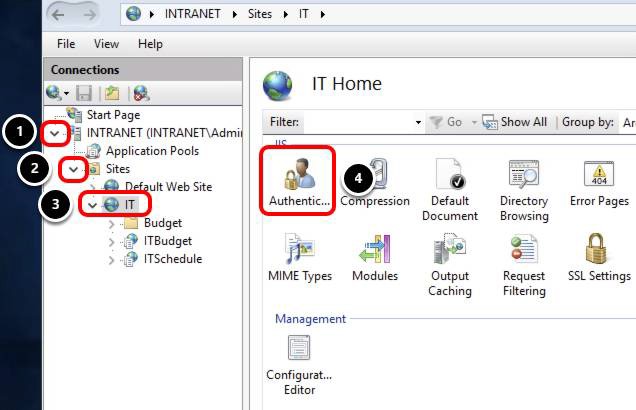
- Expand INTRANET.
- Expand Sites.
- Select IT Site.
- Double-click Authentication.
Enable Windows Authentication Method
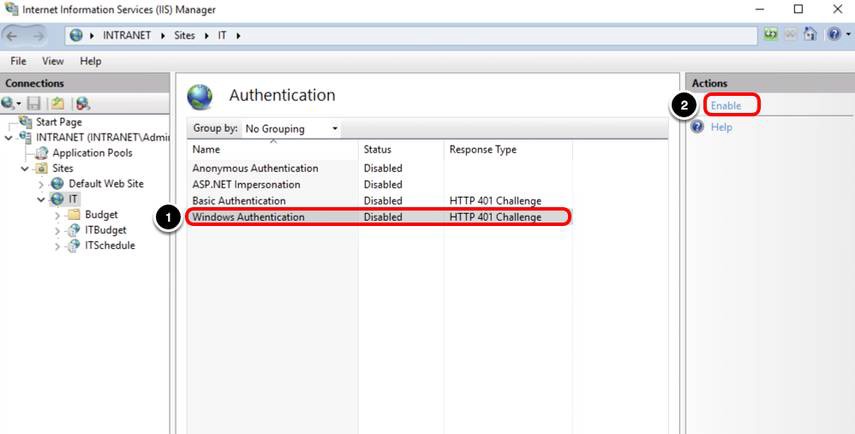
- Select Windows Authentication.
- Click Enable.
Note: Make sure Anonymous Authentication, ASP.NET Impersonation, and Basic Authentication are Disabled. When you install IIS for the first time, Anonymous Authentication is always enabled by default.
Configure Authentication Providers
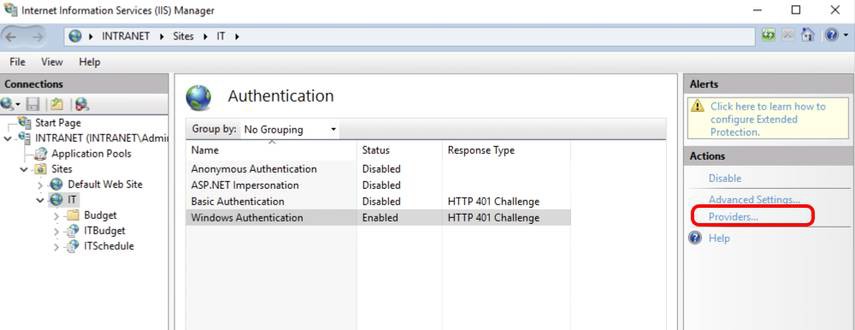
After you enable the Windows authentication method, you can set up the authentication providers. Click Providers to open the list of providers available for Windows authentication.
Configure Providers
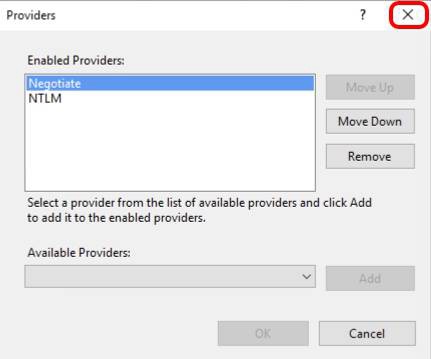
In this example, Negotiate and NTLM have already been configured as the two enabled providers available. In a new IIS installation, you must install the providers as part of the IIS installation and add those here. This procedure is outside the scope of this exercise.
Negotiate is a container that uses Kerberos as the first authentication method. If the authentication fails, NTLM is used, which means username and password will be used.
Important: It is mandatory that Negotiate comes first in the list of providers. Confirm that Negotiate is first and NTLM second. Click X to close the dialog box.
Configure Kernel-Mode Authentication
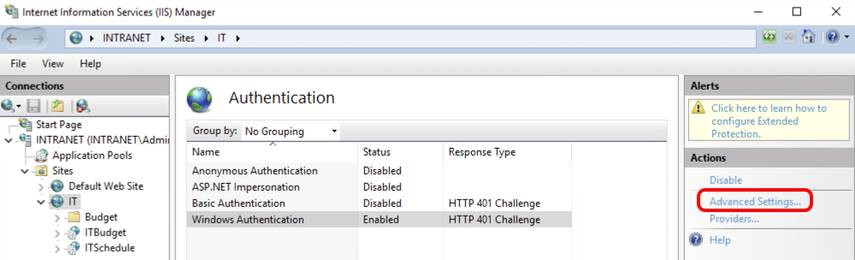
Click Advanced Settings...
Enable Kernel-Mode Authentication

- Select the Enable Kernel-mode authentication check box.
- Click OK.
Keep Extended Protection Off for this exercise. However, in a production environment you should configure this option, as it enhances the existing Windows Authentication functionality to mitigate authentication relay attacks. For more information about Extended Protection, see the Microsoft article Description of the update that implements Extended Protection for Authentication in Internet Information Services (IIS).
Configure IIS Application Pool
Configure the Application Pool to launch from a specific account.
Configure Identity for an Application Pool
- Select Application Pools.
- Select IT in the Application Pools list.
- Click Advanced Settings.
Update the Application Pool Identity
Click the dot icon for Identity under Process Model.
Select Custom Account
- Select Custom account.
- Click Set...
Set Custom Account Credentials
In this step, select an account to be used to launch the Pool. This example uses CORP\iis_it.
- Enter the User name.
- Enter the Password.
- Confirm the password.
- Click OK.
Confirm Custom Account for Application Pool Identity
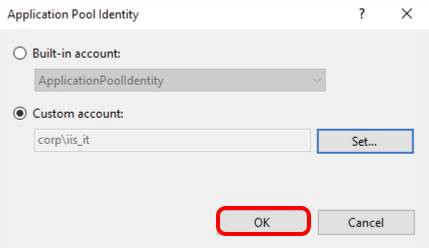
Click OK to confirm that corp\iis_it is the account to be used by this pool.
Confirm the Updated Application Pool Identity
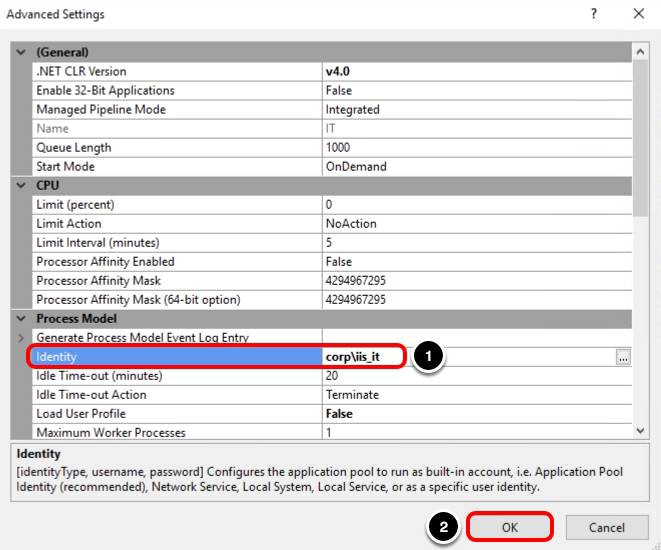
- Confirm that the correct account is listed for Identity.
- Click OK.
Configure Application Pool to use Identity Credentials
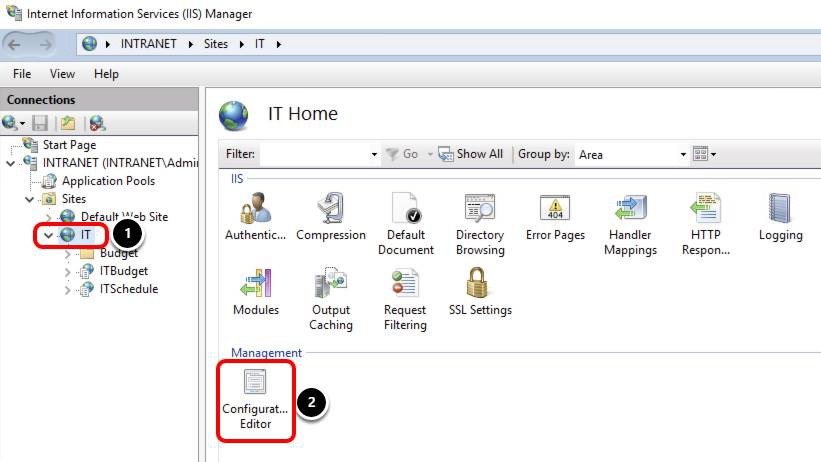
- Select the IT website.
- Double-click Configuration Editor.
Select Windows Authentication
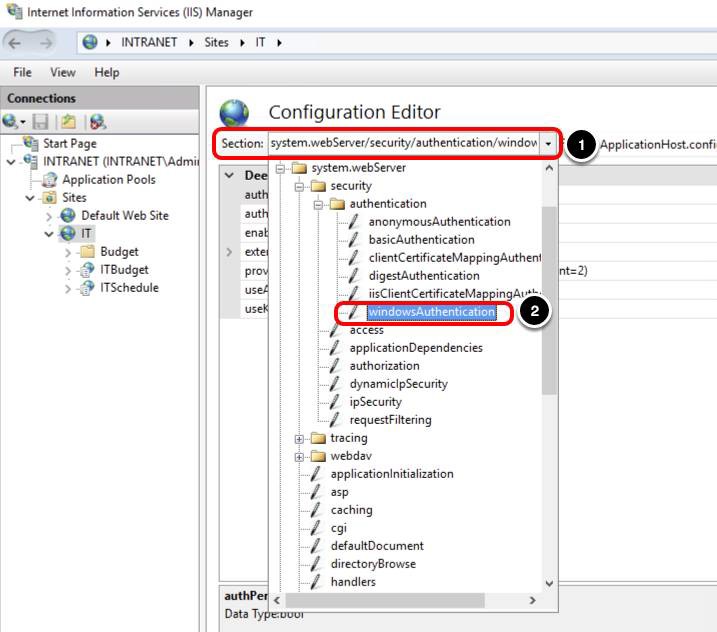
- Open the Section list.
- Navigate to system.webServer > security > authentication > windowsAuthentication.
Update Windows Authentication Configuration
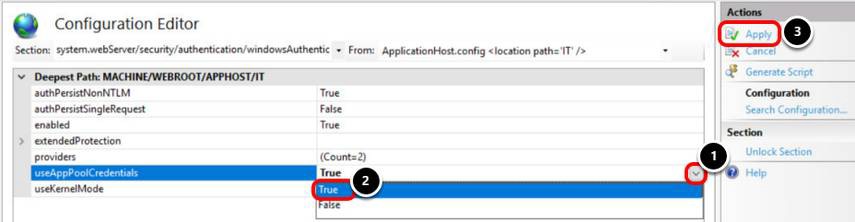
- Click the dropdown arrow for useAppPoolCredentials.
- Select True for useAppPoolCredentials.
- Click Apply.
When you set useAppPoolCredentials to true you are telling IIS that it must use it's application pool identity (which you set for CORP\iis_it) to decrypt the Kerberos token/ticket which was obtained from AD and forwarded by the client to the server to authenticate the user.
Reset IIS
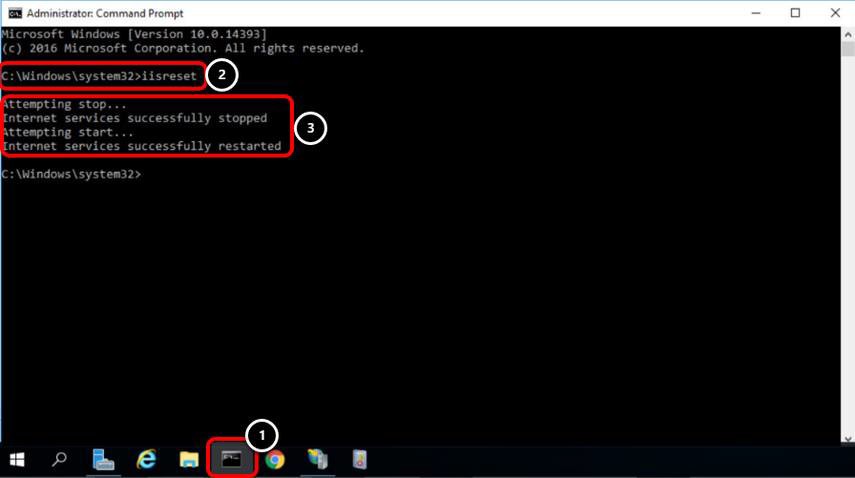
- Click the Command Prompt icon from the taskbar.
- Enter iisreset and press Enter.
- Confirm IIS successfully stops and then starts again.
Selecting Identity Bridging Option
Now that you have completed the initial configuration for identity bridging, select one of the following two options.
- Configuring SAML to Kerberos Option in Identity Bridging
- Configuring Certificate to Kerberos Option in Identity Bridging
Configuring SAML to Kerberos Option for Identity Bridging
Unified Access Gateway in identity bridging mode (SAML to Kerberos) acts as the service provider that passes user authentication to the configured legacy applications. Workspace ONE Access acts as an identity provider and provides SSO into SAML applications. When users access legacy applications that require KCD or header-based authentication, Workspace ONE Access authenticates the user. A SAML assertion with the user's information is sent to the Unified Access Gateway. Unified Access Gateway uses this authentication to allow users to access the application.
This section helps you to configure the SAML to Kerberos option in identity bridging by providing SSO to legacy web applications using KCD.
This set of exercises covers a Unified Access Gateway 3.3 deployment with Workspace ONE Access 3.2.1 in vSphere 6.5 U1. Procedures include:
- Deploying a Unified Access Gateway appliance with two NICs, one facing the internet and the second one dedicated to management and back-end access.
- Configuring identity bridging on Unified Access Gateway.
- Configuring Web application (SAML) on Workspace ONE Access.
- Testing external access to an internal web application (SAML) using SSO through identity bridging (Kerberos).
The steps are sequential and build upon one another, so make sure that you complete each step before going to the next step.
Authentication Flow
The following diagram describe the authentication flow that you will configure in this section.
- Client navigates to application URL (https://uag.airwlab.com/itbudget).
- Client is redirected to the IdP (Workspace One) for authentication (https://vidm.airwlab.com). The IdP issues a SAML assertion upon authentication.
- Client passes the SAML assertion to Unified Access Gateway (http://uag.airwlab.com). Unified Access Gateway validates that the SAML assertion is from a trusted IdP.
- Unified Access Gateway extracts the client’s username from the SAML assertion and requests a Kerberos ticket from Active Directory (CORP.LOCAL) on behalf of that user.
- Unified Access Gateway authenticates against the internal web server (https://it.corp.local) using the Kerberos ticket obtained from AD.
Prerequisites
Before you can perform the steps in this exercise, you must install and configure the following components:
- Omnissa Workspace ONE UEM SaaS or latest on-premises version
- vSphere ESX host with a vCenter Server (vSphere 6® and later)
- vSphere data store and network to use
- PowerShell script running on Windows 10 or Windows Server 2020+
- Windows machine running the PowerShell script with OVF Tool command installed (see OVR Tool Software Download to install OVF Tool 4.3 or later)
- Obtain a Unified Access Gateway virtual appliance image OVA file, such as .euc-access-point-3.3.X.X-XXXXXXXXXXX.ova(see Omnissa Product Interoperability Matrixes to determine which version to download)
- Unified Access Gateway PowerShell script, such as uagdeploy-VERSION.ZIP (download from my.workspaceone.com, and extract the files into a folder on your Windows machine)
- Network access from the Unified Access Gateway back-end services NIC to the internal website used on the reverse proxy
Logging In to the vSphere Web Client
To perform most of this exercise, you need to log in to the vSphere Web Client.
- Launch Chrome Browser.
- Authenticate to the vSphere Web Client.
Preparing Web Reverse Proxy INI Settings for Deployment
You can deploy and configure Unified Access Gateway using a PowerShell script.
This section helps you to configure the required INI settings for a Web Reverse Proxy instance during the Unified Access Gateway appliance deployment.
Configuring the General Deployment Settings
A INI file containing all the configuration settings is required to deploy the Unified Access Gateway appliance.
In this exercise, you use the uag-ReverseProxy.ini file to provide the respective parameters for your deployment.
You deploy a new Unified Access Gateway appliance called UAG-2NIC, which has two NICs. NIC one is Internet-facing and NIC two is for back end and management.
Edit the UAG-ReverseProxy.ini File
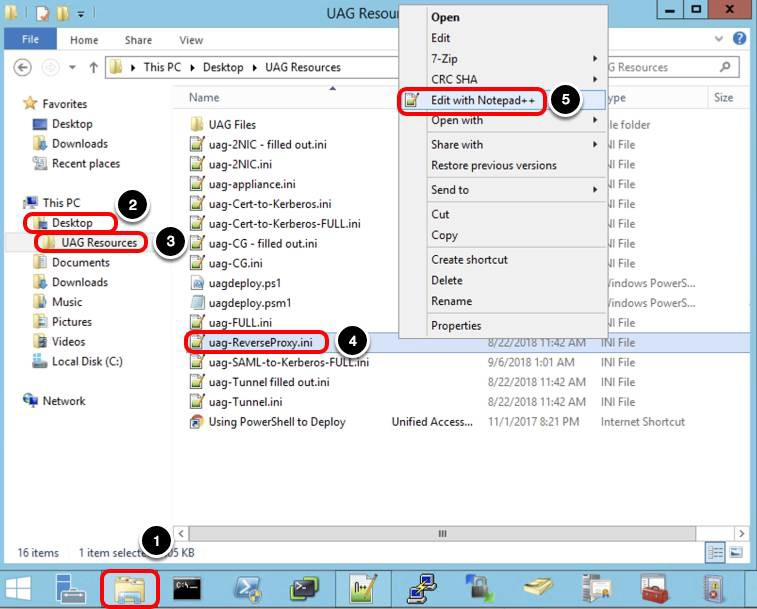
Navigate to uag-ReverseProxy.ini. In this example, the INI file is located in UAG Resources.
- Click the File Explorer icon on the task bar.
- Select Desktop.
- Select UAG Resources.
- Right-click the uag-ReverseProxy.ini file.
- Click Edit with Notepad++.
Configure General Settings (1/2)
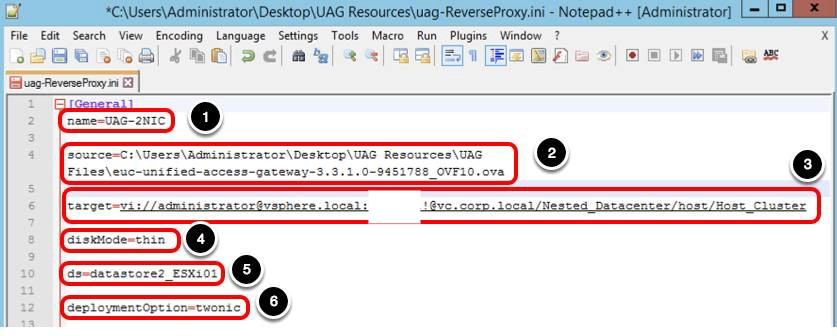
In the General section, configure the following parameters. Your values will differ.
- For name, enter UAG-2NIC.
- For source, enter the path and name of the OVA File. For example, the OVA file is located in C:\Users\Administrator\Desktop\UAG Resources\UAG Files.
- For target, enter vi://administrator@vsphere.local:password!@vc.corp.local/Nested_Datacenter/host/Host_Cluster. Note: You can replace the password with 'PASSWORD' and the script prompts for the password during the PowerShell execution.
- For diskmode, enter thin.
- For ds, enter datastore2_ESXi01 (ds refers to data store).
- For deploymentOption, enter twonic.
Configure General Settings (2/2)
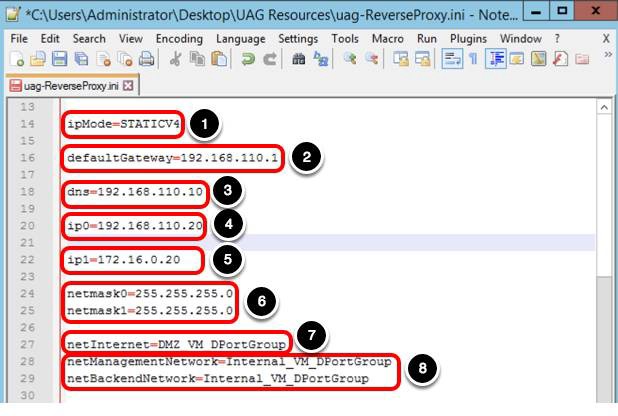
Continue with the General section configuration, configure the following parameters in the INI file.
- For ipMode, enter STATICV4.
- For defaultGateway, enter 192.168.110.1 .
- For dns, enter 192.168.110.10.
- For ip0, enter 192.168.110.20.
Note: ip0 is the Internet-facing NIC.
- For ip1, enter 172.16.0.20.
Note: ip1 is the internally facing NIC.
- For netmask0 and netmask1, enter 255.255.255.0.
- For netInternet, enter DMZ_VM_DPortGroup.
- For netManagementNetwork and netBackendNetwork, enter Internal_VM_DPortGroup.
Configure TLS/SSL Certificates for Unified Access Gateway Appliance

SSLCert and SSLCertAdmin contain SSL certificate information for the administration and Internet interfaces.
- For pfxCerts under SSLCert, enter C:\AW Tools\airwlab.com.pfx (this certificate is for the Internet interface).
- For pfxCerts under SSLCertAdmin, enter C:\AW Tools\airwlab.com.pfx (this certificate is for the administration interface).
The certificate password is requested during the deployment.
Configure Web Reverse Proxy instance
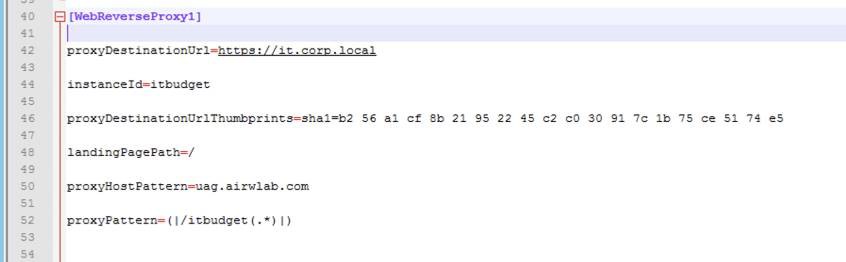
In addition to the regular settings responsible for the appliance configuration, you add an additional section named
WebReverseProxy1. The following steps help you to configure a Web reverse proxy instance named itbudget.
- For proxyDestinationUrl, enter an internal URL. For example, https://it.corp.local.
- For instanceId, enter a name such as, itbudget.
- For proxyDestinationUrlThumbprints, enter sha1=b2 56 a1 cf 8b 21 95 22 45 c2 c0 30 91 7c 1b 75 ce 51 74 e5.
- For landingPagePath, enter /.
- For proxyHostPattern, enter uag.airwlab.com.
- For proxyPattern, enter (|/itbudget(.*)|).
You can configure this WebReverseProxy instance in the Unified Access Gateway administration console, however, this exercise shows you how to automate that configuration. The following list describes the required parameters.
- proxyDestinationUrl — The internal address of the Web application, which is usually the back-end URL.
- instanceId — The unique name to identify and differentiate a Web reverse proxy instance from all other Web reverse proxy instances.
- proxyDestinationUrlThumbprints — A list of acceptable SSL server certificate thumbprints for the proxyDestination URL.
- landingPage — The page the user is redirected to when accessing the website.
- proxyHostPattern — External host name used to check the incoming host to see whether it matches the pattern for that instance. Host pattern is optional, when configuring Web reverse proxy instances.
- proxyPattern — the matching URI paths that forward to the destination URL.
Deploying Unified Access Gateway Appliance
After you have configured the INI file for your Unified Access Gateway deployment, the next step is to run the uagdeploy.ps1 PowerShell script passing the INI as a parameter.
Deploy Unified Access Gateway Using PowerShell
Click the PowerShell icon and run the script.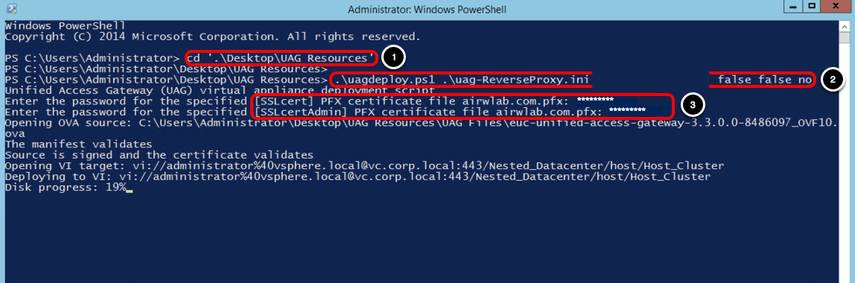
After you run the script, it prompts for input.
- Navigate to the folder containing your INI file. For example, enter cd '.\Desktop\UAG Resources' then press Enter.
- Enter .\uagdeploy.ps1 .\<uag-tunnel>.ini <password1> <password2> false false no then press Enter.
Replace <uag-tunnel> with your INI file name.
Replace <password1> with the root password for the UAG appliance.
Replace <password2> with the administrator password for REST API management access.
The first false is to not skip the validation of signature and certificate.
The second false is to not skip SSL verification for the vSphere connection. The no is to not join the CEIP program. - Enter the password for the certificated that will be used on the following fields SSLcert and SSLcertAdmin.
Enter the password for the apiuser previously defined on the INI file, which allows Unified Access Gateway to obtain the Tunnel settings from Workspace ONE UEM. - To avoid a password request for the certificate, remove the pfxCert values and provide a PEM certificate in the INI file. Set the
- pemCerts and pemPrivKey for the SSLCert and SSLCertAdmin sections in the INI file.
- The deployment starts and you can follow the progress in the same window or on your vSphere Web Client.
Confirm the PowerShell Script Deployment Completes
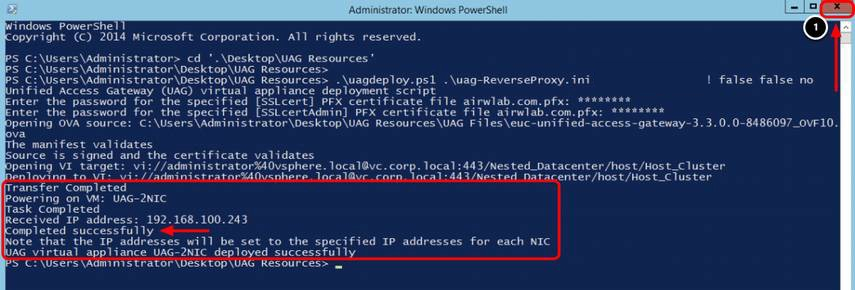
Confirm the deployment has been completed successfully. The Completed successfully text is shown in the output.
- Click Close.
After a successful deployment, the script automatically powers on the VM UAG-2NIC.
The Received IP address presented by the script log is a temporary IP; the final IPs for NIC one and NIC two are assigned to the Unified Access Gateway appliance during the first start. Return to the vSphere Web Client and validate the IP address in the next step.
Validate Unified Access Gateway Deployment
- Click VM and Templates.
- Click UAG-2NIC.
- Click View all 2 IP addresses.
Important: If the Unified Access Gateway appliance does not finalize the configuration during the first startup, you receive an error message from vSphere Web Client. If that happens, wait for the appliance to finalize, and refresh the entire Google Chrome browser.
Log In to Unified Access Gateway Administration Console
- Click the New Tab button to open a new tab.
- Navigate to the Unified Access Gateway administration console URL, for example https://uagmgt-int.airwlab.com:9443/admin.
- Enter the username, for example, admin.
- Enter the password.
- Click Login.
Validate Configuration Settings
A successful login redirects you to the following screen. Keep this window open as you will return to the administration console later.
Click Select to configure settings manually.
Confirm the Web Reverse Proxy Instance is Running
Follow the next steps to confirm that a web reverse proxy instance named itbudget has been automatically configured.
- Click SHOW, after you click SHOW, it changes to HIDE.
- Click the arrow next to Reverse Proxy Settings.
- Confirm that itbudget exists.
Obtaining IdP metadata from Workspace ONE Access
This section helps you to retrieve the IdP metadata file from Workspace ONE Access.
Log In to the Workspace ONE Access Administration Console
Return to Google Chrome.
- Click the New tab button.
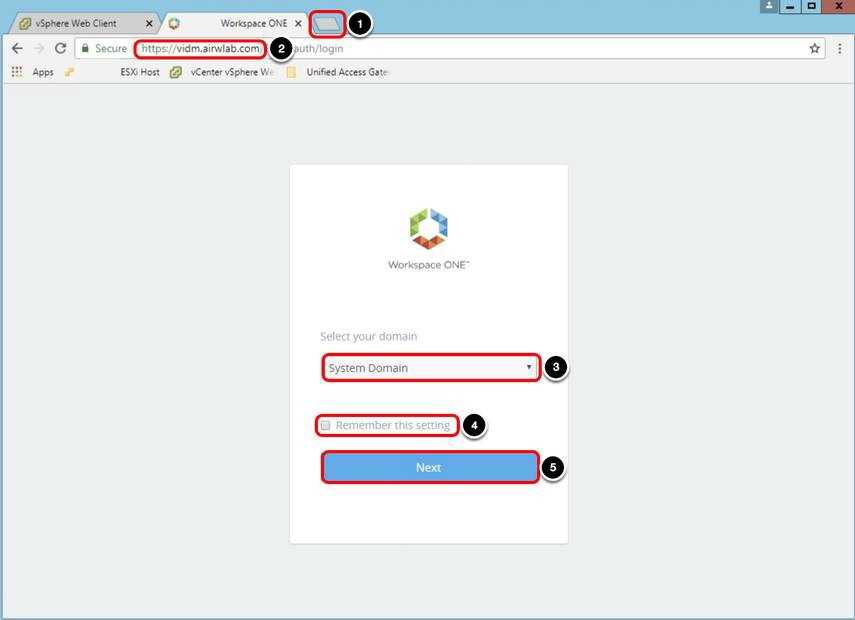
- Enter the Workspace ONE Access administration console URL, for example, https://vidm.airwlab.com and press Enter.
- Select System Domain.
- Deselect the Remember this setting check box.
- Click Next.
Enter the Administrator Credentials
- Enter the Username, for example, admin.
- Enter the Password.
- Click Sign in.
Navigate to Catalog
Click Catalog.
Access Catalog Settings
Click Settings.
Download the Identity Provider Metadata
- Click SAML Metadata.
- Right-click Identity Provider (IdP) metadata.
- Click Save link as...
You need this file during the identity bridging configuration.
Save the Identity Provider Metadata
- Verify the Downloads folder is selected.
- Check the file name for the metadata is set to idp.xml.
- Click Save.
Close the Catalog Settings
Click the Close button to close the Catalog Settings screen.
Configuring Identity Bridging on Unified Access Gateway
You have deployed the Unified Access Gateway appliance and confirmed that the itbudget web reverse proxy was configured. The next steps are performed in the Unified Access Gateway administration console.
Navigate to the Unified Access Gateway Administration Console
- Click the New Tab button.
- Navigate to the Unified Access Gateway administration console, for example, https://uagmgt-int.airwlab.com:9443/admin.
- Enter the username, for example, admin.
- Enter the password.
- Click Login.
Configure Identity Provider
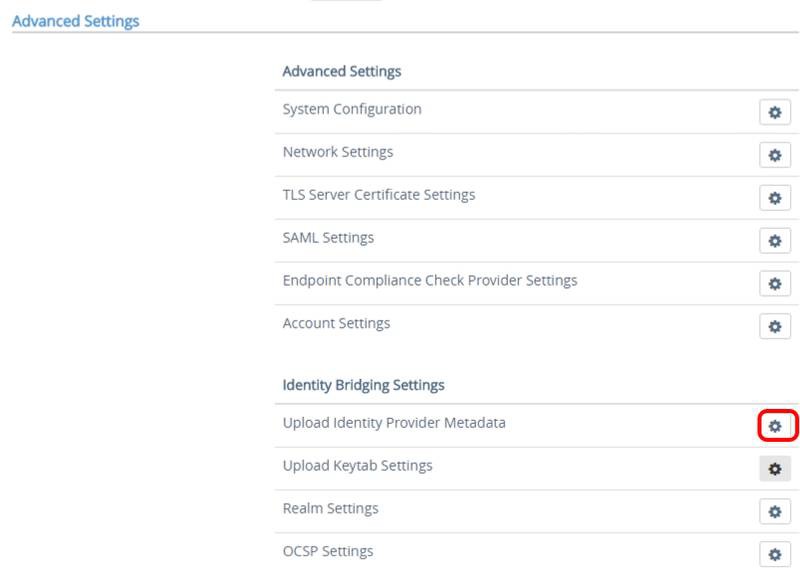
Scroll down to Identity Bridging Settings and click the gear icon next to Upload Identity Provider Metadata.
Upload the Identity Provider Metadata
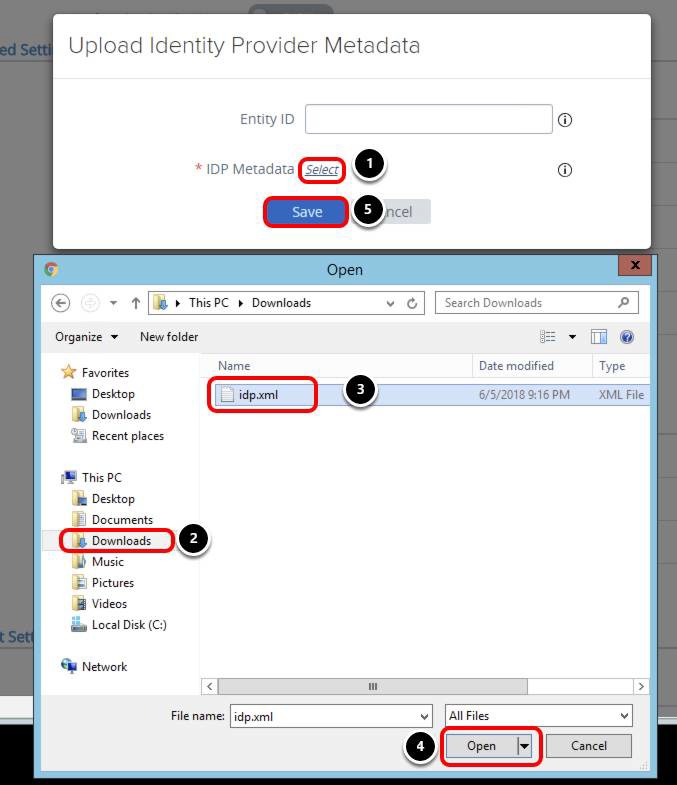
Navigate to the idp.xml file. In this example, idp.xml is located in the Downloads folder.
- Click Select.
- Select Downloads.
- Select idp.xml.
- Click Open.
- Click Save.
After you click Save, you should see the message Configuration saved successfully.
Note: The Entity ID is retrieved from the IDP metadata XML, so there is no need to manually enter the value.
Configure Keytab
Under Identity Bridging Settings, click the gear icon next to Upload Keytab Settings.
Update the Keytab Settings
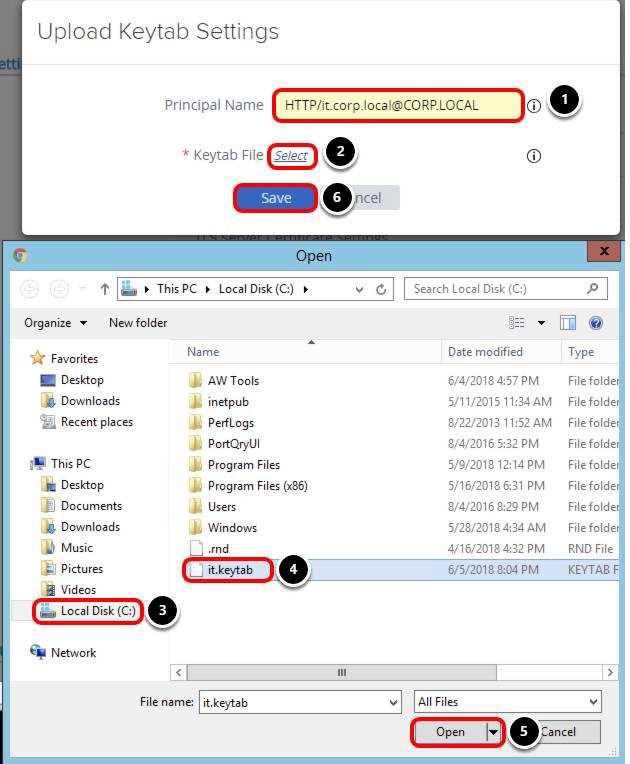
- Enter the Principal Name, for example, HTTP/it.corp.local@CORP.LOCAL.
- Click Select.
- Select Local Disk (C:) folder.
- Select the it.keytab file.
- Click Open.
- Click Save.
After you click Save, you should see the message Keytab upload is successful.
Note: If you do not enter a Principal Name value, then the first Principal Name found in the keytab file will be used. If your keytab contains multiple Principal Names, you should manually enter Principal Name in Keytab Settings.
Configure Realm
Under Identity Bridging Settings, click the gear icon next to Realm Settings.
Add a Realm Setting
Click Add.
Configure the Realm Settings
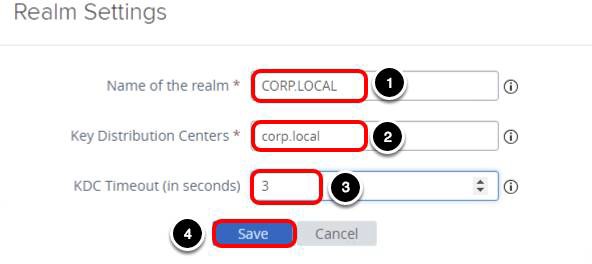
- Enter the Name of the realm, for example, CORP.LOCAL.
Note: This entry must use capital letters.
- Enter the Key Distribution Centers, for example, corp.local.
- Enter 3 for KCD Timeout (in seconds).
- Click Save.
After you click Save, you should see the message Configuration saved successful.
Close the Realm Settings
You have configured the Realm settings. Click Close.
Configure Identity Bridging
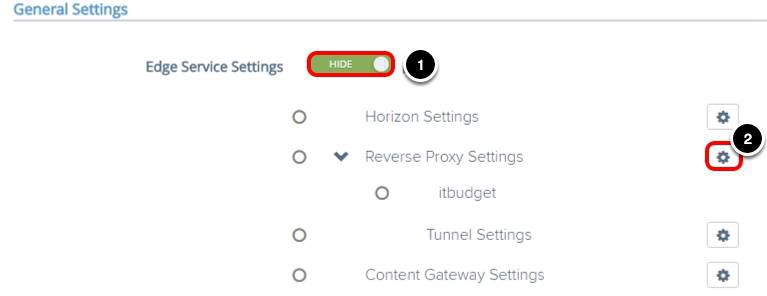
- If the Edge Service Settings are currently hidden, click the Show toggle to display the settings.
- Select the gear icon for Reverse Proxy Settings.
Open the itbudget Reverse Proxy Settings
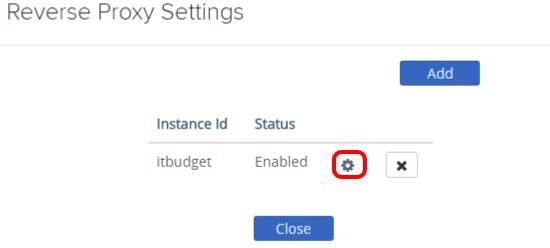
Select the gear icon for the itbudget reverse proxy Instance.
Update the itbudget Reverse Proxy Settings
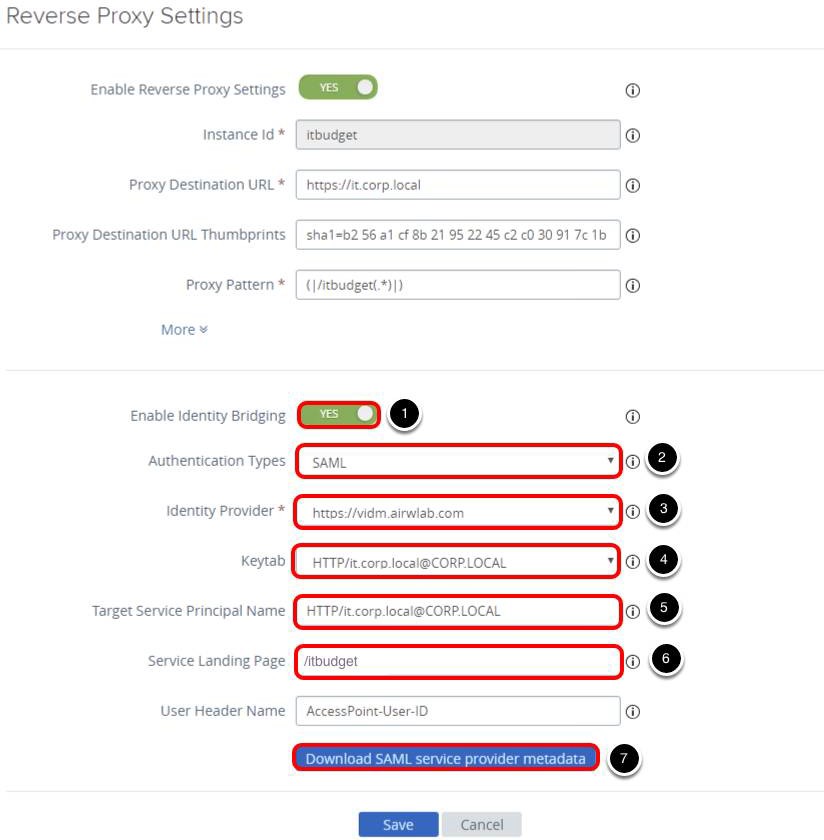
- Click NO to show the Enable Identity Bridging, it changes YES after you click NO.
- Select SAML for Authentication Types.
- Select your Identity Provider, for example, https://vidm.airwlab.com.
- Select the Keytab, for example, HTTP/it.corp.local@CORP.LOCAL.
- Enter the Target Service Principal Name, for example, HTTP/it.corp.local@CORP.LOCAL.
- Enter /itbudget for Service Landing Page. After a successful authentication UAG will redirect the user to the Service Landing Page, the default value is /, this value must match with your proxy pattern.
- Click Download SAML service provider metadata. This will open a dialog box.
Important: Do not click Save at this point. Continue to the next step.
Download the SAML Service Provider Metadata
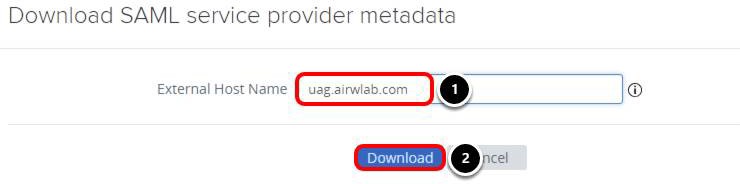
- Enter the External Host Name, for example, uag.airwlab.com.
- Click Download.
An XML file is downloaded to the Downloads folder. This file will be used during the Web App setup in Workspace ONE Access.
Save the Reverse Proxy Settings
Click Save.
Confirm the Reverse Proxy Settings Saved
Confirm the Configuration is saved successfully message is displayed.
Configuring a Web Application in Workspace ONE Access
This section helps you to configure a web application named IT Budget in Workspace ONE Access.
Add New Web App
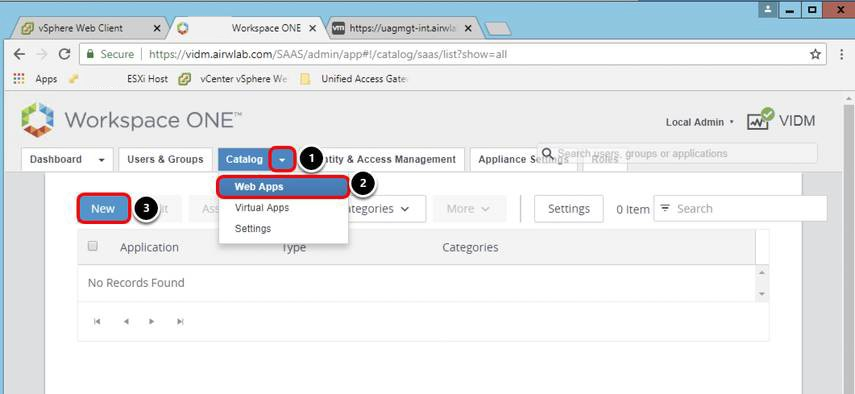
In the Workspace ONE Access administration console:
- Click the drop-down arrow next to Catalog.
- Click Web Apps.
- Click New.
Configure Web App
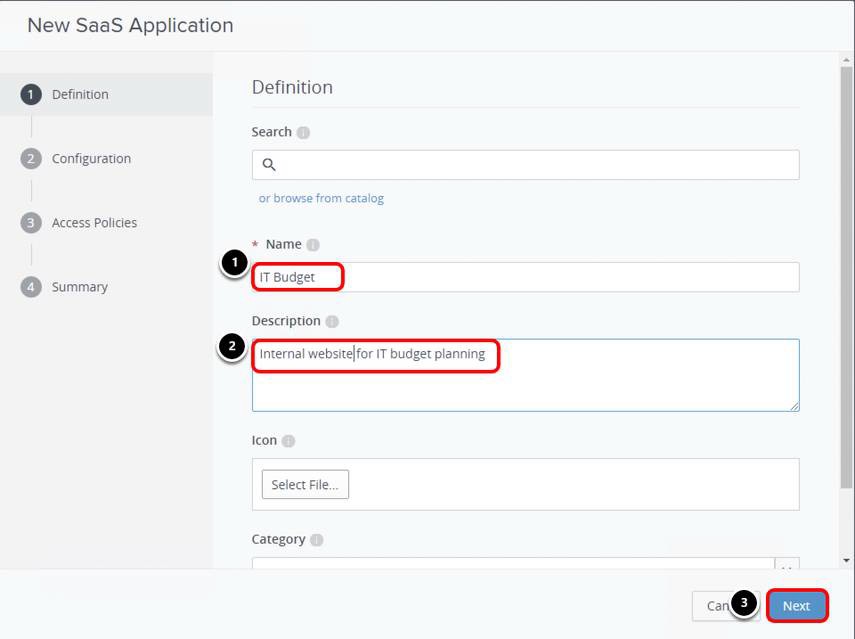
- Enter a Name, for example, IT Budget.
- Enter the Description, for example, Internal website for IT Budget planning.
- Click Next.
Upload SAML Service Provider Metadata
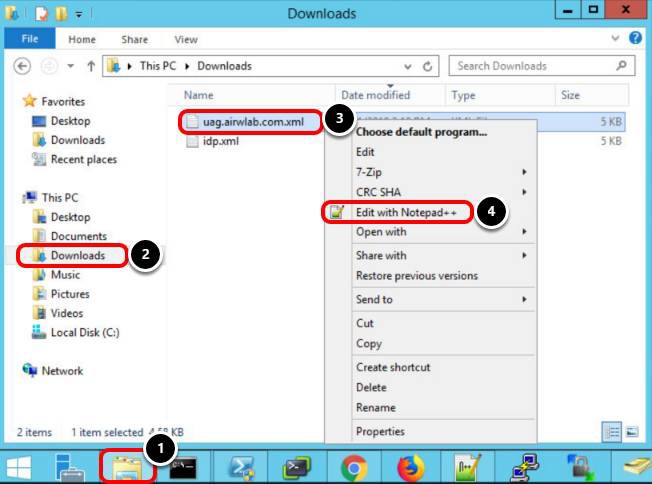
In this step, you navigate to the SAML XML file downloaded in Download the SAML Service Provider Metadata.
- Click the File Explorer icon from the taskbar.
- Select the Downloads folder.
- Right-click the xml file, for example, uag.airwlab.com.xml.
- Select Edit with Notepad++.
Copy the SAML XML
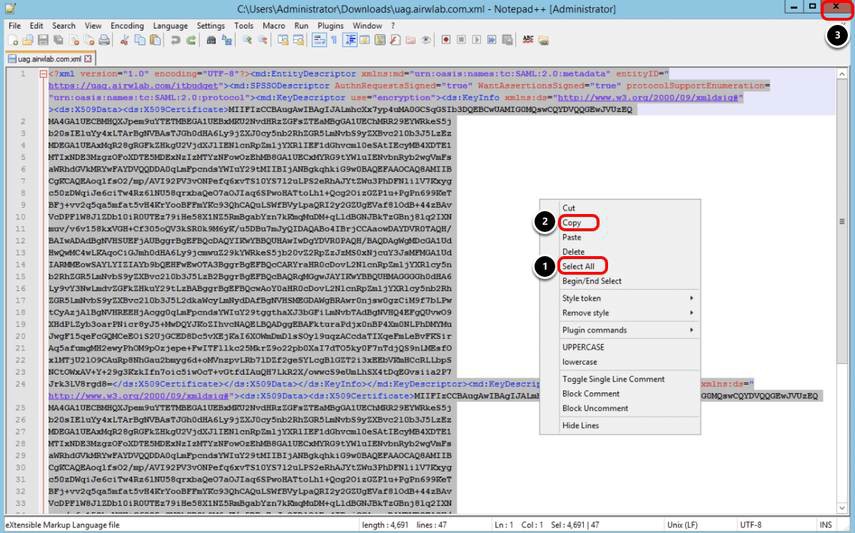
- Right-click the content and click Select All.
- Right-click the content and click Copy.
- Click X to close Notepad++.
Paste the SAML XML
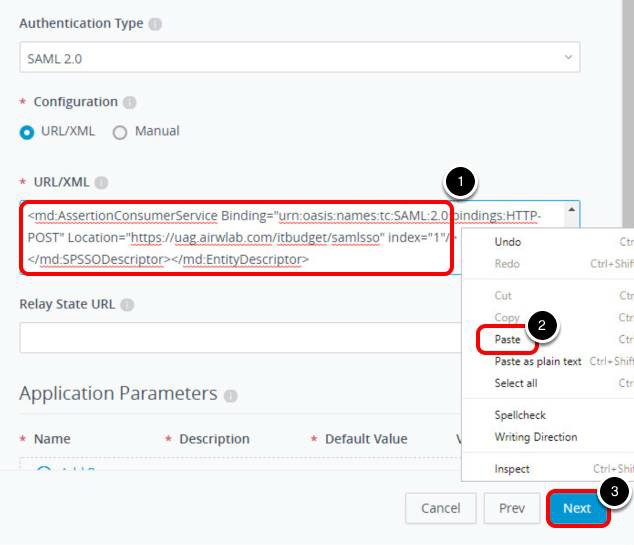
Return to the Workspace ONE Access Console.
- Right-click in the URL/XML text box.
- Click Paste, and confirm that the copied text is entered.
- Click Next.
Define Access Policies
Click Next.
You will use the default access policy already defined in Workspace ONE Access.
Save Web App Configuration
Click Save & Assign.
Assign Web App to an Active Directory Group
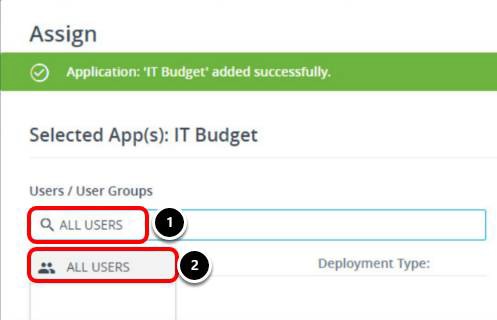
- Enter ALL USERS in the Users / User Groups text box.
- Select ALL USERS.
Update the Deployment Type and Save
- Select Automatic in the drop-down menu for Deployment Type.
- Click Save.
Testing Access to Web Application using SSO through Identity Bridging
You now have the IT Budget web application configured and added to the catalog.
- In Google Chrome, click the three dots menu on the upper-right corner.
- Select New incognito window.
Access the Intranet Site
- Enter your intranet address, for example, https://uag.airwlab.com/itbudget and press Enter.
- Select the Domain.
You are redirected to Workspace ONE Access for authentication on your domain, for example, corp.local. Click Next.
Enter Domain User Credentials
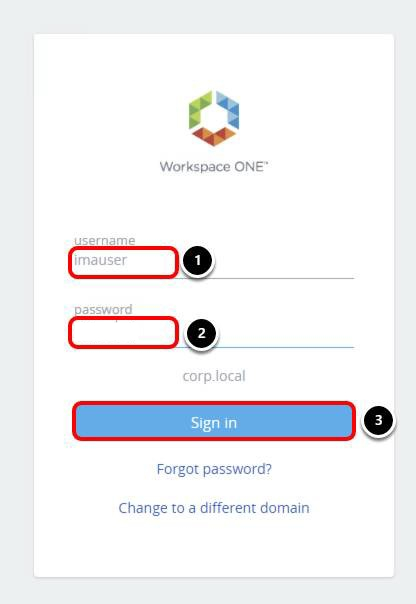
- Enter your username, for example, imauser.
- Enter your password.
- Click Sign in.
Confirm Access after Successful Authentication
You should see the internal website after a successful authentication.
Return to your intranet machine and open Event Viewer.
View Logon Logs
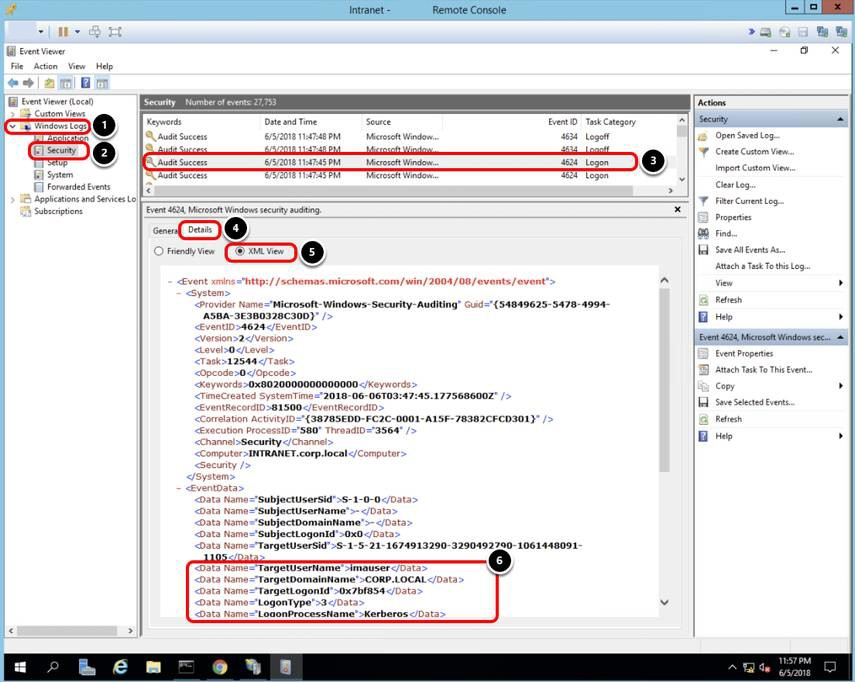
- Expand the Windows Logs node.
- Select Security.
- Select one Logon Category event
- Select the Details tab.
- Click the XML View toggle.
- The log details show an authentication on behalf of the user imauser using Kerberos.
Conclusion
In this set of exercises, you have learned how to:
- Deploy the Unified Access Gateway on two NICs and configure a Web reverse proxy instance using a PowerShell script.
- Configure Internet Information Server (IIS) to support Kerberos authentication Set up Kerberos delegation on the service account.
- Configure a Web application (SAML) on Workspace ONE Access.
- Configure identity bridging for a Web reverse proxy instance on Unified Access Gateway to provide single sign-on (SSO) to legacy Web applications.
For more information, see the Omnissa Unified Access Gateway documentation.
Configuring Certificate to Kerberos Option for Identity Bridging
Unified Access Gateway in identity bridging mode acts as the service provider that passes user authentication to the configured legacy applications.
When you use Workspace ONE Web to access the target website; the target website acts as the reverse-proxy. Unified Access Gateway validates the presented certificate. If the certificate is valid, the browser displays the user interface page for the back-end application.
This section helps you to configure the certificate to Kerberos option in identity bridging to provide SSO for legacy web applications using Workspace ONE Web and Unified Access Gateway. You also learn how to leverage Workspace ONE UEM to deploy and manage the user certificate life cycle on the device, automating the entire process and eliminating manual configurations.
Any browser can be used to access the internal web application through Unified Access Gateway; however, other browsers open a dialog requesting the user certificate. Workspace ONE Web does not request a user certificate initially, as the browser checks the local certificate store for a certificate that matches the one requested, therefore providing a silent experience to the end user. In this scenario, you can still use Workspace ONE UEM to deploy and manage the user certificate on managed devices.
These exercises cover a Unified Access Gateway 3.3 deployment integrated with Workspace ONE UEM 9.6. Procedures include:
- Deploying a Unified Access Gateway appliance with two NICs, one facing the internet and the second one dedicated to management and back-end access.
- Configuring Identity Bridging on Unified Access Gateway.
- Configuring AirWatch Cloud Connector o integrate Microsoft AD with Workspace ONE UEM.
- Configuring CA integration in Workspace ONE UEM.
- Configuring Workspace ONE Web to use certificate for authentication.
- Testing SSO access to an internal web application performing certificate to Kerberos authentication through Workspace ONE Web.
The steps are sequential and build upon one another, so make sure that you complete each step before going to the next step.
Authentication Flow
The following diagram describe the authentication flow that you will configure in this section.
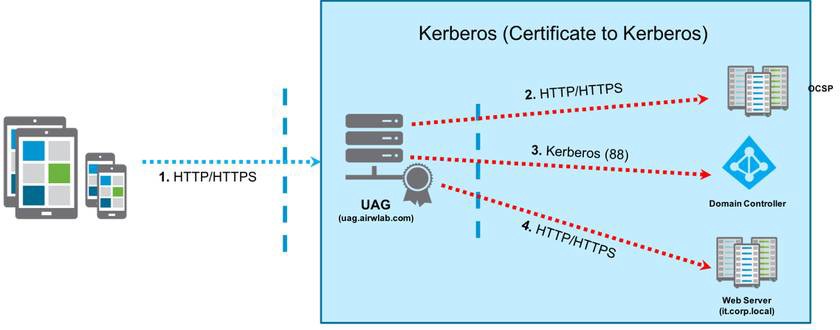
- Client navigates to application URL (https://uag.airwlab.com/itbudget). (The client certificate is sent to Unified Access Gateway in TLS handshake).
- Unified Access Gateway checks if the client certificate is valid or revoked.
- Unified Access Gateway extracts the client’s UPN from the certificate and requests a Kerberos ticket from Active Directory (CORP.LOCAL) on behalf of that user.
- Unified Access Gateway authenticates against the internal web server (https://it.corp.local) using the Kerberos ticket obtained from AD.
Prerequisites
Before you can perform the steps in this exercise, you must install and configure the following components:
- Omnissa Workspace ONE UEM SaaS or on-premises latest version
- vSphere ESX host with a vCenter Server (vSphere 6® and later)
- vSphere data store and network to use
- PowerShell script running on Windows 8.1 or later machines, or Windows Server 2008 R2 or later
- Windows machine running the PowerShell script with OVF Tool command installed
- Unified Access Gateway PowerShell script, such as uagdeploy-VERSION.ZIP (download from my.workspaceone.com, and extract the files into a folder on your Windows machine)
- iPhone, iPad, and iPod Touch devices running later OS version
- CA Root and Intermediate certificate, and user certificate to configure Device Certificate Authentication
Ensure the following settings are enabled in the Workspace ONE UEM Console:
- Organization Group created and set as Customer Type
- Device Root Certificate issued
- REST API Key generated at the Organization Group where Workspace ONE Tunnel will be enabled
Integrating Active Directory and Workspace ONE UEM
This section helps you to integrate Microsoft AD with Workspace ONE UEM. This integration is required for a few reasons:
- The user certificate is generated based on the enrolled user information.
- Workspace ONE UEM sends the certificate request to Microsoft CA. This request is based on a certificate template that requires the user information.
- To perform Kerberos authentication, a domain account is required.
Perform these exercises on the machine where you will install the AirWatch Cloud Connector.
Navigate to All Settings
- In the Workspace ONE admin console, select Groups & Settings.
- Select All Settings.
Enable AirWatch Cloud Connector
In this step, you enable AirWatch Cloud Connector, which acts as a gateway between your devices and internal services such as Microsoft AD, Certificate Authority, SMP Server, and so on.
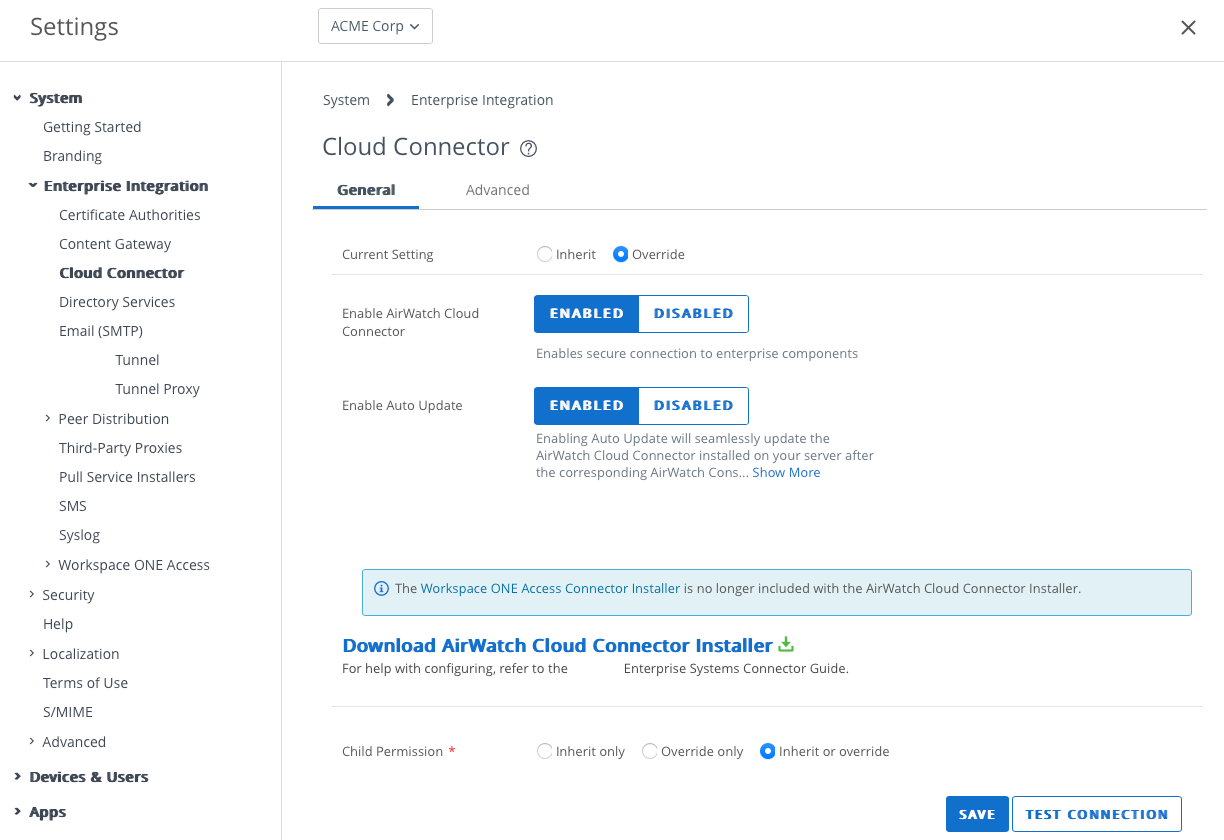
- Select System.
- Select Enterprise Integration.
- Select AirWatch Cloud Connector.
- Select Override.
- Select Enabled for AirWatch Connector.
- Select Enable for Enable Auto Update.
- Click Save.
Download AirWatch Cloud Connector
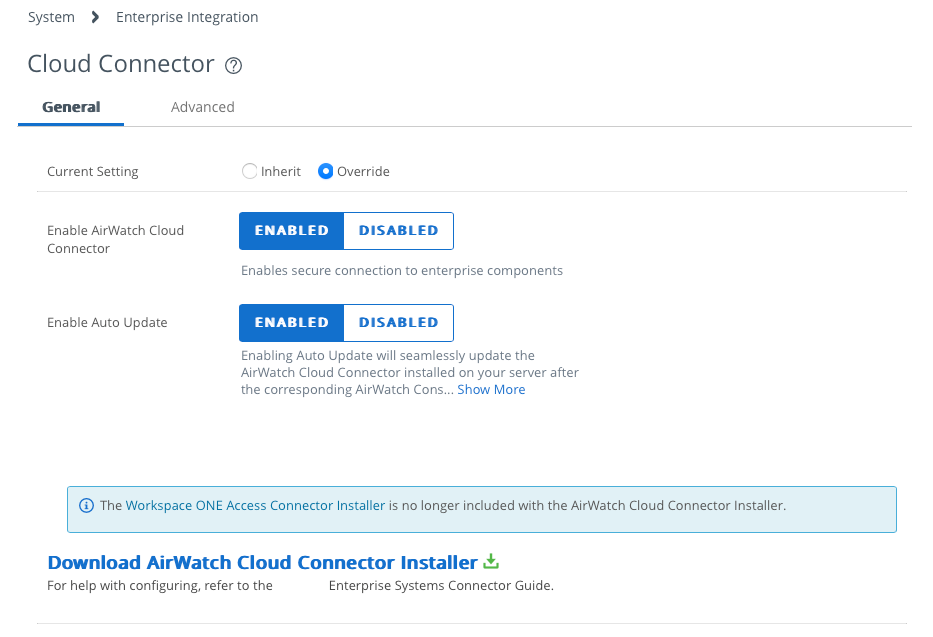
- Click Download AirWatch Cloud Connector Installer.
- Create a password for the AirWatch Cloud Connector Installer Certificate.
When you run the installer, a password is requested. This password allows the import of current settings to the AirWatch Cloud Connector.
After you provide the password, the installer is downloaded to the Downloads folder.
- Enter the Password.
- Confirm the password.
- Click Download.
Install the AirWatch Cloud Connector
Ensure you are logged into the machine where you will install AirWatch Cloud Connector.
Confirm the AirWatch Cloud Connector Installation was Successful
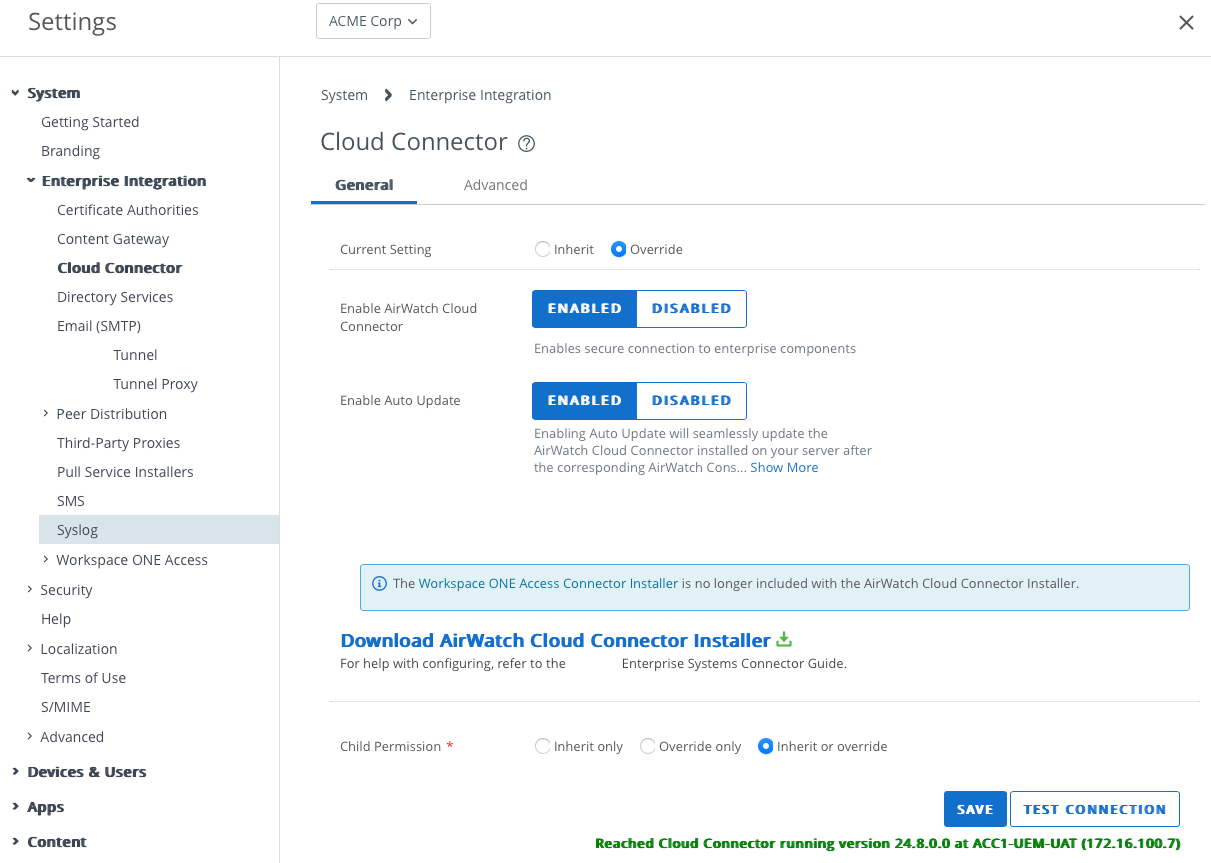
In the Workspace ONE UEM Console:
- In the AirWatch Cloud Connector settings, scroll down to find the Test Connection button.
- Click Test Connection. Ensure the Reached Cloud Connector running version XXX at SERVER NAME is displayed.
Integrate Microsoft AD and Workspace ONE UEM
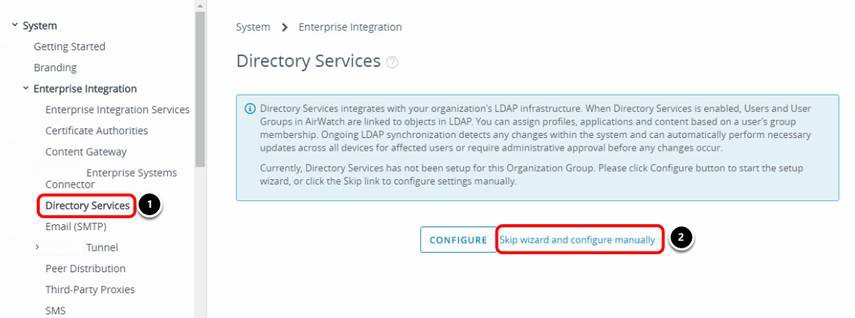
To integrate Active Directory with Workspace ONE UEM, navigate to the Directory Services settings.
- Select Directory Services under Enterprise Integration.
- Click Skip wizard and configure manually.
Configure AD Server Settings

- Select Override for Current Settings.
- Select Active Directory for Directory Type.
- Enter the Server, for example, controlcenter.corp.local.
- Select NONE for Encryption Type.
- Enter 389 for Port.
- Enter 3 for Protocol Version.
- Select Disabled for Use Service Account Credentials.
- Select GSS-Negotiate for Bind Authentication Type.
- Enter the Bind UserName, for example, corp\imaservice.
- Enter the Bind Password.
- Enter the Domain, for example, CORP.
- Select the User tab located on the top.
Configure AD User Settings
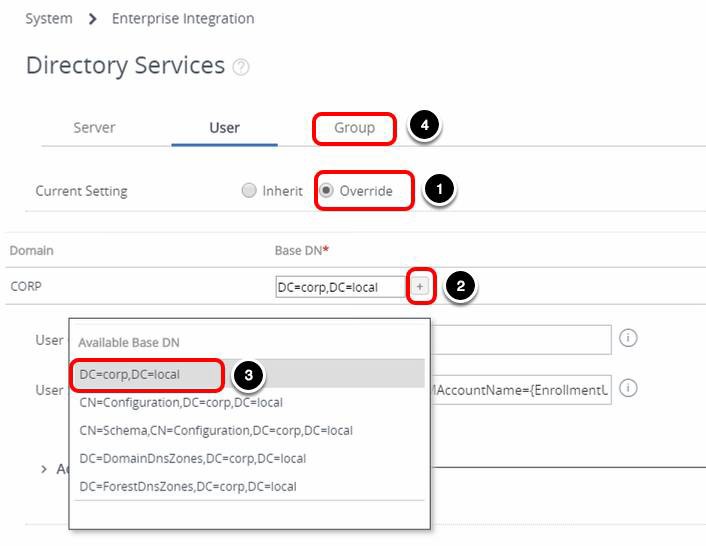
- Select Override for Current Settings.
- Click the plus icon next to CORP domain.
- Select the Base DN, for example, DC=corp, DC=local.
- Select the Group tab.
Configure AD Group Settings
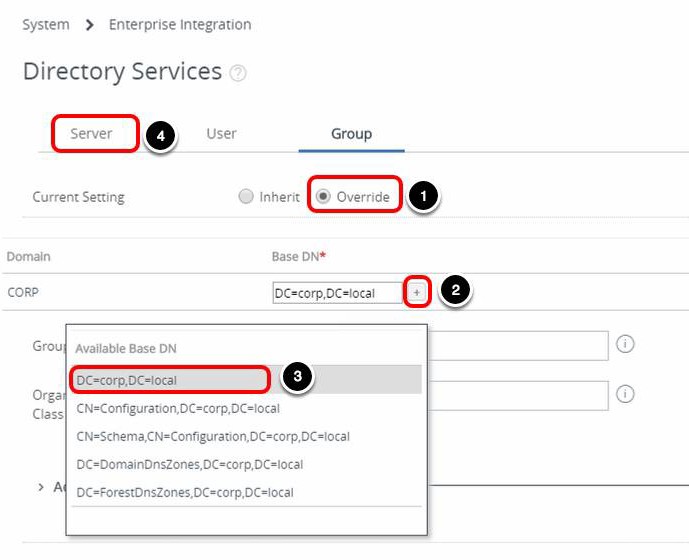
- Select Override for Current Settings.
- Click the plus icon next to CORP domain.
- Select the Base DN, for example, DC=corp, DC=local.
- Select Server to return to the server settings.
Test AD Connection
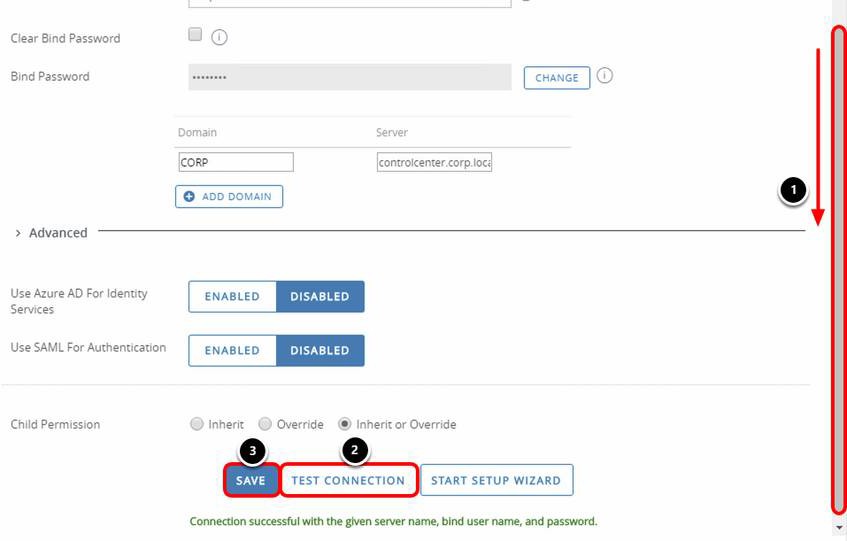
- Scroll down to find the Test Connection button.
- Click Test Connection and check for the message Connection successful with the given server name, bind username, and password.
- Click Save.
Integrating Certificate Authority with Workspace ONE UEM
This section helps you to integrate Microsoft Certificate Authority (CA) with Workspace ONE UEM, and configure the Certificate Template to be requested by Workspace ONE Web.
This integration is required for a few reasons:
- Workspace ONE UEM requests and delivers the user certificate on the user device, fully automated.
- Workspace ONE UEM revokes the certificate when the device is unenrolled.
- Workspace ONE Web presents the user certificate to Unified Access Gateway when accessing the internal website, to initiate the validation process and transformation of the request to Kerberos.
Add Certificate Authority to Workspace ONE UEM
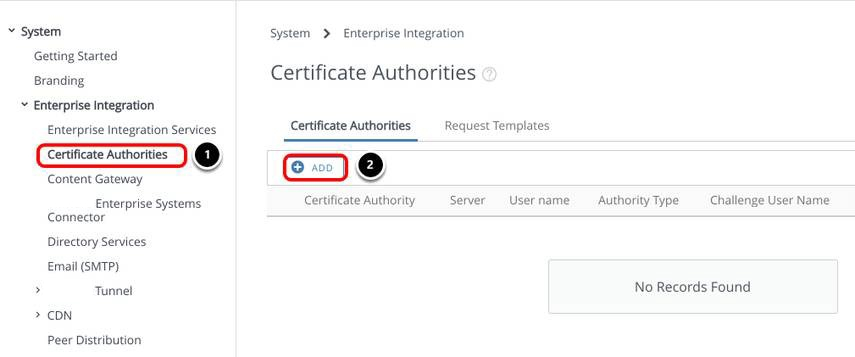
In the Workspace ONE UEM console:
- Navigate to System > Enterprise Integration > Certificate Authorities.
- Click Add under the Certificate Authorities tab.
Configure Certificate Authority
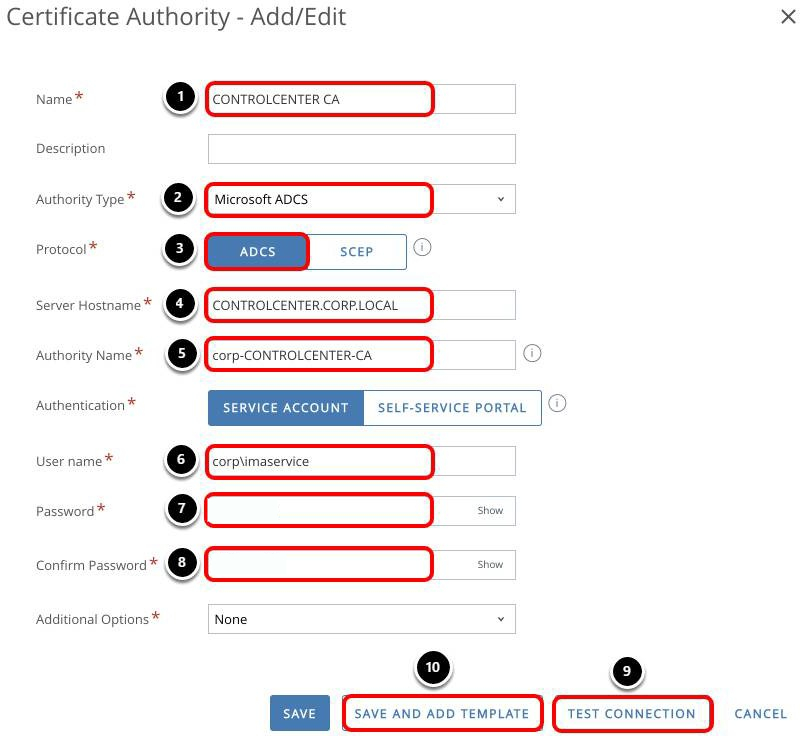
- Enter a name, for example, CONTROLCENTER CA.
- Select Microsoft ADCS.
- Select ADCS.
- Enter the Server Hostname, for example, controlcenter.corp.local.
- Enter the Authority Name, for example, corp-CONTROLCENTER-CA.
- Enter the User name, for example, corp\imaservice. This service account must have permission to request, renew, and revoke certificates on the CA.
- Enter the Password.
- Enter the password again.
- Click Test Connection. You should see the message Test is successful .
- Click Save and Add Template.
Add Certificate Template
In this step, you add the certificate template that associates the CA used to generate the user certificate.
The properties of this certificate template must match the template defined on the CA, otherwise the user cannot authenticate using the certificate.
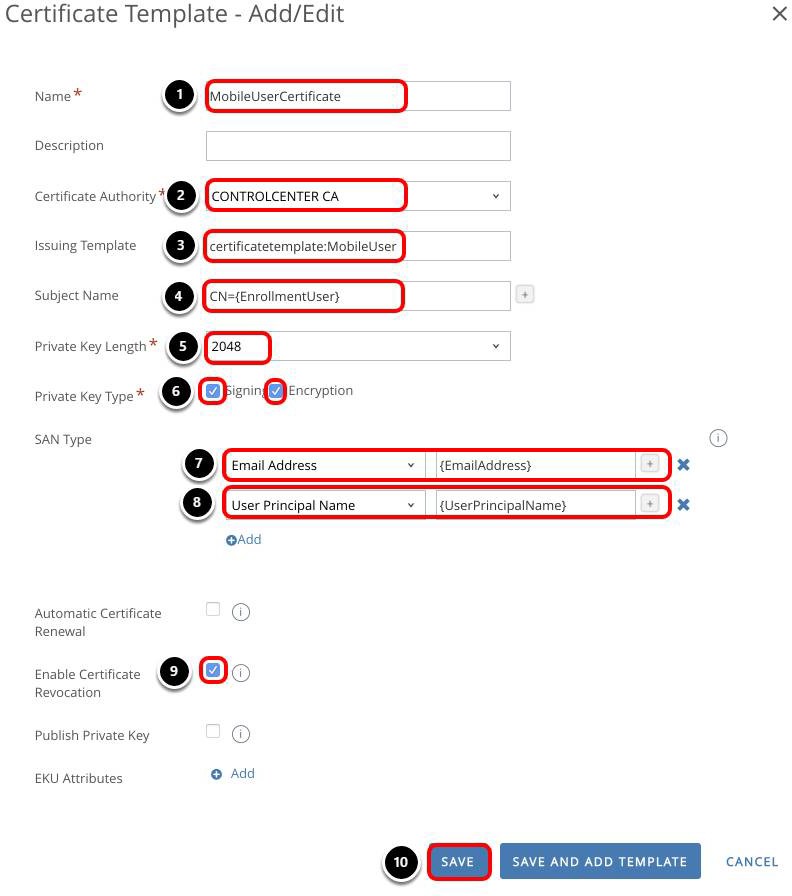
- Enter a Name, for example, MobileUserCertificate.
- Select the Certificate Authority, for example, CONTROLCENTER CA.
- Enter certificatetemplate:MobileUser for Issuing Template. The issuing template must match the template on the CA. In this example, the template name is MobileUser.
- Enter CN={EnrollmentUser} for Subject Name.
- Select 2048 for Private Key Length.
- Select both the Signing and Encryption options for Private Key Type.
- For SAN Type, select Email Address and {Email Address}.
- Add a second SAN Type and select User Principal Name and {UserPrincipalName}.
- Select the Enable Certificate Revocation check box.
- Click Save.
Confirm the Certificate Authority was Created
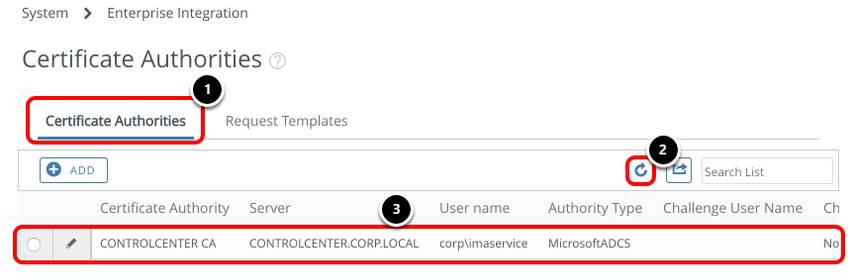
- Select the Certificate Authorities tab.
- Click Refresh if needed.
- Confirm that the CONTROLCENTER.CORP.LOCAL Certificate Authority was added.
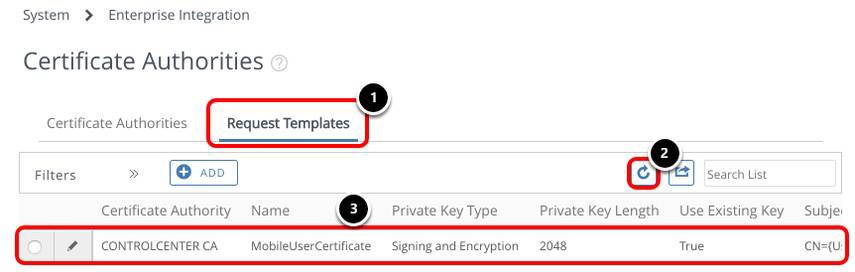
Confirm the Certificate Request Template was Created
- Select the Request Templates tab.
- Click Refresh if needed.
- Confirm the MobileUserCertificate Request Template was added.
Validate the Certificate Template
There are several ways to validate that the Certificate Template is available on Microsoft CA. If you are using Enterprise Microsoft CA, open the Certificate Authority and you will see a folder named Certificate Template. If you are using Standalone CA (as in this exercise), use mmc.exe to see the list of templates.
Launch MMC on your machine. In this example, the MMC snap-in is available on the task bar.
Select MobileUser Template
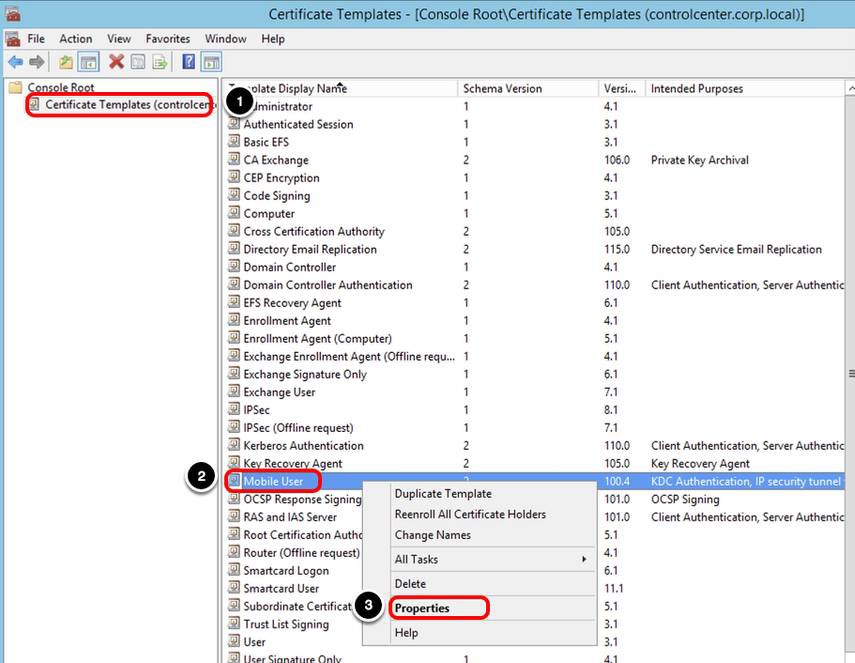
- Click Certificate Templates.
- Right-click the user template, for example, Mobile User.
- Click Properties.
The next steps help you to locate some of the template attributes that you defined in the Workspace ONE UEM console.
Validate Template Name
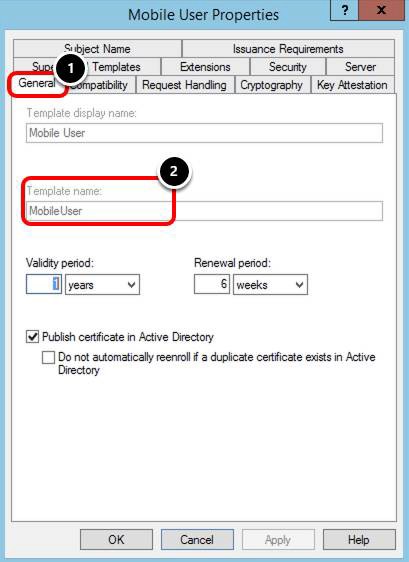
- Select the General tab.
- Validate your Template name, for example, MobileUser.
Validate Private Key Type
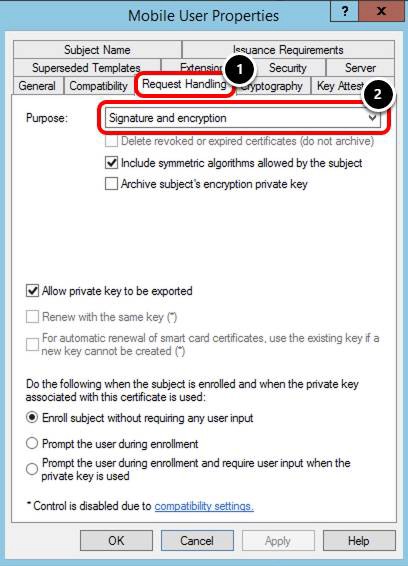
- Select the Request Handling tab.
- Confirm the Purpose is set to Signature and encryption.
Validate Private Key Length
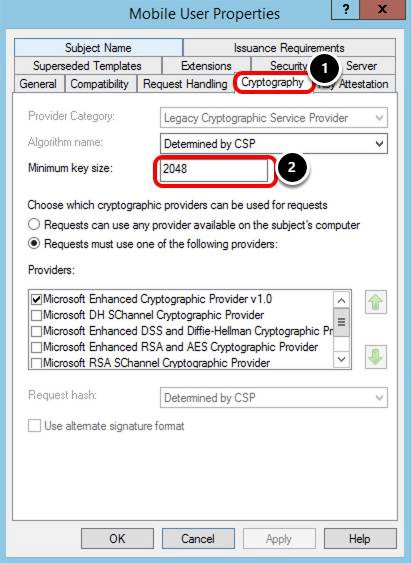
- Select the Cryptography tab.
- Ensure the Minimum key size is 2048.
Validate Subject Name Request
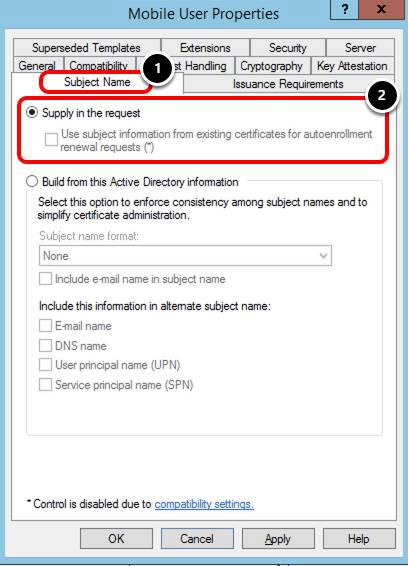
- Select the Subject Name tab.
- Ensure Supply in the request is selected.
Enabling Workspace ONE Tunnel in the Workspace ONE UEM Console
When the Tunnel edge service is enabled on the Unified Access Gateway appliance, it retrieves the Tunnel configuration from Workspace ONE UEM. Therefore, the Tunnel must be configured first in the Workspace ONE UEM Console, prior to deployment of the Unified Access Gateway appliance.
This section helps you to configure Tunnel in the Workspace ONE UEM console.
Open All Settings
- Select Groups & Settings.
- Select All Settings.
Configure Tunnel Settings
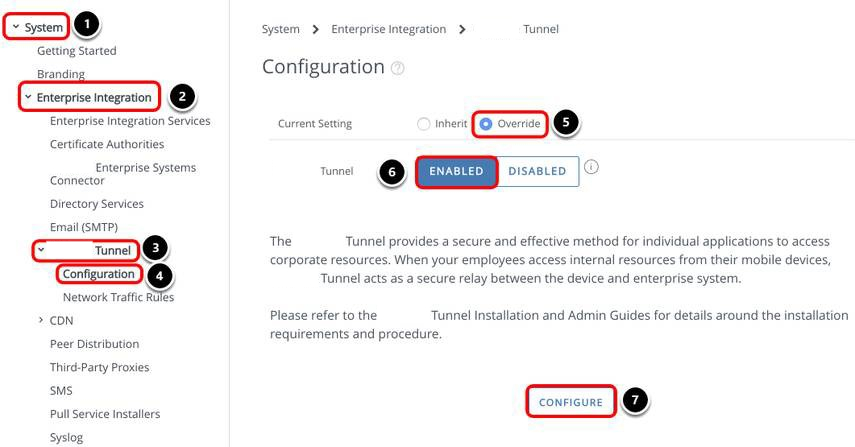
- Select System.
- Select Enterprise Integration.
- Select Tunnel.
- Select Configuration.
- Change the setting to Override.
- Select Enabled for Tunnel.
- Click Configure.
Configure Deployment Type
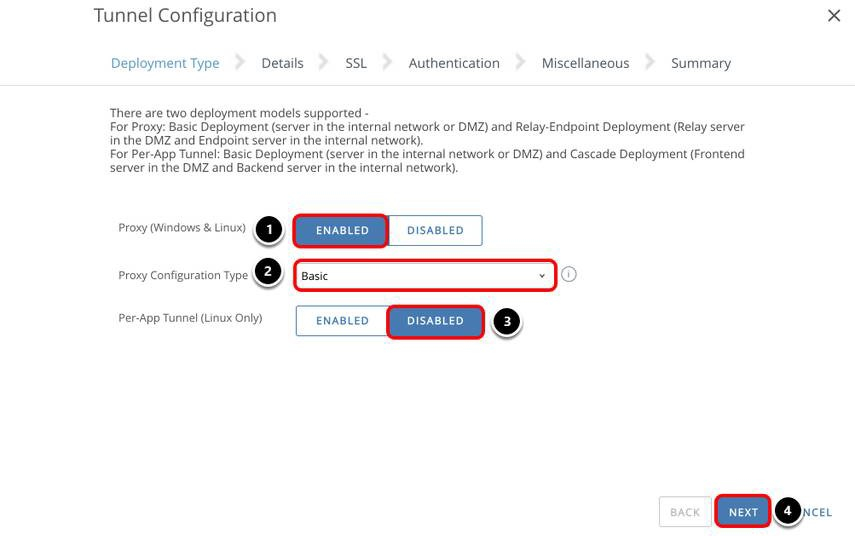
- Select Enabled for Proxy (Windows & Linux).
- Select Basic (Single-Tier) from the drop-down menu for VPN Configuration Type. The Unified Access Gateway appliance is deployed on a DMZ where the Tunnel edge service is enabled to communicate with the internal network.
- Select Disabled for Per-App Tunnel (Linux Only).
- Click Next to continue.
Enabling the Proxy option allows access to internal websites exclusively through Workspace ONE Web, which uses port 2020 to communicate with the front-end appliance. In this exercise, Proxy is not enabled.
Configure Hostname and Port Details
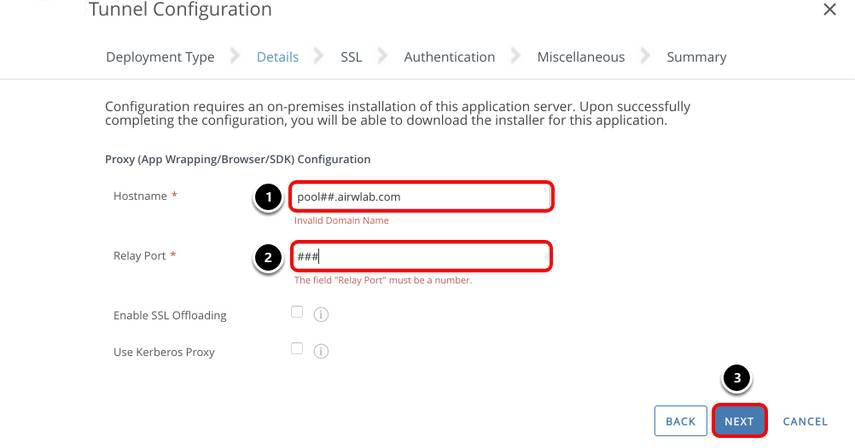
- Enter the Tunnel server host name for Hostname.
- Enter a Port number.
- Click Next.
Configure Tunnel SSL Certificate
- Ensure Use Public SSL Certificate is selected.
- Click Upload and navigate to your certificate. This example uses the airwlab.pfx file in C:\AW Tools.
- Click Next.
Select Authentication
- Select Default.
- Click Next.
Select Miscellaneous Details
- Select Disabled for Access Logs.
- Click Next to continue.
Confirm Tunnel Settings
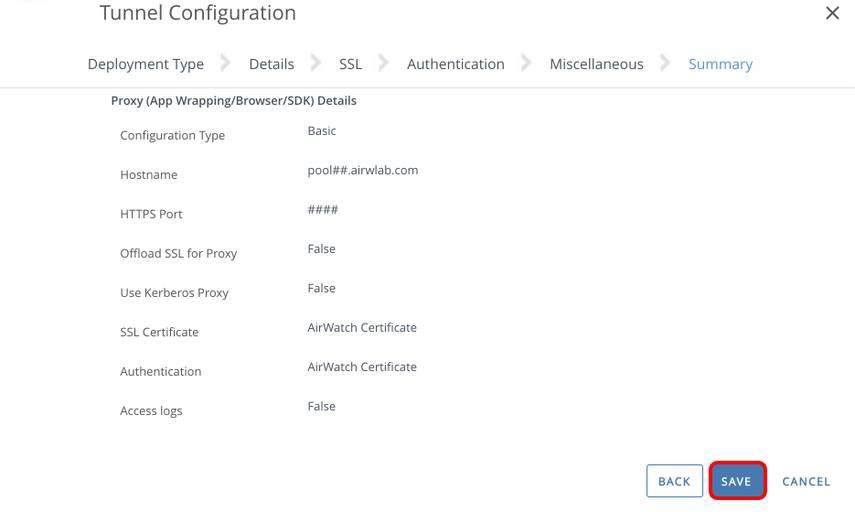
Verify that the configuration summary is correct. Click Save to continue.
Download the Unified Access Gateway Appliance
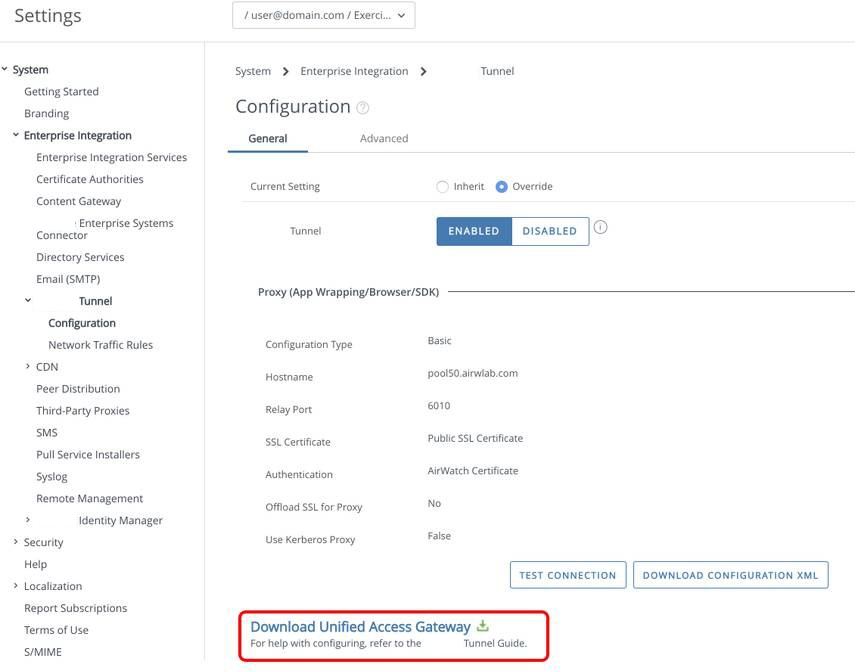
After the configuration is saved, click Download the Unified Access Gateway to download the virtual appliance. Extract the ZIP file on the Windows machine where you will install Unified Access Gateway.
Workspace ONE Web Application Settings and Policies
The Settings and Policies section of the Workspace ONE UEM Console contains settings that control security, behavior, and the data retrieval of specific applications. The settings are often called SDK settings because they run on the Workspace ONE SDK framework.
You can apply these SDK features to applications built with the Workspace ONE SDK, to supported Workspace ONE UEM applications, and to applications wrapped by the Workspace ONE App Wrapping engine. The same features can be applied because the Workspace ONE SDK framework processes the functionality.
Workspace ONE Web can use these Setting and Policies, which can be based on two types of SDK settings:
- Default settings work well across organization groups, applied to large numbers of devices.
- Custom settings work with individual devices or for small numbers of devices with applications that require special mobile application management (MAM) features.
In this exercise, you change the default settings of Workspace ONE Web.
Configure Workspace ONE Browser
- Select Apps.
- Select Browser.
- Select Override for Current Setting.
- Scroll down to find the Mode section.
Configure Browser Mode
- Select Disabled for Kiosk Mode.
- Enter your intranet website for Home Page URL.
- Select Allow for Selection Mode.
- Enter your Allowed Site URLs, for example, *.corp.local and *.airwlab.com.
- Click Save.
Configure Security Policies
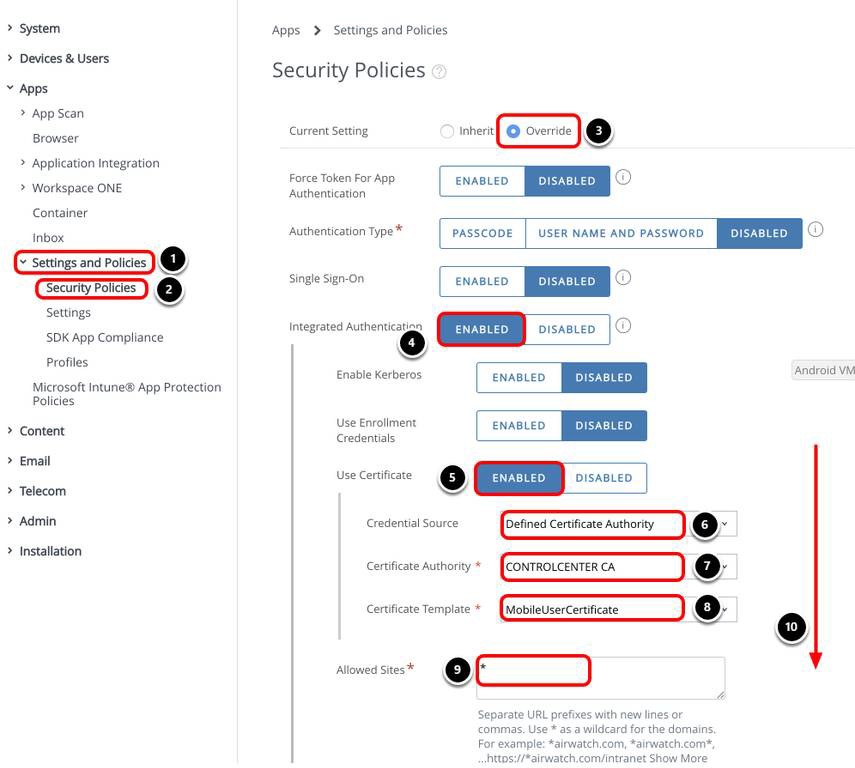
- Select Settings and Policies.
- Select Security Policies.
- Select Override for Current Setting.
- Select Enabled for Integrated Authentication.
- Select Enabled for Use Certificate.
- Select Defined Certificate Authority for Credential Source.
- Select the Certificate Authority, for example, CONTROLCENTER CA.
- Select the Certificate Template, for example, MobileUserCertificate.
- Enter * for Allowed Sites.
- Scroll down to the end of the page.
This configuration allows the user credentials to be passed on to allowed sites for integrated authentication. In this example, the user certificate is the user credential.
Configure App Tunnel Mode Settings
- Select Enabled for AirWatch App Tunnel.
- Select Tunnel - Proxy for App Tunnel Mode.
- Enter the App Tunnel URLs, for example, *.corp.local and *uag.airwlab.com*.
- Click Save.
In this step, you define how Workspace ONE Web redirects the traffic to access internal resources. Any requests from Workspace ONE Web that match the App Tunnel URLs, are redirected through Tunnel Proxy.
Preparing Workspace ONE Tunnel and Reverse Proxy INI Settings for Deployment
This section covers the required INI settings to configure Tunnel and web reverse proxy during the Unified Access Gateway appliance deployment.
Configure the General Deployment settings
The INI file contains all the configuration settings required to deploy the Unified Access Gateway appliance.
This exercise uses the uag-Cert-to-Kerberos.ini file and is configured for a Unified Access Gateway appliance called uag-Cert, that has two NICs—NIC one is set to internet facing and NIC two for back end and management.
Edit the INI File
Navigate to your Unified Access Gateway INI file. In this example, the INI file is located in UAG Resources.
- Click the File Explorer icon from the task bar.
- Select Desktop.
- Select UAG Resources.
- Right-click the ini file, for example, uag-Cert-to-Kerberos.
- Click Edit with Notepad++.
General and Network Settings
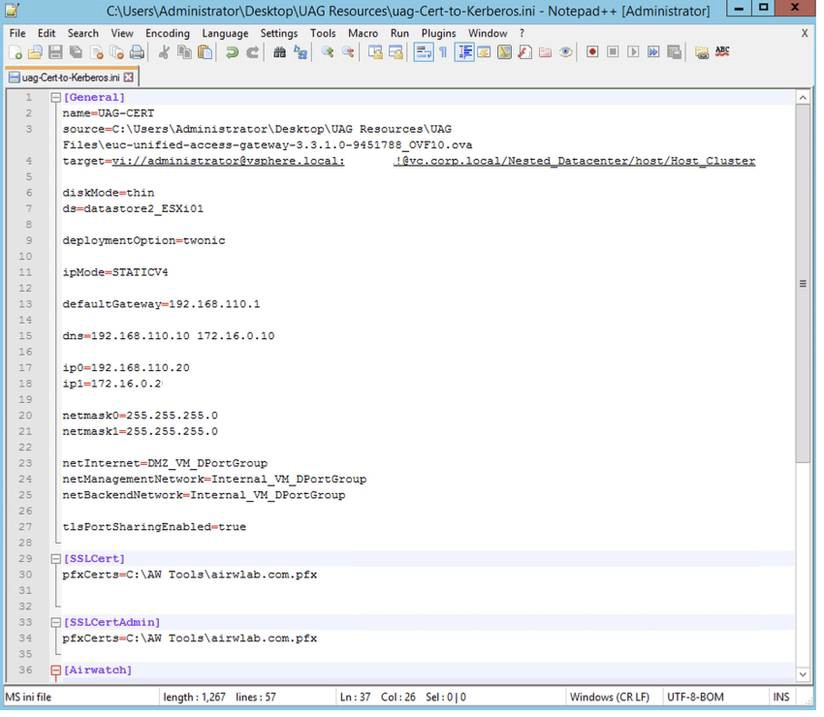
In this example, the settings are already filled out. The General section includes details such as deployment location and network configuration for the Unified Access Gateway appliance.
The SSLCert and SSLCertAdmin sections contain SSL certificate location for the administrator and Internet interfaces.
Configuring Workspace ONE Tunnel Settings
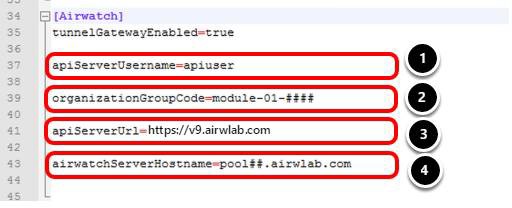
The AirWatch section contains the required parameters to enable the Tunnel edge service on your Unified Access Gateway appliance.
- Enter the apiServerUsername.
- Enter your Group ID for the Organization Group.
- Enter the apiServerUrl, for example, https://v9.airwlab.com.
- Enter the airwatchServerHostname, for example, https://pool##.airwlab.com.
During the Unified Access Gateway deployment, the PowerShell script prompts you for the apiServerUsername password.
Validate Web Reverse Proxy Configuration
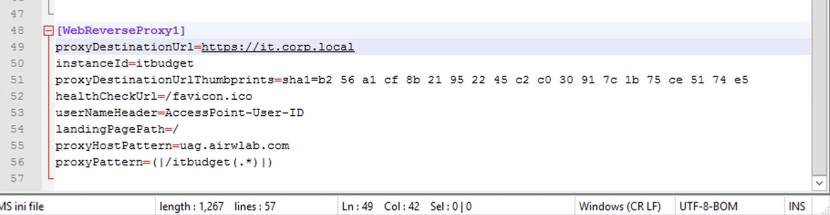
A web reverse proxy instance called ITBUDGET has been added to this INI file. You use this instance to enable identity bridging and perform certificate to Kerberos authentication in a later exercise.
In this exercise, proxyDestinationUrl is set to https://it.corp.local. For your environment, set proxyDestinationUrl to an intranet address.
Save INI File
Click the Save icon to save your changes.
Deploying Unified Access Gateway Appliance
After you have configured the INI file for your Unified Access Gateway deployment, the next step is to run the uagdeploy.ps1 PowerShell script passing the INI as a parameter.
Deploy Unified Access Gateway using PowerShell
Click the PowerShell icon and run the script.
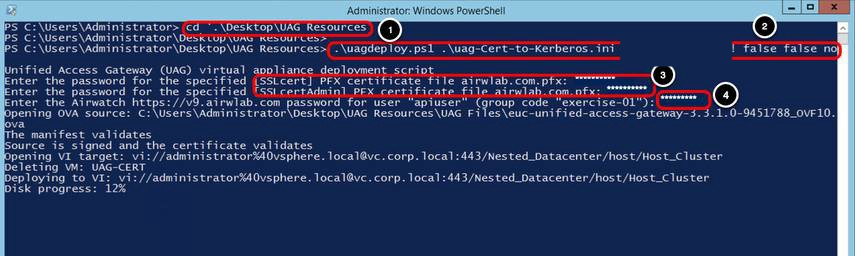
After you run the script, it prompts for input.
- Navigate to the folder containing your INI file. For example, enter cd '.\Desktop\UAG Resources' then press Enter.
- Enter .\uagdeploy.ps1 .\<uag-tunnel>.ini <password1> <password2> false false no then press Enter.
Replace <uag-tunnel> with your INI file name.
Replace <password1> with the root password for the UAG appliance.Replace <password2> with the administrator password for REST API management access.
The first false is to not skip the validation of signature and certificate.
The second false is to not skip SSL verification for the vSphere connection.
The no is to not join the CEIP program.
- Enter the password for the certificated that will be used on the following fields SSLcert and SSLcertAdmin.
- Enter the password for the apiuser previously defined on the INI file, which allows Unified Access Gateway to obtain the Workspace ONE Tunnel settings from Workspace ONE UEM.
To avoid a password request for the certificate, remove the pfxCert values and provide a PEM certificate in the INI file. Set the pemCerts and pemPrivKey for the SSLCert and SSLCertAdmin sections in the INI file.
The deployment starts and you can follow the progress in the same window or on your vSphere Web Client.
Confirm the PowerShell Script Deployment Completes
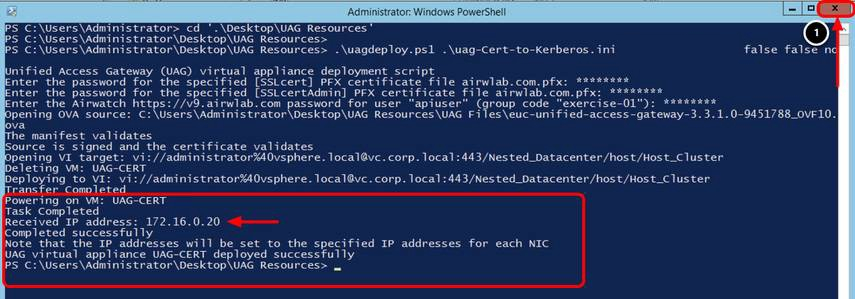
- Confirm the deployment has been completed successfully. The Completed successfully text is shown in the output.
- Click Close.
- After a successful deployment, the script automatically powers on the VM UAG-CERT.
- The Received IP address presented by the script log is a temporary IP; the final IPs for NIC one and NIC two are assigned to the Unified Access Gateway appliance during the first start. Return to the vSphere Web Client and validate the IP address in the next step.
Validate Unified Access Gateway Deployment
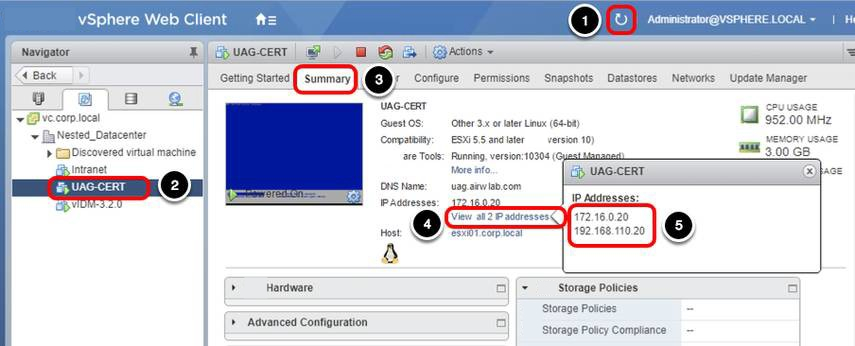
Return to the vSphere Web Client tab in Google Chrome.
- If you do not see the UAG-CERT VM under Nested_Datacenter, you may need to click Refresh.
- Click UAG-CERT.
- Click the Summary tab.
- Click View all 2 IP addresses.
In this example, the IP addresses are:
192.168.110.20
172.16.0.20
Important: If the Unified Access Gateway appliance does not finalize the configuration during the first startup, you receive an error message from vSphere Web Client. If that happens, wait for the appliance to finalize, and refresh the entire Google Chrome browser.
Log In to Unified Access Gateway Administration Console
- Click the New Tab button to open a new tab.
- Navigate to the Unified Access Gateway administration console URL, for example,
- https://uagmgt-int.airwlab.com:9443/admin.
- Enter the username, for example, admin .
- Enter the password.
- Click Login.
Validate Configuration Settings
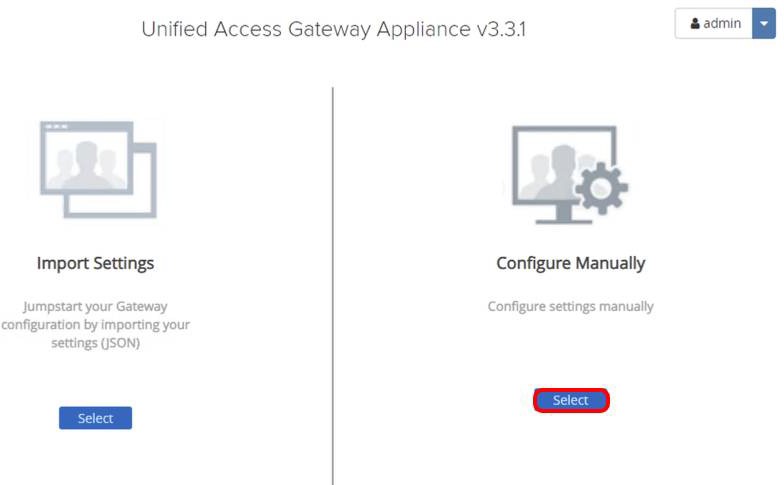
A successful login redirects you to the following screen. Click Select to configure settings manually.
Confirm the Web Reverse Proxy Instance is Running
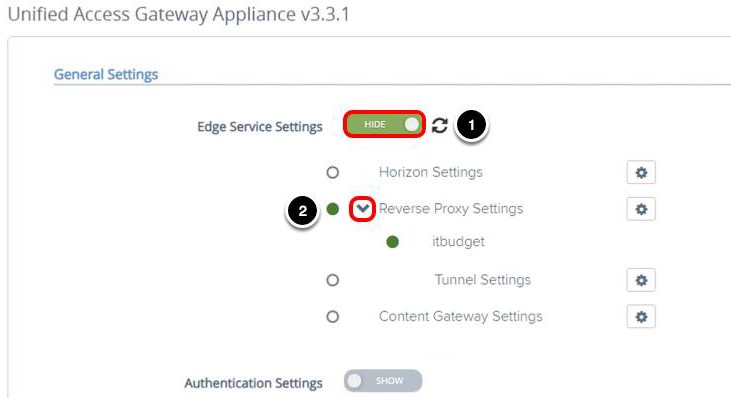
Follow the next steps to confirm that a web reverse proxy instance named itbudget has been automatically configured.
- Click SHOW, after you click SHOW, it changes to HIDE.
- Click the arrow next to Reverse Proxy Settings.
- Confirm that itbudget exists.
Keep the administration console open as the next step is to enable the identity bridging feature for itbudget.
Test Tunnel Proxy Connection
Return to the Workspace ONE UEM console to perform a test connection between Tunnel Proxy and Workspace ONE UEM API, AWCM, and device service.
- Select Groups & Settings.
- Select All Settings.
Perform Test Connection for Tunnel Proxy
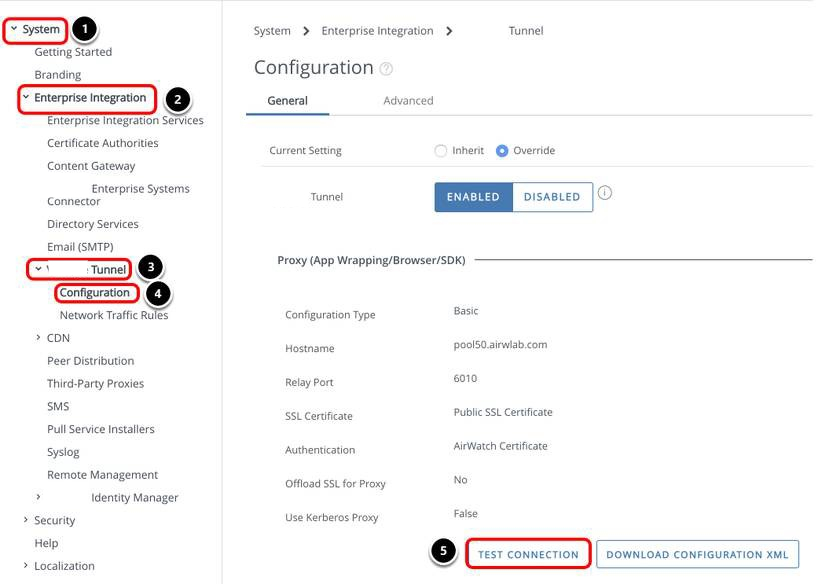
- Select System.
- Select Enterprise Integration.
- Select Tunnel.
- Select Configuration.
- Click Test Connection.
Verify Test Connection Result
If all test connection results are green, your environment is setup correctly and you can proceed to the next steps. Click Cancel or the X button to close the screen.
Configuring Identity Bridging on Unified Access Gateway
You have deployed the Unified Access Gateway appliance, confirmed that the itbudget web reverse proxy was configured, and tested the Tunnel Proxy connection settings. The next steps are performed in the Unified Access Gateway administration console.
Return to the Unified Access Gateway Administration Console
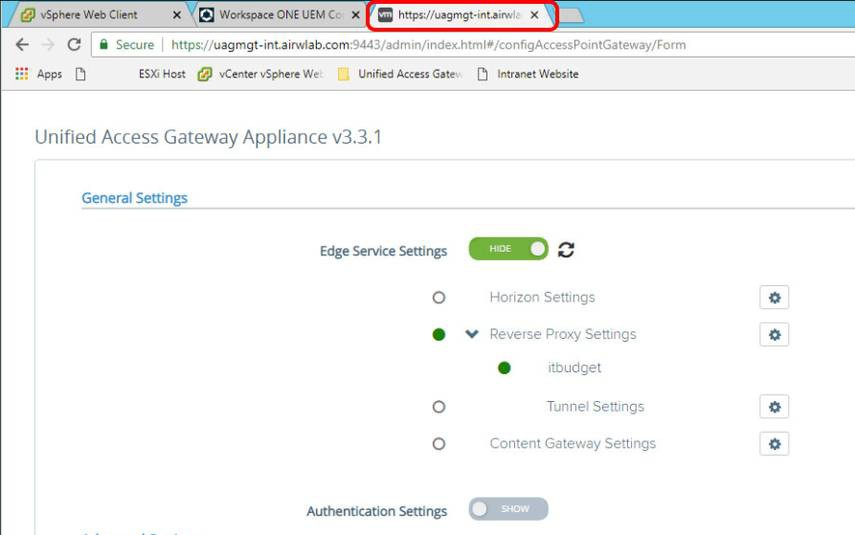
Return to the Unified Access Gateway administration console.
Configure Certificate Authentication Settings
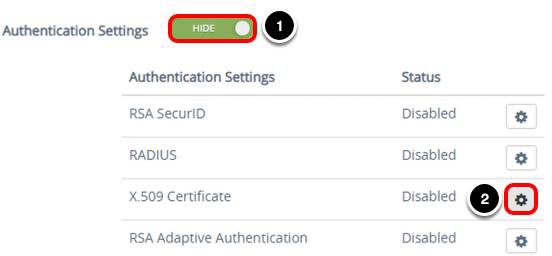
- Click Show for the Authentication Settings.
- Click the gear icon next to X.509 Certificate.
Upload Certificate to Unified Access Gateway Appliance
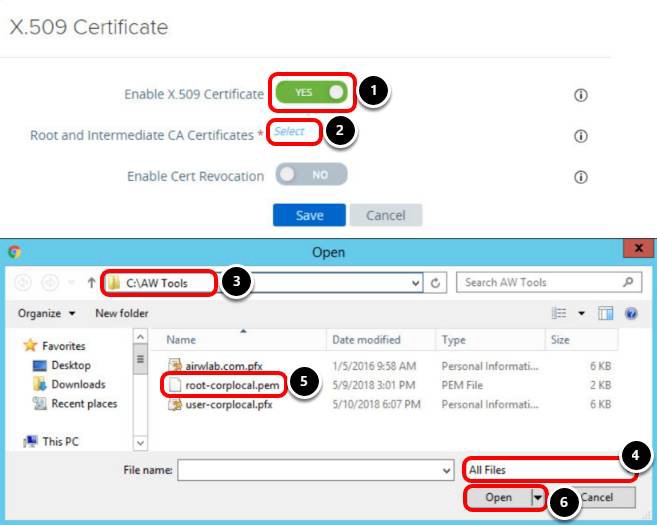
- Click NO to enable X.509 Certificate. After you click NO, the toggle changes to YES and you will see additional options.
- Click Select to upload the Root and Intermediate CA Certificates.
- Navigate to your certificate location, for example, C:\AW Tools and press Enter.
- Click the combo box and select All Files.
- Select your root certificate, for example, root-corplocal.pem.
- Click Open.
Enable Certificate Revocation
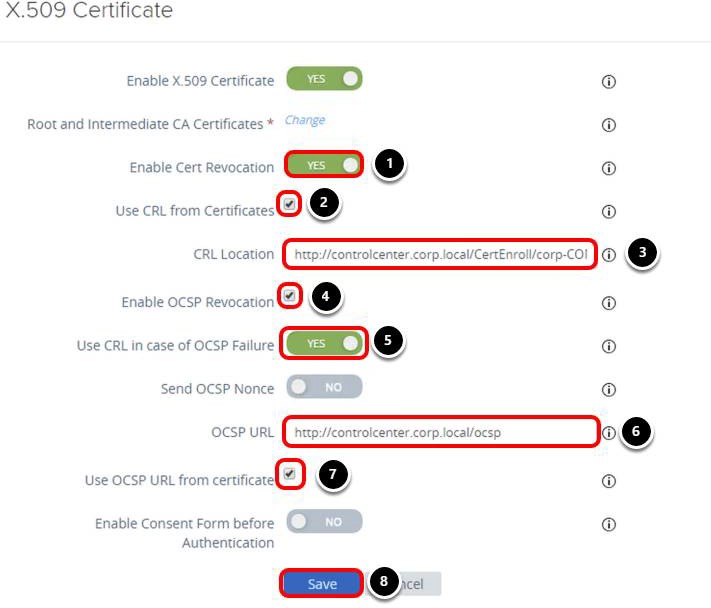
Point to the information icon to read a tip on each of the following steps.
Unified Access Gateway can perform a certificate revocation check in two ways; through CRL (Certificate Revocation List) or OCSP (Online Certificate Status Protocol). In this step, you configure Unified Access Gateway to use OCSP and in case it fails, to use the CRL.
- Click Yes to Enable Cert Revocation.
- Select the Use CRL from Certificate check box.
- Enter the CRL Location, for example, http://controlcenter.corp.local/CertEnroll/corp-CONTROLCENTER-CA.crl.
- Select the Enable OCSP Revocation check box.
- Click Yes for Use CRL in case of OCSP Failure.
- Enter the OCSP URL, for example, http://controlcenter.corp.local/ocsp.
- Select the Use OCSP URL from certificate check box.
- Click Save.
Configure Keytab

Click the gear icon for Upload Keytab Settings under Identity Bridging Settings.
Update the Keytab Settings

- Enter the Principal Name, for example, HTTP/it.corp.local@CORP.LOCAL.
- Click Select.
- Select Local Disk (C:) folder.
- Select the it.keytab file.
- Click Open.
- Click Save.
- After you click Save, you should see the message Keytab upload is successful.
Note: If you do not enter a Principal Name value, then the first Principal Name found in the keytab file will be used. If your keytab contains multiple Principal Names, you should manually enter Principal Name in Keytab Settings.
Configure Realm

Click the gear icon for Realm Settings under Advanced Settings.
Add a Realm Setting

Click Add.
Configure the Realm Settings
- Enter the Name of the realm, for example, CORP.LOCAL.
Note: This entry must use capital letters.
- Enter the Key Distribution Centers, for example, corp.local.
- Enter 3 for KCD Timeout (in seconds).
- Click Save.
- After you click Save, you should see the message Configuration saved successful.
Close the Realm Settings

You have configured the Realm settings. Click Close.
Configure OCSP Settings
The Online Certificate Status Protocol (OCSP) is an Internet protocol used for obtaining the revocation status of an X.509 digital certificate.
Unified Access Gateway sends the OCSP request to the specified URL and receives a response that contains information indicating whether or not the certificate is revoked. To allow that communication, the OCSP Signing Certificate must be uploaded to the Unified Access Gateway appliance.
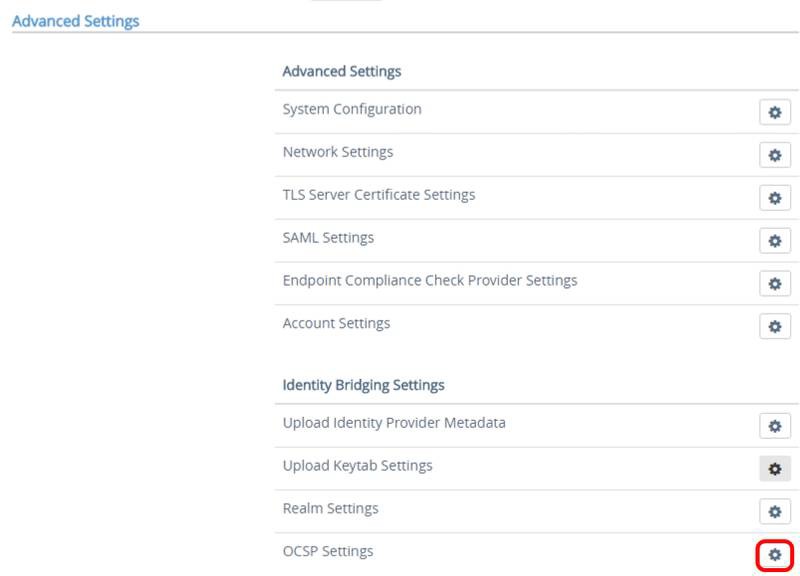
In Identity Bridging Settings, click the gear icon next to OCSP Settings.
How to Obtain the OCSP Signing Certificate
You can view and export the OCSP signing certificate in the Online Responder Management Console. You can install and configure the Online Responder Management Console from Windows Features. During the configuration, you are requested to create the OCSP signing certificate on the CA. Therefore, in a production scenario, you have two options to obtain the signing certificate.
In this example, the certificate has already been exported to C:\AW Tools, named ocsp.crt.
Add OCSP Setting
Click Add.
Select OCSP Signing Certificate
- Click Select.
- Navigate to C:\AW Tools.
- Change the filter to All Files.
- Select the ocsp.crt certificate — This is the certificate used to sign your OCSP Responder.
- Click Open.
- Click Save.
Confirm OCSP Settings
After you click Save, confirm that you see the OCSP signing certificate information. Click Close.
Configure Identity Bridging for Web Reverse Proxy Instance
Next, configure identity bridging for the Web reverse proxy instance; itbudget.
Open the ITBUDGET Reverse Proxy Settings
- If the Edge Service Settings are currently hidden, click the Show toggle to display the settings.
- Select the gear icon for Reverse Proxy Settings.
Select ITBUDGET Reverse Proxy Instance

Select the gear icon for the itbudget reverse proxy instance.
Update the ITBUDGET Identity Bridging Settings
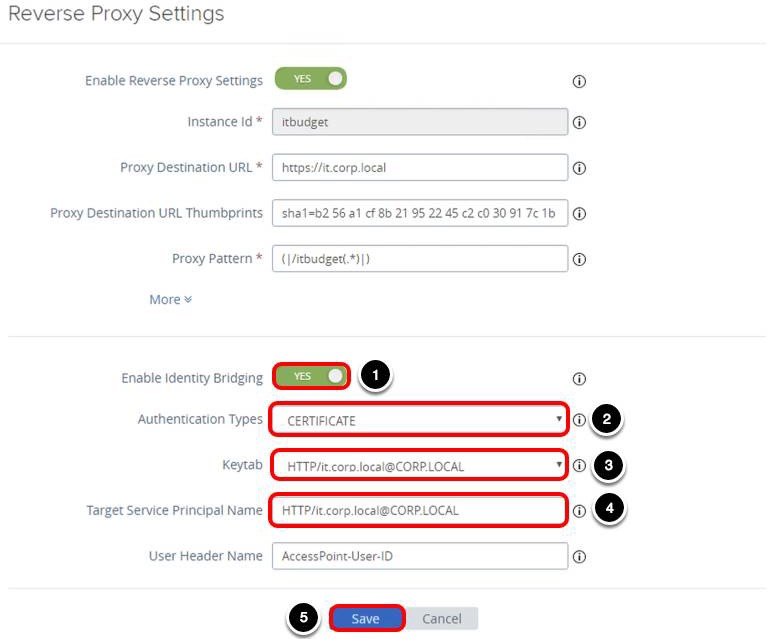
- Click NO to show the Enable Identity Bridging settings. After you click No, it changes to YES.
- Select CERTIFICATE for Authentication Types.
- Select the Keytab, for example, HTTP/it.corp.local@CORP.LOCAL.
- Enter the Target Service Principal Name, for example, HTTP/it.corp.local@CORP.LOCAL.
- Click Save.
Confirm the Identity Bridging Settings Saved

Confirm the Configuration is saved successfully message is displayed.
Enrolling an iOS or Android Device
In this section, enroll your iOS or Android device in Workspace ONE UEM by installing the Workspace ONE Intelligent Hub (formerly the AirWatch Agent). After enrollment deploy the Workspace ONE Web as managed application to the device and follow the next steps to test access to internal website.
Testing Access to Workspace ONE Web using SSO through Identity Bridging
Now that you have enabled identity bridging and configured the certificate to Kerberos option, you are ready to test access to Workspace ONE Web on your iOS device.
Launch Workspace ONE Web

Confirm that Workspace ONE Web is already installed on your device. Tap Browser to open the application.
Confirm Access to Intranet Site
In a previous exercise (Configure Browser Mode), you set an intranet address as the home page for Workspace ONE Web, for example, http://intranet.corp.local. This intranet page should now be showing.
In this example, Workspace ONE Web uses the Tunnel Proxy component of the Tunnel service to provide access to this internal website. However, you cannot access the intranet URL from any other external network.
Access ITBDUGET Website from Workspace ONE Web
Navigate to https://uag.airwlab.com/itbudget.
You should see the webpage without any prompt to provide any credentials.
Validate Kerberos Authentication
This section helps you to validate Kerberos authentication.
Launch Event Viewer
Open Event Viewer.
Connect to Event Viewer From Another Computer

- Right-click Event Viewer (Local).
- Select Connect to Another Computer.
Connect to INTRANET Server Event Viewer
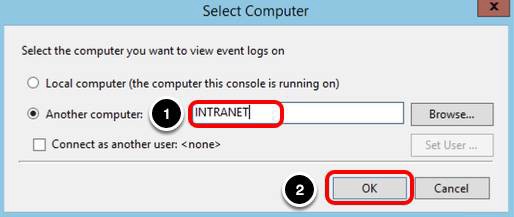
- Enter a name for Another Computer, for example, INTRANET.
- Click OK.
View Logon Logs

- Expand the Windows Logs node.
- Select Security.
- Select one Logon Category event.
- Select the Details tab.
- Click the XML View toggle.
- The log details show an authentication on behalf of the user PSILVER using Kerberos.
Validate Certificate requested by Workspace ONE Web
This section helps you to confirm that Workspace ONE Web requested a certificate for authentication.
Launch Certificate Authority

Click the Certificate Authority icon.
Open Most Recently Issued Certificate
- Click Issued Certificates.
- Select the last issued certificate.
- Right-click and select Open.
Confirm the Certificate Was Issued to Correct User
Confirm the most recently issued certificate was issued to psilver@corp.local.
Conclusion
In this set of exercises, you have learned how to:
- Deploy an Unified Access Gateway appliance with two NICs, one NIC is internet-facing and the second NIC is dedicated to management and back-end access. The Web reverse proxy configuration to access the intranet is automatically configured during deployment.
- Configure Internet Information Server (IIS) to support Kerberos authentication.
- Set up Kerberos delegation on the service account.
- Configure identity bridging on Unified Access Gateway.
- Configure Enterprise System Connector to integrate Microsoft AD with Workspace ONE UEM
- Integrate CA with Workspace ONE UEM.
- Configure Workspace ONE Web to use certificate for authentication.
- Access an internal website through Unified Access Gateway, performing certificate to Kerberos authentication through Workspace ONE Web.
For more information, see the Omnissa Unified Access Gateway documentation.
Summary and Additional Resources
This operational tutorial provided steps to configure web reverse proxy with device certificate authentication and to configure the identity bridging feature with two options: SAML to Kerberos and Certificate to Kerberos.
Additional Resources
For more information about Workspace ONE, explore the Omnissa Workspace ONE UEM page. This product page provides step-by- step guidance to help you level up in your Workspace ONE knowledge. You will find everything from beginner to advanced curated assets in the form of articles, videos, and labs.
Additionally, you can check out the Omnissa Workspace ONE and Horizon Reference Architecture which provides a framework and guidance for architecting an integrated digital workspace using Omnissa Workspace ONE and Omnissa Horizon.
Changelog
The following updates were made to this guide:
| Date | Description of Changes |
| 2024/09/17 | Rebranded the document. |
About the Author
This tutorial was written by:
- Andreano Lanusse, Omnissa alumni.
Feedback
Your feedback is valuable.
To comment on this paper, either use the feedback button or contact us at tech_content_feedback@omnissa.com.